lock

Key Factors For Customer Success Management Ppt Powerpoint Presentation Outline Guide
This is a key factors for customer success management ppt powerpoint presentation outline guide. This is a three stage process. The stages in this process are eys for success, keys for achievement, highlights for success.
Key Factors To Achieving Competitive Success Ppt Powerpoint Presentation Outline Ideas
This is a key factors to achieving competitive success ppt powerpoint presentation outline ideas. This is a three stage process. The stages in this process are eys for success, keys for achievement, highlights for success.

Key Smart Goals To Achieve Business Success Ppt Powerpoint Presentation Portfolio Example Topics
This is a key smart goals to achieve business success ppt powerpoint presentation portfolio example topics. This is a four stage process. The stages in this process are eys for success, keys for achievement, highlights for success.
Safety And Authentication Vector Icon Ppt Powerpoint Presentation Model Rules
This is a safety and authentication vector icon ppt powerpoint presentation model rules. This is a one stage process. The stages in this process are password, access approval, authentication icon.
Unlock Future Vector Icon Ppt PowerPoint Presentation Inspiration Images
Presenting this set of slides with name unlock future vector icon ppt powerpoint presentation inspiration images. This is a one stage process. The stages in this process are vision icon, business, planning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vendor Supply Ordering Ppt PowerPoint Presentation Infographic Template Layout Cpb
Presenting this set of slides with name vendor supply ordering ppt powerpoint presentation infographic template layout cpb. This is an editable Powerpoint five stages graphic that deals with topics like vendor supply ordering to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Company Vulnerability Administration Introduction Designs PDF
Presenting company vulnerability administration introduction designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like need for vulnerability management, vulnerability management model, vulnerability management levels, overview. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Vulnerability Administration Need For Vulnerability Management Introduction PDF
Presenting company vulnerability administration need for vulnerability management introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detective controls, responsive controls, vulnerability management is a standard process, implementing a vulnerability management program. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Authentication Process Flow Of Verification Factors For User Profile Authentication Icon Portrait PDF
Persuade your audience using this authentication process flow of verification factors for user profile authentication icon portrait pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including authentication process flow of verification factors for user profile authentication icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cover Letter Real Estate Property Management Proposal Ppt Professional Slide PDF
Take your presentations to the next level with our Cover Letter Real Estate Property Management Proposal Ppt Professional Slide PDF template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights.

Our Pricing Packages For Real Estate Property Management Proposal Ppt Summary Background Image PDF
This slide showcases various packages that are provided by real estate property management company to its clients. It includes components like services offered, monthly management fees, lease renewal fee, financial reports etc. Take your presentations to the next level with our Our Pricing Packages For Real Estate Property Management Proposal Ppt Summary Background Image PDF template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights.
Computer Cyber Security Icon Infographics PDF
Presenting Computer Cyber Security Icon Infographics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Computer Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
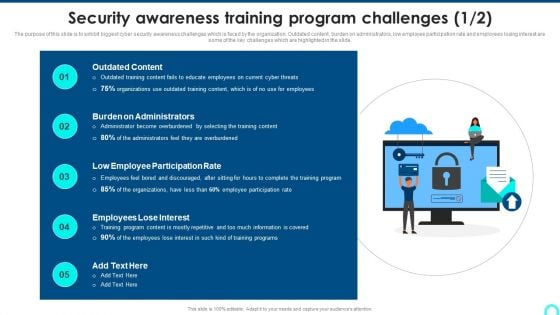
Security Awareness Training Program Challenges Rules PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Presenting Security Awareness Training Program Challenges Rules PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Outdated Content, Burden On Administrators, Employee Participation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Recruitment And Selection Powerpoint Slide Influencers
This is a recruitment and selection powerpoint slide influencers. This is a seven stage process. The stages in this process are recruitment and selection, industrial relations, career development, compensation and benefits, safety and health, training and development, performance management.

Entrepreneurial Spirit And Growth Example Powerpoint Images
This is a entrepreneurial spirit and growth example powerpoint images. This is a three stage process. The stages in this process are ability, success, growth.

