Construction Safety Plan
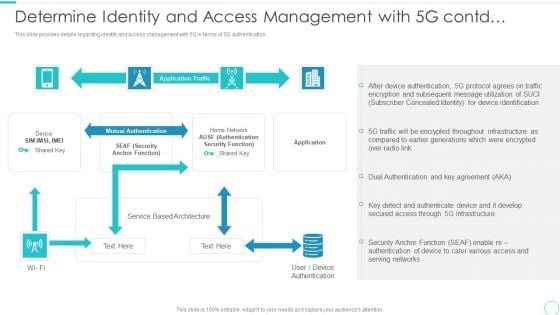
5G Evolution Architectural Technology Determine Identity And Access Management With 5G Contd Microsoft PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Determine Identity And Access Management With 5G Contd Microsoft PDF Use them to share invaluable insights on Uthentication, Security Function, Based Architecture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparison Analysis Between Security Operations And Devops Inspiration PDF
This slide summarizes the difference between SecOps and DevOps methodologies that increase the efficiency and scalability of complex operations. It includes parameters such as goal, processing strategy, change implementation, focus on, team involved, etc. Showcasing this set of slides titled Comparison Analysis Between Security Operations And Devops Inspiration PDF. The topics addressed in these templates are Implementation, Processing Strategy, Security Infrastructure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
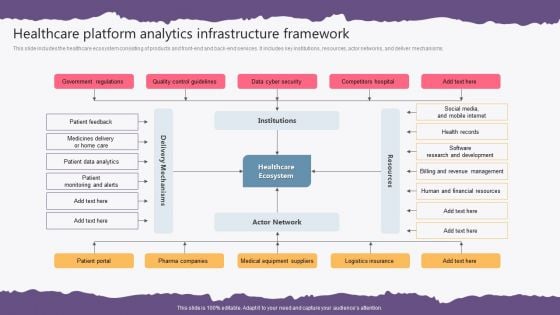
Healthcare Platform Analytics Infrastructure Framework Background PDF
This slide includes the healthcare ecosystem consisting of products and front-end and back-end services. It includes key institutions, resources, actor networks, and deliver mechanisms. Pitch your topic with ease and precision using this Healthcare Platform Analytics Infrastructure Framework Background PDF. This layout presents information on Government Regulations, Quality Control Guidelines, Data Cyber Security, Competitors Hospital. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
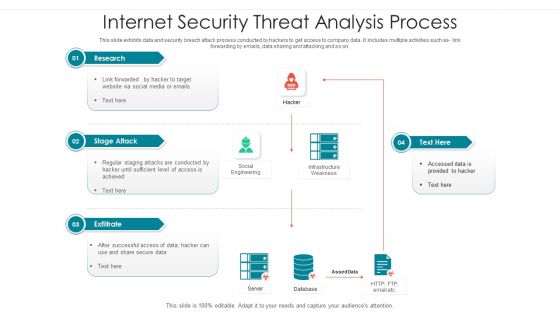
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
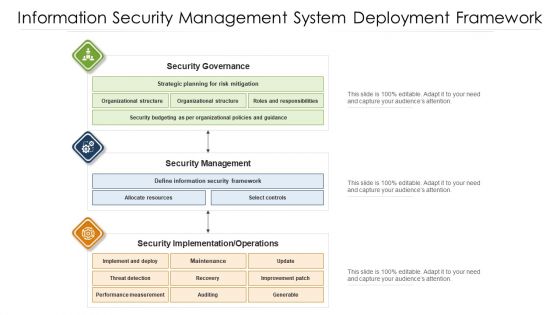
Information Security Management System Deployment Framework Ppt PowerPoint Presentation File Structure PDF
Showcasing this set of slides titled information security management system deployment framework ppt powerpoint presentation file structure pdf. The topics addressed in these templates are security management, security governance, security implementation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
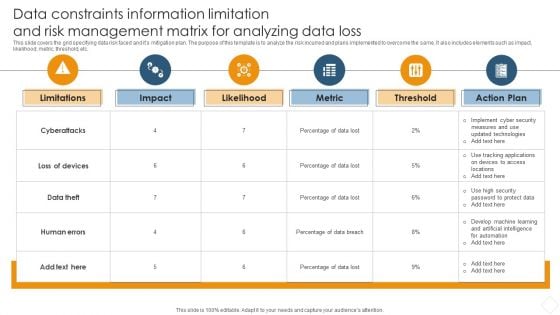
Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF
This slide covers the grid specifying data risk faced and its mitigation plan. The purpose of this template is to analyze the risk incurred and plans implemented to overcome the same. It also includes elements such as impact, likelihood, metric, threshold, etc.Showcasing this set of slides titled Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF. The topics addressed in these templates are Data Distribution, Secure Computation, Verifiable Computation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF
Pitch your topic with ease and precision using this Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF. This layout presents information on Pathway Change Framework, Food Security Sustainable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
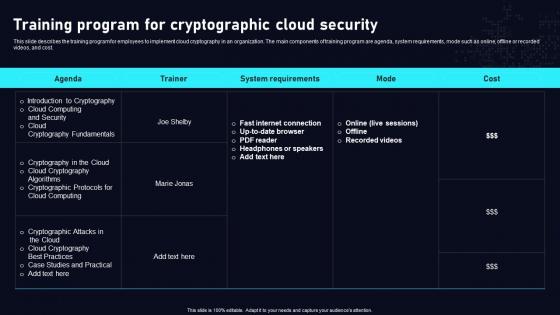
Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Security Guards Of Bank Standing Outside For Security Ppt PowerPoint Presentation File Visual Aids PDF
Showcasing this set of slides titled security guards of bank standing outside for security ppt powerpoint presentation file visual aids pdf. The topics addressed in these templates are security guards of bank standing outside for security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
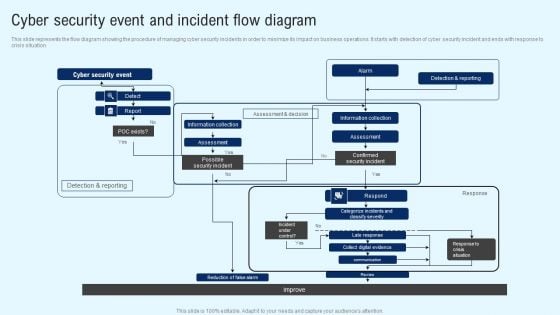
Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
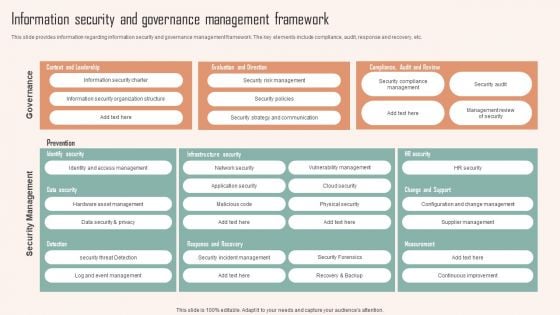
Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
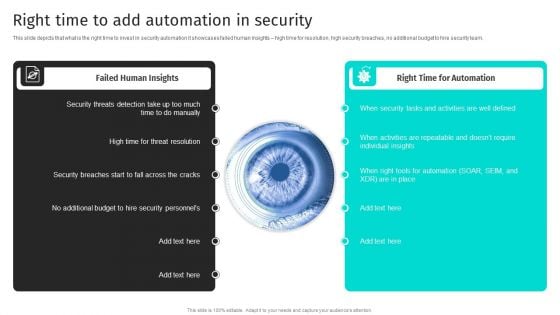
Security Automation To Analyze And Mitigate Cyberthreats Right Time To Add Automation In Security Inspiration PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Automation To Analyze And Mitigate Cyberthreats Right Time To Add Automation In Security Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
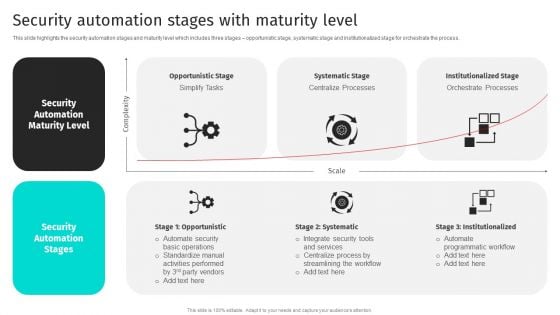
Security Automation To Analyze And Mitigate Cyberthreats Security Automation Stages Infographics PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process.This Security Automation To Analyze And Mitigate Cyberthreats Security Automation Stages Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Automation To Analyze And Mitigate Cyberthreats Security Automation Stages Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an awe inspiring pitch with this creative Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF bundle. Topics like Ransomware, Reduce Ransomware, Cybersecurity Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
