Collateral Management
ISO 27001 Organizational Qualifying Procedure Statement Of Applicability Slides PDF
Following slide illustrates statement of applicability covering sections namely control reference, control, its description, status, reason for selection and associated asset.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Statement Of Applicability Slides PDF bundle. Topics like Information Security, Segregation Of Duties, Management Responsibilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
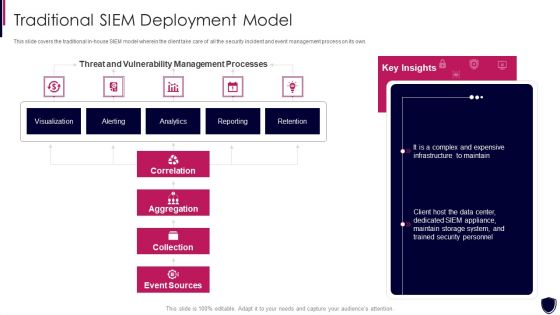
Enhancing Cyber Safety With Vulnerability Administration Traditional SIEM Deployment Designs PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this enhancing cyber safety with vulnerability administration traditional siem deployment designs pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources, our company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Efficiency Administration Software Investor Financing Different Phases Depicting Progressive Professional PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. This is a efficiency administration software investor financing different phases depicting progressive professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application, networking, services, secured digital. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

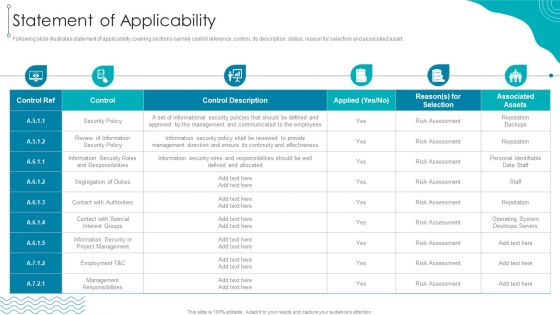
Info Safety And ISO 27001 Statement Of Applicability Ppt PowerPoint Presentation File Visual Aids PDF
Following slide illustrates statement of applicability covering sections namely control reference, control, its description, status, reason for selection and associated asset. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Statement Of Applicability Ppt PowerPoint Presentation File Visual Aids PDF. Use them to share invaluable insights on Security Policy, Segregation Duties, Management Responsibilities, Contact Authorities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
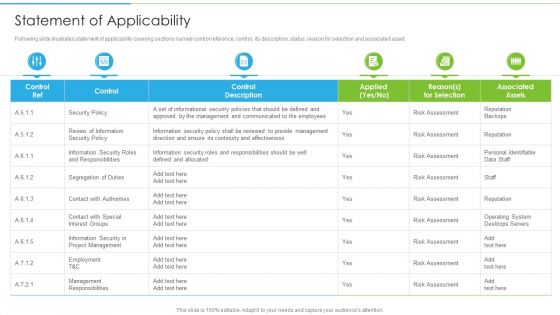
Ways To Accomplish ISO 27001 Accreditation Statement Of Applicability Demonstration PDF
Following slide illustrates statement of applicability covering sections namely control reference, control, its description, status, reason for selection and associated asset. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Statement Of Applicability Demonstration PDF. Use them to share invaluable insights on Security Policy, Contact Authorities, Project Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
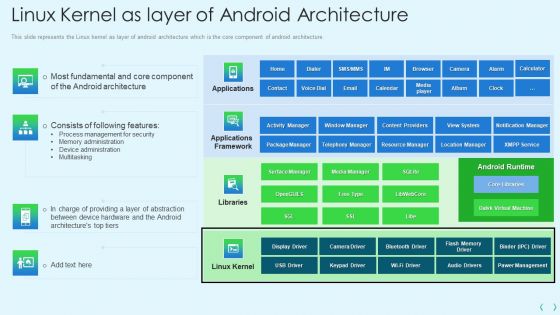
Smartphone Operating System Development IT Linux Kernel As Layer Of Android Architecture Information PDF
This slide represents the Linux kernel as layer of android architecture which is the core component of android architecture.Deliver an awe inspiring pitch with this creative smartphone operating system development it linux kernel as layer of android architecture information pdf bundle. Topics like process management for security, memory administration, device administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
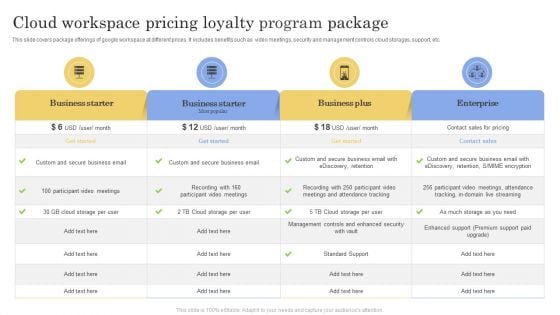
Cloud Workspace Pricing Loyalty Program Package Ppt Infographic Template Styles PDF
