Web Security
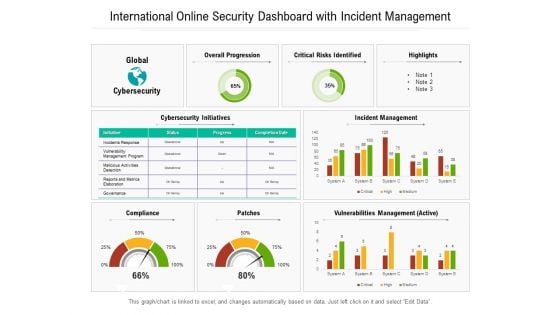
International Online Security Dashboard With Incident Management Ppt PowerPoint Presentation File Background PDF
Presenting this set of slides with name international online security dashboard with incident management ppt powerpoint presentation file background pdf. The topics discussed in these slides are management, vulnerabilities, cybersecurity. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
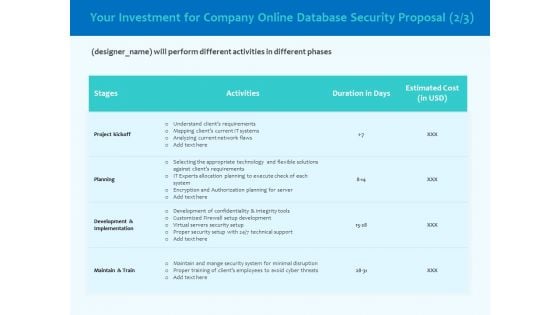
Best Data Security Software Your Investment For Company Online Database Proposal Infographics PDF
Presenting this set of slides with name best data security software your investment for company online database proposal infographics pdf. The topics discussed in these slides are project kickoff, planning, development and implementation, maintain and train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Create an editable Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Organizing Security Awareness In House Training Schedule We Will Implement Background PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and iot-based attack. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Organizing Security Awareness In House Training Schedule We Will Implement Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Organizing Security Awareness In House Training Schedule We Will Implement Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
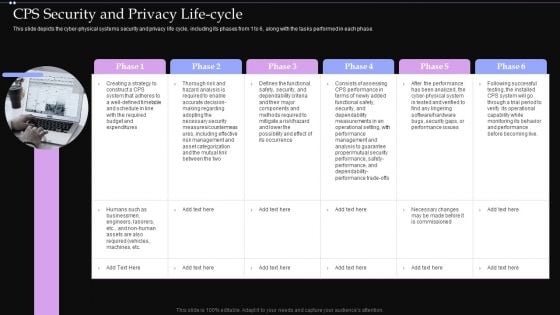
CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Information Security Cyber Safety Tips Protection Against Cyberattacks Ppt Slides Ideas PDF
Presenting information security cyber safety tips protection against cyberattacks ppt slides ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network, protect, systems, sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
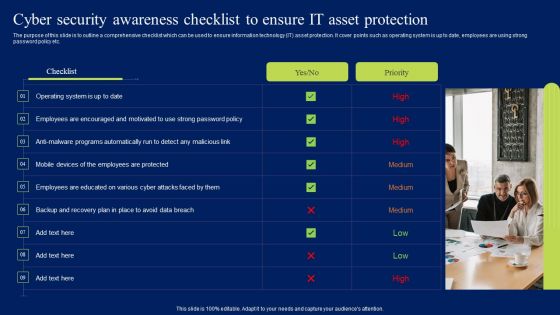
Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
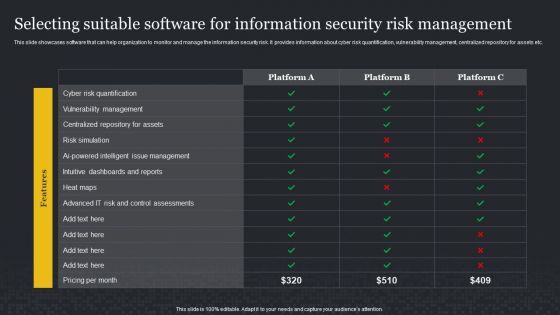
Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases software that can help organization to monitor and manage the information security risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. If you are looking for a format to display your unique thoughts, then the professionally designed Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
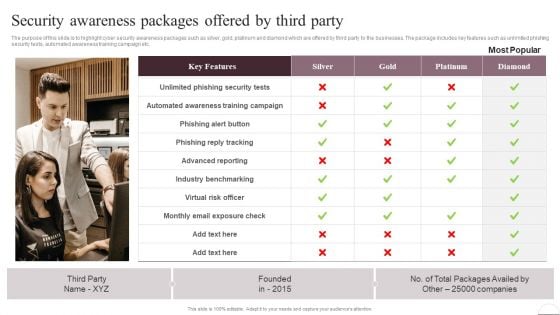
Prevention Of Information Security Awareness Packages Offered By Third Party Information PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Prevention Of Information Security Awareness Packages Offered By Third Party Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
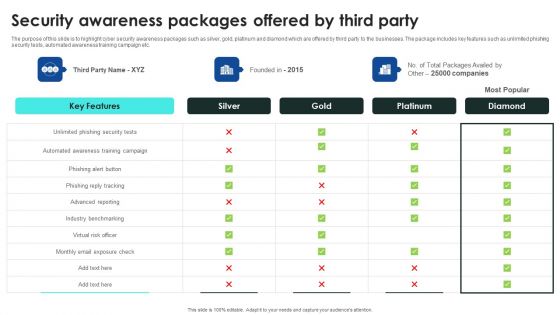
Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Packages Offered By Third Party Clipart PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Explore a selection of the finest Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
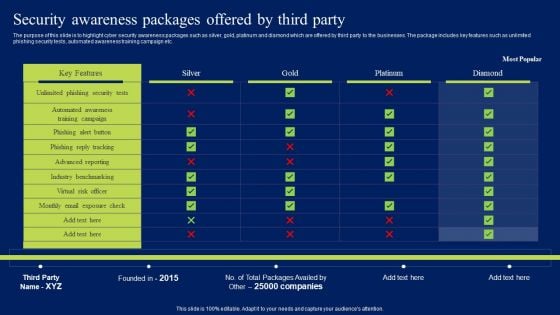
Security Awareness Packages Offered By Third Party Ppt Layouts Topics PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This Security Awareness Packages Offered By Third Party Ppt Layouts Topics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

How To Overcome The Security Awareness Training Program Challenges Infographics PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Create an editable How To Overcome The Security Awareness Training Program Challenges Infographics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. How To Overcome The Security Awareness Training Program Challenges Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
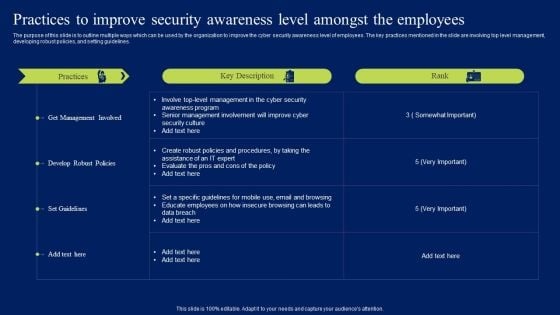
Practices To Improve Security Awareness Level Amongst The Employees Portrait PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Practices To Improve Security Awareness Level Amongst The Employees Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Practices To Improve Security Awareness Level Amongst The Employees Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
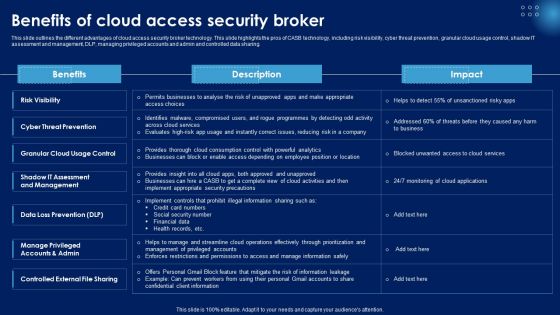
Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.

