Email Template

Assessment Matrix Of Cyber Risks IT Security IT Ppt Ideas Display PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Presenting assessment matrix of cyber risks it security it ppt ideas display pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like industrial, multifamily, data center, retail, health care. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Communication Plan For Cybersecurity Events And Incidents Ppt Icon Good PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this communication plan for cybersecurity events and incidents ppt icon good pdf. Use them to share invaluable insights on resources training, awareness training, cybersecurity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
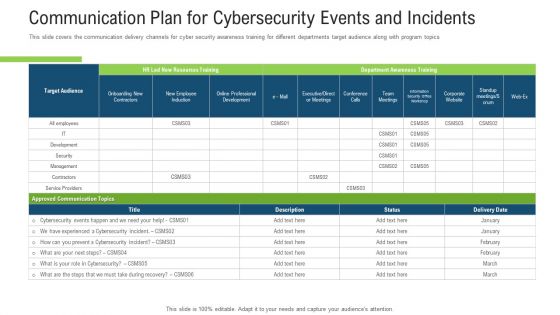
Communication Plan For Cybersecurity Events And Incidents Ppt Inspiration Graphic Images PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this communication plan for cybersecurity events and incidents ppt inspiration graphic images pdf. Use them to share invaluable insights on communication plan for cybersecurity events and incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
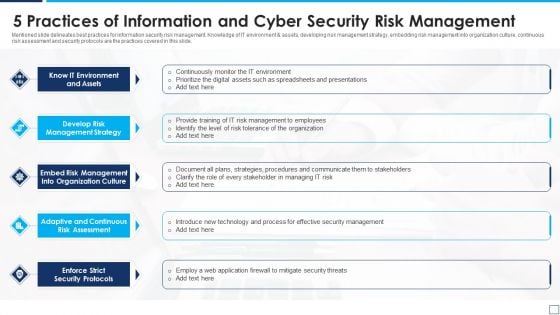
5 Practices Of Information And Cyber Security Risk Management Graphics PDF
Mentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting 5 practices of information and cyber security risk management graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including know it environment and assets, develop risk management strategy, enforce strict security protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
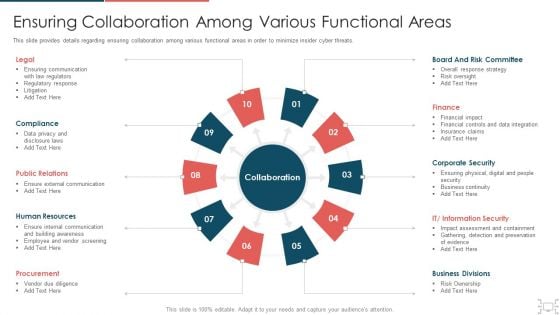
cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Contd Guidelines PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting corporate security and risk management addressing various ways to handle insider cyber threats contd guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
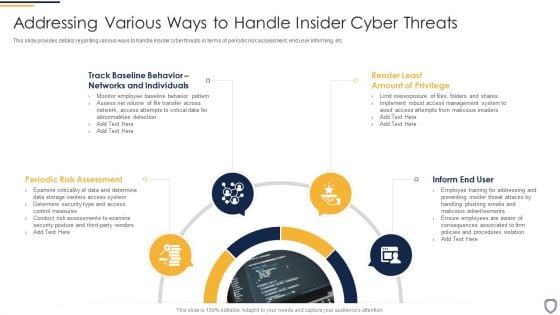
Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Infographics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a corporate security and risk management addressing various ways to handle insider cyber threats infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, inform end user, render least amount of privilege, track baseline behavior networks and individuals . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Sprint Report, Delivery Method, Frequency Responsible. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
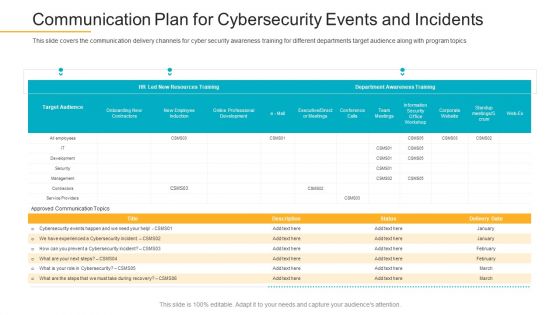
Data Breach Prevention Recognition Communication Plan For Cybersecurity Events And Incidents Pictures PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition communication plan for cybersecurity events and incidents pictures pdf. Use them to share invaluable insights on communication plan for cybersecurity events and incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
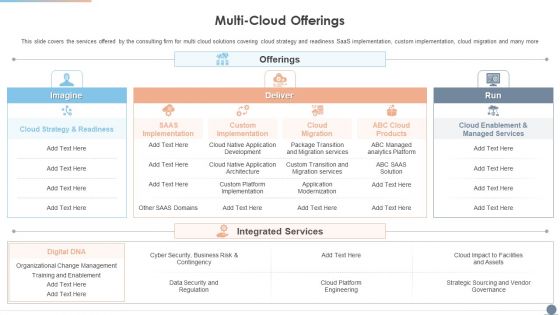
Multi Cloud Complexity Management Multi Cloud Offerings Inspiration PDF
This slide covers the services offered by the consulting firm for multi cloud solutions covering cloud strategy and readiness SaaS implementation, custom implementation, cloud migration and many more. Deliver and pitch your topic in the best possible manner with this Multi Cloud Complexity Management Multi Cloud Offerings Inspiration PDF. Use them to share invaluable insights on Cloud Strategy, Organizational Change Management, Cyber Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Types Of Threats In Information Security Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting info security types of threats in information security ppt powerpoint presentation gallery layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
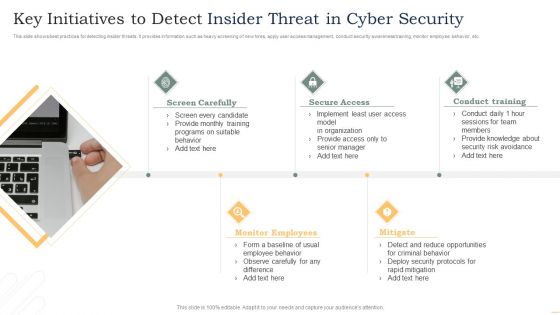
Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
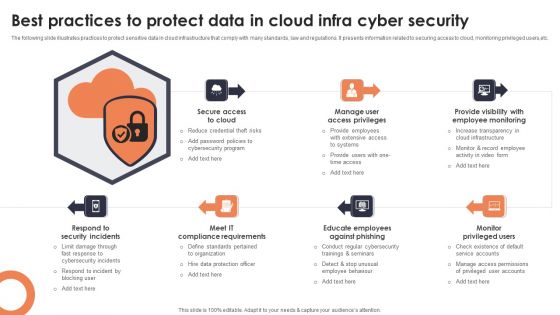
Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF
The following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users,etc. Presenting Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Secure Access Cloud, Manage User Access Privileges, Provide Visibility Employee. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
