Collateral Management

Cloud Architecture At Scale How To Execute A Cloud Infrastructure Evaluation Establish Priorities In Cloud Architecture Themes PDF
This slide covers the criterias to set priorities in cloud infrastructure review for newer teams implementing full architectures for the first time. Deliver an awe inspiring pitch with this creative cloud architecture at scale how to execute a cloud infrastructure evaluation establish priorities in cloud architecture themes pdf bundle. Topics like network architecture, application presence, management, security, cost management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
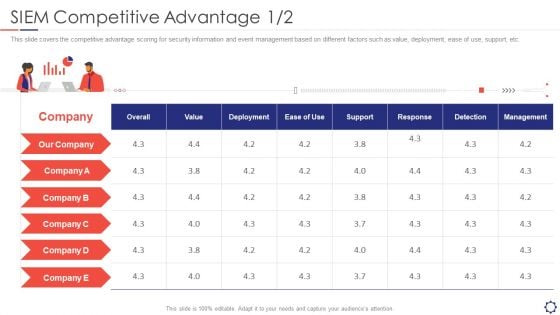
SIEM Competitive Advantage Detection Ppt Layouts Outline PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver and pitch your topic in the best possible manner with this siem competitive advantage detection ppt layouts outline pdf. Use them to share invaluable insights on value, deployment, response, detection, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
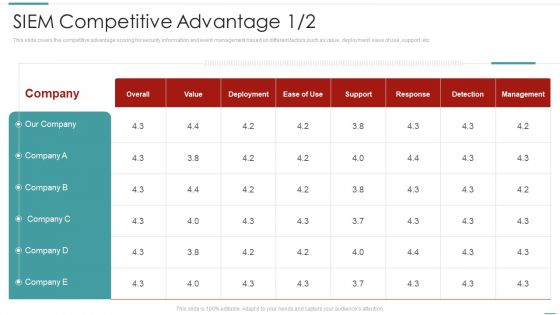
Risk Recognition Automation Siem Competitive Advantage Ppt Layouts Themes PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver and pitch your topic in the best possible manner with this risk recognition automation siem competitive advantage ppt layouts themes pdf. Use them to share invaluable insights on value, support, response, detection, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
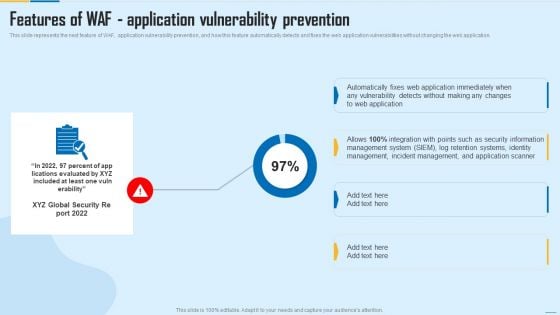
Features Of WAF Application Vulnerability Prevention WAF Platform Designs PDF
This slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Deliver and pitch your topic in the best possible manner with this Features Of WAF Application Vulnerability Prevention WAF Platform Designs PDF. Use them to share invaluable insights on Management System, Incident Management, Security Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Pharmaceutical And Clinical Research Summary Case Study Information PDF
The slide showcases the challenge faced by healthcare business to develop digital capabilities. The company leveraged technology partner to develop and deploy customized cloud-based patient management platform for easy data access with added security. Deliver an awe inspiring pitch with this creative Pharmaceutical And Clinical Research Summary Case Study Information PDF bundle. Topics like Patient Management, Payment, Integrated Patient can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Iot Logistics Comprehensive Training Program Ideas PDF
This slide showcases internet of things IoT comprehensive training program. It provides details such as modules, trainer, time, outcome, worker performance, productivity, IoT architecture, big data, analytics, warehouse IoT, testing, support, etc. Deliver and pitch your topic in the best possible manner with this Iot Logistics Comprehensive Training Program Ideas PDF. Use them to share invaluable insights on Transportation Management, Security, Data Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
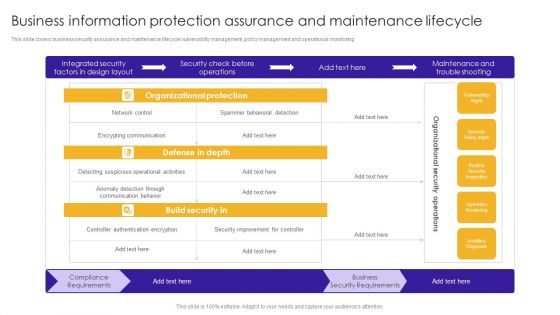
Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF
This slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring.Showcasing this set of slides titled Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF. The topics addressed in these templates are Encrypting Communication, Detecting Suspicious, Authentication Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
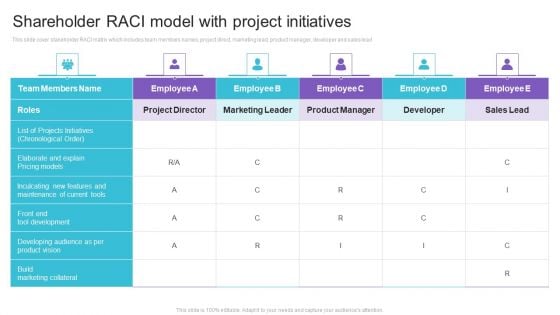
Shareholder RACI Model With Project Initiatives Guidelines PDF
This slide cover stakeholder RACI matrix which includes team members names, project direct, marketing lead, product manager, developer and sales lead. Pitch your topic with ease and precision using this Shareholder RACI Model With Project Initiatives Guidelines PDF. This layout presents information on Front End Tool Development, Build Marketing Collateral. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
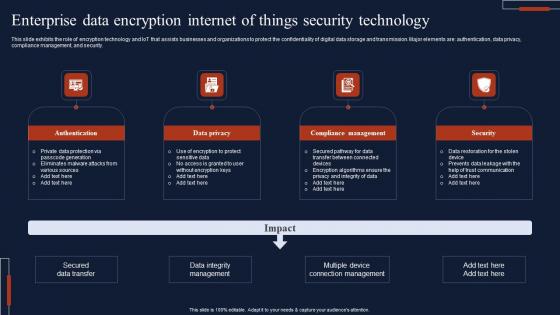
Enterprise Data Encryption Internet Of Things Security Technology Summary Pdf
This slide exhibits the role of encryption technology and IoT that assists businesses and organizations to protect the confidentiality of digital data storage and transmission. Major elements are authentication, data privacy, compliance management, and security. Showcasing this set of slides titled Enterprise Data Encryption Internet Of Things Security Technology Summary Pdf The topics addressed in these templates are Authentication, Data Privacy, Compliance Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide exhibits the role of encryption technology and IoT that assists businesses and organizations to protect the confidentiality of digital data storage and transmission. Major elements are authentication, data privacy, compliance management, and security.

B2B Direct Field Marketing Strategic Plan Formats PDF
This slide presents B2B field marketing plan that helps brand to acquire new customers and retain existing ones. It includes knowing audience, using marketing collaterals, launching campaigns, evaluating competitors and measuring return on investment. Presenting B2B Direct Field Marketing Strategic Plan Formats PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Marketing Collateral, Launch Campaigns, Evaluate Competition. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
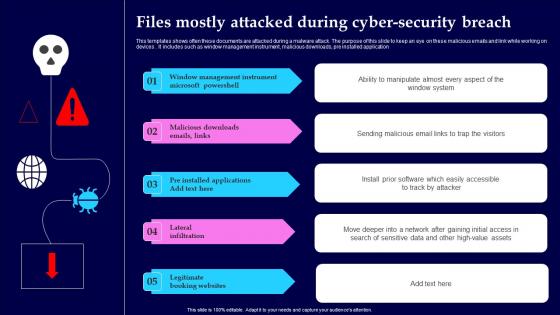
Files Mostly Attacked During Cyber Security Breach Structure Pdf
This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application Showcasing this set of slides titled Files Mostly Attacked During Cyber Security Breach Structure Pdf The topics addressed in these templates are Window Management, Instrument Microsoft, Lateral Infiltration All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application

Brand Kickoff Promotional Plan Typography Guidelines For Brands Content Graphics Pdf
This template covers topography usage guidelines for brand content. It also depicts a particular font family, size is used to create headlines on embedded or printed collateral. Present like a pro with Brand Kickoff Promotional Plan Typography Guidelines For Brands Content Graphics Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This template covers topography usage guidelines for brand content. It also depicts a particular font family, size is used to create headlines on embedded or printed collateral.