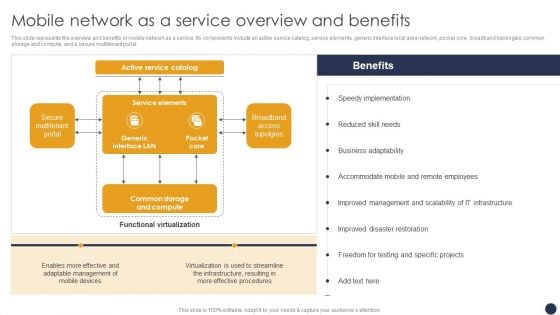
Integrating Naas Service Model Mobile Network As A Service Overview And Benefits Ppt Model Examples PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. Explore a selection of the finest Integrating Naas Service Model Mobile Network As A Service Overview And Benefits Ppt Model Examples PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Naas Service Model Mobile Network As A Service Overview And Benefits Ppt Model Examples PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
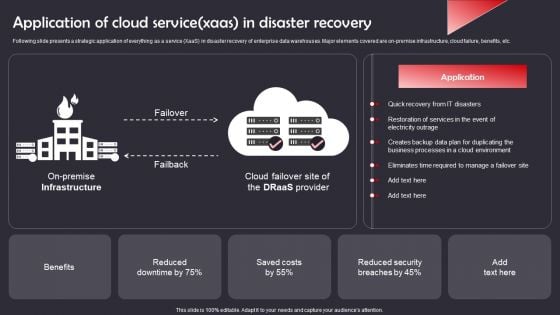
Application Of Cloud Service Xaas In Disaster Recovery Demonstration PDF
Following slide presents a strategic application of everything as a service XaaS in disaster recovery of enterprise data warehouses. Major elements covered are on-premise infrastructure, cloud failure, benefits, etc. Showcasing this set of slides titled Application Of Cloud Service Xaas In Disaster Recovery Demonstration PDF. The topics addressed in these templates are Benefits, Reduced Security Breaches, Quick Recovery IT Disasters . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
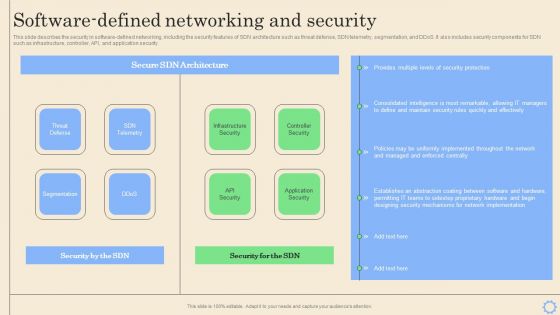
Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Want to ace your presentation in front of a live audience Our Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
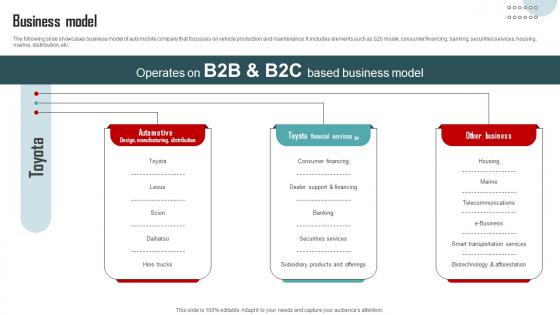
Business Model Vehicle Company Capital Funding Pitch Deck
The following slide showcases business model of automobile company that focusses on vehicle production and maintenance. It includes elements such as b2b model, consumer financing, banking, securities services, housing, marine, distribution, etc. Boost your pitch with our creative Business Model Vehicle Company Capital Funding Pitch Deck. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The following slide showcases business model of automobile company that focusses on vehicle production and maintenance. It includes elements such as b2b model, consumer financing, banking, securities services, housing, marine, distribution, etc.

