Authentication
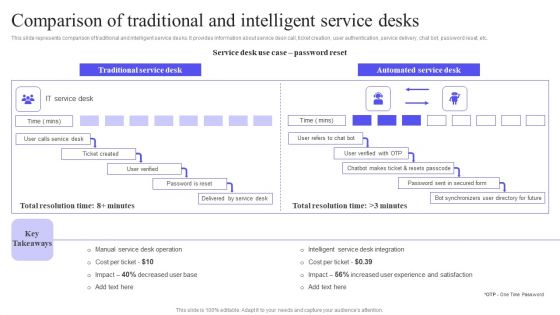
Comparison Of Traditional And Intelligent Service Desks Background PDF
This slide represents comparison of traditional and intelligent service desks. It provides information about service desk call, ticket creation, user authentication, service delivery, chat bot, password reset, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Comparison Of Traditional And Intelligent Service Desks Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Zero Trust Policy And Why You Should Embrace It Cloud Computing Security IT Ppt Infographics Gridlines PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a zero trust policy and why you should embrace it cloud computing security it ppt infographics gridlines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication, device validation, restrict access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
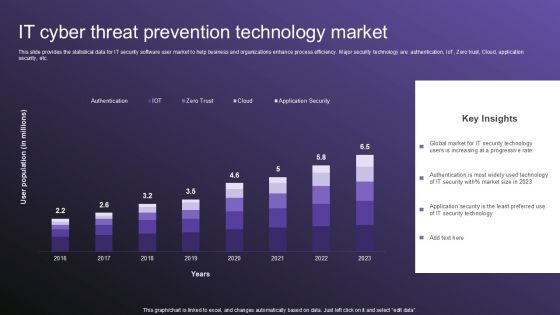
IT Cyber Threat Prevention Technology Market Topics PDF

Digital Transformation Toolkit Accounting Finance Accounting And Financial Software Features Slides PDF
In this slide, we have showcased key specifications and features that can help in achieving maximum efficiency in business operations like sales invoice, registration, advance security and input tax credit. This is a digital transformation toolkit accounting finance accounting and financial software features slides pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like export management, client authentication, latest security features. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
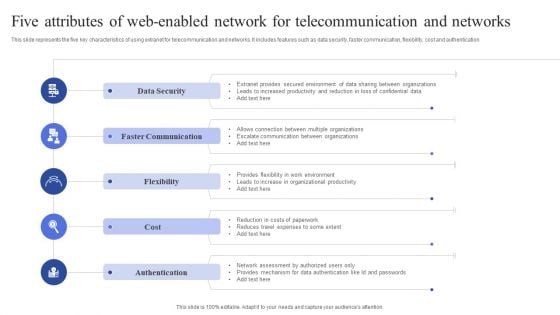
Five Attributes Of Web Enabled Network For Telecommunication And Networks Guidelines PDF
This slide represents the five key characteristics of using extranet for telecommunication and networks. It includes features such as data security, faster communication, flexibility, cost and authentication. Persuade your audience using this Five Attributes Of Web Enabled Network For Telecommunication And Networks Guidelines PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Security, Faster Communication, Flexibility. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT System Risk Management Guide Preventive IT Technical Control Measures Graphics PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. This IT System Risk Management Guide Preventive IT Technical Control Measures Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.
