Construction Safety Plan

Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf
This slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments Showcasing this set of slides titled Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf. The topics addressed in these templates are Security Assessments, Building Security, Facility Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments
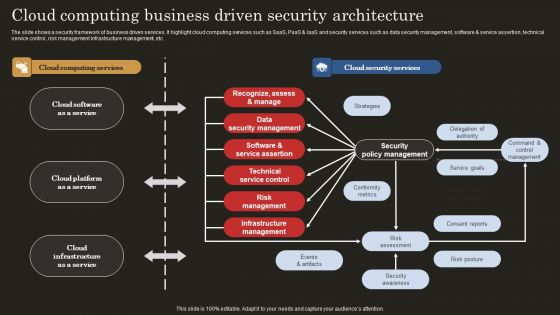
Cloud Computing Business Driven Security Architecture Introduction PDF
The slide shows a security framework of business driven services. It highlight cloud computing services such as SaaS, PaaS and IaaS and security services such as data security management, software and service assertion, technical service control, risk management infrastructure management, etc. Showcasing this set of slides titled Cloud Computing Business Driven Security Architecture Introduction PDF. The topics addressed in these templates are Strategies, Delegation Authority, Service Goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Technical Criteria Billing Building Utility Billing And Invoicing Management System Structure Pdf
Following slide represents technological factor to consider while selecting billing system. It includes pointers such as security, deployment options and developer experience. Find a pre designed and impeccable Technical Criteria Billing Building Utility Billing And Invoicing Management System Structure Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Following slide represents technological factor to consider while selecting billing system. It includes pointers such as security, deployment options and developer experience.

Applications Of Secure Web Gateway In Various Industries Web Threat Protection System
This slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc. Create an editable Applications Of Secure Web Gateway In Various Industries Web Threat Protection System that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Applications Of Secure Web Gateway In Various Industries Web Threat Protection System is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc.
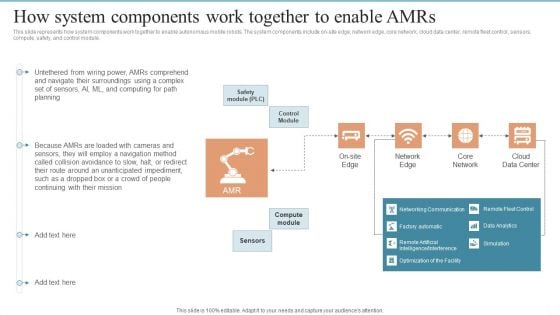
AMR Robot How System Components Work Together To Enable Amrs Ppt PowerPoint Presentation File Slides PDF
This slide represents how system components work together to enable autonomous mobile robots. The system components include on-site edge, network edge, core network, cloud data center, remote fleet control, sensors, compute, safety, and control module. This AMR Robot How System Components Work Together To Enable Amrs Ppt PowerPoint Presentation File Slides PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
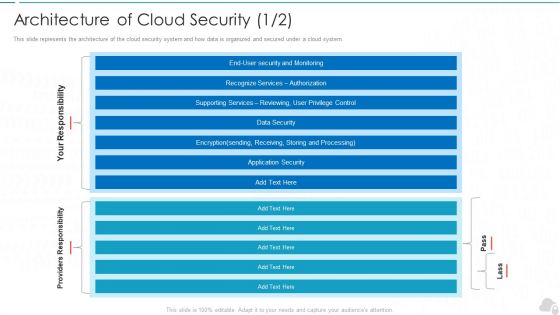
Architecture Of Cloud Security Authorization Cloud Computing Security IT Ppt Model Sample PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative architecture of cloud security authorization cloud computing security it ppt model sample pdf bundle. Topics like monitoring, security, authorization, services, data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
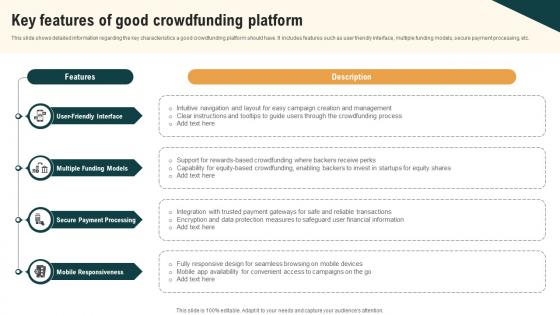
Key Features Of Good Crowdfunding Platform Real Estate Crowdfunding To Unlock Fin SS V
This slide shows detailed information regarding the key characteristics a good crowdfunding platform should have. It includes features such as user friendly interface, multiple funding models, secure payment processing, etc. Are you searching for a Key Features Of Good Crowdfunding Platform Real Estate Crowdfunding To Unlock Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Features Of Good Crowdfunding Platform Real Estate Crowdfunding To Unlock Fin SS V from Slidegeeks today. This slide shows detailed information regarding the key characteristics a good crowdfunding platform should have. It includes features such as user friendly interface, multiple funding models, secure payment processing, etc.
