Data Protection

Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf
This slide illustrate Cyber security incident communication plan flowchart across various members. It includes elements such as technical coordinator, incident manager, support coordinator, business owner and forensic partner Showcasing this set of slides titled Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf The topics addressed in these templates are Technical Coordinator, Incident Manager, Support Coordinator All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrate Cyber security incident communication plan flowchart across various members. It includes elements such as technical coordinator, incident manager, support coordinator, business owner and forensic partner
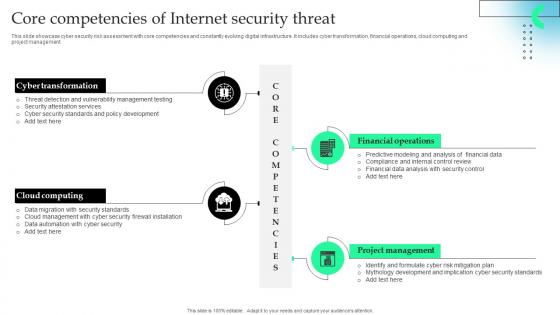
Core Competencies Of Internet Security Threat Portrait Pdf
This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.Showcasing this set of slides titled Core Competencies Of Internet Security Threat Portrait Pdf The topics addressed in these templates are Cyber Transformation, Cloud Computing, Financial Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.

Email Locked Confidential Information Security PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Email Locked Confidential Information Security PowerPoint Templates PPT Backgrounds For Slides 0313.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Use our Services PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download our Business PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides have the Brilliant backdrops. Guaranteed to illuminate the minds of your audience.Use these PowerPoint slides for presentations relating to Locked envelope with key security, security, services, technology, business, shapes. The prominent colors used in the PowerPoint template are Green, Black, Blue light. Our Email Locked Confidential Information Security PowerPoint Templates Ppt Backgrounds For Slides 0313 are apt for any age. They are an excellent device to educate anyone
PowerPoint Designs Corporate Strategy Swot Analysis Ppt Themes
PowerPoint Designs Corporate Strategy swot analysis PPT Themes-These high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Empower yourself with our PowerPoint Designs Corporate Strategy Swot Analysis Ppt Themes. Put extra force behind your thoughts.

IoT Device Management Fundamentals Key Factors For Selecting Right IoT Device Management IoT Ss V
This slide exhibits specific factors to consider for selecting an IoT device management platform. These factors include connectivity management, scalability, security, and ability to adapt technological changes. The IoT Device Management Fundamentals Key Factors For Selecting Right IoT Device Management IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide exhibits specific factors to consider for selecting an IoT device management platform. These factors include connectivity management, scalability, security, and ability to adapt technological changes.
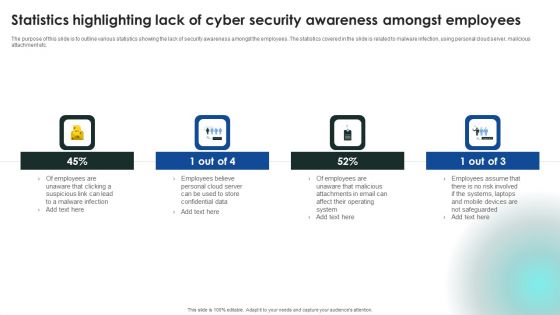
Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V
This slide shows information regarding various types of threats associated with Bitcoins security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V. This slide shows information regarding various types of threats associated with Bitcoins security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.
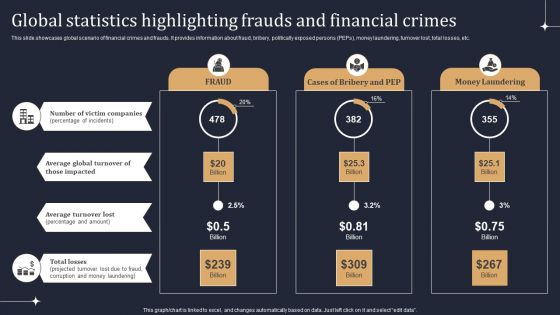
KYC Transaction Monitoring System Business Security Global Statistics Highlighting Frauds Diagrams PDF
This slide showcases global scenario of financial crimes and frauds. It provides information about fraud, bribery, politically exposed persons PEPs, money laundering, turnover lost, total losses, etc. Take your projects to the next level with our ultimate collection of KYC Transaction Monitoring System Business Security Global Statistics Highlighting Frauds Diagrams PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
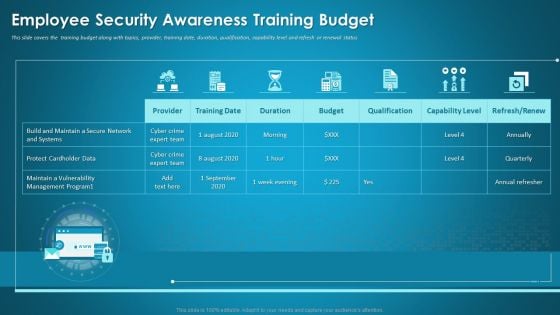
Organizational Network Staff Learning Employee Security Awareness Training Budget Information PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver and pitch your topic in the best possible manner with this organizational network staff learning employee security awareness training budget information pdf. Use them to share invaluable insights on capability level, budget, duration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
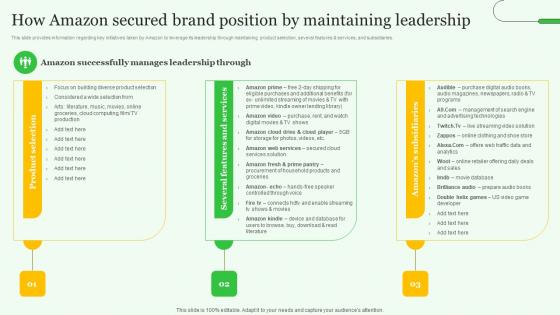
How Amazon Secured Brand Exploring Amazons Global Business Model Growth Topics Pdf
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. This How Amazon Secured Brand Exploring Amazons Global Business Model Growth Topics Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Amazon Secured Brand Exploring Amazons Global Business Model Growth Topics Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries.

Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V
This slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Get a simple yet stunning designed Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today. This slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc.
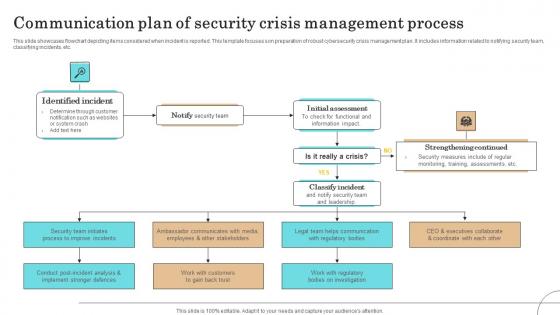
Communication Plan Of Security Crisis Management Process Pictures Pdf
This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.Pitch your topic with ease and precision using this Communication Plan Of Security Crisis Management Process Pictures Pdf This layout presents information on Identified Incident, Initial Assessment, Strengthening Continued It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.
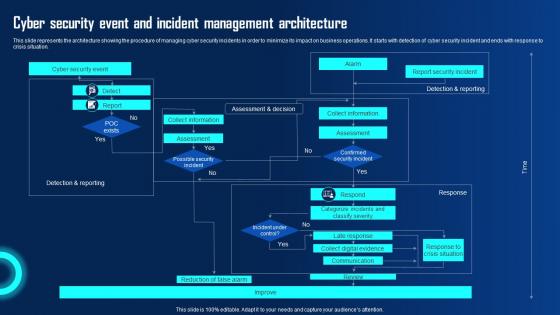
Cyber Security Event And Incident Management Ppt Powerpoint Presentation Diagram Graph Charts Pdf
This slide represents the architecture showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Security Event And Incident Management Ppt Powerpoint Presentation Diagram Graph Charts Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the architecture showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation.
Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.

