Email Template
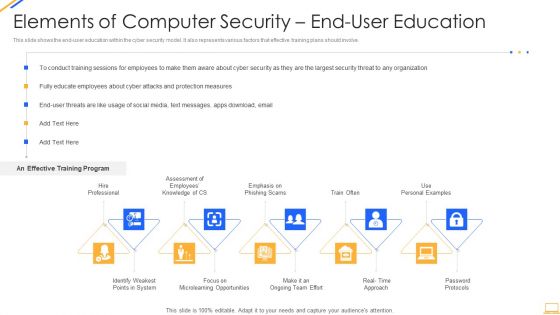
Desktop Security Management Elements Of Computer Security End User Education Background PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a desktop security management elements of computer security end user education background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, opportunities, security, organization, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Desktop Security Management What Are The Benefits Of Computer Security Icons PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting desktop security management what are the benefits of computer security icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, environment, potential, devices, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
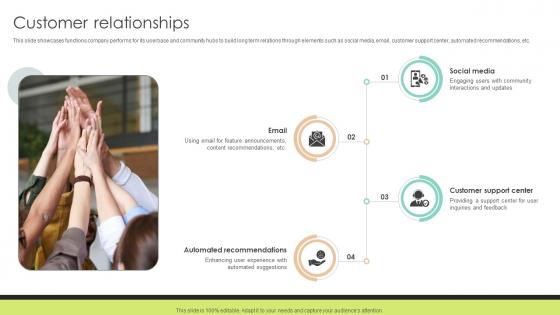
Customer Relationships Community Networking Platform Business Model
This slide showcases functions company performs for its userbase and community hubs to build long term relations through elements such as social media, email, customer support center, automated recommendations, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Customer Relationships Community Networking Platform Business Model for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases functions company performs for its userbase and community hubs to build long term relations through elements such as social media, email, customer support center, automated recommendations, etc.
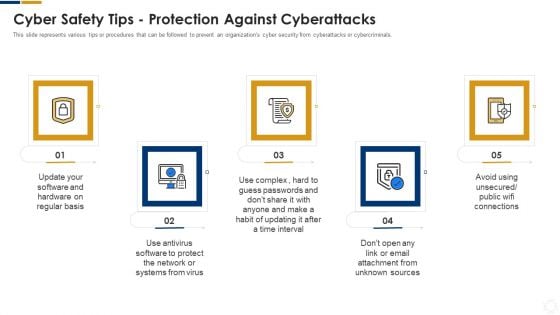
Cybersecurity Cyber Safety Tips Protection Against Cyberattacks Ppt Styles Gallery PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a cybersecurity cyber safety tips protection against cyberattacks ppt styles gallery pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

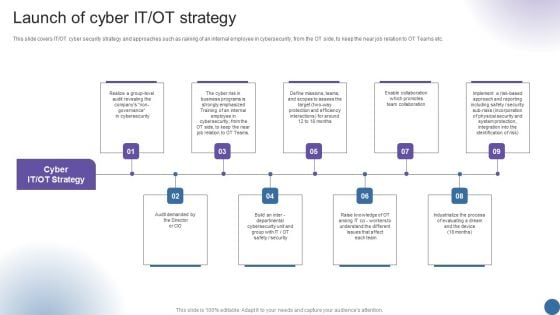
Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Audit Demanded, Enable Collaboration, Industrialize Process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
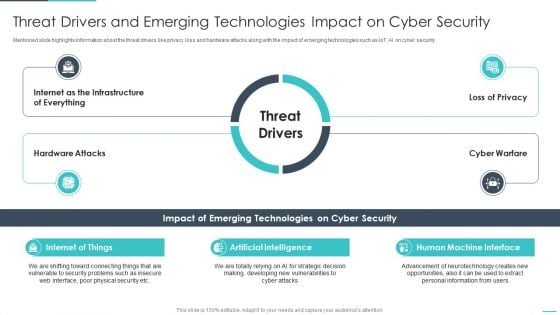
Handling Cyber Threats Digital Era Threat Drivers And Emerging Technologies Ppt Styles Ideas PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era threat drivers and emerging technologies ppt styles ideas pdf. Use them to share invaluable insights on internet of things, artificial intelligence, human machine interface and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Business Process Flowchart Examples 3d Men On Http Protocol PowerPoint Slides
We present our business process flowchart examples 3d men on http protocol PowerPoint Slides.Download and present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Download and present our Internet PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download and present our Symbol PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Present our Business PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape.Use these PowerPoint slides for presentations relating to 3d, address, browser, cartoon, character, computer, connection, cyberspace, data, design, display, domain, e-commerce, e-mail, ecommerce, engineer, help, hosting, http, hyperlink, icon, iconic, illustration, information, internet, isolated, laptop, male, man, network, notebook, pc, people, person, puppet, render, seo, service, sign, site, style, surf, symbol, technology, web, webdesign, webhosting, webpage, website, white. The prominent colors used in the PowerPoint template are Yellow, Black, Brown. PowerPoint presentation experts tell us our business process flowchart examples 3d men on http protocol PowerPoint Slides will make the presenter look like a pro even if they are not computer savvy. Use our browser PowerPoint templates and PPT Slides are visually appealing. You can be sure our business process flowchart examples 3d men on http protocol PowerPoint Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Presenters tell us our connection PowerPoint templates and PPT Slides look good visually. You can be sure our business process flowchart examples 3d men on http protocol PowerPoint Slides will get their audience's attention. Professionals tell us our connection PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Make your presentations helpful with our Business Process Flowchart Examples 3d Men On Http Protocol PowerPoint Slides. Dont waste time struggling with PowerPoint. Let us do it for you.