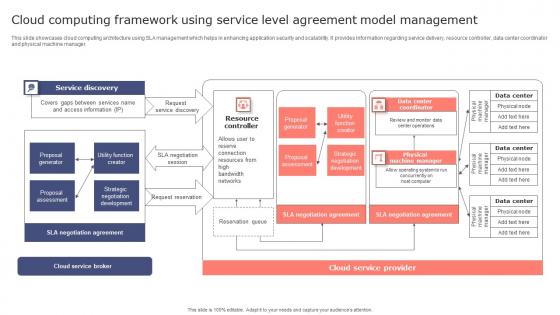
Cloud Computing Framework Using Service Level Agreement Model Management Topics Pdf
This slide showcases cloud computing architecture using SLA management which helps in enhancing application security and scalability. It provides information regarding service delivery, resource controller, data center coordinator and physical machine manager. Showcasing this set of slides titled Cloud Computing Framework Using Service Level Agreement Model Management Topics Pdf. The topics addressed in these templates are Service Discovery, Resource Controller. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases cloud computing architecture using SLA management which helps in enhancing application security and scalability. It provides information regarding service delivery, resource controller, data center coordinator and physical machine manager.
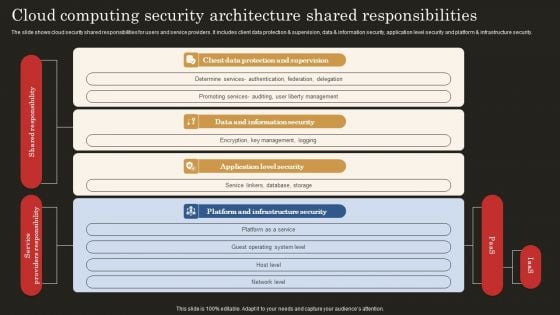
Cloud Computing Security Architecture Shared Responsibilities Brochure PDF
The slide shows cloud security shared responsibilities for users and service providers. It includes client data protection and supervision, data and information security, application level security and platform and infrastructure security. Showcasing this set of slides titled Cloud Computing Security Architecture Shared Responsibilities Brochure PDF. The topics addressed in these templates are Client Data Protection, Data Information Security, Application Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
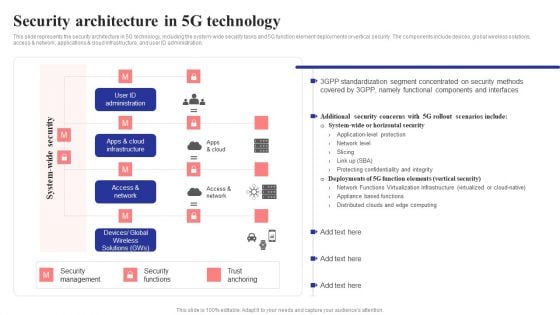
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
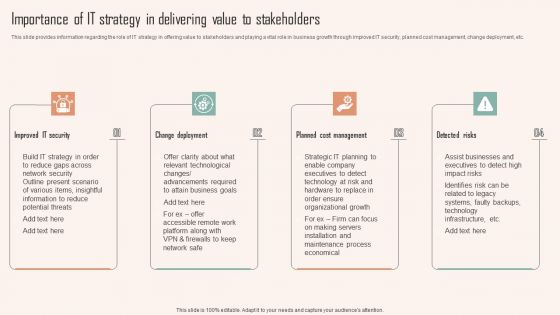
Importance Of IT Strategy In Delivering Value To Stakeholders Ppt PowerPoint Presentation File Infographic Template PDF
This slide provides information regarding the role of IT strategy in offering value to stakeholders and playing a vital role in business growth through improved IT security, planned cost management, change deployment, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Importance Of IT Strategy In Delivering Value To Stakeholders Ppt PowerPoint Presentation File Infographic Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Importance Of IT Strategy In Delivering Value To Stakeholders Ppt PowerPoint Presentation File Infographic Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
Bank Building With CCTV Cameras For Security Ppt PowerPoint Presentation Icon Background Images PDF
Showcasing this set of slides titled bank building with cctv cameras for security ppt powerpoint presentation icon background images pdf. The topics addressed in these templates are bank building with cctv cameras for security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Products And Services Offered Investor Oriented Urbanlogiq Fundraising Deck
This slide includes services offered by company to integrate and visualize data. It includes services for transportation data, economic development, and fire safety. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Investor Oriented Urbanlogiq Fundraising Deck to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide includes services offered by company to integrate and visualize data. It includes services for transportation data, economic development, and fire safety.
