Data Protection
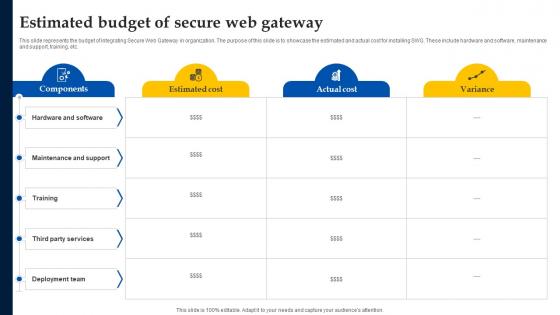
Web Access Control Solution Estimated Budget Of Secure Web Gateway
This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Web Access Control Solution Estimated Budget Of Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Web Access Control Solution Estimated Budget Of Secure Web Gateway. This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc.
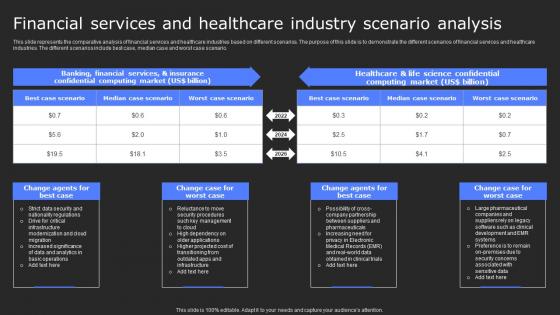
Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. Retrieve professionally designed Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario.
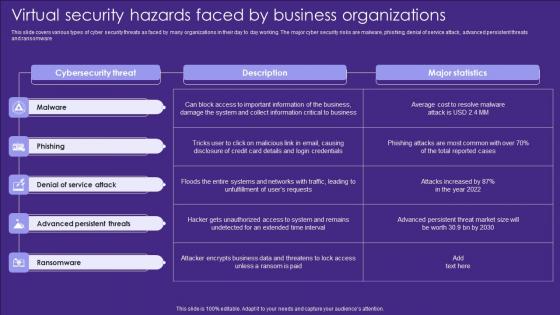
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware
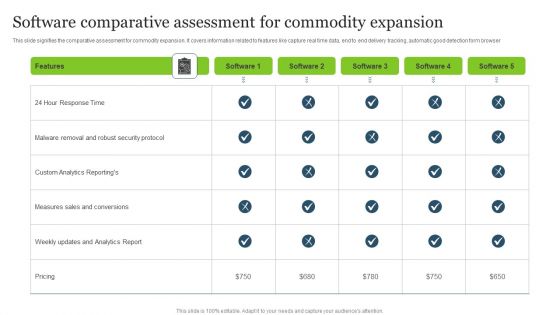
Software Comparative Assessment For Commodity Expansion Microsoft PDF
This slide signifies the comparative assessment for commodity expansion. It covers information related to features like capture real time data, end to end delivery tracking, automatic good detection form browser.Pitch your topic with ease and precision using this Software Comparative Assessment For Commodity Expansion Microsoft PDF. This layout presents information on Malware Removal, Security Protocol, Custom Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
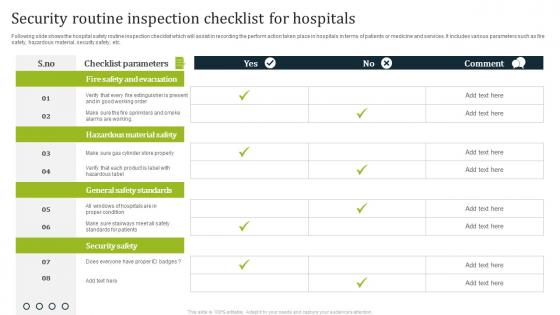
Security Routine Inspection Checklist For Hospitals Diagrams Pdf
Following slide shows the hospital safety routine inspection checklist which will assist in recording the perform action taken place in hospitals in terms of patients or medicine and services. It includes various parameters such as fire safety, hazardous material, security safety, etc. Showcasing this set of slides titled Security Routine Inspection Checklist For Hospitals Diagrams Pdf. The topics addressed in these templates are Checklist Parameters, Comment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the hospital safety routine inspection checklist which will assist in recording the perform action taken place in hospitals in terms of patients or medicine and services. It includes various parameters such as fire safety, hazardous material, security safety, etc.