This slide covers package offerings of google workspace at different prices. It includes benefits such as video meetings, security and management controls cloud storages, support, etc. Showcasing this set of slides titled Cloud Workspace Pricing Loyalty Program Package Ppt Infographic Template Styles PDF. The topics addressed in these templates are Business Starter, Business Plus, Enterprise. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF
This slide provides information regarding ITIL process areas in terms of service strategy and service design and associated sequential activities. Deliver an awe inspiring pitch with this creative Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF bundle. Topics like Sequential Activities Processes, Strategy Management Execution, Sequential Activities Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
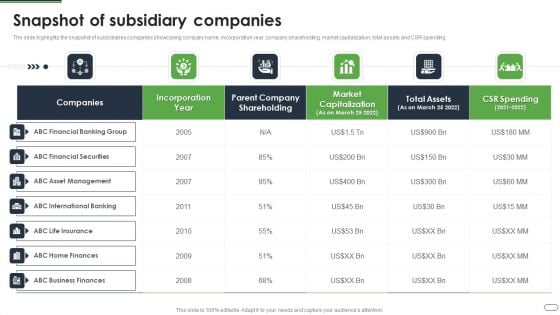
Financial Solutions Company Profile Snapshot Of Subsidiary Companies Graphics PDF
The slide highlights the snapshot of subsidiaries companies showcasing company name, incorporation year, company shareholding, market capitalization, total assets and CSR spending Deliver and pitch your topic in the best possible manner with this Financial Solutions Company Profile Snapshot Of Subsidiary Companies Graphics PDF Use them to share invaluable insights on Financial Banking, Financial Securities, Asset Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
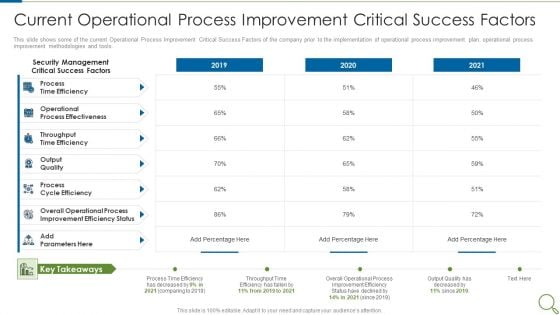
Current Operational Process Improvement Critical Success Factors Topics PDF
This slide shows some of the current Operational Process Improvement Critical Success Factors of the company prior to the implementation of operational process improvement plan, operational process improvement methodologies and tools. Deliver and pitch your topic in the best possible manner with this current operational process improvement critical success factors topics pdf. Use them to share invaluable insights on process, output quality, security management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
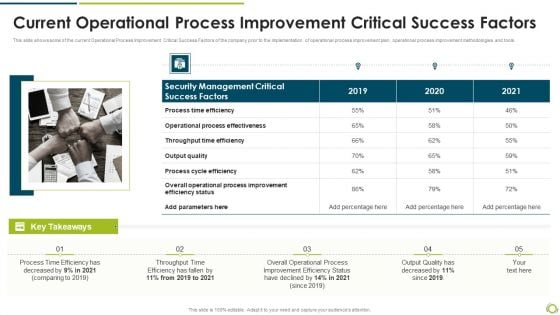
Current Operational Process Improvement Critical Success Factors Sample PDF
This slide shows some of the current Operational Process Improvement Critical Success Factors of the company prior to the implementation of operational process improvement plan, operational process improvement methodologies and tools.Deliver an awe inspiring pitch with this creative current operational process improvement critical success factors sample pdf bundle. Topics like security management critical, process time efficiency, throughput time efficiency can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
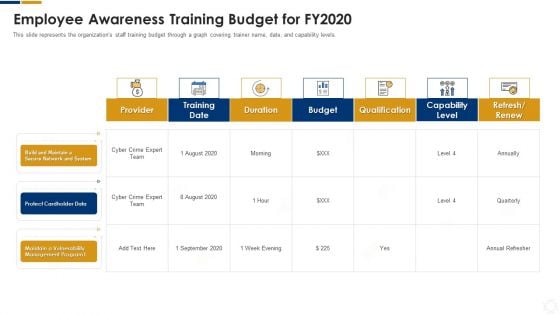
Cybersecurity Employee Awareness Training Budget For FY2020 Ppt Summary Objects PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative cybersecurity employee awareness training budget for fy2020 ppt summary objects pdf bundle. Topics like network, system, secure, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Information Technology Threat Mitigation Methods Background PDF
This is a Agenda For Information Technology Threat Mitigation Methods Background PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise, Organization, Management Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
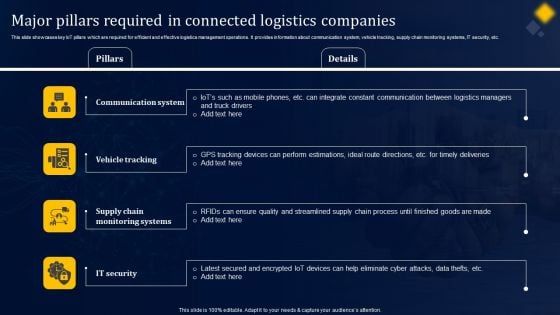
Major Pillars Required In Connected Logistics Companies Guidelines PDF