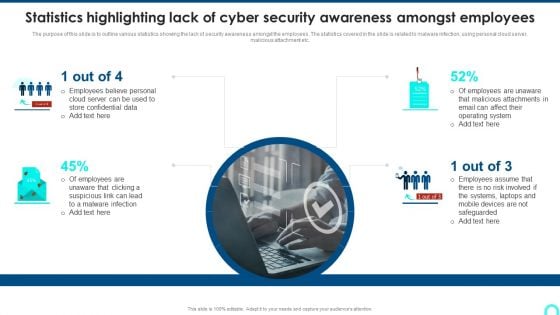
Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc.Presenting Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Employees Believe, Store Confidential, Malicious Attachments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
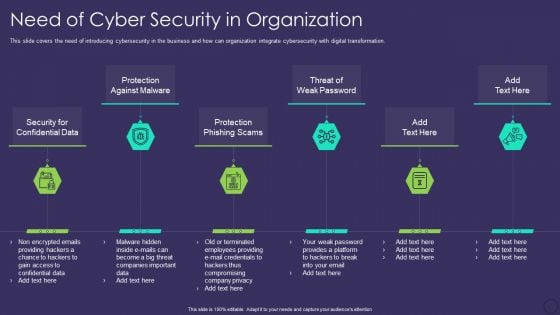
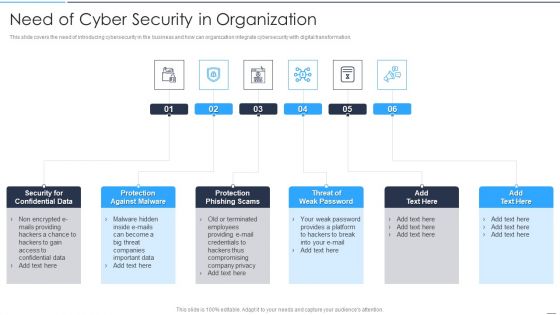
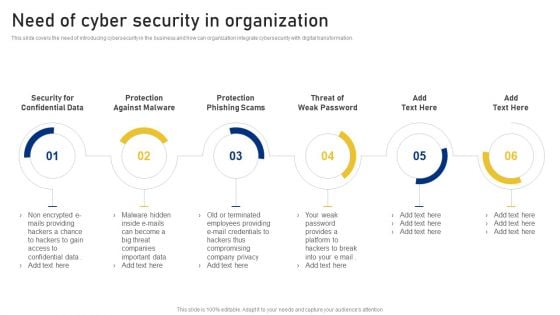
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
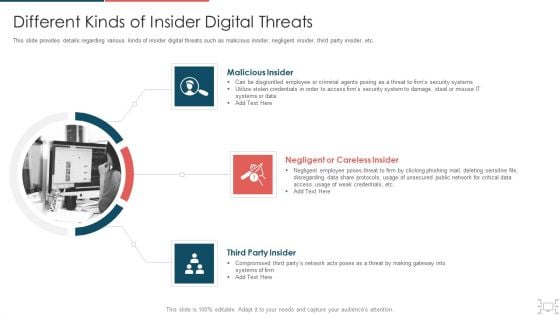
Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Management Inspiration PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting enhancing cyber safety with vulnerability administration security information and event management inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like data retention, forensic analysis, dashboards, data correlation, data aggregation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
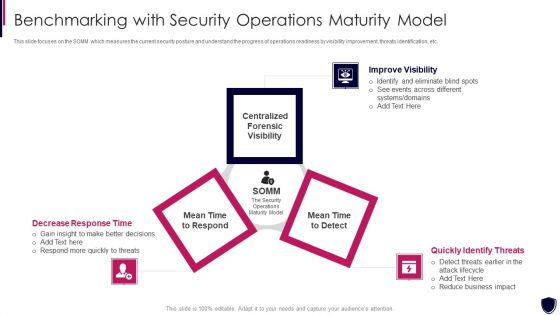
Enhancing Cyber Safety With Vulnerability Administration Benchmarking With Security Inspiration PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. This is a enhancing cyber safety with vulnerability administration benchmarking with security inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like improve visibility, quickly identify threats, decrease response time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
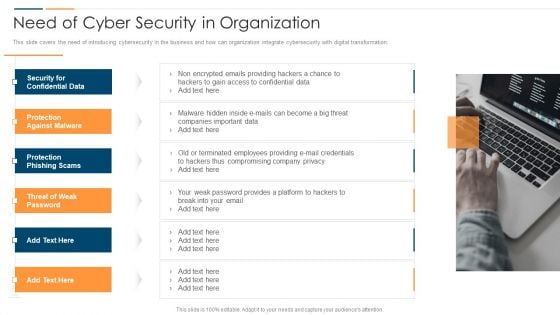
Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
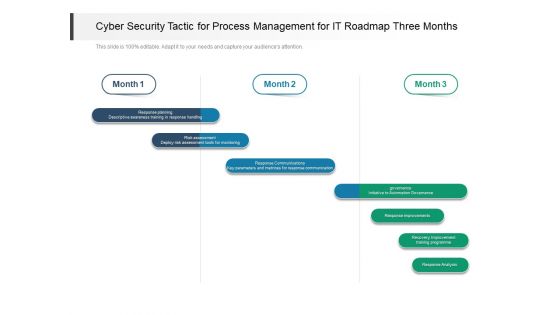
Cyber Security Tactic For Process Management For IT Roadmap Three Months Demonstration
Presenting our jaw dropping cyber security tactic for process management for it roadmap three months demonstration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
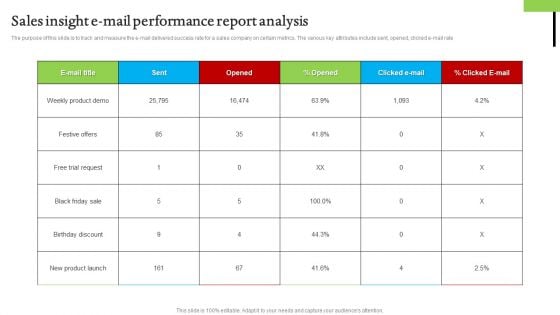
Sales Insight E Mail Performance Report Analysis Brochure PDF
