Cyber Attack

Visionary Guide To Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V
This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Visionary Guide To Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems.

Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V
The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future.

Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V
The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as. The Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as.
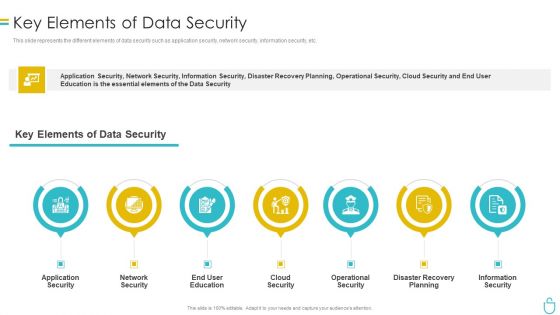
Information Security Key Elements Of Data Security Ppt Pictures Show PDF
This slide represents the different elements of data security such as application security, network security, information security, etc. Presenting information security key elements of data security ppt pictures show pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like network security, application security, cloud security, operational security, information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
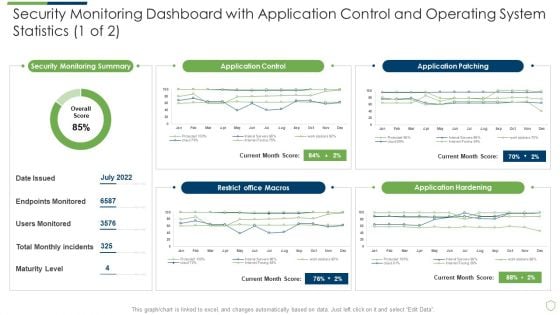
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Application Slides PDF
Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with application slides pdf. Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Are you searching for a IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF from Slidegeeks today.
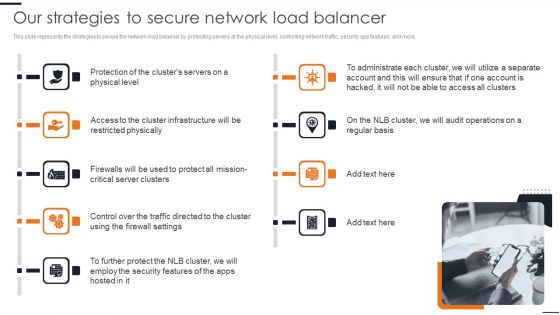
Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. This modern and well arranged Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
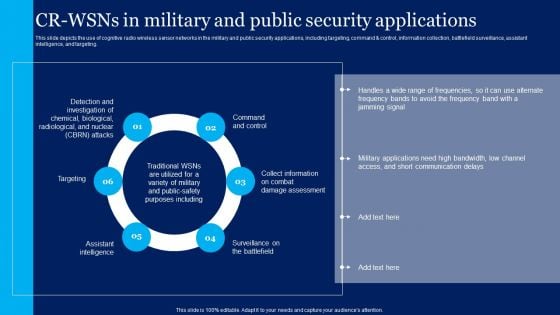
Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
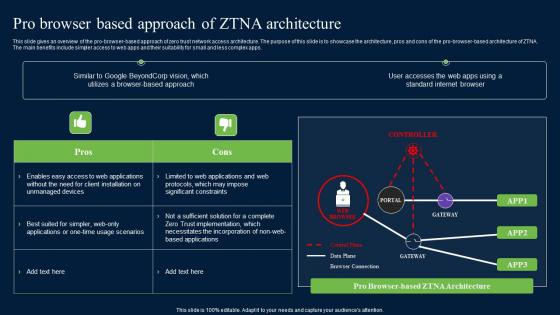
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf
The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
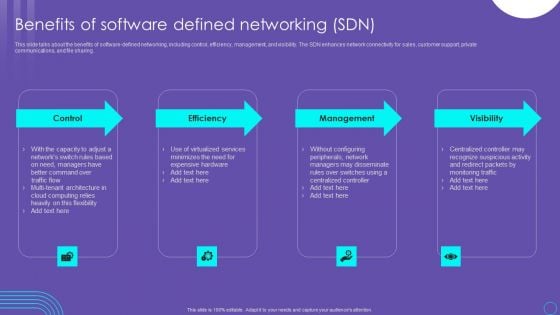
SDN Security Architecture Benefits Of Software Defined Networking SDN Information PDF
This slide talks about the benefits of software defined networking, including control, efficiency, management, and visibility. The SDN enhances network connectivity for sales, customer support, private communications, and file sharing. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward SDN Security Architecture Benefits Of Software Defined Networking SDN Information PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal SDN Security Architecture Benefits Of Software Defined Networking SDN Information PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Role IT Team Digital Transformation It Professional Upskilling For Cybersecurity Introduction PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a role it team digital transformation it professional upskilling for cybersecurity introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
