lock
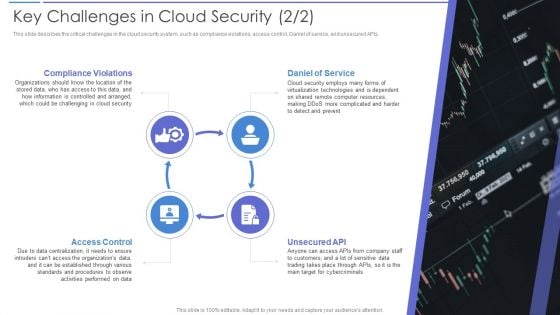
Key Challenges In Cloud Security Portrait PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting Key Challenges In Cloud Security Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Daniel Of Service, Compliance Violations, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
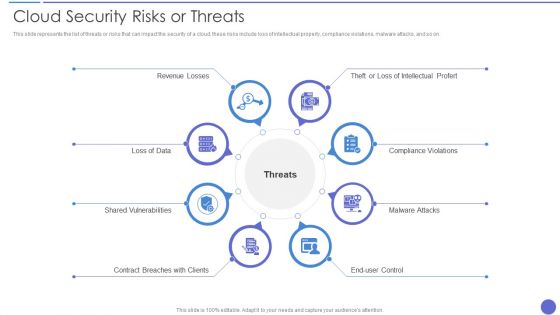
Cloud Security Risks Or Threats Brochure PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Security Risks Or Threats Brochure PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Malware Attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
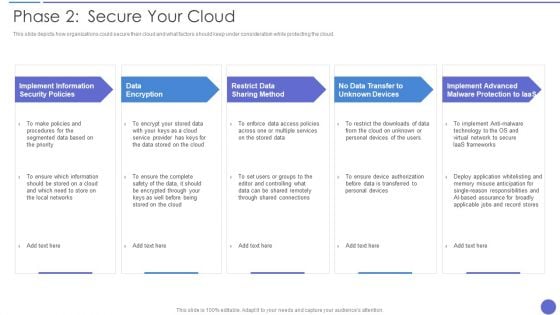
Phase 2 Secure Your Cloud Clipart PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Presenting Phase 2 Secure Your Cloud Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Encryption, Restrict Data Sharing Method, Implement Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
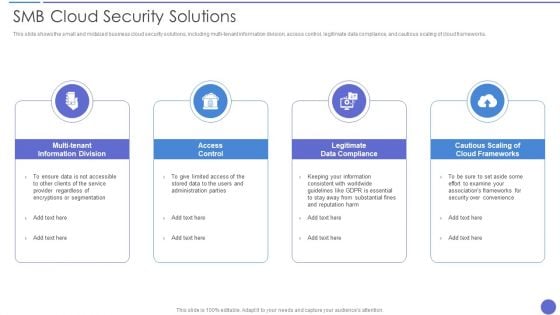
Smb Cloud Security Solutions Download PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. This is a Smb Cloud Security Solutions Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Legitimate Data Compliance, Cloud Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
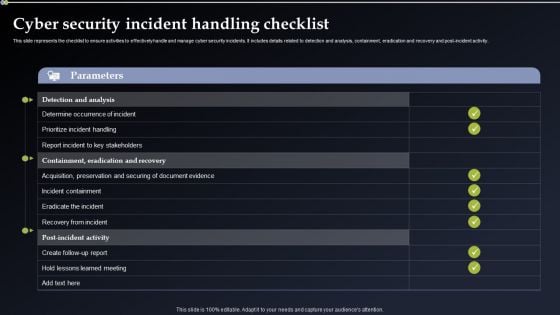
Cyber Security Incident Handling Checklist Elements PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Take your projects to the next level with our ultimate collection of Cyber Security Incident Handling Checklist Elements PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
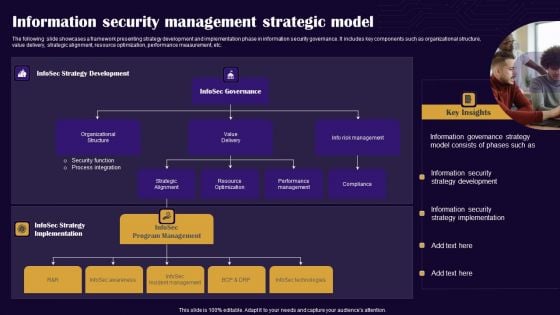
Information Security Management Strategic Model Inspiration PDF
The following slide showcases a framework presenting strategy development and implementation phase in information security governance. It includes key components such as organizational structure, value delivery, strategic alignment, resource optimization, performance measurement, etc. Presenting Information Security Management Strategic Model Inspiration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Value Delivery, Key Insights, Organizational Structure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
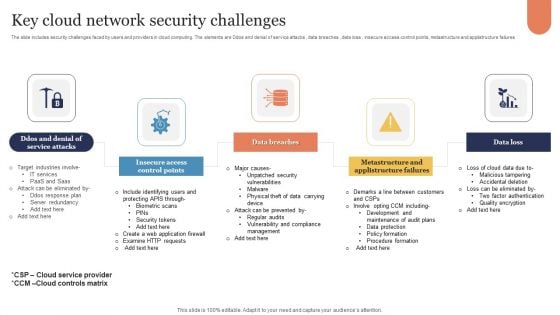
Key Cloud Network Security Challenges Sample PDF