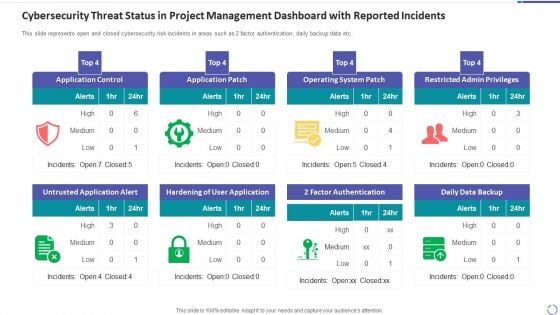
Cybersecurity Threat Status In Project Management Dashboard With Reported Incidents Introduction PDF
This slide represents open and closed cybersecurity risk incidents in areas such as 2 factor authentication, daily backup data etc. Showcasing this set of slides titled cybersecurity threat status in project management dashboard with reported incidents introduction pdf. The topics addressed in these templates are application control, application patch, operating system patch, restricted admin privileges, untrusted application alert. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Guide For Software Developers Feature Release Schedule For New Product Pictures PDF
Mentioned slide showcases release schedule that will assist product development manager to address project manager about the various features to be added in the product after releasing each versions. Deliver and pitch your topic in the best possible manner with this guide for software developers feature release schedule for new product pictures pdf. Use them to share invaluable insights on authentication, create shipment, shipment index, invoice assignment, dashboard, reporting and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
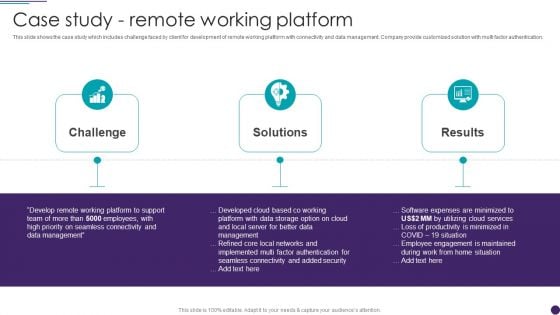
IT Services Business Profile Case Study Remote Working Platform Infographics PDF
This slide shows the case study which includes challenge faced by client for development of remote working platform with connectivity and data management. Company provide customized solution with multi factor authentication. Presenting IT Services Business Profile Case Study Remote Working Platform Infographics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Challenge, Solutions, Results. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

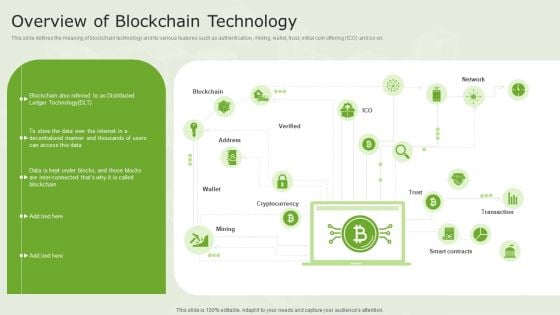
Blockchain And DLT Framework Overview Of Blockchain Technology Diagrams PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. This is a Blockchain And DLT Framework Overview Of Blockchain Technology Diagrams PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Blockchain, Cryptocurrency, Transaction, Smart Contracts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
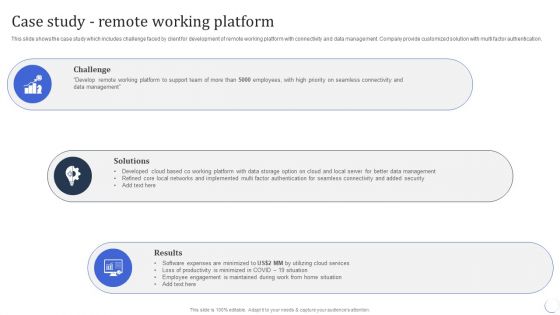
Infotech Solutions Research And Development Company Summary Case Study Remote Working Platform Diagrams PDF
This slide shows the case study which includes challenge faced by client for development of remote working platform with connectivity and data management. Company provide customized solution with multi factor authentication. This is a Infotech Solutions Research And Development Company Summary Case Study Remote Working Platform Diagrams PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Challenge, Solutions, Results. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Application Services Company Outline Case Study Remote Working Platform Icons PDF
This slide shows the case study which includes challenge faced by client for development of remote working platform with connectivity and data management. Company provide customized solution with multi factor authentication. This is a IT Application Services Company Outline Case Study Remote Working Platform Icons PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Solutions, Results, Challenge. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
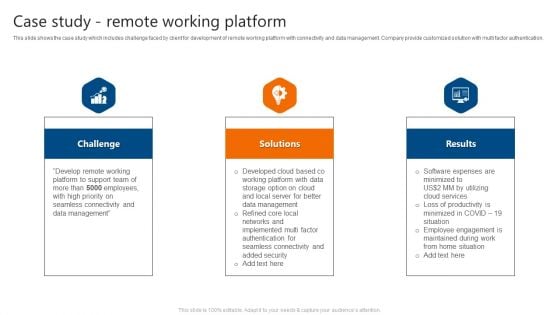
Case Study Remote Working Platform IT Software Development Company Profile Diagrams PDF
