Breakthrough
Serverless Computing System Role Serverless Computing Modern Technology Topics Pdf
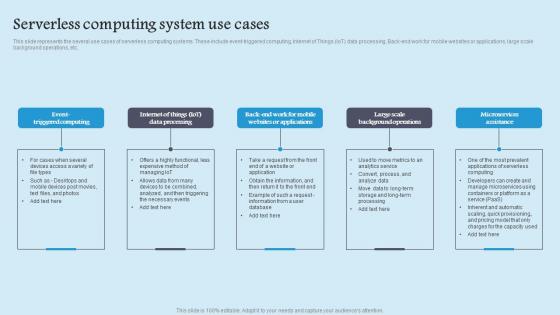
This slide represents the several use cases of serverless computing systems. These include event triggered computing, Internet of Things IoT data processing, Back end work for mobile websites or applications, large scale background operations, etc. Take your projects to the next level with our ultimate collection of Serverless Computing System Role Serverless Computing Modern Technology Topics Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the several use cases of serverless computing systems. These include event triggered computing, Internet of Things IoT data processing, Back end work for mobile websites or applications, large scale background operations, etc.
Services Provided By Serverless Role Serverless Computing Modern Technology Graphics Pdf
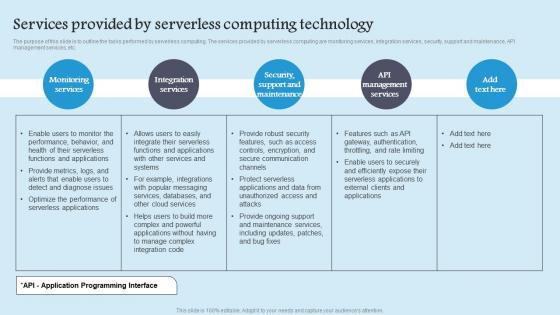
The purpose of this slide is to outline the tasks performed by serverless computing. The services provided by serverless computing are monitoring services, integration services, security, support and maintenance, API management services, etc. Do you know about Slidesgeeks Services Provided By Serverless Role Serverless Computing Modern Technology Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of this slide is to outline the tasks performed by serverless computing. The services provided by serverless computing are monitoring services, integration services, security, support and maintenance, API management services, etc.
Top Serverless Computing Role Serverless Computing Modern Technology Rules Pdf
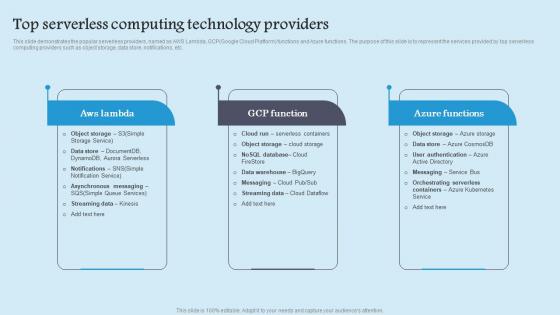
This slide demonstrates the popular serverless providers, named as AWS Lambda, GCPGoogle Cloud Platform functions and Azure functions. The purpose of this slide is to represent the services provided by top serverless computing providers such as object storage, data store, notifications, etc. Want to ace your presentation in front of a live audience Our Top Serverless Computing Role Serverless Computing Modern Technology Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the popular serverless providers, named as AWS Lambda, GCPGoogle Cloud Platform functions and Azure functions. The purpose of this slide is to represent the services provided by top serverless computing providers such as object storage, data store, notifications, etc.
Benefits Of Digital Biomarkers Biomedical Data Science And Health Informatics Diagrams Pdf
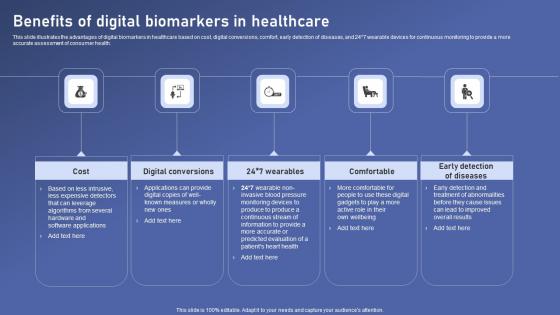
This slide illustrates the advantages of digital biomarkers in healthcare based on cost, digital conversions, comfort, early detection of diseases, and 24 7 wearable devices for continuous monitoring to provide a more accurate assessment of consumer health. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Benefits Of Digital Biomarkers Biomedical Data Science And Health Informatics Diagrams Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide illustrates the advantages of digital biomarkers in healthcare based on cost, digital conversions, comfort, early detection of diseases, and 24 7 wearable devices for continuous monitoring to provide a more accurate assessment of consumer health.
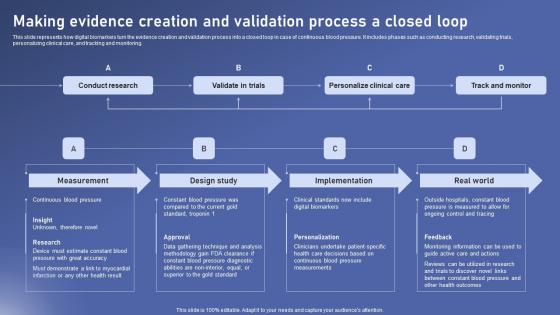
Making Evidence Creation Biomedical Data Science And Health Informatics Professional Pdf
This slide represents how digital biomarkers turn the evidence creation and validation process into a closed loop in case of continuous blood pressure. It includes phases such as conducting research, validating trials, personalizing clinical care, and tracking and monitoring. Take your projects to the next level with our ultimate collection of Making Evidence Creation Biomedical Data Science And Health Informatics Professional Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents how digital biomarkers turn the evidence creation and validation process into a closed loop in case of continuous blood pressure. It includes phases such as conducting research, validating trials, personalizing clinical care, and tracking and monitoring.
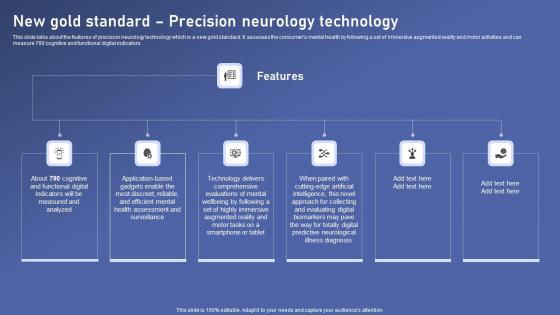
New Gold Standard Precision Biomedical Data Science And Health Informatics Microsoft Pdf
This slide talks about the features of precision neurology technology which is a new gold standard. It assesses the consumers mental health by following a set of immersive augmented reality and motor activities and can measure 790 cognitive and functional digital indicators. Boost your pitch with our creative New Gold Standard Precision Biomedical Data Science And Health Informatics Microsoft Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the features of precision neurology technology which is a new gold standard. It assesses the consumers mental health by following a set of immersive augmented reality and motor activities and can measure 790 cognitive and functional digital indicators.

