Data Encryption

Timeline Deploying Iot Into Logistics Department Clipart PDF
This slide depicts logistics internet of things IoT deployment timeline. It includes details such as technologies, devices, prototypes, gateways, operating system, network connections, data encryption, pallets, fleet, training, user acceptance testing, etc. Deliver an awe inspiring pitch with this creative Timeline Deploying Iot Into Logistics Department Clipart PDF bundle. Topics like Planning And Research, Preparing Secondary Layer, Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
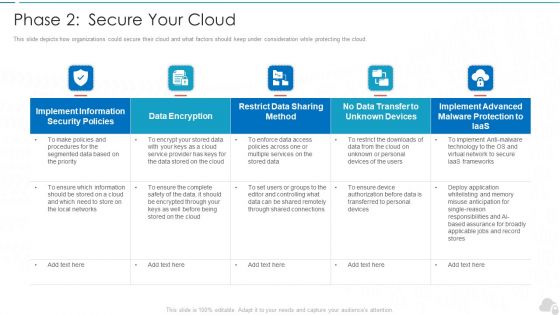
Phase 2 Secure Your Cloud Cloud Computing Security IT Ppt Slides Skills PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative phase 2 secure your cloud cloud computing security it ppt slides skills pdf bundle. Topics like implement, security policies, data encryption, services, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Process Management With Data Loss Prevention Ppt PowerPoint Presentation Icon Example File PDF
Presenting information process management with data loss prevention ppt powerpoint presentation icon example file pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including encryption and right management, monitoring and tracking, classification, document identity, compliance, data loss prevention. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
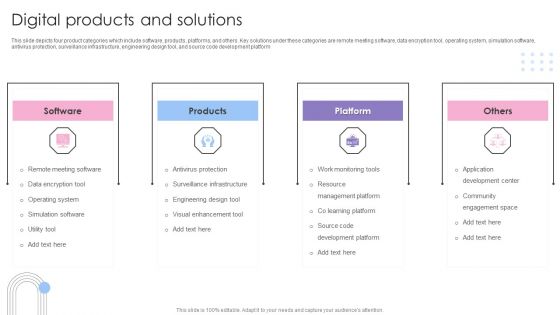
Software Products And Solutions Firm Details Digital Products And Solutions Slides PDF
This slide depicts four product categories which include software, products, platforms, and others. Key solutions under these categories are remote meeting software, data encryption tool, operating system, simulation software, antivirus protection, surveillance infrastructure, engineering design tool, and source code development platform. This is a Software Products And Solutions Firm Details Digital Products And Solutions Slides PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Software, Products, Platform, Others. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
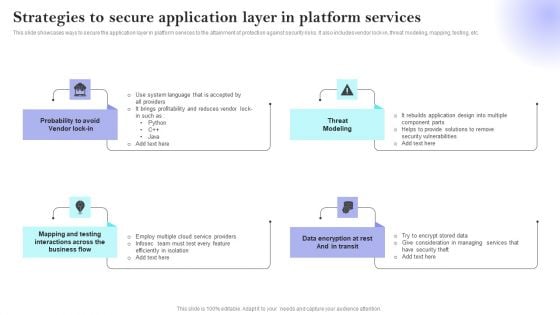
Strategies To Secure Application Layer In Platform Services Topics PDF
This slide showcases ways to secure the application layer in platform services to the attainment of protection against security risks. It also includes vendor lock-in, threat modeling, mapping, testing, etc. Presenting Strategies To Secure Application Layer In Platform Services Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Probability, Threat Modeling, Data Encryption Rest Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
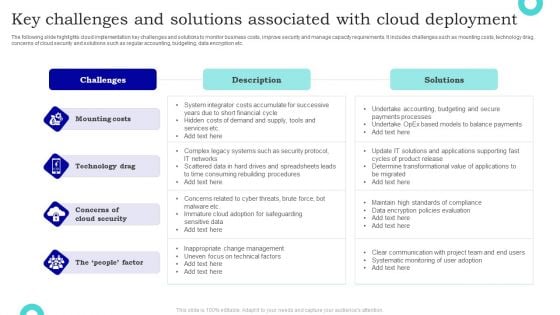
Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF
The following slide highlights cloud implementation key challenges and solutions to monitor business costs, improve security and manage capacity requirements. It includes challenges such as mounting costs, technology drag, concerns of cloud security and solutions such as regular accounting, budgeting, data encryption etc. Pitch your topic with ease and precision using this Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF. This layout presents information on Challenges, Description, Solutions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
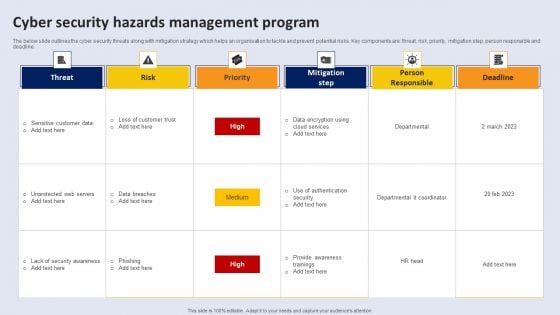
Cyber Security Hazards Management Program Pictures PDF