This slide shows the case study which includes challenge faced by client for development of remote working platform with connectivity and data management. Company provide customized solution with multi factor authentication. This is a Case Study Remote Working Platform IT Software Development Company Profile Diagrams PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Challenge, Solutions, Results. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
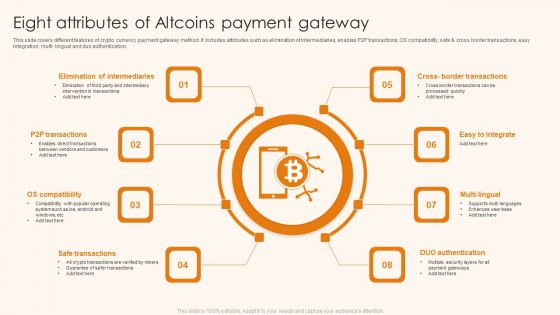
Eight Attributes Of Altcoins Payment Gateway Ppt Show Example Topics PDF
This slide covers different features of crypto currency payment gateway method. It includes attributes such as elimination of intermediaries, enables P2P transactions, OS compatibility, safe and cross border transactions, easy integration, multi- lingual and duo authentication. Presenting Eight Attributes Of Altcoins Payment Gateway Ppt Show Example Topics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Elimination Intermediaries, P2P Transactions, OS Compatibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
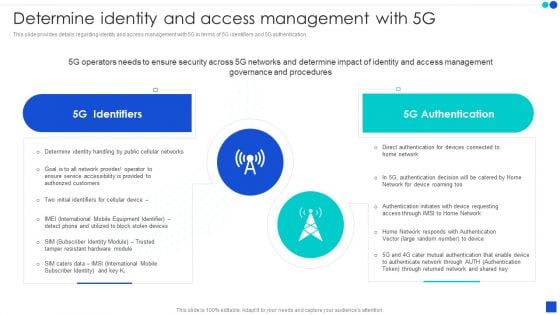
5G Technology Development For Digital Transformation Determine Identity And Access Management With 5G Background PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download 5G Technology Development For Digital Transformation Determine Identity And Access Management With 5G Background PDF from Slidegeeks and deliver a wonderful presentation.
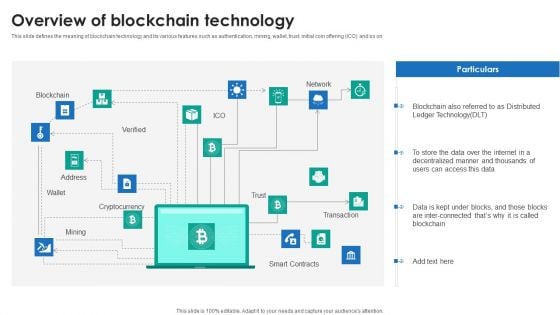
P2P Ledger Overview Of Blockchain Technology Demonstration PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on.The P2P Ledger Overview Of Blockchain Technology Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
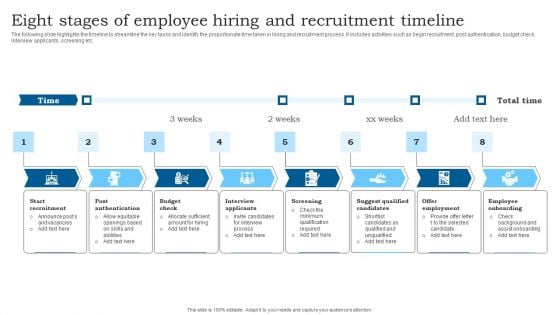
Eight Stages Of Employee Hiring And Recruitment Timeline Template PDF
The following slide highlights the timeline to streamline the key tasks and identify the proportionate time taken in hiring and recruitment process. It includes activities such as begin recruitment, post authentication, budget check, interview applicants, screening etc. Presenting Eight Stages Of Employee Hiring And Recruitment Timeline Template PDF to dispense important information. This template comprises Eight stages. It also presents valuable insights into the topics including Eight Stages, Employee Hiring, Recruitment Timeline. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

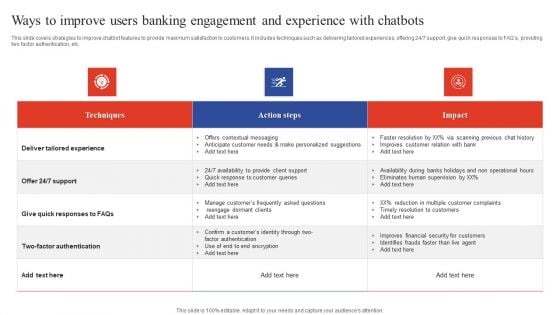
Ways To Improve Users Banking Engagement And Experience With Chatbots Information PDF
This slide covers strategies to improve chatbot features to provide maximum satisfaction to customers. It includes techniques such as delivering tailored experiences, offering 24 or 7 support, give quick responses to FAQs, providing two factor authentication, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Ways To Improve Users Banking Engagement And Experience With Chatbots Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
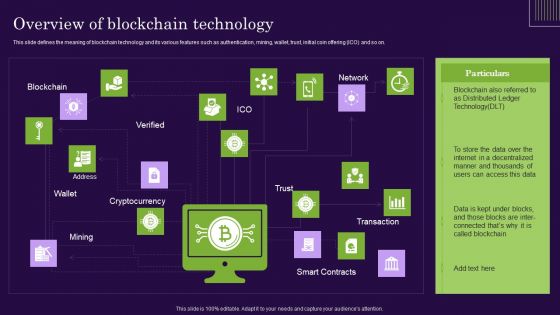
DLT Technology Overview Of Blockchain Technology Ppt Infographics Infographic Template PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. Take your projects to the next level with our ultimate collection of DLT Technology Overview Of Blockchain Technology Ppt Infographics Infographic Template PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors thell make your projects stand out from the rest.
