Web Security

Proposal For Corporate Meeting Scope One Pager Sample Example Document
The slide presents the scope of services for the proposal project in terms of catering, internet and audio visual equipment , logistics, security and decor. Presenting you an exemplary Proposal For Corporate Meeting Scope One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Corporate Meeting Scope One Pager Sample Example Document brilliant piece now.

Scope For Scientific Conference One Pager Sample Example Document
The slide presents the scope of services for the proposal project in terms of catering, internet and audio-visual equipment, logistics, security and decor. Presenting you an exemplary Scope For Scientific Conference One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Scope For Scientific Conference One Pager Sample Example Document brilliant piece now.
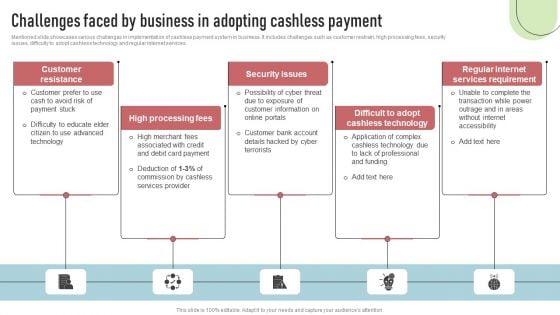
Cashless Payment Strategies To Enhance Business Performance Challenges Faced By Business In Adopting Microsoft PDF
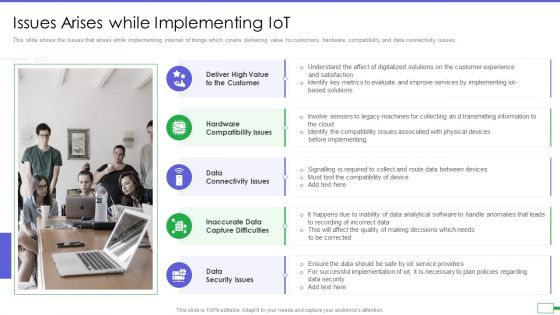
Iot And Digital Twin To Reduce Costs Post Covid Issues Arises While Implementing Iot Themes PDF
This slide shows the issues that arises while implementing internet of things which covers delivering value to customers, hardware compatibility and data connectivity issues. Presenting iot and digital twin to reduce costs post covid issues arises while implementing iot themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like high value to the customer, hardware compatibility issues, data connectivity issues, inaccurate data capture difficulties, data security issues. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
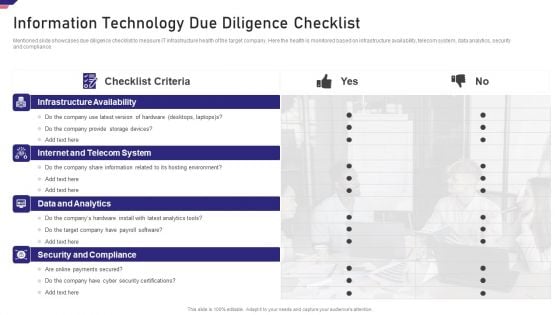
Mergers Acquisition Playbook Mergers Acquisition Playbook Information Technology Due Ideas PDF
Mentioned slide showcases due diligence checklist to measure IT infrastructure health of the target company. Here the health is monitored based on infrastructure availability, telecom system, data analytics, security and compliance.This is a Mergers Acquisition Playbook Mergers Acquisition Playbook Information Technology Due Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Infrastructure Availability, Internet And Telecom System, Data And Analytics You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
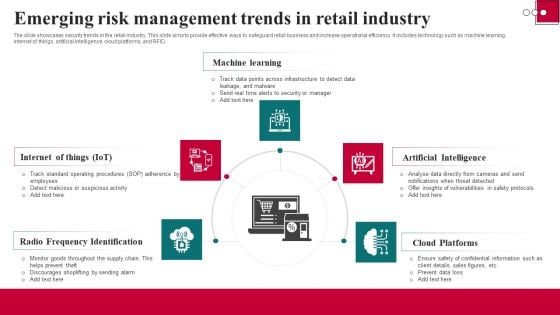
Emerging Risk Management Trends In Retail Industry Background PDF
The slide showcases security trends in the retail industry. This slide aims to provide effective ways to safeguard retail business and increase operational efficiency. It includes technology such as machine learning, internet of things, artificial intelligence, cloud platforms, and RFID. Persuade your audience using this Emerging Risk Management Trends In Retail Industry Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Radio Frequency Identification, Artificial Intelligence, Cloud Platforms. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
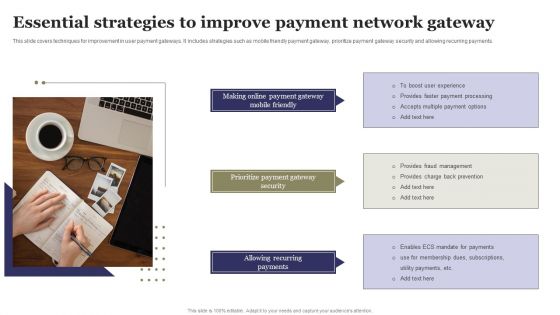
Essential Strategies To Improve Payment Network Gateway Ppt Gallery Background Designs PDF
