Data Encryption
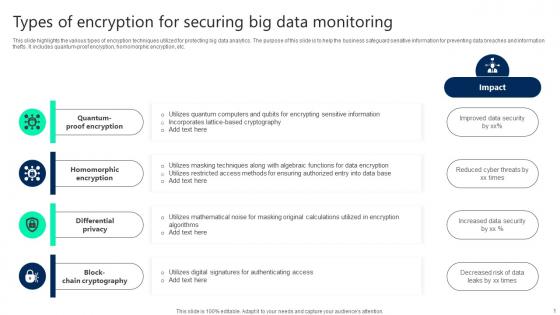
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.
Encrypted Business Data Cyber Security Assessment Icon Professional PDF
Presenting Encrypted Business Data Cyber Security Assessment Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
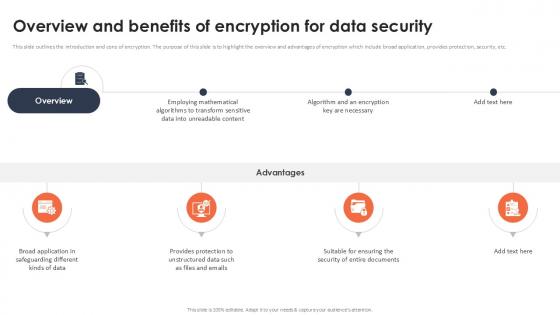
Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint
This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Retrieve professionally designed Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc.
Email Security Encryption And Data Loss Prevention Proposal Icons Slide Summary PDF
Download our innovative and attention-grabbing email security encryption and data loss prevention proposal icons slide summary pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
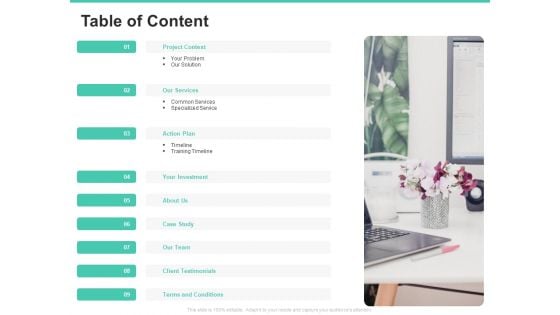
Email Security Encryption And Data Loss Prevention Table Of Content Slides PDF
Presenting email security encryption and data loss prevention table of content slides pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like project context, our services, action plan, investment, about us, case study, our team, client testimonials, terms and conditions. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Email Security Encryption And Data Loss Prevention 30 60 90 Days Plan Diagrams PDF
This is a email security encryption and data loss prevention 30 60 90 days plan diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Email Security Encryption And Data Loss Prevention Client Testimonial Guidelines PDF
This Slide shows the testimonials of the previous clients who have worked with you. Presenting email security encryption and data loss prevention client testimonial guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like client testimonial. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Email Security Encryption And Data Loss Prevention Your Investment For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed investment of your client into various security softwares. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention your investment for e mail security proposal diagrams pdf bundle. Topics like product, free version, starting price, frequency, per user can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Email Security Encryption And Data Loss Prevention Your Problem E Mail Security Proposal Rules PDF
This slide covers the problems that are faced by the clients. Presenting email security encryption and data loss prevention your problem e mail security proposal rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security confidential data, protection against malware, protection phishing scams, threat weak password. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
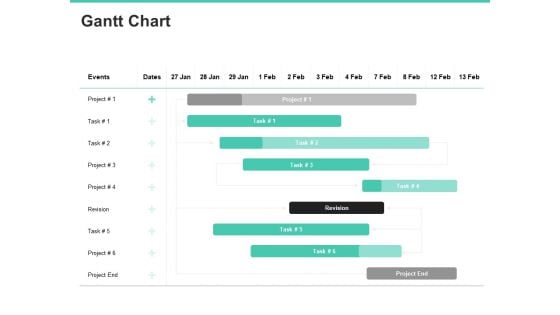
Email Security Encryption And Data Loss Prevention Gantt Chart Information PDF
Your complex projects can be managed and organized simultaneously using this detailed email security encryption and data loss prevention gantt chart information pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well-crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.
Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf
Showcasing this set of slides titled Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf. The topics addressed in these templates are Encryption Techniques, IconSecuring, Big Data Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Virtual Private Network Tunnel Layout Showing Encrypted Data Ppt PowerPoint Presentation File Summary PDF
Persuade your audience using this virtual private network tunnel layout showing encrypted data ppt powerpoint presentation file summary pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network tunnel layout showing encrypted data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
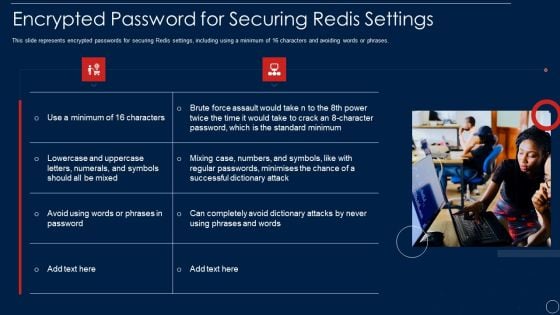
Redis Cache Data Structure IT Encrypted Password For Securing Redis Settings Formats PDF
This slide represents encrypted passwords for securing Redis settings, including using a minimum of 16 characters and avoiding words or phrases. This is a redis cache data structure it encrypted password for securing redis settings formats pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypted password for securing redis settings. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
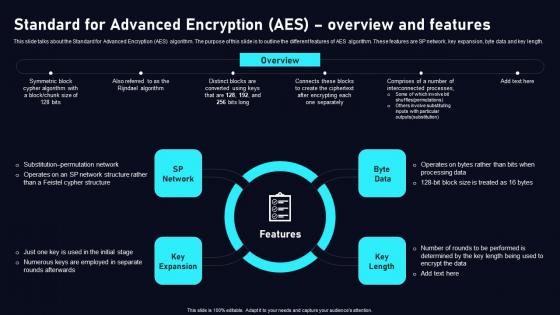
Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.

Factors To Consider While Choosing Tokenization Over Encryption Securing Your Data Ppt Example
This slide showcases the aspects to consider while choosing tokenization over encryption. The purpose of this slide is to outline the aspects such as reduction of compliance scope, format attributes, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Factors To Consider While Choosing Tokenization Over Encryption Securing Your Data Ppt Example was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Factors To Consider While Choosing Tokenization Over Encryption Securing Your Data Ppt Example This slide showcases the aspects to consider while choosing tokenization over encryption. The purpose of this slide is to outline the aspects such as reduction of compliance scope, format attributes, etc.
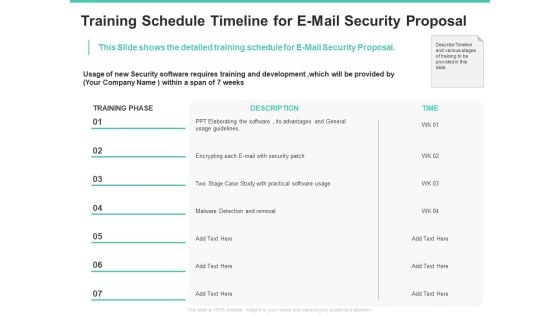
Email Security Encryption And Data Loss Prevention Training Schedule Timeline For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed training schedule for E-Mail Security Proposal. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention training schedule timeline for e mail security proposal diagrams pdf bundle. Topics like case study, security, development, timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
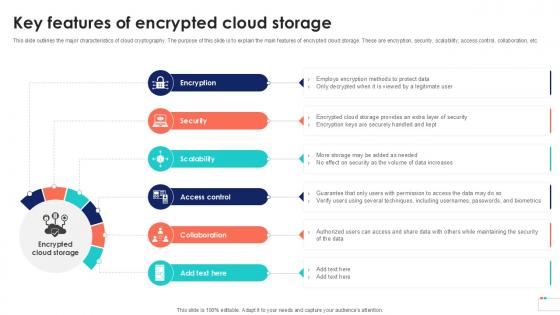
Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. This Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.

Comparative Analysis Of Encryption And Tokenization In Ds Securing Your Data Ppt Presentation
This slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective, and so on Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparative Analysis Of Encryption And Tokenization In Ds Securing Your Data Ppt Presentation With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparative Analysis Of Encryption And Tokenization In Ds Securing Your Data Ppt Presentation today and make your presentation stand out from the rest This slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective, and so on
Encrypt And Create Backup Of Useful Data Ppt PowerPoint Presentation File Icon PDF
The following slide illustrates various methods to encrypt and back-up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost, Explore a selection of the finest Encrypt And Create Backup Of Useful Data Ppt PowerPoint Presentation File Icon PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Encrypt And Create Backup Of Useful Data Ppt PowerPoint Presentation File Icon PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
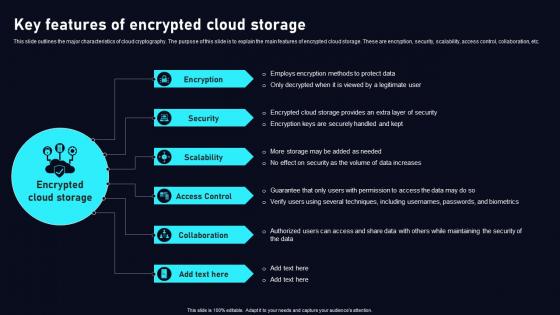
Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.