The below slide outlines the cyber security threats along with mitigation strategy which helps an organisation to tackle and prevent potential risks. Key components are threat, risk, priority, mitigation step, person responsible and deadline.Showcasing this set of slides titled Cyber Security Hazards Management Program Pictures PDF. The topics addressed in these templates are Sensitive Customer, Data Encryption Using. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Software Development Company Profile Digital Products And Solutions Guidelines PDF
This slide depicts four product categories which include software, products, platforms, and others. Key solutions under these categories are remote meeting software, data encryption tool, operating system, simulation software, antivirus protection, surveillance infrastructure, engineering design tool, and source code development platform. Presenting Business Software Development Company Profile Digital Products And Solutions Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Software, Products, Platform, Others. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Contractual Risk Reduction Plan With Key Strategies Download PDF
Mentioned slide provides insight about key risk mitigation strategies which can be used by business for timely delivery of project to client. It includes strategy such as automated workflow, clause and template library, secured approval and data encryption Presenting Contractual Risk Reduction Plan With Key Strategies Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Automated Workflow, Language Compliance, Secured Approval . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

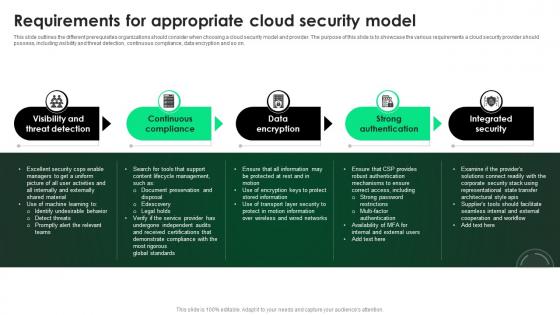
Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. There are so many reasons you need a Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
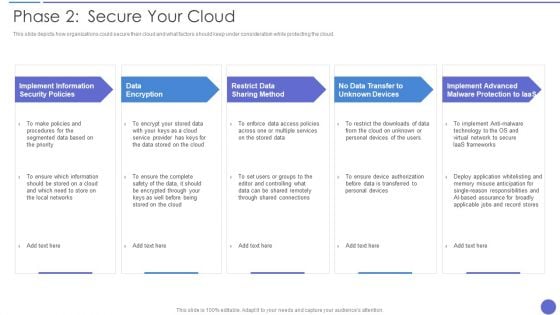
Phase 2 Secure Your Cloud Clipart PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Presenting Phase 2 Secure Your Cloud Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Encryption, Restrict Data Sharing Method, Implement Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
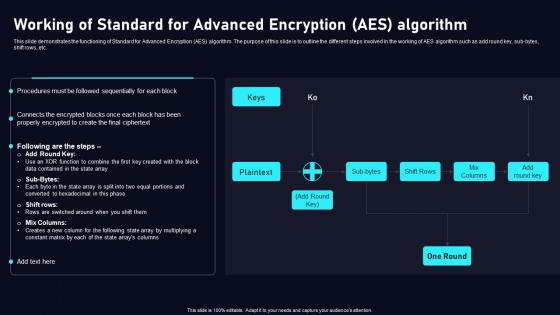
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc.
CASB 2 0 IT Requirements For Appropriate Cloud Security Model
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Find highly impressive CASB 2 0 IT Requirements For Appropriate Cloud Security Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CASB 2 0 IT Requirements For Appropriate Cloud Security Model for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on.
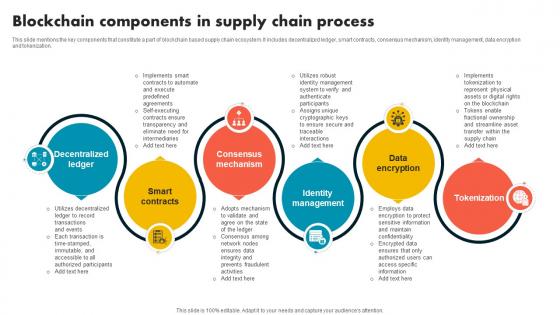
Blockchain Components In Supply Chain Process Supply Chain Evolution Harnessing The Power BCT SS V
This slide mentions the key components that constitute a part of blockchain based supply chain ecosystem. It includes decentralized ledger, smart contracts, consensus mechanism, identity management, data encryption and tokenization. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Blockchain Components In Supply Chain Process Supply Chain Evolution Harnessing The Power BCT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Blockchain Components In Supply Chain Process Supply Chain Evolution Harnessing The Power BCT SS V today and make your presentation stand out from the rest This slide mentions the key components that constitute a part of blockchain based supply chain ecosystem. It includes decentralized ledger, smart contracts, consensus mechanism, identity management, data encryption and tokenization.