Electronic Bank Account Technology PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Electronic Bank Account Technology PowerPoint Templates PPT Backgrounds For Slides 1212.Download our Security PowerPoint Templates because this slide can help to bullet point your views. Use our Finance PowerPoint Templates because you can Be the cynosure of all eyes with our template depicting . Present our Computer PowerPoint Templates because your ideas are fundamentally stable with a broad base of workable possibilities. Present our Finance PowerPoint Templates because it Highlights the results of you thought process and convinces your team of the reasons for selecting a particular path to follow. Present our Technology PowerPoint Templates because you can Take your team along by explaining your plans.Use these PowerPoint slides for presentations relating to Electronic bank account, money, security, computer, finance, technology. The prominent colors used in the PowerPoint template are Green, Blue, Black. Professionals tell us our Electronic Bank Account Technology PowerPoint Templates PPT Backgrounds For Slides 1212 are Vintage. Use our account PowerPoint templates and PPT Slides are Exuberant. We assure you our Electronic Bank Account Technology PowerPoint Templates PPT Backgrounds For Slides 1212 are Liberated. We assure you our finance PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Presenters tell us our Electronic Bank Account Technology PowerPoint Templates PPT Backgrounds For Slides 1212 are readymade to fit into any presentation structure. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides are Romantic. Teach your team with our Electronic Bank Account Technology PowerPoint Templates Ppt Backgrounds For Slides 1212. Download without worries with our money back guaranteee.
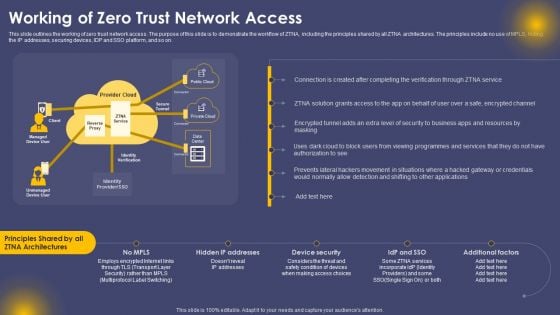
Working Of Zero Trust Network Access Ppt Professional File Formats PDF
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Are you searching for a Working Of Zero Trust Network Access Ppt Professional File Formats PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Working Of Zero Trust Network Access Ppt Professional File Formats PDF from Slidegeeks today.

Cyber Crime Security PowerPoint Themes And PowerPoint Slides 0411
Microsoft PowerPoint Theme and Slide with an open door with hands holding guns surrounded by words like cyber-crime stolen Feel the ' chi ' with our Cyber Crime Security PowerPoint Themes And PowerPoint Slides 0411. Your inner energies will be on the rise.
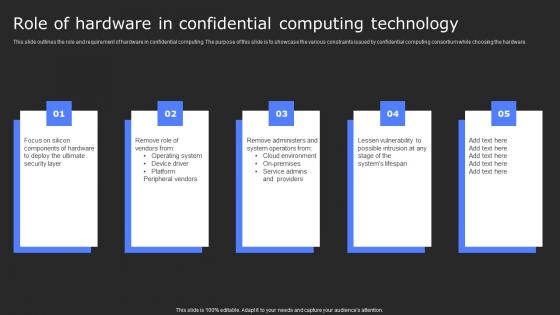
Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Find highly impressive Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.
Contact Us Voice Assistance Security Platform Investor Funding Presentation Download Pdf
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Contact Us Voice Assistance Security Platform Investor Funding Presentation Download Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Our Contact Us Voice Assistance Security Platform Investor Funding Presentation Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
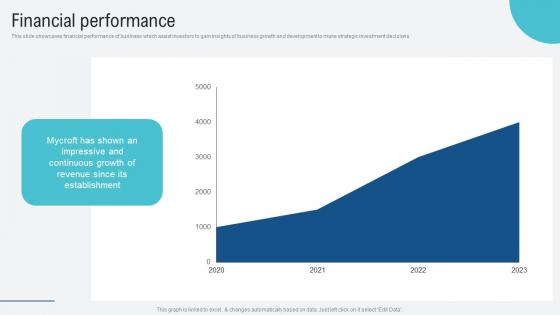
Financial Performance Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf
This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions. Explore a selection of the finest Financial Performance Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Financial Performance Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions.

Laptop With Lock Internet Security PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112.Download and present our Technology PowerPoint Templates because we provide the means to project your views. Download and present our Business PowerPoint Templates because this template can project the path to sucess that you have charted. Use our Security PowerPoint Templates because you can Explore the various hues and layers existing in your in your plans and processes using this slide. Use our Computer PowerPoint Templates because it demonstrates the seeds of many of our successes. Download and present our Shapes PowerPoint Templates because the Gear train is a basic element of living and daily business.Use these PowerPoint slides for presentations relating to Lock laptop keyboard safety security on the internet, technology, Security, business, shapes, computer. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. People tell us our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112 are Flirty. Presenters tell us our technology PowerPoint templates and PPT Slides are Pretty. PowerPoint presentation experts tell us our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112 provide great value for your money. Be assured of finding the best projection to highlight your words. Customers tell us our on PowerPoint templates and PPT Slides are Reminiscent. Customers tell us our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112 are Fantastic. Customers tell us our security PowerPoint templates and PPT Slides are Stunning. Develop their craving for your creativity. Become a brand name with our Laptop With Lock Internet Security PowerPoint Templates Ppt Backgrounds For Slides 1112.
Icons Slide For Info Security Ppt PowerPoint Presentation File Graphics Download PDF
Download our innovative and attention grabbing icons slide for info security ppt powerpoint presentation file graphics download pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