Data Lake Architecture Future Of Data Analysis What Are The Challenges Of Cloud Data Lake Download PDF
This slide depicts the cloud data lake challenges such as data security, data swamp, on-premise data warehouse, and data governance. Deliver an awe inspiring pitch with this creative Data Lake Architecture Future Of Data Analysis What Are The Challenges Of Cloud Data Lake Download PDF bundle. Topics like Sensitive Information, Data Warehousing, Unstructured Data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf
This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc.

A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF
Showcasing this set of slides titled Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF. The topics addressed in these templates are Data Warehouse, Security Mechanism, Procedure Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
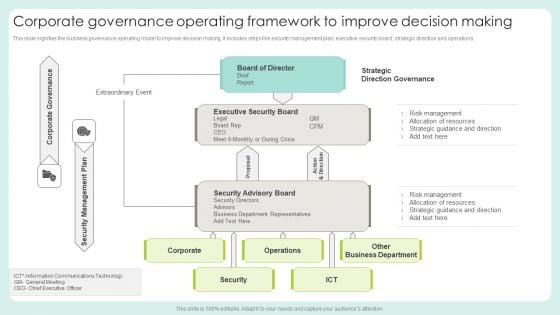
Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
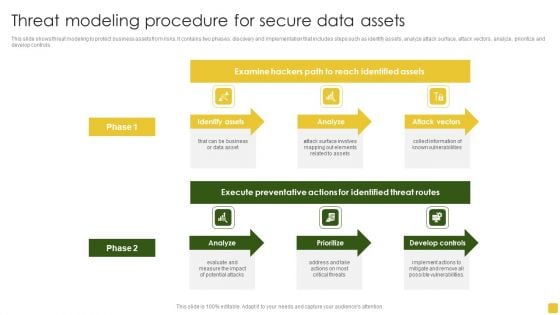
Threat Modeling Procedure For Secure Data Assets Formats PDF
This slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Pitch your topic with ease and precision using this Threat Modeling Procedure For Secure Data Assets Formats PDF. This layout presents information on Execute Preventative, Identified Threat, Develop Controls. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
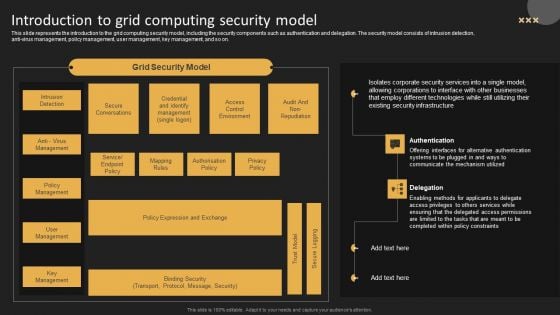
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Table Of Contents KYC Transaction Monitoring System For Business Security Designs PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents KYC Transaction Monitoring System For Business Security Designs PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents KYC Transaction Monitoring System For Business Security Designs PDF today and make your presentation stand out from the rest.