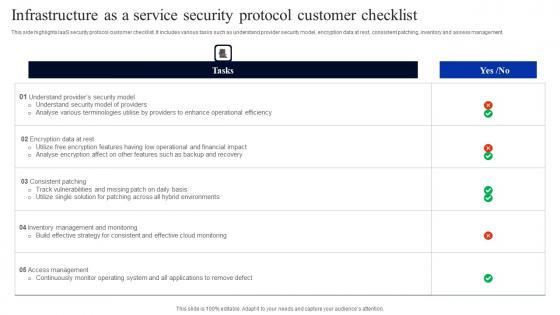
Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf
This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management. Showcasing this set of slides titled Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf. The topics addressed in these templates are Encryption Data Rest, Consistent Patching, Inventory Assess Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management.
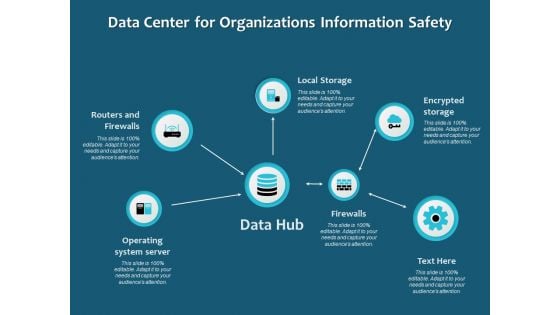
Data Center For Organizations Information Safety Ppt PowerPoint Presentation Infographics Deck PDF
Persuade your audience using this data center for organizations information safety ppt powerpoint presentation infographics deck pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including local storage, encrypted storage, firewalls, operating system server, routers and firewalls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills
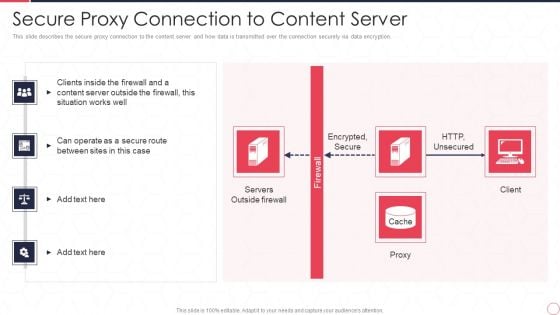
Reverse Proxy Server IT Secure Proxy Connection To Content Server Ppt Gallery Brochure PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Presenting reverse proxy server it secure proxy connection to content server ppt gallery brochure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like encrypted, secure, http, unsecured, servers, outside firewall, proxy, client. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
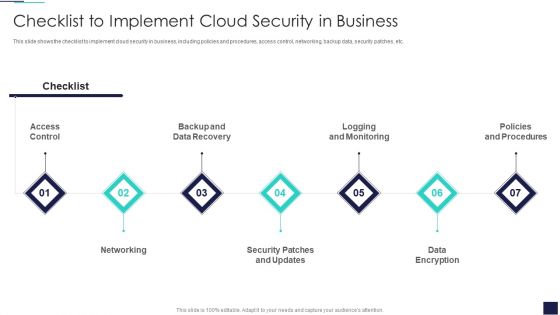
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
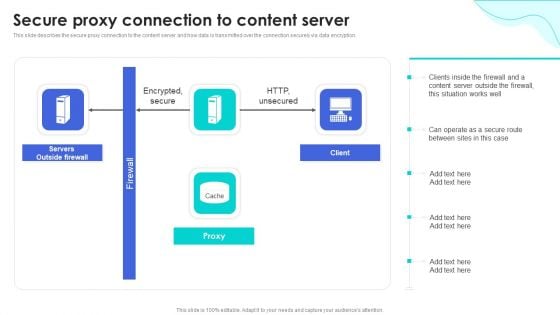
Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Find a pre-designed and impeccable Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
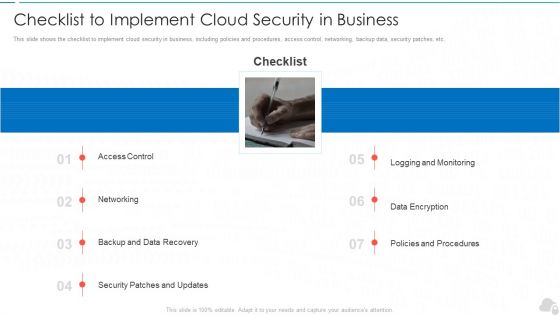
Checklist To Implement Cloud Security In Business Cloud Computing Security IT Ppt Infographic Template Example File
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Deliver an awe inspiring pitch with this creative checklist to implement cloud security in business cloud computing security it ppt infographic template example file bundle. Topics like networking, policies and procedures, logging and monitoring, data encryption, security patches and updates can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Explore a selection of the finest Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc.