This slide showcases key IoT pillars which are required for efficient and effective logistics management operations. It provides information about communication system, vehicle tracking, supply chain monitoring systems, IT security, etc. There are so many reasons you need a Major Pillars Required In Connected Logistics Companies Guidelines PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
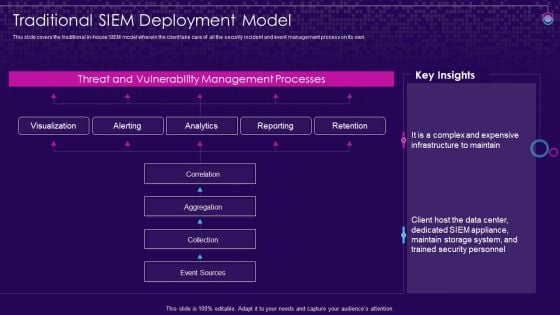
SIEM Services Traditional SIEM Deployment Model Ppt Gallery Layout Ideas PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative siem services traditional siem deployment model ppt gallery layout ideas pdf bundle. Topics like alerting, analytics, reporting, retention can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Risk Recognition Automation Traditional Siem Deployment Model Ppt Icon Graphic Tips PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative risk recognition automation traditional siem deployment model ppt icon graphic tips pdf bundle. Topics like alerting, visualization, analytics, reporting, retention can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
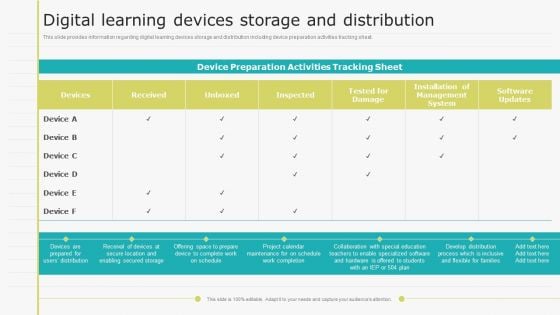
Virtual Learning Playbook Digital Learning Devices Storage And Distribution Diagrams PDF
This slide provides information regarding digital learning devices storage and distribution including device preparation activities tracking sheet. Deliver and pitch your topic in the best possible manner with this Virtual Learning Playbook Digital Learning Devices Storage And Distribution Diagrams PDF. Use them to share invaluable insights on Management System, Develop Distribution Process, Secure Location and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
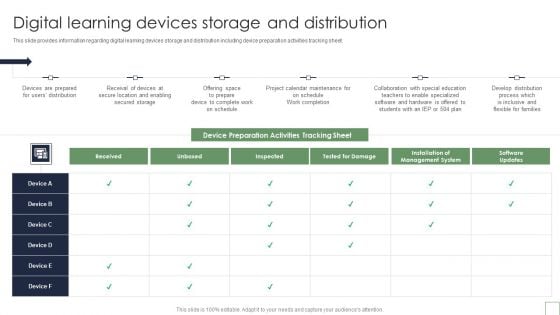
Remote Learning Playbook Digital Learning Devices Storage And Distribution Information PDF
This slide provides information regarding digital learning devices storage and distribution including device preparation activities tracking sheet. Deliver an awe inspiring pitch with this creative Remote Learning Playbook Digital Learning Devices Storage And Distribution Information PDF bundle. Topics like Installation Of Management System, Secure Location, Develop Distribution Process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Distressed Debt Refinancing For Organizaton Bankruptcy Ppt PowerPoint Presentation Infographic Template Graphics Template PDF
Presenting this set of slides with name distressed debt refinancing for organizaton bankruptcy ppt powerpoint presentation infographic template graphics template pdf. The topics discussed in these slides are creditor meeting, takeover by court appointed trustee, petition filling, credit counseling, chapter 7 eligibility, nonexempted property takeover, disposal of secured debts, financial management course, case closure, failure success rate. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Designing And Deployment CRM Training Program For Employees Introduction PDF
This slide highlights the CRM training Program for employees which includes overview training, lead management session, customization and data security session. Deliver an awe inspiring pitch with this creative designing and deployment crm training program for employees introduction pdf bundle. Topics like training session, involved, trainer, program, duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
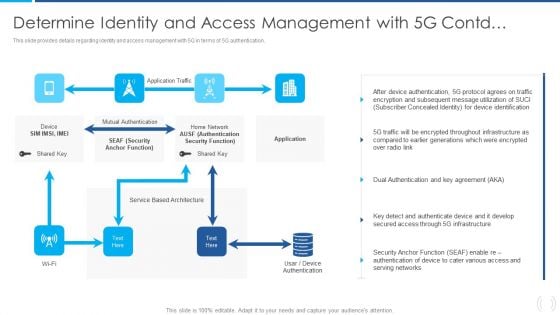