The slide includes security challenges faced by users and providers in cloud computing. The elements are Ddos and denial of service attacks , data breaches , data loss , insecure access control points, metastructure and applistructure failures Persuade your audience using this Key Cloud Network Security Challenges Sample PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Insecure Access Control Points, Data Breaches, Data Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
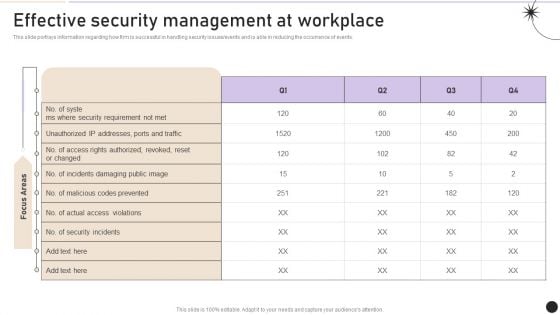
Effective Security Management At Workplace Designs PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Present like a pro with Effective Security Management At Workplace Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
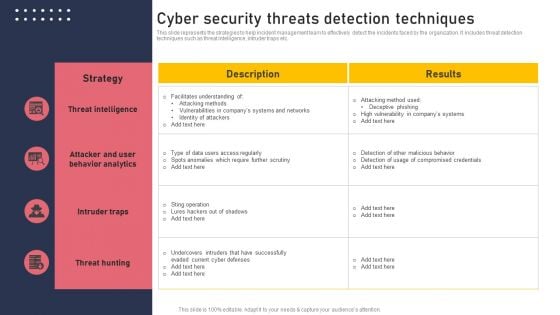
Cyber Security Threats Detection Techniques Demonstration PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Create an editable Cyber Security Threats Detection Techniques Demonstration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Threats Detection Techniques Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
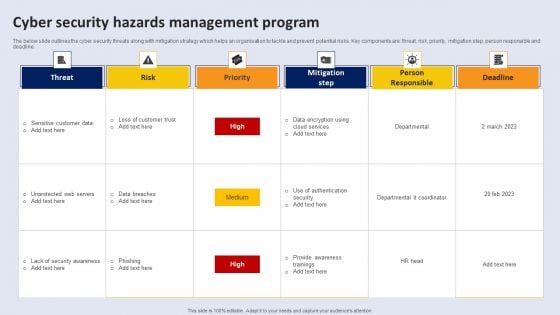
Cyber Security Hazards Management Program Pictures PDF
The below slide outlines the cyber security threats along with mitigation strategy which helps an organisation to tackle and prevent potential risks. Key components are threat, risk, priority, mitigation step, person responsible and deadline.Showcasing this set of slides titled Cyber Security Hazards Management Program Pictures PDF. The topics addressed in these templates are Sensitive Customer, Data Encryption Using. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information IT Security Communication Plan Guidelines PDF
This slide showcases an information cyber security communication plan to effectively communicate cyber incident and action plan. It includes cyber incidents such as virus, spyware, firewall hacking and phishing. Showcasing this set of slides titled Information IT Security Communication Plan Guidelines PDF. The topics addressed in these templates are Run Microsoft Defender Offline, Install Antivirus, Block Traffic Default. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
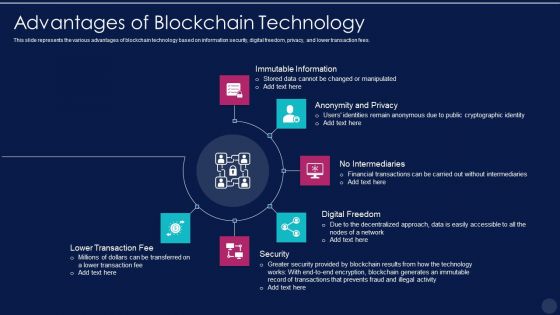
Blockchain Technology Framework IT Pros And Cons Of Consortium Blockchain Elements PDF
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. This is a blockchain technology framework it advantages of blockchain technology graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like immutable information, anonymity and privacy, no intermediaries, digital freedom, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
