Web Security
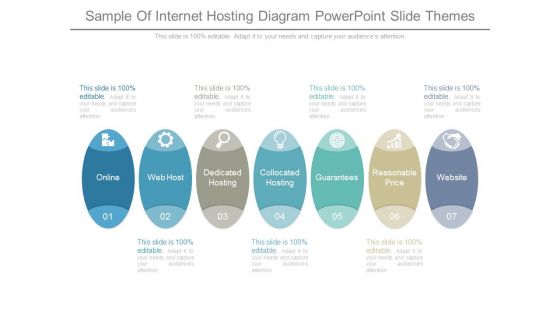
Sample Of Internet Hosting Diagram Powerpoint Slide Themes
This is a sample of internet hosting diagram powerpoint slide themes. This is a seven stage process. The stages in this process are online, web host, dedicated hosting, collocated hosting, guarantees, reasonable price, website.
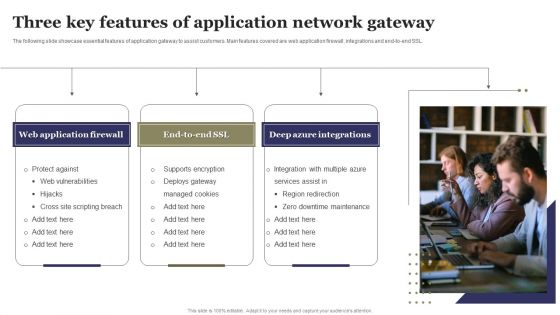
Three Key Features Of Application Network Gateway Ppt Portfolio Introduction PDF
The following slide showcase essential features of application gateway to assist customers. Main features covered are web application firewall, integrations and end-to-end SSL. Presenting Three Key Features Of Application Network Gateway Ppt Portfolio Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewall, Deep Azure Integrations, Protect Against. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Login For Income Statement Powerpoint Template
Our above slide display graphics of log in page on mobile phone with money flowing out of tap. Download this diagram slide to display security measures for money saving account. Adjust the above diagram in your business presentations to visually support your content.

Table Of Contents For Cyber Intelligent Computing System Infographics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Cyber Intelligent Computing System Infographics PDF bundle. Topics like Systems Development, Systems Implementation, Security Strategy Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
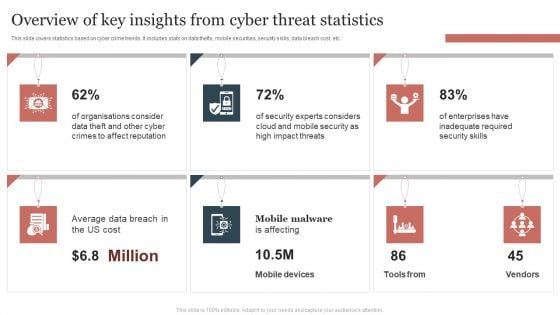
Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Internet Of Things Advantages In Business Ppt PowerPoint Presentation Gallery Icon PDF
Presenting internet of things advantages in business ppt powerpoint presentation gallery icon pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including security system, operational expenditure, rich data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
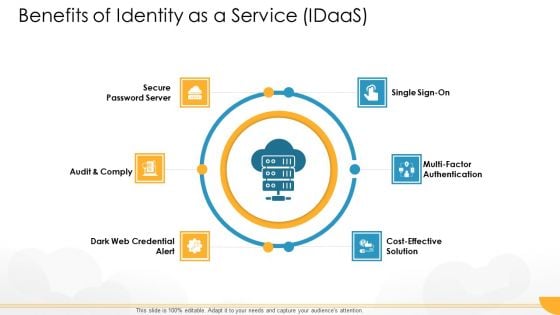
Technology Guide For Serverless Computing Benefits Of Identity As A Service Idaas Summary PDF
This is a technology guide for serverless computing benefits of identity as a service idaas summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secure password server, audit and comply, cost effective solution, multi factor authentication, dark web credential alert. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
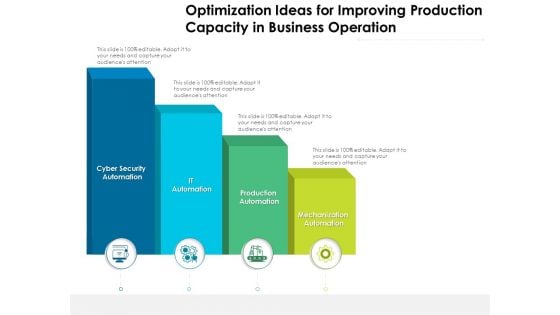
Optimization Ideas For Improving Production Capacity In Business Operation Ppt PowerPoint Presentation Outline Visual Aids PDF