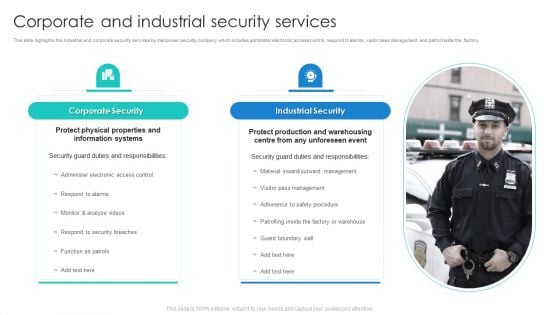
Manpower Corporate Security Business Profile Corporate And Industrial Security Services Designs PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Corporate And Industrial Security Services Designs PDF bundle. Topics like Corporate Security, Industrial Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Integration Of SWG Inside SASE Architecture Web Threat Protection System
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integration Of SWG Inside SASE Architecture Web Threat Protection System to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc.
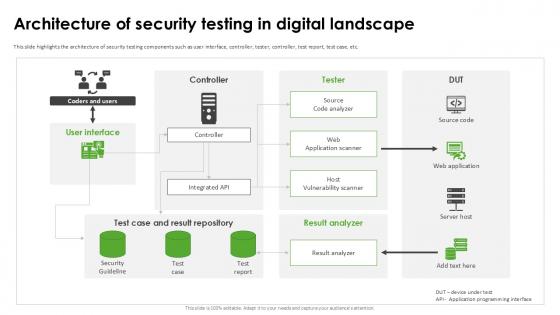
Architecture Of Security Harnessing The World Of Ethical Ppt Template
This slide highlights the architecture of security testing components such as user interface, controller, tester, controller, test report, test case, etc. There are so many reasons you need a Architecture Of Security Harnessing The World Of Ethical Ppt Template The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide highlights the architecture of security testing components such as user interface, controller, tester, controller, test report, test case, etc.

CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Get a simple yet stunning designed CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc.

Key Objectives Of Business Scalability And Improvement Process Inspiration Pdf
This slide shows main objectives of making business contingency plan in order to mitigate various risks associated with workplace. It include objectives such as ensuring safety, minimising financial loss and recovery plan, etc. Pitch your topic with ease and precision using this Key Objectives Of Business Scalability And Improvement Process Inspiration Pdf. This layout presents information on Minimise Financial Loss, Mitigation Plan, Provide Recovery Plan. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows main objectives of making business contingency plan in order to mitigate various risks associated with workplace. It include objectives such as ensuring safety, minimising financial loss and recovery plan, etc.
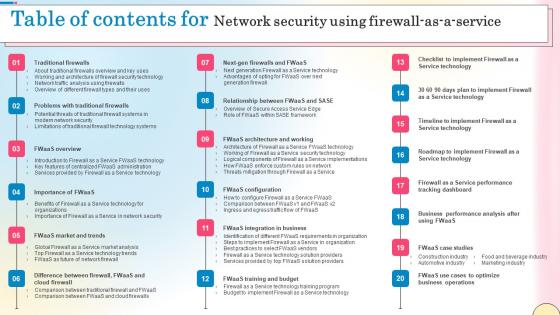
Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
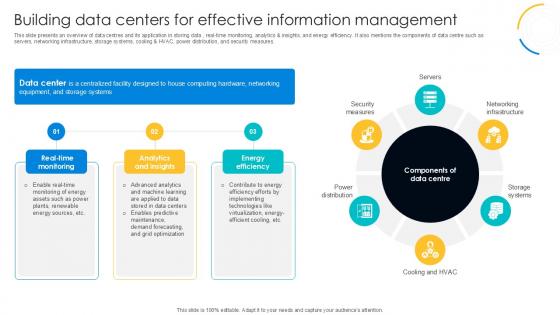
Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V
This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures. If you are looking for a format to display your unique thoughts, then the professionally designed Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures.