Managed Blockchain Service Overview Of Blockchain Technology Sample PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. Welcome to our selection of the Managed Blockchain Service Overview Of Blockchain Technology Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
Deployment Of Omnichannel Banking Solutions Ways To Improve Users Banking Engagement And Experience Mockup PDF
This slide covers strategies to improve chatbot features to provide maximum satisfaction to customers. It includes techniques such as delivering tailored experiences, offering 24 7 support, give quick responses to FAQ s, providing two factor authentication, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Deployment Of Omnichannel Banking Solutions Ways To Improve Users Banking Engagement And Experience Mockup PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
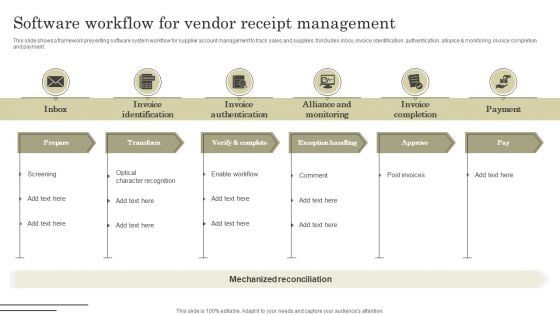
Software Workflow For Vendor Receipt Management Portrait PDF
This slide shows a framework presenting software system workflow for supplier account management to track sales and supplies. It includes inbox, invoice identification, authentication, alliance and monitoring, invoice completion and payment. Presenting Software Workflow For Vendor Receipt Management Portrait PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prepare, Transform, Verify and complete, Exception handling, Approve, Pay. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
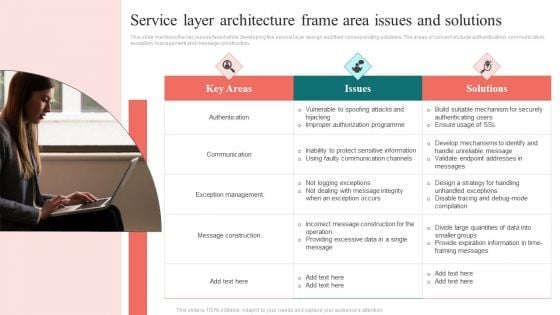
Service Layer Architecture Frame Area Issues And Solutions Information PDF
This slide mentions the key issues faced while developing the service layer design and their corresponding solutions. The areas of concern include authentication, communication, exception management and message construction. Presenting Service Layer Architecture Frame Area Issues And Solutions Information PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Communication, Message Construction, Exception Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
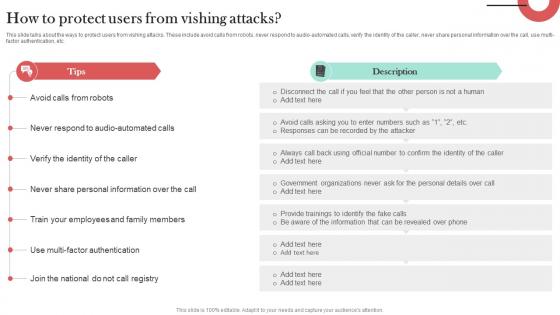
How To Protect Users From Vishing Attacks Man In The Middle Phishing IT
This slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc. Are you searching for a How To Protect Users From Vishing Attacks Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download How To Protect Users From Vishing Attacks Man In The Middle Phishing IT from Slidegeeks today. This slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc.

Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V
This slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc.
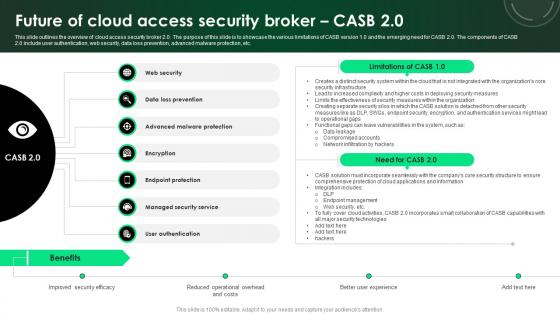
CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0 for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc.

Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V
This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc.
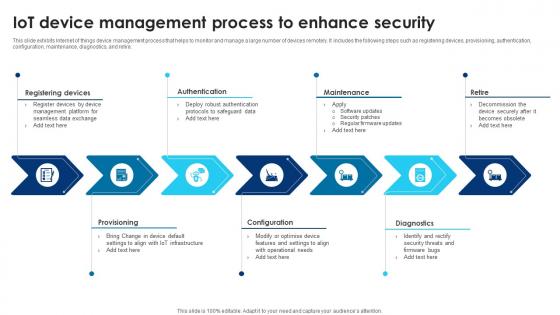
Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V
This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire. Are you searching for a Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V from Slidegeeks today. This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire.
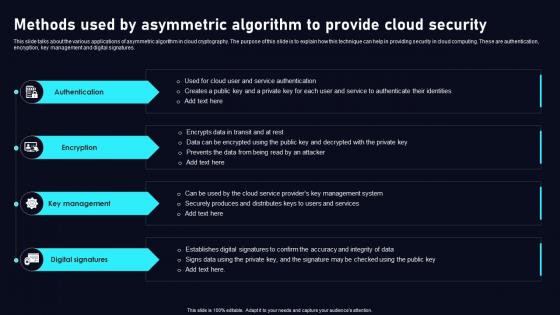
Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.

Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf today and make your presentation stand out from the rest The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc.
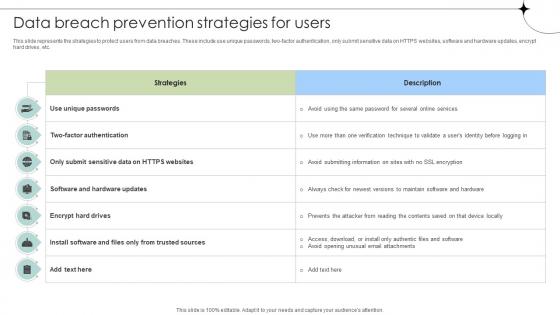
Data Breach Prevention Strategies For Users Data Fortification Strengthening Defenses
This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Users Data Fortification Strengthening Defenses was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Users Data Fortification Strengthening Defenses. This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc.
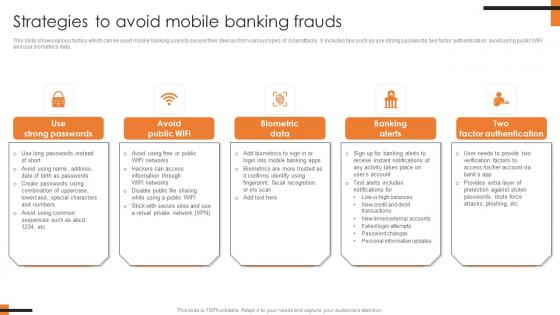
Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.This modern and well-arranged Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.
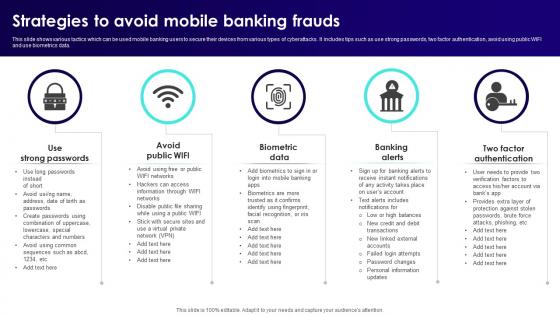
Wireless Banking To Improve Strategies To Avoid Mobile Banking Frauds Fin SS V
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data. Welcome to our selection of the Wireless Banking To Improve Strategies To Avoid Mobile Banking Frauds Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.