Presenting this set of slides with name optimization ideas for improving production capacity in business operation ppt powerpoint presentation outline visual aids pdf. This is a four stage process. The stages in this process are mechanization automation, production automation, it automation, cyber security automation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
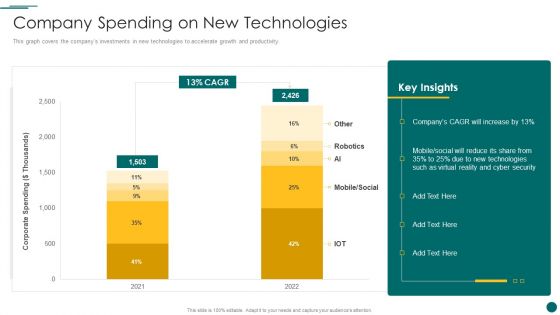
Organization Reinvention Company Spending On New Technologies Microsoft PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Reinvention Company Spending On New Technologies Microsoft PDF bundle. Topics like Social, Technologies, Cyber Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
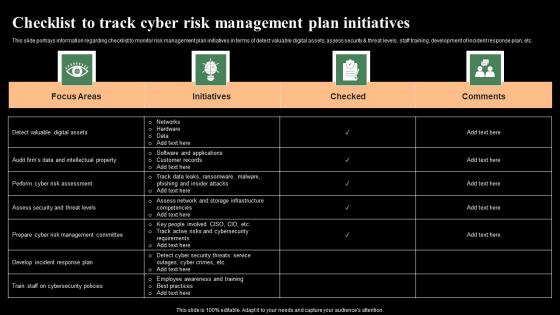
Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf
This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Do you know about Slidesgeeks Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc.

Internet Technology Domain Layout Powerpoint Slide Ideas
This is a internet technology domain layout powerpoint slide ideas. This is a fourteen stage process. The stages in this process are product management, security, erp, crm, wcdma, it infrastructure, rdbms, system software, embedded technology, technical trainer, semiconductor, application software, web technology, mainframe.
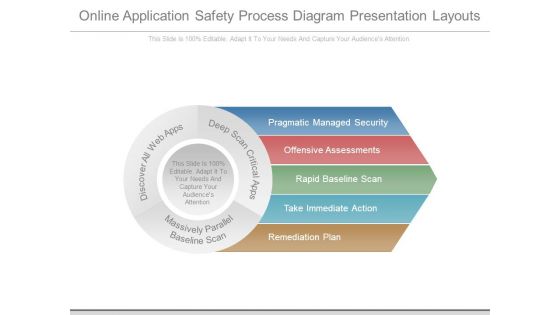
Online Application Safety Process Diagram Presentation Layouts
This is a online application safety process diagram presentation layouts. This is a five stage process. The stages in this process are pragmatic managed security, offensive assessments, rapid baseline scan, take immediate action, remediation plan, discover all web apps, deep scan critical apps, massively parallel, baseline scan.
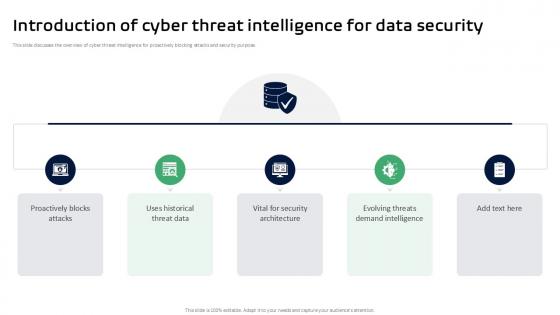
Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template
This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose.
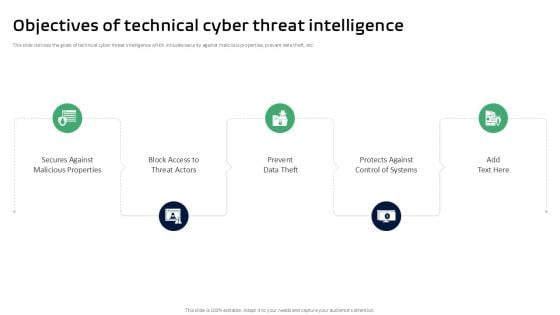
Objectives Of Technical Cyber Threat Intelligence Ppt Slides
This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc. This Objectives Of Technical Cyber Threat Intelligence Ppt Slides is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Objectives Of Technical Cyber Threat Intelligence Ppt Slides features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc.
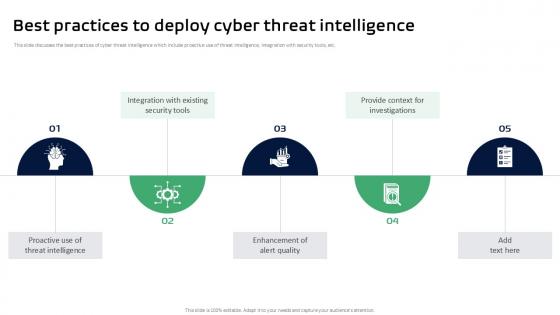
Best Practices To Deploy Cyber Threat Intelligence Ppt Slides
This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices To Deploy Cyber Threat Intelligence Ppt Slides for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc.