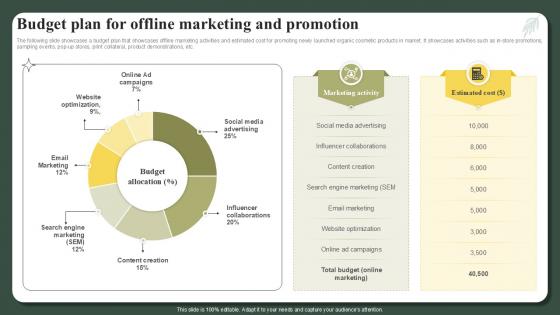
Budget Plan For Offline Marketing And Promotion Successful Launch Ppt Sample
The following slide showcases a budget plan that showcases offline marketing activities and estimated cost for promoting newly launched organic cosmetic products in market. It showcases activities such as in-store promotions, sampling events, pop-up stores, print collateral, product demonstrations, etc. Want to ace your presentation in front of a live audience Our Budget Plan For Offline Marketing And Promotion Successful Launch Ppt Sample can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The following slide showcases a budget plan that showcases offline marketing activities and estimated cost for promoting newly launched organic cosmetic products in market. It showcases activities such as in-store promotions, sampling events, pop-up stores, print collateral, product demonstrations, etc.

Quarterly Roadmap To Successfully Develop Cloud Migration Strategy Background PDF
This slide shows quarterly timeline to develop cloud migration strategy. It includes three stages which are planning, infrastructure and implementation. Showcasing this set of slides titled Quarterly Roadmap To Successfully Develop Cloud Migration Strategy Background PDF. The topics addressed in these templates are Readiness Questionnaire, Select Cloud Provider, Internal Collateral. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Asset Based Lending For Raising Funds Pictures PDF
This slide showcases plan that can help organization to obtain loan from market in exchange of collateral. Its key components are asset, value of asset, credit, loan value and gain or loss. Deliver an awe inspiring pitch with this creative Asset Based Lending For Raising Funds Pictures PDF bundle. Topics like Value, Gain Or Loss, Creditor can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
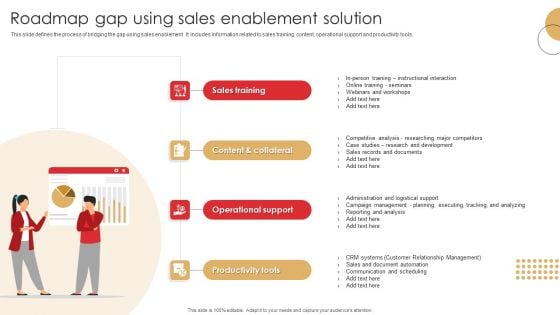
Roadmap Gap Using Sales Enablement Solution Graphics PDF
This slide defines the process of bridging the gap using sales enablement . It includes information related to sales training, content, operational support and productivity tools.Presenting Roadmap Gap Using Sales Enablement Solution Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Operational Support, Productivity Tools, Content Collateral. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Security Elements Of Data Security Operational Security Ppt Icon Background Designs PDF
This slide defines the operational security element of data security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a information security elements of data security operational security ppt icon background designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control, restrict device access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
