Collateral Management

Operational Process Improvement Plan Steps In Detail Process Redesigning Elements PDF
This slide provides information about the third step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Redesigning. Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail process redesigning elements pdf bundle. Topics like risk analysis, metrics, implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
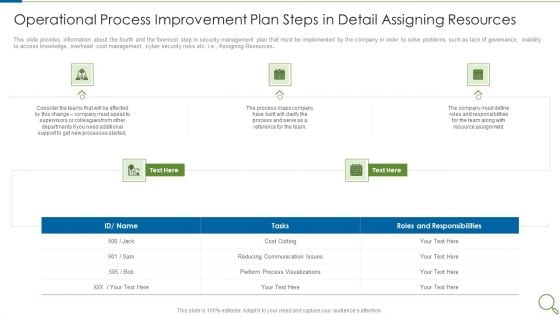
Operational Process Improvement Plan Steps In Detail Assigning Resources Professional PDF
This slide provides information about the fourth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational process improvement plan steps in detail assigning resources professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processes, team, cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Monitoring And Optimization Demonstration PDF
This slide provides information about the seventh and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Monitoring and Optimization. Presenting operational process improvement plan steps in detail monitoring and optimization demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like process improvement, performance, team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Monitoring And Optimization Clipart PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Monitoring and Optimization.Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail monitoring and optimization clipart pdf. Use them to share invaluable insights on technical business process monitoring, process improvement, implementation costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Assigning Resources Background PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Assigning Resources. Presenting operational process improvement plan steps in detail assigning resources background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reducing communication issues, perform process visualizations, roles and responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
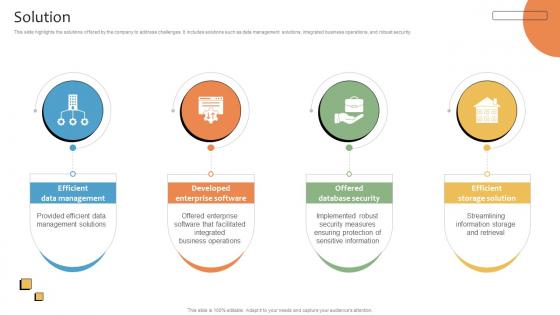
Solution CRMS Platform Business Model BMC SS V
This slide highlights the solutions offered by the company to address challenges. It includes solutions such as data management solutions, integrated business operations, and robust security. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution CRMS Platform Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide highlights the solutions offered by the company to address challenges. It includes solutions such as data management solutions, integrated business operations, and robust security.
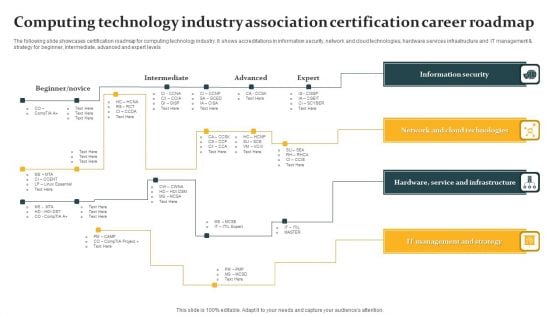
Computing Technology Industry Association Certification Career Roadmap Professional PDF
The following slide showcases certification roadmap for computing technology industry. It shows accreditations in information security, network and cloud technologies, hardware services infrastructure and IT management and strategy for beginner, intermediate, advanced and expert levels. Persuade your audience using this Computing Technology Industry Association Certification Career Roadmap Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security, Network And Cloud Technologies, IT Management And Strategy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
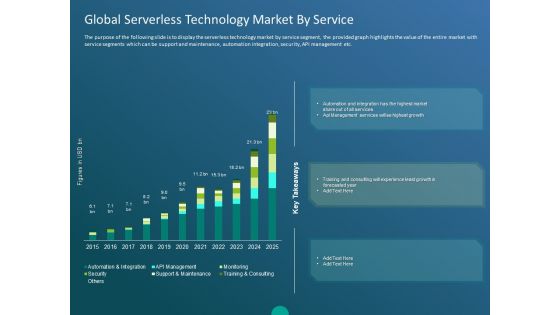
Functioning Of Serverless Computing Global Serverless Technology Market By Service Ppt Model Topics PDF