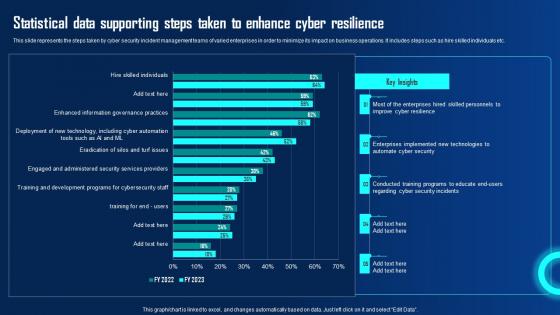
Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf
This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc.
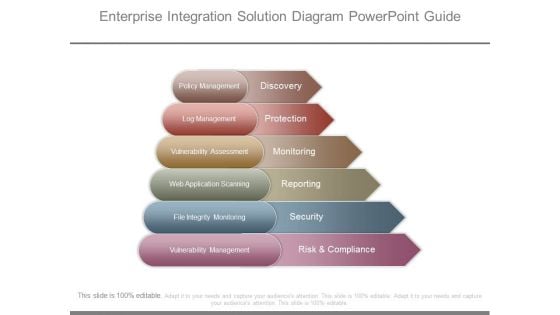
Enterprise Integration Solution Diagram Powerpoint Guide
This is a enterprise integration solution diagram powerpoint guide. This is a six stage process. The stages in this process are policy management, log management, vulnerability assessment, web application scanning, file integrity monitoring, vulnerability management, discovery, protection, monitoring, reporting, security, risk and compliance.

Online Payment Techniques Challenges Faced By Business In Adopting Cashless
Mentioned slide showcases various challenges in implementation of cashless payment system in business. It includes challenges such as customer restrain, high processing fees, security issues, difficulty to adopt cashless technology and regular internet services. Explore a selection of the finest Online Payment Techniques Challenges Faced By Business In Adopting Cashless here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Online Payment Techniques Challenges Faced By Business In Adopting Cashless to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide showcases various challenges in implementation of cashless payment system in business. It includes challenges such as customer restrain, high processing fees, security issues, difficulty to adopt cashless technology and regular internet services.
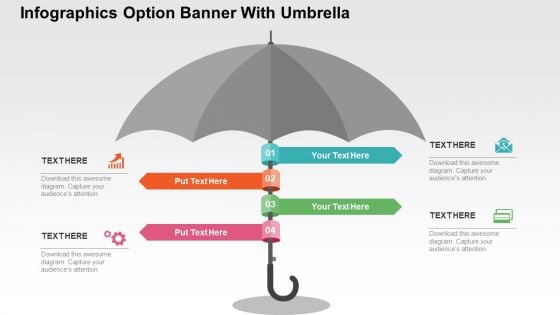
Infographics Option Banner With Umbrella Powerpoint Templates
Who doesn?t want to have a secure life? Be it financial security, safety of your child or safe environment at home and at work place. Well we hope for that but we can definitely save you from making ugly PowerPoint presentations. Above is the slide which is of umbrella with four options and along with it are four icons. This slide is one of our most downloaded PowerPoint slides and can be used to depict safety and security of any kind. The umbrella here can be used to indicate the safety, security, protection so you can choose this slide to show why it is safe to be associated with your company, or with your business, with your school, how your money is safe and secured in your bank or how it is safe if you pay online and much more. It is a multipurpose slide and can easily be modified as you want. Choose this slide to make your PowerPoint presentation look even more fantastic.

Online Business Challenges And Best Practices Brochure Pdf
The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc. Pitch your topic with ease and precision using this Online Business Challenges And Best Practices Brochure Pdf. This layout presents information on Pain Points, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc.

Technology Trends In Online Insurance Essential Personnel Required For Digital Transformation Team
The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business or technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Technology Trends In Online Insurance Essential Personnel Required For Digital Transformation Team from Slidegeeks and deliver a wonderful presentation. The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business or technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists.
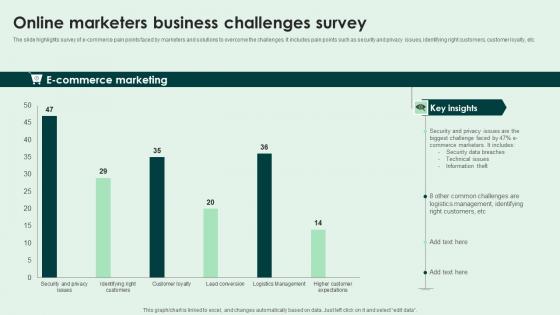
Online Marketers Business Challenges Survey Slides Pdf
The slide highlights survey of e-commerce pain points faced by marketers and solutions to overcome the challenges. It includes pain points such as security and privacy issues, identifying right customers, customer loyalty, etc. Pitch your topic with ease and precision using this Online Marketers Business Challenges Survey Slides Pdf. This layout presents information on E Commerce Marketing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide highlights survey of e-commerce pain points faced by marketers and solutions to overcome the challenges. It includes pain points such as security and privacy issues, identifying right customers, customer loyalty, etc.