E Commerce Brand Building With Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V
This slide provides the various offerings for businesses using a digital wallet that helps in brand building and increasing audience reach. The different offerings are a wide range of payment options, customer rewards, enhanced security, etc. If you are looking for a format to display your unique thoughts, then the professionally designed E Commerce Brand Building With Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download E Commerce Brand Building With Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides the various offerings for businesses using a digital wallet that helps in brand building and increasing audience reach. The different offerings are a wide range of payment options, customer rewards, enhanced security, etc.
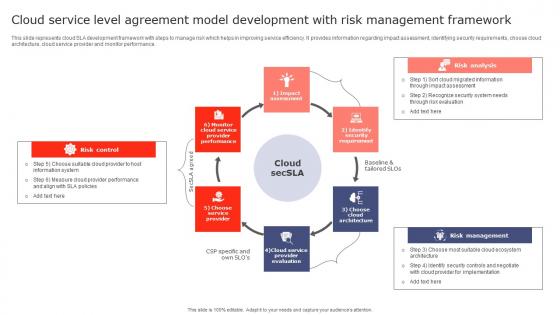
Cloud Service Level Agreement Model Development With Risk Management Framework Inspiration Pdf
This slide represents cloud SLA development framework with steps to manage risk which helps in improving service efficiency. It provides information regarding impact assessment, identifying security requirements, choose cloud architecture, cloud service provider and monitor performance. Showcasing this set of slides titled Cloud Service Level Agreement Model Development With Risk Management Framework Inspiration Pdf. The topics addressed in these templates are Risk Control, Risk Analysis, Risk Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents cloud SLA development framework with steps to manage risk which helps in improving service efficiency. It provides information regarding impact assessment, identifying security requirements, choose cloud architecture, cloud service provider and monitor performance.
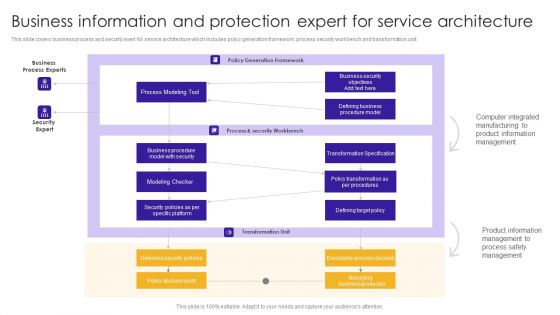
Business Information And Protection Expert For Service Architecture Demonstration PDF
This slide covers business process and security exert for service architecture which includes policy generation framework, process security workbench and transformation unit.Showcasing this set of slides titled Business Information And Protection Expert For Service Architecture Demonstration PDF. The topics addressed in these templates are Business Process, Computer Integrated, Product Information. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Private Security Service Provider Company Summary Report Clipart PDF
This slide provide information of firm providing security services to safeguards life of human beings who are facing threats. It includes elements such as about, category, services, company stats, packages, our service benefits. Pitch your topic with ease and precision using this Private Security Service Provider Company Summary Report Clipart PDF. This layout presents information on Provide World, Security Guard, Security Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
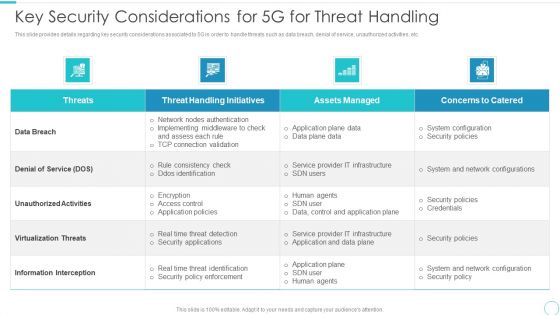
5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API.
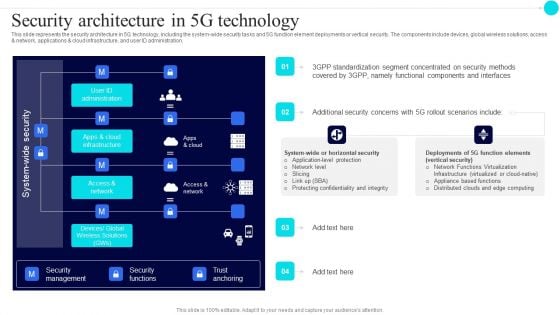
Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
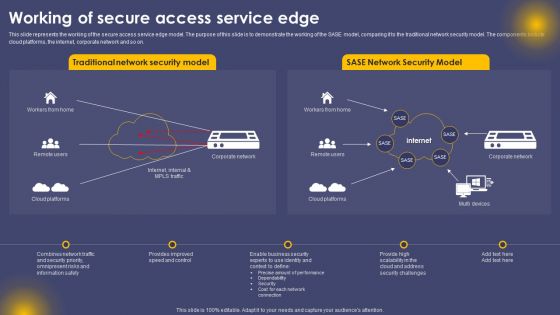
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
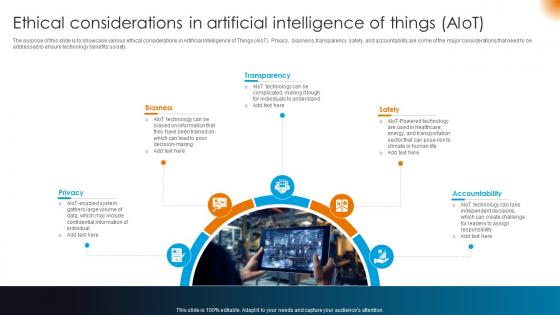
Integrating AI With IoT Ethical Considerations In Artificial Intelligence Of Things AIoT IoT SS V
The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Integrating AI With IoT Ethical Considerations In Artificial Intelligence Of Things AIoT IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Integrating AI With IoT Ethical Considerations In Artificial Intelligence Of Things AIoT IoT SS V effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society.