Portable Smart Devices Used Biomedical Data Science And Health Informatics Microsoft Pdf
This slide depicts the portable devices used for digital biomarkers and some major players in the industry. It includes smartphones and tablets, smart inhalers, electrocardiogram monitors, and contactless sleep monitors. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Portable Smart Devices Used Biomedical Data Science And Health Informatics Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the portable devices used for digital biomarkers and some major players in the industry. It includes smartphones and tablets, smart inhalers, electrocardiogram monitors, and contactless sleep monitors.
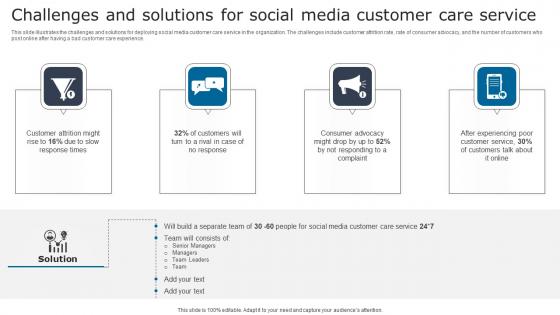
Challenges And Solutions Social Digital Signage In Internal Communication Channels Portrait Pdf
This slide illustrates the challenges and solutions for deploying social media customer care service in the organization. The challenges include customer attrition rate, rate of consumer advocacy, and the number of customers who post online after having a bad customer care experience. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Challenges And Solutions Social Digital Signage In Internal Communication Channels Portrait Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Challenges And Solutions Social Digital Signage In Internal Communication Channels Portrait Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide illustrates the challenges and solutions for deploying social media customer care service in the organization. The challenges include customer attrition rate, rate of consumer advocacy, and the number of customers who post online after having a bad customer care experience.
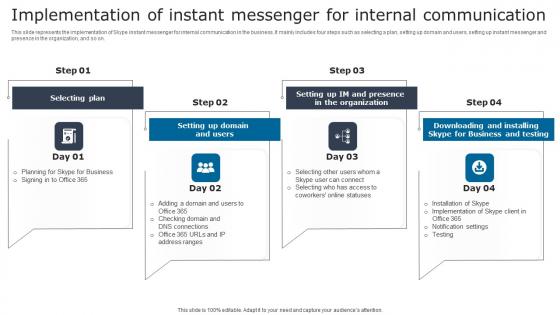
Implementation Of Instant Messenger Digital Signage In Internal Communication Channels Structure Pdf
This slide represents the implementation of Skype instant messenger for internal communication in the business. It mainly includes four steps such as selecting a plan, setting up domain and users, setting up instant messenger and presence in the organization, and so on. Boost your pitch with our creative Implementation Of Instant Messenger Digital Signage In Internal Communication Channels Structure Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the implementation of Skype instant messenger for internal communication in the business. It mainly includes four steps such as selecting a plan, setting up domain and users, setting up instant messenger and presence in the organization, and so on.