SIEM Architecture Flowchart SIEM Services Ppt Infographic Template Graphics Download PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a siem architecture flowchart siem services ppt infographic template graphics download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like siem architecture flowchart. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
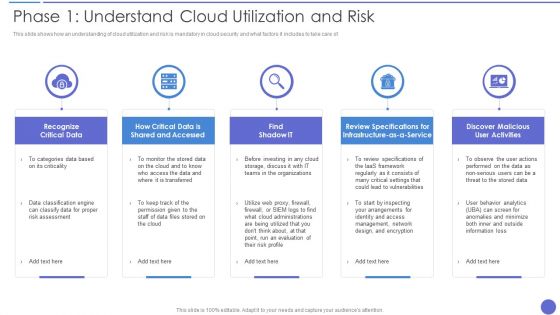
Phase 1 Understand Cloud Utilization And Risk Topics PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. This is a Phase 1 Understand Cloud Utilization And Risk Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Recognize Critical Data, Risk Assessment, Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Our Service And Capabilities For Radio Air Service Marketing Campaign Proposal Formats PDF
This slide represents key services and capabilities for radio air business proposal offered to the client. It covers radio stations, radio networks and digital services. Elevate your presentations with our intuitive Our Service And Capabilities For Radio Air Service Marketing Campaign Proposal Formats PDF template. Whether you are delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression.

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparison Between ITIL V2 And ITIL V3 IT Service Management Framework Structure PDF
This slide represents the difference between ITIL v2 and ITIL v3, based on focus, approach, security management, number of processes, and functions.The Comparison Between ITIL V2 And ITIL V3 IT Service Management Framework Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Network Security Small Business Ppt PowerPoint Presentation Gallery Ideas Cpb
Presenting this set of slides with name network security small business ppt powerpoint presentation gallery ideas cpb. This is an editable Powerpoint ten stages graphic that deals with topics like network security small business to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
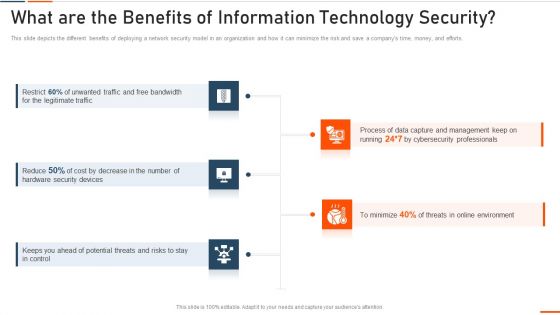
What Are The Benefits Of Information Technology Security Ppt Styles Model PDF
This slide depicts the different benefits of deploying a network security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting what are the benefits of information technology security ppt styles model pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like bandwidth, legitimate, security devices, potential . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
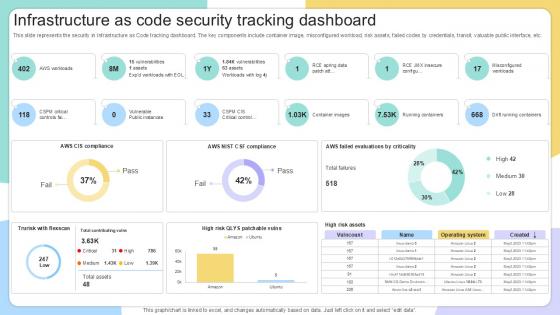
Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide
This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide. This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc.

Importance Of Secure Ecommerce Evaluation And Deployment Of Enhanced Portrait Pdf
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. Welcome to our selection of the Importance Of Secure Ecommerce Evaluation And Deployment Of Enhanced Portrait Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today. This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc.

Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V
This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc.