This slide covers techniques for improvement in user payment gateways. It includes strategies such as mobile friendly payment gateway, prioritize payment gateway security and allowing recurring payments. Presenting Essential Strategies To Improve Payment Network Gateway Ppt Gallery Background Designs PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Making Online, Payment Gateway, Prioritize Payment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Different Training Formats For Different Organization Levels Brochure PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. Presenting different training formats for different organization levels brochure pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like automated security awareness platform, interactive protection simulation, cybersecurity for it online. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risks Involved And Mitigation Strategies Designs PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, and Key Strategies Measures for effectively mitigating the risk.Deliver and pitch your topic in the best possible manner with this risks involved and mitigation strategies designs pdf. Use them to share invaluable insights on warehousing and logistics risks, online security and privacy risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risks Involved And Mitigation Strategies Background PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, and Key Strategies Measures for effectively mitigating the risk.Deliver and pitch your topic in the best possible manner with this risks involved and mitigation strategies background pdf. Use them to share invaluable insights on warehousing and logistics risks, online security and privacy risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
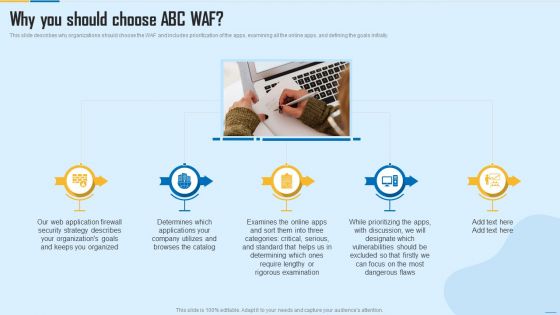
WAF Platform Why You Should Choose ABC WAF Information PDF
This slide describes why organizations should choose the WAF and includes prioritization of the apps, examining all the online apps, and defining the goals initially. Presenting WAF Platform Why You Should Choose ABC WAF Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Applications, Determines, Security Strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
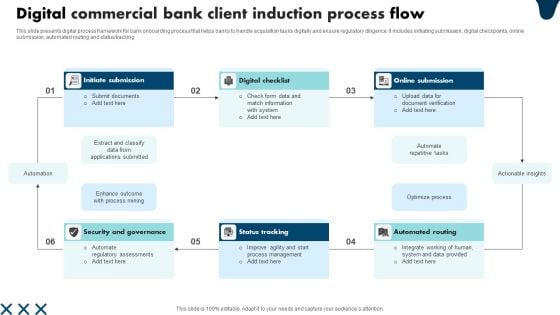
Digital Commercial Bank Client Induction Process Flow Background PDF
This slide presents digital process framework for bank onboarding process that helps banks to handle acquisition tasks digitally and ensure regulatory diligence. It includes initiating submission, digital checkpoints, online submission, automated routing and status tracking. Presenting Digital Commercial Bank Client Induction Process Flow Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security And Governance, Status Tracking, Automated Routing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
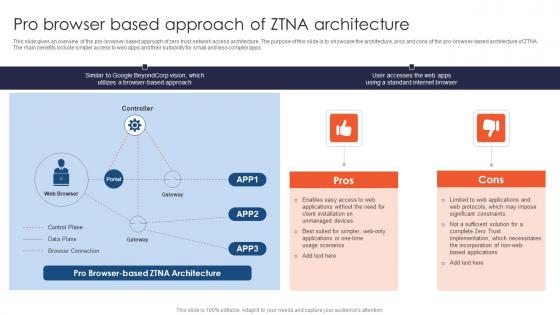
Zero Trust Network Access Pro Browser Based Approach Of ZTNA Architecture
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. There are so many reasons you need a Zero Trust Network Access Pro Browser Based Approach Of ZTNA Architecture. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps.

Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
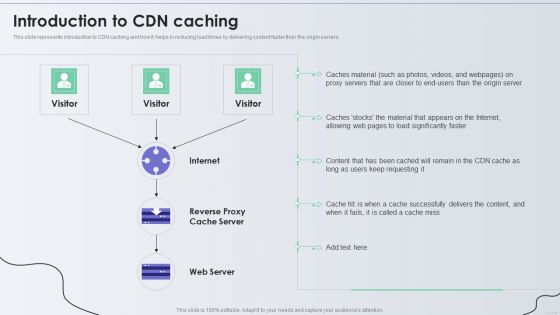
Distribution Network Introduction To CDN Caching Diagrams PDF
This slide represents introduction to CDN caching and how it helps in reducing load times by delivering content faster than the origin servers. Deliver an awe inspiring pitch with this creative Distribution Network Introduction To CDN Caching Diagrams PDF bundle. Topics like Internet, Material, Web Server can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
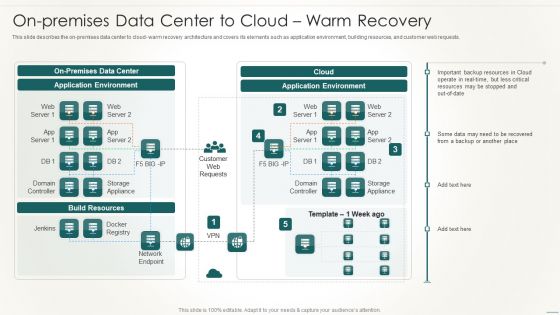
Information Technology Disaster Resilience Plan On-Premises Data Center To Cloudwarm Recovery Ideas PDF
This slide describes the on-premises data center to cloud- warm recovery architecture and covers its elements such as application environment, building resources, and customer web requests.Deliver an awe inspiring pitch with this creative Information Technology Disaster Resilience Plan On-Premises Data Center To Cloudwarm Recovery Ideas PDF bundle. Topics like Domain Controller, Storage Appliance, Network Endpoint can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
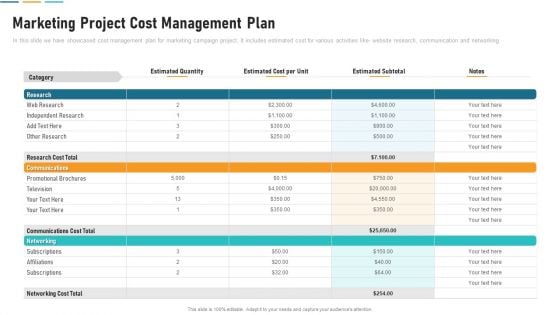
Marketing Project Cost Management Plan Sample PDF
In this slide we have showcased cost management plan for marketing campaign project. It includes estimated cost for various activities like website research, communication and networking. Pitch your topic with ease and precision using this marketing project cost management plan sample pdf. This layout presents information on research cost, communications cost, web research. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Film Production House Portfolio Film Media Company Profile Ppt PowerPoint Presentation Icon PDF
This slide covers the portfolio of our production company which includes web series, movies and documentaries. It also provides information such as names, release date, networks and IMDB score.Deliver an awe inspiring pitch with this creative Film Production House Portfolio Film Media Company Profile Ppt PowerPoint Presentation Icon PDF bundle. Topics like Documentaries, Ott Platforms, Release Date can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

On Premises Data Center To Cloud Warm Recovery Background PDF
This slide describes the on premises data center to cloud warm recovery architecture and covers its elements such as application environment, building resources, and customer web requests. Deliver and pitch your topic in the best possible manner with this On Premises Data Center To Cloud Warm Recovery Background PDF. Use them to share invaluable insights on Application Environment, Build Resources, Network Endpoint and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Choose The Right Door Of Opportunity PowerPoint Templates Ppt Backgrounds For Slides 0513
Use Our business Power Point Templates To Weave A Web Of Your Great Ideas. They Are Guaranteed To Attract Even The Most Critical Of Your Colleagues. Our people Power Point Templates Are Designed To Help You Succeed. They Have All The Ingredients You Need. Help your audience to absorb it with equanimity. Calm ruffled nerves with our Choose The Right Door Of Opportunity PowerPoint Templates Ppt Backgrounds For Slides 0513.