Vector For Data Migration From Smart Phone To Encrypted Files Ppt PowerPoint Presentation Outline Background Images PDF
Presenting vector for data migration from smart phone to encrypted files ppt powerpoint presentation outline background images pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vector for data migration from smart phone to encrypted files. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
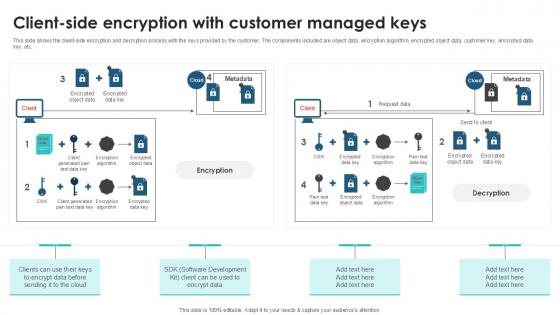
Client Side Encryption With Customer Client Side Encryption PPT Presentation
This slide shows the client-side encryption and decryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encrypted data key, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Side Encryption With Customer Client Side Encryption PPT Presentation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide shows the client-side encryption and decryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encrypted data key, etc.
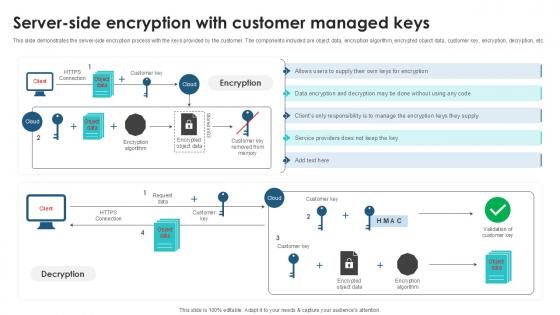
Server Side Encryption With Customer Client Side Encryption PPT Example
This slide demonstrates the server-side encryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encryption, decryption, etc. Retrieve professionally designed Server Side Encryption With Customer Client Side Encryption PPT Example to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide demonstrates the server-side encryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encryption, decryption, etc.
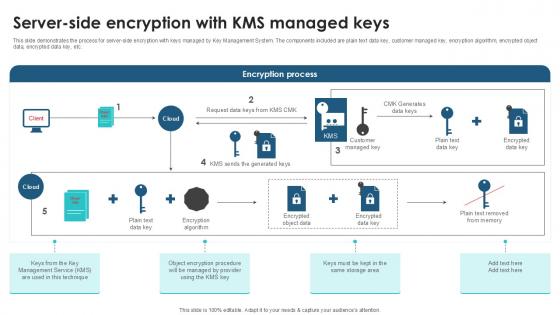
Server Side Encryption With KMS Client Side Encryption PPT PowerPoint
This slide demonstrates the process for server-side encryption with keys managed by Key Management System. The components included are plain text data key, customer managed key, encryption algorithm, encrypted object data, encrypted data key, etc. Slidegeeks has constructed Server Side Encryption With KMS Client Side Encryption PPT PowerPoint after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide demonstrates the process for server-side encryption with keys managed by Key Management System. The components included are plain text data key, customer managed key, encryption algorithm, encrypted object data, encrypted data key, etc.
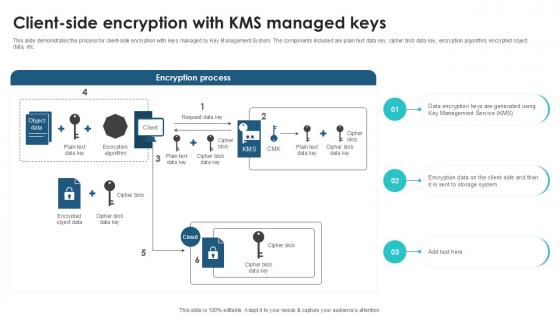
Client Side Encryption With KMS Client Side Encryption PPT Template
This slide demonstrates the process for client-side encryption with keys managed by Key Management System. The components included are plain text data key, cipher blob data key, encryption algorithm, encrypted object data, etc. Present like a pro with Client Side Encryption With KMS Client Side Encryption PPT Template. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide demonstrates the process for client-side encryption with keys managed by Key Management System. The components included are plain text data key, cipher blob data key, encryption algorithm, encrypted object data, etc.