Governance Kpi Examples Powerpoint Slide Rules
This is a governance kpi examples powerpoint slide rules. This is a five stage process. The stages in this process are define targets, scope and governance, industry benchmarks, metric identification, baseline measurement.

Permission Based Email Marketing Status Checklist Guidelines PDF
This slide represents status of company implementing permission based email marketing to promote business. It include steps such as customer consent, customer privacy statement, provide unsubscribe option etc. with completion status. Showcasing this set of slides titled Permission Based Email Marketing Status Checklist Guidelines PDF. The topics addressed in these templates are Consumer Privacy, Security, Requirement. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
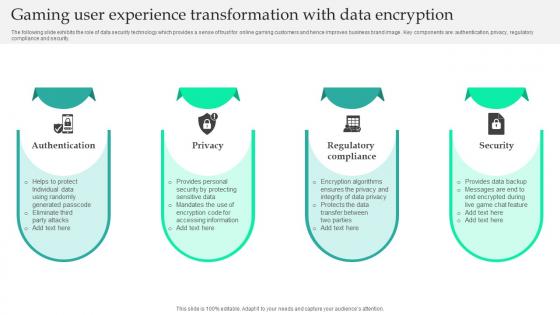
Gaming User Experience Transformation With Data Encryption Portrait Pdf
The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security. Pitch your topic with ease and precision using this Gaming User Experience Transformation With Data Encryption Portrait Pdf. This layout presents information on Authentication, Privacy, Regulatory Compliance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security.
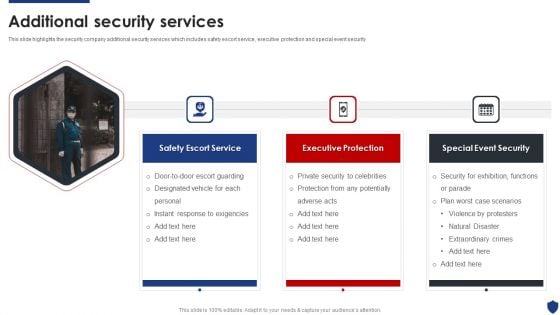
Security Officer Service Company Profile Additional Security Services Ppt PowerPoint Presentation Gallery Introduction PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Presenting Security Officer Service Company Profile Additional Security Services Ppt PowerPoint Presentation Gallery Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Safety Escort Service, Executive Protection, Special Event Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Presenting Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Corporate Security, Industrial Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Small Business Network Diagram With Magnifying Glass Looking At The Golden Key PowerPoint Slides
We present our small business network diagram with magnifying glass looking at the golden key PowerPoint Slides.Present our People PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Use our Security PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Use our Shapes PowerPoint Templates because You are working at that stage with an air of royalty. Let our PowerPoint Templates and Slides be the jewels in your crown.Use these PowerPoint slides for presentations relating to 3d, access, achieve, ambition, business, businessman, career, cgi, challenge, competition, concept, door, examine, find, focus, glass, goal, gold, golden, holding, illustration, job, key, leader, look, magnifier, magnifying, man, market, metaphor, motivation, opportunity, person, personal, render, search, seek, skill, solution, strategy, success, successful, tool, unlock, victory, white, win, work, worker\n. The prominent colors used in the PowerPoint template are Red, Gray, Black. PowerPoint presentation experts tell us our small business network diagram with magnifying glass looking at the golden key PowerPoint