Proactive Method For 5G Deployment By Telecom Companies Determine Identity And Acces Microsoft PDF Structure PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this Proactive Method For 5G Deployment By Telecom Companies Determine Identity And Acces Microsoft PDF Structure PDF Use them to share invaluable insights on Mutual Authentication, Authentication Security, Service Based and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
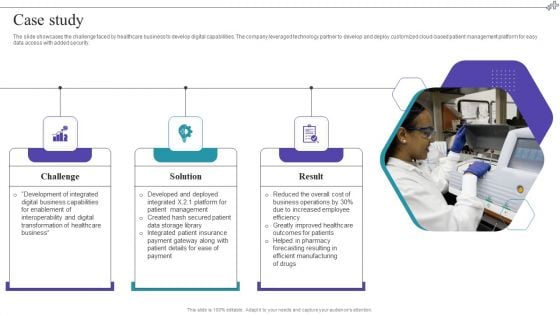
Medical Care Company Overview Case Study Sample PDF
The slide showcases the challenge faced by healthcare business to develop digital capabilities. The company leveraged technology partner to develop and deploy customized cloud-based patient management platform for easy data access with added security. Deliver and pitch your topic in the best possible manner with this Medical Care Company Overview Case Study Sample PDF. Use them to share invaluable insights on Solution, Result, Challenge and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Prioritized Risk And Response Grid With Likelihood Severity And Detention Assessment Introduction PDF
This slide displays the project management risk and response matrix. It risk details such as effect, likelihood, severity, detention, Risk Priority Number RPN, and response strategy. Showcasing this set of slides titled Prioritized Risk And Response Grid With Likelihood Severity And Detention Assessment Introduction PDF. The topics addressed in these templates are Incompetent Security, Equipment, Insurance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
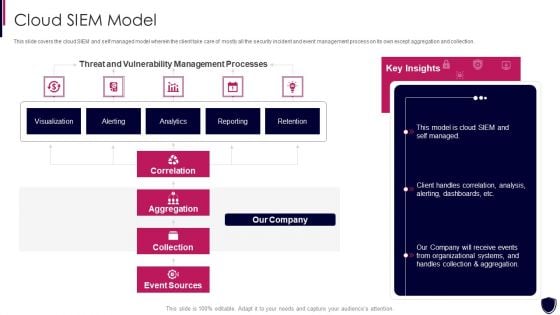
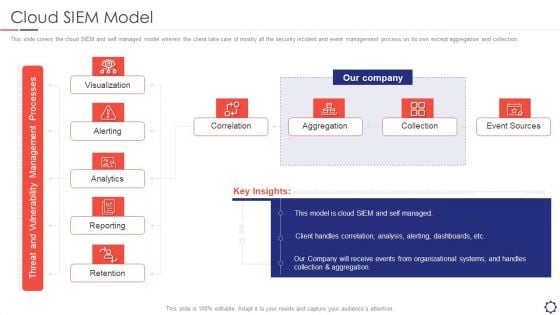
Enhancing Cyber Safety With Vulnerability Administration Cloud SIEM Model Clipart PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this enhancing cyber safety with vulnerability administration cloud siem model clipart pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources, our company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Tools Corporate Vulnerability Analysis In The Organization Guidelines PDF
This slide showcases tools for enterprise vulnerability management helps businesses secure their networks by identifying and fixing issues. It also includes tools such as nessus professional,nexpose community edition, openvas, manageengine vulnerability manager plus, etc. Persuade your audience using this Tools Corporate Vulnerability Analysis In The Organization Guidelines PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Organizations Environment, Limitless Evaluation, Implement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
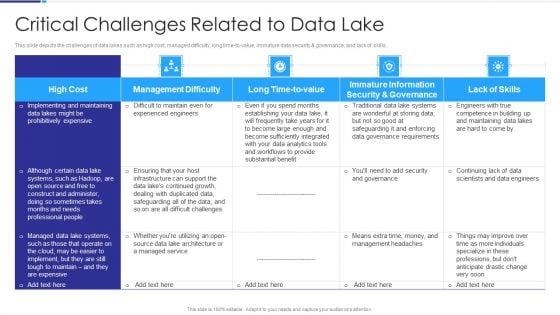
Data Lake Architecture Critical Challenges Related To Data Lake Slides PDF
This slide depicts the challenges of data lakes such as high cost, managed difficulty, long time-to-value, immature data security And governance, and lack of skills. Deliver and pitch your topic in the best possible manner with this Data Lake Architecture Critical Challenges Related To Data Lake Slides PDF. Use them to share invaluable insights on High Cost, Management Difficulty, Long Time To Value, Lack Skills and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
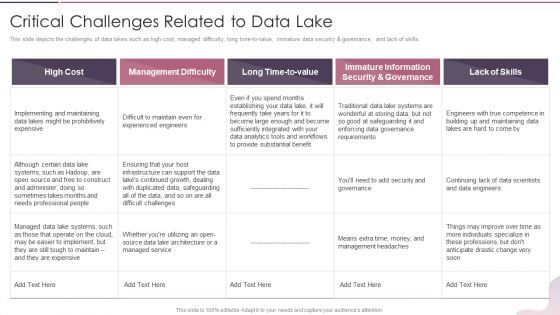
Data Lake Development With Azure Cloud Software Critical Challenges Related To Data Lake Guidelines PDF