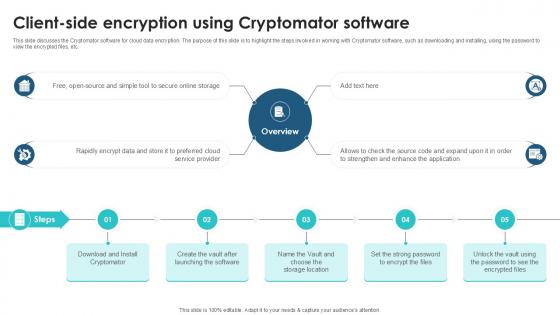
Client Side Encryption Using Cryptomator Client Side Encryption PPT Presentation
This slide discusses the Cryptomator software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with Cryptomator software, such as downloading and installing, using the password to view the encrypted files, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Client Side Encryption Using Cryptomator Client Side Encryption PPT Presentation a try. Our experts have put a lot of knowledge and effort into creating this impeccable Client Side Encryption Using Cryptomator Client Side Encryption PPT Presentation. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide discusses the Cryptomator software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with Cryptomator software, such as downloading and installing, using the password to view the encrypted files, etc.

Client Side Encryption Using Nordlocker Client Side Encryption PPT Presentation
This slide discusses the NordLocker software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with NordLocker software, such as downloading and installing, creating a password, using the password to view the encrypted files, etc. Get a simple yet stunning designed Client Side Encryption Using Nordlocker Client Side Encryption PPT Presentation. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Side Encryption Using Nordlocker Client Side Encryption PPT Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide discusses the NordLocker software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with NordLocker software, such as downloading and installing, creating a password, using the password to view the encrypted files, etc.
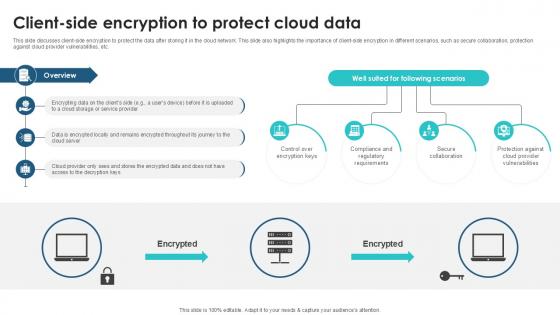
Client Side Encryption To Protect Client Side Encryption PPT Example
This slide discusses client-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client-side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc. There are so many reasons you need a Client Side Encryption To Protect Client Side Encryption PPT Example. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide discusses client-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client-side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc.
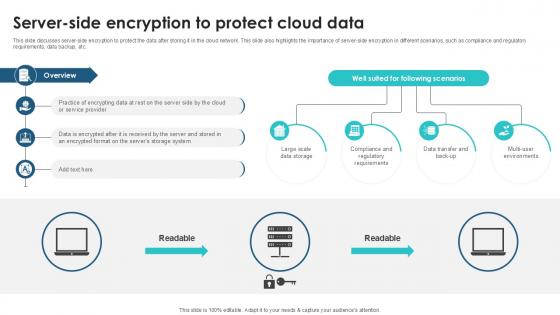
Server Side Encryption To Protect Client Side Encryption PPT Presentation
This slide discusses server-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of server-side encryption in different scenarios, such as compliance and regulatory requirements, data backup, etc. Are you searching for a Server Side Encryption To Protect Client Side Encryption PPT Presentation that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Server Side Encryption To Protect Client Side Encryption PPT Presentation from Slidegeeks today. This slide discusses server-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of server-side encryption in different scenarios, such as compliance and regulatory requirements, data backup, etc.
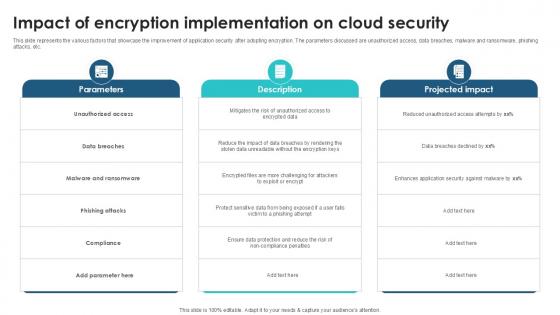
Impact Of Encryption Implementation Client Side Encryption PPT Presentation
This slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Impact Of Encryption Implementation Client Side Encryption PPT Presentation to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc.

Client Side Encryption Implementation Guide Ppt Template

Cloud Encryption Techniques IT Ppt Powerpoint

Comparison Between Server Side And Client Side Encryption PPT PowerPoint
The purpose of this slide is to compare client-side and server-side encryption procedures. The comparison is carried out based on several factors, such as encryption performed, key management, data privacy, complexity, collaboration, performance overhead, etc. Find highly impressive Comparison Between Server Side And Client Side Encryption PPT PowerPoint on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comparison Between Server Side And Client Side Encryption PPT PowerPoint for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to compare client-side and server-side encryption procedures. The comparison is carried out based on several factors, such as encryption performed, key management, data privacy, complexity, collaboration, performance overhead, etc.
