Data Encryption

Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample
This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample today and make your presentation stand out from the rest This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
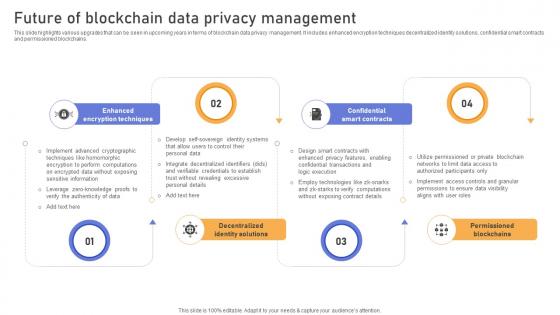
A87 Comprehensive Look At Blockchain Technologys Future Of Blockchain Data Privacy BCT SS V
This slide highlights various upgrades that can be seen in upcoming years in terms of blockchain data privacy management. It includes enhanced encryption techniques decentralized identity solutions, confidential smart contracts and permissioned blockchains. Create an editable A87 Comprehensive Look At Blockchain Technologys Future Of Blockchain Data Privacy BCT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. A87 Comprehensive Look At Blockchain Technologys Future Of Blockchain Data Privacy BCT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide highlights various upgrades that can be seen in upcoming years in terms of blockchain data privacy management. It includes enhanced encryption techniques decentralized identity solutions, confidential smart contracts and permissioned blockchains.
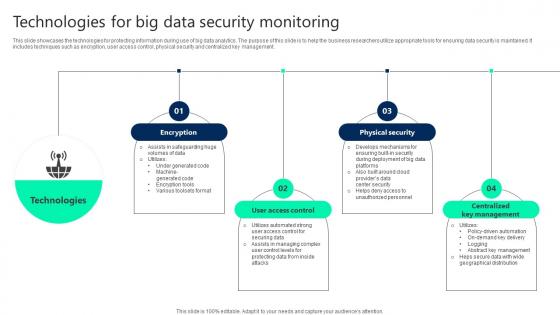
Technologies For Big Data Security Monitoring Summary pdf
This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Showcasing this set of slides titled Technologies For Big Data Security Monitoring Summary pdf. The topics addressed in these templates are User Access Control, Physical Security, Centralized Key Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management.
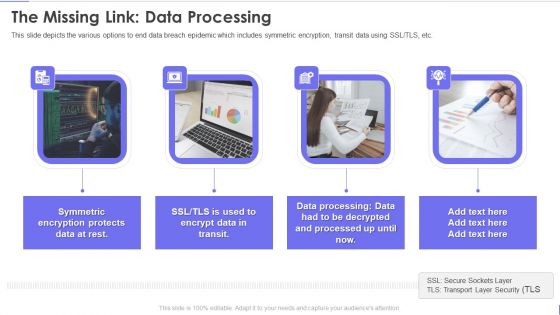
Evervault Capital Investment Elevator Pitch Deck The Missing Link Data Processing Portrait PDF
This slide depicts the various options to end data breach epidemic which includes symmetric encryption, transit data using SSL or TLS, etc. This is a evervault capital investment elevator pitch deck the missing link data processing portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like the missing link data processing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.