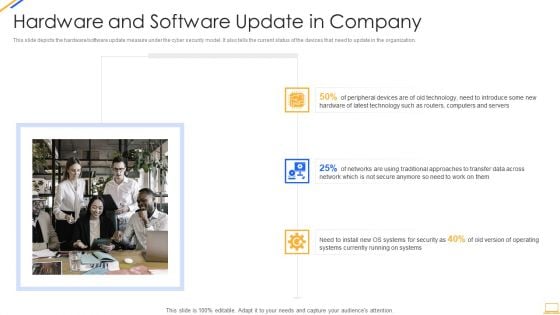
Information Security Hardware And Software Update In Company Ppt Outline Graphics Pictures PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a information security hardware and software update in company ppt outline graphics pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, technology, devices, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Desktop Security Management Hardware And Software Update In Company Portrait PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a desktop security management hardware and software update in company portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, servers, devices, network, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
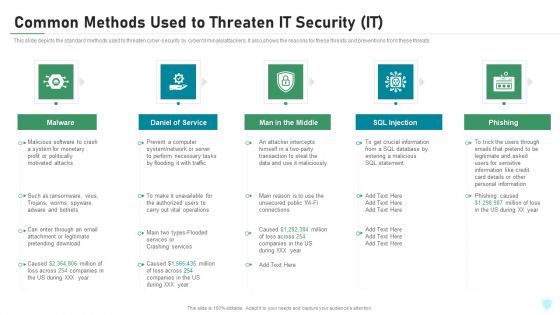
Common Methods Used To Threaten IT Security IT Ppt Inspiration Rules PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten it security it ppt inspiration rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Common Methods Used To Threaten Electronic Information Security Ppt Infographics Inspiration PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a cybersecurity common methods used to threaten electronic information security ppt infographics inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
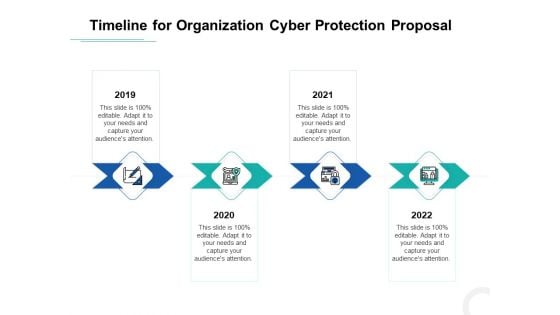
Develop Corporate Cyber Security Risk Mitigation Plan Timeline For Organization Protection Proposal Themes PDF
This is a develop corporate cyber security risk mitigation plan timeline for organization protection proposal themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2019 to 2022. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
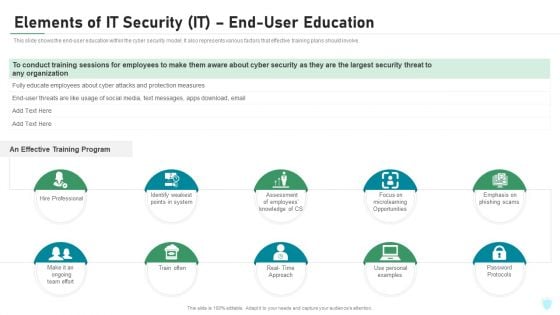
Elements Of IT Security IT End User Education Ppt Model Deck PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a elements of it security it end user education ppt model deck pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hire professional, train often, password protocols, microlearning opportunities, effective training. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Compliance Framework With Individual Rights Ppt PowerPoint Presentation Infographics Graphics Pictures
Presenting this set of slides with name cyber security compliance framework with individual rights ppt powerpoint presentation infographics graphics pictures. This is a twelve stage process. The stages in this process are raise awareness, information held, communicating privacy, individual rights, subject access requests, legalities of processing personal data, consent, protecting childrens data, data breaches, data protection by design, data protection officers, international work. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
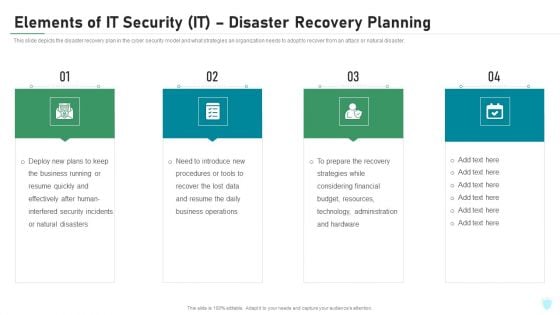