Real Time Assessment Of Security Threats Table Of Contents Real Time Assessment Of Security Threats Mockup PDF
Deliver an awe inspiring pitch with this creative real time assessment of security threats table of contents real time assessment of security threats mockup pdf bundle. Topics like company overview, challenges and solutions, services offered, siem hosting models, siem architecture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
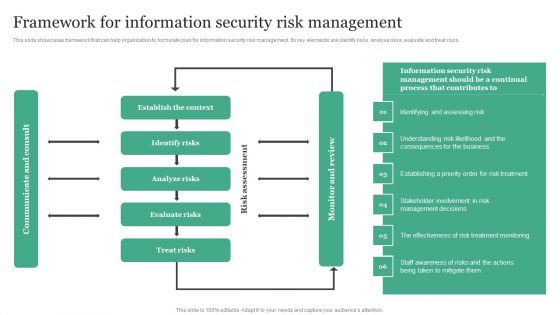
Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF can be your best option for delivering a presentation. Represent everything in detail using Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
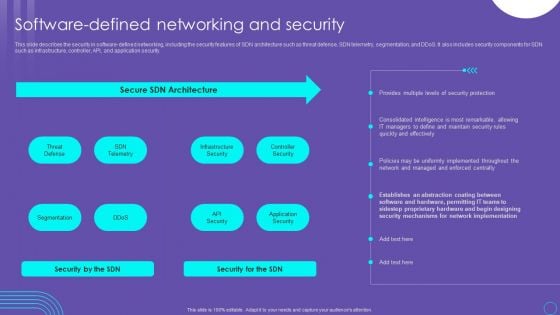
SDN Security Architecture Software Defined Networking And Security Guidelines PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate SDN Security Architecture Software Defined Networking And Security Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
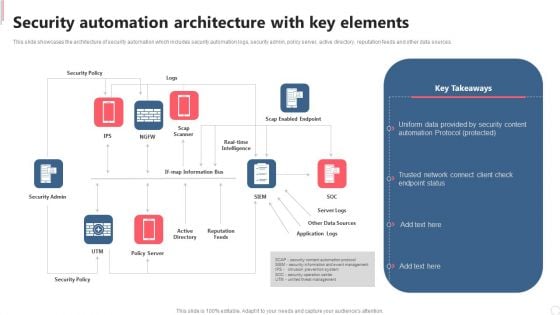
Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. This modern and well arranged Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template
This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor.
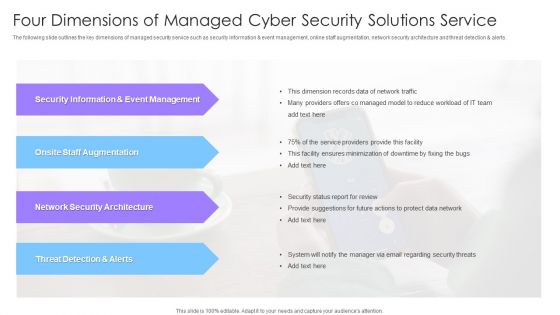
Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF
The following slide outlines the key dimensions of managed security service such as security information and event management, online staff augmentation, network security architecture and threat detection and alerts. Pitch your topic with ease and precision using this Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF. This layout presents information on Security Information, Event Management, Staff Augmentation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security Camera System Company Profile Company Overview With Key Services Icons PDF
This slide highlights security company background information which includes the company services offered, area served, total employees, headquarter, website and company value added services.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Company Overview With Key Services Icons PDF bundle. Topics like Monitory Services, Home Automation, Manage All Devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
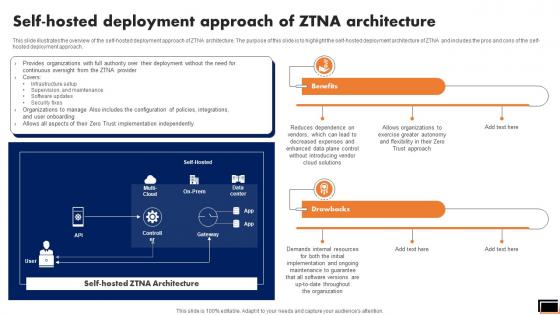
Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Do you know about Slidesgeeks Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.