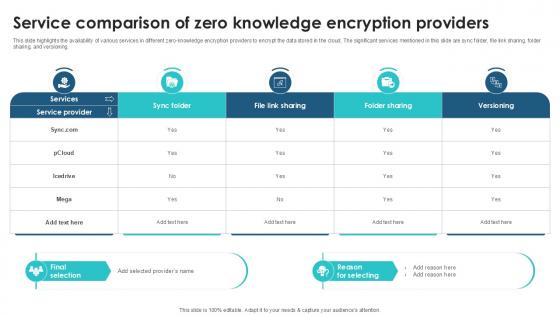
Service Comparison Of Zero Knowledge Client Side Encryption PPT Presentation
This slide highlights the availability of various services in different zero-knowledge encryption providers to encrypt the data stored in the cloud. The significant services mentioned in this slide are sync folder, file link sharing, folder sharing, and versioning. Presenting this PowerPoint presentation, titled Service Comparison Of Zero Knowledge Client Side Encryption PPT Presentation, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Service Comparison Of Zero Knowledge Client Side Encryption PPT Presentation. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Service Comparison Of Zero Knowledge Client Side Encryption PPT Presentation that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide highlights the availability of various services in different zero-knowledge encryption providers to encrypt the data stored in the cloud. The significant services mentioned in this slide are sync folder, file link sharing, folder sharing, and versioning.
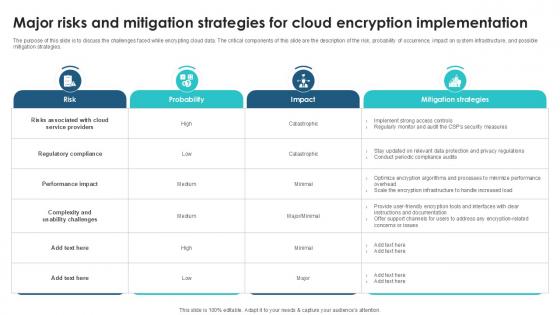
Major Risks And Mitigation Strategies Client Side Encryption PPT Template
The purpose of this slide is to discuss the challenges faced while encrypting cloud data. The critical components of this slide are the description of the risk, probability of occurrence, impact on system infrastructure, and possible mitigation strategies. This Major Risks And Mitigation Strategies Client Side Encryption PPT Template is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Major Risks And Mitigation Strategies Client Side Encryption PPT Template features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The purpose of this slide is to discuss the challenges faced while encrypting cloud data. The critical components of this slide are the description of the risk, probability of occurrence, impact on system infrastructure, and possible mitigation strategies.

Main Goals Of Application Level Encryption Application Security Testing
This slide showcases the objectives of application-level encryption in application security which include data protection, increased security, etc. Retrieve professionally designed Main Goals Of Application Level Encryption Application Security Testing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases the objectives of application-level encryption in application security which include data protection, increased security, etc.
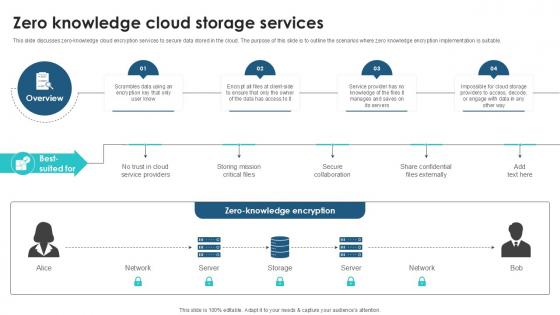
Zero Knowledge Cloud Storage Client Side Encryption PPT Template
This slide discusses zero-knowledge cloud encryption services to secure data stored in the cloud. The purpose of this slide is to outline the scenarios where zero knowledge encryption implementation is suitable. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Knowledge Cloud Storage Client Side Encryption PPT Template to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Knowledge Cloud Storage Client Side Encryption PPT Template. This slide discusses zero-knowledge cloud encryption services to secure data stored in the cloud. The purpose of this slide is to outline the scenarios where zero knowledge encryption implementation is suitable.