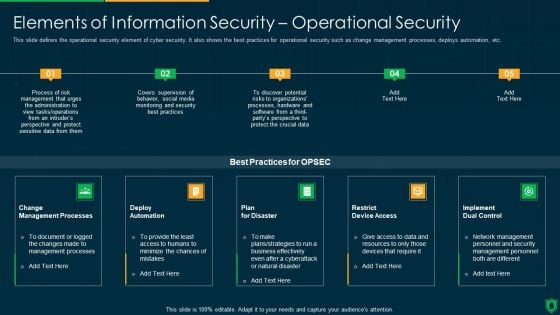
Info Security Elements Of Information Security Operational Security Ppt PowerPoint Presentation File Backgrounds PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a info security elements of information security operational security ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
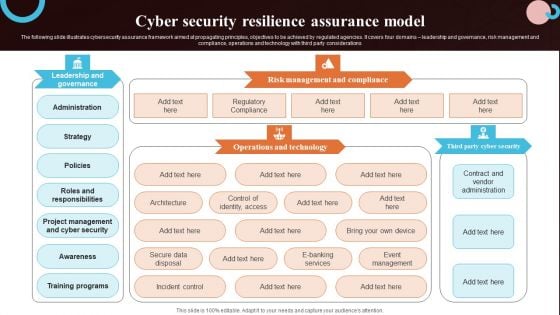
Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
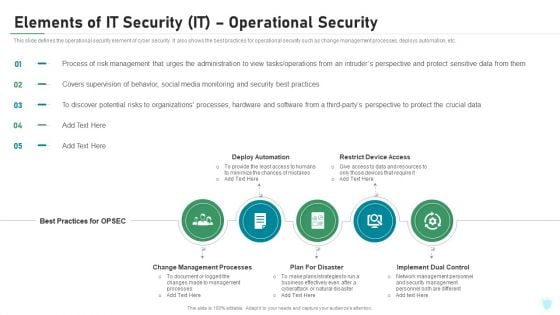
Elements Of IT Security IT Operational Security Ppt Outline Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting elements of it security it operational security ppt outline ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like change management processes, deploy automation, restrict device access, plan for disaster, implement dual control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Elements Of Information Technology Security Operational Security Ppt Icon Guidelines PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a elements of information technology security operational security ppt icon guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process, sensitive, management, administration, operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Current Information Security Issues Faced By Organization Clipart PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating,This is a Information Security Risk Evaluation Current Information Security Issues Faced By Organization Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Untrained Employees, Complex Risk, Management Policy . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Elements Of Electronic Information Security Operational Security Ppt Portfolio Rules PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting cybersecurity elements of electronic information security operational security ppt portfolio rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, risk, plans, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
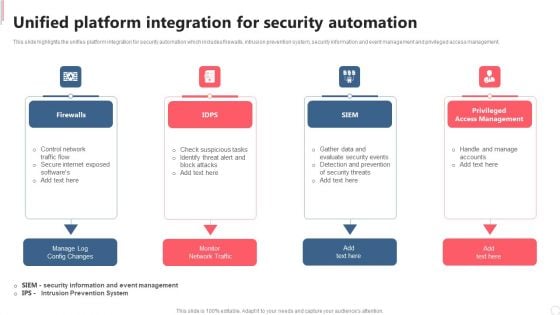
Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present like a pro with Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
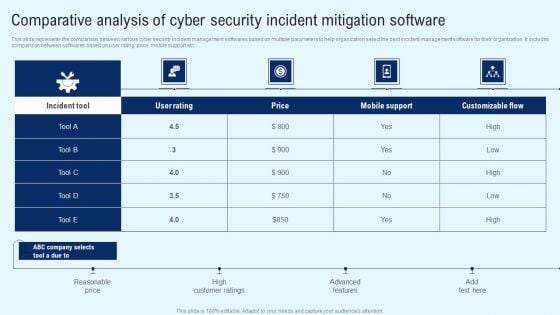
Implementing Cyber Security Incident Comparative Analysis Of Cyber Security Background PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cyber Security Incident Comparative Analysis Of Cyber Security Background PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
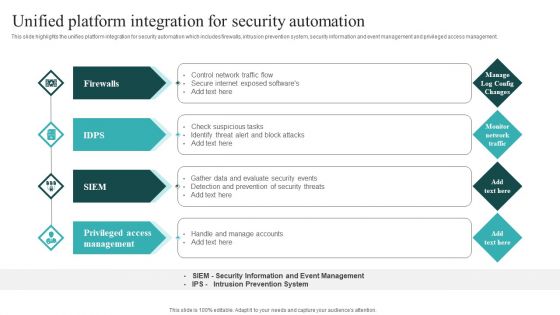
IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
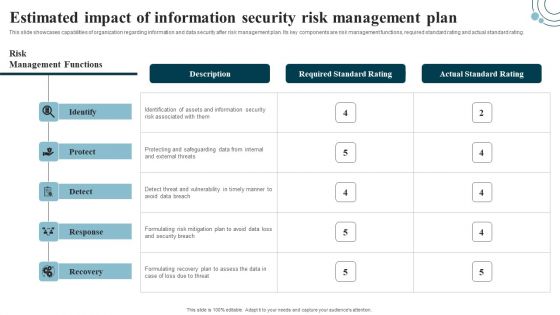