Telehealth Venture Capitalist Funding Elevator Why Invest On Our Organization Ideas PDF
The following slide displays the key overview of the organization as it provides an overview of the industry verticals such as healthcare, life science, incubators etc. The following also displays the key capabilities of the industries. Deliver an awe inspiring pitch with this creative telehealth venture capitalist funding elevator why invest on our organization ideas pdf bundle. Topics like software, big data, cyber security, organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Devops Deployment And Transformation Services Advisory Solution For System Operations As A People Problem Professional PDF
This slide covers the solution of the problems faced by the clients such as monitoring, containers, metrics, analytics, logs, performance security etc. Elevate your presentations with our intuitive Devops Deployment And Transformation Services Advisory Solution For System Operations As A People Problem Professional PDF template. Whether youre delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percenteditable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression.
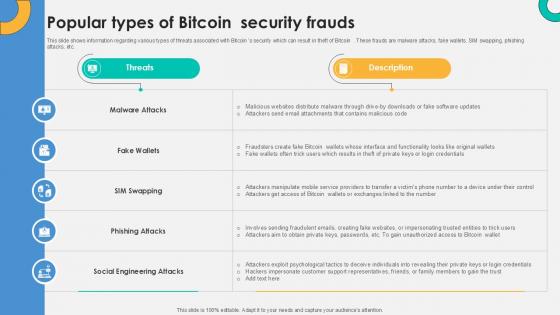
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.

Exploring Investment Opportunities With Security Token Offerings Complete Deck
This seventy nine slide Exploring Investment Opportunities With Security Token Offerings Complete Deck is your content ready tool to impress the stakeholders with your business planning and its manner of execution. Showcase your ideas and how you plan to make them real in detail with this PPT Template Bundle. The slides have the conceptual bandwidth to present the crucial aspects of your plan, such as funding, marketing, resource allocation, timeline, roadmap, and more. When you present your plans with this PPT Layout, the stakeholders are sure to come on board because you will be able to present a succinct, thought-out, winning project. Download this Complete Deck now to take control into your hands. The 100 percent customizable offer is just too good to be resisted. Our Exploring Investment Opportunities With Security Token Offerings Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
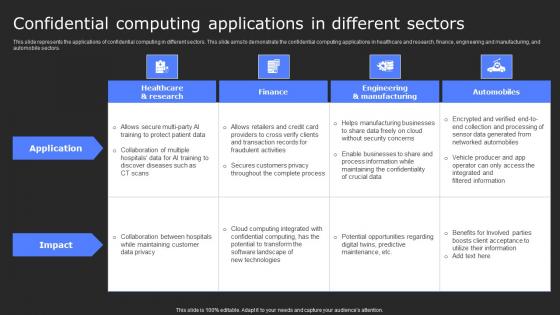
Confidential Computing Applications In Secure Computing Framework Demonstration Pdf
This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Find highly impressive Confidential Computing Applications In Secure Computing Framework Demonstration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Confidential Computing Applications In Secure Computing Framework Demonstration Pdffor your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors.

Application Security Testing Ppt Powerpoint Presentation Complete Deck With Slides