The purpose of the following slide is to display the serverless technology market by service segment, the provided graph highlights the value of the entire market with service segments which can be support and maintenance, automation integration, security, API management etc. Deliver an awe-inspiring pitch with this creative functioning of serverless computing global serverless technology market by service ppt model topics pdf bundle. Topics like key takeaways, automation and integration, monitoring, security, support and maintenance, api management, training and consulting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
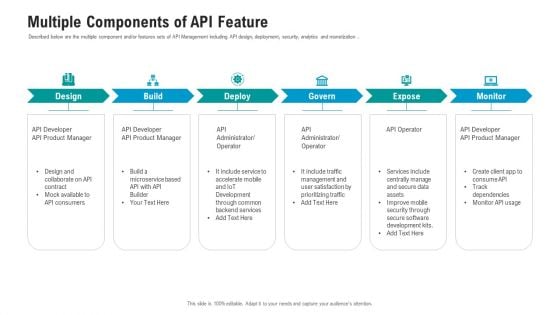
API Ecosystem Multiple Components Of API Feature Designs PDF
Described below are the multiple component and or features sets of API Management including API design, deployment, security, analytics and monetization. This is a api ecosystem multiple components of api feature designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like developer, consumers, service, management, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
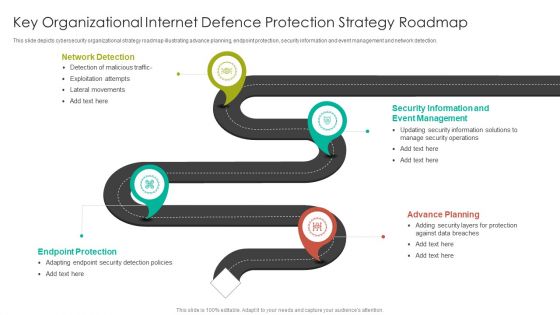
Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF
This slide depicts cybersecurity organizational strategy roadmap illustrating advance planning, endpoint protection, security information and event management and network detection.Persuade your audience using this Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Detection, Event Management, Security Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
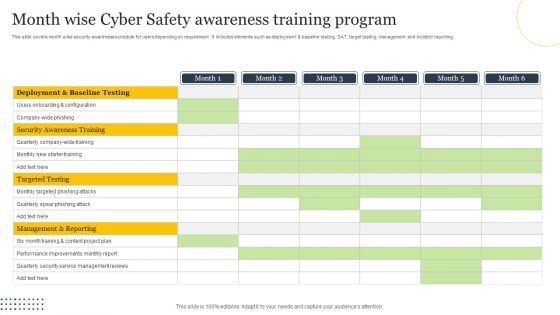
Month Wise Cyber Safety Awareness Training Program Ppt Styles Display PDF
This slide covers month wise security awareness schedule for users depending on requirement. It includes elements such as deployment and baseline testing, SAT, target testing, management and incident reporting. Showcasing this set of slides titled Month Wise Cyber Safety Awareness Training Program Ppt Styles Display PDF. The topics addressed in these templates are Security Awareness Training, Targeted Testing, Management And Reporting. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Impact Of Employing Digital Payments Strategy In Events And Venues Ppt Styles Layout Ideas PDF
This slide showcases the benefits of using cashless payments for events and venues to ensure better management. It includes benefits such as revenue growth, queue reduction, security, sales insight and vendor management etc. Presenting Impact Of Employing Digital Payments Strategy In Events And Venues Ppt Styles Layout Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Revenue Growth, Queues Reduction, Safe And Secure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Challenges Faced By Companies In Online Marketing Efficient Marketing Tactics Structure Pdf
Following slide outlines major challenges of ecommerce websites and potential solutions to overcome them. It include issues such as cyber security, online data verification, data management and customer experiences. There are so many reasons you need a Challenges Faced By Companies In Online Marketing Efficient Marketing Tactics Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide outlines major challenges of ecommerce websites and potential solutions to overcome them. It include issues such as cyber security, online data verification, data management and customer experiences.

Solution Offered Delivery Service Provider Business Model BMC SS V
This slide showcases solutions such as a delivery management system, live tracking, security and reliability, and responsive customer support. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Offered Delivery Service Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases solutions such as a delivery management system, live tracking, security and reliability, and responsive customer support.