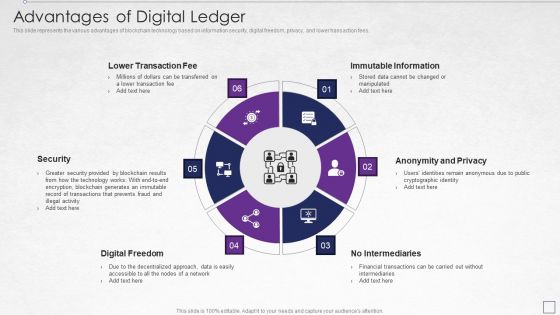
Digitized Record Book Technology Advantages Of Digital Ledger Elements PDF
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. This is a digitized record book technology advantages of digital ledger elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like lower transaction fee, immutable information, anonymity and privacy, security, digital freedom. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
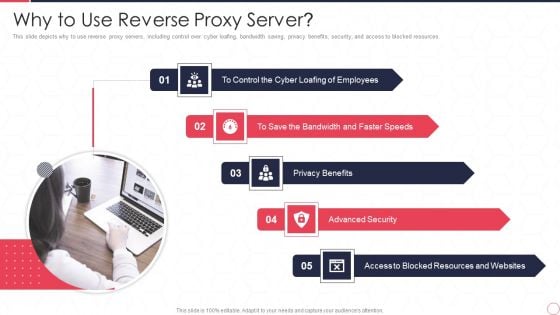
Reverse Proxy Server IT Why To Use Reverse Proxy Server Ppt Gallery Good PDF
This slide depicts why to use reverse proxy servers, including control over cyber loafing, bandwidth saving, privacy benefits, security, and access to blocked resources. Presenting reverse proxy server it why to use reverse proxy server ppt gallery good pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like employees, privacy benefits, advanced security, access to blocked, resources and websites. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
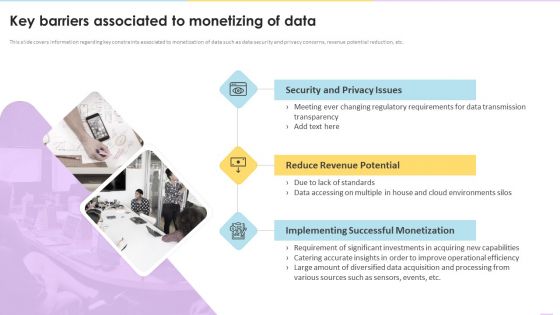
Data Valuation And Monetization Key Barriers Associated To Monetizing Of Data Sample PDF
This slide covers information regarding key constraints associated to monetization of data such as data security and privacy concerns, revenue potential reduction, etc.Presenting Data Valuation And Monetization Key Barriers Associated To Monetizing Of Data Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Security Privacy, Reduce Revenue, Implementing Successful. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Challenges Faced By Information Technology Enabled Services Icons PDF
This slide covers the challenges faced by the information technology enabled services company during providing these services to the customers. It includes data security and privacy, high attrition rate, absence of policy reforms, etc. Presenting Challenges Faced By Information Technology Enabled Services Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Absence Of Policy Reforms, Data Security And Privacy, High Attrition Rates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
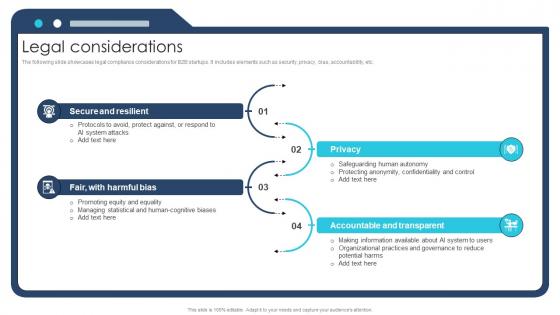
Legal Considerations Ai Chatbot Service Market Entry Strategy