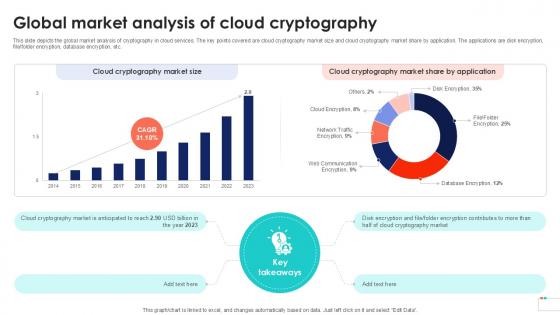
Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file, folder encryption, database encryption, etc. Are you searching for a Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint from Slidegeeks today. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file, folder encryption, database encryption, etc.

Supply Chain Management Iot Application Pre Implementation Audit Checklist Introduction PDF
This slide shows pre implementation audit checklist for internet of things IoT application. It provides information about accuracy, system design, Wi-Fi, real time location service, Bluetooth low energy, transfer method, battery life, data encryption, etc. This is a Supply Chain Management Iot Application Pre Implementation Audit Checklist Introduction PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Parameters, Locate Packages, Iot Systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Best Practices For Cloud Security Topics PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. This is a desktop security management best practices for cloud security topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, management, measures, planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
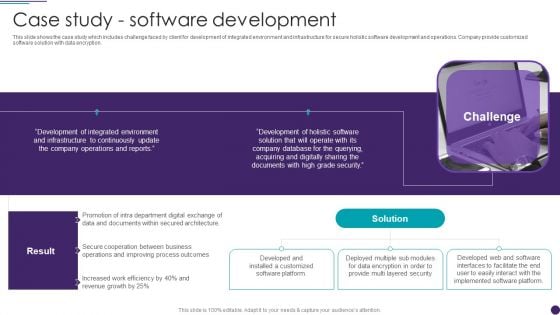
IT Services Business Profile Case Study Software Development Guidelines PDF
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. This is a IT Services Business Profile Case Study Software Development Guidelines PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Environment, Development, Company Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
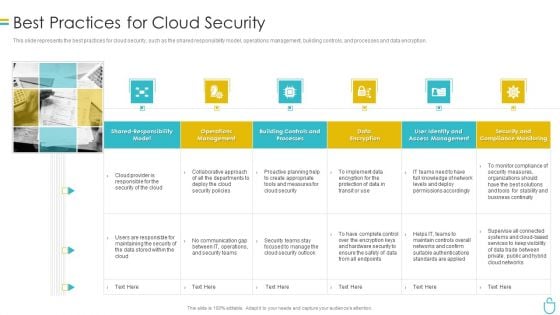
Information Security Best Practices For Cloud Security Ppt Ideas Deck PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting information security best practices for cloud security ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, measures, planning, teams, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Iot Application Pre Implementation Audit Checklist Guidelines PDF
This slide shows pre implementation audit checklist for internet of things IoT application. It provides information about accuracy, system design, Wi Fi, real time location service, Bluetooth low energy, transfer method, battery life, data encryption, etc. Presenting Iot Application Pre Implementation Audit Checklist Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Design System, Location Service, Positioning Accuracy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
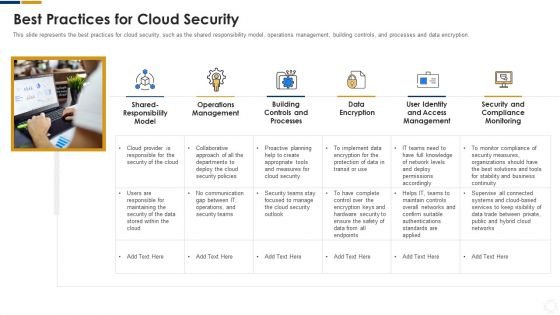
Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
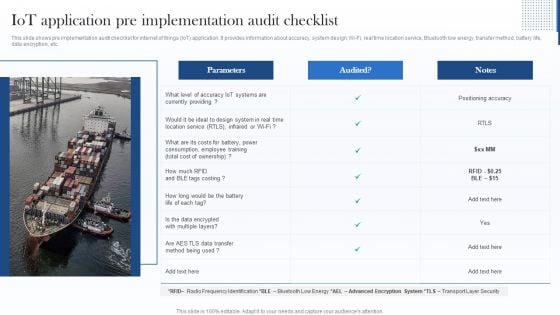
Iot Application Pre Implementation Audit Checklist Download PDF
This slide shows pre implementation audit checklist for internet of things IoT application. It provides information about accuracy, system design, Wi Fi, real time location service, Bluetooth low energy, transfer method, battery life, data encryption, etc. Deliver an awe inspiring pitch with this creative Iot Application Pre Implementation Audit Checklist Download PDF bundle. Topics like Cost Of Ownership, Design System, Method can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Infotech Solutions Research And Development Company Summary Case Study Software Development Summary PDF