Outdated Internal Business Digital Signage In Internal Communication Channels Slides Pdf
This slide represents the outdated internal business communication strategy that involves emails and in person meetings. It also includes the impact of these strategies on employees and how these strategies impact their work. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Outdated Internal Business Digital Signage In Internal Communication Channels Slides Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the outdated internal business communication strategy that involves emails and in person meetings. It also includes the impact of these strategies on employees and how these strategies impact their work.
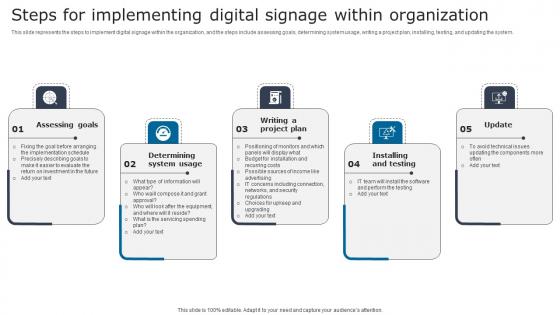
Steps For Implementing Digital Signage In Internal Communication Channels Demonstration Pdf
This slide represents the steps to implement digital signage within the organization, and the steps include assessing goals, determining system usage, writing a project plan, installing, testing, and updating the system. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Steps For Implementing Digital Signage In Internal Communication Channels Demonstration Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the steps to implement digital signage within the organization, and the steps include assessing goals, determining system usage, writing a project plan, installing, testing, and updating the system.
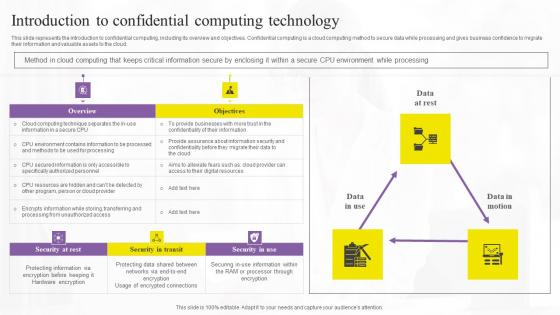
Introduction To Confidential Computing Technology Structure Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Structure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
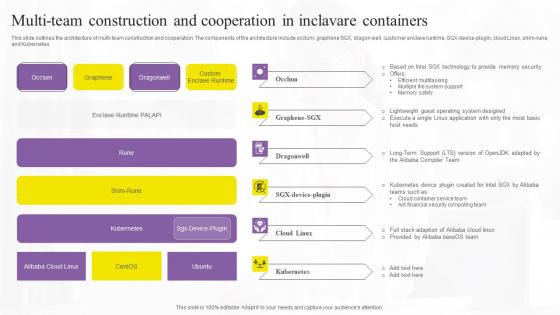
Multi Team Construction And Confidential Computing Technologies Themes Pdf
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Create an editable Multi Team Construction And Confidential Computing Technologies Themes Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Multi Team Construction And Confidential Computing Technologies Themes Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes.
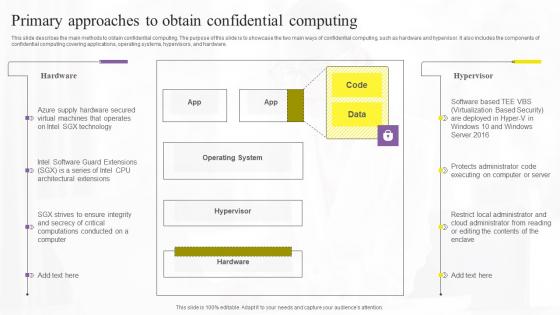
Primary Approaches To Obtain Confidential Computing Technologies Guidelines Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Primary Approaches To Obtain Confidential Computing Technologies Guidelines Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
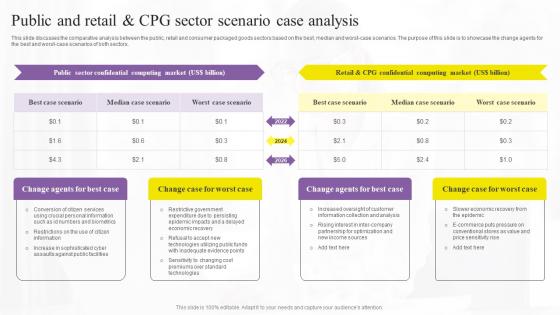
Public And Retail And Cpg Sector Confidential Computing Technologies Graphics Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Want to ace your presentation in front of a live audience Our Public And Retail And Cpg Sector Confidential Computing Technologies Graphics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
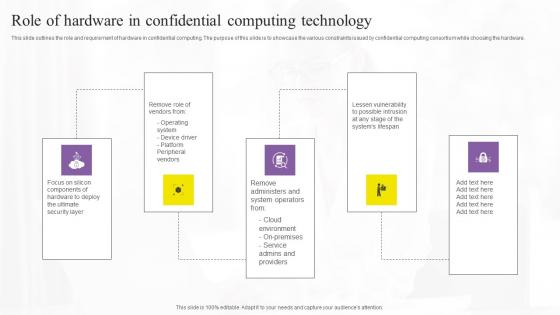
Role Of Hardware In Confidential Computing Technology Portrait Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. There are so many reasons you need a Role Of Hardware In Confidential Computing Technology Portrait Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.
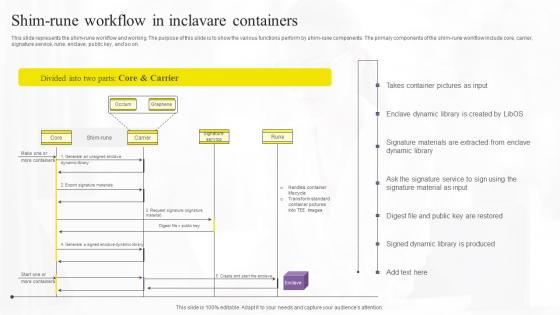
Shim Rune Workflow In Inclavare Confidential Computing Technologies Sample Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Shim Rune Workflow In Inclavare Confidential Computing Technologies Sample Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Shim Rune Workflow In Inclavare Confidential Computing Technologies Sample Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.
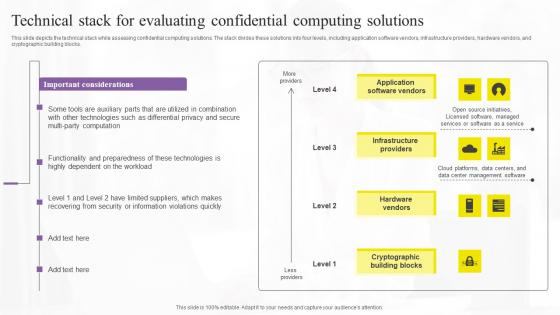
Technical Stack For Evaluating Confidential Computing Technologies Structure Pdf
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Technical Stack For Evaluating Confidential Computing Technologies Structure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
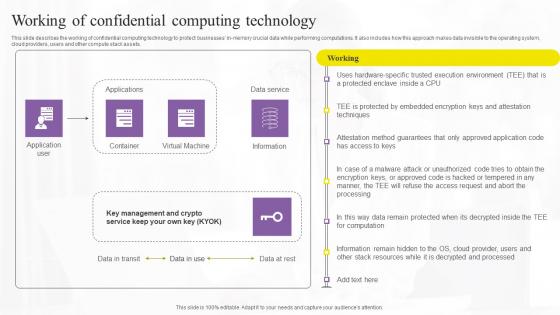
Working Of Confidential Computing Technology Demonstration Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Boost your pitch with our creative Working Of Confidential Computing Technology Demonstration Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.