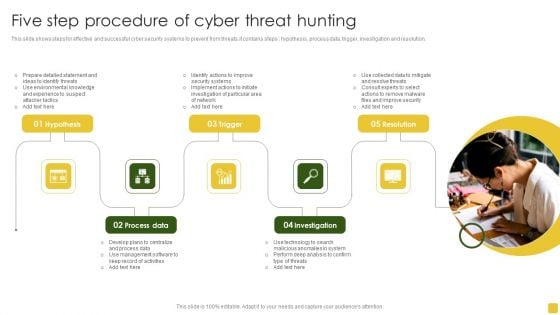
Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Risk Associated With Team Working Environment In Workplace Ppt Icon Examples PDF
This slide represents risk associated with collaborative working environment in workplace. It covers risk such as wasting time, poor project management poor strategy execution, negative impact n employee morale and security risk. Pitch your topic with ease and precision using this Risk Associated With Team Working Environment In Workplace Ppt Icon Examples PDF. This layout presents information on Risk, Strategy Execution, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
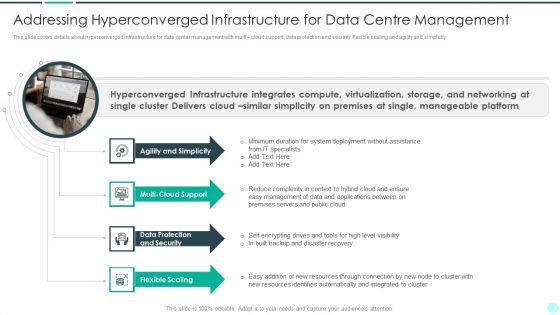
Executing Advance Data Analytics At Workspace Addressing Hyperconverged Professional PDF
This slide covers details about hyperconverged infrastructure for data center management with multi cloud support, data protection and security, flexible scaling and agility and simplicity. This is a executing advance data analytics at workspace addressing hyperconverged professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agility, resources, integrated, resources, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
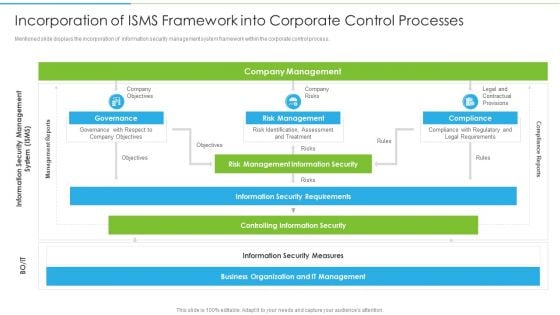
Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process. This is a Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Company Objectives, Company Management, Company Risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Focus Areas For Internal Audit And Review Teams In FY23 Icons PDF
This slide illustrates key areas of focus for internal auditors for risk management and lawful following of compliance laws. It includes proposed areas like health and safety, payroll, IT security etc.Presenting Focus Areas For Internal Audit And Review Teams In FY23 Icons PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Proposed Internal, Reputational Risk, Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
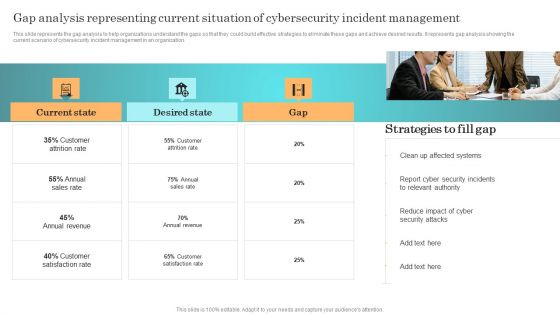
Incident Response Techniques Deployement Gap Analysis Representing Current Situation Of Cybersecurity Designs PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. There are so many reasons you need a Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
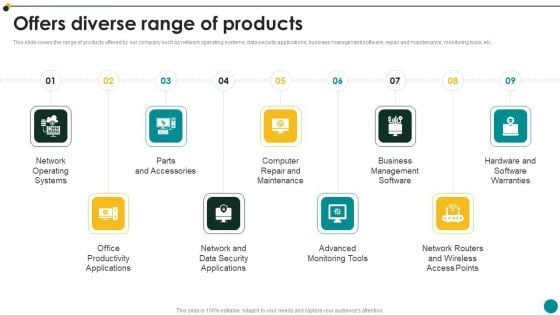
IT Services And Consulting Company Profile Offers Diverse Range Of Products Themes PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a IT Services And Consulting Company Profile Offers Diverse Range Of Products Themes PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Parts And Accessories, Business Management Software, Advanced Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
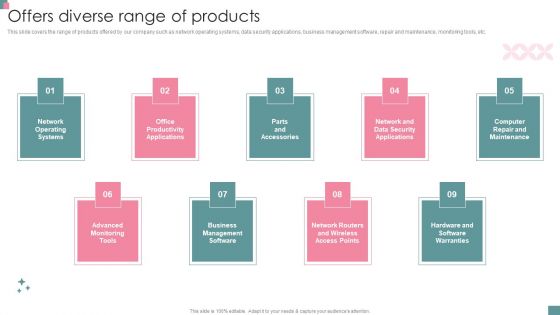
Small Business Venture Company Profile Offers Diverse Range Of Products Clipart PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a Small Business Venture Company Profile Offers Diverse Range Of Products Clipart PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operating Systems, Advanced Monitoring, Management Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Technologies To Ensure Data Protection And Privacy Background PDF