Safety First Concept Business Security PowerPoint Templates And PowerPoint Themes 1112
We present our Safety First Concept Business Security PowerPoint Templates And PowerPoint Themes 1112.Use our Computer PowerPoint Templates because, Emphasise on any critical or key factors within them. Use our Technology PowerPoint Templates because,And watch them strenthen your companys sinews. Use our Business PowerPoint Templates because,Show them how you can save the day. Use our Internet PowerPoint Templates because, Set out the goals and your plan of action for them. Use our Security PowerPoint Templates because, Clarity of thought has been the key to your growth.Use these PowerPoint slides for presentations relating to Safety first concept, computer, technology, business, internet, security . The prominent colors used in the PowerPoint template are Red, White, Black Index your ascent with our Safety First Concept Business Security PowerPoint Templates And PowerPoint Themes 1112. Illustrate every step of the way.
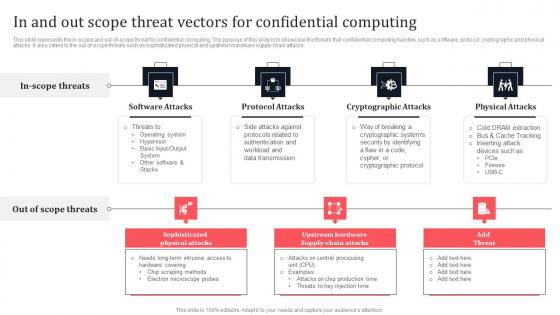
In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.
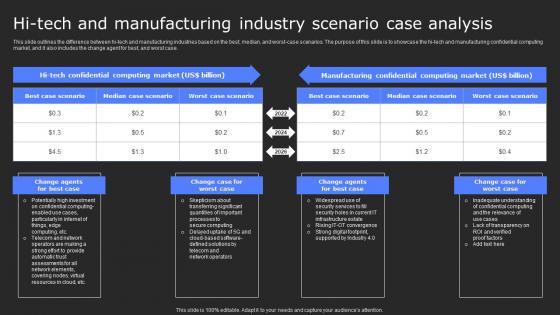
Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.

Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V
This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc.
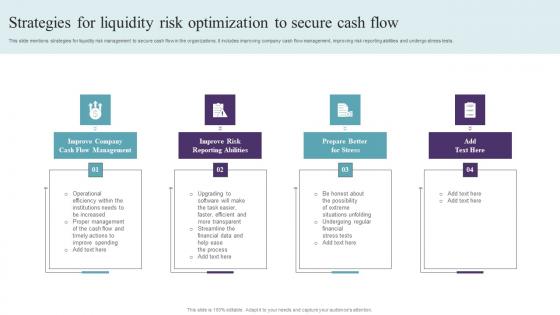
Strategies For Liquidity Risk Optimization To Secure Cash Flow Themes Pdf
This slide mentions strategies for liquidity risk management to secure cash flow in the organizations. It includes improving company cash flow management, improving risk reporting abilities and undergo stress tests. Pitch your topic with ease and precision using this Strategies For Liquidity Risk Optimization To Secure Cash Flow Themes Pdf. This layout presents information on Improve Risk Reporting Abilities, Prepare Better For Stress. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide mentions strategies for liquidity risk management to secure cash flow in the organizations. It includes improving company cash flow management, improving risk reporting abilities and undergo stress tests.
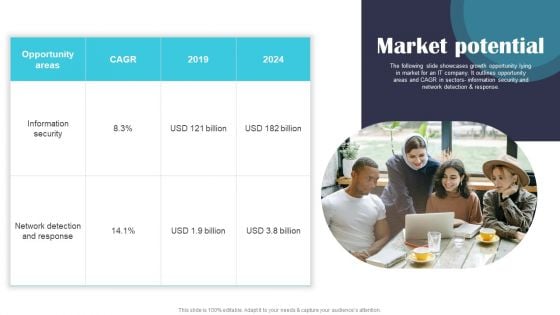
Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF
The following slide showcases growth opportunity lying in market for an IT company. It outlines opportunity areas and CAGR in sectors information security and network detection and response. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
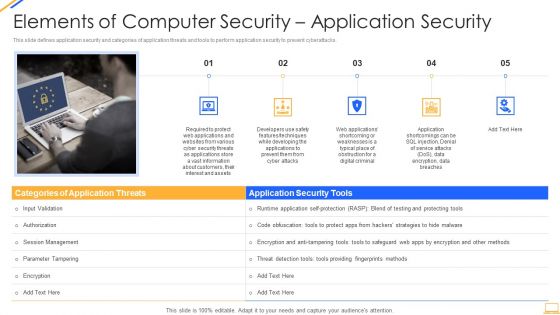
Desktop Security Management Elements Of Computer Security Application Security Download PDF
This is a desktop security management elements of computer security application security download pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, security, customers, required. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf
This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector. Explore a selection of the finest Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector.