Slides have awesome images to get your point across. Professionals tell us our challenge PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. People tell us our small business network diagram with magnifying glass looking at the golden key PowerPoint Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Presenters tell us our ambition PowerPoint templates and PPT Slides are incredible easy to use. Professionals tell us our small business network diagram with magnifying glass looking at the golden key PowerPoint Slides are designed by a team of presentation professionals. We assure you our businessman PowerPoint templates and PPT Slides are designed to make your presentations professional. Success without failure is difficult to achieve. Our Small Business Network Diagram With Magnifying Glass Looking At The Golden Key PowerPoint Slides help add to the chances.
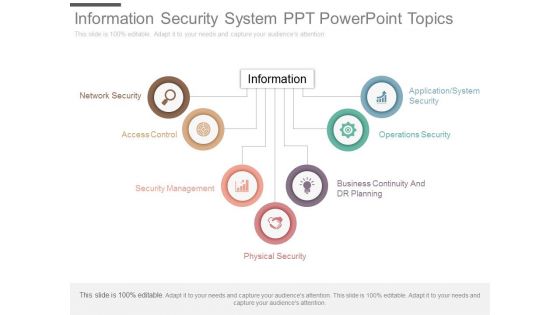
Information Security System Ppt Powerpoint Topics
This is a information security system ppt powerpoint topics. This is a seven stage process. The stages in this process are network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security, information.
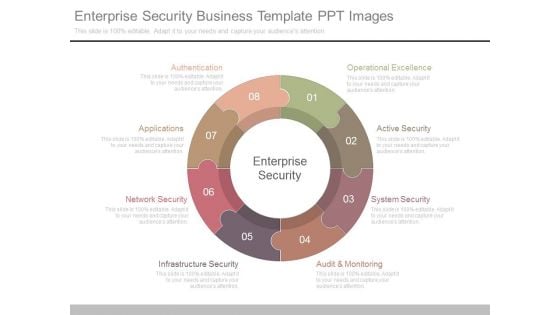
Enterprise Security Business Template Ppt Images
This is a enterprise security business template ppt images. This is a eight stage process. The stages in this process are enterprise security, authentication, applications, network security, infrastructure security, audit and monitoring, system security, active security, operational excellence.
Icon Of Security Computer System Interface For Securing Information Ppt Professional Background PDF
Persuade your audience using this Icon Of Security Computer System Interface For Securing Information Ppt Professional Background PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Security Computer, System Interface Securing, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Information Application Protection Testing Flow Chart Themes PDF
This slide covers business application security testing flow chart which includes secure application model, security standard recognition and privacy testing.Pitch your topic with ease and precision using this Business Information Application Protection Testing Flow Chart Themes PDF. This layout presents information on Security Consistency, Target Weighting, Target Recognition. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
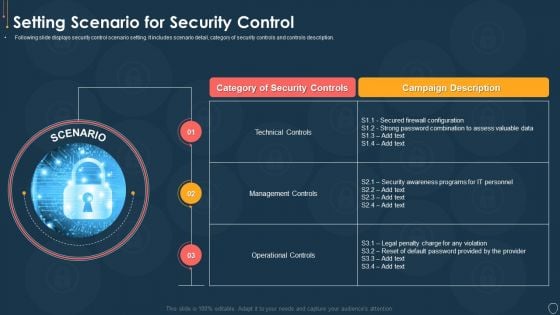
Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
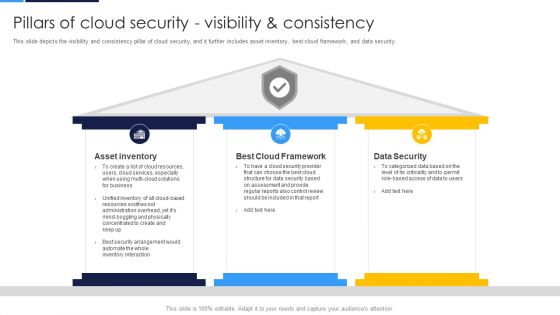
Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Presenting Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Asset Inventory, Cloud Framework, Data Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
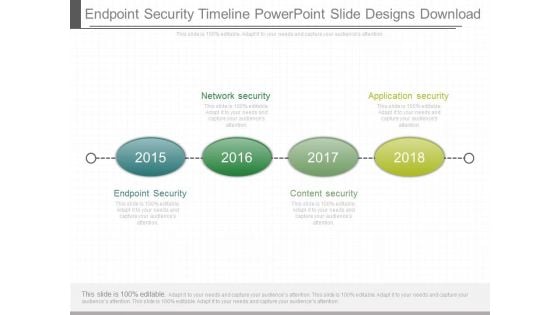
Endpoint Security Timeline Powerpoint Slide Designs Download
This is a endpoint security timeline powerpoint slide designs download. This is a four stage process. The stages in this process are network security, application security, endpoint security, content security.

Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. Find highly impressive Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
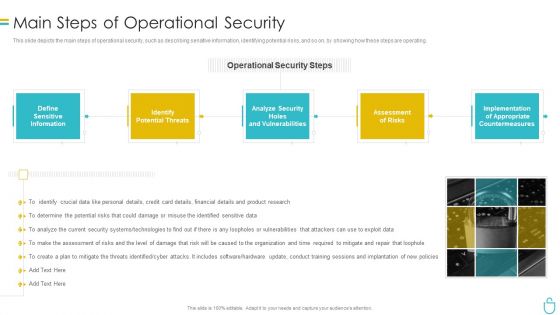
Information Security Main Steps Of Operational Security Ppt Inspiration Show PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting information security main steps of operational security ppt inspiration show pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like sensitive information, potential threats, analyze security, assessment of risks, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
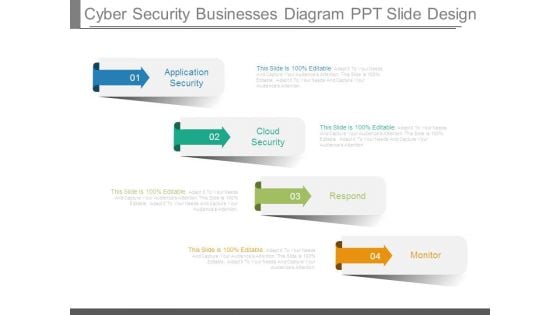
Cyber Security Businesses Diagram Ppt Slide Design
This is a cyber security businesses diagram ppt slide design. This is a four stage process. The stages in this process are application security, cloud security, respond, monitor.
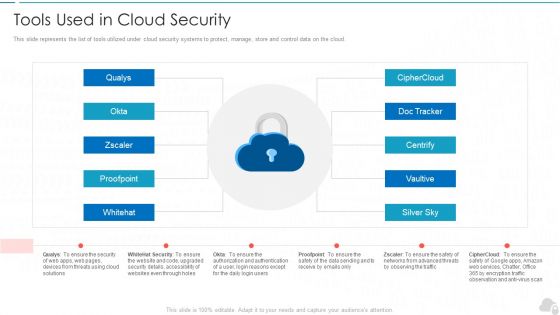
Tools Used In Cloud Security Cloud Computing Security IT Ppt Background Images PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a tools used in cloud security cloud computing security it ppt background images pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like silver sky, centrify, doc tracker, proofpoint, whitehat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
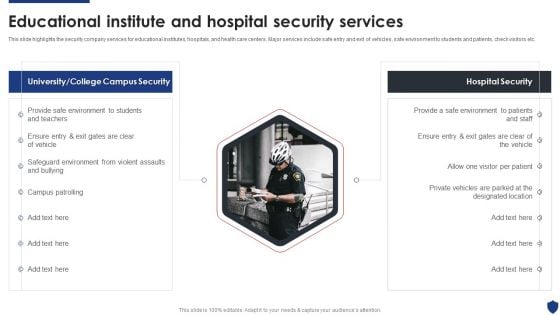
Security Officer Service Company Profile Educational Institute And Hospital Security Services Ideas PDF
This slide highlights the security company services for educational institutes, hospitals, and health care centers. Major services include safe entry and exit of vehicles, safe environment to students and patients, check visitors etc. This is a Security Officer Service Company Profile Educational Institute And Hospital Security Services Ideas PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Provide Safe Environment, Safeguard Environment, Campus Patrolling. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Marketing Problems Analysis Ppt Powerpoint Ideas
This is a email marketing problems analysis ppt powerpoint ideas. This is a six stage process. The stages in this process are permission, privacy, reputation, preferences, expectations, compliance.
Workspace Flexibility Diagram Sample Presentations
This is a workspace flexibility diagram sample presentations. This is a three stage process. The stages in this process are individual control, territoriality, privacy, environmental control.