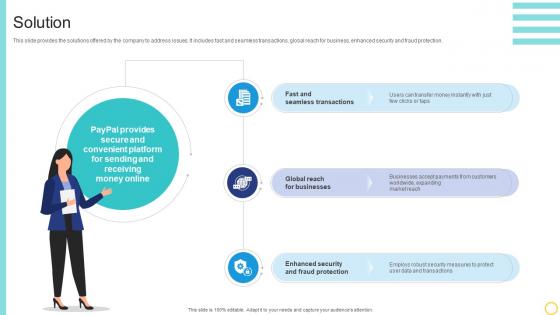
Solution Online Transaction Facilitator Business Model BMC SS V
This slide provides the solutions offered by the company to address issues. It includes fast and seamless transactions, global reach for business, enhanced security and fraud protection. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Online Transaction Facilitator Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides the solutions offered by the company to address issues. It includes fast and seamless transactions, global reach for business, enhanced security and fraud protection.
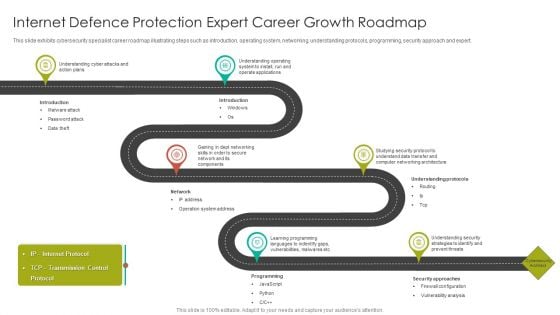
Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
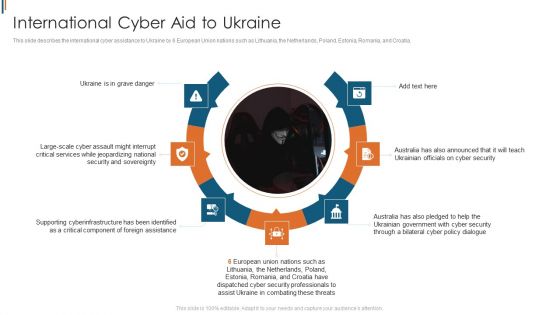
Ukraine Cyberwarfare International Cyber Aid To Ukraine Brochure Pdf
This slide describes the international cyber assistance to Ukraine by 6 European Union nations such as Lithuania, the Netherlands, Poland, Estonia, Romania, and Croatia. This is a ukraine cyberwarfare international cyber aid to ukraine brochure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine is in grave danger, australia has also announced that it will teach ukrainian officials on cyber security, australia has also pledged to help the ukrainian government with cyber security through a bilateral cyber policy dialogue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
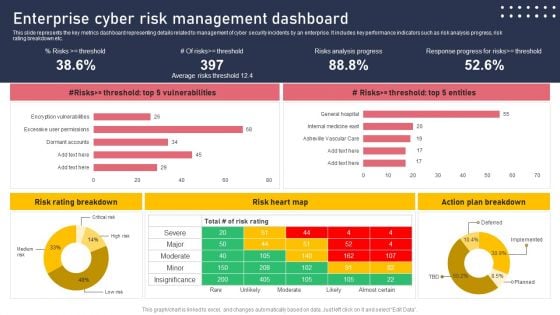
Enterprise Cyber Risk Management Dashboard Sample PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. There are so many reasons you need a Enterprise Cyber Risk Management Dashboard Sample PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
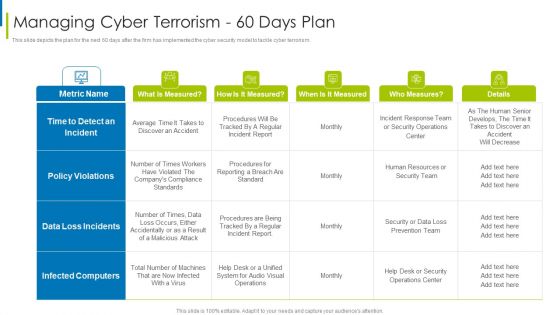
Cyber Terrorism Assault Managing Cyber Terrorism 60 Days Plan Clipart PDF
This slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault managing cyber terrorism 60 days plan clipart pdf Use them to share invaluable insights on time to detect an incident, data loss incidents, infected computers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
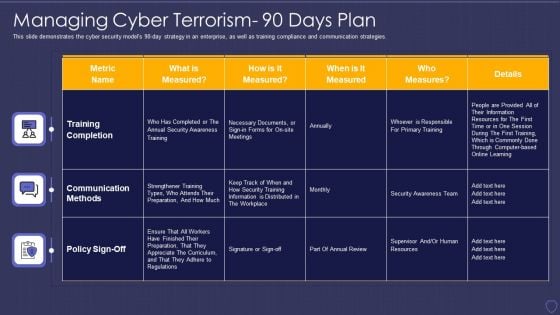
Global Cyber Terrorism Incidents On The Rise IT Managing Cyber Terrorism 90 Days Plan Structure PDF
This slide demonstrates the cyber security models 90-day strategy in an enterprise, as well as training compliance and communication strategies. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it managing cyber terrorism 90 days plan structure pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