Be The Part Of Team PowerPoint Templates Ppt Backgrounds For Slides 0513
Use Our leadership Power Point Templates To Weave A Web Of Your Great Ideas. They Are Guaranteed To Attract Even The Most Critical Of Your Colleagues. Our people Power Point Templates Are Designed To Help You Succeed. They Have All The Ingredients You Need. Our Be The Part Of Team PowerPoint Templates Ppt Backgrounds For Slides 0513 give you the correct feel. Connect with your audience in a convincing way.

Create A Circle For Business Growth PowerPoint Templates Ppt Backgrounds For Slides 0513
Use Our business Power Point Templates To Weave A Web Of Your Great Ideas. They Are Guaranteed To Attract Even The Most Critical Of Your Colleagues. Our puzzles or puzzles Power Point Templates Are Designed To Help You Succeed. They Have All The Ingredients You Need. Accentuate the beauty of your thoughts with our Create A Circle For Business Growth PowerPoint Templates Ppt Backgrounds For Slides 0513. They will prove an apt adornment.

Business Network Is Important PowerPoint Templates Ppt Backgrounds For Slides 0613
Use our People Powerpoint Templates to weave a web of your great ideas. They are guaranteed to attract even the most critical of your colleagues. Our Network diagrams Powerpoint Templates are designed to help you succeed. They have all the ingredients you need. Be clear and crisp with our Business Network Is Important PowerPoint Templates Ppt Backgrounds For Slides 0613. All dillemas will begin to disappear.
Networking Process Diagram 7 Stages Business Plan For Small PowerPoint Slides
We present our networking process diagram 7 stages business plan for small PowerPoint Slides.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas. Download and present our Network Diagrams PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Download and present our Circle Charts PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas. Download and present our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Blue, Gray, White. Face the crunch moment with our Networking Process Diagram 7 Stages Business Plan For Small PowerPoint Slides. Bite the bullet with your thoughts.
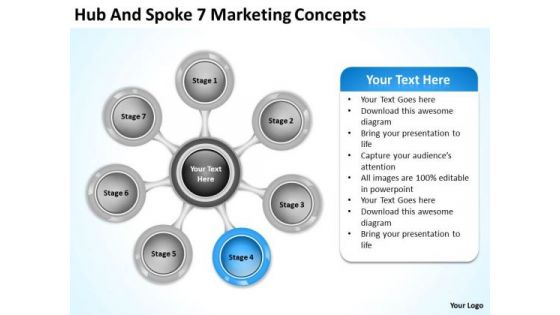
Hub And Spoke 7 Marketing Concepts Standard Business Plan PowerPoint Templates
We present our hub and spoke 7 marketing concepts standard business plan PowerPoint templates.Present our Circle Charts PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas. Use our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Download and present our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune.Use these PowerPoint slides for presentations relating to Hub, networking, concept, diagram, flowchart, work, points, net, corporation, corporate, business, plan, render, teamwork, seven, circle,scheme, analysis, technology, relation, idea, team, graph, molecule, illustration, pie, object, connection, chart, strategy, prioritize, web, group,organization, connect, organize, connectivity, marketing, interact, site, structure, international, communication. The prominent colors used in the PowerPoint template are Blue, Gray, White. Display an ambitious attitude with our Hub And Spoke 7 Marketing Concepts Standard Business Plan PowerPoint Templates. Your audience will become believers.
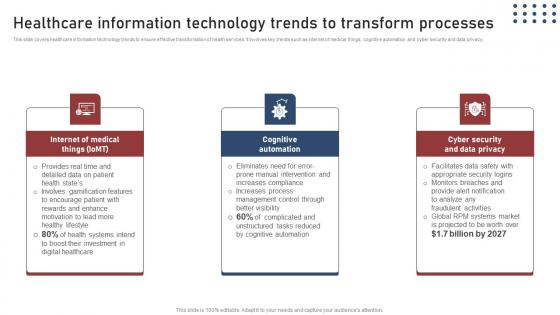
Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.