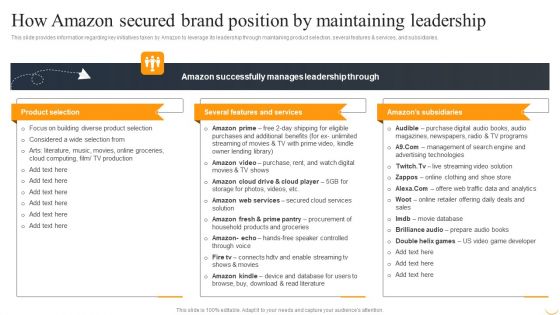
How Amazon Secured Brand Position By Maintaining Leadership Designs PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Get a simple yet stunning designed How Amazon Secured Brand Position By Maintaining Leadership Designs PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Amazon Secured Brand Position By Maintaining Leadership Designs PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
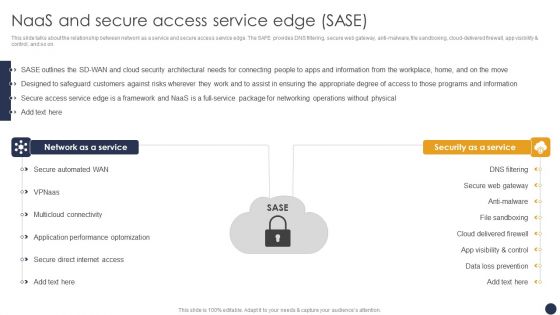
Integrating Naas Service Model Naas And Secure Access Service Edge Sase Ppt Model Picture PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. The Integrating Naas Service Model Naas And Secure Access Service Edge Sase Ppt Model Picture PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
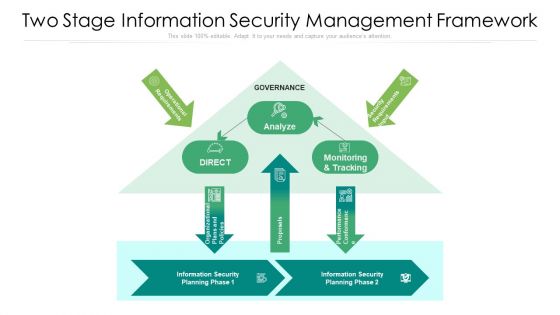
Two Stage Information Security Management Framework Ppt PowerPoint Presentation File Background Image PDF
Showcasing this set of slides titled two stage information security management framework ppt powerpoint presentation file background image pdf. The topics addressed in these templates are analyze, proposals, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icons Slide For Security Guard Services Proposal Ppt Summary Design Inspiration PDF
Introducing our well-designed icons slide for security guard services proposal ppt summary design inspiration pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
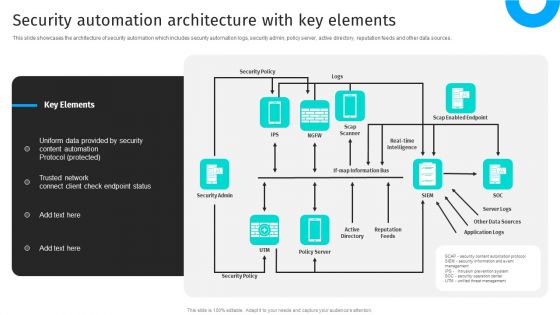
Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources.This modern and well-arranged Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Solution Offered Delivery Service Provider Business Model BMC SS V
This slide showcases solutions such as a delivery management system, live tracking, security and reliability, and responsive customer support. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Offered Delivery Service Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases solutions such as a delivery management system, live tracking, security and reliability, and responsive customer support.

Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF
Slidegeeks has constructed Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
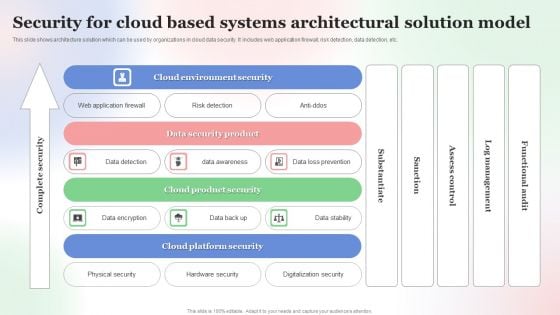
Security For Cloud Based Systems Architectural Solution Model Background PDF
This slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Showcasing this set of slides titled Security For Cloud Based Systems Architectural Solution Model Background PDF. The topics addressed in these templates are Security For Cloud Based, Systems Architectural Solution Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example
This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc. This modern and well-arranged Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc.
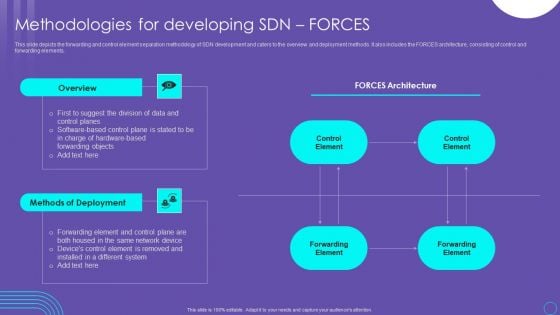
SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF
This slide depicts the forwarding and control element separation methodology of SDN development and caters to the overview and deployment methods. It also includes the FORCES architecture, consisting of control and forwarding elements. Take your projects to the next level with our ultimate collection of SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
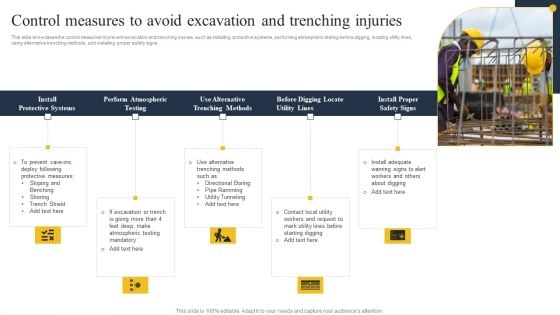
Security Control Techniques For Real Estate Project Control Measures To Avoid Excavation And Trenching Injuries Diagrams PDF
Welcome to our selection of the Security Control Techniques For Real Estate Project Control Measures To Avoid Excavation And Trenching Injuries Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
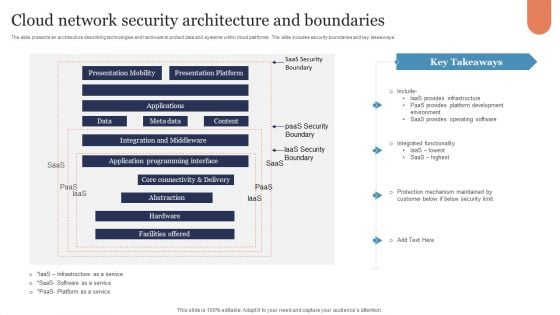
Cloud Network Security Architecture And Boundaries Graphics PDF
The slide presents an architecture describing technologies and hardware to protect data and systems within cloud platforms . The slide includes security boundaries and key takeaways. Showcasing this set of slides titled Cloud Network Security Architecture And Boundaries Graphics PDF. The topics addressed in these templates are Presentation Mobility, Presentation Platform, Applications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
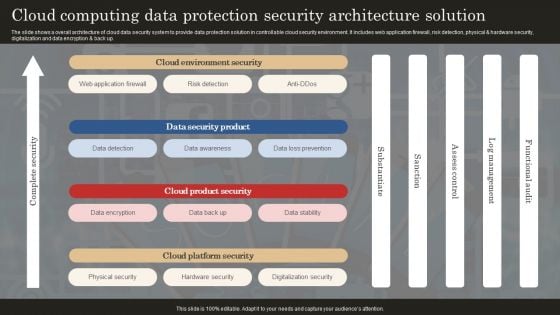
Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
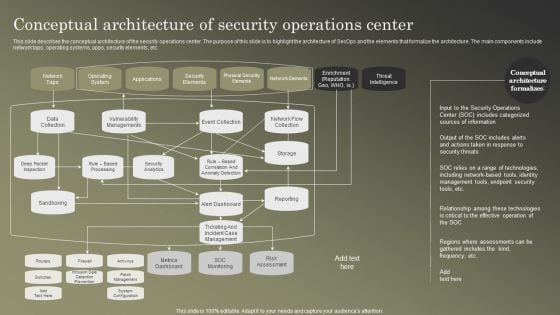
Cybersecurity Operations Cybersecops Conceptual Architecture Of Security Operations Summary PDF