This slide depicts the challenges of data lakes such as high cost, managed difficulty, long time to value, immature data security and governance, and lack of skills. Deliver and pitch your topic in the best possible manner with this Data Lake Development With Azure Cloud Software Critical Challenges Related To Data Lake Guidelines PDF. Use them to share invaluable insights on Management Difficulty, High Cost, Immature Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Contractual Risk Reduction Plan For Construction Firm Sample PDF
Mentioned slide provides insight about risk management plan which can be used by business to improve customer satisfaction. It includes risks such as financial risk, project risk, project implementation risk and security risk Presenting Contractual Risk Reduction Plan For Construction Firm Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk Category, Description, Risk Manager. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
SIEM Cloud SIEM Model Ppt Infographics Picture PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. This is a siem cloud siem model ppt infographics picture pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like visualization, alerting, analytics, reporting, retention. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
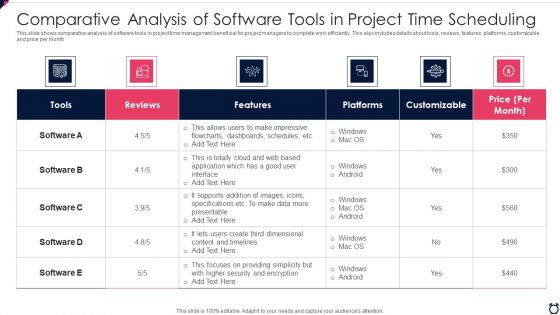
Comparative Analysis Of Software Tools In Project Time Scheduling Summary PDF
This slide shows comparative analysis of software tools in project time management beneficial for project managers to complete work efficiently. This also includes details about tools, reviews, features, platforms, customizable and price per month Showcasing this set of slides titled comparative analysis of software tools in project time scheduling summary pdf. The topics addressed in these templates are security, data, application. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
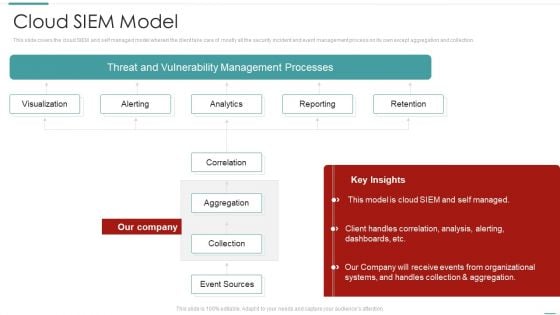
Risk Recognition Automation Cloud Siem Model Ppt Layouts Templates PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this risk recognition automation cloud siem model ppt layouts templates pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
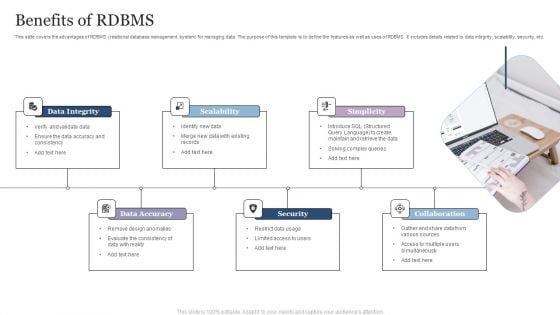
Benefits Of RDBMS Summary PDF
This slide covers the advantages of RDBMS relational database management system for managing data. The purpose of this template is to define the features as well as uses of RDBMS. It includes details related to data integrity, scalability, security, etc.Persuade your audience using this v. This PPT design covers Six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Integrity, Scalability, Simplicity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
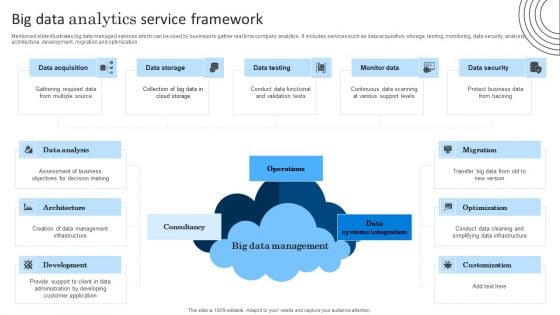
Big Data Analytics Service Framework Graphics PDF
Mentioned slide illustrates big data managed services which can be used by business to gather real time company analytics. It includes services such as data acquisition, storage, testing, monitoring, data security, analysis, architecture, development, migration and optimization. Persuade your audience using this Big Data Analytics Service Framework Graphics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Data Analysis, Assessment Of Business, Management Infrastructure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
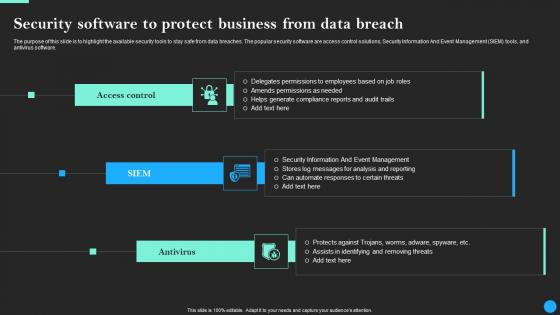
Security Software To Protect Business From Data Breach Prevention Elements Pdf
Want to ace your presentation in front of a live audience Our Security Software To Protect Business From Data Breach Prevention Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software.