The purpose of this slide is to track and measure the e-mail delivered success rate for a sales company on certain metrics. The various key attributes include sent, opened, clicked e-mail rate Showcasing this set of slides titled Sales Insight E Mail Performance Report Analysis Brochure PDF. The topics addressed in these templates are Sales Insight E Mail, Performance Report Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Disaster Recuperation Six Months Roadmap To Eradicate Intrusion Icons
Presenting the cyber security disaster recuperation six months roadmap to eradicate intrusion icons. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
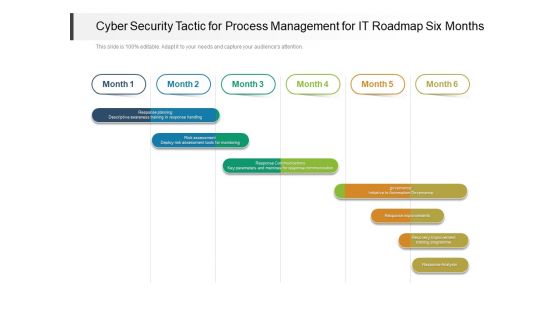
Cyber Security Tactic For Process Management For IT Roadmap Six Months Clipart
Presenting the cyber security tactic for process management for it roadmap six months clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
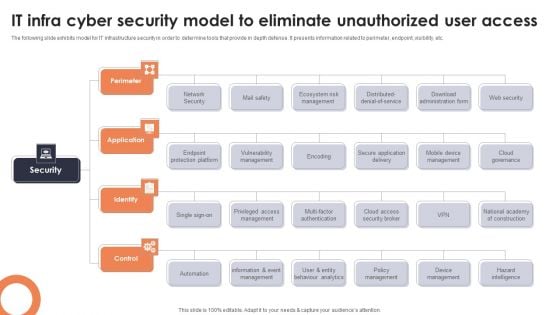
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Administration In Organization Various Types Of Workplace Violence And Threats Inspiration PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber security administration in organization various types of workplace violence and threats inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical, threatening, behavior, stalking, harassment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Workplace Incident Summary Report Brochure PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a cyber security administration in organization workplace incident summary report brochure pdf template with various stages. Focus and dispense information on eigt stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident, employees, location, emergency, assistance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
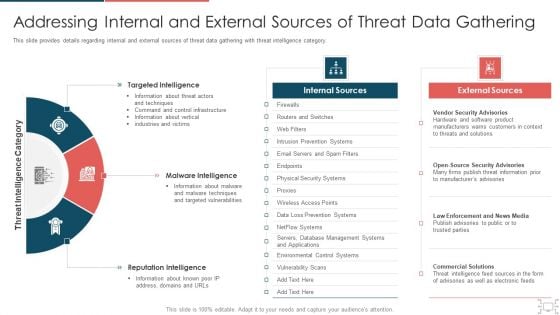
cyber security administration in organization addressing internal and external sources of gathering structure pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a cyber security administration in organization addressing internal and external sources of gathering structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, sources, internal, intelligence, reputation . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