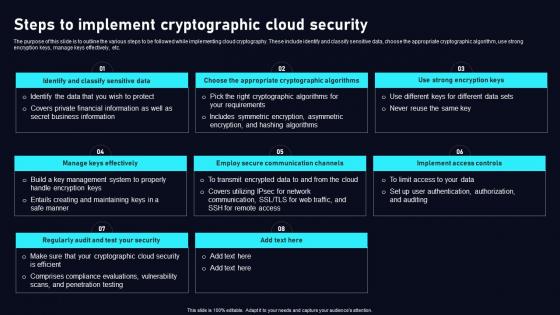
Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Get a simple yet stunning designed Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.
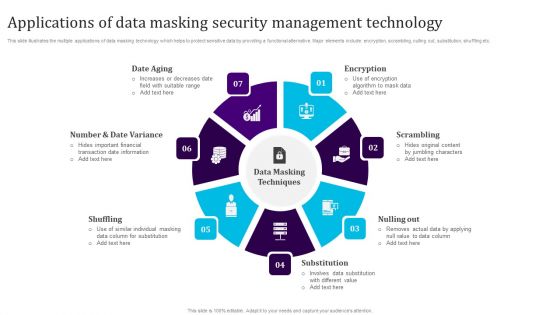
Applications Of Data Masking Security Management Technology Sample PDF
This slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Persuade your audience using this Applications Of Data Masking Security Management Technology Sample PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Date Aging, Shuffling, Substitution, Nulling Out, Scrambling, Encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
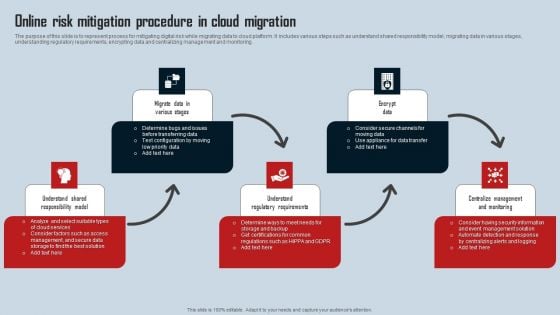
Online Risk Mitigation Procedure In Cloud Migration Mockup PDF
The purpose of this slide is to represent process for mitigating digital risk while migrating data to cloud platform. It includes various steps such as understand shared responsibility model, migrating data in various stages, understanding regulatory requirements, encrypting data and centralizing management and monitoring. Presenting Online Risk Mitigation Procedure In Cloud Migration Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Migrate Data, Encrypt Data, Centralize Management Monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Visionary Guide To Blockchain Future Of Blockchain Data Privacy Management BCT SS V
This slide highlights various upgrades that can be seen in upcoming years in terms of blockchain data privacy management. It includes enhanced encryption techniques decentralized identity solutions, confidential smart contracts and permissioned blockchains. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Visionary Guide To Blockchain Future Of Blockchain Data Privacy Management BCT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Visionary Guide To Blockchain Future Of Blockchain Data Privacy Management BCT SS V. This slide highlights various upgrades that can be seen in upcoming years in terms of blockchain data privacy management. It includes enhanced encryption techniques decentralized identity solutions, confidential smart contracts and permissioned blockchains.

Optimizing Digital Marketing Strategy Use Cloud Technology To Manage Data While Slides PDF
This template covers the process of using cloud technology for managing data. It also includes the benefits of cloud technology, such as encrypting all data and defining who has access. Slidegeeks is here to make your presentations a breeze with Optimizing Digital Marketing Strategy Use Cloud Technology To Manage Data While Slides PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
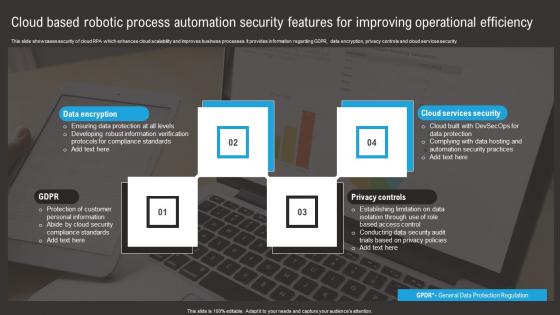
Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf
This slide showcases security of cloud RPA which enhances cloud scalability and improves business processes. It provides information regarding GDPR, data encryption, privacy controls and cloud services security. Pitch your topic with ease and precision using this Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf. This layout presents information on Data Encryption, Privacy Controls, Cloud Services Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases security of cloud RPA which enhances cloud scalability and improves business processes. It provides information regarding GDPR, data encryption, privacy controls and cloud services security.
Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Find highly impressive Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.