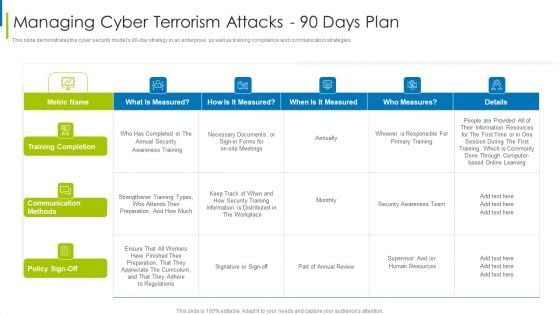
Cyber Terrorism Assault Managing Cyber Terrorism Attacks 90 Days Plan Formats PDF
This slide demonstrates the cyber security models 90 to day strategy in an enterprise, as well as training compliance and communication strategies.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault managing cyber terrorism attacks 90 days plan formats pdf Use them to share invaluable insights on training completion, communication methods, information is distributed and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Intelligent Computing System Sensing Components Of Cyber Physical Systems Elements PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Sensing Components Of Cyber Physical Systems Elements PDF bundle. Topics like Information Acquired, Analyze, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
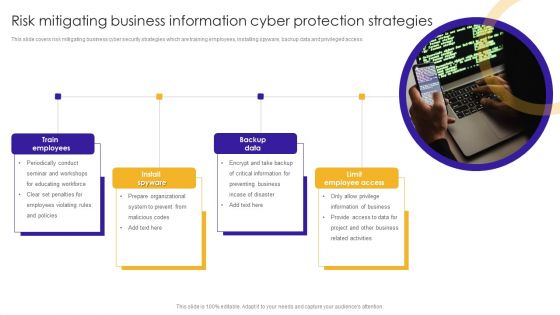
Risk Mitigating Business Information Cyber Protection Strategies Themes PDF
This slide covers risk mitigating business cyber security strategies which are training employees, installing spyware, backup data and privileged access.Presenting Risk Mitigating Business Information Cyber Protection Strategies Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Information Business, Related Activities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf today and make your presentation stand out from the rest This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.

Enhancing Cyber Safety With Vulnerability Administration SIEM Integrations Inspiration PDF
This is a enhancing cyber safety with vulnerability administration siem integrations inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Awareness Course Program List Ppt Infographics Shapes PDF
This slide covers list of programs available for increasing security awareness. It includes elements such as programs included for three levels covering essential, advanced and enterprise related services. Showcasing this set of slides titled Cyber Safety Awareness Course Program List Ppt Infographics Shapes PDF. The topics addressed in these templates are Programs, Essentials, Advanced. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
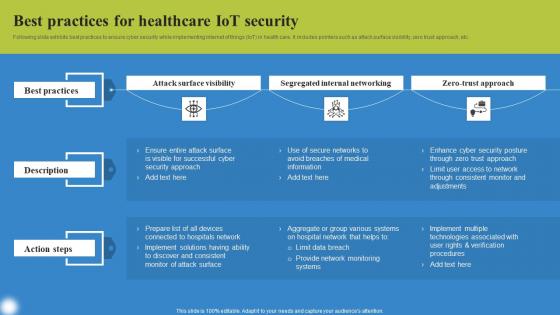
Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf
Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. This modern and well arranged Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc.