Secure Your Business Mails PowerPoint Templates Ppt Backgrounds For Slides 0713
Our Secure Your Business Mails PowerPoint Templates PPT Backgrounds For Slides will will follow the drill. They accomplish the task assigned to them. Do the drill with our Security PowerPoint Templates. Your ideas will march ahead. Place the orders with your thoughts. Our People PowerPoint Templates know the drill. Achieve productivity improvement with our Secure Your Business Mails PowerPoint Templates Ppt Backgrounds For Slides 0713. They will make you look good.

Security Information And Event Management Strategies For Financial Audit And Compliance Next Evolution Of Siem Software Download PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting security information and event management strategies for financial audit and compliance next evolution of siem software download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like user entity and behavior analytics, network traffic analysis, endpoint monitoring, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Wireless Network Security System Smart Lock Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this wireless network security system smart lock ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
Smart Radio Military And Security Applications Icon Structure Pdf
Pitch your topic with ease and precision using this Smart Radio Military And Security Applications Icon Structure Pdf. This layout presents information on Smart Radio Military, Security Applications Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Smart Radio Military And Security Applications Icon Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF
Showcasing this set of slides titled Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF. The topics addressed in these templates are Endpoint Security, Network Security, Messaging Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents Cyber Security Administration In Organization Security Sample PDF
This is a table of contents cyber security administration in organization security sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring, financial, assets, security, workforce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Complete Beginners Guide Key Features Of Good Cryptocurrency Exchange Fin SS V
This slide shows information regarding the characteristics cryptocurrency exchange which can be used by individuals or businesses to select good exchanges. These features includes security, user friendly interface, etc. The Complete Beginners Guide Key Features Of Good Cryptocurrency Exchange Fin SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide shows information regarding the characteristics cryptocurrency exchange which can be used by individuals or businesses to select good exchanges. These features includes security, user friendly interface, etc.

Lockable Informative Laptop PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Lockable Informative Laptop PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Download and present our Security PowerPoint Templates because You are well armed with penetrative ideas. Our PowerPoint Templates and Slides will provide the gunpowder you need. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime. Present our Shapes PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides.Use these PowerPoint slides for presentations relating to Notebook Lockable, computer, technology, security, signs, shapes. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Dont create mammoth presentations. Be clear and succinct with our Lockable Informative Laptop PowerPoint Templates Ppt Backgrounds For Slides 0313. You'll always stay ahead of the game.
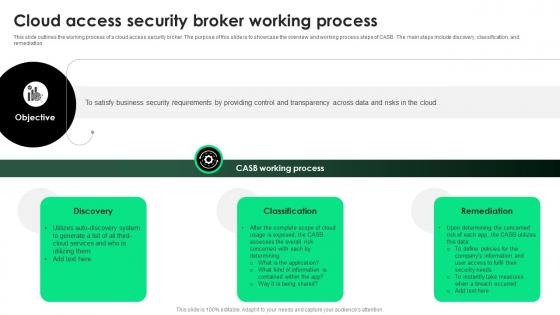
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.

Products And Services Offered Manufacturing Control Software Company Investor PPT Template
This slide caters to details related to a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Manufacturing Control Software Company Investor PPT Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide caters to details related to a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights.
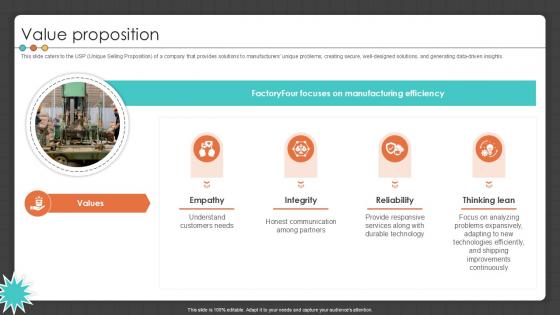
Value Proposition Manufacturing Control Software Company Investor PPT Template
This slide caters to the USP Unique Selling Proposition of a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights. Explore a selection of the finest Value Proposition Manufacturing Control Software Company Investor PPT Template here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Value Proposition Manufacturing Control Software Company Investor PPT Template to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide caters to the USP Unique Selling Proposition of a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights.