Comparative Assessment Of Data Loss Prevention Software Structure PDF
Following slide illustrates comparison of various data loss prevention softwares used in the retail industry. The comparison is drawn on the features such as detecting suspicious activity, endpoint protection platform, enforced encryption etc. Showcasing this set of slides titled Comparative Assessment Of Data Loss Prevention Software Structure PDF. The topics addressed in these templates are System Audit, Pricing, Enforced Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
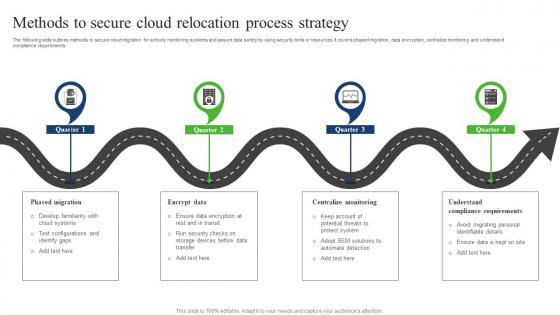
Methods To Secure Cloud Relocation Process Strategy Sample Pdf
The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Showcasing this set of slides titled Methods To Secure Cloud Relocation Process Strategy Sample Pdf. The topics addressed in these templates are Centralize Monitoring, Understand Compliance Requirements, Phased Migration, Encrypt Data . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements.
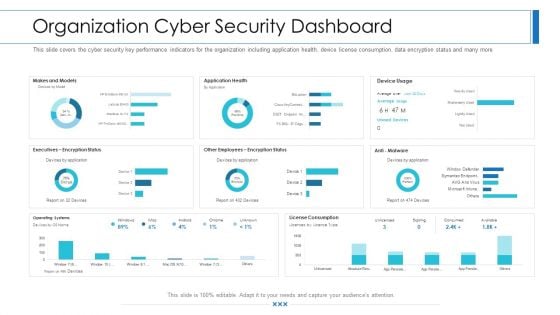
Workforce Security Realization Coaching Plan Organization Cyber Security Dashboard Template PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization cyber security dashboard template pdf bundle. Topics like makes and models, operating systems, encryption status, application health, license consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
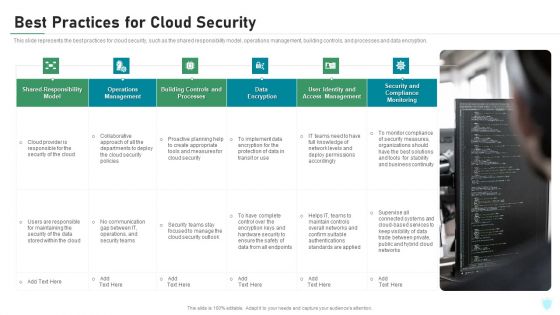
Best Practices For Cloud Security Ppt Infographics Show PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. This is a best practices for cloud security ppt infographics show pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processes, management, monitoring, data encryption, implement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Best Practices For Cloud Security Ppt Icon Pictures PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting it security best practices for cloud security ppt icon pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like operations management, security and compliance monitoring, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cost Estimation For Strategy Implementation Ppt Model Icon PDF
The slide shows the estimation of major cost involved in the next four years 2021 to 2025 for implementing the strategies. The strategies are implementing Data Encryption, Increase Employee Awareness, Restricting Access to Physical Devices etc. Deliver an awe inspiring pitch with this creative cost estimation for strategy implementation ppt model icon pdf bundle. Topics like data encryption, increasing employee awareness, restricted access to physical devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
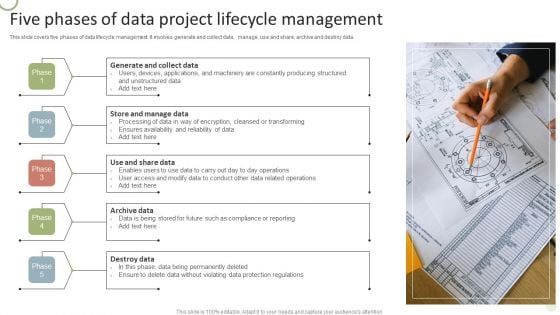
Five Phases Of Data Project Lifecycle Management Formats PDF
This slide covers five phases of data lifecycle management. It involves generate and collect data, manage, use and share, archive and destroy data.Persuade your audience using this Five Phases Of Data Project Lifecycle Management Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Constantly Producing, Encryption Cleansed, Protection Regulations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. The Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc.

Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc. Take your projects to the next level with our ultimate collection of Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc.

Addressing Cybersecurity Challenges In Complete Guide On Managing Banking Fin SS V
This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Addressing Cybersecurity Challenges In Complete Guide On Managing Banking Fin SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc.