The following slide showcases legal compliance considerations for B2B startups. It includes elements such as security, privacy, bias, accountability, etc.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Legal Considerations Ai Chatbot Service Market Entry Strategy and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide showcases legal compliance considerations for B2B startups. It includes elements such as security, privacy, bias, accountability, etc.

Our Solution Open Source Solution Investor Funding Elevator Pitch Deck
The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform. Make sure to capture your audiences attention in your business displays with our gratis customizable Our Solution Open Source Solution Investor Funding Elevator Pitch Deck. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform.
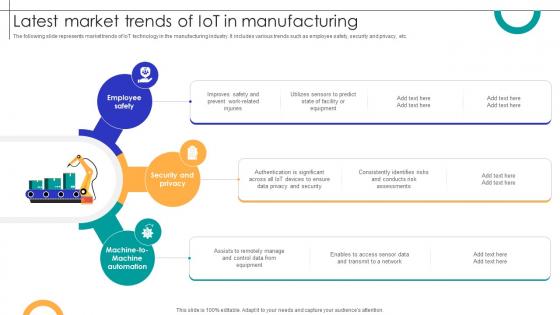
Latest Market Trends Of IOT In Manufacturing Streamlining Production Ppt Powerpoint
The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc. Find a pre-designed and impeccable Latest Market Trends Of IOT In Manufacturing Streamlining Production Ppt Powerpoint The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc.

Secured World PowerPoint Templates Ppt Backgrounds For Slides 0713
Double your chances with our Secured World PowerPoint Templates PPT Backgrounds For Slides. The value of your thoughts will increase two-fold. Charm the audience with your thoughts. Add our security PowerPoint Templates and they will be dotty for you. Double up our umbrellas PowerPoint Templates with your thoughts. They will make an awesome pair. Achievements flow from our Secured World PowerPoint Templates Ppt Backgrounds For Slides 0713. They encourage affirmative action.

Sold Personal Data Security PowerPoint Template 0910
3d illustration of a red Sold sticker with curled ends stuck to a large orange fingerprint on a red surface Our content is special. Join the revolution with our Sold Personal Data Security PowerPoint Template 0910. You'll always stay ahead of the game.
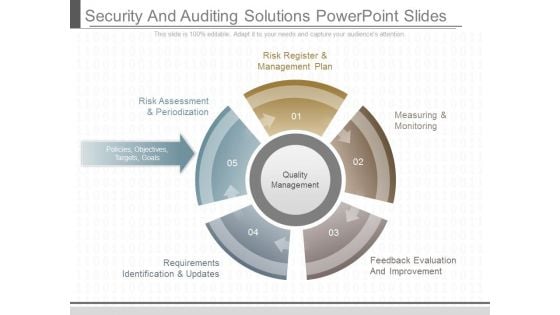
Security And Auditing Solutions Powerpoint Slides
This is a security and auditing solutions powerpoint slides. This is a five stage process. The stages in this process are risk register and management plan, risk assessment and periodization, policies objectives targets goals, requirements identification and updates, measuring and monitoring, feedback evaluation and improvement, quality management.