Healthcare Information Technology Healthcare Information Tech Enhance Medical Facilities Professional Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Healthcare Information Technology Healthcare Information Tech Enhance Medical Facilities Professional Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
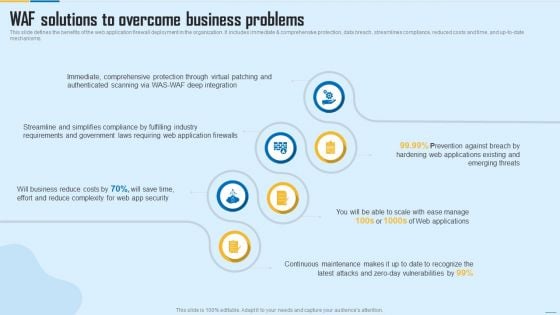
WAF Solutions To Overcome Business Problems WAF Platform Clipart PDF
This slide defines the benefits of the web application firewall deployment in the organization. It includes immediate and comprehensive protection, data breach, streamlines compliance, reduced costs and time, and up to date mechanisms. This is a WAF Solutions To Overcome Business Problems WAF Platform Clipart PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirements, Security, Applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
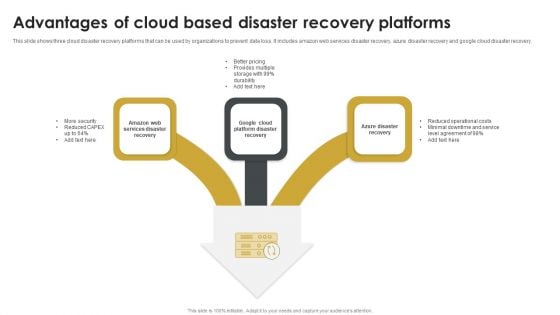
Advantages Of Cloud Based Disaster Recovery Platforms Sample PDF
This slide shows three cloud disaster recovery platforms that can be used by organizations to prevent data loss. It includes amazon web services disaster recovery, azure disaster recovery and google cloud disaster recovery. Persuade your audience using this Advantages Of Cloud Based Disaster Recovery Platforms Sample PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Azure Disaster Recovery, Security, Reduced Operational Costs. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Find highly impressive Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.

Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf today and make your presentation stand out from the rest. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.
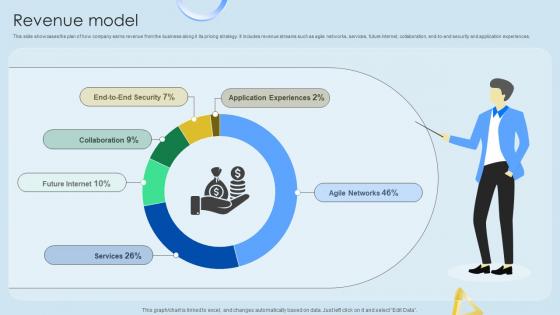
Revenue Model Cloud Networking Service Provider Business Model BMC SS V
This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences. Find highly impressive Revenue Model Cloud Networking Service Provider Business Model BMC SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Revenue Model Cloud Networking Service Provider Business Model BMC SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences.

Key Takeaways And Strategic Port Terminal Industry Ppt PowerPoint
The purpose of this slide is to provide a brief insights related to the ports market and its growth. It covers opportunity protection, macro and geopolitical insights related to the insurers, and demand for cyber security ports and services analysis.Explore a selection of the finest Key Takeaways And Strategic Port Terminal Industry Ppt PowerPoint here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Takeaways And Strategic Port Terminal Industry Ppt PowerPoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The purpose of this slide is to provide a brief insights related to the ports market and its growth. It covers opportunity protection, macro and geopolitical insights related to the insurers, and demand for cyber security ports and services analysis.

Data Breach Awareness Training Program Data Breach Prevention Professional Pdf
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs. Find highly impressive Data Breach Awareness Training Program Data Breach Prevention Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Breach Prevention Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Data Breach Awareness Training Program Data Fortification Strengthening Defenses
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.Find highly impressive Data Breach Awareness Training Program Data Fortification Strengthening Defenses on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Fortification Strengthening Defenses for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.
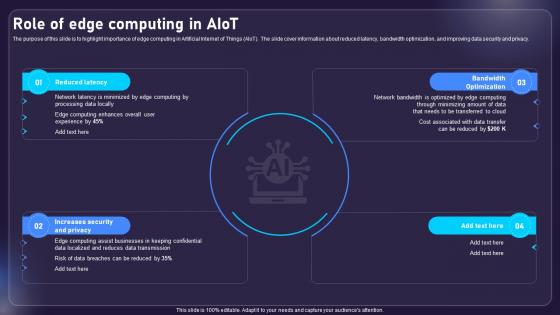
Role Of Edge Computing In AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to highlight importance of edge computing in Artificial Internet of Things AIoT. The slide cover information about reduced latency, bandwidth optimization, and improving data security and privacy. Find highly impressive Role Of Edge Computing In AIOT Applications For Various Industries IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Edge Computing In AIOT Applications For Various Industries IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to highlight importance of edge computing in Artificial Internet of Things AIoT. The slide cover information about reduced latency, bandwidth optimization, and improving data security and privacy.