Developing IT Security Strategy Estimated Impact Of Information Security Risk Clipart PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating. Find a pre-designed and impeccable Developing IT Security Strategy Estimated Impact Of Information Security Risk Clipart PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
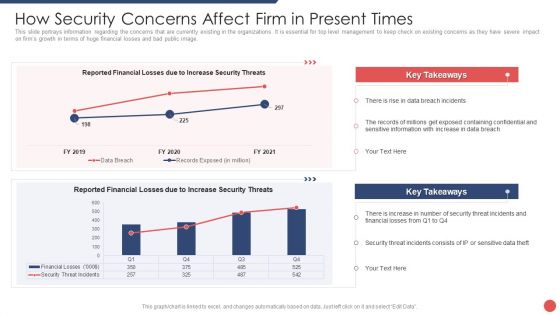
Security Functioning Centre How Security Concerns Affect Firm In Present Times Ideas PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver and pitch your topic in the best possible manner with this security functioning centre how security concerns affect firm in present times ideas pdf. Use them to share invaluable insights on financial, security threat, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
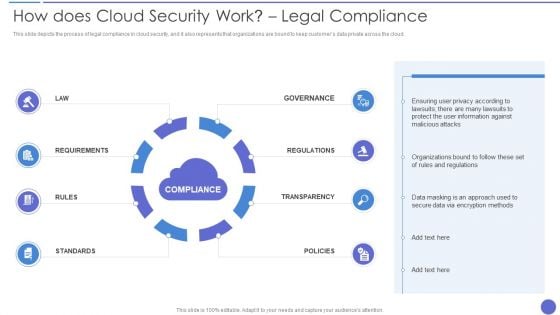
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
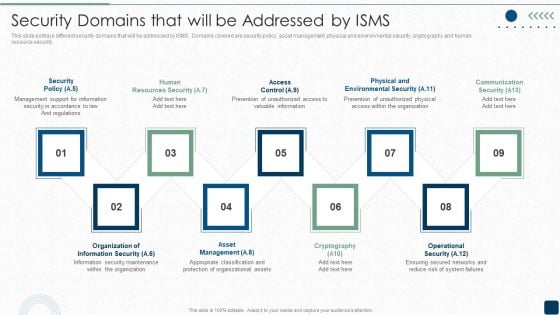
Security Domains That Will Be Addressed By ISMS Diagrams PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.This is a Security Domains That Will Be Addressed By ISMS Diagrams PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Support, Resources Security, Prevention Of Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
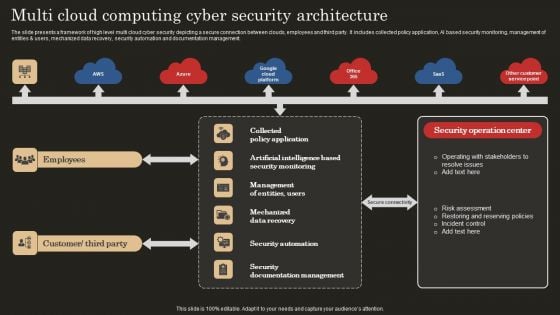
Multi Cloud Computing Cyber Security Architecture Microsoft PDF
The slide presents a framework of high level multi cloud cyber security depicting a secure connection between clouds, employees and third party. It includes collected policy application, AI based security monitoring, management of entities and users, mechanized data recovery, security automation and documentation management. Showcasing this set of slides titled Multi Cloud Computing Cyber Security Architecture Microsoft PDF. The topics addressed in these templates are Mechanized Data Recovery, Security Automation, Employees. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
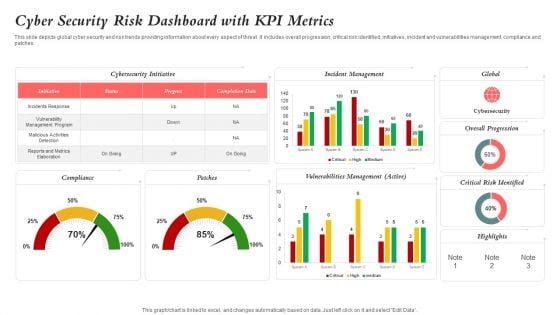
Cyber Security Risk Dashboard With KPI Metrics Elements PDF
This slide depicts global cyber security and risk trends providing information about every aspect of threat. It includes overall progression, critical risk identified, initiatives, incident and vulnerabilities management, compliance and patches. Showcasing this set of slides titled Cyber Security Risk Dashboard With KPI Metrics Elements PDF. The topics addressed in these templates are Vulnerability Management Program, Reports And Metrics Elaboration, Critical Risk Identified. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
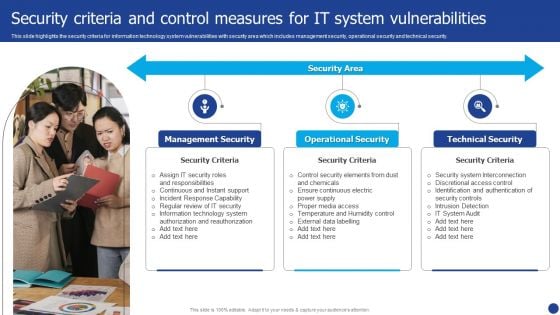
Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Executing Advance Data Analytics At Workspace Enabling Data Security Risk Demonstration PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace enabling data security risk demonstration pdf. Use them to share invaluable insights on enabling data security risk management action plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Executing Advance Data Analytics At Workspace Enabling Data Security Risk Icons PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace enabling data security risk icons pdf. Use them to share invaluable insights on enabling data security risk management action plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
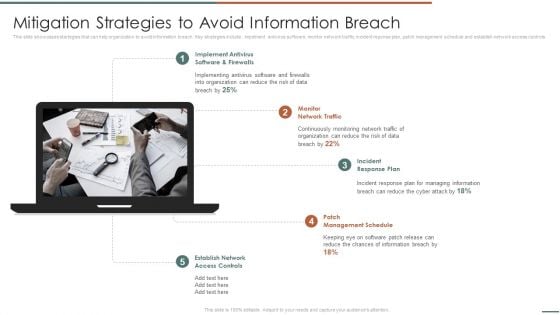
Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
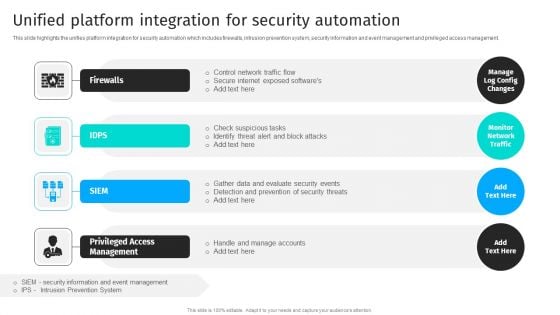
Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management.The Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
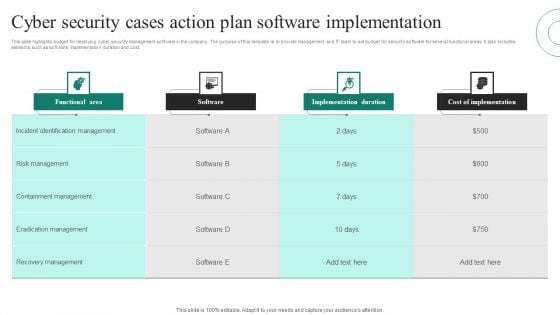
Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF
This slide highlights budget for deploying cyber security management software in the company. The purpose of this template is to provide management and IT team to set budget for security software for several functional areas. It also includes elements such as software, implementation duration and cost. Pitch your topic with ease and precision using this Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF. This layout presents information on Functional Area, Software, Implementation Duration, Cost Implementation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
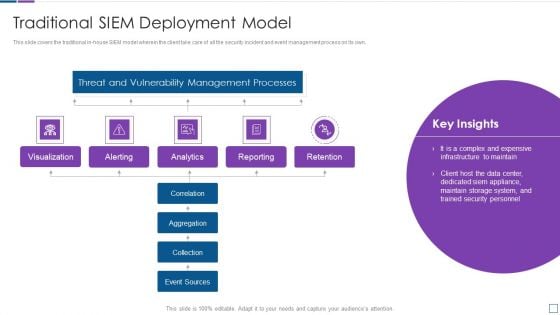
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
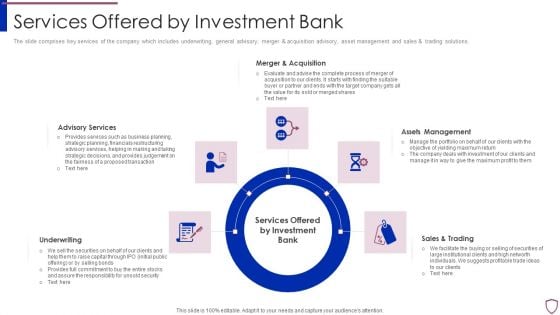
Financing Catalogue For Security Underwriting Agreement Services Offered By Investment Pictures PDF
The slide comprises key services of the company which includes underwriting, general advisory, merger and acquisition advisory, asset management and sales and trading solutions. This is a financing catalogue for security underwriting agreement services offered by investment pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like underwriting, advisory services, merger and acquisition, assets management, sales and trading. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Services Offered By Investment Bank Designs PDF
The slide comprises key services of the company which includes underwriting, general advisory, merger and acquisition advisory, asset management and sales trading solutions. Presenting Investment Banking Security Underwriting Pitchbook Services Offered By Investment Bank Designs PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Advisory Services, Merger And Acquisition, Assets Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
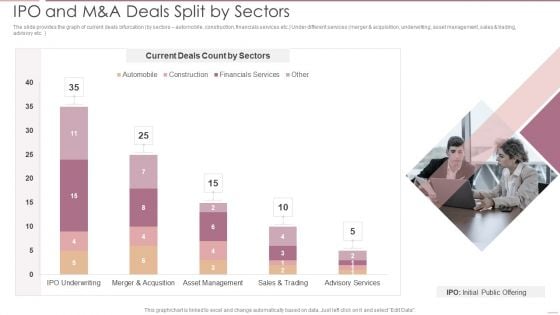
Investment Banking Security Underwriting Pitchbook IPO And M And A Deals Split By Sectors Brochure PDF