Mastering Blockchain Wallets Best Practices For Enabling Blockchain Wallet Safety BCT SS V
This slide covers tips for enabling safety of blockchain wallets helping users. The purpose of this template is to provide an overview on key practices to be followed such as keeping small quantities of crypto assets in online, generating impenetrable wallets requiring authentication, ensuring wallet software and mobile is constantly updated, securing wallets with Fort Knox by using complex long form password, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Mastering Blockchain Wallets Best Practices For Enabling Blockchain Wallet Safety BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide covers tips for enabling safety of blockchain wallets helping users. The purpose of this template is to provide an overview on key practices to be followed such as keeping small quantities of crypto assets in online, generating impenetrable wallets requiring authentication, ensuring wallet software and mobile is constantly updated, securing wallets with Fort Knox by using complex long form password, etc.

Process To Add Funds In Digital Wallet In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the step to add funds to an e-wallet that helps to understand the working. The steps involve selecting a funding source, link and authentication, and confirmation. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Process To Add Funds In Digital Wallet In Depth Guide To Digital Wallets Fin SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide highlights the step to add funds to an e-wallet that helps to understand the working. The steps involve selecting a funding source, link and authentication, and confirmation.
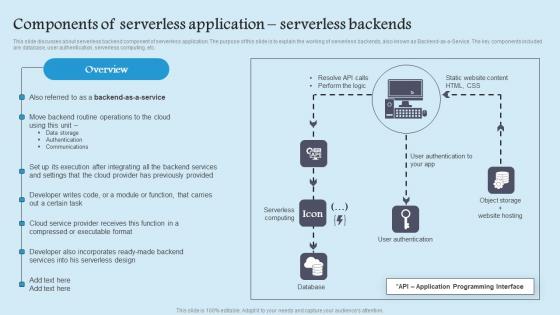
Components Serverless Application Role Serverless Computing Modern Technology Rules Pdf
This slide discusses about serverless backend component of serverless application. The purpose of this slide is to explain the working of serverless backends, also known as Backend as a Service. The key components included are database, user authentication, serverless computing, etc. Slidegeeks has constructed Components Serverless Application Role Serverless Computing Modern Technology Rules Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. This slide discusses about serverless backend component of serverless application. The purpose of this slide is to explain the working of serverless backends, also known as Backend as a Service. The key components included are database, user authentication, serverless computing, etc.
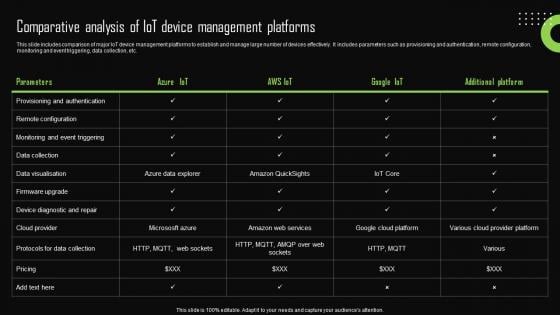
Comparative Analysis Of Iot Device Management Iot Device Management Portrait Pdf
This slide includes comparison of major IoT device management platforms to establish and manage large number of devices effectively. It includes parameters such as provisioning and authentication, remote configuration, monitoring and event triggering, data collection, etc. Find highly impressive Comparative Analysis Of Iot Device Management Iot Device Management Portrait Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comparative Analysis Of Iot Device Management Iot Device Management Portrait Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide includes comparison of major IoT device management platforms to establish and manage large number of devices effectively. It includes parameters such as provisioning and authentication, remote configuration, monitoring and event triggering, data collection, etc.