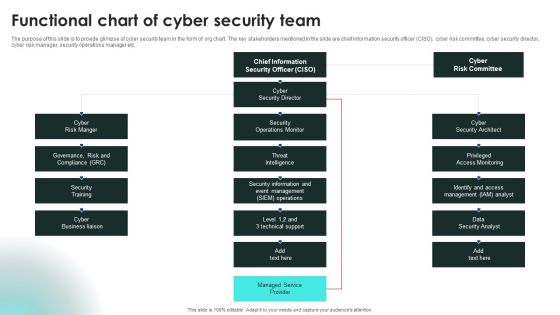
Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT teams etc. Presenting Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Cyber Risk, Process Of Evaluating. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Launch Of Cyber IT OT Strategy Managing Organizational Transformation Sample PDF
This slide covers IT OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Launch Of Cyber IT OT Strategy Managing Organizational Transformation Sample PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategy, Launch Of Cyber, Business Programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

A97 B2B Marketing Techniques To Increase Wholesale Marketing Strategies For Improving
This slide showcases various strategies adopted by wholesale business to improve brand awareness and increase sales revenues. It provides information regarding techniques such as social media, email, direct mail marketing, referral program and cold calling. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A97 B2B Marketing Techniques To Increase Wholesale Marketing Strategies For Improving for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases various strategies adopted by wholesale business to improve brand awareness and increase sales revenues. It provides information regarding techniques such as social media, email, direct mail marketing, referral program and cold calling.
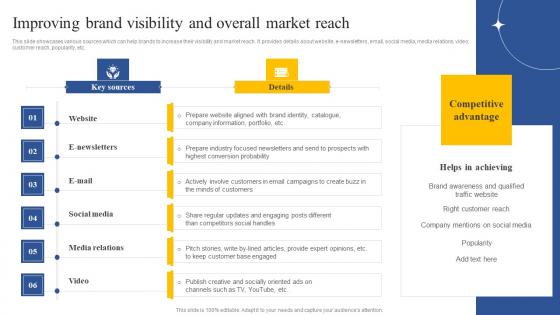
Improving Brand Visibility And Overall Market Reach How To Implement Product Brochure Pdf
This slide showcases various sources which can help brands to increase their visibility and market reach. It provides details about website, e-newsletters, email, social media, media relations, video, customer reach, popularity, etc. Slidegeeks has constructed Improving Brand Visibility And Overall Market Reach How To Implement Product Brochure Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases various sources which can help brands to increase their visibility and market reach. It provides details about website, e-newsletters, email, social media, media relations, video, customer reach, popularity, etc.
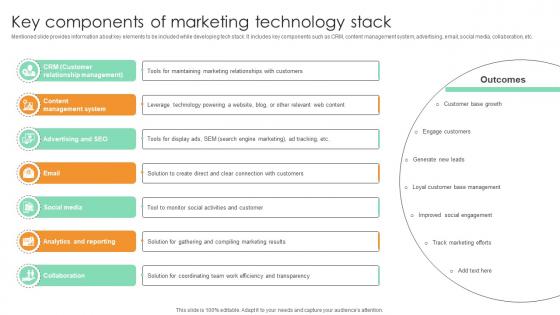
Key Components Of Marketing Technology Stack Comprehensive Guide For Marketing Technology
Mentioned slide provides information about key elements to be included while developing tech stack. It includes key components such as CRM, content management system, advertising, email, social media, collaboration, etc.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Components Of Marketing Technology Stack Comprehensive Guide For Marketing Technology for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Mentioned slide provides information about key elements to be included while developing tech stack. It includes key components such as CRM, content management system, advertising, email, social media, collaboration, etc.
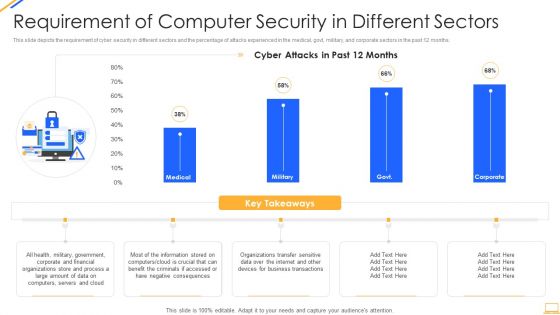
Desktop Security Management Requirement Of Computer Security In Different Sectors Sample PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this desktop security management requirement of computer security in different sectors sample pdf. Use them to share invaluable insights on information, organizations, financial, servers, internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Tracking Candidates Through Application Cloud Recruiting Technologies PPT Slide
This slide showcases illustration of application tracking system ATS software which HRs can refer to influence their adoption decision. It provides details about email, rating, status, mobile, current position, quality of hire, cost per hire, bounce rates, etc. Slidegeeks has constructed Tracking Candidates Through Application Cloud Recruiting Technologies PPT Slide after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases illustration of application tracking system ATS software which HRs can refer to influence their adoption decision. It provides details about email, rating, status, mobile, current position, quality of hire, cost per hire, bounce rates, etc.