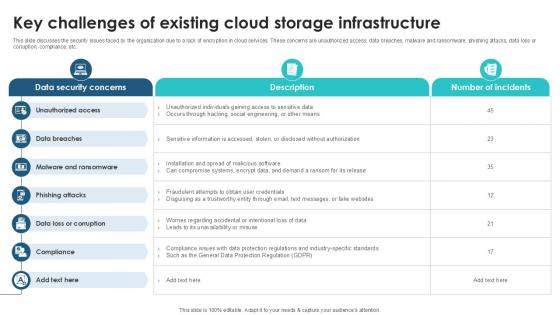
Key Challenges Of Existing Cloud Client Side Encryption PPT Slide
This slide discusses the security issues faced by the organization due to a lack of encryption in cloud services. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc. This modern and well-arranged Key Challenges Of Existing Cloud Client Side Encryption PPT Slide provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide discusses the security issues faced by the organization due to a lack of encryption in cloud services. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc.
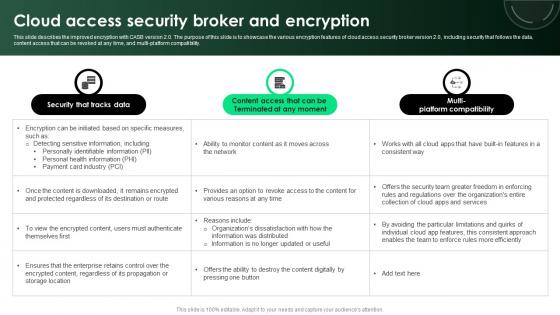
CASB 2 0 IT Cloud Access Security Broker And Encryption
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Cloud Access Security Broker And Encryption. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility.
End To End Scenario Icon For Message Encryption Clipart Pdf
Pitch your topic with ease and precision using this End To End Scenario Icon For Message Encryption Clipart Pdf This layout presents information on End To End Scenario, Icon Message Encryption It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our End To End Scenario Icon For Message Encryption Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Comparative Analysis Of Encryption And Tokenization In Ds PPT Template
This slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective. Boost your pitch with our creative Comparative Analysis Of Encryption And Tokenization In Ds PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective, and so on

Table Of Contents Client Side Encryption Implementation Guide PPT PowerPoint
Take your projects to the next level with our ultimate collection of Table Of Contents Client Side Encryption Implementation Guide PPT PowerPoint. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest Our Table Of Contents Client Side Encryption Implementation Guide PPT PowerPoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
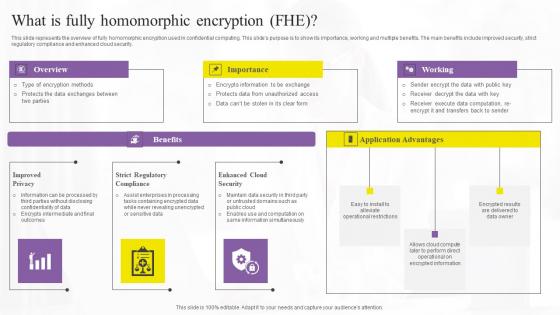
What Is Fully Homomorphic Encryption Confidential Computing Technologies Inspiration Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Whether you have daily or monthly meetings, a brilliant presentation is necessary. What Is Fully Homomorphic Encryption Confidential Computing Technologies Inspiration Pdf can be your best option for delivering a presentation. Represent everything in detail using What Is Fully Homomorphic Encryption Confidential Computing Technologies Inspiration Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.

Agenda Client Side Encryption Implementation Guide PPT Sample
Find a pre-designed and impeccable Agenda Client Side Encryption Implementation Guide PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda Client Side Encryption Implementation Guide PPT Sample are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Document Encryption Vector Icon Ppt PowerPoint Presentation Styles Clipart Images
Presenting this set of slides with name document encryption vector icon ppt powerpoint presentation styles clipart images. This is a one stage process. The stage in this process is document encryption vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
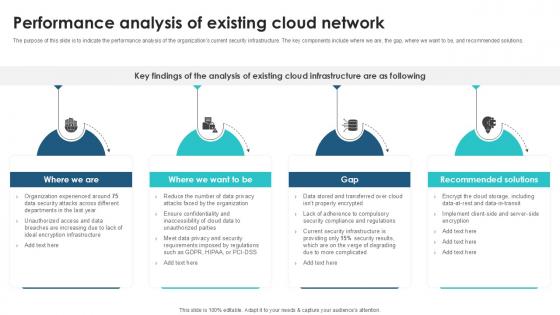
Performance Analysis Of Existing Client Side Encryption PPT Example
The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Welcome to our selection of the Performance Analysis Of Existing Client Side Encryption PPT Example. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions.