Global Security Industry Report Ppt Presentation IR CD V
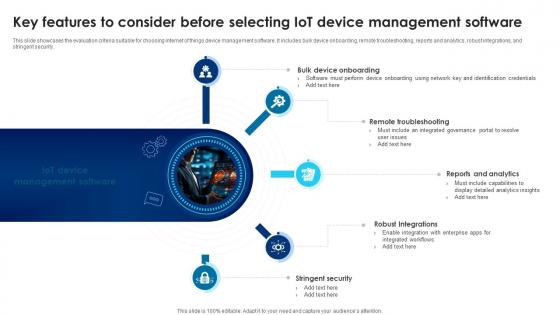
Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V
This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security. Take your projects to the next level with our ultimate collection of Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security.
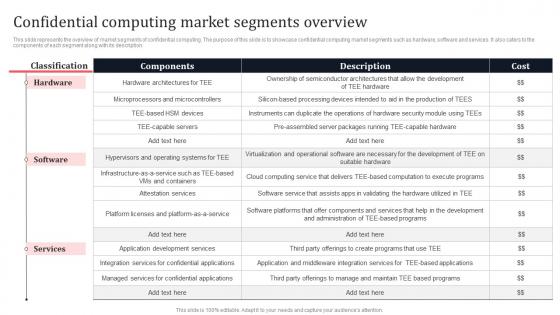
Confidential Computing Market Segments Overview Secure Multi Party Background Pdf
This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing Market Segments Overview Secure Multi Party Background Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing Market Segments Overview Secure Multi Party Background Pdf This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description.
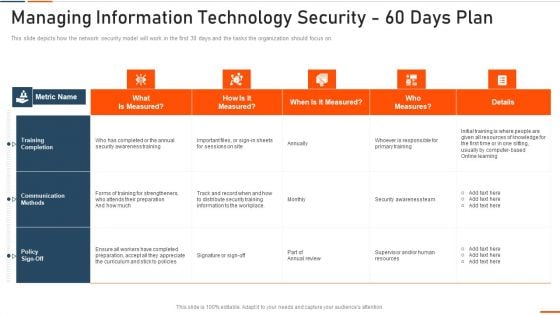
Managing Information Technology Security 60 Days Ppt Infographic Template Samples PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative managing information technology security 60 days ppt infographic template samples pdf bundle. Topics like managing information technology security 60 days plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Workplace Facility Management Services Company Hard And Soft Facility Management Services Mockup PDF
This slide highlights hard and soft facility management services which are offered by the company which includes cleaning services, support services, security services, catering services and technical services. The Workplace Facility Management Services Company Hard And Soft Facility Management Services Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Certified Information Systems Security Professional CISSP Examination Details Infographics PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. This is a Certified Information Systems Security Professional CISSP Examination Details Infographics PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirements, Network Security, Risk Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
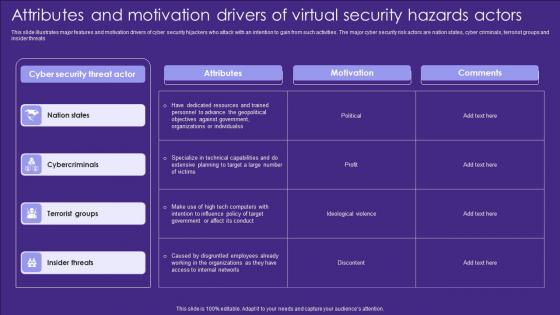
Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf
This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats Showcasing this set of slides titled Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf. The topics addressed in these templates are Attributes, Motivation, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
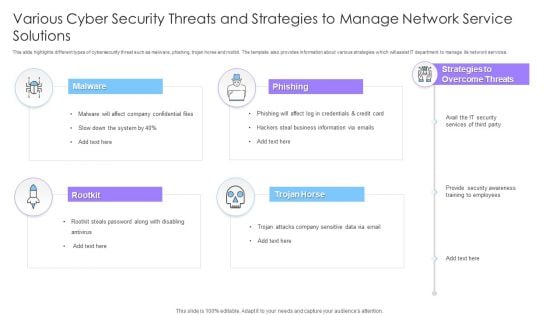
Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V
This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery. There are so many reasons you need a Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery.

Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf
This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities.
Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf
Slidegeeks has constructed Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. Our Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
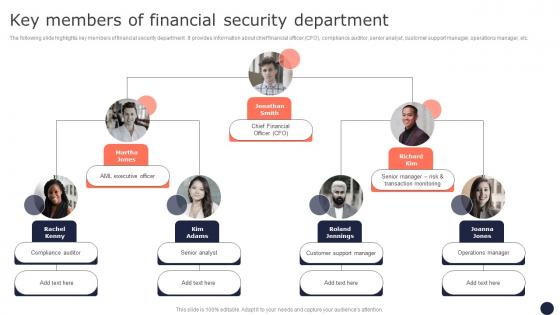
Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc.

Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides
This Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing thirteen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides PPT slideshow. Our Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides
This Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twenty slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides PPT slideshow. Our Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides
This Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing seventeen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides PPT slideshow. Our Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides
This Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas,vision,thoughts,etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in house and outside presentations depending upon your needs and business demands. Entailing seventeen slides with a consistent design and theme,this template will make a solid use case. As it is intuitively designed,it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color,design,shapes,and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well thought and crafted presentation can be delivered with ease and precision by downloading this Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow. Our Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Agenda For Exploring Investment Opportunities With Security Token Offerings Designs Pdf
Boost your pitch with our creative Agenda For Exploring Investment Opportunities With Security Token Offerings Designs Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Agenda For Exploring Investment Opportunities With Security Token Offerings Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
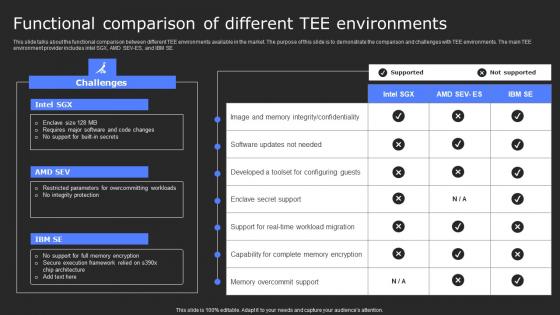
Functional Comparison Of Different Tee Secure Computing Framework Diagrams Pdf
This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes intel SGX, AMD SEV-ES, and IBM SE. Slidegeeks has constructed Functional Comparison Of Different Tee Secure Computing Framework Diagrams Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes intel SGX, AMD SEV-ES, and IBM SE.
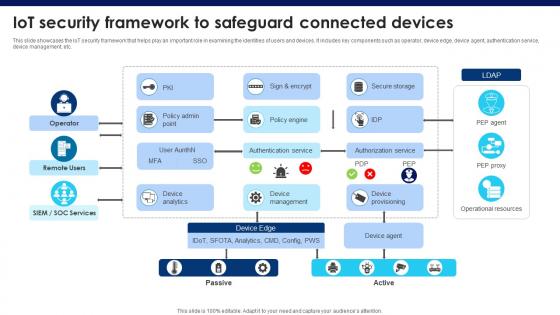
Building Trust With IoT Security IoT Security Framework To Safeguard Connected Devices IoT SS V
This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc. This Building Trust With IoT Security IoT Security Framework To Safeguard Connected Devices IoT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc.

Checklist For Inspecting Office Security To Ensure Employees Portrait Pdf
Following slide shows checklist for office safety inspection to assure staff which will assist in reducing employee turnover because of work environment. It includes major parameters such as housekeeping, ergonomics, electricals, etc. Showcasing this set of slides titled Checklist For Inspecting Office Security To Ensure Employees Portrait Pdf. The topics addressed in these templates are Satisfactory, Unsatisfactory, Checklist Parameters. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows checklist for office safety inspection to assure staff which will assist in reducing employee turnover because of work environment. It includes major parameters such as housekeeping, ergonomics, electricals, etc.
Food Security Checklist To Fulfill Customer Standards Icons Pdf
Following slide shows the food safety check list to satisfy consumer requirements which will assist in measuring quality standards of food. It includes such as food preparation safety, contamination and frozen food. Showcasing this set of slides titled Food Security Checklist To Fulfill Customer Standards Icons Pdf. The topics addressed in these templates are Parameter, Inspected, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the food safety check list to satisfy consumer requirements which will assist in measuring quality standards of food. It includes such as food preparation safety, contamination and frozen food.