E Mail Marketing Key Stats Efficient B2B And B2C Marketing Techniques For Organization Guidelines PDF
Purpose of the following slide is to display key statistics of e-mail marketing as a tool for b2b and b2c services. It highlights major industry statistics such as daily users of e-mail, earning per dollar spent, conversion rate etc. Explore a selection of the finest E Mail Marketing Key Stats Efficient B2B And B2C Marketing Techniques For Organization Guidelines PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our E Mail Marketing Key Stats Efficient B2B And B2C Marketing Techniques For Organization Guidelines PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
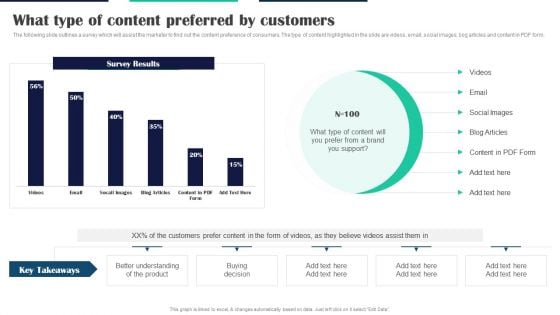
Executing Video Promotional What Type Of Content Preferred By Customers Professional PDF
The following slide outlines different YouTube guidelines which will assist the marketer to grow organic subscribers. The key guidelines highlighted in the slide are channel icon, trailer, links and brand visuals. The following slide outlines a survey which will assist the marketer to find out the content preference of consumers. The type of content highlighted in the slide are videos, email, social images, bog articles and content in PDF form. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Executing Video Promotional What Type Of Content Preferred By Customers Professional PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Executing Video Promotional Youtube Brand Guidelines To Increase Subscribers Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Handling Cyber Threats Digital Era Categorization Worksheet For Assets Ppt Icon Outline PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting handling cyber threats digital era categorization worksheet for assets ppt icon outline pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like server computer, system location, system accessibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Handling Cyber Threats Digital Era Defining Business Priorities To Ensure Ppt Gallery Brochure PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting handling cyber threats digital era defining business priorities to ensure ppt gallery brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like efficient risk management, standardized incident management process, transparent communication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
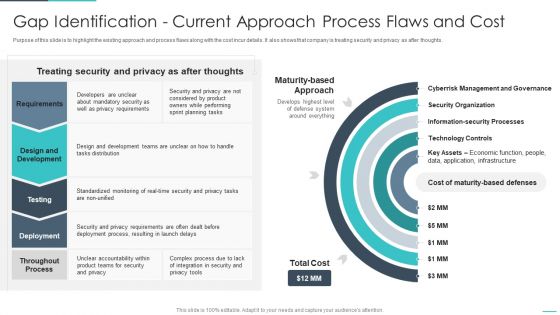
Handling Cyber Threats Digital Era Gap Identification Current Approach Process Ppt Outline Objects PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era gap identification current approach process ppt outline objects pdf. Use them to share invaluable insights on gap identification current approach process flaws and cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
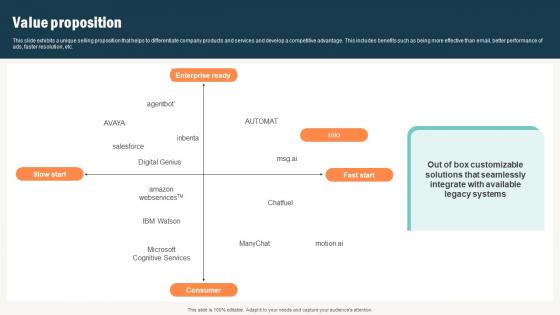
Value Proposition Conversational Commerce Platform Investor
This slide exhibits a unique selling proposition that helps to differentiate company products and services and develop a competitive advantage. This includes benefits such as being more effective than email, better performance of ads, faster resolution, etc. Explore a selection of the finest Value Proposition Conversational Commerce Platform Investor here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Value Proposition Conversational Commerce Platform Investor to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide exhibits a unique selling proposition that helps to differentiate company products and services and develop a competitive advantage. This includes benefits such as being more effective than email, better performance of ads, faster resolution, etc.