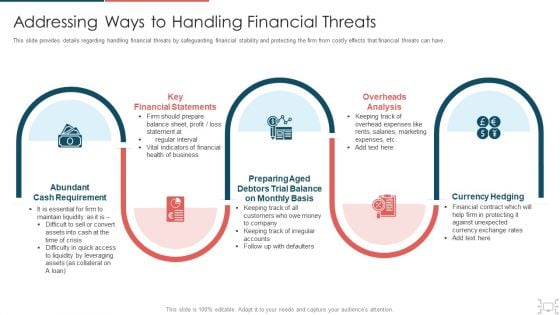
cyber security administration in organization addressing ways to handling financial threats summary pdf
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. This is a cyber security administration in organization addressing ways to handling financial threats summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, statements, requirement, preparing, balance . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
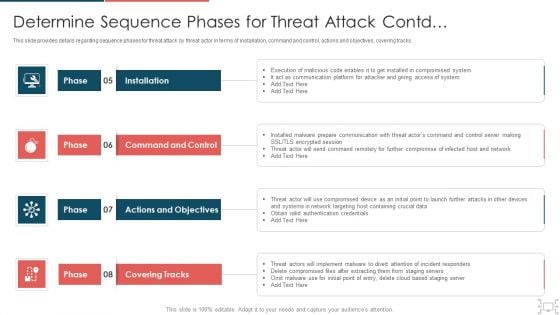
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
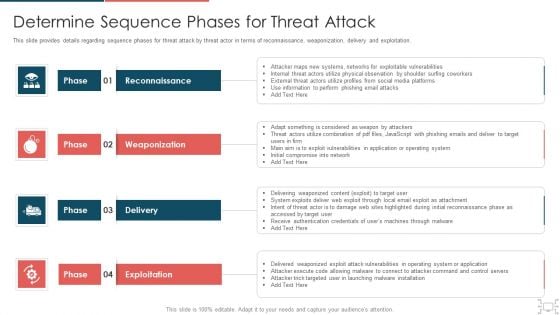
cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
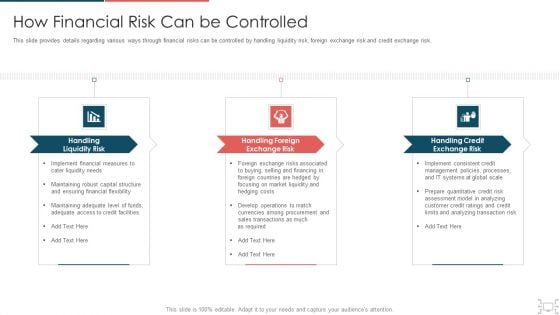
cyber security administration in organization how financial risk can be controlled inspiration pdf
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. This is a cyber security administration in organization how financial risk can be controlled inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like handling, liquidity, financial, flexibility, structure . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
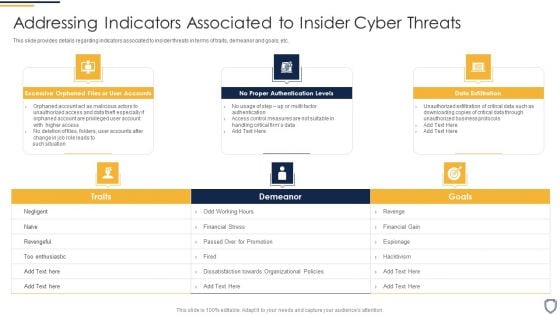
Corporate Security And Risk Management Addressing Indicators Associated To Insider Cyber Threats Topics PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. This is a corporate security and risk management addressing indicators associated to insider cyber threats topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like excessive orphaned files or user accounts, no proper authentication levels, data exfiltration . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Contingency Plan For Cyber Threat Handling Structure PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Presenting corporate security and risk management contingency plan for cyber threat handling structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like contingency solutions, contingency considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Against Malware, Phishing Scams In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