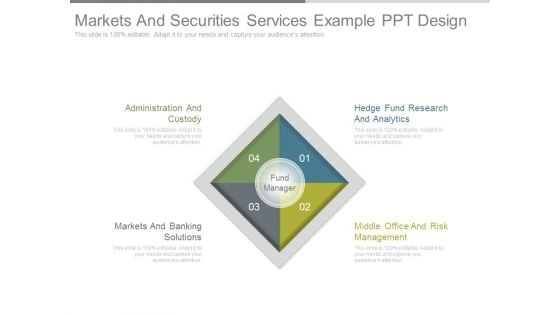
Markets And Securities Services Example Ppt Design
This is a markets and securities services example ppt design. This is a four stage process. The stages in this process are administration and custody, markets and banking solutions, hedge fund research and analytics, middle office and risk management, fund manager.

Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.

Organizational Security Solutions Quotes Ppt Model PDF
Deliver an awe inspiring pitch with this creative organizational security solutions quotes ppt model pdf bundle. Topics like quotes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Organizational Security Solutions Financial Icons PDF
Presenting organizational security solutions financial icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like euro, dollar, pound. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Growing Cyber Security Issues Portrait PDF
Deliver and pitch your topic in the best possible manner with this growing cyber security issues portrait pdf. Use them to share invaluable insights on unprecedented attacks, cyber espionage, data theft and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
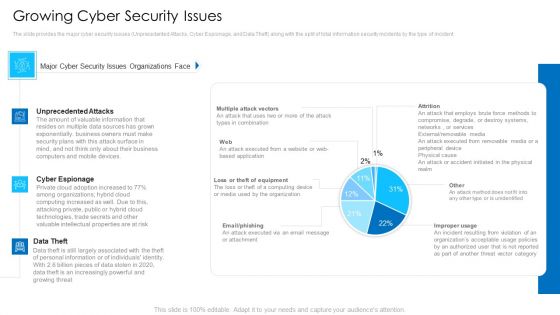
Growing Cyber Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative growing cyber security issues mockup pdf bundle. Topics like unprecedented attacks, cyber espionage, data theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
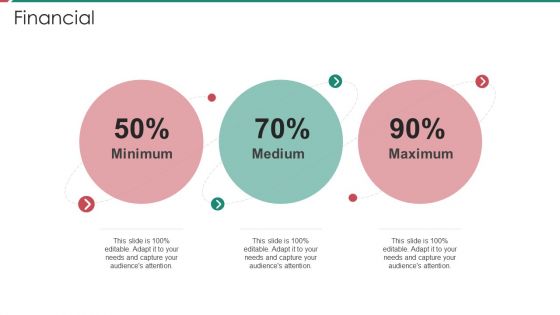
Security And Process Integration Financial Formats PDF
Presenting security and process integration financial formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Agenda For Desktop Security Management Structure PDF
This is a agenda for desktop security management structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan, strategies, information systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For IT Security Designs PDF
Download our innovative and attention grabbing icons slide for it security designs pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
Agenda For Cloud Security Assessment Infographics PDF
Presenting Agenda For Cloud Security Assessment Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Hacker Agenda Background PDF
Presenting IT Security Hacker Agenda Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Strategy Review Keep Keys For Security Concepts
Our business strategy review keep keys for security concepts Powerpoint Templates Allow You To Do It With Ease. Just Like Picking The Low Hanging Fruit.

House With Key Security PowerPoint Templates And PowerPoint Themes 0812
House With Key Security PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with house with key Our House With Key Security PowerPoint Templates And PowerPoint Themes 0812 save time creating a mind blowing presentation. With our money back guarantee you have nothing to lose.
Business Diagram Key With Security Icons Presentation Template
This diagram contains graphics of key with security icons. Download this diagram slide to display concepts of safety and security. This diagram provides an effective way of displaying information you can edit text, color, shade and style as per you need.