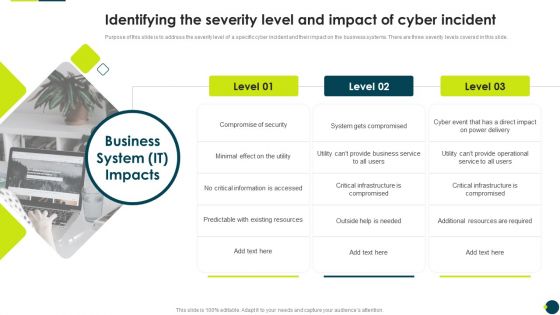
IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Presenting IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Compromise Security, Information Accessed, Existing Resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
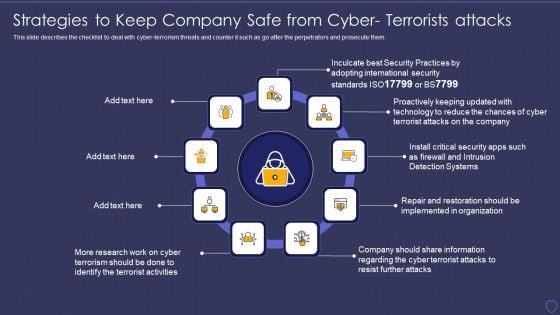
Global Cyber Terrorism Incidents On The Rise IT Strategies To Keep Company Safes Portrait PDF
This slide describes the checklist to deal with cyber-terrorism threats and counter it such as go after the perpetrators and prosecute them. This is a global cyber terrorism incidents on the rise it strategies to keep company safes portrait pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implemented, organization, technology, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
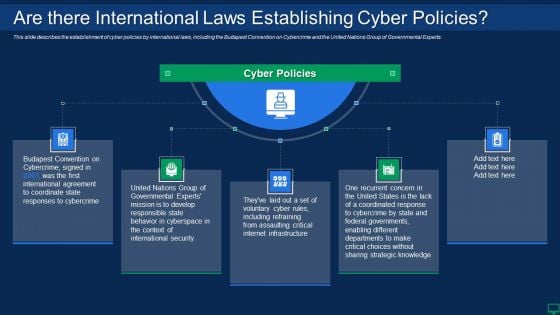
Russian Cyber Attacks On Ukraine IT Are There International Mockup PDF
This slide describes the establishment of cyber policies by international laws, including the Budapest Convention on Cybercrime and the United Nations Group of Governmental Experts. This is a russian cyber attacks on ukraine it are there international mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, strategic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
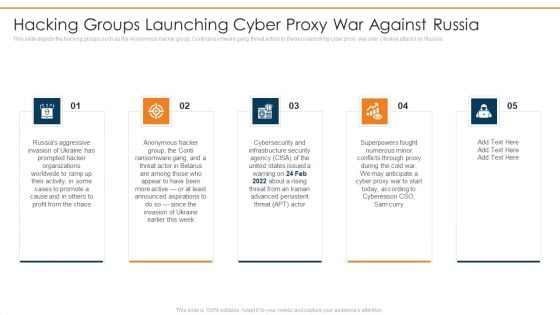
Data Wiper Spyware Attack Hacking Groups Launching Cyber Proxy War Against Russia Portrait PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.This is a data wiper spyware attack hacking groups launching cyber proxy war against russia portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure security, superpowers fought, conflicts through proxy You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Weaknesses Of Russian Cyber Cell Microsoft PDF
This slide represents the weaknesses of Russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials.Presenting data wiper spyware attack weaknesses of russian cyber cell microsoft pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like lack of skilled professionals, corruption, security agencies In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
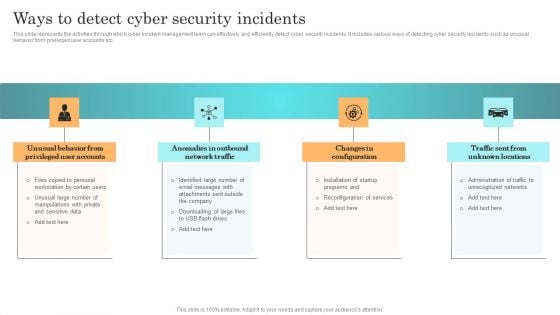
Incident Response Techniques Deployement Ways To Detect Cyber Security Incidents Infographics PDF

Comparison Of Various Security Awareness Training Software Elements PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver and pitch your topic in the best possible manner with this Comparison Of Various Security Awareness Training Software Elements PDF. Use them to share invaluable insights on Individualized Security, Industry Specific, Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
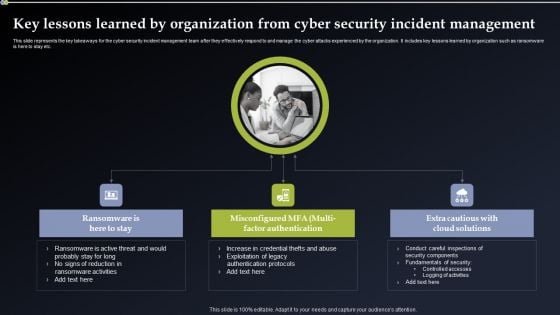
Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF can be your best option for delivering a presentation. Represent everything in detail using Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