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. Presenting Infotech Solutions Research And Development Company Summary Case Study Software Development Summary PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Challenge, Solution, Result. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Supply Chain Management Timeline Deploying Iot Into Logistics Department Diagrams PDF
This slide depicts logistics internet of things IoT deployment timeline. It includes details such as technologies, devices, prototypes, gateways, operating system, network connections, data encryption, pallets, fleet, training, user acceptance testing, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Timeline Deploying Iot Into Logistics Department Diagrams PDF. Use them to share invaluable insights on Planning And Research, Evaluating Current Technologies, Choosing Operating System and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
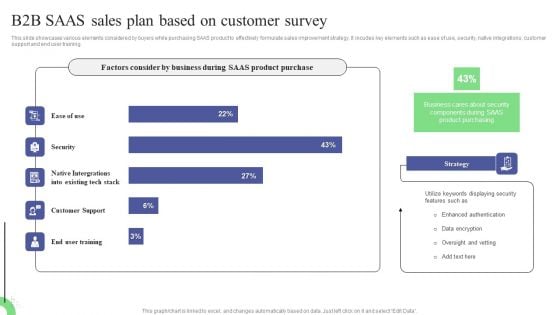
B2B SAAS Sales Plan Based On Customer Survey Demonstration PDF
This slide showcases various elements considered by buyers while purchasing SAAS product to effectively formulate sales improvement strategy. It incudes key elements such as ease of use, security, native integrations, customer support and end user training. Showcasing this set of slides titled B2B SAAS Sales Plan Based On Customer Survey Demonstration PDF. The topics addressed in these templates are Data Encryption, Displaying Security, Strategy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
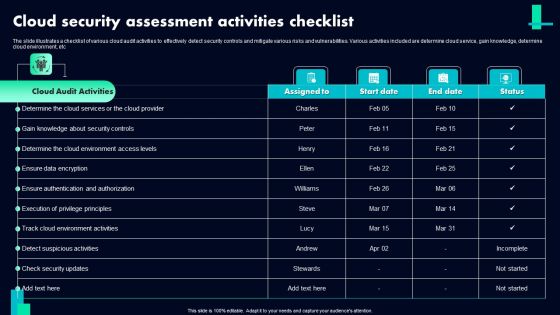
Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF
The slide illustrates a checklist of various cloud audit activities to effectively detect security controls and mitigate various risks and vulnerabilities. Various activities included are determine cloud service, gain knowledge, determine cloud environment, etc. Showcasing this set of slides titled Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF. The topics addressed in these templates are Cloud Audit Activities, Ensure Data Encryption, Detect Suspicious Activities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
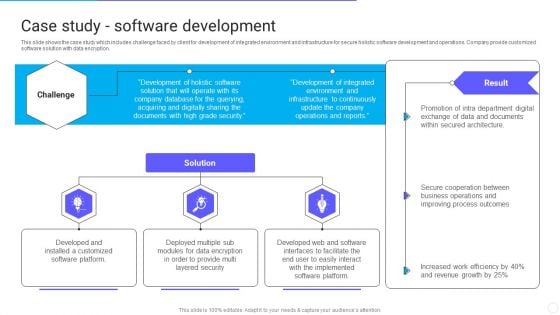
IT Application Services Company Outline Case Study Software Development Infographics PDF
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. Presenting IT Application Services Company Outline Case Study Software Development Infographics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Layered Security, Implemented, Developed Web. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
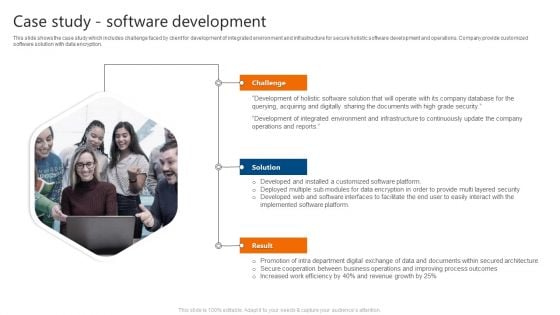
Case Study Software Development IT Software Development Company Profile Microsoft PDF
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. Presenting Case Study Software Development IT Software Development Company Profile Microsoft PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Development, Company, Process Outcomes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Iot Application Pre Implementation Audit Checklist Topics PDF