The following slide showcases some technologies to administer organizational data privacy and security concerns. It includes elements such as data encryption, change management and auditing, user and behavior analytics UEBA, backup and recovery etc. Presenting Technologies To Ensure Data Protection And Privacy Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Encryption, Change Management And Auditing, Backup And Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
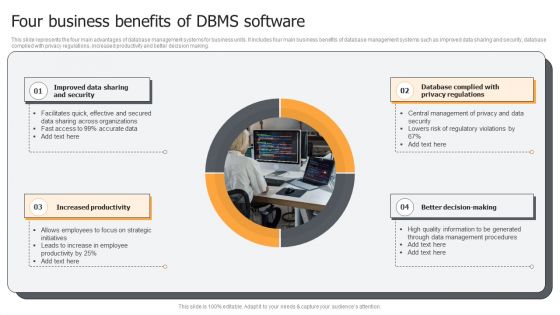
Four Business Benefits Of DBMS Software Ppt PowerPoint Presentation File Skills PDF
This slide represents the four main advantages of database management systems for business units. It includes four main business benefits of database management systems such as improved data sharing and security, database complied with privacy regulations, increased productivity and better decision making. Presenting Four Business Benefits Of DBMS Software Ppt PowerPoint Presentation File Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Improved Data Sharing, Increased Productivity, Better Decision Making. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
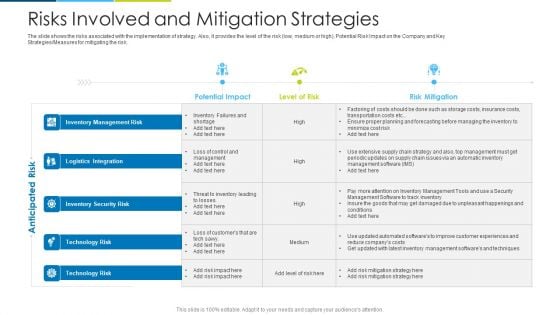
Risks Involved And Mitigation Strategies Ppt Design Templates PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies or Measures for mitigating the risk. Deliver an awe inspiring pitch with this creative risks involved and mitigation strategies ppt design templates pdf bundle. Topics like inventory management risk, inventory management risk, inventory security risk, technology risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
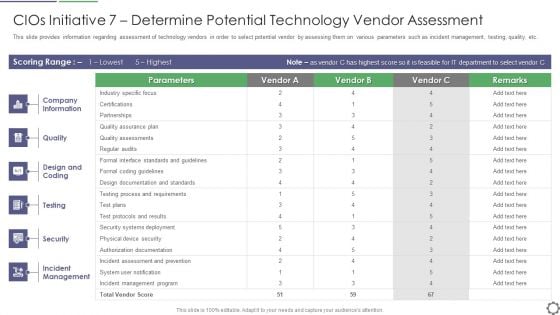
Cios Initiative 7 Determine Potential Technology Vendor Assessment Ppt Gallery Example Introduction PDF
This slide provides information regarding assessment of technology vendors in order to select potential vendor by assessing them on various parameters such as incident management, testing, quality, etc. Deliver and pitch your topic in the best possible manner with this cios initiative 7 determine potential technology vendor assessment ppt gallery example introduction pdf. Use them to share invaluable insights on company information, design and coding, security, incident management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CRM Implementation Strategy CRM Training Program For Employees Infographics PDF
This slide highlights the CRM training Program for employees which includes overview training, lead management session, customization and data security session.This is a CRM Implementation Strategy CRM Training Program For Employees Infographics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Session, Customization Session, Overview Training You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Solutions Business Profile We Also Deliver Support Services Clipart PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a Information Technology Solutions Business Profile We Also Deliver Support Services Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Private Networking, Network Firewall. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Small Business Venture Company Profile We Also Deliver Support Services Summary PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a Small Business Venture Company Profile We Also Deliver Support Services Summary PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Private Networking, Firewall Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