ACK TEE Introduction And Version 10 Confidential Computing Technologies Diagrams Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Boost your pitch with our creative ACK TEE Introduction And Version 10 Confidential Computing Technologies Diagrams Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
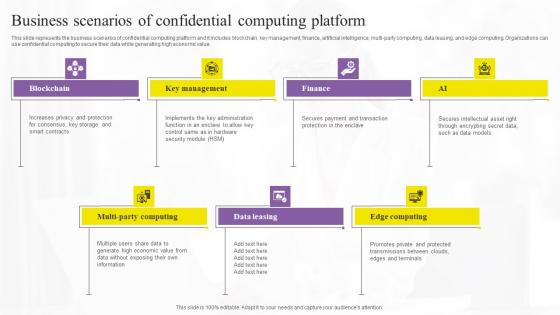
Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
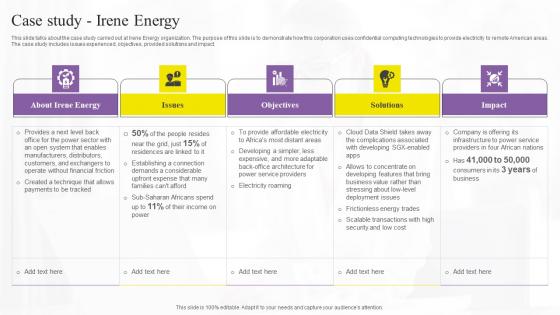
Case Study Irene Energy Confidential Computing Technologies Download Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Irene Energy Confidential Computing Technologies Download Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Irene Energy Confidential Computing Technologies Download Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
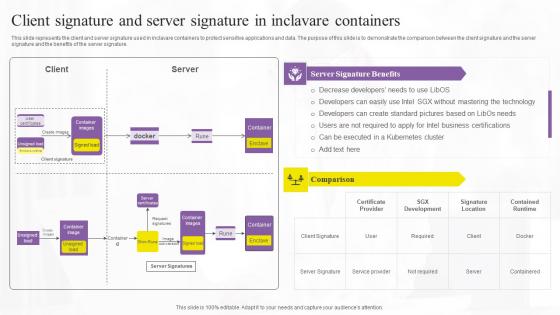
Client Signature And Server Signature In Confidential Computing Technologies Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Confidential Computing Technologies Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.
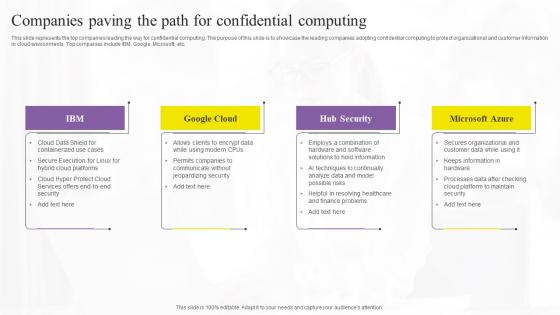
Companies Paving The Path For Confidential Computing Technologies Demonstration Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Present like a pro with Companies Paving The Path For Confidential Computing Technologies Demonstration Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
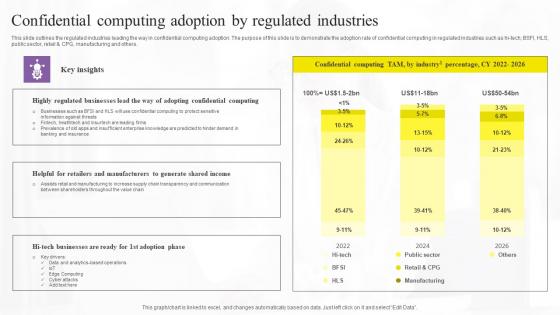
Confidential Computing Adoption By Confidential Computing Technologies Elements Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Adoption By Confidential Computing Technologies Elements Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Adoption By Confidential Computing Technologies Elements Pdf today and make your presentation stand out from the rest This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
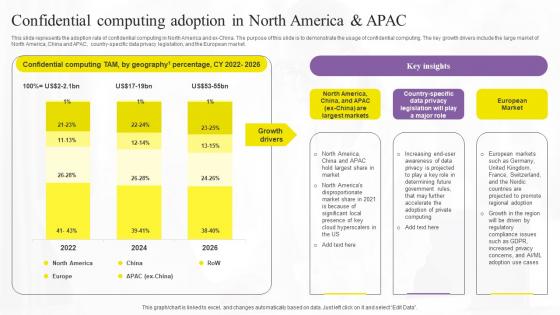
Confidential Computing Adoption In Confidential Computing Technologies Download Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In Confidential Computing Technologies Download Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In Confidential Computing Technologies Download Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
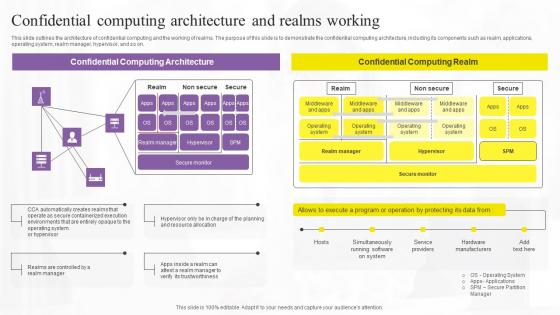
Confidential Computing Architecture And Confidential Computing Technologies Demonstration Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Confidential Computing Architecture And Confidential Computing Technologies Demonstration Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.
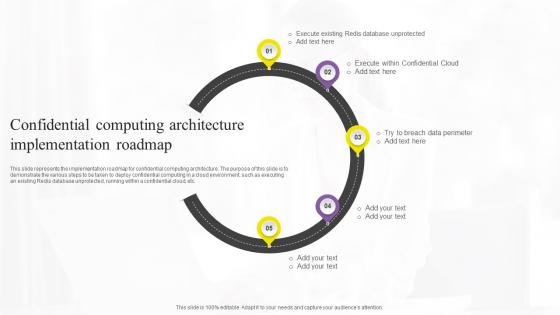
Confidential Computing Architecture Confidential Computing Technologies Diagrams Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Confidential Computing Architecture Confidential Computing Technologies Diagrams Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.

Confidential Computing For Total Confidential Computing Technologies Background Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing For Total Confidential Computing Technologies Background Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing For Total Confidential Computing Technologies Background Pdf This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.