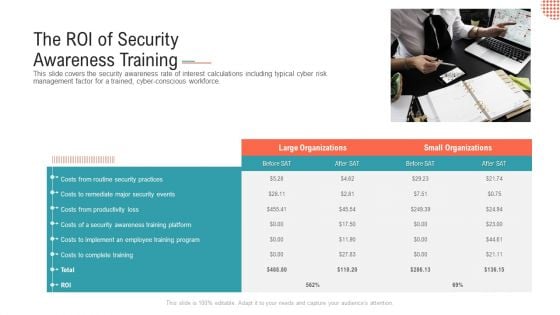
The ROI Of Security Awareness Training Ppt Slides Background PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyberconscious workforce.This is a the roi of security awareness training ppt slides background pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs from routine security practices, costs from productivity loss. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
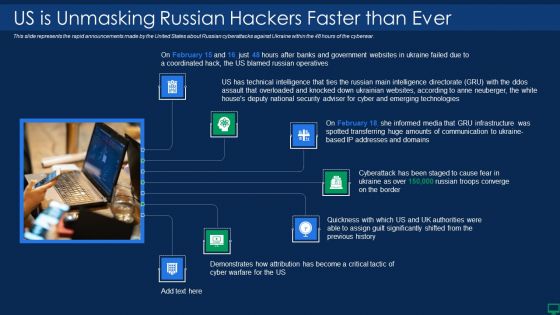
Russian Cyber Attacks On Ukraine IT Us Is Unmasking Russian Inspiration PDF
This slide represents the rapid announcements made by the United States about Russian cyberattacks against Ukraine within the 48 hours of the cyberwar. Presenting russian cyber attacks on ukraine it us is unmasking russian inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like technical, security, communication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
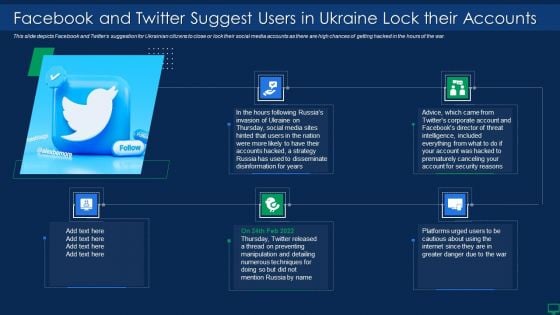
Russian Cyber Attacks On Ukraine IT Facebook And Twitter Suggest Rules PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. This is a russian cyber attacks on ukraine it facebook and twitter suggest rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, accounts, strategy, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Germany Asks To Avoid Russias Sample PDF
This slide depicts the official announcement to avoid Russias Kaspersky antivirus tool by German officials as Kaspersky has been accused of working for the Russian government. This is a russian cyber attacks on ukraine it germany asks to avoid russias sample pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, portfolio. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
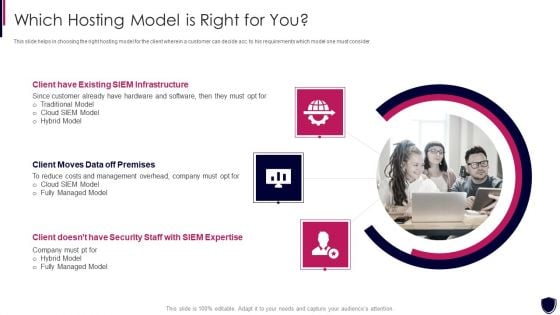
Enhancing Cyber Safety With Vulnerability Administration Which Hosting Model Is Right Ideas PDF
This slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. Presenting enhancing cyber safety with vulnerability administration which hosting model is right ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like client have existing siem infrastructure, client moves data off premises, client doesnt have security staff with siem expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
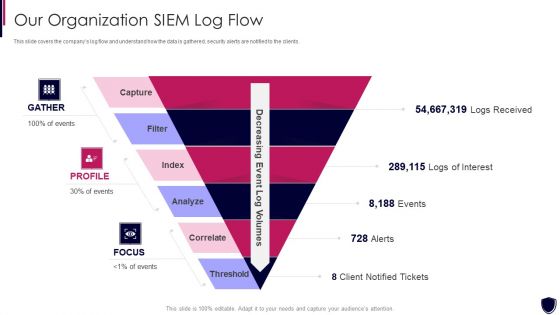
Enhancing Cyber Safety With Vulnerability Administration Our Organization SIEM Log Flow Inspiration PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. Presenting enhancing cyber safety with vulnerability administration our organization siem log flow inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like index, analyz, correlate, threshold, capture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Cyber Officials Urge Agencies To Armor Download PDF