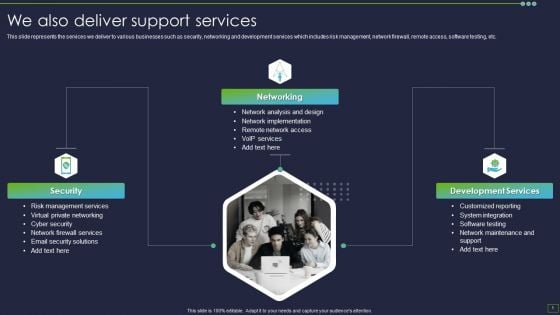
IT Consultancy Services Company Profile We Also Deliver Support Services Structure PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a IT Consultancy Services Company Profile We Also Deliver Support Services Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Services, Management Services, Network Implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Drone Tech Applications In Farming Industry Brochure PDF
The following slide highlights usage of drone technology for surveying topographic boundaries and soil monitoring. It includes components such as planting and seeding, spray treatment, security, livestock management and crop surveillance etc.Showcasing this set of slides titled Drone Tech Applications In Farming Industry Brochure PDF. The topics addressed in these templates are Planting Seeding, Livestock Management, Spray Treatment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Communication Infrastructure Services Download PDF
The following slide demonstrates information and communication technology infrastructure services for optimizing output, mitigate internal and external security threat. It includes components such as operations and network management etc. Persuade your audience using this IT Communication Infrastructure Services Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Applications, Description, Operations Management . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
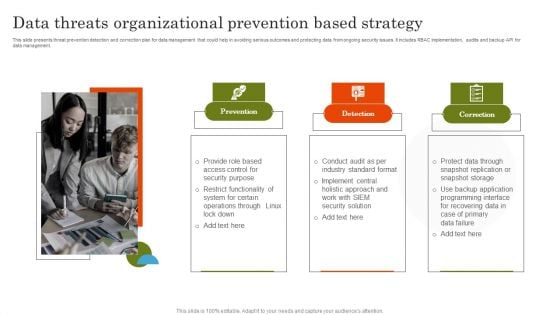
Data Threats Organizational Prevention Based Strategy Infographics PDF
This slide presents threat prevention detection and correction plan for data management that could help in avoiding serious outcomes and protecting data from ongoing security issues. It includes RBAC implementation, audits and backup API for data management. Increase audience engagement and knowledge by dispensing information using Data Threats Organizational Prevention Based Strategy Infographics PDF. This template helps you present information on three stages. You can also present information on Prevention, Detection, Correction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
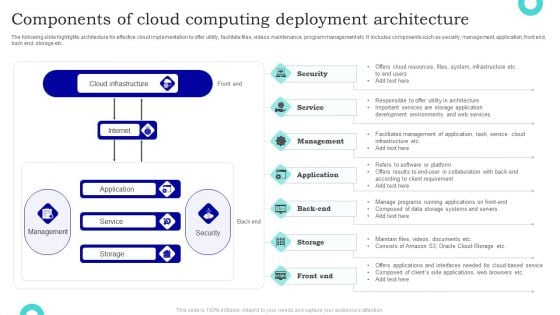
Components Of Cloud Computing Deployment Architecture Sample PDF
The following slide highlights architecture for effective cloud implementation to offer utility, facilitate files, videos maintenance, program management etc. It includes components such as security, management, application, front end, back end, storage etc. Pitch your topic with ease and precision using this Components Of Cloud Computing Deployment Architecture Sample PDF. This layout presents information on Cloud Infrastructure, Application, Service. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents Food Security Excellence Ppt Model Inspiration PDF
Deliver an awe inspiring pitch with this creative table of contents food security excellence ppt model inspiration pdf bundle. Topics like executive, processing, performance, training, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
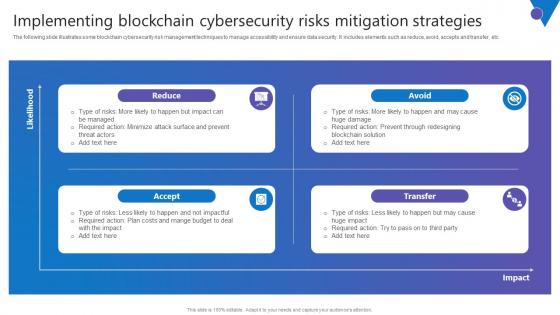
Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc.
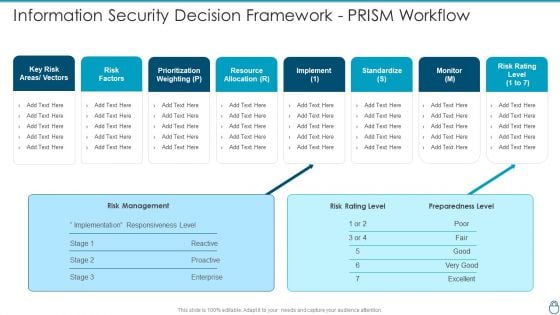
Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF Use them to share invaluable insights on Prioritization Weighting, Resource Allocation, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
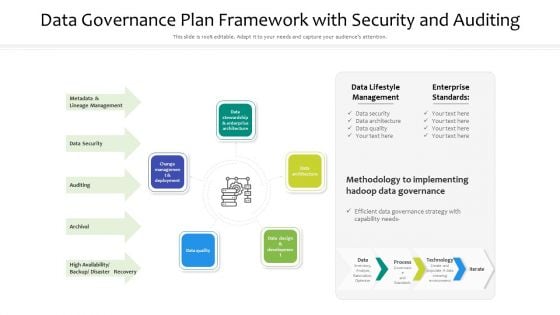
Data Governance Plan Framework With Security And Auditing Ppt PowerPoint Presentation File Template PDF
Presenting data governance plan framework with security and auditing ppt powerpoint presentation file template pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including data architecture, data quality, change management and deployment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
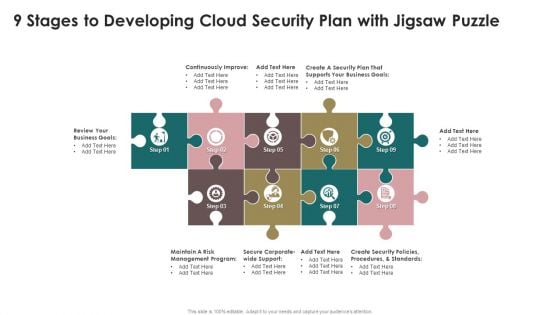
9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF
Presenting 9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Management Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
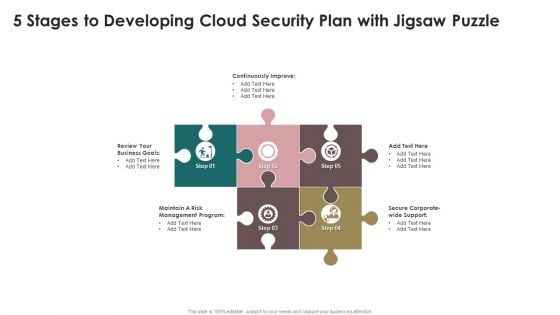
5 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Portrait PDF
Presenting 5 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Portrait PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Business Goals, Management Program, Secure Corporate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
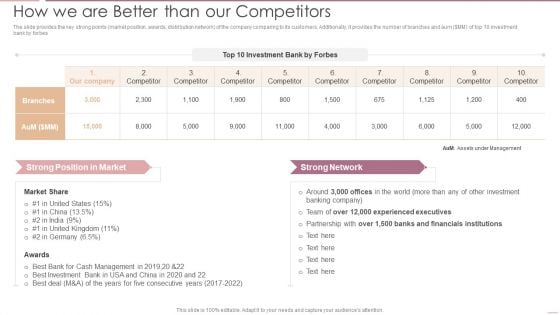
Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF
Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF bundle. Topics like Experienced Executives, Financials Institutions, Cash Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
3 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Icons PDF
Presenting 3 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Icons PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Business Goals, Management Program, Continuously Improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
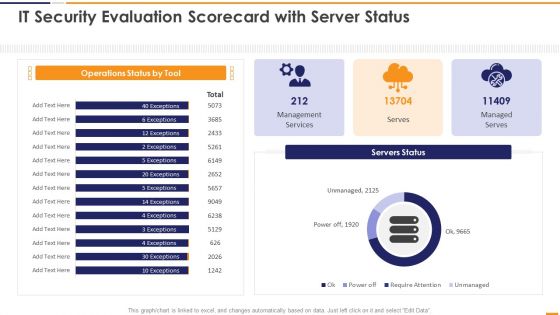
IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF bundle. Topics like Operations Status Tool, Management Services Managed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
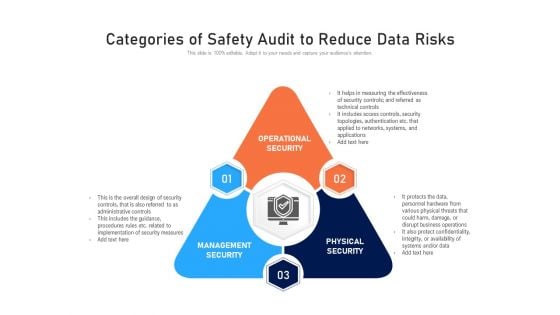
Categories Of Safety Audit To Reduce Data Risks Ppt PowerPoint Presentation Gallery Graphics Download PDF
Presenting categories of safety audit to reduce data risks ppt powerpoint presentation gallery graphics download pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including operational security, physical security, management security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
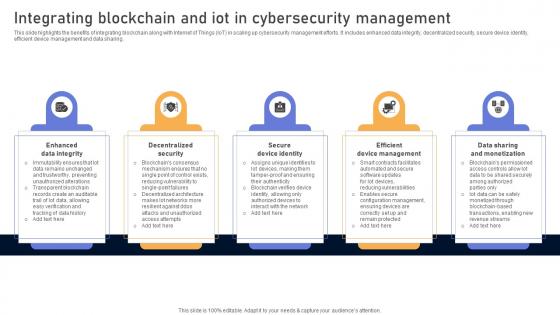
Comprehensive Look At Blockchain Technologys Integrating Blockchain And IoT BCT SS V
This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comprehensive Look At Blockchain Technologys Integrating Blockchain And IoT BCT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comprehensive Look At Blockchain Technologys Integrating Blockchain And IoT BCT SS V today and make your presentation stand out from the rest This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing.
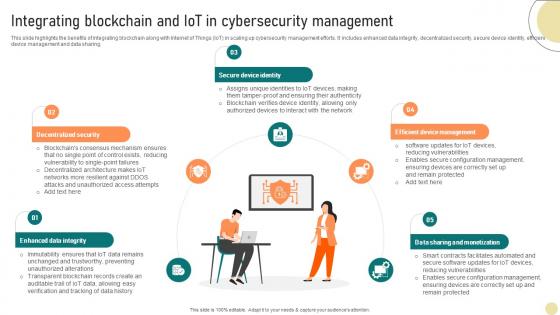
Visionary Guide To Blockchain Technologys Integrating Blockchain And IoT BCT SS V
This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing. Find highly impressive Visionary Guide To Blockchain Technologys Integrating Blockchain And IoT BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Visionary Guide To Blockchain Technologys Integrating Blockchain And IoT BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing.