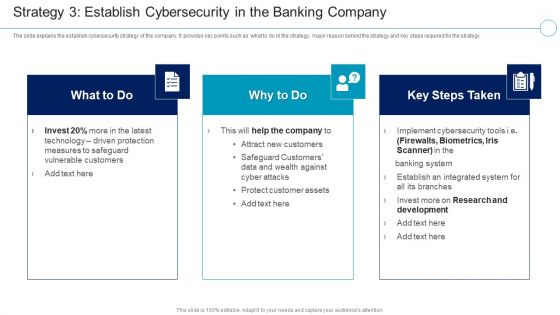
Financial Services Enterprise Transformation Strategy 3 Cybersecurity In The Banking Company Mockup PDF
The slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy This is a Financial Services Enterprise Transformation Strategy 3 Cybersecurity In The Banking Company Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Research And Development, Measures To Safeguard, Technology Driven Protection You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF
This slide represents risk assessment software dashboard for cybersecurity. It includes risk percentage, number of risks, risk analysis progress, risk response progress, risk rating etc. Showcasing this set of slides titled Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF. The topics addressed in these templates are Risk Rating Breakdown, Action Plan Breakdown, Top 5 Entities Prone To Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Digital Technology Adoption In Banking Industry Case Competition Strategy 3 Establish Cybersecurity Guidelines PDF
The slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy Presenting Digital Technology Adoption In Banking Industry Case Competition Strategy 3 Establish Cybersecurity Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Technology Driven Protection Measures, Safeguard Vulnerable Customers, Establish An Integrated System In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
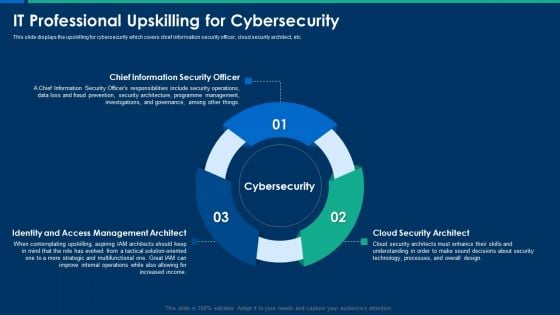
CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Management Architect, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF. Use them to share invaluable insights on Goal, Security System, Reduce and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF. Use them to share invaluable insights on Reduce Ransomware, Reduce Distributed, Approaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
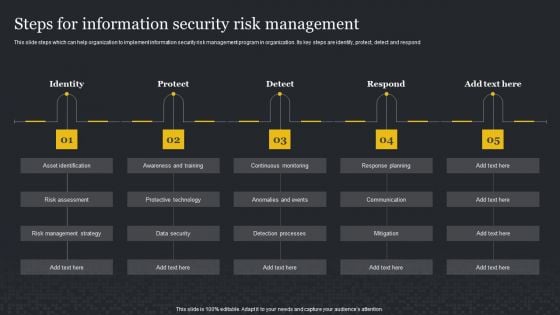
Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Create an editable Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF
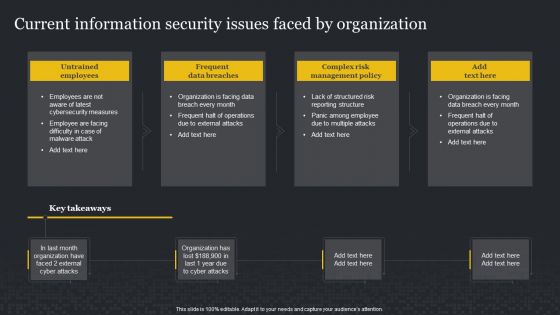
Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF
This Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF
Are you searching for a Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF from Slidegeeks today.

Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cybersecurity Guidelines IT Employee Awareness Training Budget For FY2022 Structure PDF
This slide describes the employee awareness training budget for FY2022. It includes provider, training date, duration, budget, qualification, capability level, and frequency. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Guidelines IT Employee Awareness Training Budget For FY2022 Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Guidelines IT Employee Awareness Training Budget For FY2022 Structure PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cybersecurity Guidelines IT Software Usage Policy Objective And General Guidelines Download PDF
This slide depicts the software usage policy, including its objective, general guidelines, and compliance. This policy covers the instructions regarding both paid and free software. Get a simple yet stunning designed Cybersecurity Guidelines IT Software Usage Policy Objective And General Guidelines Download PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Cybersecurity Guidelines IT Software Usage Policy Objective And General Guidelines Download PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Cybersecurity Guidelines IT About Us Ppt PowerPoint Presentation Gallery Clipart PDF
Find highly impressive Cybersecurity Guidelines IT About Us Ppt PowerPoint Presentation Gallery Clipart PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cybersecurity Guidelines IT About Us Ppt PowerPoint Presentation Gallery Clipart PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Cybersecurity Guidelines IT Idea Generation Ppt PowerPoint Presentation File Designs PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Guidelines IT Idea Generation Ppt PowerPoint Presentation File Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Guidelines IT Idea Generation Ppt PowerPoint Presentation File Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Guidelines IT Our Team Ppt PowerPoint Presentation Gallery Brochure PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Guidelines IT Our Team Ppt PowerPoint Presentation Gallery Brochure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Guidelines IT Our Team Ppt PowerPoint Presentation Gallery Brochure PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Cybersecurity Guidelines IT Thank You Ppt PowerPoint Presentation Gallery Tips PDF
This Cybersecurity Guidelines IT Thank You Ppt PowerPoint Presentation Gallery Tips PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cybersecurity Guidelines IT Thank You Ppt PowerPoint Presentation Gallery Tips PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Ppt PowerPoint Presentation File Icon PDF
This slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Take your projects to the next level with our ultimate collection of Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Ppt PowerPoint Presentation File Icon PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Slides PDF
This slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. The Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Slides PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
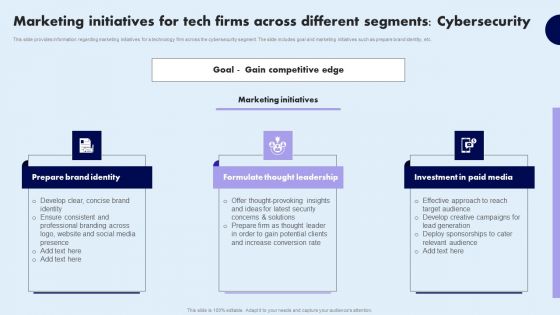
Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Pictures PDF
This slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Find a pre-designed and impeccable Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Pictures PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
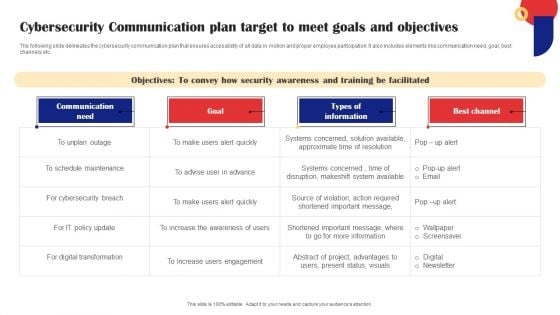
Cybersecurity Communication Plan Target To Meet Goals And Objectives Information PDF
The following slide delineates the cybersecurity communication plan that ensures accessibility of all data in motion and proper employee participation. It also includes elements like communication need, goal, best channels etc. Pitch your topic with ease and precision using this Cybersecurity Communication Plan Target To Meet Goals And Objectives Information PDF. This layout presents information on Communication Need, Goal, Digital Transformation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
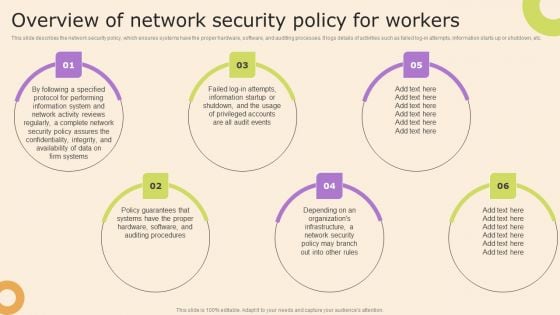
Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF from Slidegeeks and deliver a wonderful presentation.
Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
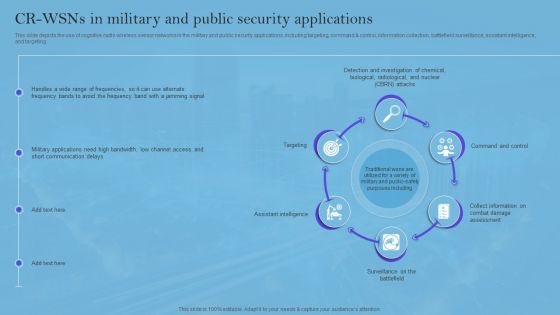
Smart Wireless Sensor Networks CR Wsns In Military And Public Security Applications Elements PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Want to ace your presentation in front of a live audience Our Smart Wireless Sensor Networks CR Wsns In Military And Public Security Applications Elements PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
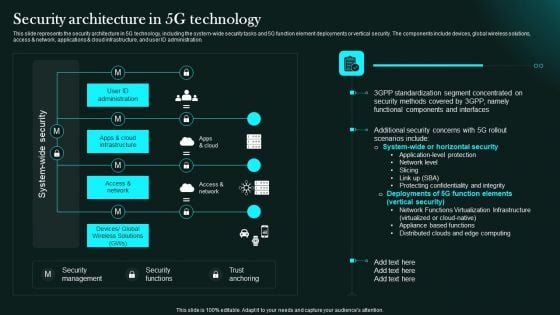
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

5G Network Applications And Features Security In 5G Technology Architecture Download PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Find highly impressive 5G Network Applications And Features Security In 5G Technology Architecture Download PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download 5G Network Applications And Features Security In 5G Technology Architecture Download PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Cloud Network Security Dimensions And Sections Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud network security dimensions and sections ppt powerpoint presentation icon background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, service, threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
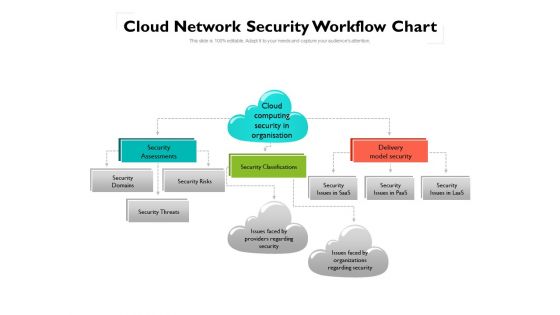
Cloud Network Security Workflow Chart Ppt PowerPoint Presentation Gallery Ideas PDF
This is a cloud network security workflow chart ppt powerpoint presentation gallery ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, organizations, domains. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organizational Network Staff Learning Security Awareness Tracking Kpis Event Ppt Slides Clipart Images PDF
Presenting organizational network staff learning security awareness tracking kpis event ppt slides clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like compliance, security culture, incident reduction. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Security Awareness Staff Learning Organization Impact Metrics Behaviours Portrait PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning organization impact metrics behaviours portrait pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
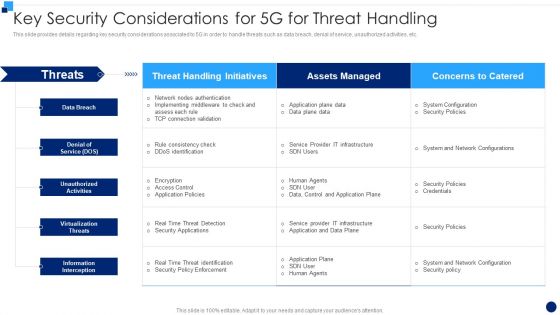
Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF bundle. Topics like Information Interception, Virtualization Threats, Denial Of Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
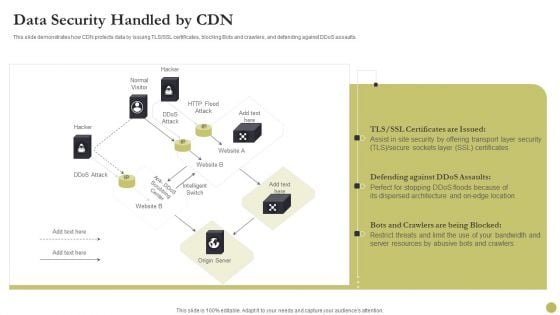
Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver and pitch your topic in the best possible manner with this Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF. Use them to share invaluable insights on Security, Location, Server Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF
The following slide showcases comparison of email security gateways along with features rating and price. Main gateways included are mimecast, ironscales, avanan and trustifi. Showcasing this set of slides titled Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF. The topics addressed in these templates are Gateway Device Establishment, Establish Strong, Identity For Gateway. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
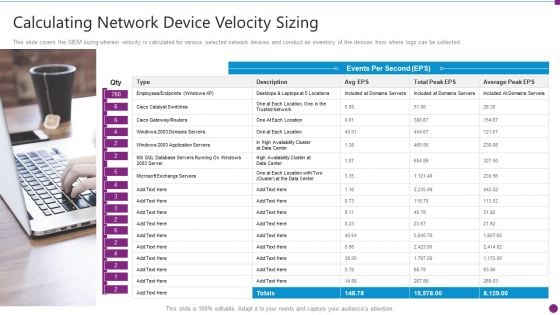
Security Information And Event Management Strategies For Financial Audit And Compliance Calculating Network Device Inspiration PDF
This slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Presenting security information and event management strategies for financial audit and compliance calculating network device inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like calculating network device velocity sizing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.
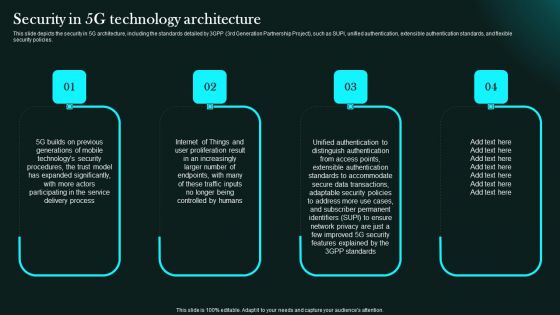
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Computer Security Incident Handling Agenda For Cybersecurity Incident Management Template PDF
Presenting this set of slides with name computer security incident handling agenda for cybersecurity incident management template pdf. The topics discussed in these slides are department, priorities, maximum allowable downtime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Analyzing IT Department On Nist Cybersecurity Framework Introduction PDF
Presenting this set of slides with name computer security incident handling analyzing it department on nist cybersecurity framework introduction pdf. The topics discussed in these slides are identify, detect, protect, respond, recover. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
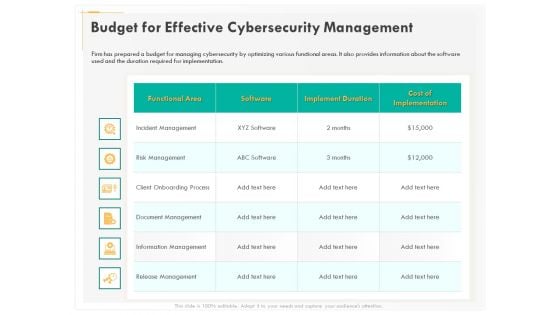
Computer Security Incident Handling Budget For Effective Cybersecurity Management Clipart PDF
Presenting this set of slides with name computer security incident handling budget for effective cybersecurity management clipart pdf. The topics discussed in these slides are functional area, software, implement duration, cost of implementation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Contingency Plan Business Impact Analysis Rules PDF
Presenting this set of slides with name computer security incident handling cybersecurity contingency plan business impact analysis rules pdf. The topics discussed in these slides are business processes, vital resources, impact, recovery priorities, max allowable outage time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
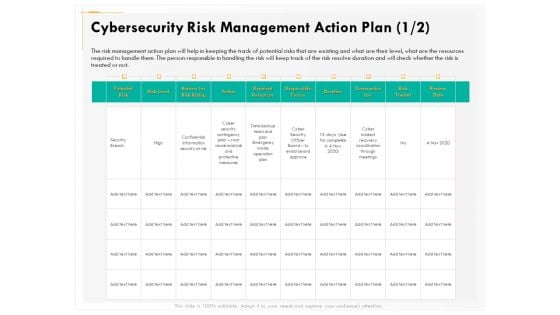