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines.Presenting data wiper spyware attack cyber officials urge agencies to armor download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like warning government, corporations to be cautious, russian cyberattacks In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
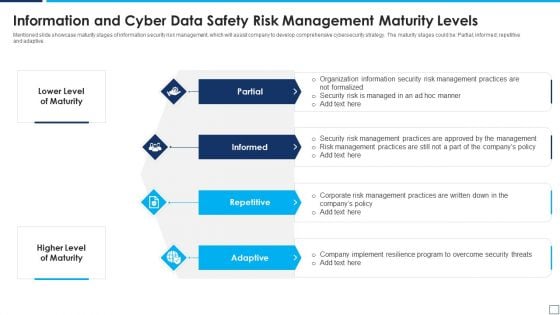
Information And Cyber Data Safety Risk Management Maturity Levels Elements PDF
Mentioned slide showcase maturity stages of information security risk management, which will assist company to develop comprehensive cybersecurity strategy. The maturity stages could be Partial informed repetitive and adaptive. Presenting information and cyber data safety risk management maturity levels elements pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including partial, informed, repetitive, adaptive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Utilizing Cyber Technology For Change Process Challenges In Digital Transformation Introduction PDF
Digital transformation, especially in the healthcare sector, is a complex process and there are some hiccups that need to be addressed for complete success.Presenting utilizing cyber technology for change process challenges in digital transformation introduction pdf. to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like workforce training, technological gaps, lack connectivity, organizational culture, security, capital. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
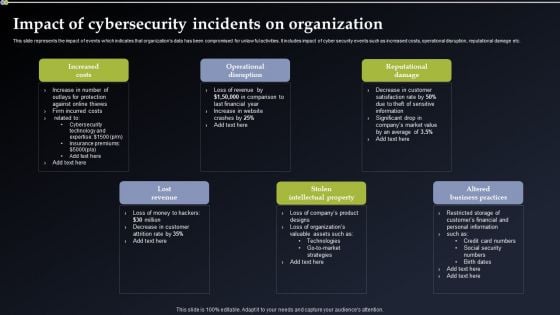
Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
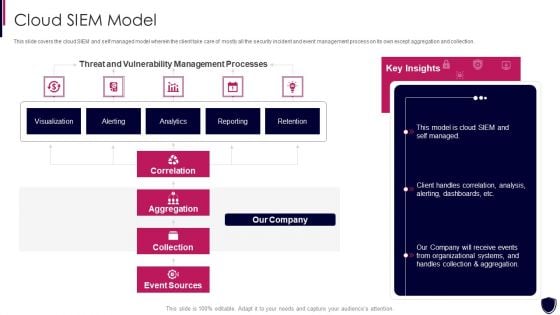
Enhancing Cyber Safety With Vulnerability Administration Cloud SIEM Model Clipart PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this enhancing cyber safety with vulnerability administration cloud siem model clipart pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources, our company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
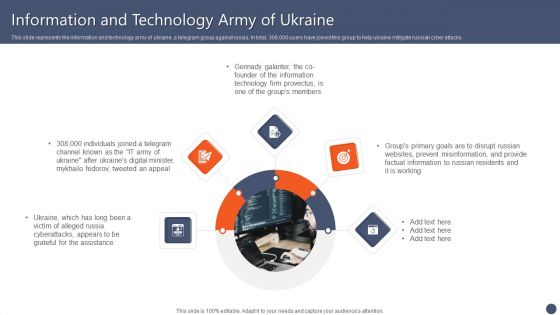
Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF
This slide represents the information and technology army of ukraine, a telegram group against russia. In total, 308,000 users have joined this group to help ukraine mitigate russian cyber attacks. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
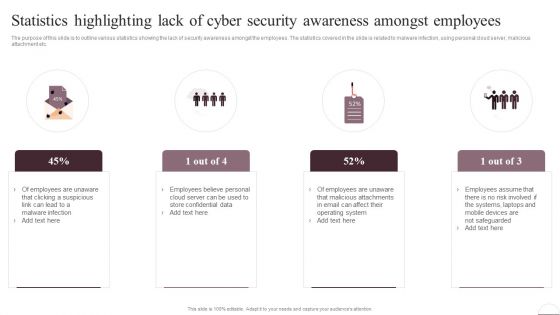
Prevention Of Information Statistics Highlighting Lack Of Cyber Security Awareness Information PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Prevention Of Information Statistics Highlighting Lack Of Cyber Security Awareness Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Prevention Of Information Statistics Highlighting Lack Of Cyber Security Awareness Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
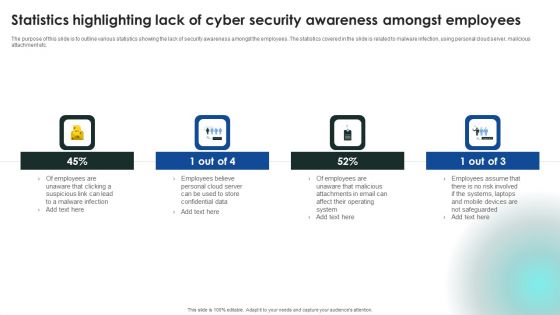
Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
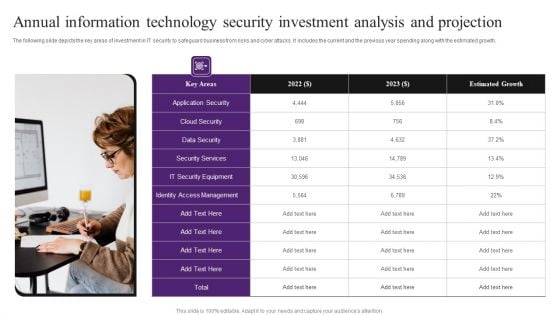