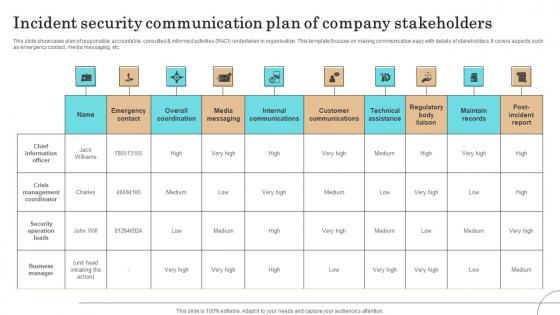
Incident Security Communication Plan Of Company Stakeholders Pictures Pdf
This slide showcases plan of responsible, accountable, consulted informed activities RACI undertaken in organisation. This template focuses on making communication easy with details of stakeholders. It covers aspects such as emergency contact, media messaging, etc.Showcasing this set of slides titled Incident Security Communication Plan Of Company Stakeholders Pictures Pdf The topics addressed in these templates are Crisis Management Coordinator, Security Operation Leads, Business Manager All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases plan of responsible, accountable, consulted informed activities RACI undertaken in organisation. This template focuses on making communication easy with details of stakeholders. It covers aspects such as emergency contact, media messaging, etc.
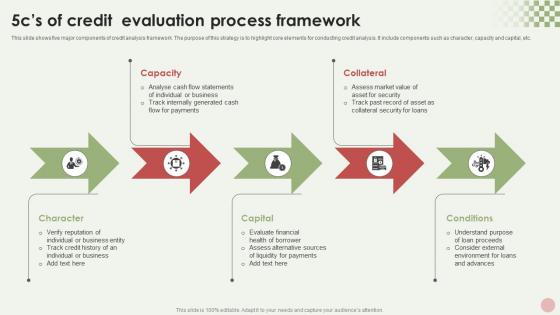
5cs Of Credit Evaluation Process Framework Mockup Pdf
This slide shows five major components of credit analysis framework. The purpose of this strategy is to highlight core elements for conducting credit analysis. It include components such as character, capacity and capital, etc. Showcasing this set of slides titled 5cs Of Credit Evaluation Process Framework Mockup Pdf. The topics addressed in these templates are Character, Capital, Collateral, Conditions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows five major components of credit analysis framework. The purpose of this strategy is to highlight core elements for conducting credit analysis. It include components such as character, capacity and capital, etc.

Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. The Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.
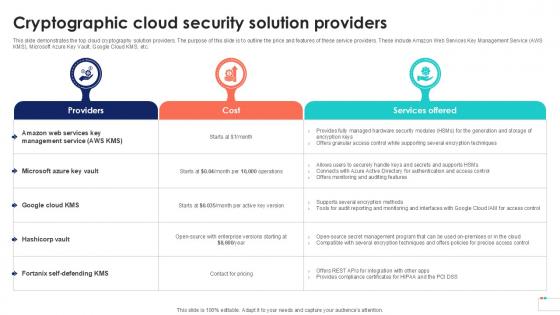
Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.
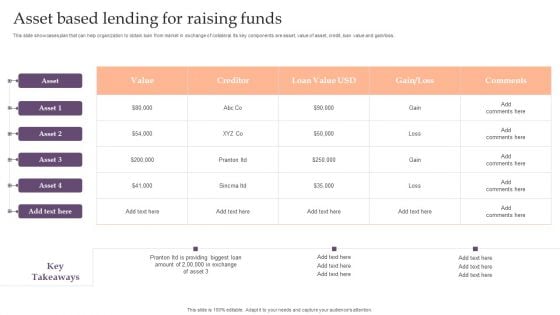
Assessing Debt And Equity Fundraising Alternatives For Business Growth Asset Based Lending Introduction PDF
This slide showcases plan that can help organization to obtain loan from market in exchange of collateral. Its key components are asset, value of asset, credit, loan value and gain loss. Present like a pro with Assessing Debt And Equity Fundraising Alternatives For Business Growth Asset Based Lending Introduction PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc. Find highly impressive Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc.

Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc.