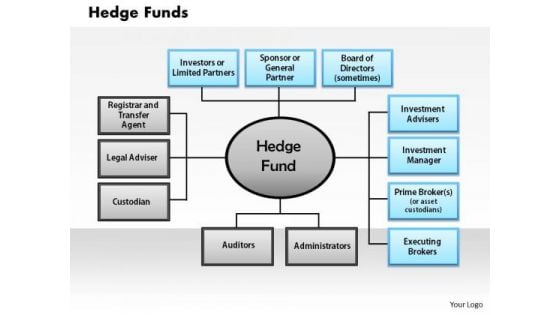
Business Framework Hedge Funds PowerPoint Presentation
This image slide displays hedge funds which is an investment vehicle that pools capital from a number of investors and invests in securities and other instruments. This image slide may be used to depict finance management in your presentations. This image slide will enhance the quality of your presentations.
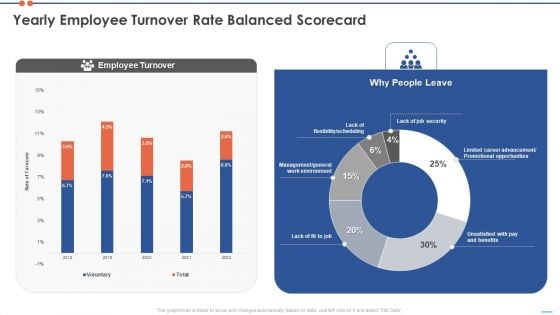
Staff Turnover Ratio BSC Yearly Employee Turnover Rate Balanced Scorecard Inspiration PDF
Deliver and pitch your topic in the best possible manner with this staff turnover ratio bsc yearly employee turnover rate balanced scorecard inspiration pdf. Use them to share invaluable insights on opportunities, job security, flexibility, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Table Of Contents For WAF Platform Plan Guidelines PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For WAF Platform Plan Guidelines PDF bundle. Topics like Web Application Firewall, Centralized Management System, Firewall Security Models can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
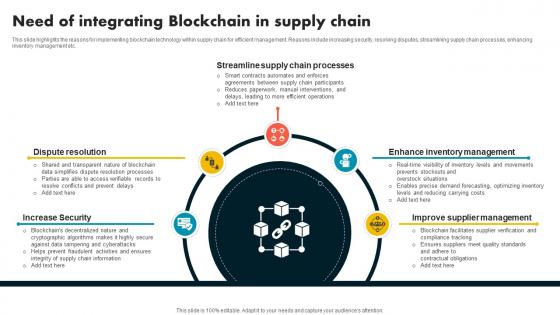
Need Of Integrating Blockchain In Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V
This slide highlights the reasons for implementing blockchain technology within supply chain for efficient management. Reasons include increasing security, resolving disputes, streamlining supply chain processes, enhancing inventory management etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Need Of Integrating Blockchain In Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Need Of Integrating Blockchain In Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V. This slide highlights the reasons for implementing blockchain technology within supply chain for efficient management. Reasons include increasing security, resolving disputes, streamlining supply chain processes, enhancing inventory management etc.
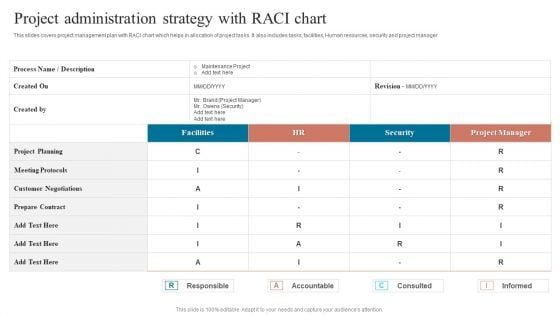
Project Administration Strategy With Raci Chart Rules PDF
This slides covers project management plan with RACI chart which helps in allocation of project tasks. It also includes tasks, facilities, Human resources, security and project manager. Showcasing this set of slides titled Project Administration Strategy With Raci Chart Rules PDF. The topics addressed in these templates are Meeting Protocols, Customer Negotiations, Meeting Protocols. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
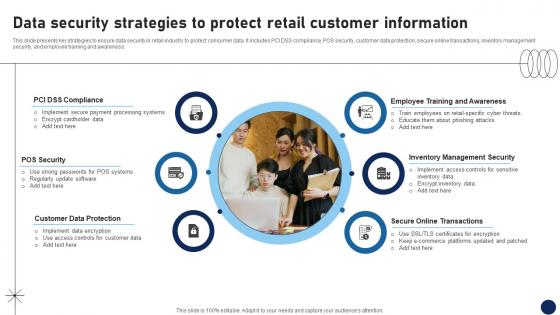
Data Security Strategies To Protect Retail Customer Information DT SS V
This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Security Strategies To Protect Retail Customer Information DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness.