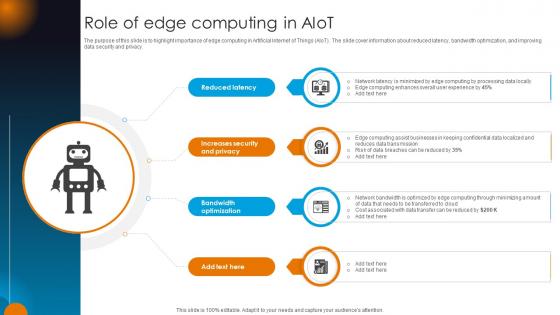
Integrating AI With IoT Role Of Edge Computing In AIoT IoT SS V
The purpose of this slide is to highlight importance of edge computing in Artificial Internet of Things AIoT. The slide cover information about reduced latency, bandwidth optimization, and improving data security and privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Integrating AI With IoT Role Of Edge Computing In AIoT IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Integrating AI With IoT Role Of Edge Computing In AIoT IoT SS V today and make your presentation stand out from the rest The purpose of this slide is to highlight importance of edge computing in Artificial Internet of Things AIoT. The slide cover information about reduced latency, bandwidth optimization, and improving data security and privacy.

Laptop With Key Chain Business PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Key Chain Business PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Internet PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Present our Computer PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Download our Finance PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download our Money PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Download our Communication PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to Laptop security keychain, internet, computer, security, finance, communication. The prominent colors used in the PowerPoint template are Black, Yellow, Gray. Many factors can create a distraction. Our Laptop With Key Chain Business PowerPoint Templates Ppt Backgrounds For Slides 0213 will not let them fall for it.
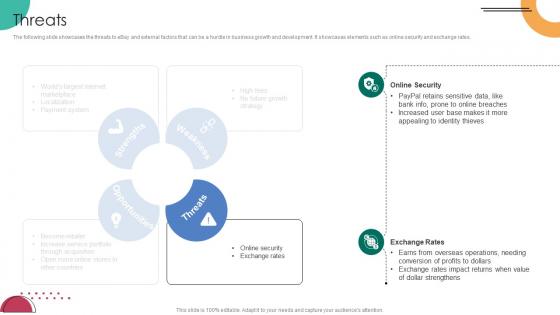
Threats C2C Ecommerce Platform Company Profile CP SS V
The following slide showcases the threats to eBay and external factors that can be a hurdle in business growth and development. It showcases elements such as online security and exchange rates.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Threats C2C Ecommerce Platform Company Profile CP SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Threats C2C Ecommerce Platform Company Profile CP SS V. The following slide showcases the threats to eBay and external factors that can be a hurdle in business growth and development. It showcases elements such as online security and exchange rates.
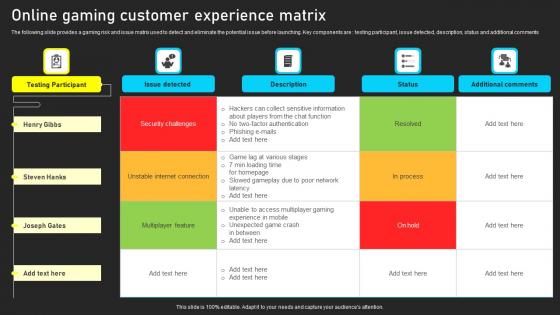
Online Gaming Customer Experience Matrix Guidelines Pdf
The following slide provides a gaming risk and issue matrix used to detect and eliminate the potential issue before launching. Key components are testing participant, issue detected, description, status and additional comments Showcasing this set of slides titled Online Gaming Customer Experience Matrix Guidelines Pdf. The topics addressed in these templates are Security Challenges, Unstable Internet Connection, Multiplayer Feature. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides a gaming risk and issue matrix used to detect and eliminate the potential issue before launching. Key components are testing participant, issue detected, description, status and additional comments