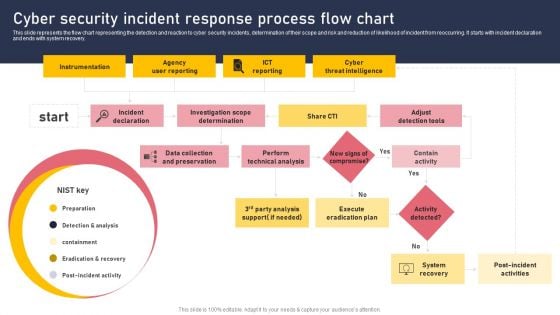
Cyber Security Incident Response Process Flow Chart Download PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. This Cyber Security Incident Response Process Flow Chart Download PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
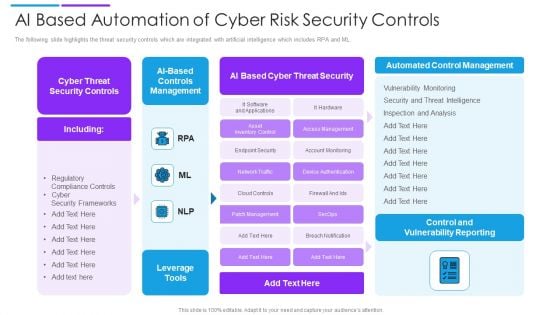
AI Based Automation Of Cyber Risk Security Controls Summary PDF
The following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Showcasing this set of slides titled ai based automation of cyber risk security controls summary pdf. The topics addressed in these templates are controls management, cyber threat security controls, ai based cyber threat security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
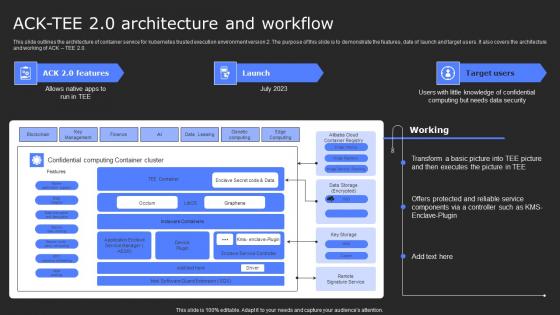
Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
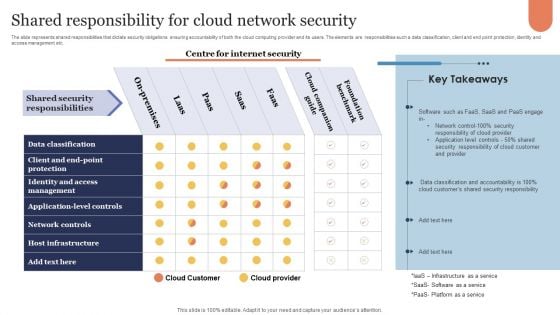
Shared Responsibility For Cloud Network Security Microsoft PDF
The slide represents shared responsibilities that dictate security obligations ensuring accountability of both the cloud computing provider and its users. The elements are responsibilities such a data classification, client and end point protection, identity and access management etc. Showcasing this set of slides titled Shared Responsibility For Cloud Network Security Microsoft PDF. The topics addressed in these templates are Cloud Companion Guide, Foundation Benchmark, On Premises. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Certification Career Roadmap Icon Pictures PDF
Showcasing this set of slides titled Cyber Security Certification Career Roadmap Icon Pictures PDF. The topics addressed in these templates are Career Roadmap Icon, Cyber Security Certification. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Risk Security Impact Mitigation Icon With Shield Themes PDF
Pitch your topic with ease and precision using this Risk Security Impact Mitigation Icon With Shield Themes PDF. This layout presents information on Icon With Shield, Risk Security Impact Mitigation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Cyber Security Compliance Traceability Matrix Icon Formats PDF
Showcasing this set of slides titled Cyber Security Compliance Traceability Matrix Icon Formats PDF. The topics addressed in these templates are Cyber Security, Compliance, Traceability Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Big Data Security Analytics Icon With Shield Symbol Background PDF
Pitch your topic with ease and precision using this Big Data Security Analytics Icon With Shield Symbol Background PDF. This layout presents information on Big Data Security Analytics, Icon With Shield Symbol. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
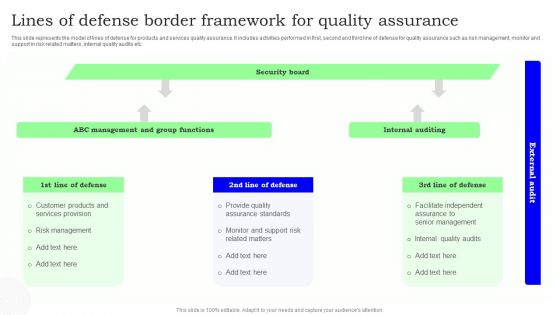
Lines Of Defense Border Framework For Quality Assurance Topics PDF