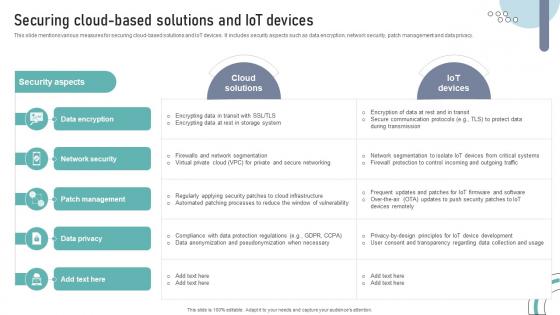
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy.
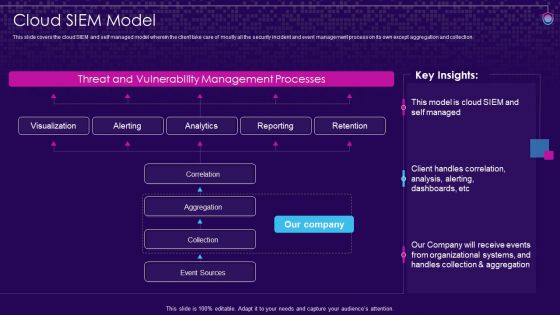
SIEM Services Cloud SIEM Model Ppt Outline Aids PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver an awe inspiring pitch with this creative siem services cloud siem model ppt outline aids pdf bundle. Topics like aggregation, correlation, collection, event sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
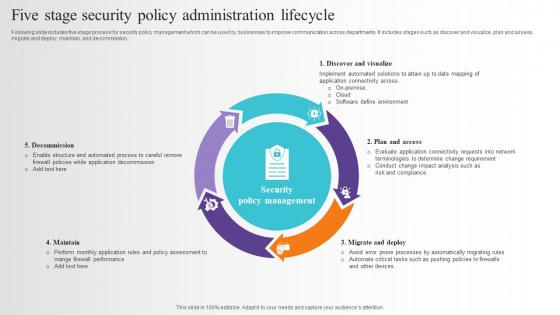
Five Stage Security Policy Administration Lifecycle Pictures Pdf
Following slide includes five stage process for security policy management which can be used by businesses to improve communication across departments. It includes stages such as discover and visualize, plan and assess, migrate and deploy, maintain, and decommission. Pitch your topic with ease and precision using this Five Stage Security Policy Administration Lifecycle Pictures Pdf. This layout presents information on Plan And Assess, Migrate And Deploy, Maintain, Decommission. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide includes five stage process for security policy management which can be used by businesses to improve communication across departments. It includes stages such as discover and visualize, plan and assess, migrate and deploy, maintain, and decommission.
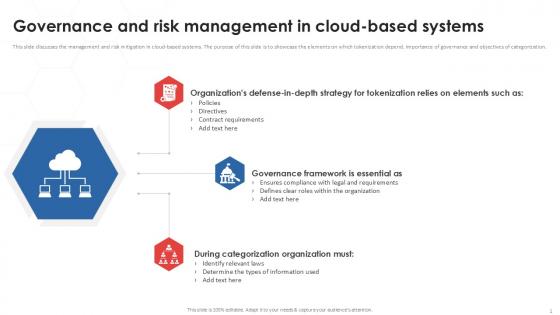
Governance And Risk Tokenization Strategies For Data Security PPT Sample
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Boost your pitch with our creative Governance And Risk Tokenization Strategies For Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization.

Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V
This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V from Slidegeeks and deliver a wonderful presentation. This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc.
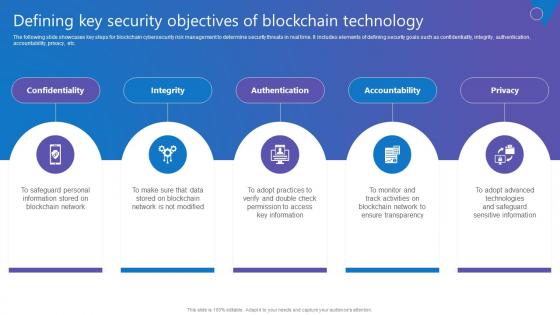
Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf
The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Want to ace your presentation in front of a live audience Our Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc.
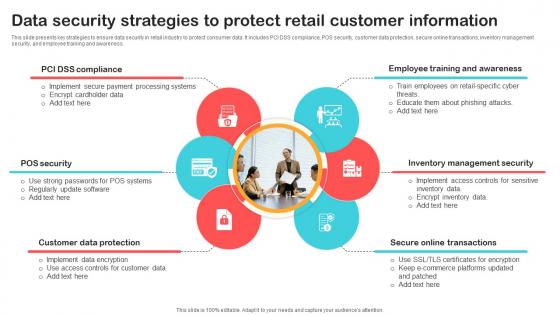
Data Security Strategies To Protect Retail Customer Optimizing Retail Operations With Digital DT SS V
This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Security Strategies To Protect Retail Customer Optimizing Retail Operations With Digital DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