Confidential Computing Technologies Confidential Computing Consortium Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Confidential Computing Technologies Confidential Computing Consortium Demonstration Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
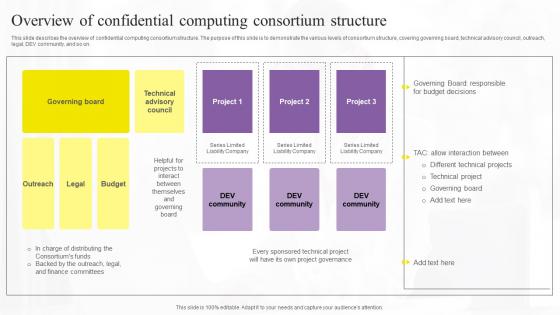
Confidential Computing Technologies Overview Of Confidential Computing Portrait Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. The Confidential Computing Technologies Overview Of Confidential Computing Portrait Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.
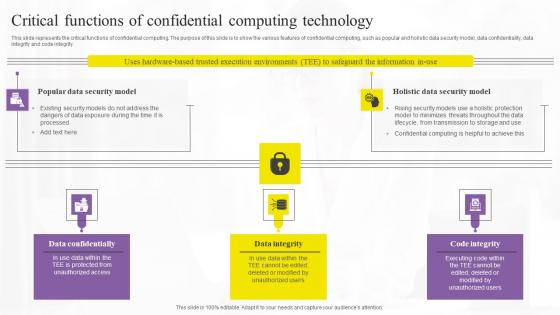
Critical Functions Of Confidential Computing Technology Demonstration Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Presenting this PowerPoint presentation, titled Critical Functions Of Confidential Computing Technology Demonstration Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Critical Functions Of Confidential Computing Technology Demonstration Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Critical Functions Of Confidential Computing Technology Demonstration Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
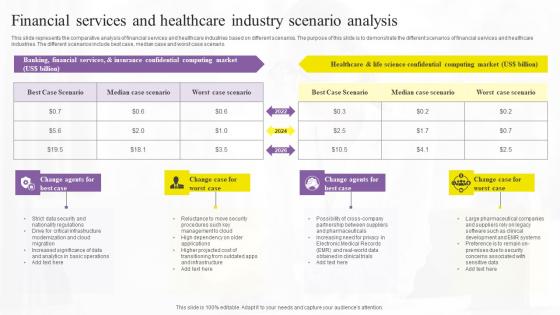
Financial Services And Healthcare Confidential Computing Technologies Demonstration Pdf
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Financial Services And Healthcare Confidential Computing Technologies Demonstration Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Financial Services And Healthcare Confidential Computing Technologies Demonstration Pdf. This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario.
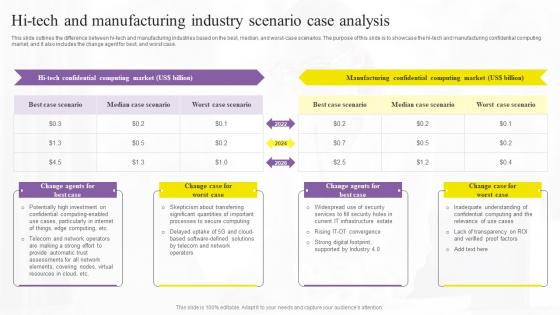
Hi Tech And Manufacturing Confidential Computing Technologies Pictures Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Do you know about Slidesgeeks HI Tech And Manufacturing Confidential Computing Technologies Pictures Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.
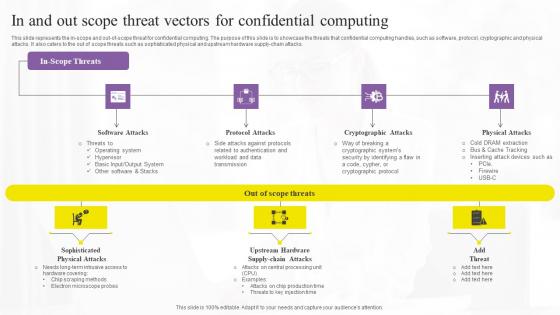
In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Are you searching for a In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf from Slidegeeks today. This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.
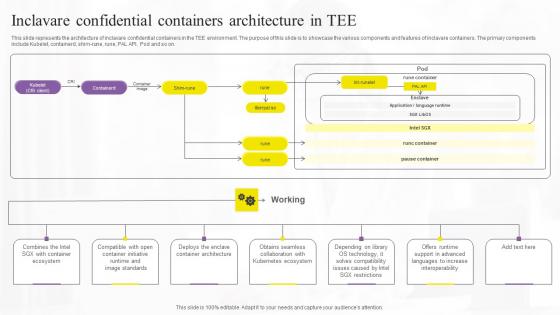
Inclavare Confidential Containers Confidential Computing Technologies Infographics Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Retrieve professionally designed Inclavare Confidential Containers Confidential Computing Technologies Infographics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.

Key Features Of Confidential Computing Technologies Introduction Pdf
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Presenting this PowerPoint presentation, titled Key Features Of Confidential Computing Technologies Introduction Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Key Features Of Confidential Computing Technologies Introduction Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Key Features Of Confidential Computing Technologies Introduction Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes.
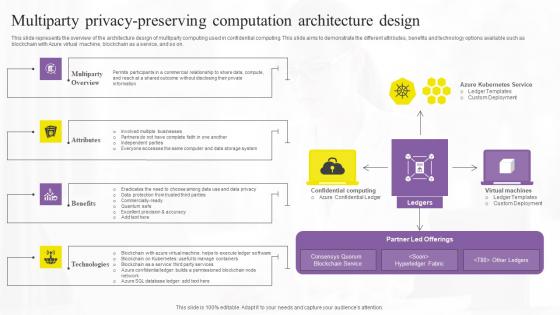
Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on.
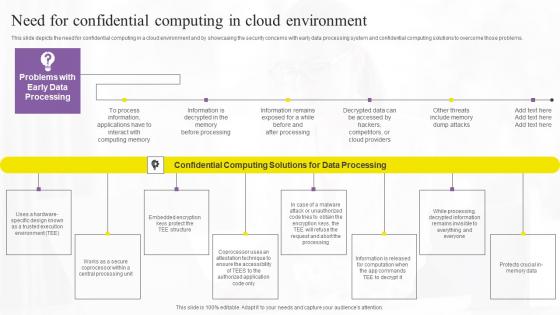
Need For Confidential Computing In Confidential Computing Technologies Structure Pdf
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. This Need For Confidential Computing In Confidential Computing Technologies Structure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems.