This slide shows pre implementation audit checklist for internet of things IoT application. It provides information about accuracy, system design, Wi-Fi, real time location service, Bluetooth low energy, transfer method, battery life, data encryption, etc. Create an editable Iot Application Pre Implementation Audit Checklist Topics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Iot Application Pre Implementation Audit Checklist Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cybersecurity And Hacking Incidents In ABS Healthcare Company Ppt Styles Inspiration PDF
This slide shows the graph of total number of Cybersecurity and Hacking Incidents in ABS Healthcare Company from the year 2017 to 2021. Additionally, it provides key insights growth rate, key recommendation, reasons etc. related to growing cybersecurity and hacking incidents. Deliver and pitch your topic in the best possible manner with this cybersecurity and hacking incidents in ABS healthcare company ppt styles inspiration pdf. Use them to share invaluable insights on protection, data encryption, cybersecurity, 2017 to 2021 and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
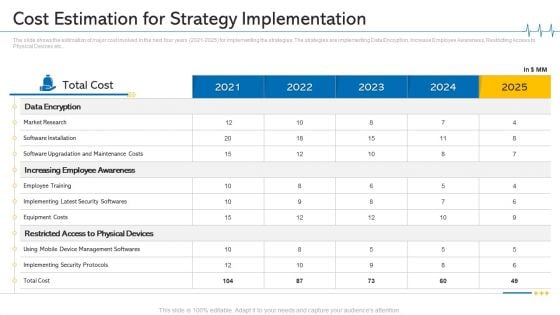
Minimize Cloud Risks Medical Care Business Case Competition Cost Estimation For Strategy Implementation Designs PDF
The slide shows the estimation of major cost involved in the next four years 2021-2025 for implementing the strategies. The strategies are implementing Data Encryption, Increase Employee Awareness, Restricting Access to Physical Devices etc. Deliver an awe inspiring pitch with this creative minimize cloud risks medical care business case competition cost estimation for strategy implementation designs pdf bundle. Topics like market research, equipment costs, implementing security protocols, 2021 to 2025 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cost Estimation For Strategy Implementation Ppt Pictures Graphics Tutorials PDF
The slide shows the estimation of major cost involved in the next four years 2021 to 2025 for implementing the strategies. The strategies are implementing Data Encryption, Increase Employee Awareness, Restricting Access to Physical Devices etc. Deliver an awe inspiring pitch with this creative cost estimation for strategy implementation ppt pictures graphics tutorials pdf bundle. Topics like market research, software installation, equipment costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
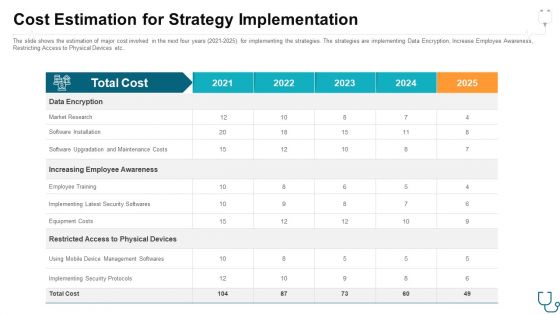
Cost Estimation For Strategy Implementation Ppt Gallery Images PDF
The slide shows the estimation of major cost involved in the next four years 2021 2025 for implementing the strategies. The strategies are implementing Data Encryption, Increase Employee Awareness, Restricting Access to Physical Devices etc. Deliver and pitch your topic in the best possible manner with this cost estimation for strategy implementation ppt gallery images pdf. Use them to share invaluable insights on market research, software installation, employee training, equipment costs, total cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
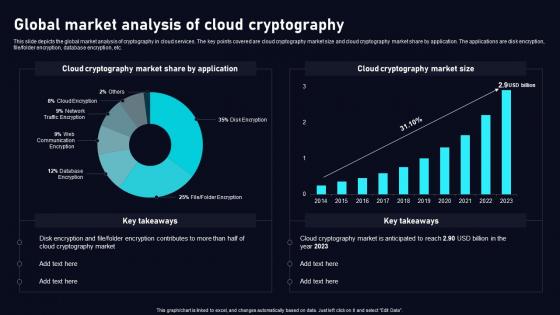
Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc. Do you know about Slidesgeeks Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc.