Elements Of IT Security IT Disaster Recovery Planning Ppt Styles Influencers PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting elements of it security it disaster recovery planning ppt styles influencers pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like effectively, business, technology, budget, resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
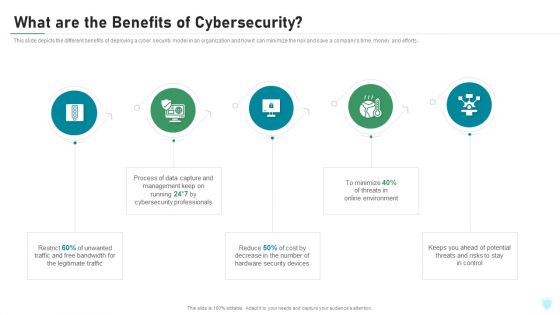
What Are The Benefits Of Cybersecurity IT Security IT Ppt Summary Professional PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a what are the benefits of cybersecurity it security it ppt summary professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like legitimate traffic, cybersecurity, management, process, potential. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Dashboard For Threat Tracking In IT Security IT Ppt Outline Examples PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative dashboard for threat tracking in it security it ppt outline examples pdf bundle. Topics like monthly threat status, threats by owners, risk by threats, current risk status, threats based on role, threat report can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
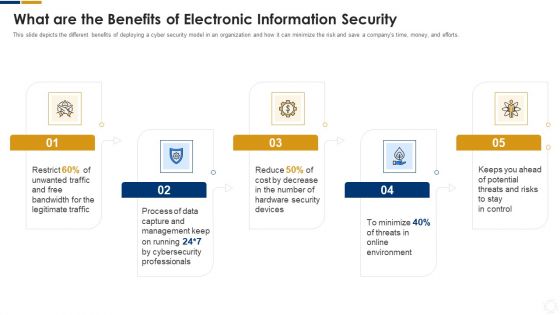
Cybersecurity What Are The Benefits Of Electronic Information Security Ppt Infographics Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting cybersecurity what are the benefits of electronic information security ppt infographics ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, process, cybersecurity, environment, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Requirement Of Electronic Information Security In Different Sectors Ppt Slides Summary PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this cybersecurity requirement of electronic information security in different sectors ppt slides summary pdf. Use them to share invaluable insights on financial, organizations, process, information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
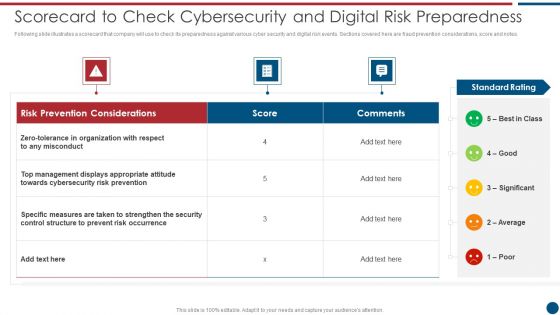
Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF. Use them to share invaluable insights on Risk Prevention, Risk Prevention, Risk Occurrence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

How To Overcome The Security Awareness Training Program Challenges Clipart PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Deliver and pitch your topic in the best possible manner with this How To Overcome The Security Awareness Training Program Challenges Clipart PDF. Use them to share invaluable insights on Burden On Administrators, Employee Participation, Lose Interest and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
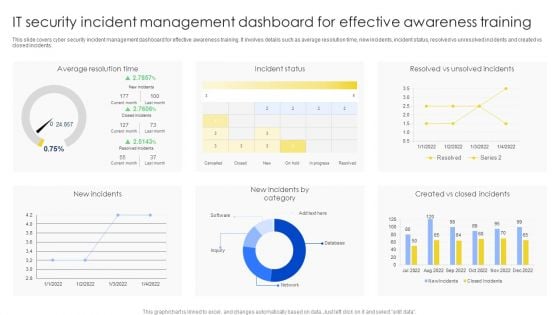
IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF
This slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Implementing Cybersecurity Awareness Program To Prevent Attacks Comparative Assessment Of Security Graphics PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. There are so many reasons you need a Implementing Cybersecurity Awareness Program To Prevent Attacks Comparative Assessment Of Security Graphics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
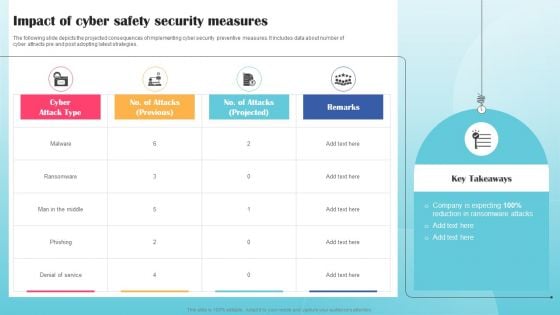
Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF
The following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Slidegeeks has constructed Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Effective Information Technology Security Service Excellence For Risk Mitigation Clipart PDF
This slide signifies the types of security provided through information technology services. It includes surveillance like network, internet, cloud and application for mitigating risk. Pitch your topic with ease and precision using this Effective Information Technology Security Service Excellence For Risk Mitigation Clipart PDF. This layout presents information on Automated Workflows, Customization Option, Multi Channel Deployment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
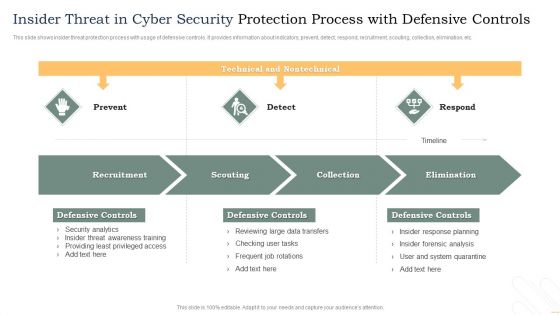
Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF
This slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF. The topics addressed in these templates are Recruitment, Scouting, Collection, Elimination. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
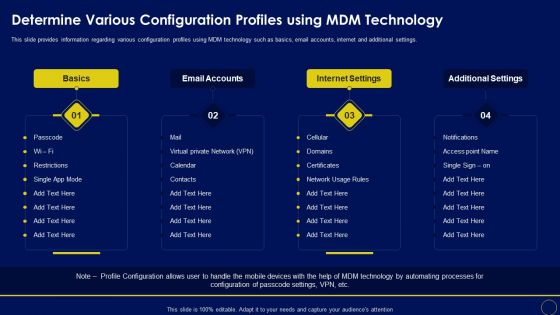
Determine Various Configuration Profiles Using Mdm Technology Business Mobile Device Security Ideas PDF
This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Presenting this PowerPoint presentation, titled Determine Various Configuration Profiles Using Mdm Technology Business Mobile Device Security Ideas PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Determine Various Configuration Profiles Using Mdm Technology Business Mobile Device Security Ideas PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Determine Various Configuration Profiles Using Mdm Technology Business Mobile Device Security Ideas PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Supply Chain Management Iot Security Lock For Safe Fleet Management Download PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Iot Security Lock For Safe Fleet Management Download PDF. Use them to share invaluable insights on Key Applications, Potential Impact, Multiple Positioning Methods and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
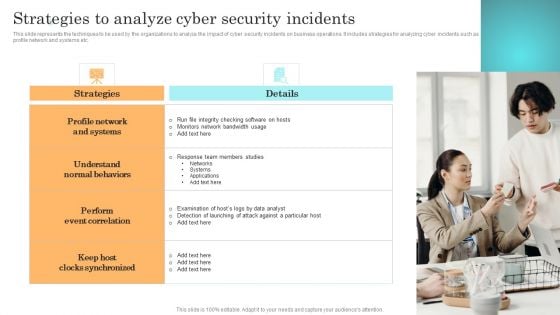
Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF
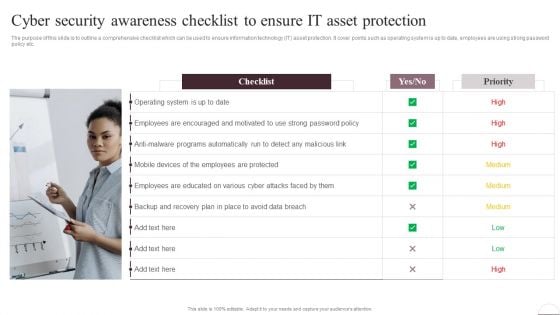
Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Get a simple yet stunning designed Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.