Occlum System Architecture And Confidential Computing Technologies Professional Pdf
This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Take your projects to the next level with our ultimate collection of Occlum System Architecture And Confidential Computing Technologies Professional Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on.
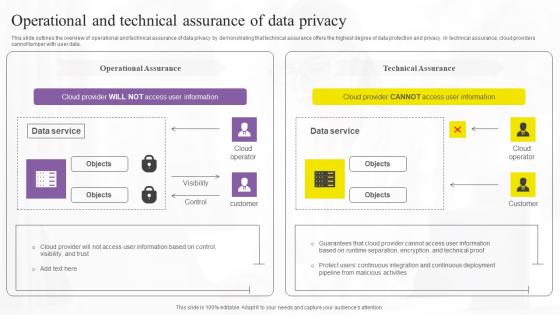
Operational And Technical Assurance Confidential Computing Technologies Inspiration Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Do you know about Slidesgeeks Operational And Technical Assurance Confidential Computing Technologies Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.
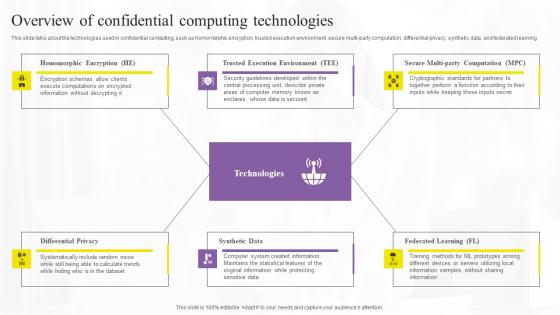
Overview Of Confidential Computing Technologies Elements Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. The Overview Of Confidential Computing Technologies Elements Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
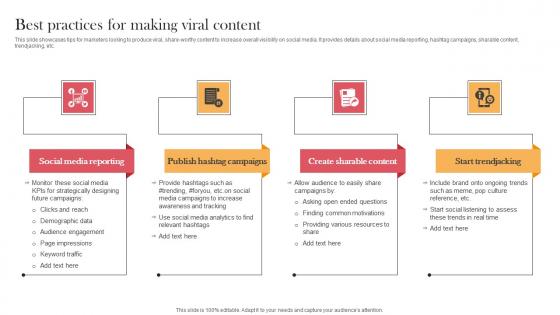
Best Practices For Making Viral Content Designing Approaches Topics Pdf
This slide showcases tips for marketers looking to produce viral, share-worthy content to increase overall visibility on social media. It provides details about social media reporting, hashtag campaigns, sharable content, trendjacking, etc. There are so many reasons you need a Best Practices For Making Viral Content Designing Approaches Topics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases tips for marketers looking to produce viral, share-worthy content to increase overall visibility on social media. It provides details about social media reporting, hashtag campaigns, sharable content, trendjacking, etc.
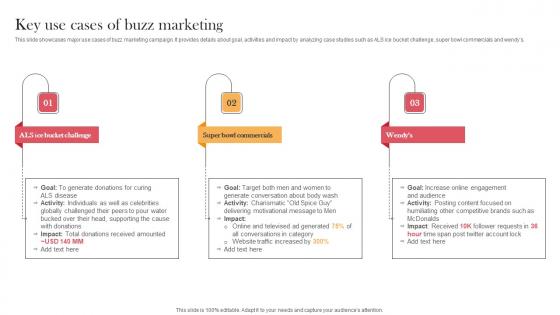
Key Use Cases Of Buzz Marketing Designing Approaches Summary Pdf
This slide showcases major use cases of buzz marketing campaign. It provides details about goal, activities and impact by analyzing case studies such as ALS ice bucket challenge, super bowl commercials and wendys. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Use Cases Of Buzz Marketing Designing Approaches Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases major use cases of buzz marketing campaign. It provides details about goal, activities and impact by analyzing case studies such as ALS ice bucket challenge, super bowl commercials and wendys.
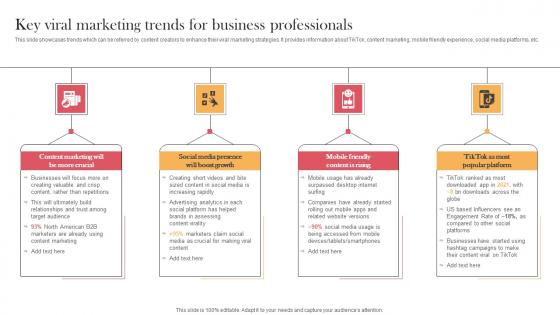
Key Viral Marketing Trends For Business Professionals Designing Approaches Brochure Pdf
This slide showcases trends which can be referred by content creators to enhance their viral marketing strategies. It provides information about TikTok, content marketing, mobile friendly experience, social media platforms, etc. This modern and well-arranged Key Viral Marketing Trends For Business Professionals Designing Approaches Brochure Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcases trends which can be referred by content creators to enhance their viral marketing strategies. It provides information about TikTok, content marketing, mobile friendly experience, social media platforms, etc.

Online Tools Used For Guerilla Marketing Designing Approaches Topics Pdf
This slide showcases online techniques which can be used to perfectly implement guerilla marketing campaigns. It provides information about E-media, Info media, internet bulletin boards, blogs, e-books, AdWords, banner exchange, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Online Tools Used For Guerilla Marketing Designing Approaches Topics Pdf from Slidegeeks and deliver a wonderful presentation. This slide showcases online techniques which can be used to perfectly implement guerilla marketing campaigns. It provides information about E-media, Info media, internet bulletin boards, blogs, e-books, AdWords, banner exchange, etc.