Personnel Policies Template Ppt Slides Download
This is a personnel policies template ppt slides download. This is a three stage process. The stages in this process are all subjects, top quality, privacy guaranteed.

Cellular Media Networking Diagram Ppt Infographics
This is a cellular media networking diagram ppt infographics. This is a four stage process. The stages in this process are communities, mashups, respect privacy, entertain.
Homeland Security Review Powerpoint Slide Inspiration
This is a homeland security review powerpoint slide inspiration. This is a four stage process. The stages in this process are national security strategy, critical infrastructure and climate, homeland security review, execute order.
Defense And National Security Powerpoint Slide Background
This is a defense and national security powerpoint slide background. This is a five stage process. The stages in this process are defense and national security, homeland security, intelligence operations, law enforcement, international affairs and commerce.

Security Operations Management Sample Presentation Images
This is a security operations management sample presentation images. This is a five stage process. The stages in this process are compliance and validation, security organization, device control, security operations, patch management.

Security Website Template Powerpoint Slide Background Designs
This is a security website template powerpoint slide background designs. This is a six stage process. The stages in this process are inventory, secure coding, secure testing, remediation plan, define next steps, deep scan.
Information Security Survey Template Ppt Example
This is a information security survey template ppt example. This is a four stage process. The stages in this process are information, security, personal, secret.
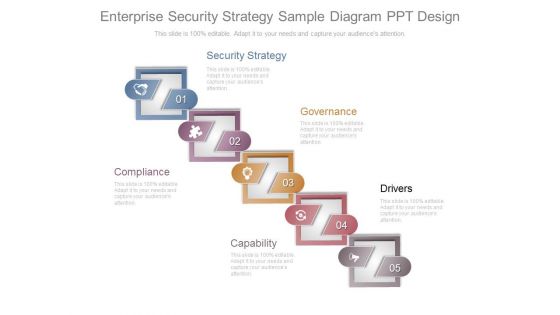
Enterprise Security Strategy Sample Diagram Ppt Design
This is a enterprise security strategy sample diagram ppt design. This is a five stage process. The stages in this process are security strategy, governance, drivers, compliance, capability.
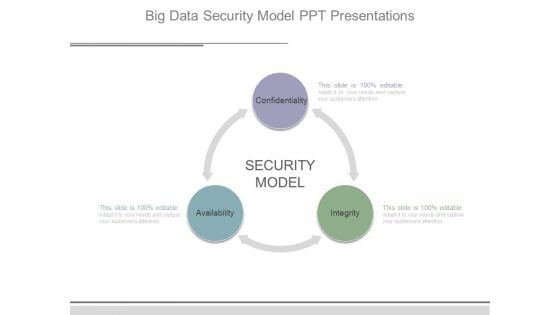
Big Data Security Model Ppt Presentations
This is a big data security model ppt presentations. This is a three stage process. The stages in this process are security model, confidentiality, availability, integrity.
Cyber Security Ppt PowerPoint Presentation Slides Cpb
This is a cyber security ppt powerpoint presentation slides cpb. This is a three stage process. The stages in this process are cyber security.