Cyber Exploitation IT Dashboard For Threat Tracking Topics PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cyber exploitation it dashboard for threat tracking topics pdf bundle. Topics like dashboard for threat tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Purpose Of Ethical Hacking Portrait PDF
This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities. Deliver an awe inspiring pitch with this creative cyber exploitation it purpose of ethical hacking portrait pdf bundle. Topics like vulnerabilities, management, process, weaknesses, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
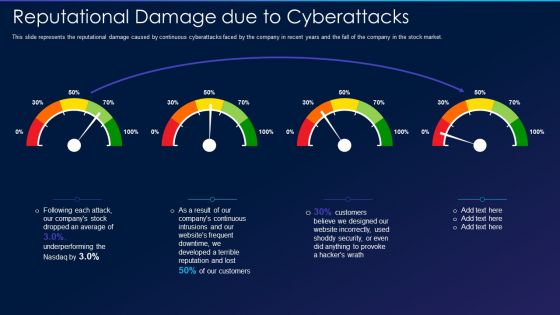
Cyber Exploitation IT Reputational Damage Due To Cyberattacks Professional PDF
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market. Deliver an awe inspiring pitch with this creative cyber exploitation it reputational damage due to cyberattacks professional pdf bundle. Topics like continuous, developed, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
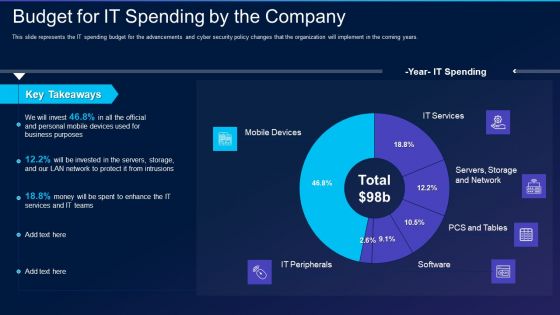
Cyber Exploitation IT Budget For IT Spending By The Company Professional PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years. Deliver an awe inspiring pitch with this creative cyber exploitation it budget for it spending by the company professional pdf bundle. Topics like mobile devices, it peripherals, it services, servers, storage and network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
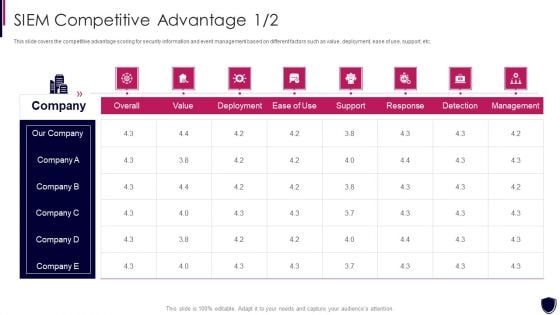
Enhancing Cyber Safety With Vulnerability Administration SIEM Competitive Advantage Designs PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration siem competitive advantage designs pdf bundle. Topics like detection, management, deployment, value can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
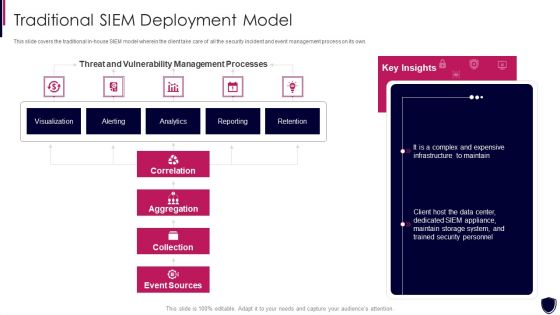
Enhancing Cyber Safety With Vulnerability Administration Traditional SIEM Deployment Designs PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this enhancing cyber safety with vulnerability administration traditional siem deployment designs pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources, our company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
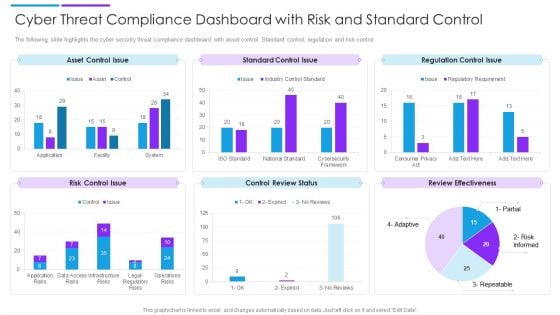
Cyber Threat Compliance Dashboard With Risk And Standard Control Sample PDF
The following slide highlights the cyber security threat compliance dashboard with asset control. Standard control, regulation and risk control. Showcasing this set of slides titled cyber threat compliance dashboard with risk and standard control sample pdf. The topics addressed in these templates are asset control issue, standard control issue, regulation control issue. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Deliver an awe inspiring pitch with this creative Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF bundle. Topics like Processing Data, Information, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