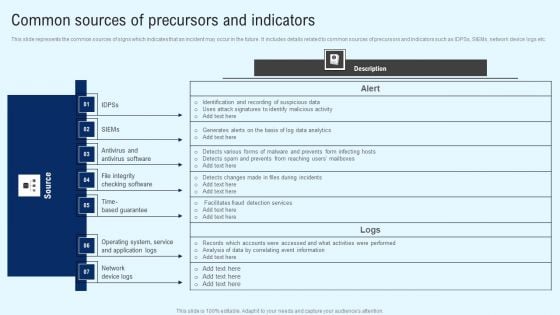
Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF
This slide showcases cyber security risk landscape which can benefit various users around the world to be proactive of potential outcomes. It includes information about target, purpose, possible outcome, social media phishing, system viruses, configuration and passcodes, allocated service denial, hacking devices and structured query language. Persuade your audience using this Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Landscape, Target, Purpose, Possible Outcome. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
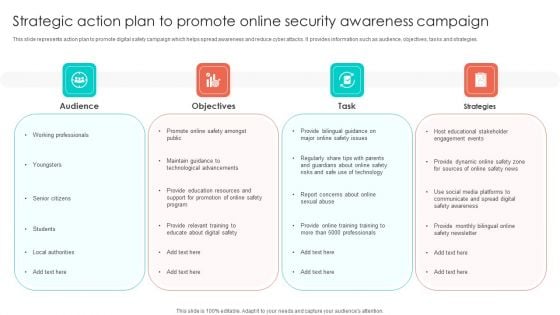
Strategic Action Plan To Promote Online Security Awareness Campaign Portrait PDF
This slide represents action plan to promote digital safety campaign which helps spread awareness and reduce cyber attacks. It provides information such as audience, objectives, tasks and strategies. Persuade your audience using this Strategic Action Plan To Promote Online Security Awareness Campaign Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Task, Strategies, Audience. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF
The following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
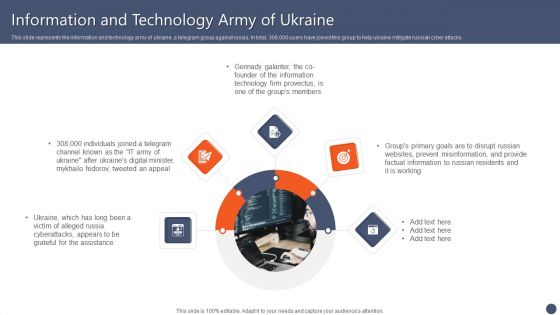
Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF
This slide represents the information and technology army of ukraine, a telegram group against russia. In total, 308,000 users have joined this group to help ukraine mitigate russian cyber attacks. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management.. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. This Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
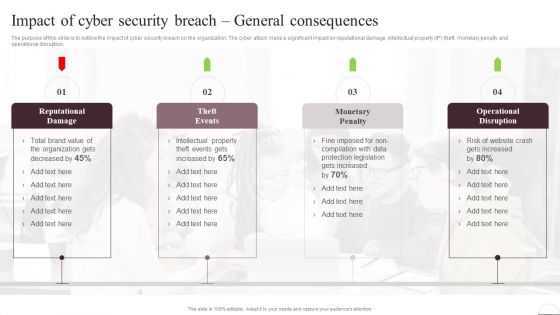
Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Information Systems Security And Risk Management Plan Cyber Attacks Faced By Different Departments Download PDF
This slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. This modern and well arranged Information Systems Security And Risk Management Plan Cyber Attacks Faced By Different Departments Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well arranged Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Impact Of Cyber Security Breach General Consequences Ppt Styles Icon PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Present like a pro with Impact Of Cyber Security Breach General Consequences Ppt Styles Icon PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
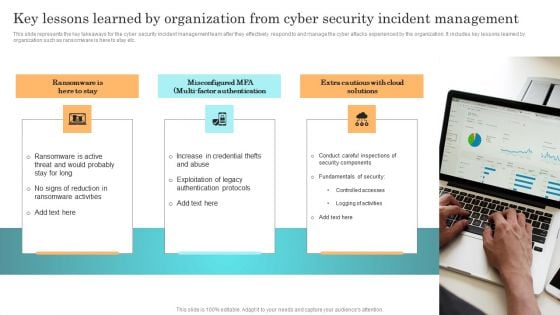
Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
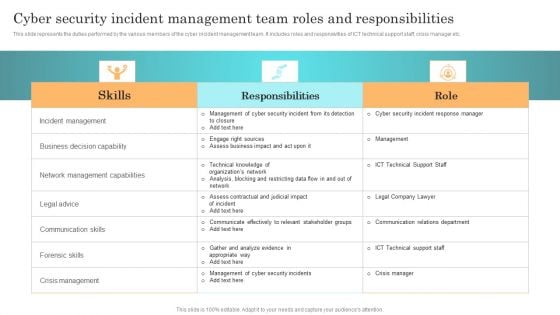
Incident Response Techniques Deployement Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. This Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
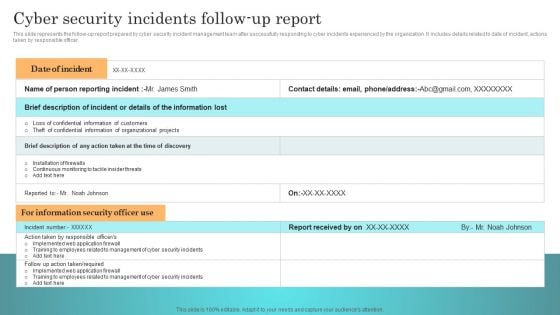
Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
The following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF


 Continue with Email
Continue with Email

 Home
Home


