The slide provides the graph of current deals bifurcation by sectors automobile, construction, financials services etc.Under different services merger and acquisition, underwriting, asset management, sales trading, advisory etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook IPO And M And A Deals Split By Sectors Brochure PDF Use them to share invaluable insights on Current Deals, Merger And Acquisition, Asset Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
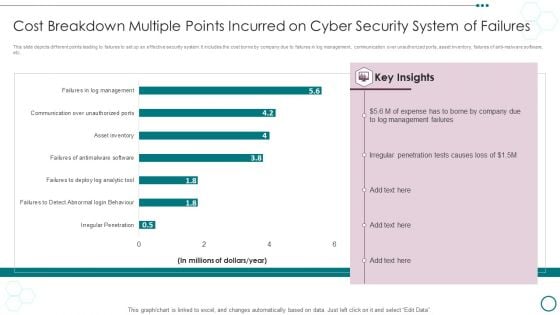
Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF
This slide depicts different points leading to failures to set up an effective security system. It includes the cost borne by company due to failures in log management, communication over unauthorized ports, asset inventory, failures of anti-malware software, etc.Showcasing this set of slides titled Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF. The topics addressed in these templates are Management Failures, Irregular Penetration, Expense Borne. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
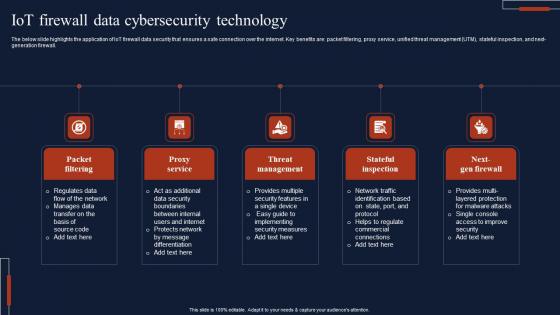
IOT Firewall Data Cybersecurity Technology Brochure Pdf
The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall. Showcasing this set of slides titled IOT Firewall Data Cybersecurity Technology Brochure Pdf The topics addressed in these templates are Packet Filtering, Proxy Service, Threat Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall.

Top To Down Approach For Business Information Protection Demonstration PDF
This slide covers top to down approach for business security which includes security leadership, program, policies and management. Further, it includes user management and information asset security.Pitch your topic with ease and precision using this Top To Down Approach For Business Information Protection Demonstration PDF. This layout presents information on Security Leadership, Security Program, Security Policies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
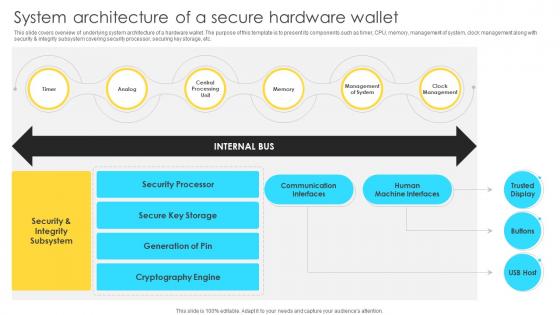
Mastering Blockchain Wallets System Architecture Of A Secure Hardware Wallet BCT SS V
This slide covers overview of underlying system architecture of a hardware wallet. The purpose of this template is to present its components such as timer, CPU, memory, management of system, clock management along with security and integrity subsystem covering security processor, securing key storage, etc. Welcome to our selection of the Mastering Blockchain Wallets System Architecture Of A Secure Hardware Wallet BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers overview of underlying system architecture of a hardware wallet. The purpose of this template is to present its components such as timer, CPU, memory, management of system, clock management along with security and integrity subsystem covering security processor, securing key storage, etc.