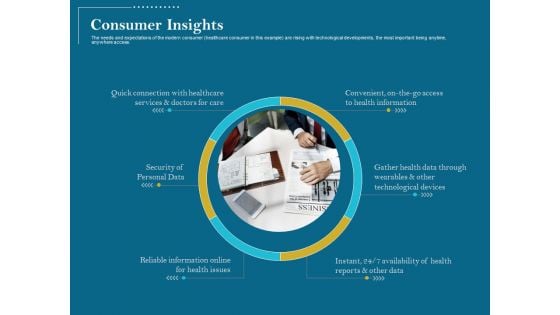
Utilizing Cyber Technology For Change Process Consumer Insights Microsoft PDF
The needs and expectations of the modern consumer healthcare consumer in this example are rising with technological developments, the most important being anytime, anywhere access. Presenting utilizing cyber technology for change process consumer insights microsoft pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security of personal data, reliable information online for health issues, gather health data through wearables and other technological devices, convenient, on the go access to health information, quick connection with healthcare services and doctors for care. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
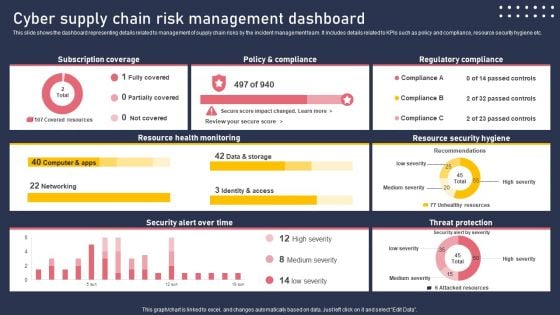
Cyber Supply Chain Risk Management Dashboard Structure PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Supply Chain Risk Management Dashboard Structure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112
Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112-Use our Security PowerPoint Templates because, Present your views using our innovative slides and be assured of leaving a lasting impression. Use our Arrows PowerPoint Templates because; Help them develop their thoughts along the way. Use our Business PowerPoint Templates because; emphasize the process of your business/corporate growth. Use our Computer PowerPoint Templates because, Clarity of thought has been the key to your growth. Use our Internet PowerPoint Templates because; transmit this concern to your staff using our helpful slides.-Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-Upload download folder icon, Computer, Arrows, Symbol, Internet, Business Environmental awareness is the call to answer. Our Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112 will fit the bill.

Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF
This slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF from Slidegeeks today.
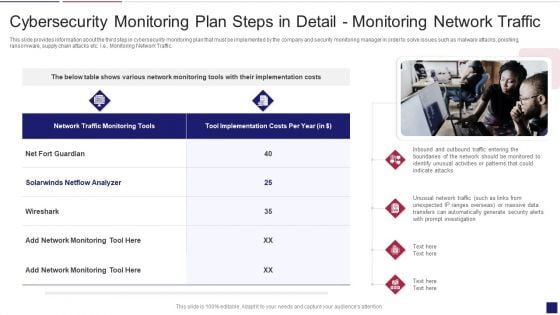
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
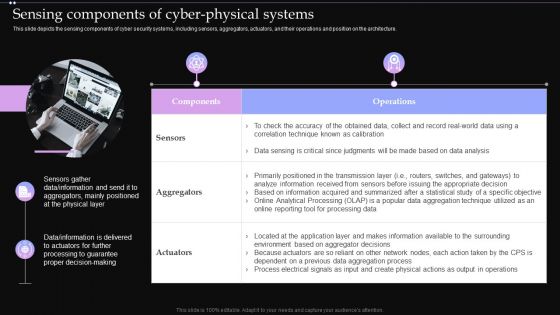
Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Find highly impressive Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
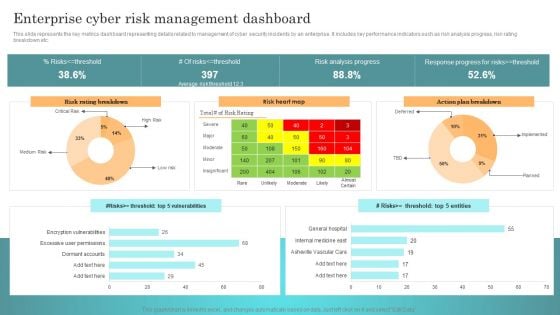
Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Find highly impressive Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF
The following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF today and make your presentation stand out from the rest.
Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
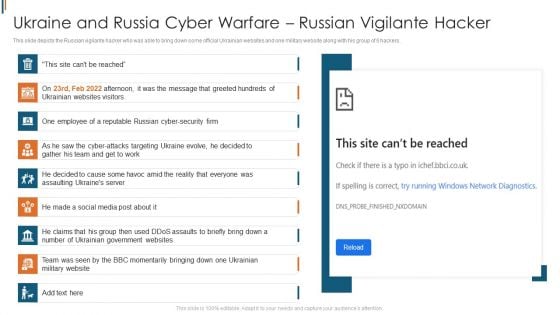
Ukraine Cyberwarfare Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Inspiration Pdf
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers. This is a ukraine cyberwarfare ukraine and russia cyber warfare russian vigilante hacker inspiration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like he made a social media post about it, one employee of a reputable russian cyber security firm, team was seen by the bbc momentarily bringing down one ukrainian military website. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
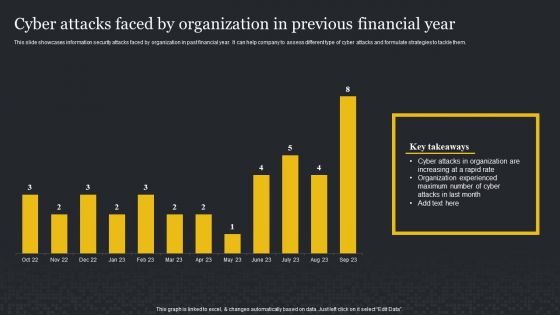
Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
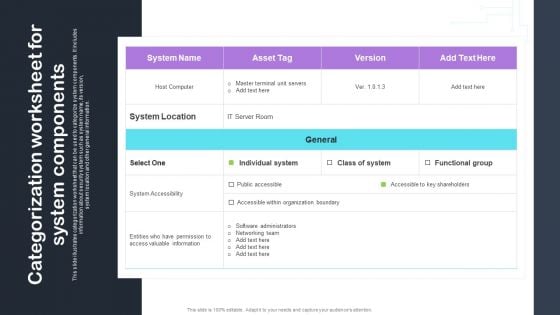
Cyber Risks And Incident Response Playbook Categorization Worksheet For System Components Structure PDF
This slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information. Get a simple yet stunning designed Cyber Risks And Incident Response Playbook Categorization Worksheet For System Components Structure PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Cyber Risks And Incident Response Playbook Categorization Worksheet For System Components Structure PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.
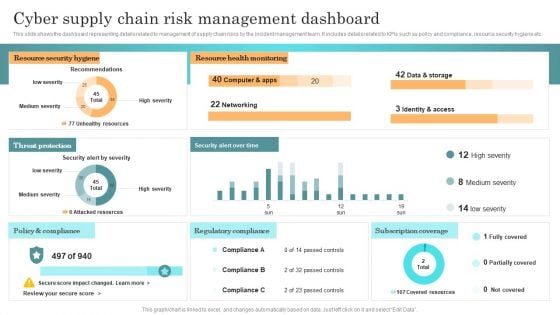
Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF can be your best option for delivering a presentation. Represent everything in detail using Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

IT Policies And Procedures Internet Usage Policy Password Guidelines Microsoft PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. Explore a selection of the finest IT Policies And Procedures Internet Usage Policy Password Guidelines Microsoft PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our IT Policies And Procedures Internet Usage Policy Password Guidelines Microsoft PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. This Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
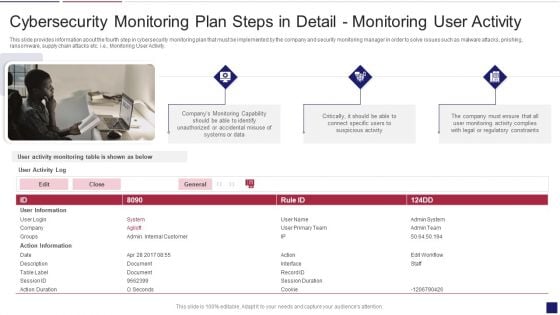
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
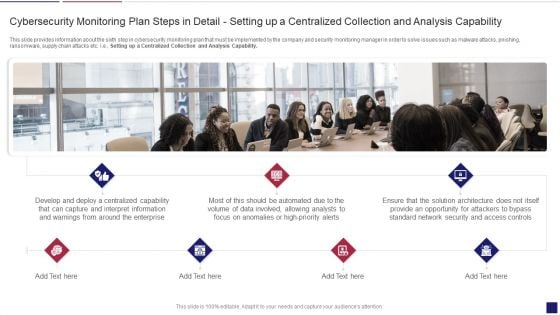
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