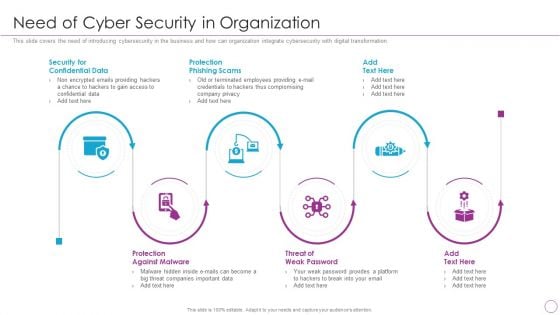
Integration Of Digital Technology In Organization Need Of Cyber Security In Organization Information PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Integration Of Digital Technology In Organization Need Of Cyber Security In Organization Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Protection Phishing, Protection Against In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
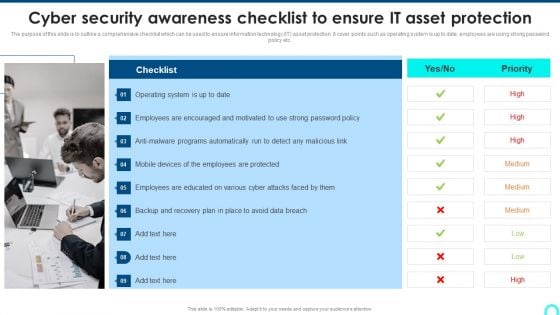
Cyber Security Awareness Checklist To Ensure IT Asset Protection Microsoft PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password.This is a Cyber Security Awareness Checklist To Ensure IT Asset Protection Microsoft PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees Encouraged, Programs Automatically, Employees Protected. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
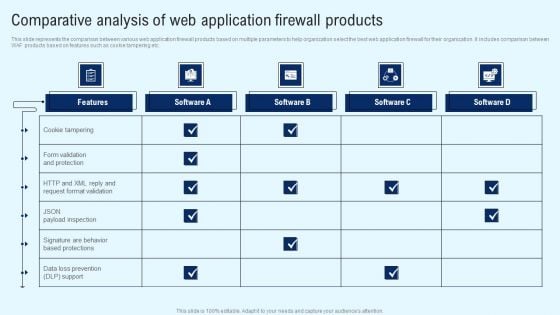
Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Boost your pitch with our creative Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
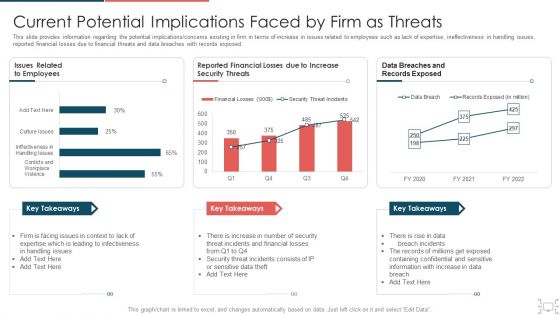
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
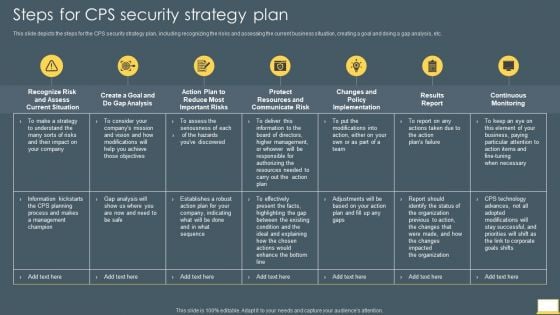
Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF. Use them to share invaluable insights on Gap Analysis, Protect Resources, Communicate Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Contact Us Writing Enhancement Software Pitch Deck PPT Presentation
This slide presents the contact details of and AI powered writing assistant . It includes details about company headquarters, website, contact number and emails, socials Facebook, Twitter, LinkedIn. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Contact Us Writing Enhancement Software Pitch Deck PPT Presentation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Contact Us Writing Enhancement Software Pitch Deck PPT Presentation. This slide presents the contact details of and AI powered writing assistant .It includes details about company headquarters, website, contact number and emails, socials Facebook, Twitter, LinkedIn.