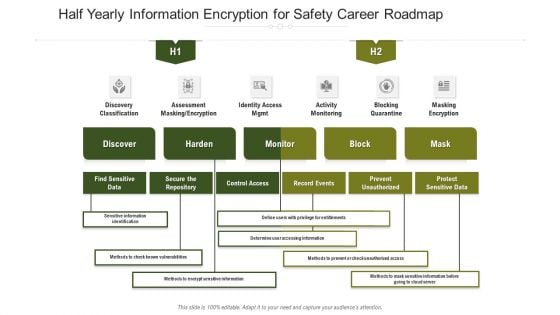
Half Yearly Information Encryption For Safety Career Roadmap Infographics
We present our half yearly information encryption for safety career roadmap infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly information encryption for safety career roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
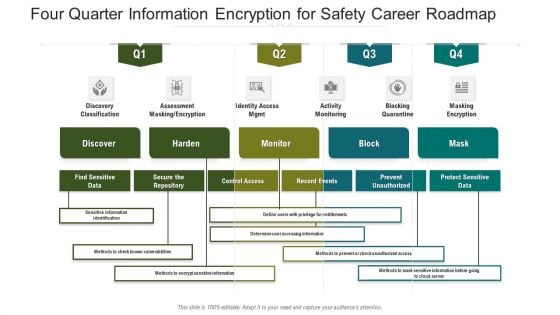
Four Quarter Information Encryption For Safety Career Roadmap Introduction
Presenting our innovatively structured four quarter information encryption for safety career roadmap introduction Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Five Year Information Encryption For Safety Career Roadmap Icons
Introducing our five year information encryption for safety career roadmap icons. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
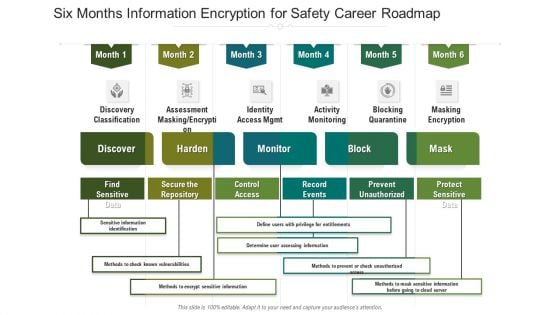
Six Months Information Encryption For Safety Career Roadmap Structure
Introducing our six months information encryption for safety career roadmap structure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
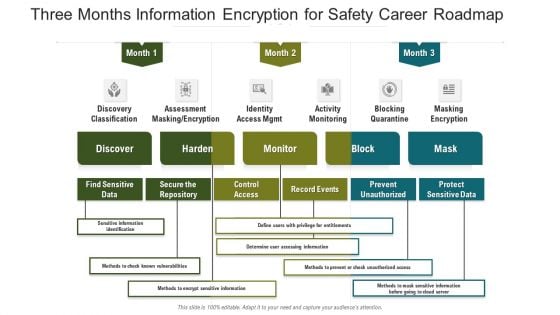
Three Months Information Encryption For Safety Career Roadmap Structure
Introducing our three months information encryption for safety career roadmap structure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
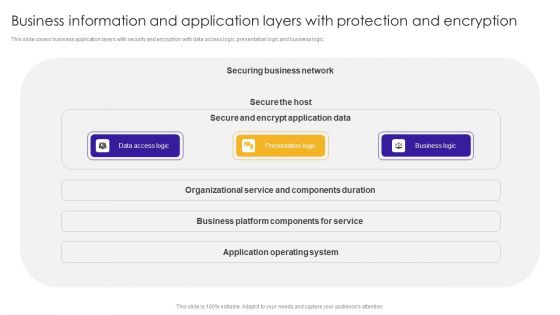
Business Information And Application Layers With Protection And Encryption Brochure PDF
This slide covers business application layers with security and encryption with data access logic, presentation logic and business logic.Pitch your topic with ease and precision using this Business Information And Application Layers With Protection And Encryption Brochure PDF. This layout presents information on Organizational Service, Components Duration, Operating System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
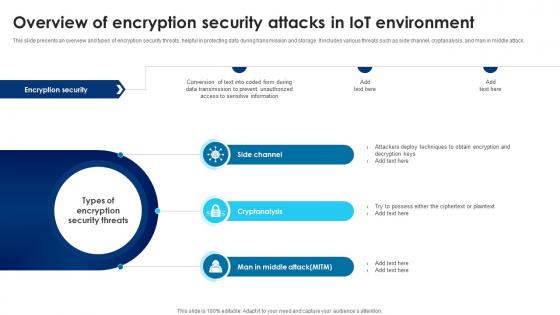
Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack.