Execute Operational Procedure Plan Steps In Detail Process Redesigning Professional PDF
This slide provides information about the Third and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver an awe inspiring pitch with this creative execute operational procedure plan steps in detail process redesigning professional pdf bundle. Topics like potential consequence, several practices, process redesigning practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
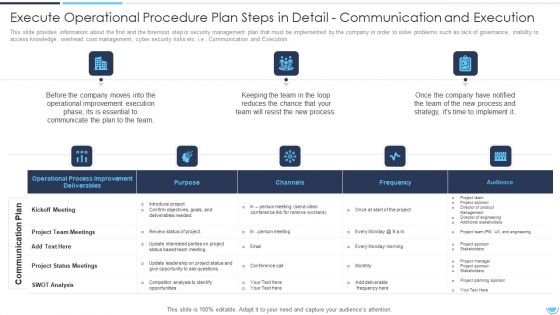
Execute Operational Procedure Plan Steps In Detail Communication And Execution Clipart PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution.Deliver an awe inspiring pitch with this creative execute operational procedure plan steps in detail communication and execution clipart pdf bundle. Topics like operational process improvement deliverables, project team meetings, project status meetings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Execute Operational Procedure Plan Steps In Detail Process Mapping Background PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping.Deliver and pitch your topic in the best possible manner with this execute operational procedure plan steps in detail process mapping background pdf. Use them to share invaluable insights on workflow applications, process mapping, process improvement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Communication And Execution Guidelines PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improvement, communicate, team, process, implement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
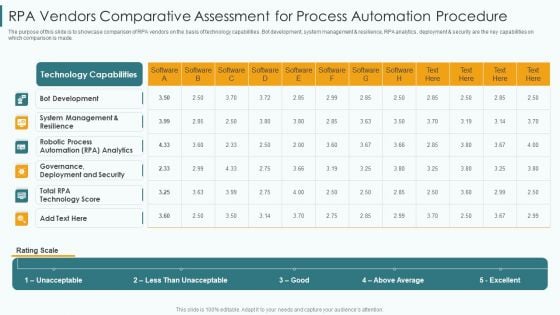
RPA Vendors Comparative Assessment For Process Automation Procedure Portrait PDF
The purpose of this slide is to showcase comparison of RPA vendors on the basis of technology capabilities. Bot development, system management and resilience, RPA analytics, deployment and security are the key capabilities on which comparison is made. Showcasing this set of slides titled rpa vendors comparative assessment for process automation procedure portrait pdf. The topics addressed in these templates are deployment, security, management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
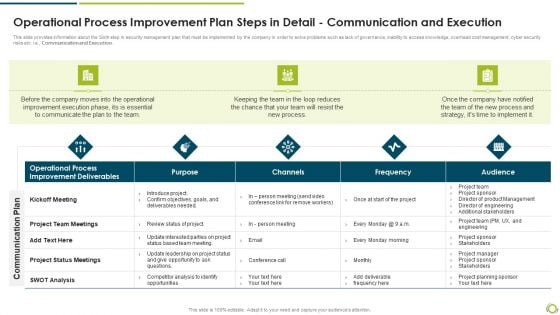
Operational Process Improvement Plan Steps In Detail Communication And Execution Rules PDF
This slide provides information about the Sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution.Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail communication and execution rules pdf bundle. Topics like improvement deliverables, operational process, project team meetings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Process Redesigning Graphics PDF
This slide provides information about the Third step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail process redesigning graphics pdf. Use them to share invaluable insights on potential consequence, process redesigning practices, practice implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
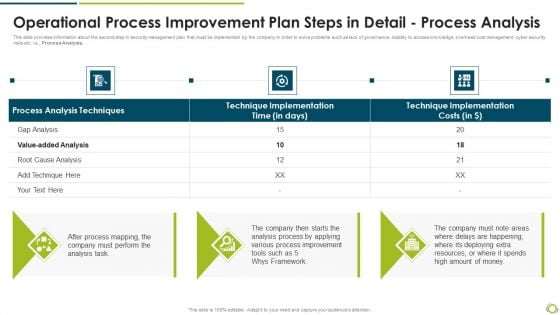
Operational Process Improvement Plan Steps In Detail Process Analysis Formats PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. Presenting operational process improvement plan steps in detail process analysis formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technique implementation, process analysis techniques, process improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Mapping Mockup PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping. Presenting operational process improvement plan steps in detail process mapping mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, graphic software, applications, accountability, productivity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Mapping Pictures PDF
This slide provides information about the first step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e, Process Mapping.Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail process mapping pictures pdf bundle. Topics like process mapping applications, workflow applications, process mapping can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Process Analysis Brochure PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Analysis. Presenting operational process improvement plan steps in detail process analysis brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like analysis, analysis process. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Redesigning Slides PDF
This slide provides information about the Third and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail process redesigning slides pdf. Use them to share invaluable insights on potential consequence, implementation, strategies, risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