Essential Pillars Of Cloud Security Brochure PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Essential Pillars Of Cloud Security Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Based Security, Network Security, Identity Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
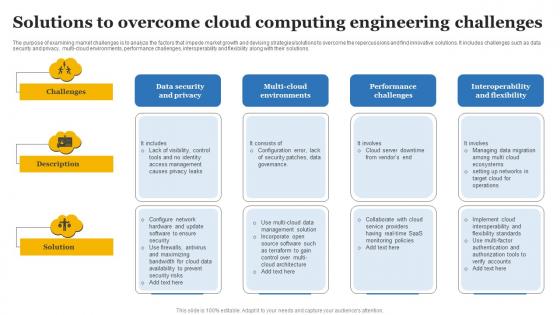
Solutions To Overcome Cloud Computing Engineering Challenges Background Pdf
The purpose of examining market challenges is to analyze the factors that impede market growth and devising strategies solutions to overcome the repercussions and find innovative solutions. It includes challenges such as data security and privacy, multi-cloud environments, performance challenges, interoperability and flexibility along with their solutions. Pitch your topic with ease and precision using this Solutions To Overcome Cloud Computing Engineering Challenges Background Pdf This layout presents information on Data Security And Privacy, Multi Cloud Environments It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of examining market challenges is to analyze the factors that impede market growth and devising strategies solutions to overcome the repercussions and find innovative solutions. It includes challenges such as data security and privacy, multi-cloud environments, performance challenges, interoperability and flexibility along with their solutions.
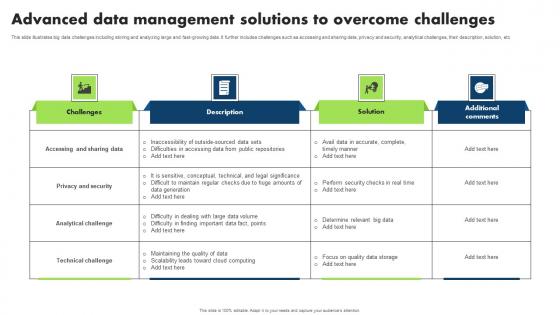
Advanced Data Management Solutions To Overcome Challenges Microsoft Pdf
This slide illustrates big data challenges including storing and analyzing large and fast growing data. It further includes challenges such as accessing and sharing data, privacy and security, analytical challenges, their description, solution, etc Pitch your topic with ease and precision using this Advanced Data Management Solutions To Overcome Challenges Microsoft Pdf. This layout presents information on Accessing Sharing Data, Privacy Security, Analytical Challenge. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates big data challenges including storing and analyzing large and fast growing data. It further includes challenges such as accessing and sharing data, privacy and security, analytical challenges, their description, solution, etc
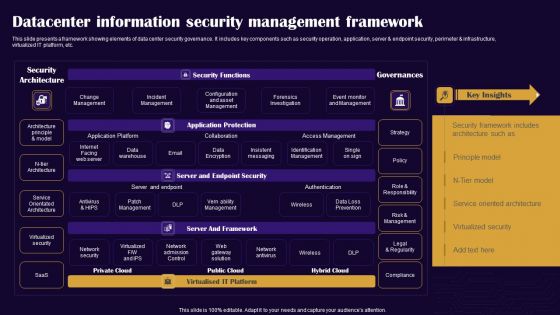
Datacenter Information Security Management Framework Professional PDF
This slide presents a framework showing elements of data center security governance. It includes key components such as security operation, application, server and endpoint security, perimeter and infrastructure, virtualized IT platform, etc. Pitch your topic with ease and precision using this Datacenter Information Security Management Framework Professional PDF. This layout presents information on Security Architecture, Security Functions, Governances. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Web Acceleration Security Software Example Of Ppt
This is a web acceleration security software example of ppt. This is a four stage process. The stages in this process are web acceleration, security software, shopping carts, data services.
Secure Trading Environment Example Ppt Slides
This is a secure trading environment example ppt slides. This is a two stage process. The stages in this process are sell routes, multiple customers, secured payments, buy routes, one interconnect, multiple suppliers, single contract, tel trade.
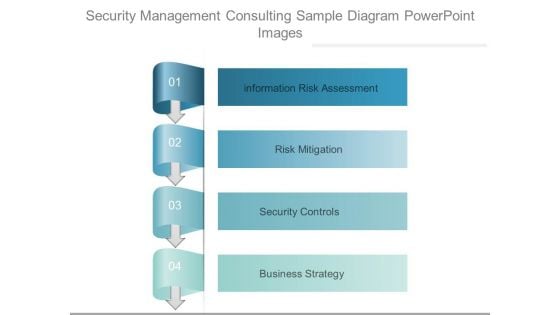
Security Management Consulting Sample Diagram Powerpoint Images
This is a security management consulting sample diagram powerpoint images. This is a four stage process. The stages in this process are information risk assessment, risk mitigation, security controls, business strategy.
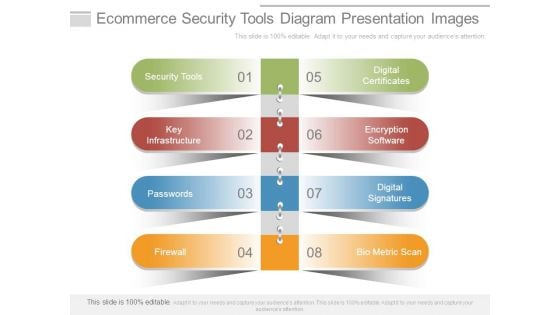
Ecommerce Security Tools Diagram Presentation Images
This is a ecommerce security tools diagram presentation images. This is a eight stage process. The stages in this process are security tools, key infrastructure, passwords, firewall, digital certificates, encryption software, digital signatures, bio metric scan.
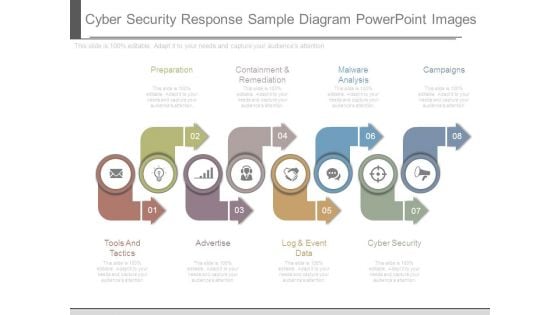
Cyber Security Response Sample Diagram Powerpoint Images
This is a cyber security response sample diagram powerpoint images. This is a eight stage process. The stages in this process are preparation, containment and remediation, malware analysis, campaigns, cyber security, log and event data, advertise, tools and tactics.