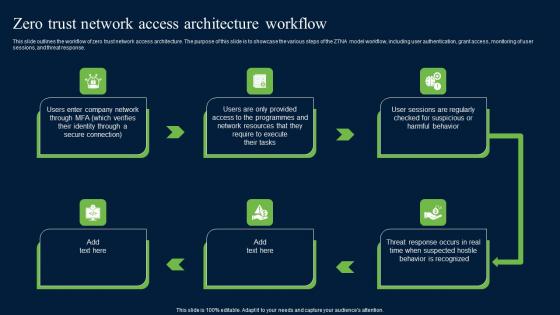
Zero Trust Network Access Architecture Workflow Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Network Access Architecture Workflow Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Network Access Architecture Workflow Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Mastering Blockchain Wallets Tips For Selecting The Ideal Crypto Software Wallet BCT SS V
This side covers recommendations for selecting most suitable software wallet for managing their cryptocurrencies. The purpose of this template is to provide best practices for selecting ideal software wallet such as checking reputation of company, two factor authentication, ensuring backup mechanism, number of cryptocurrencies, finding adequate transparency, etc. Explore a selection of the finest Mastering Blockchain Wallets Tips For Selecting The Ideal Crypto Software Wallet BCT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Mastering Blockchain Wallets Tips For Selecting The Ideal Crypto Software Wallet BCT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This side covers recommendations for selecting most suitable software wallet for managing their cryptocurrencies. The purpose of this template is to provide best practices for selecting ideal software wallet such as checking reputation of company, two factor authentication, ensuring backup mechanism, number of cryptocurrencies, finding adequate transparency, etc.
Circular Years Timeline Display 2 PowerPoint Slides And Ppt Diagram Templates
Our Circular Years Timeline Display 2 PowerPoint Slides And Ppt Diagram Templates are designed for authenticity. They do not encourage any farce.
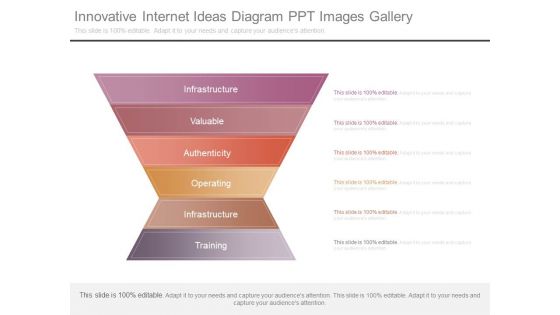
Innovative Internet Ideas Diagram Ppt Images Gallery
This is a innovative internet ideas diagram ppt images gallery. This is a six stage process. The stages in this process are infrastructure, valuable, authenticity, operating, infrastructure, training.
Brand Communication Ppt PowerPoint Presentation Icon Ideas
This is a brand communication ppt powerpoint presentation icon ideas. This is a twelve stage process. The stages in this process are quality, accessible, authenticity, variety, convenient, affordable.

Mobile Security Powerpoint Presentation Slides
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Mobile Security Powerpoint Presentation Slides has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has Mobile Threat Defense, Mobile Authentication, Mobile Encryption, Mobile Privacy, Mobile Vulnerability Management-slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance. The mobile security powerpoint template covers key aspects of mobile security, including threats, vulnerabilities, best practices, and implementation strategies.
Leverage Strong And Complex Password Management Ppt PowerPoint Presentation File Icon PDF
The following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi-factor authentication, conducting test etc. Do you know about Slidesgeeks Leverage Strong And Complex Password Management Ppt PowerPoint Presentation File Icon PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Dos And Donts Of Cyber Security Awareness Professional PDF