Voice Assistance Security Platform Investor Funding Presentation Complete Deck
This unique Voice Assistance Security Platform Investor Funding Presentation Complete Deck is a compendium of amazing information,actionable ideas on all business issues. The design of the presentation template ensures you have an ample opportunity to pick and choose areas you might want to emphasize. The thirty eight slides in the presentation template or all wonderfully colour coded to and ensure that you can get on with delivering your message with speed,and amazing effectiveness. Talk about management,leadership,change management,digital transformation etc with the unparalleled advantage of 100 percent customization of each and every elements of all our slides. Download now and see presentation take on a new dimension. Our Voice Assistance Security Platform Investor Funding Presentation Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

One Year Career Advancement Strategy Information Pdf
This slide shows detailed comprehensive plan for one year. The purpose of this slide is to highlight essential activities such as set short goals, focus on building networks and stretch your goals for long term vision, etc. Showcasing this set of slides titled One Year Career Advancement Strategy Information Pdf. The topics addressed in these templates are Skills Like, Demonstrate Leadership Skills, Consider Personal Ambitions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows detailed comprehensive plan for one year. The purpose of this slide is to highlight essential activities such as set short goals, focus on building networks and stretch your goals for long term vision, etc.
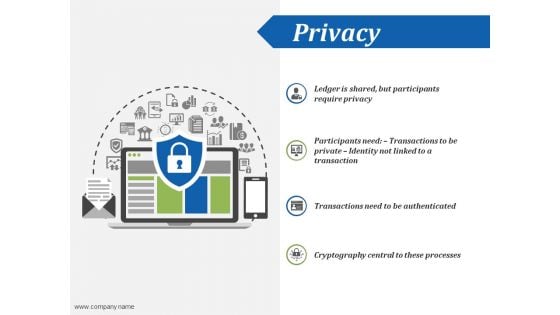
Privacy Ppt PowerPoint Presentation Outline File Formats
This is a privacy ppt powerpoint presentation outline file formats. This is a four stage process. The stages in this process are transactions need to be authenticated, cryptography central to these processes, icons, strategy.
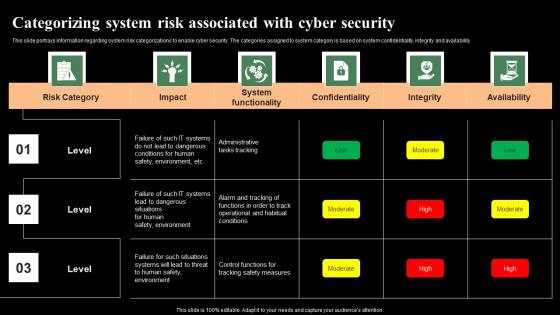
Categorizing System Risk Associated With Cyber Security Monitoring Digital Assets Professional Pdf
This slide portrays information regarding system risk categorizations to enable cyber security. The categories assigned to system category is based on system confidentiality, integrity and availability. Take your projects to the next level with our ultimate collection of Categorizing System Risk Associated With Cyber Security Monitoring Digital Assets Professional Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide portrays information regarding system risk categorizations to enable cyber security. The categories assigned to system category is based on system confidentiality, integrity and availability.

CASB 2 0 IT Training Program For Cloud Access Security Broker
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Training Program For Cloud Access Security Broker was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Training Program For Cloud Access Security Broker. This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training.
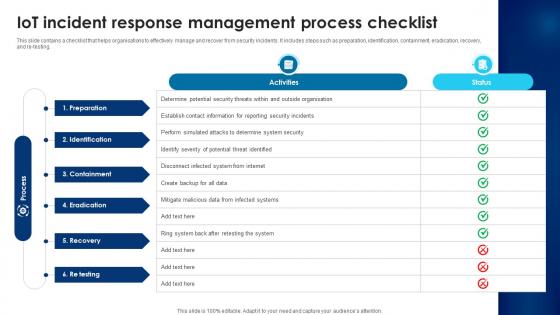
Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V
This slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re-testing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V. This slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re-testing.