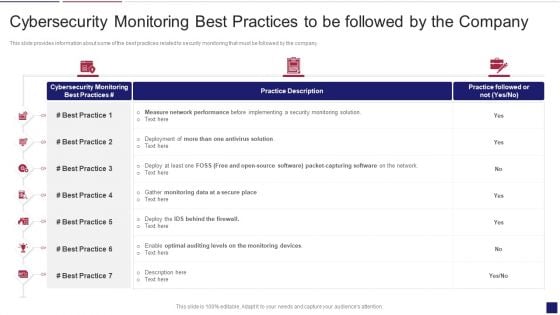
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Best Mockup PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring best mockup pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Cyber Terrorism Incidents On The Rise IT Implement Strong IT Guidelines Pictures PDF
This slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it implement strong it guidelines pictures pdf bundle. Topics like implement strong it guidelines in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
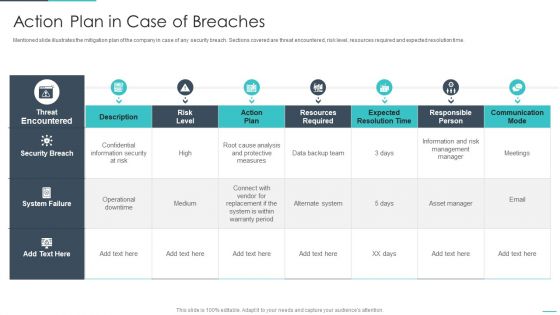
Handling Cyber Threats Digital Era Action Plan In Case Of Breaches Ppt Styles Objects PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative handling cyber threats digital era action plan in case of breaches ppt styles objects pdf bundle. Topics like action plan in case of breaches can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
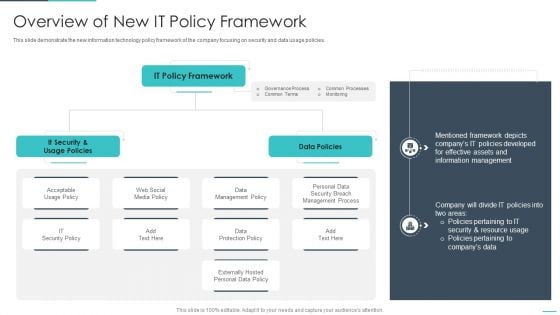
Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
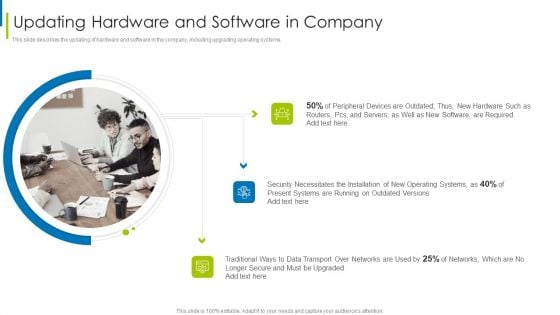
Cyber Terrorism Assault Updating Hardware And Software In Company Infographics PDF
This slide describes the updating of hardware and software in the company, including upgrading operating systems.Deliver an awe inspiring pitch with this creative cyber terrorism assault updating hardware and software in company infographics pdf bundle. Topics like peripheral devices, security necessitates, traditional ways to data transport can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
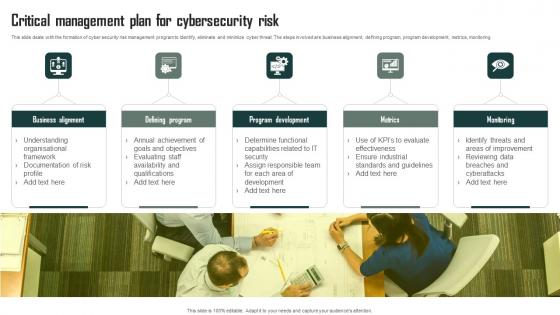
Critical Management Plan For Cybersecurity Risk Demonstration Pdf
This slide deals with the formation of cyber security risk management program to identify, eliminate and minimize cyber threat. The steps involved are business alignment, defining program, program development, metrics, monitoring Pitch your topic with ease and precision using this Critical Management Plan For Cybersecurity Risk Demonstration Pdf This layout presents information on Business Alignment, Defining Program, Program Development It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide deals with the formation of cyber security risk management program to identify, eliminate and minimize cyber threat. The steps involved are business alignment, defining program, program development, metrics, monitoring
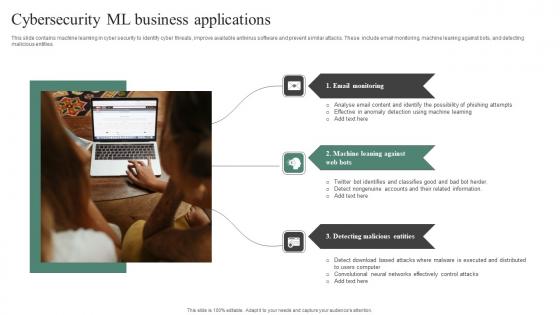
Cybersecurity ML Business Applications Sample Pdf
This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities. Pitch your topic with ease and precision using this Cybersecurity ML Business Applications Sample Pdf. This layout presents information on Email Monitoring, Machine Leaning, Detecting Malicious Entities. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities.