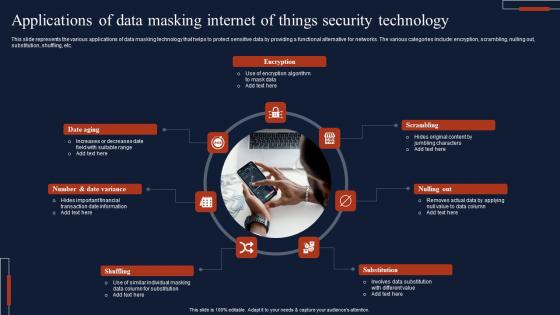
Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc.

Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf
This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum safe cryptography, secure multi party computation, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Emerging Trends In Cryptographic Cloud Data Security Using Cryptography Rules Pdf. This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum safe cryptography, secure multi party computation, etc.
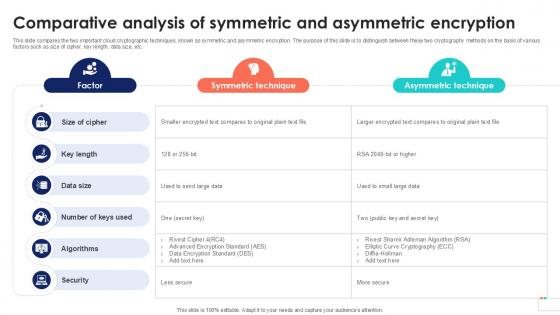
Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.

Revenue Streams Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers the pricing model for the software company. It includes information about various pricing plans which include facilities such as HIPAA compliant email encryption, inbound emails, inbound mail security protection. This modern and well-arranged Revenue Streams Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide covers the pricing model for the software company. It includes information about various pricing plans which include facilities such as HIPAA compliant email encryption, inbound emails, inbound mail security protection.

Our Solution Email And Data Protection Platform Capital Funding Pitch Deck PPT Sample
This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA-compliant email encryption. Make sure to capture your audiences attention in your business displays with our gratis customizable Our Solution Email And Data Protection Platform Capital Funding Pitch Deck PPT Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA-compliant email encryption.
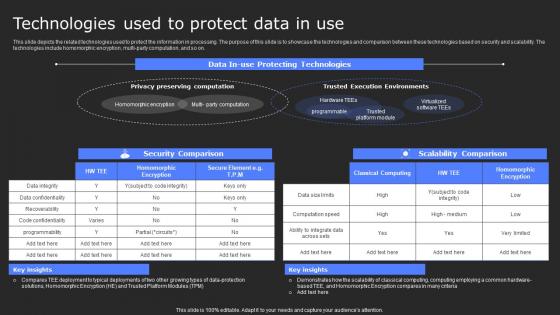
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Boost your pitch with our creative Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
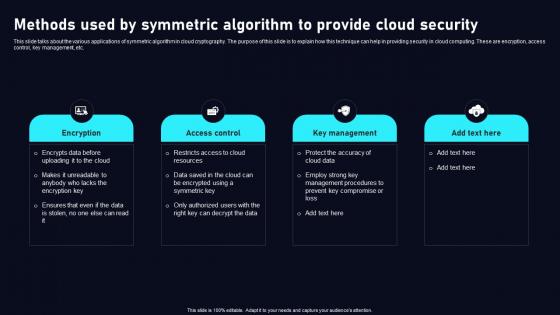
Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.
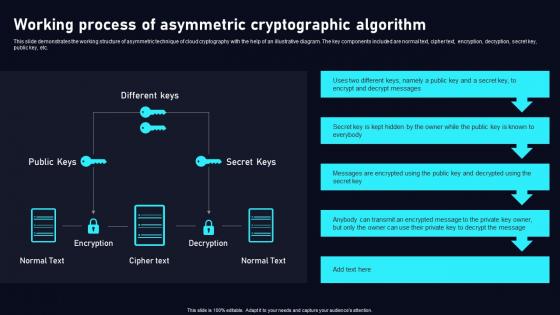
Working Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulateWorking Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.
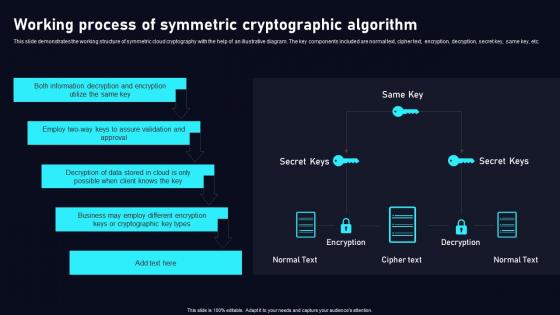
Working Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Want to ace your presentation in front of a live audience OurWorking Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.