Annual Information Technology Security Investment Analysis And Projection Portrait PDF
The following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Presenting Annual Information Technology Security Investment Analysis And Projection Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cloud Security, Security Services, Identity Access Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
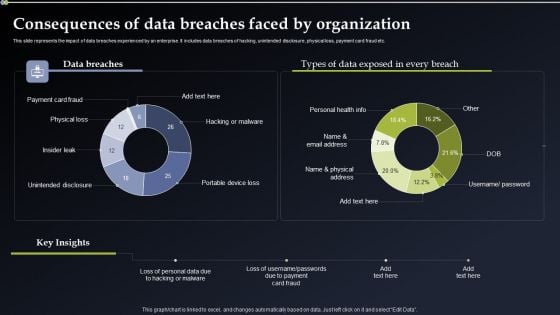
Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
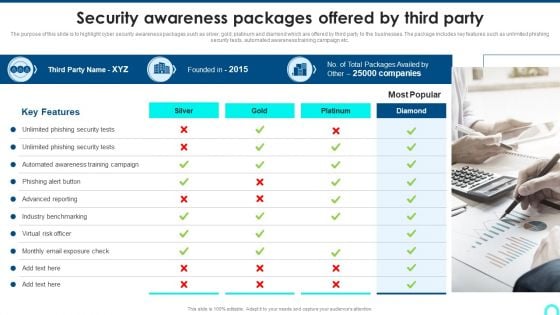
Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This is a Security Awareness Packages Offered By Third Party Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Unlimited Phishing, Automated Awareness, Industry Benchmarking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
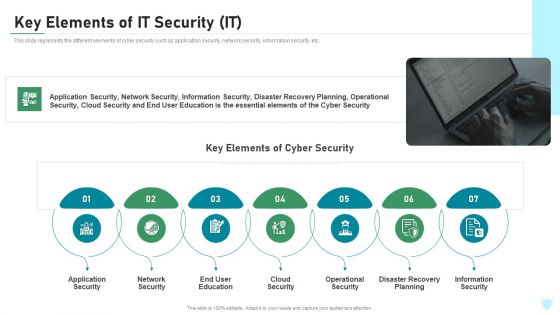
Key Elements Of IT Security IT Ppt Pictures Inspiration PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a key elements of it security it ppt pictures inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, end user education, cloud security, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
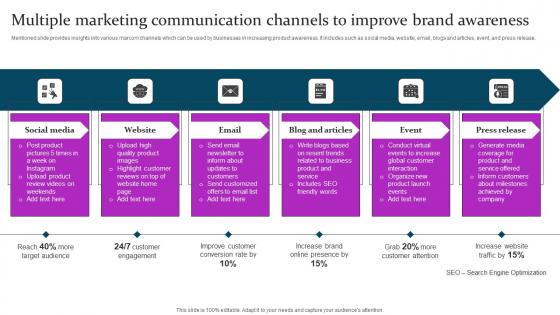
Multiple Marketing Communication Channels Marketing Mix Communication Guide Client Sample Pdf
Mentioned slide provides insights into various marcom channels which can be used by businesses in increasing product awareness. It includes such as social media, website, email, blogs and articles, event, and press release. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Multiple Marketing Communication Channels Marketing Mix Communication Guide Client Sample Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Mentioned slide provides insights into various marcom channels which can be used by businesses in increasing product awareness. It includes such as social media, website, email, blogs and articles, event, and press release.
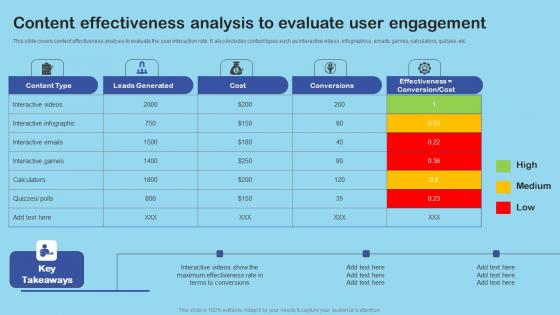
Content Effectiveness Analysis Enhance Client Engagement With Interactive Advertising Microsoft Pdf
This slide covers content effectiveness analysis to evaluate the user interaction rate. It also includes content types such as interactive videos, infographics, emails, games, calculators, quizzes, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Content Effectiveness Analysis Enhance Client Engagement With Interactive Advertising Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide covers content effectiveness analysis to evaluate the user interaction rate. It also includes content types such as interactive videos, infographics, emails, games, calculators, quizzes, etc.
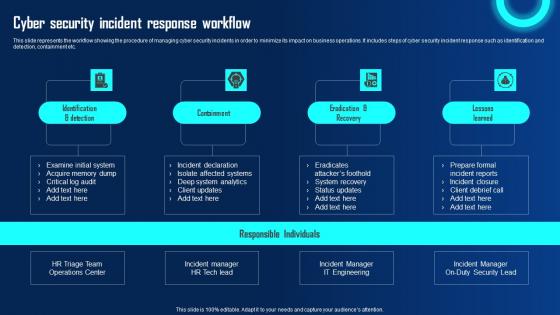
Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf
This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc. This Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc.