IT Security Types Of Threats In Information Technology Security Ppt Summary Aids PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting it security types of threats in information technology security ppt summary aids pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
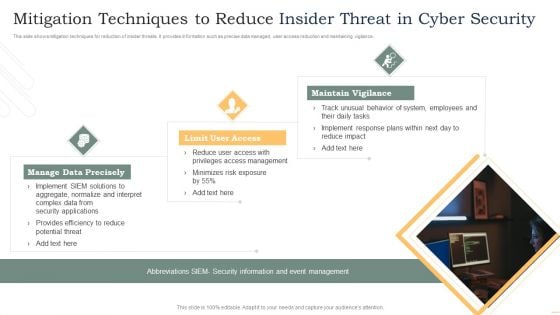
Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
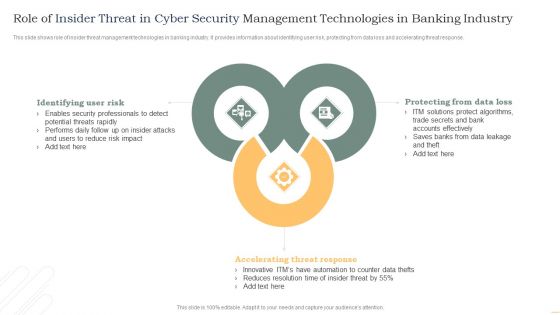
Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF
This slide shows role of insider threat management technologies in banking industry. It provides information about identifying user risk, protecting from data loss and accelerating threat response. Presenting Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Identifying User Risk, Accelerating Threat Response, Protecting Data Loss. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
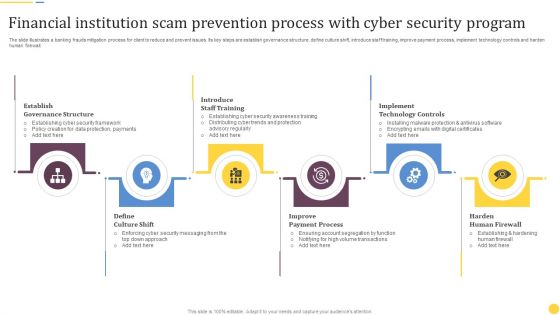
Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Prevention Of Information Key Stakeholders Of Cyber Security Awareness Training Icons PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Prevention Of Information Key Stakeholders Of Cyber Security Awareness Training Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF
The following slide showcases various approaches to AI infrastructure which bodes well for future of organizations association. It presents information related to regulatory framework, expert consultations, etc. Presenting Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Regulatory Framework, Protect AI Related Data, Involve Cybersecurity Experts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Workplace Employee Assistance Program Professional PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting cyber security administration in organization workplace employee assistance program professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical, services, employer, management, consultations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
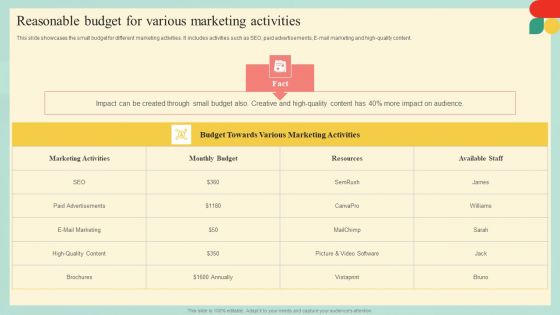
Guide Developing Strategies Improve Travel Tourism Marketing Reasonable Budget For Various Guidelines PDF
This slide showcases the small budget for different marketing activities. It includes activities such as SEO, paid advertisements, E-mail marketing and high-quality content. There are so many reasons you need a Guide Developing Strategies Improve Travel Tourism Marketing Reasonable Budget For Various Guidelines PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Process Of E Mail Marketing Strategy Efficient B2B And B2C Marketing Techniques For Organization Clipart PDF
Purpose of the following slide is to display a detailed e-mail marketing strategy process. The process can help the organization in developing a complete e-mail marketing campaign and increase revenues.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Process Of E Mail Marketing Strategy Efficient B2B And B2C Marketing Techniques For Organization Clipart PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Process Of E Mail Marketing Strategy Efficient B2B And B2C Marketing Techniques For Organization Clipart PDF.