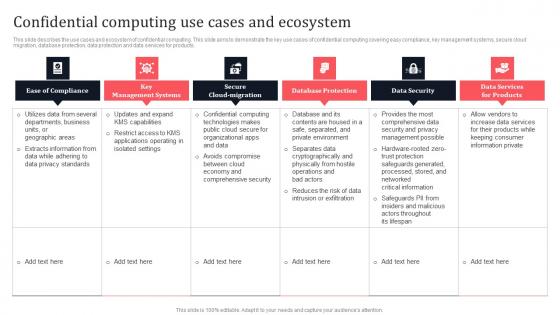
Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Explore a selection of the finest Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
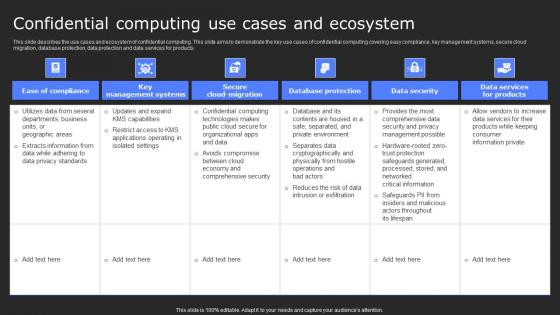
Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. The Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
How To Set Up Facebook Page For Brand Ppt PowerPoint Presentation File Icon PDF
The following slide outlines six step process that can be used by marketers to set up Facebook page and connect with target audience. The process begins with collecting brand collateral, creating new page, adding page images, business details, adding call-to-action CTA button, and publishing content. This modern and well arranged How To Set Up Facebook Page For Brand Ppt PowerPoint Presentation File Icon PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

New Brand Introduction Plan Typography Guidelines For Brands Content Professional PDF
This template covers topography usage guidelines for brand content. It also depicts a particular font family, size is used to create headlines on embedded or printed collateral. Explore a selection of the finest New Brand Introduction Plan Typography Guidelines For Brands Content Professional PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our New Brand Introduction Plan Typography Guidelines For Brands Content Professional PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
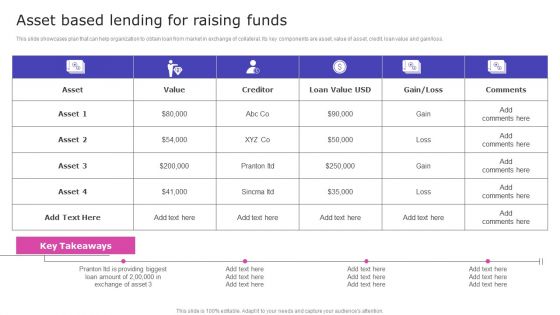
Strategic Fund Acquisition Plan For Business Opertions Expansion Asset Based Lending For Raising Funds Mockup PDF
This slide showcases plan that can help organization to obtain loan from market in exchange of collateral. Its key components are asset, value of asset, credit, loan value and gain or loss. This Strategic Fund Acquisition Plan For Business Opertions Expansion Asset Based Lending For Raising Funds Mockup PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
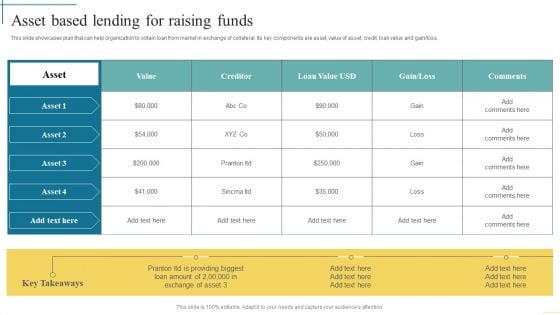
Asset Based Lending For Raising Funds Developing Fundraising Techniques Diagrams PDF
This slide showcases plan that can help organization to obtain loan from market in exchange of collateral. Its key components are asset, value of asset, credit, loan value and gain loss.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Asset Based Lending For Raising Funds Developing Fundraising Techniques Diagrams PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Asset Based Lending For Raising Funds Developing Fundraising Techniques Diagrams PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Capital Acquisition Strategy For Startup Business Asset Based Lending For Raising Funds Pictures PDF
This slide showcases plan that can help organization to obtain loan from market in exchange of collateral. Its key components are asset, value of asset, credit, loan value and gain or loss. This Capital Acquisition Strategy For Startup Business Asset Based Lending For Raising Funds Pictures PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Presenting Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Corporate Security, Industrial Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
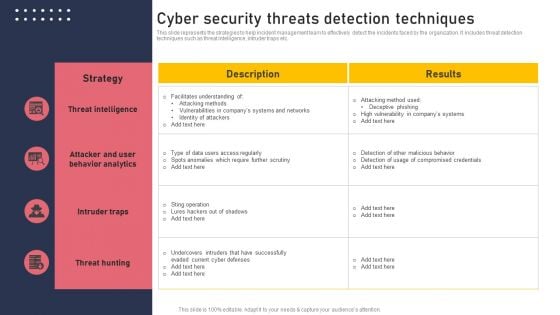
Cyber Security Threats Detection Techniques Demonstration PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Create an editable Cyber Security Threats Detection Techniques Demonstration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Threats Detection Techniques Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
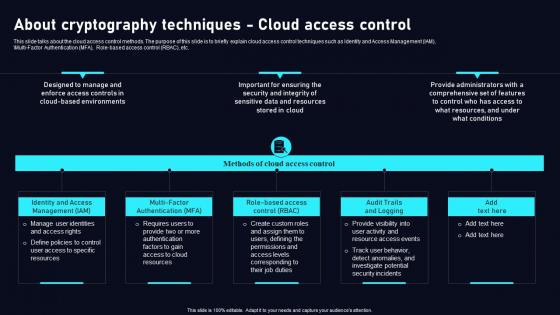
About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf
This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf today and make your presentation stand out from the rest This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc.