Computer Security Incident Handling Cybersecurity Risk Management Action Plan Diagrams PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management action plan diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason for risk rating, action, required resources, responsible person, duration, communication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
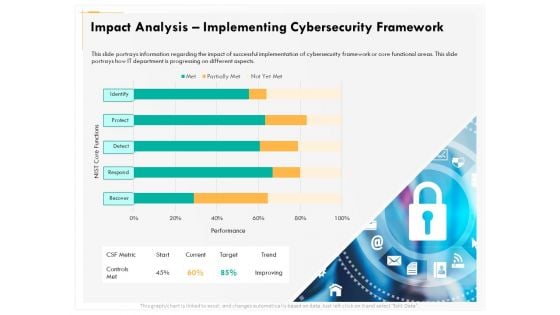
Computer Security Incident Handling Impact Analysis Implementing Cybersecurity Framework Designs PDF
Presenting this set of slides with name computer security incident handling impact analysis implementing cybersecurity framework designs pdf. The topics discussed in these slides are recover, detect, respond, protect, identify. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
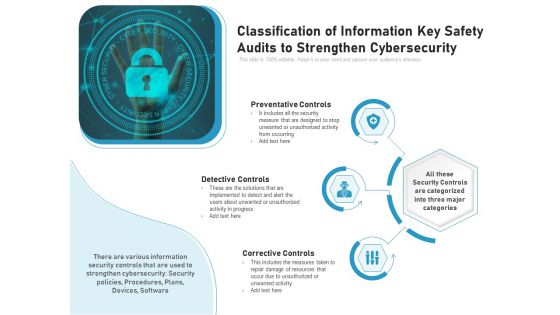
Classification Of Information Key Safety Audits To Strengthen Cybersecurity Ppt PowerPoint Presentation File Formats PDF
Presenting classification of information key safety audits to strengthen cybersecurity ppt powerpoint presentation file formats pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including preventative controls, detective controls, corrective controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Impact On Revenue Due To Increasing Cybersecurity Cases Ppt Icon Design Templates PDF
Deliver and pitch your topic in the best possible manner with this impact on revenue due to increasing cybersecurity cases ppt icon design templates pdf. Use them to share invaluable insights on revenue, customer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Effective Cybersecurity Training To Raise Awareness Icons Slide Ppt Infographics Example File PDF
Presenting our innovatively structured effective cybersecurity training to raise awareness icons slide ppt infographics example file pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.

Agenda For Approaches To Implement Advanced Cybersecurity Monitoring Plan Brochure PDF
This is a agenda for approaches to implement advanced cybersecurity monitoring plan brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Approaches To Implement Advanced Cybersecurity Monitoring Plan Linear Process Information PDF
Presenting approaches to implement advanced cybersecurity monitoring plan linear process information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like linear process. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
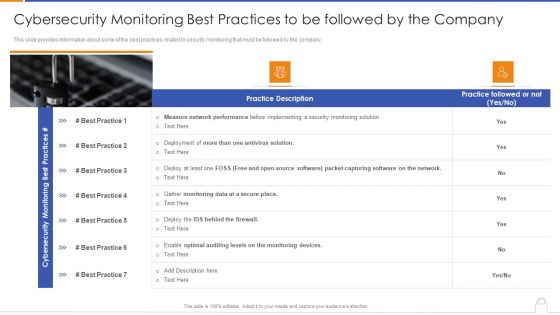
Cybersecurity Monitoring Best Practices To Be Followed By The Company Demonstration PDF
Deliver an awe inspiring pitch with this creative cybersecurity monitoring best practices to be followed by the company demonstration pdf bundle. Topics like gather monitoring, enable optimal auditing, deployment of more than can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