Secure Future Technology Leadership Powerpoint Slides Design
This is a secure future technology leadership powerpoint slides design. This is a four stage process. The stages in this process are optimize productivity infrastructure, expand distribution, executive initiatives, secure future technology leadership.
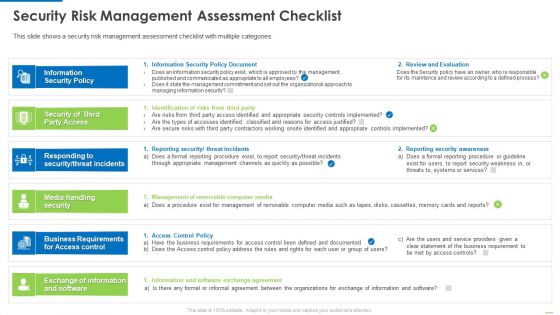
Security Risk Management Assessment Checklist Inspiration PDF
This is a security risk management assessment checklist inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security policy, security of third party access, media handling security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Risk Management Assessment Checklist Structure PDF
Presenting security risk management assessment checklist structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, media handling security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Risk Management Assessment Checklist Mockup PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver an awe inspiring pitch with this creative security risk management assessment checklist mockup pdf bundle. Topics like information security policy document, identification of risks from third party, reporting security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

What Is Cloud Security Guidelines PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Deliver an awe inspiring pitch with this creative What Is Cloud Security Guidelines PDF bundle. Topics like Computing Systems, Protocols, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
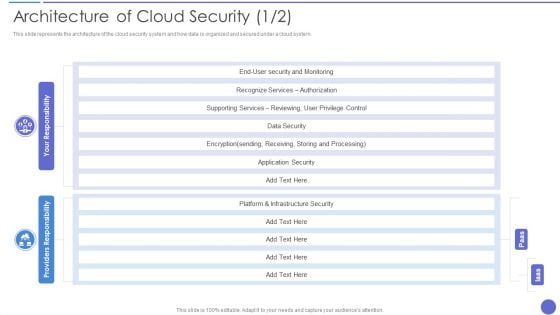
Architecture Of Cloud Security Ideas PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Architecture Of Cloud Security Ideas PDF bundle. Topics like Recognize Services, Supporting Services, Infrastructure Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