Laptop With Pair Of Keys Security PowerPoint Templates And PowerPoint Themes 0812
Laptop With Pair Of Keys Security PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with a pair of keys and a laptop Bet on your assets coming good for you. Sign the cheque with our Laptop With Pair Of Keys Security PowerPoint Templates And PowerPoint Themes 0812.

Computer Folder With Key Security PowerPoint Templates And PowerPoint Themes 0912
Computer Folder With Key Security PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with folder with key Our Computer Folder With Key Security PowerPoint Templates And PowerPoint Themes 0912 get you a promotion. With our money back guarantee you have nothing to lose.

Application Security Case Study Kroll Application Security Testing
This slide highlights the overview of the company, problems faced, and their related solutions in the case study. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Application Security Case Study Kroll Application Security Testing for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights the overview of the company, problems faced, and their related solutions in the case study.
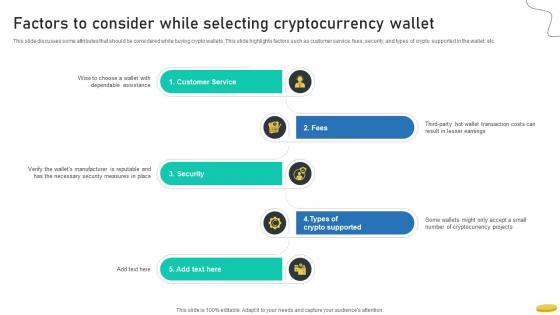
Factors To Consider While Selecting Cryptocurrency Wallet Cryptocurrency Management With Blockchain
This slide discusses some attributes that should be considered while buying crypto wallets. This slide highlights factors such as customer service, fees, security, and types of crypto supported in the wallet, etc.The Factors To Consider While Selecting Cryptocurrency Wallet Cryptocurrency Management With Blockchain is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide discusses some attributes that should be considered while buying crypto wallets. This slide highlights factors such as customer service, fees, security, and types of crypto supported in the wallet, etc.
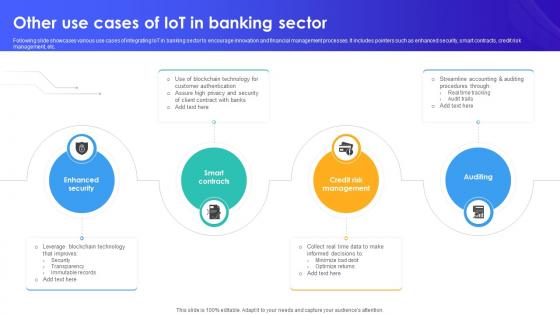
Other Use Cases Of IoT In Banking Sector IoT In Banking For Digital Future IoT SS V
Following slide showcases various use cases of integrating IoT in banking sector to encourage innovation and financial management processes. It includes pointers such as enhanced security, smart contracts, credit risk management, etc. The Other Use Cases Of IoT In Banking Sector IoT In Banking For Digital Future IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Following slide showcases various use cases of integrating IoT in banking sector to encourage innovation and financial management processes. It includes pointers such as enhanced security, smart contracts, credit risk management, etc.

Laptop With Lock And Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Internet PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Download and present our Computer PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Use our Technology PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas.Use these PowerPoint slides for presentations relating to Computer security concept, computer, internet, success, technology, security. The prominent colors used in the PowerPoint template are Brown, Black, Gray. People tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. People tell us our security PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. PowerPoint presentation experts tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are incredible easy to use. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Presenters tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. The feedback we get is that our technology PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Examine the causes with our Laptop With Lock And Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Let everyone know what's behind it all.

Our Proposed Network Architecture For Firewall Migration Proposal
This slide represents the proposed network architecture for the firewall migration proposal. It shows the network architecture after migrating to a new firewall solution, and its components include workstation PCs, internal switch, directory server, internet, internal and external firewalls, etc.Power up your presentations with our Our Proposed Network Architecture For Firewall Migration Proposal single-slide PPT template. Our visually-stunning template will help you deliver your message with confidence. With easy-to-use editing options and fully customizable features, you can create polished and captivating presentations in no time. Say goodbye to boring slides and hello to impactful presentations with our top-quality template. Download now and get ready to wow your audience. singles This slide represents the proposed network architecture for the firewall migration proposal. It shows the network architecture after migrating to a new firewall solution, and its components include workstation PCs, internal switch, directory server, internet, internal and external firewalls, etc.