The purpose of this slide is to highlight the major dos and donts of cyber security awareness. The dos covered in the slide are using multi-factor authentication, password manager, frequently changing the password, etc. The donts are using the same password, simple and short passwords, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Dos And Donts Of Cyber Security Awareness Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
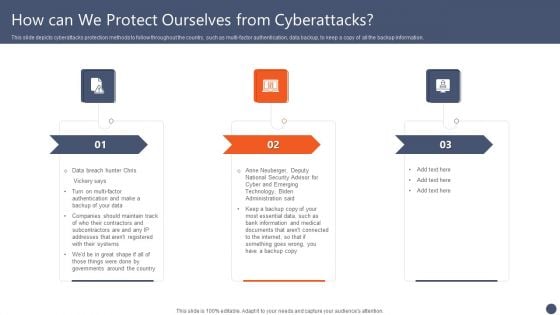
Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

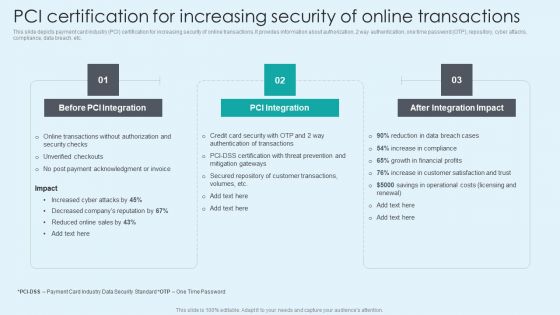
PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
PCI Certification For Increasing Security Of Online Transactions Background PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Explore a selection of the finest PCI Certification For Increasing Security Of Online Transactions Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PCI Certification For Increasing Security Of Online Transactions Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
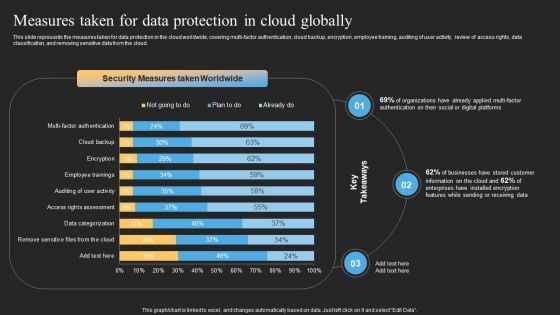
Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF
This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. This Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. The Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
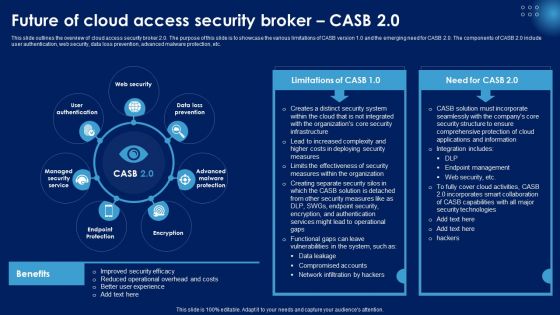
Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Explore a selection of the finest Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
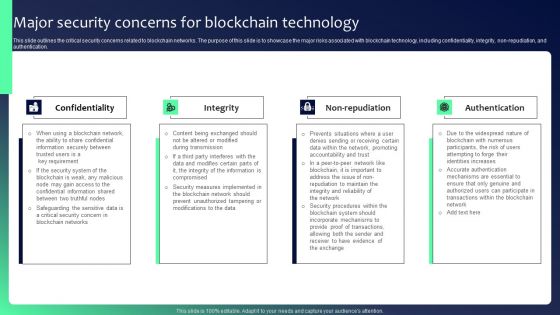
Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF
This slide outlines the critical security concerns related to blockchain networks. The purpose of this slide is to showcase the major risks associated with blockchain technology, including confidentiality, integrity, non-repudiation, and authentication. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF today and make your presentation stand out from the rest
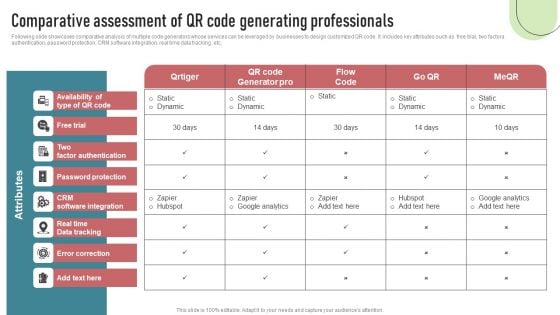
Cashless Payment Strategies To Enhance Business Performance Comparative Assessment Of QR Code Guidelines PDF
Following slide showcases comparative analysis of multiple code generators whose services can be leveraged by businesses to design customized QR code. It includes key attributes such as free trial, two factora authentication, password protection, CRM software integration, real time data tracking, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cashless Payment Strategies To Enhance Business Performance Comparative Assessment Of QR Code Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Cashless Payment Strategies To Enhance Business Performance Comparative Assessment Of QR Code Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data. This modern and well arranged Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
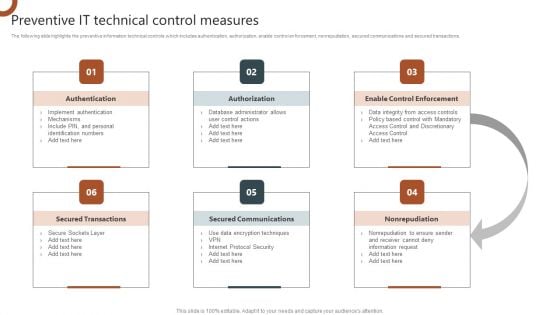
Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Slidegeeks is here to make your presentations a breeze with Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Explore a selection of the finest CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.


 Continue with Email
Continue with Email

 Home
Home


