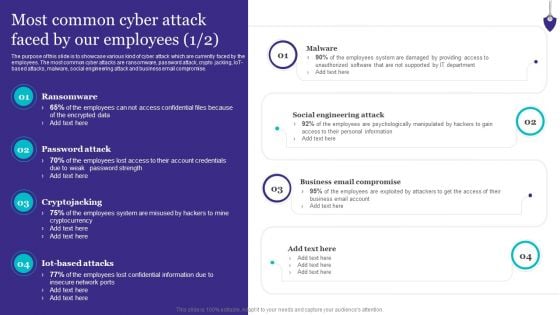
Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
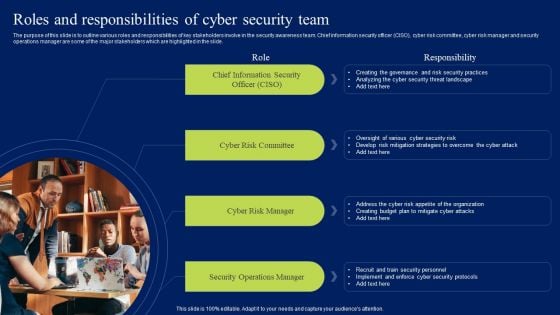
Roles And Responsibilities Of Cyber Security Team Ppt Portfolio
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roles And Responsibilities Of Cyber Security Team Ppt Portfolio can be your best option for delivering a presentation. Represent everything in detail using Roles And Responsibilities Of Cyber Security Team Ppt Portfolio and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Best Practices For Cyber Safety At Job Safety Infographics PDF
This slide covers the best practices for cyber safety at workplace which includes protecting the data, using strong password protection, connecting to the secure wi-fi, investing in security systems, etc. Presenting best practices for cyber safety at job safety infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including protecting data, connect to secure wi fi, invest in security systems, strong password protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
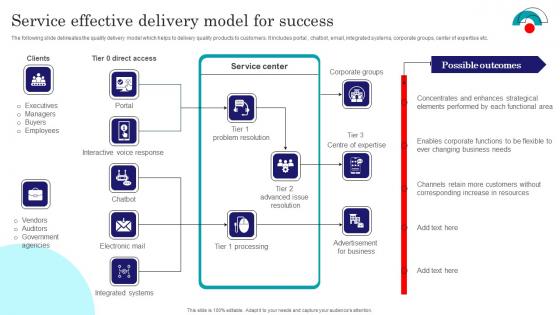
Service Effective Delivery Model For Success Brochure Pdf
The following slide delineates the quality delivery model which helps to delivery quality products to customers. It includes portal , chatbot, email, integrated systems, corporate groups, center of expertise etc. Showcasing this set of slides titled Service Effective Delivery Model For Success Brochure Pdf. The topics addressed in these templates are Direct Access, Chatbot, Electronic Mail. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide delineates the quality delivery model which helps to delivery quality products to customers. It includes portal , chatbot, email, integrated systems, corporate groups, center of expertise etc.
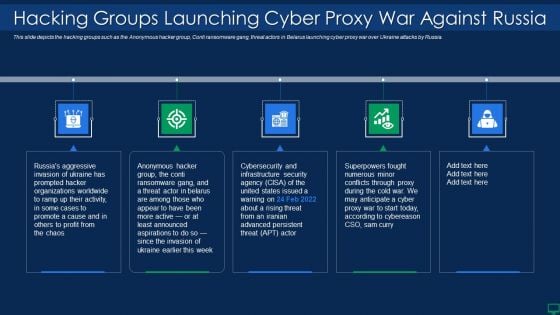
Russian Cyber Attacks On Ukraine IT Hacking Groups Launching Cyber Rules PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting russian cyber attacks on ukraine it hacking groups launching cyber rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Application Programming Interface Marketplace Cost Breakdown To Setup A Company In US Diagrams PDF
The description below is the professional summary of the company, includes information of features, license, pricing structure and size of users. Deliver and pitch your topic in the best possible manner with this application programming interface marketplace cost breakdown to setup a company in us diagrams pdf. Use them to share invaluable insights on cyber security plan, business operation, time frequency and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