Software Services Business Profile Digital Products And Solutions Ppt PowerPoint Presentation File Infographics PDF
This slide depicts four product categories which include software, products, platforms, and others. Key solutions under these categories are remote meeting software, data encryption tool, operating system, simulation software, antivirus protection, surveillance infrastructure, engineering design tool, and source code development platform. This is a Software Services Business Profile Digital Products And Solutions Ppt PowerPoint Presentation File Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Remote Meeting Software, Data Encryption Tool, Operating System. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
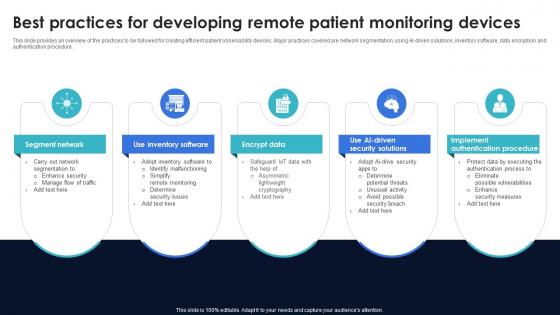
Optimization Of IoT Remote Monitoring Best Practices For Developing Remote Patient Monitoring IoT SS V
This slide provides an overview of the practices to be followed for creating efficient patient observability devices. Major practices covered are network segmentation, using AI-driven solutions, inventory software, data encryption and authentication procedure. Present like a pro with Optimization Of IoT Remote Monitoring Best Practices For Developing Remote Patient Monitoring IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides an overview of the practices to be followed for creating efficient patient observability devices. Major practices covered are network segmentation, using AI-driven solutions, inventory software, data encryption and authentication procedure.

Beginners Guide To Commercial Addressing Cybersecurity Challenges In Commercial Fin SS V
This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc. Want to ace your presentation in front of a live audience Our Beginners Guide To Commercial Addressing Cybersecurity Challenges In Commercial Fin SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc.

Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF bundle. Topics like Implement Information, Security Policies, Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Organization Cyber Security Dashboard Ppt Icon Sample PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard ppt icon sample pdf. Use them to share invaluable insights on makes and models, application health, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
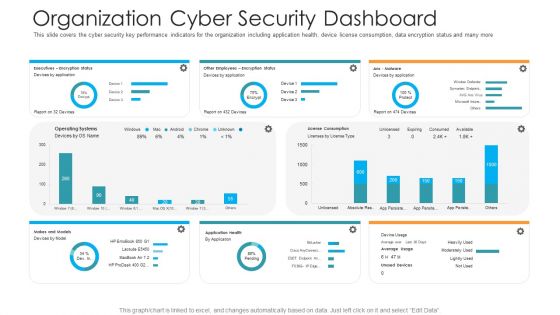
Organization Cyber Security Dashboard Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on executives, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
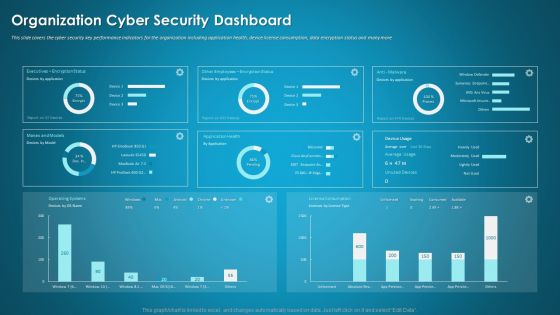
Organizational Network Security Awareness Staff Learning Organization Cyber Security Dashboard Elements PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization cyber security dashboard elements pdf. Use them to share invaluable insights on organization cyber security dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
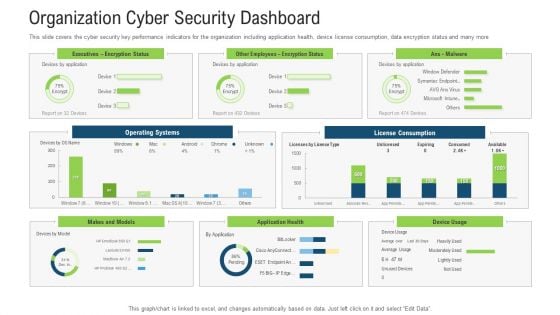
Organization Cyber Security Dashboard Ppt Show Outfit PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe inspiring pitch with this creative organization cyber security dashboard ppt show outfit pdf bundle. Topics like operating systems, license consumption, makes and models, other employees can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Measures Taken For Data Protection In Cloud Globally Ethical Dimensions Of Datafication Clipart Pdf
This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. Take your projects to the next level with our ultimate collection of Measures Taken For Data Protection In Cloud Globally Ethical Dimensions Of Datafication Clipart Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Web Consulting Business Performance Best Practices For Web Security
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Web Consulting Business Performance Best Practices For Web Security a try. Our experts have put a lot of knowledge and effort into creating this impeccable Web Consulting Business Performance Best Practices For Web Security. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup
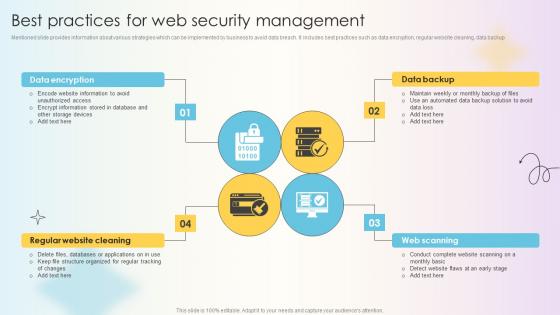
Managing Technical And Non Technical Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup Present like a pro with Managing Technical And Non Technical Best Practices For Web Security Management. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup

Comprehensive Guide For Website Development Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup This modern and well-arranged Comprehensive Guide For Website Development Best Practices For Web Security Management provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup
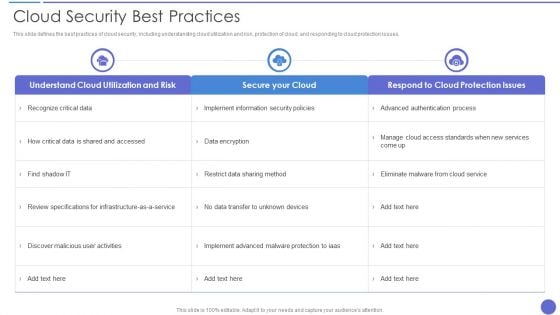
Cloud Security Best Practices Themes PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Security Best Practices Themes PDF. Use them to share invaluable insights on Secure Your Cloud, Data Encryption, Recognize Critical Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
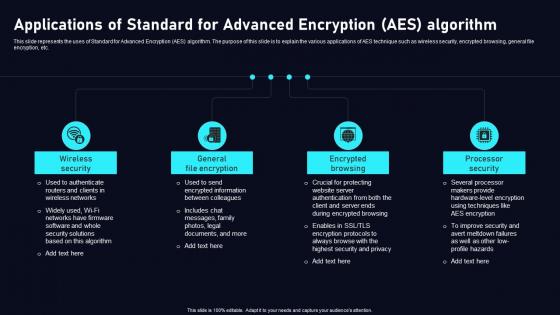
Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc.
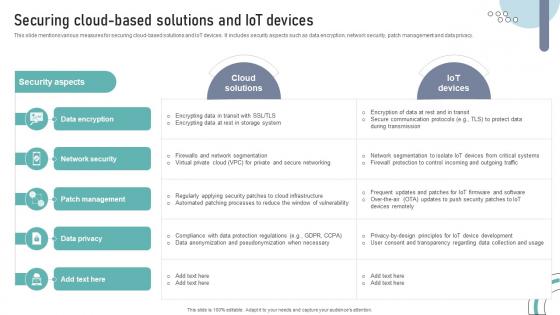
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy.

Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
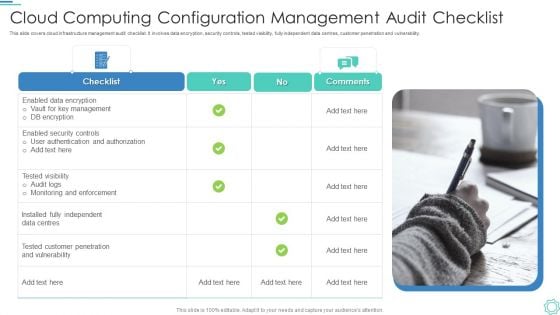
Cloud Computing Configuration Management Audit Checklist Professional PDF
This slide covers cloud infrastructure management audit checklist. It involves data encryption, security controls, tested visibility, fully independent data centres, customer penetration and vulnerability.Presenting Cloud Computing Configuration Management Audit Checklist Professional PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Management, Customer, Data Centres. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Overview And Benefits Of Tokenization Strategies For Data Security PPT Sample
This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Boost your pitch with our creative Overview And Benefits Of Tokenization Strategies For Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc.
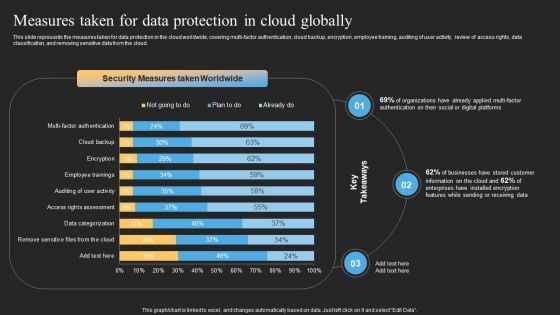
Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF
This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. This Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
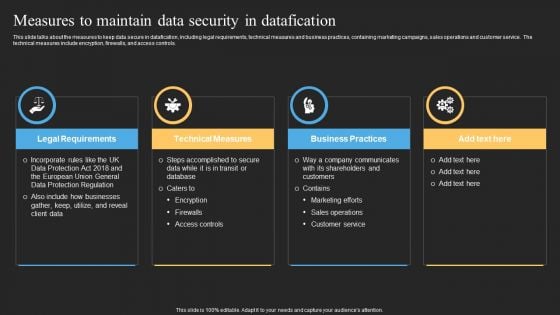
Datafy Measures To Maintain Data Security In Datafication Diagrams PDF
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Welcome to our selection of the Datafy Measures To Maintain Data Security In Datafication Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Challenge And Solutions 2 Cloud Threats And Security Ppt Outline Design Inspiration PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt outline design inspiration pdf bundle. Topics like implement data encryption techniques to eliminate risk of infiltration, security and compliance risks are major considerations for the company, professional business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
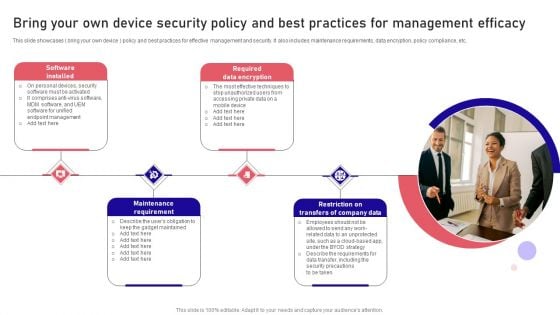
Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF
This slide showcases bring your own device policy and best practices for effective management and security. It also includes maintenance requirements, data encryption, policy compliance, etc. Persuade your audience using this Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Software Installed, Maintenance Requirement, Encryption . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. Slidegeeks is here to make your presentations a breeze with Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc.
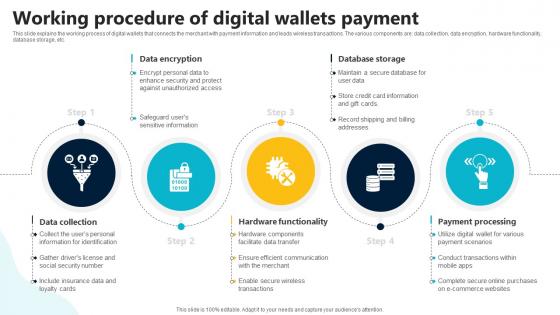
Working Procedure Of Digital Wallets Payment In Depth Guide To Digital Wallets Fin SS V
This slide explains the working process of digital wallets that connects the merchant with payment information and leads wireless transactions. The various components are data collection, data encryption, hardware functionality, database storage, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Working Procedure Of Digital Wallets Payment In Depth Guide To Digital Wallets Fin SS V from Slidegeeks and deliver a wonderful presentation. This slide explains the working process of digital wallets that connects the merchant with payment information and leads wireless transactions. The various components are data collection, data encryption, hardware functionality, database storage, etc.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Ppt Gallery Background Images PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Deliver an awe inspiring pitch with this creative strategies for reducing cybersecurity risks in abs healthcare company ppt gallery background images pdf bundle. Topics like set strong passwords and use data encryption, ensure proper data management and use updated software, proper employee training, protect devices that can be physically accessed, strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Are you searching for a Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf from Slidegeeks today. The following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc.