This slide represents the model of lines of defense for products and services quality assurance. It includes activities performed in first, second and third line of defense for quality assurance such as risk management, monitor and support in risk related matters, internal quality audits etc. Showcasing this set of slides titled Lines Of Defense Border Framework For Quality Assurance Topics PDF. The topics addressed in these templates are Security Board, Internal Auditing, Assurance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
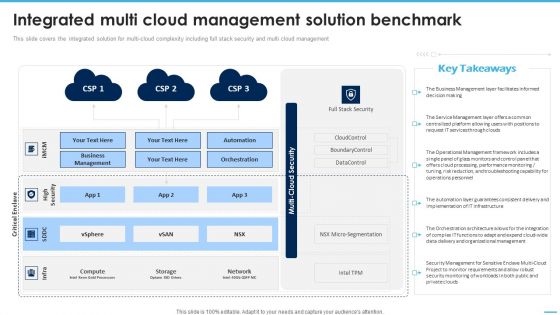
Integrated Multi Cloud Management Solution Benchmark Managing Complexity Of Multiple Cloud Platforms Rules PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Integrated Multi Cloud Management Solution Benchmark Managing Complexity Of Multiple Cloud Platforms Rules PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
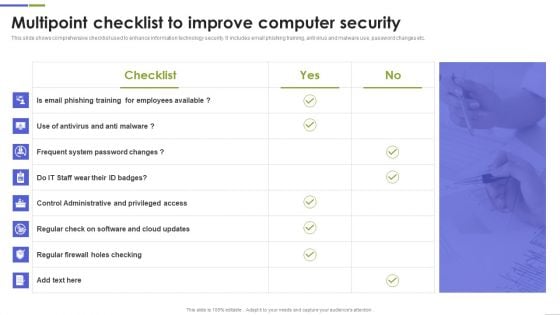
Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
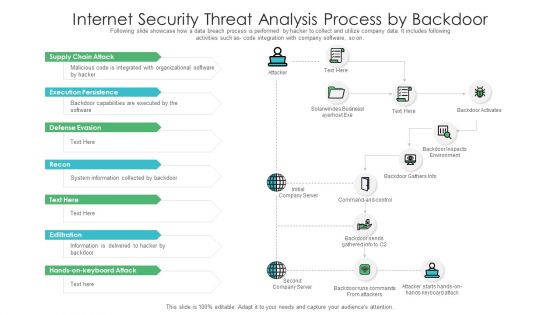
Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

IT Security Risk Management Process For Organization Template PDF
This slide displays flow diagram to illustrate cybersecurity risk management process to ensure continuous monitoring. It includes components such as threats, vulnerabilities, impacts, intelligence, etc. Showcasing this set of slides titled IT Security Risk Management Process For Organization Template PDF. The topics addressed in these templates are Organization, Cyber Intelligence, Continuous Monitoring, Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

New Product Launch Event Management Activities Existing Products And Service Offerings Of Firm Introduction PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Make sure to capture your audiences attention in your business displays with our gratis customizable New Product Launch Event Management Activities Existing Products And Service Offerings Of Firm Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
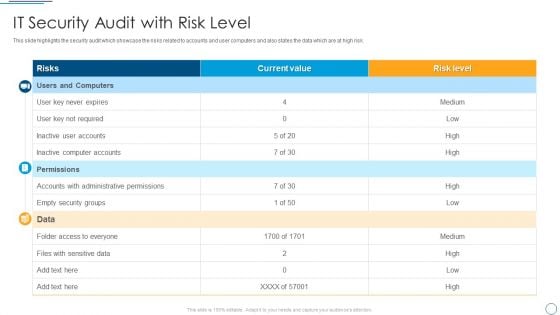
Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk.Deliver an awe inspiring pitch with this creative Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF bundle. Topics like Administrative Permissions, Empty Security, Computer Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
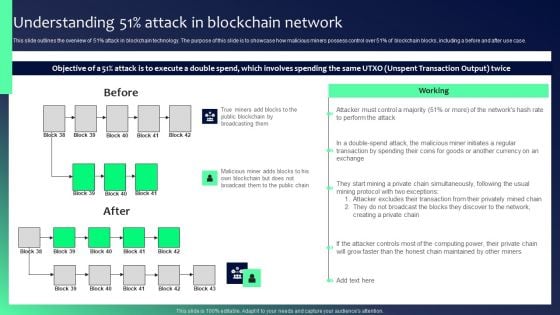
Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF
This slide outlines the overview of 51 percent attack in blockchain technology. The purpose of this slide is to showcase how malicious miners possess control over 51 percent of blockchain blocks, including a before and after use case. Retrieve professionally designed Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Query Slide Diagram For Designing A Secure Network Perimeter Diagrams PDF
Showcasing this set of slides titled query slide diagram for designing a secure network perimeter diagrams pdf. The topics addressed in these templates are query slide diagram for designing a secure network perimeter. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