Picture Of Cyber Security Background Ppt PowerPoint Presentation Layouts Layout
Presenting this set of slides with name picture of cyber security background ppt powerpoint presentation layouts layout. This is a one stage process. The stage in this process is picture of cyber security background. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
System Security Vector Icon Ppt PowerPoint Presentation Model Templates
Presenting this set of slides with name system security vector icon ppt powerpoint presentation model templates. This is a four stage process. The stages in this process are system security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Computer Security Vector Icon Ppt PowerPoint Presentation File Outline PDF
Presenting this set of slides with name computer security vector icon ppt powerpoint presentation file outline pdf. This is a three stage process. The stages in this process are computer security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security System Image Ppt PowerPoint Presentation Styles Microsoft PDF
Presenting this set of slides with name cyber security system image ppt powerpoint presentation styles microsoft pdf. This is a three stage process. The stages in this process are cyber security system image. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icon For Hotel Safety And Cyber Security Icon Professional PDF
Presenting Icon For Hotel Safety And Cyber Security Icon Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon For Hotel, Safety Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
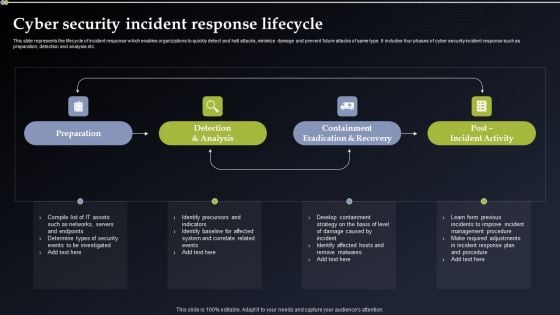
Cyber Security Incident Response Lifecycle Diagrams PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Incident Response Lifecycle Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
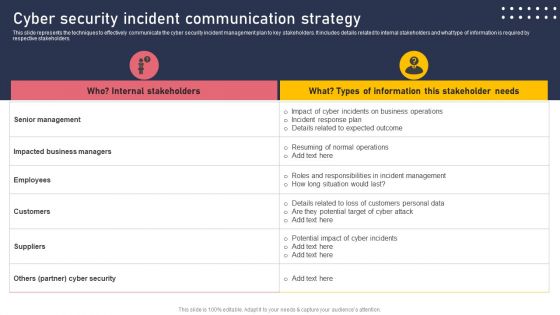
Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
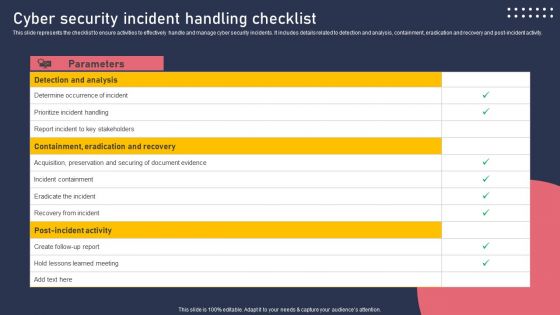