Types Of Access Control In Application Security Testing Ppt Powerpoint Topics
This slide outlines the different types of access control safeguards in application security which include Role-based Access Control RBAC, Access Control Lists, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Types Of Access Control In Application Security Testing Ppt Powerpoint Topics to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Types Of Access Control In Application Security Testing Ppt Powerpoint Topics. This slide outlines the different types of access control safeguards in application security which include Role-based Access Control RBAC, Access Control Lists, etc.
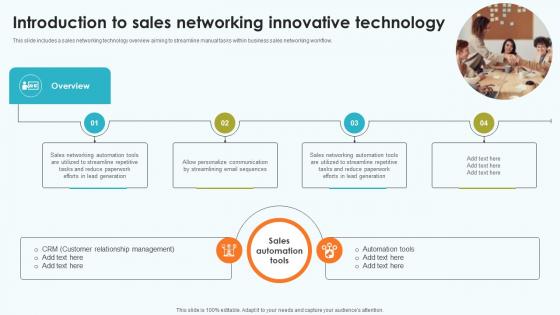
Elevating Sales Networks Introduction To Sales Networking Innovative Technology SA SS V
This slide includes a sales networking technology overview aiming to streamline manual tasks within business sales networking workflow. Retrieve professionally designed Elevating Sales Networks Introduction To Sales Networking Innovative Technology SA SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide includes a sales networking technology overview aiming to streamline manual tasks within business sales networking workflow.
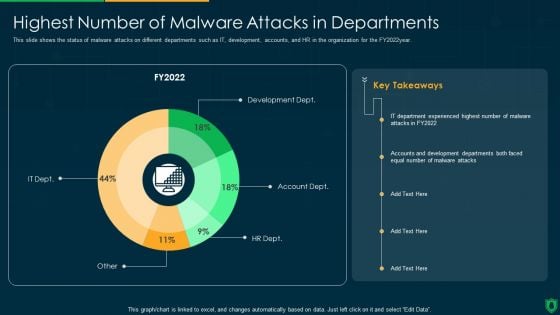
Info Security Highest Number Of Malware Attacks In Departments Ppt PowerPoint Presentation Gallery Format PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022year. Deliver an awe inspiring pitch with this creative info security highest number of malware attacks in departments ppt powerpoint presentation gallery format pdf bundle. Topics like development dept, account dept, hr dept, it dept can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
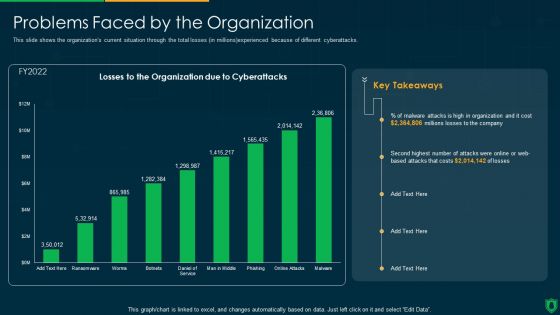
Info Security Problems Faced By The Organization Ppt PowerPoint Presentation File Slide PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this info security problems faced by the organization ppt powerpoint presentation file slide pdf. Use them to share invaluable insights on losses organization, due cyberattacks, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
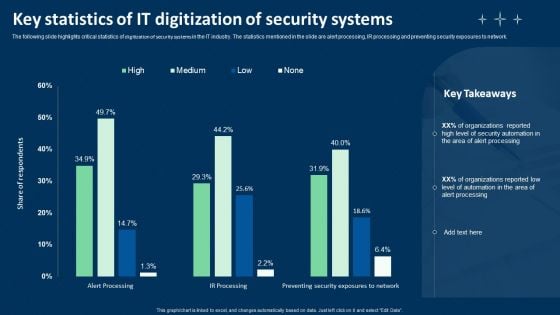
Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure, Code Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Yellow Computer Folder With Golden Key Security PowerPoint Templates And PowerPoint Themes 1112
We present our Yellow Computer Folder With Golden Key Security PowerPoint Templates And PowerPoint Themes 1112.Use our Computer PowerPoint Templates because, Tachometer:- You have a good idea of the roadmap to your desired destination. Use our Internet PowerPoint Templates because, Display your ideas and highlight thei ability to accelerate the the growth of your company and you. Use our Communication PowerPoint Templates because,Explain the process by which you intend to right it. Use our Security PowerPoint Templates because, Build on your foundation or prepare for change ahead to enhance the future. Use our Symbol PowerPoint Templates because, You have the plans to increase the strength of your business relationships.Use these PowerPoint slides for presentations relating to Yellow computer folder with key Internet Security Computer Symbol Communication. The prominent colors used in the PowerPoint template are Yellow, White, Orange Soak in the energy our Yellow Computer Folder With Golden Key Security PowerPoint Templates And PowerPoint Themes 1112 emit. Your thoughts will find them exhilirating.