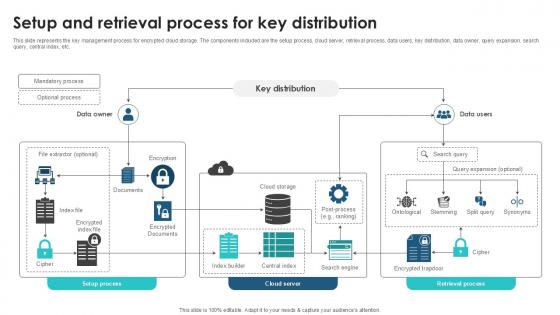
Setup And Retrieval Process For Key Client Side Encryption PPT Presentation
This slide represents the key management process for encrypted cloud storage. The components included are the setup process, cloud server, retrieval process, data users, key distribution, data owner, query expansion, search query, central index, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Setup And Retrieval Process For Key Client Side Encryption PPT Presentation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Setup And Retrieval Process For Key Client Side Encryption PPT Presentation. This slide represents the key management process for encrypted cloud storage. The components included are the setup process, cloud server, retrieval process, data users, key distribution, data owner, query expansion, search query, central index, etc.
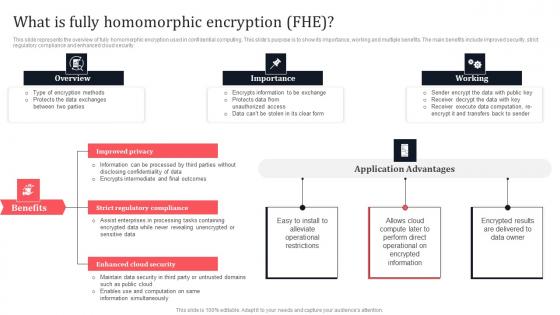
What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Make sure to capture your audiences attention in your business displays with our gratis customizable What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.
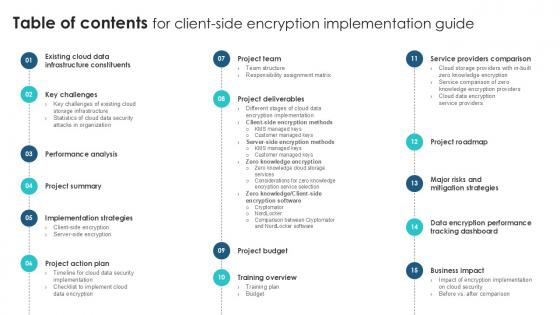
Table Of Contents For Client Side Encryption Implementation Guide PPT Slide
Do you know about Slidesgeeks Table Of Contents For Client Side Encryption Implementation Guide PPT Slide These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. Our Table Of Contents For Client Side Encryption Implementation Guide PPT Slide are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
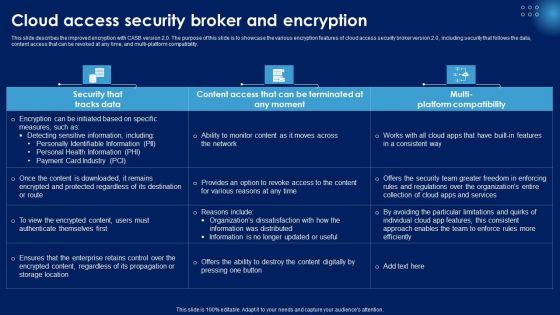
Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Presenting this PowerPoint presentation, titled Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
End To End Encryption Vector Icon Ppt PowerPoint Presentation Gallery Show PDF
Presenting this set of slides with name end to end encryption vector icon ppt powerpoint presentation gallery show pdf. This is a three stage process. The stages in this process are end to end encryption vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Distributed Ledger Technology Icon With Encryption Symbol Ppt PowerPoint Presentation Gallery Visuals PDF
Persuade your audience using this distributed ledger technology icon with encryption symbol ppt powerpoint presentation gallery visuals pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including distributed ledger technology icon with encryption symbol. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
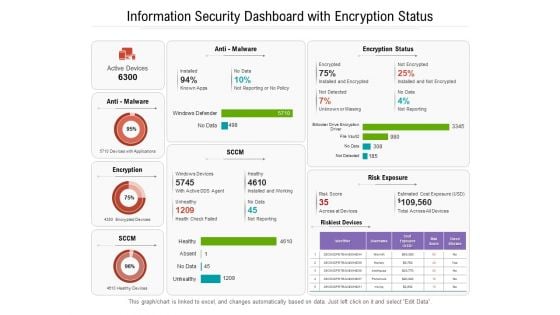
Information Security Dashboard With Encryption Status Ppt PowerPoint Presentation Gallery Pictures PDF
Presenting this set of slides with name information security dashboard with encryption status ppt powerpoint presentation gallery pictures pdf. The topics discussed in these slides are devices, cost, malware. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