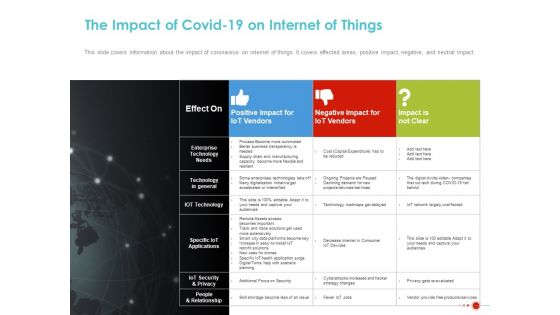
COVID 19 Mitigating Impact On High Tech Industry The Impact Of COVID 19 On Internet Of Things Brochure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry the impact of covid 19 on internet of things brochure pdf. The topics discussed in these slides are positive impact, iot vendors, negative impact iot vendors, impact not clear, enterprise technology needs, technology general, iot technology, specific iot applications, iot security and privacy, people and relationship. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
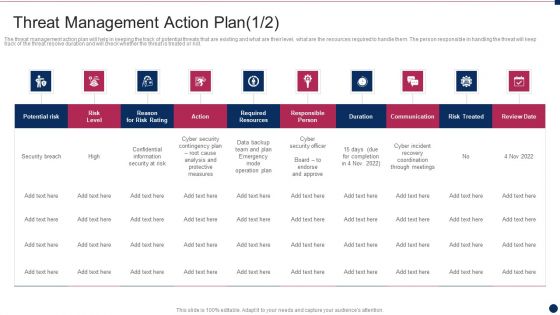
Threat Management At Workplace Threat Management Action Plan Responsible Person Template PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this threat management at workplace threat management action plan responsible person template pdf. Use them to share invaluable insights on cyber incident recovery coordination through meetings, confidential information security at risk, cyber security officer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
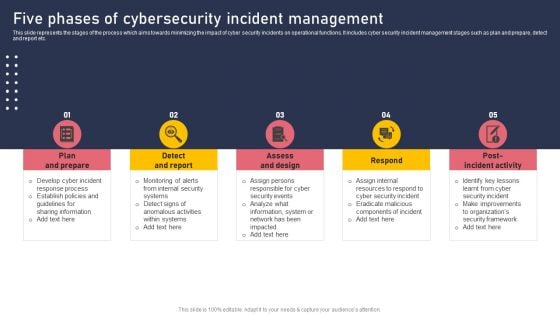
Five Phases Of Cybersecurity Incident Management Topics PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Five Phases Of Cybersecurity Incident Management Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Five Phases Of Cybersecurity Incident Management Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Optimizing Business Integration Key Trends That Drive The Industry Information Pdf
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Optimizing Business Integration Key Trends That Drive The Industry Information Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology.
Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.

Business Analysis Ability Mapping Model With Techniques Sample Pdf
This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc. Showcasing this set of slides titled Business Analysis Ability Mapping Model With Techniques Sample Pdf The topics addressed in these templates are Business Competency, Proficiency Scale, Specialized Areas All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc.

Obstacles Encountered In Current Banking Processes Incorporating Banking Operational Growth
The purpose of this slide is to showcase the various challenges associated with the functioning of banking operations. It includes cyber security threats, client retention, outdated mobile experiences, continuous innovations, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Obstacles Encountered In Current Banking Processes Incorporating Banking Operational Growth for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The purpose of this slide is to showcase the various challenges associated with the functioning of banking operations. It includes cyber security threats, client retention, outdated mobile experiences, continuous innovations, etc.
Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
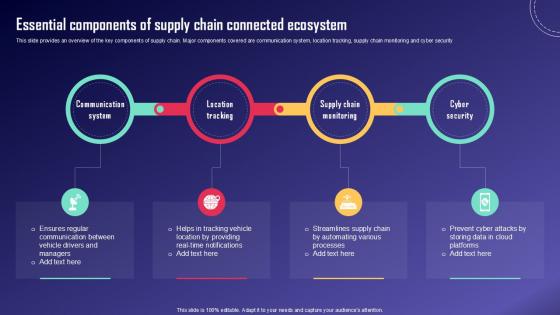
Essential Components Of Supply IoT Fleet Monitoring Ppt Example IoT SS V
This slide provides an overview of the key components of supply chain. Major components covered are communication system, location tracking, supply chain monitoring and cyber security . Whether you have daily or monthly meetings, a brilliant presentation is necessary. Essential Components Of Supply IoT Fleet Monitoring Ppt Example IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Essential Components Of Supply IoT Fleet Monitoring Ppt Example IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide provides an overview of the key components of supply chain. Major components covered are communication system, location tracking, supply chain monitoring and cyber security


 Continue with Email
Continue with Email

 Home
Home


