Preparing Content Schedule For Social Media Designing Approaches Download Pdf
The following slide showcases content schedule for social media platforms. It provides details about Twitter, Facebook, Tumblr, Instagram, Pinterest, engaging content, high-activity hours, algorithm, social media platforms, etc. The Preparing Content Schedule For Social Media Designing Approaches Download Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The following slide showcases content schedule for social media platforms. It provides details about Twitter, Facebook, Tumblr, Instagram, Pinterest, engaging content, high-activity hours, algorithm, social media platforms, etc.
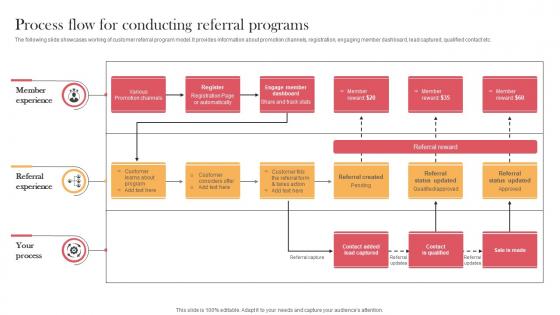
Process Flow For Conducting Referral Programs Designing Approaches Pictures Pdf
The following slide showcases working of customer referral program model. It provides information about promotion channels, registration, engaging member dashboard, lead captured, qualified contact etc. Are you searching for a Process Flow For Conducting Referral Programs Designing Approaches Pictures Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Process Flow For Conducting Referral Programs Designing Approaches Pictures Pdf from Slidegeeks today. The following slide showcases working of customer referral program model. It provides information about promotion channels, registration, engaging member dashboard, lead captured, qualified contact etc.

Steps To Launch Offline Guerilla Marketing Campaign Designing Approaches Guidelines Pdf
This slide showcases stages which can help offline marketers in launching guerilla campaigns. It provides details about set target audience, goals, market environment, plan, execution, measure results, etc. Presenting this PowerPoint presentation, titled Steps To Launch Offline Guerilla Marketing Campaign Designing Approaches Guidelines Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Steps To Launch Offline Guerilla Marketing Campaign Designing Approaches Guidelines Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Steps To Launch Offline Guerilla Marketing Campaign Designing Approaches Guidelines Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide showcases stages which can help offline marketers in launching guerilla campaigns. It provides details about set target audience, goals, market environment, plan, execution, measure results, etc.
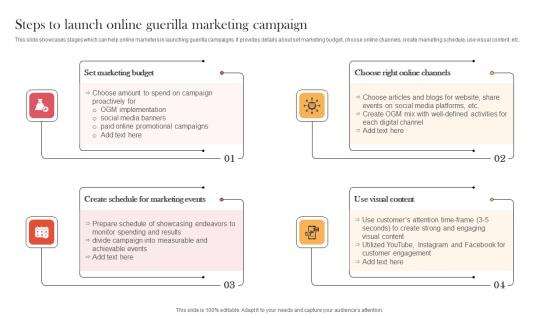
Steps To Launch Online Guerilla Marketing Campaign Designing Approaches Graphics Pdf
This slide showcases stages which can help online marketers in launching guerilla campaigns. It provides details about set marketing budget, choose online channels, create marketing schedule, use visual content, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Steps To Launch Online Guerilla Marketing Campaign Designing Approaches Graphics Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Steps To Launch Online Guerilla Marketing Campaign Designing Approaches Graphics Pdf. This slide showcases stages which can help online marketers in launching guerilla campaigns. It provides details about set marketing budget, choose online channels, create marketing schedule, use visual content, etc.
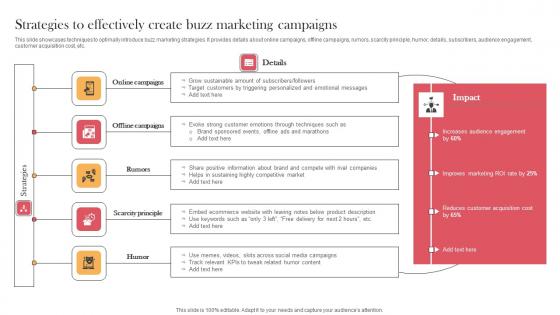
Strategies To Effectively Create Buzz Marketing Campaigns Designing Approaches Summary Pdf
This slide showcases techniques to optimally introduce buzz marketing strategies. It provides details about online campaigns, offline campaigns, rumors, scarcity principle, humor, details, subscribers, audience engagement, customer acquisition cost, etc. This Strategies To Effectively Create Buzz Marketing Campaigns Designing Approaches Summary Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases techniques to optimally introduce buzz marketing strategies. It provides details about online campaigns, offline campaigns, rumors, scarcity principle, humor, details, subscribers, audience engagement, customer acquisition cost, etc.

Using Different Types Of Guerilla Marketing Methods Designing Approaches Mockup Pdf
This slide showcases variations which can help online marketers in launching guerilla campaigns. It provides details about ambient, ambush, buzz, grassroots marketing along with their campaign activity and impact analysis. Do you know about Slidesgeeks Using Different Types Of Guerilla Marketing Methods Designing Approaches Mockup Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide showcases variations which can help online marketers in launching guerilla campaigns. It provides details about ambient, ambush, buzz, grassroots marketing along with their campaign activity and impact analysis.
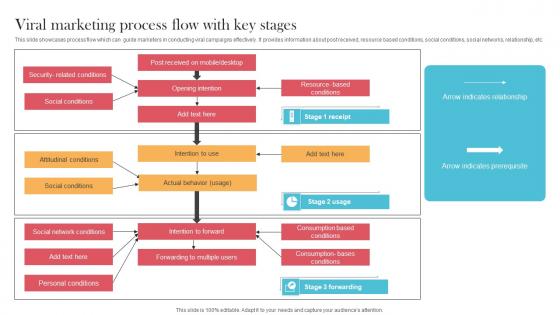
Viral Marketing Process Flow With Key Stages Designing Approaches Slides Pdf
This slide showcases process flow which can guide marketers in conducting viral campaigns effectively. It provides information about post received, resource based conditions, social conditions, social networks, relationship, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Viral Marketing Process Flow With Key Stages Designing Approaches Slides Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases process flow which can guide marketers in conducting viral campaigns effectively. It provides information about post received, resource based conditions, social conditions, social networks, relationship, etc.