This slide describes the conceptual architecture of the security operations center. The purpose of this slide is to highlight the architecture of SecOps and the elements that formalize the architecture. The main components include network taps, operating systems, apps, security elements, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cybersecurity Operations Cybersecops Conceptual Architecture Of Security Operations Summary PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
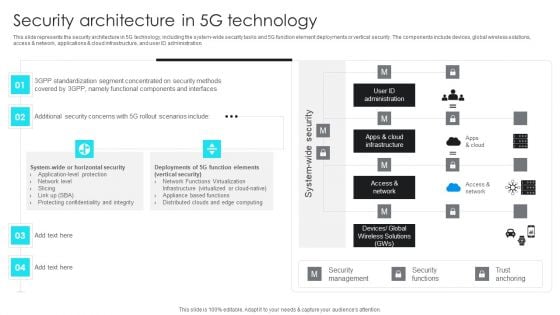
5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
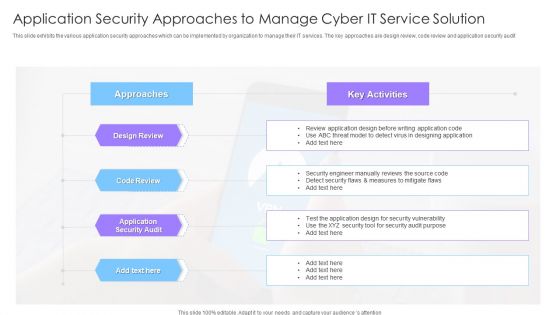
Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF
This slide exhibits the various application security approaches which can be implemented by organization to manage their IT services. The key approaches are design review, code review and application security audit Showcasing this set of slides titled Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF. The topics addressed in these templates are Design Review, Code Review, Approaches, Application Security Audit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
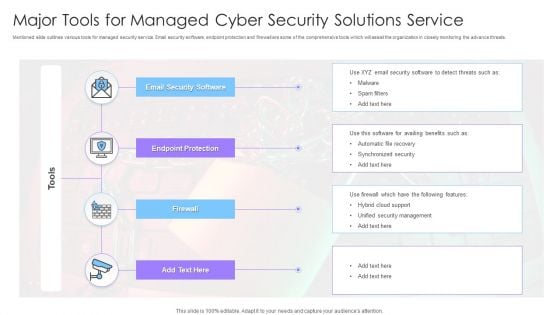
Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF
Mentioned slide outlines various tools for managed security service. Email security software, endpoint protection and firewall are some of the comprehensive tools which will assist the organization in closely monitoring the advance threats. Showcasing this set of slides titled Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF. The topics addressed in these templates are Endpoint Protection, Firewall, Email Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
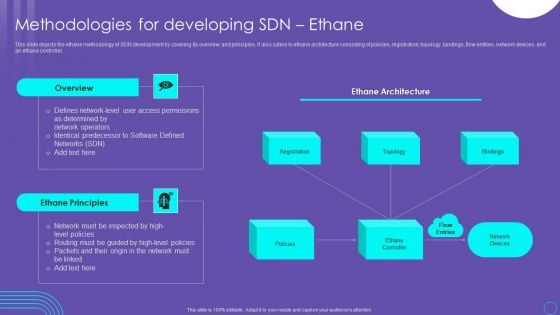
SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. This SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF
Slidegeeks has constructed Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
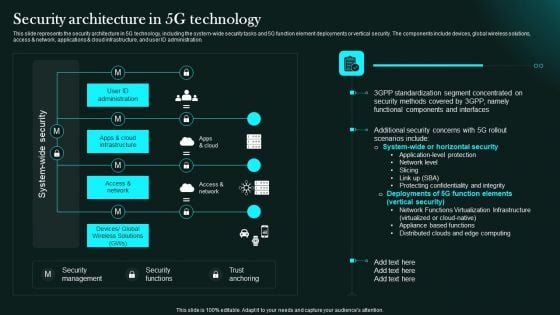
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Products And Services Offered Manufacturing Control Software Company Investor PPT Template
This slide caters to details related to a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Manufacturing Control Software Company Investor PPT Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide caters to details related to a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights.

Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost.
Icons Slide For Secure Computing Framework Designs Pdf
Download our innovative and attention grabbing Icons Slide For Secure Computing Framework Designs Pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Secure Computing Framework Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