Cyber Security Breach Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Cyber Security Breach Ppt Powerpoint Presentation Complete Deck With Slides Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twenty this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Cyber Security Breach Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Security Strategic Agenda Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Security Strategic Agenda Ppt Powerpoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising seventeen this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Security Strategic Agenda Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Security Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Internet Security Ppt Powerpoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising seventeen this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Internet Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Virus Assistant Performing Concentration Determining Security Powerpoint Ppt Template Bundles
This Virus Assistant Performing Concentration Determining Security Powerpoint Ppt Template Bundles is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This twelve-slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now. Designed, these Concentration Determining Security slides under Our Virus Assistant Perform, our presenters intend to ensure easy follow-up regarding your audience about getting insights from whats inside- that virus, detection concentration measures, and safety. The methodology in detecting these viruses and concentrations using these templates puts your focus sharply.
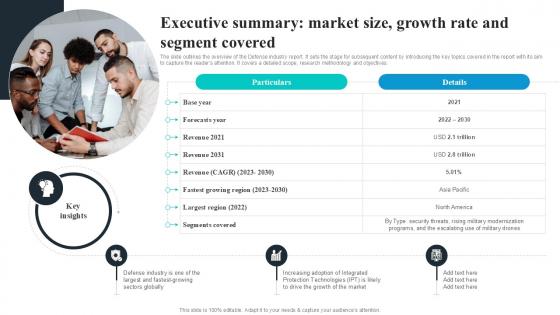
Executive Summary Market Size Growth Rate Global Security Industry PPT Presentation IR SS V
The slide outlines the overview of the Defense industry report. It sets the stage for subsequent content by introducing the key topics covered in the report with its aim to capture the readers attention. It covers a detailed scope, research methodology and objectives. Find highly impressive Executive Summary Market Size Growth Rate Global Security Industry PPT Presentation IR SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Executive Summary Market Size Growth Rate Global Security Industry PPT Presentation IR SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The slide outlines the overview of the Defense industry report. It sets the stage for subsequent content by introducing the key topics covered in the report with its aim to capture the readers attention. It covers a detailed scope, research methodology and objectives.
Info Security Minimize Administrative And Staff Privileges Ppt PowerPoint Presentation Icon Files PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting info security minimize administrative and staff privileges ppt powerpoint presentation icon files pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like employees, prevent cyber attacks, administrative staff. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
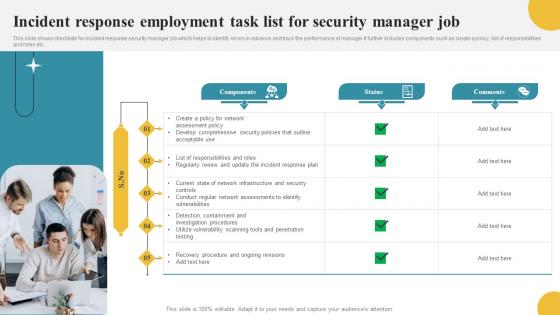
Incident Response Employment Task List For Security Manager Job Themes Pdf
This slide shows checklists for incident response security manager job which helps to identify errors in advance and track the performance of manager It further includes components such as create a policy, list of responsibilities and roles etc. Showcasing this set of slides titled Incident Response Employment Task List For Security Manager Job Themes Pdf The topics addressed in these templates are Components, Responsibilities And Roles, Response Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows checklists for incident response security manager job which helps to identify errors in advance and track the performance of manager It further includes components such as create a policy, list of responsibilities and roles etc.
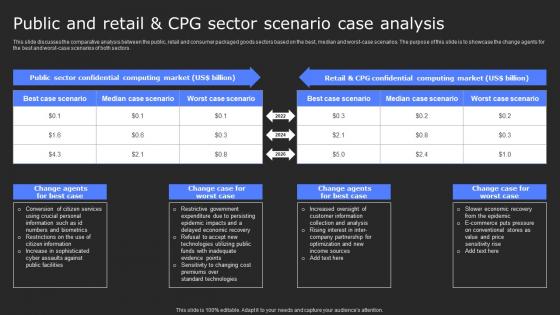
Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.

Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide highlights the positive impacts from the workplace safety which showcases reduce medical compensation, zero regulatory fines, few legal repercussion and reduce indirect costs. Explore a selection of the finest Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide highlights the positive impacts from the workplace safety which showcases reduce medical compensation, zero regulatory fines, few legal repercussion and reduce indirect costs.
Wifi Systems Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Wifi Systems Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Wifi Systems Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Wifi Systems Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Computer Personal Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Computer Personal Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Personal Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Computer Personal Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