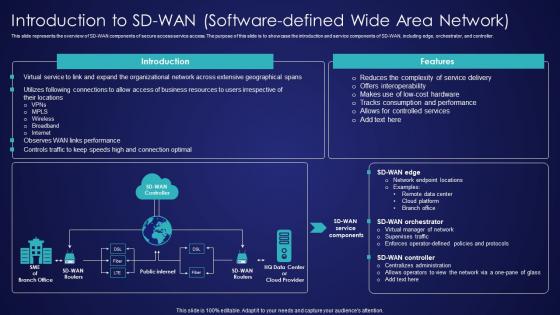
Introduction To SD Wan Software Defined Wide Area Network Wide Area Network Services Background Pdf
This slide represents the overview of SD-WAN components of secure access service access. The purpose of this slide is to showcase the introduction and service components of SD-WAN, including edge, orchestrator, and controller. If you are looking for a format to display your unique thoughts, then the professionally designed Introduction To SD Wan Software Defined Wide Area Network Wide Area Network Services Background Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Introduction To SD Wan Software Defined Wide Area Network Wide Area Network Services Background Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of SD-WAN components of secure access service access. The purpose of this slide is to showcase the introduction and service components of SD-WAN, including edge, orchestrator, and controller.
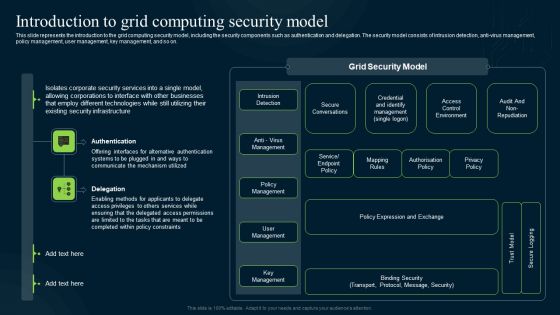
Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. This modern and well-arranged Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

A LA Carte Business Strategy Managed Services Industry Trends Pictures PDF
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. Create an editable A LA Carte Business Strategy Managed Services Industry Trends Pictures PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. A LA Carte Business Strategy Managed Services Industry Trends Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
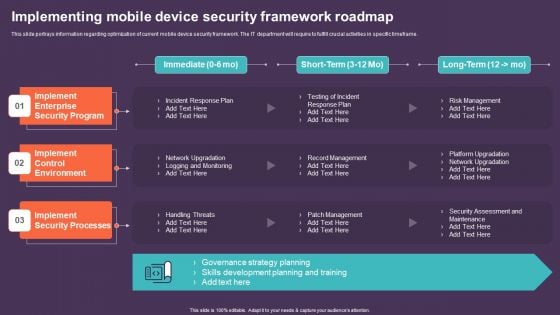
Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. The Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
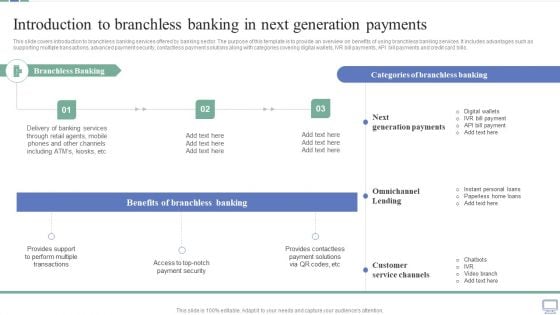
Omnichannel Banking Services Platform Introduction To Branchless Banking In Next Generation Payments Demonstration PDF
This slide covers introduction to branchless banking services offered by banking sector. The purpose of this template is to provide an overview on benefits of using branchless banking services. It includes advantages such as supporting multiple transactions, advanced payment security, contactless payment solutions along with categories covering digital wallets, IVR bill payments, API bill payments and credit card bills. Take your projects to the next level with our ultimate collection of Omnichannel Banking Services Platform Introduction To Branchless Banking In Next Generation Payments Demonstration PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
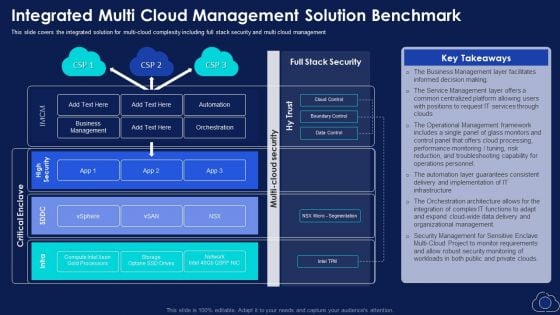
Integrated Multi Cloud Management Solution Benchmark Microsoft PDF
This slide covers the integrated solution for multi cloud complexity including full stack security and multi cloud management. Deliver and pitch your topic in the best possible manner with this Integrated Multi Cloud Management Solution Benchmark Microsoft PDF. Use them to share invaluable insights on Service Management, Business Management, Performance Monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