Digital Wallet Management System For Secure In Depth Guide To Digital Wallets Fin SS V
This slide provides a financial management strategy for businesses with the help of digital wallet integration. The process involves contactless payments with QR codes, collaboration with digital wallet apps, choosing the right payment processing, customer rewards, etc. Find highly impressive Digital Wallet Management System For Secure In Depth Guide To Digital Wallets Fin SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Wallet Management System For Secure In Depth Guide To Digital Wallets Fin SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide provides a financial management strategy for businesses with the help of digital wallet integration. The process involves contactless payments with QR codes, collaboration with digital wallet apps, choosing the right payment processing, customer rewards, etc.
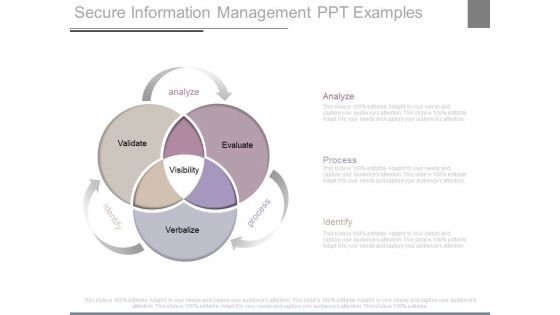
Secure Information Management Ppt Examples
This is a secure information management ppt examples. This is a three stage process. The stages in this process are analyze, process, identify, evaluate, validate, visibility, verbalize.
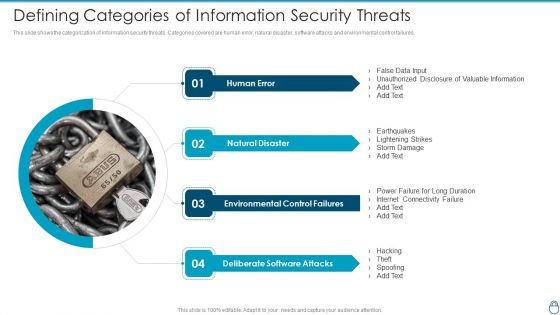
Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.This is a Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disaster, Environmental Control Failures, Deliberate Software Attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
8 Stages Circular Process Flow Diagram Network Marketing Business Plan PowerPoint Slides
We present our 8 stages circular process flow diagram network marketing business plan PowerPoint Slides.Use our Marketing PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team. Use our Finance PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas. Use our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Use our Business PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Use our Targets PowerPoint Templates because You can safely bank on our PowerPoint Templates and Slides. They will provide a growth factor to your valuable thoughts.Use these PowerPoint slides for presentations relating to Pie, chart, network, isolnobody, green, copy, flow, business, sign, render, symbol, diagram, change, circle, finance, data, rendering, process, flowchart, plastic, graphics, shape, computer, graph, cycle, connection, circular, strategy, round, shiny, reflection, solution, design, cylinder, growth, single, financial, 3d. The prominent colors used in the PowerPoint template are Blue, Gray, White. Correct wrongs with our 8 Stages Circular Process Flow Diagram Network Marketing Business Plan PowerPoint Slides. Download without worries with our money back guaranteee.
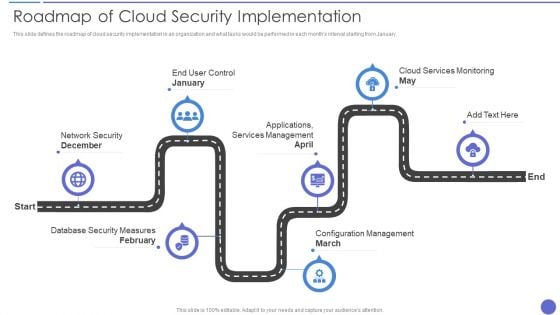
Roadmap Of Cloud Security Implementation Infographics PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Roadmap Of Cloud Security Implementation Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Applications Services Management, Cloud Services Monitoring, Network Security December. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