Viral Marketing Strategies Buzz Online Guerilla And Wom Designing Approaches Topics Pdf
This slide showcases overview major viral marketing strategies namely buzz, online, guerilla and word of mouth. It provides details about campaign, product service marketing, social media platforms, videos, search engine, etc. Want to ace your presentation in front of a live audience Our Viral Marketing Strategies Buzz Online Guerilla And Wom Designing Approaches Topics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases overview major viral marketing strategies namely buzz, online, guerilla and word of mouth. It provides details about campaign, product service marketing, social media platforms, videos, search engine, etc.

Viral Marketing Strategies To Share Social Media Campaigns Designing Approaches Microsoft Pdf
This slide showcases strategies which marketers can refer who want to reach bigger audience through viral marketing. It provides details about visuals, creative campaigns, emotional appeals, timely sharing, target audience, etc. There are so many reasons you need a Viral Marketing Strategies To Share Social Media Campaigns Designing Approaches Microsoft Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases strategies which marketers can refer who want to reach bigger audience through viral marketing. It provides details about visuals, creative campaigns, emotional appeals, timely sharing, target audience, etc.
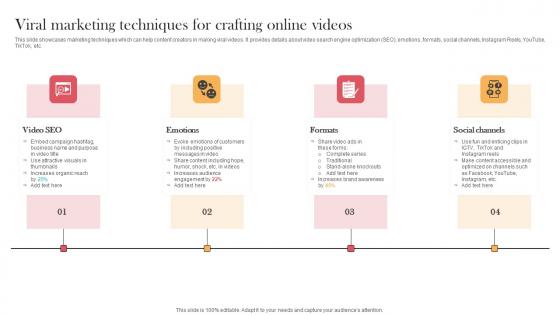
Viral Marketing Techniques For Crafting Online Videos Designing Approaches Professional Pdf
This slide showcases marketing techniques which can help content creators in making viral videos. It provides details about video search engine optimization SEO, emotions, formats, social channels, Instagram Reels, YouTube, TikTok, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Viral Marketing Techniques For Crafting Online Videos Designing Approaches Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Viral Marketing Techniques For Crafting Online Videos Designing Approaches Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases marketing techniques which can help content creators in making viral videos. It provides details about video search engine optimization SEO, emotions, formats, social channels, Instagram Reels, YouTube, TikTok, etc.
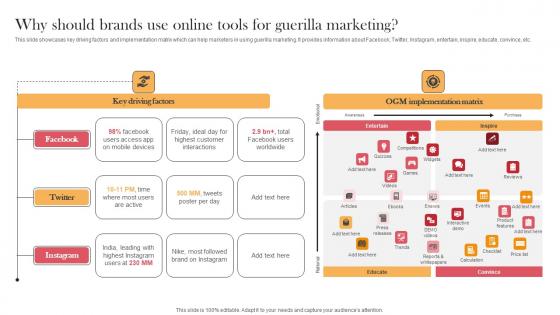
Why Should Brands Use Online Tools For Guerilla Marketing Designing Approaches Diagrams Pdf
This slide showcases key driving factors and implementation matrix which can help marketers in using guerilla marketing. It provides information about Facebook, Twitter, Instagram, entertain, inspire, educate, convince, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Why Should Brands Use Online Tools For Guerilla Marketing Designing Approaches Diagrams Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases key driving factors and implementation matrix which can help marketers in using guerilla marketing. It provides information about Facebook, Twitter, Instagram, entertain, inspire, educate, convince, etc.
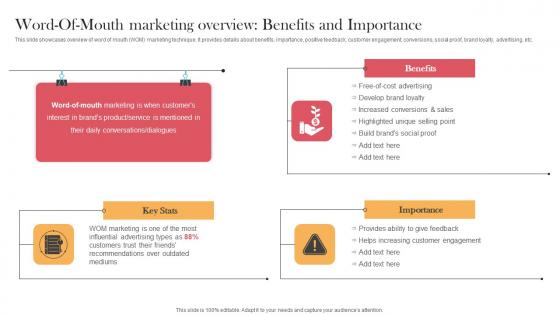
Word Of Mouth Marketing Overview Benefits And Importance Designing Approaches Structure Pdf
This slide showcases overview of word of mouth WOM marketing technique. It provides details about benefits, importance, positive feedback, customer engagement, conversions, social proof, brand loyalty, advertising, etc. Present like a pro with Word Of Mouth Marketing Overview Benefits And Importance Designing Approaches Structure Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases overview of word of mouth WOM marketing technique. It provides details about benefits, importance, positive feedback, customer engagement, conversions, social proof, brand loyalty, advertising, etc.
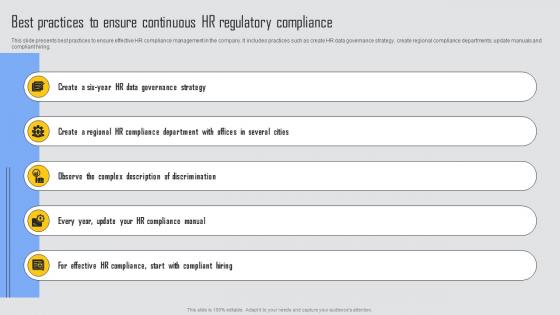
Best Practices To Ensure Managing Risks And Establishing Trust Through Efficient Introduction Pdf
This slide presents best practices to ensure effective HR compliance management in the company. It includes practices such as create HR data governance strategy, create regional compliance departments, update manuals and compliant hiring. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Best Practices To Ensure Managing Risks And Establishing Trust Through Efficient Introduction Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Best Practices To Ensure Managing Risks And Establishing Trust Through Efficient Introduction Pdf This slide presents best practices to ensure effective HR compliance management in the company. It includes practices such as create HR data governance strategy, create regional compliance departments, update manuals and compliant hiring.


 Continue with Email
Continue with Email

 Home
Home


