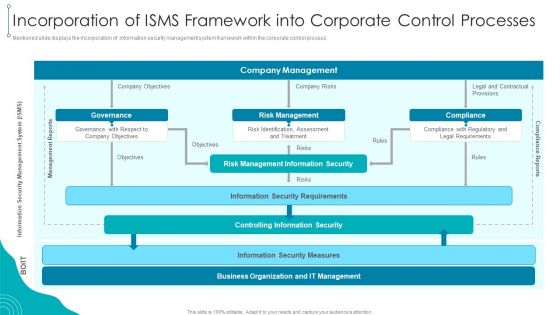
Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF. Use them to share invaluable insights on Management Information, Security Requirements, Information Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
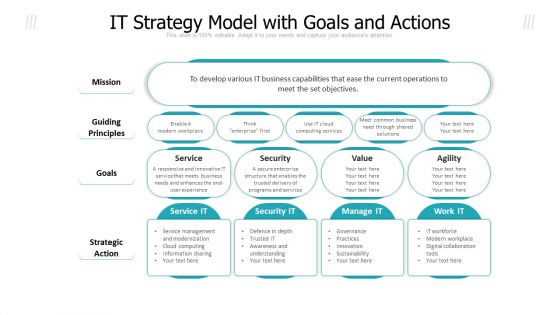
IT Strategy Model With Goals And Actions Ppt PowerPoint Presentation File Layout Ideas PDF
Pitch your topic with ease and precision using this it strategy model with goals and actions ppt powerpoint presentation file layout ideas pdf. This layout presents information on security, service, value. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Advantages Of Artificial Intelligence In Mobile App Development Infographics PDF
This slide signifies the benefits of artificial intelligence in mobile app development. It covers information about powerful app authentication, improved security, recommendation services and AI powered chatbot Pitch your topic with ease and precision using this Advantages Of Artificial Intelligence In Mobile App Development Infographics PDF. This layout presents information on Powerful App Authentication, Improved Security, Recommendation Services. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Vector Showing Technology Issues Of Information Security Ppt PowerPoint Presentation File Sample PDF
Showcasing this set of slides titled vector showing technology issues of information security ppt powerpoint presentation file sample pdf. The topics addressed in these templates are vector showing technology issues of information security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Bank Vault To Secure Valuables And Money Ppt PowerPoint Presentation Gallery Infographic Template PDF
Showcasing this set of slides titled bank vault to secure valuables and money ppt powerpoint presentation gallery infographic template pdf. The topics addressed in these templates are bank vault to secure valuables and money. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Blockchain In Financial Sector For Security Ppt PowerPoint Presentation File Slide Portrait PDF
Showcasing this set of slides titled blockchain in financial sector for security ppt powerpoint presentation file slide portrait pdf. The topics addressed in these templates are security, digital transactions, authentication of users. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Vector Showing IT Security Under Threat Ppt PowerPoint Presentation Gallery Deck PDF
Showcasing this set of slides titled vector showing it security under threat ppt powerpoint presentation gallery deck pdf. The topics addressed in these templates are vector showing it security under threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