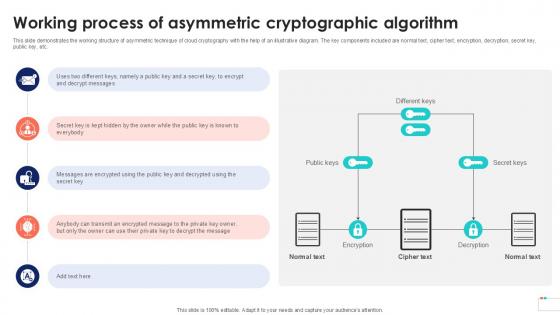
Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.
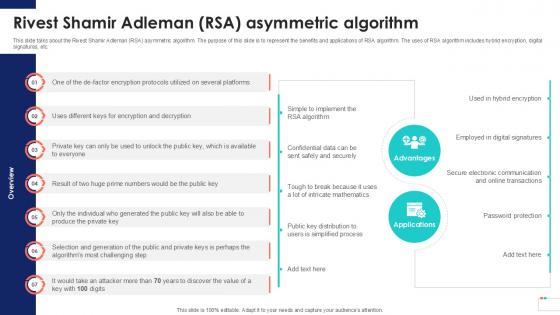
Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Want to ace your presentation in front of a live audience Our Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.
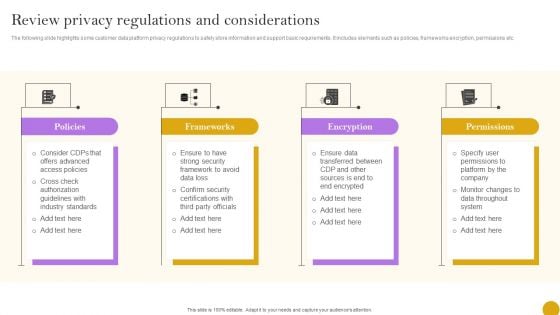
Comprehensive Customer Data Platform Guide Optimizing Promotional Initiatives Review Privacy Regulations Considerations Ideas PDF
The following slide highlights some customer data platform privacy regulations to safely store information and support basic requirements. It includes elements such as policies, frameworks encryption, permissions etc. There are so many reasons you need a Comprehensive Customer Data Platform Guide Optimizing Promotional Initiatives Review Privacy Regulations Considerations Ideas PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Secure Sockets Layer SSL Proxy Server And Its Architecture Reverse Proxy For Load Balancing Brochure PDF
This slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server.Deliver and pitch your topic in the best possible manner with this Secure Sockets Layer SSL Proxy Server And Its Architecture Reverse Proxy For Load Balancing Brochure PDF. Use them to share invaluable insights on Data Encrypted, Suitable Businesses, Security Against and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Science Tools For Data Science Sas Ppt PowerPoint Presentation Infographics Graphic Images PDF
This slide describes the Statistical Analysis System used in data science for data management and modeling. It includes robust data, SAS studio, various data types support, and data encryption.This is a Information Science Tools For Data Science Sas Ppt PowerPoint Presentation Infographics Graphic Images PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Proprietary Software, Statistical Modeling, Data Scientists. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
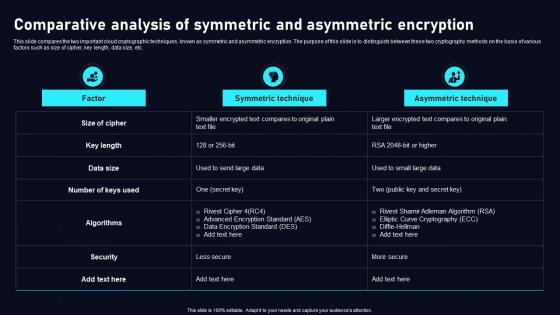
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.

Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Do you know about Slidesgeeks Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls.
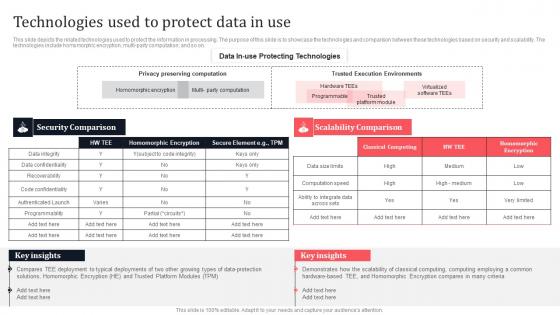
Technologies Used To Protect Data In Use Secure Multi Party Template Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Technologies Used To Protect Data In Use Secure Multi Party Template Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Technologies Used To Protect Data In Use Secure Multi Party Template Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.


 Continue with Email
Continue with Email

 Home
Home


