Cyber Security Incident Handling Checklist Information PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Welcome to our selection of the Cyber Security Incident Handling Checklist Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
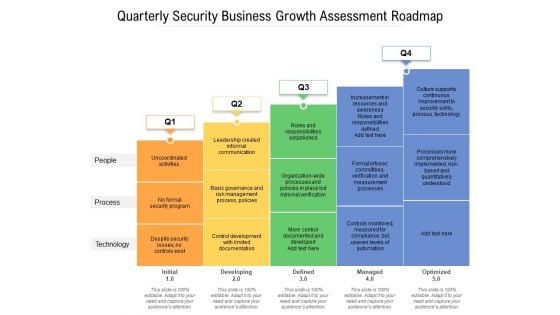
Quarterly Security Business Growth Assessment Roadmap Infographics
Presenting our jaw-dropping quarterly security business growth assessment roadmap infographics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
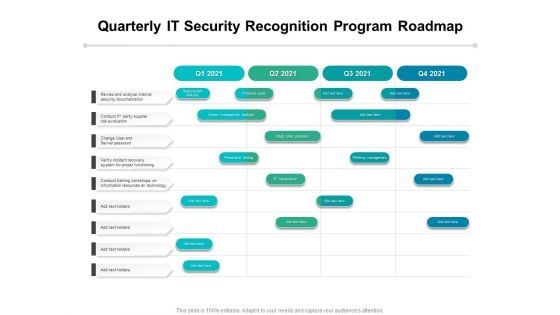
Quarterly IT Security Recognition Program Roadmap Infographics
Presenting our innovatively-structured quarterly it security recognition program roadmap infographics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
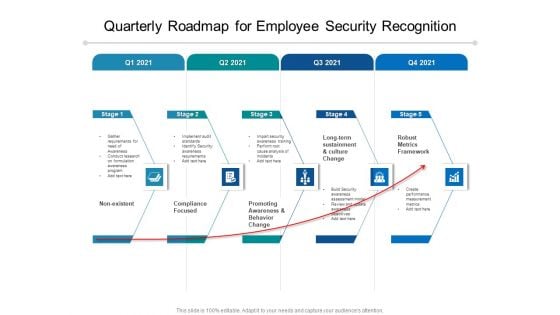
Quarterly Roadmap For Employee Security Recognition Pictures
Introducing our quarterly roadmap for employee security recognition pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Cyber Security Half Yearly Strategic Timeline Icons
Presenting our innovatively structured cyber security half yearly strategic timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
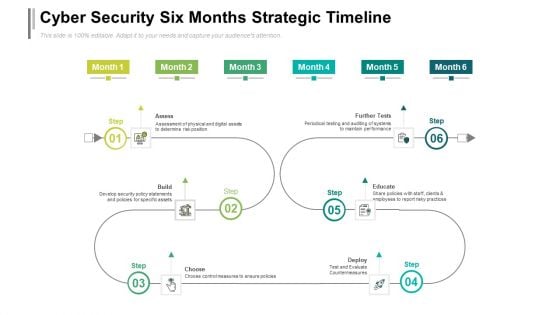
Cyber Security Six Months Strategic Timeline Designs
Introducing our cyber security six months strategic timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
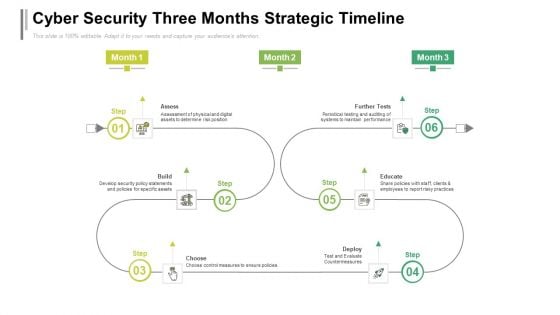
Cyber Security Three Months Strategic Timeline Sample
Presenting our jaw dropping cyber security three months strategic timeline sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
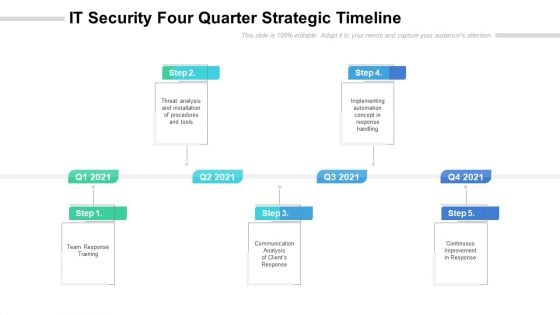
IT Security Four Quarter Strategic Timeline Slides
Presenting our innovatively structured it security four quarter strategic timeline slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
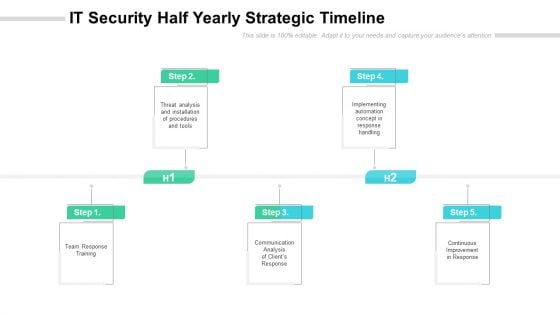
IT Security Half Yearly Strategic Timeline Diagrams
Introducing our it security half yearly strategic timeline diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
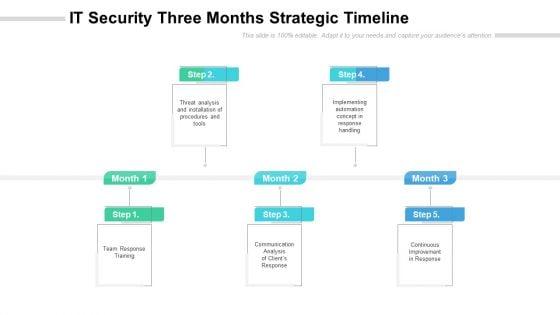