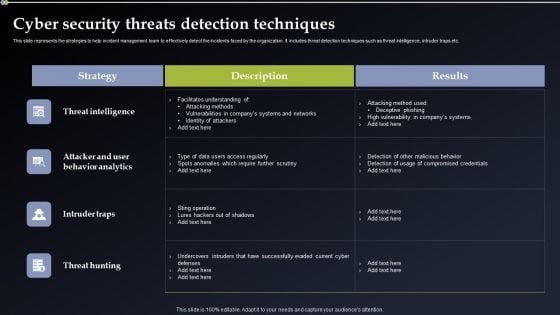
Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Want to ace your presentation in front of a live audience Our Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
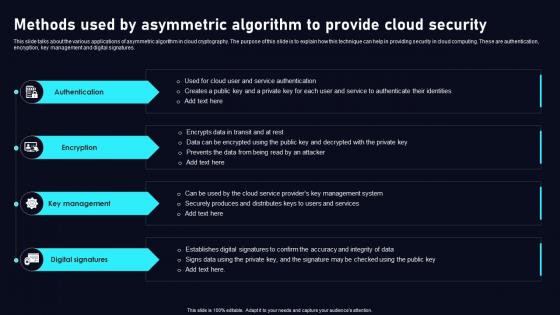
Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
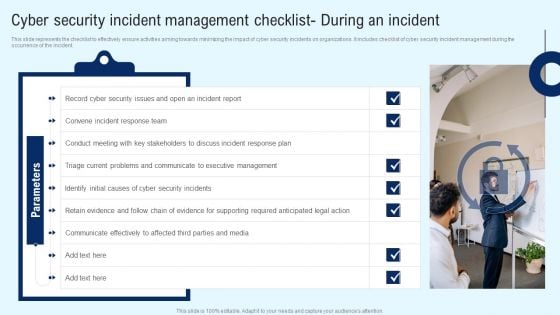
Implementing Cyber Security Incident Cyber Security Incident Checklist During An Incident Formats PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. Want to ace your presentation in front of a live audience Our Implementing Cyber Security Incident Cyber Security Incident Checklist During An Incident Formats PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
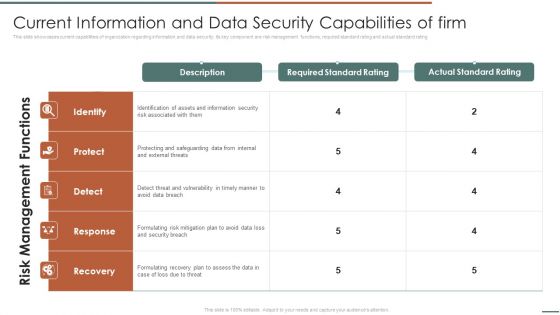
Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF. Use them to share invaluable insights on Required Standard Rating Actual, Standard Rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
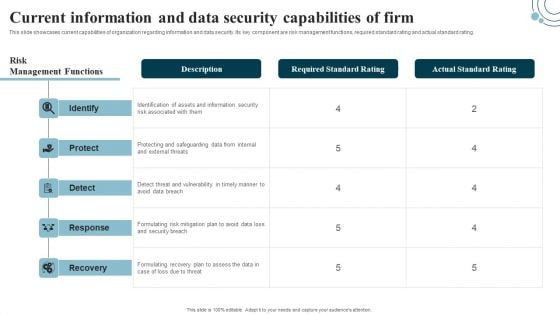
Developing IT Security Strategy Current Information And Data Security Capabilities Designs PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Developing IT Security Strategy Current Information And Data Security Capabilities Designs PDF from Slidegeeks and deliver a wonderful presentation.

Security And Process Integration How Security Concerns Affect Firm In Present Times Microsoft PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative security and process integration how security concerns affect firm in present times microsoft pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
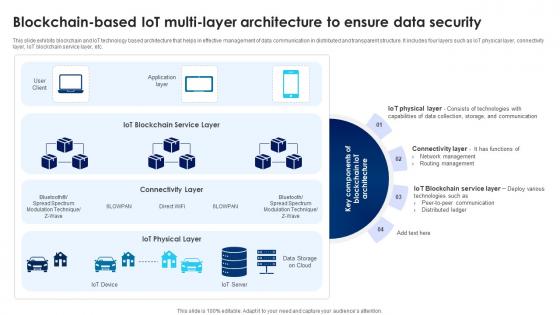
Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V
This slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc. Get a simple yet stunning designed Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc.

CYBER Security Breache Response Strategy User Awareness Training Program Prevent Cyber Security Incidents Demonstration PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find a pre designed and impeccable CYBER Security Breache Response Strategy User Awareness Training Program Prevent Cyber Security Incidents Demonstration PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Information And Technology Security Operations How Security Concerns Affect Firm In Present Times Rules PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative information and technology security operations how security concerns affect firm in present times rules pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