Solutions To Overcome Multiple Cybersecurity Challenges Mastering Investment Banking Fin SS V
This slide shows information which can be used by individuals or investment bankers to get the right solution for cybersecurity challenges. These solutions include cybersecurity framework, training, data encryption, etc. Slidegeeks is here to make your presentations a breeze with Solutions To Overcome Multiple Cybersecurity Challenges Mastering Investment Banking Fin SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows information which can be used by individuals or investment bankers to get the right solution for cybersecurity challenges. These solutions include cybersecurity framework, training, data encryption, etc.

Solutions To Overcome Multiple Cybersecurity Investment Banking Simplified Functions Fin SS V
This slide shows information which can be used by individuals or investment bankers to get the right solution for cybersecurity challenges. These solutions include cybersecurity framework, training, data encryption, etc. Slidegeeks is here to make your presentations a breeze with Solutions To Overcome Multiple Cybersecurity Investment Banking Simplified Functions Fin SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows information which can be used by individuals or investment bankers to get the right solution for cybersecurity challenges. These solutions include cybersecurity framework, training, data encryption, etc.
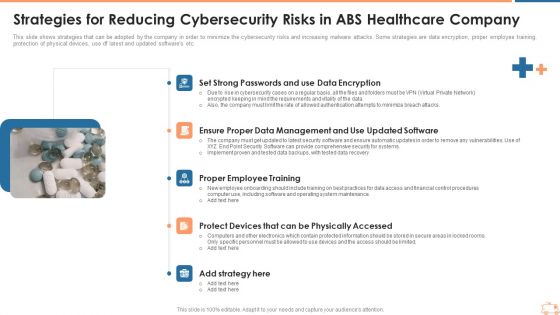
Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Rules PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Presenting strategies for reducing cybersecurity risks in abs healthcare company rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like set strong passwords and use data encryption, proper employee training, protect devices that can be physically accessed, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
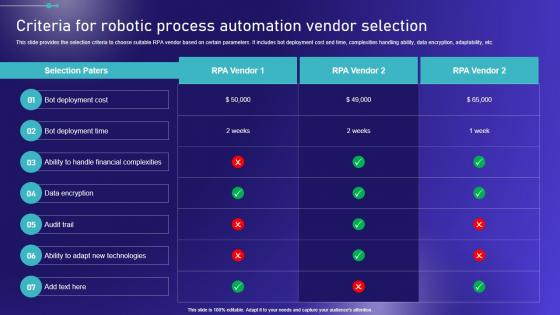
Criteria For Robotic Process Automation Vendor Embracing Robotic Process Microsoft PDF
This slide provides the selection criteria to choose suitable RPA vendor based on certain parameters. It includes bot deployment cost and time, complexities handling ability, data encryption, adaptability, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Criteria For Robotic Process Automation Vendor Embracing Robotic Process Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Criteria For Robotic Process Automation Vendor Embracing Robotic Process Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide provides the selection criteria to choose suitable RPA vendor based on certain parameters. It includes bot deployment cost and time, complexities handling ability, data encryption, adaptability, etc.

Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc. Create an editable Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Table Of Contents For Cloud Computing Security IT Monitoring Ppt Styles Introduction PDF
Presenting table of contents for cloud computing security it monitoring ppt styles introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, business, implement, roadmap, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF bundle. Topics like Implement Information, Data Encryption, Implement Advanced can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
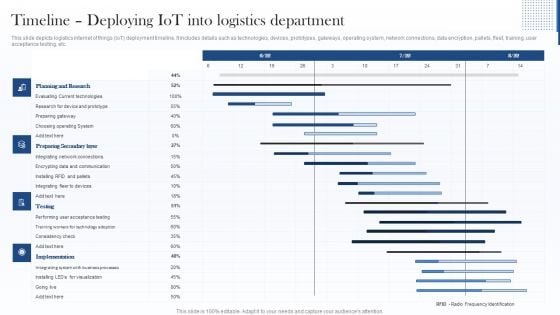
Timeline Deploying Iot Into Logistics Department Introduction PDF
This slide depicts logistics internet of things IoT deployment timeline. It includes details such as technologies, devices, prototypes, gateways, operating system, network connections, data encryption, pallets, fleet, training, user acceptance testing, etc. Deliver an awe inspiring pitch with this creative Timeline Deploying Iot Into Logistics Department Introduction PDF bundle. Topics like Preparing Secondary Layer, Planning And Research, Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