IT Security Three Months Strategic Timeline Portrait
Presenting our jaw dropping it security three months strategic timeline portrait. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Security Strategic Four Quarter Functional Timeline Icons
Presenting our innovatively structured security strategic four quarter functional timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
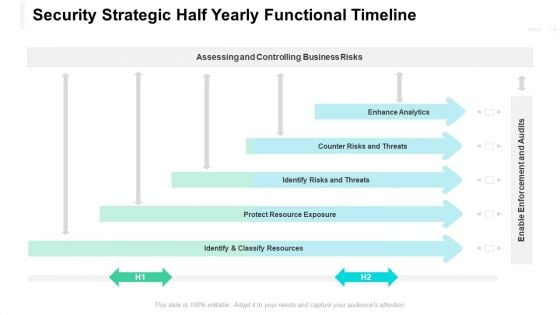
Security Strategic Half Yearly Functional Timeline Designs
Introducing our security strategic half yearly functional timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
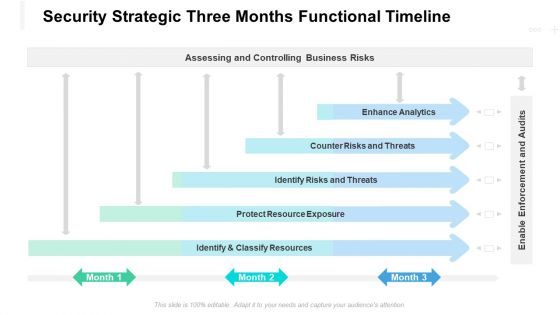
Security Strategic Three Months Functional Timeline Introduction
Presenting our jaw dropping security strategic three months functional timeline introduction. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Information Security Ppt PowerPoint Presentation Complete Deck
Incorporate this Information Security Ppt PowerPoint Presentation Complete Deck to define the objectives of business performance and how to drive results. List goals and outline a plan to achieve all your enterprise targets using this well-crafted complete deck in sixty four slides. Walk your audience through the key objectives of your business set-up, especially for customers and inspire them to work with diligence using this predesigned presentation template. Download now with the added assurance of a 100 percent customizable and editable product.
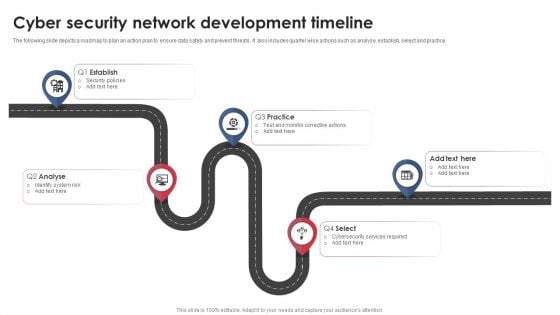
Cyber Security Network Development Timeline Download PDF
The following slide depicts a roadmap to plan an action plan to ensure data safety and prevent threats. It also includes quarter wise actions such as analyse, establish, select and practice. Presenting Cyber Security Network Development Timeline Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Establish, Analyse, Practice. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