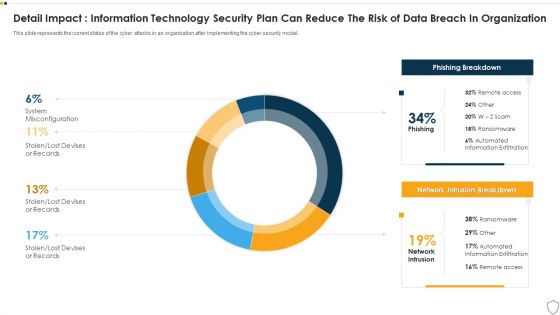
IT Security Detail Impact Information Technology Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Layouts Show PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this it security detail impact information technology security plan can reduce the risk of data breach in organization ppt layouts show pdf. Use them to share invaluable insights on detail impact information technology security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
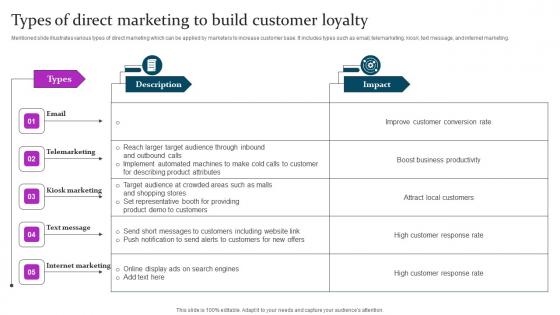
Types Of Direct Marketing To Build Marketing Mix Communication Guide Client Pictures Pdf
Mentioned slide illustrates various types of direct marketing which can be applied by marketers to increase customer base. It includes types such as email, telemarketing, kiosk, text message, and internet marketing. Explore a selection of the finest Types Of Direct Marketing To Build Marketing Mix Communication Guide Client Pictures Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Types Of Direct Marketing To Build Marketing Mix Communication Guide Client Pictures Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide illustrates various types of direct marketing which can be applied by marketers to increase customer base. It includes types such as email, telemarketing, kiosk, text message, and internet marketing.
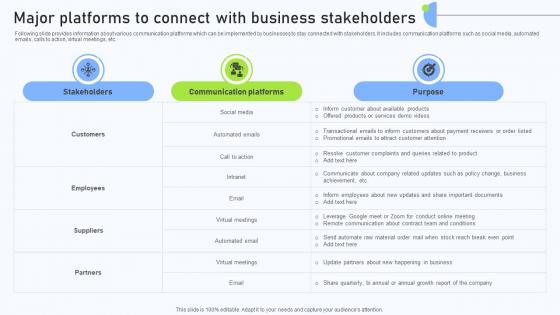
Relationship Management Automation Major Platforms To Connect With Business Stakeholders
Following slide provides information about various communication platforms which can be implemented by businesses to stay connected with stakeholders. It includes communication platforms such as social media, automated emails, calls to action, virtual meetings, etc. Explore a selection of the finest Relationship Management Automation Major Platforms To Connect With Business Stakeholders here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Relationship Management Automation Major Platforms To Connect With Business Stakeholders to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Following slide provides information about various communication platforms which can be implemented by businesses to stay connected with stakeholders. It includes communication platforms such as social media, automated emails, calls to action, virtual meetings, etc.

Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF from Slidegeeks today.

Complete Guide To Launch Best Practices For Website Security Management
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Get a simple yet stunning designed Complete Guide To Launch Best Practices For Website Security Management. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Guide To Launch Best Practices For Website Security Management can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.

Cybersecurity Security Of Employees Devices Ppt Styles Graphic Images PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. This is a cybersecurity security of employees devices ppt styles graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of employees devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
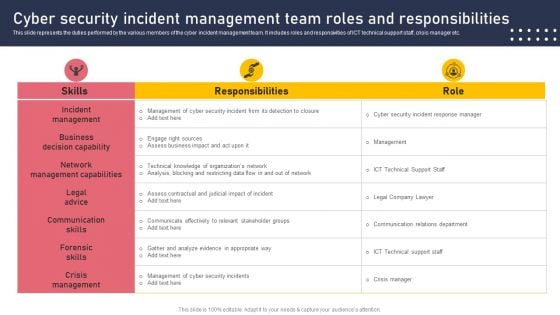
Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Are you searching for a Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF from Slidegeeks today.
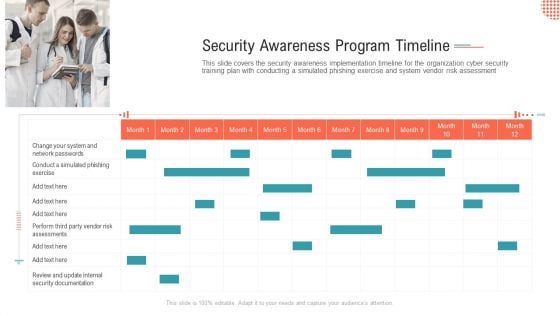
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































