Information Security Ppt
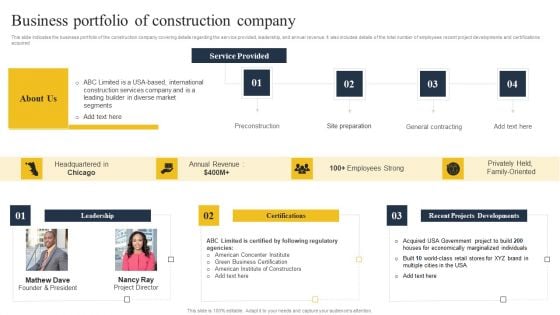
Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF
This slide indicates the business portfolio of the construction company covering details regarding the service provided, leadership, and annual revenue. It also includes details of the total number of employees recent project developments and certifications acquired. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF
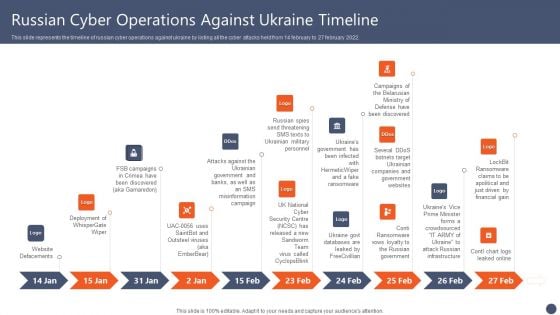
Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF
This slide represents the timeline of russian cyber operations against ukraine by listing all the cyber attacks held from 14 february to 27 february 2022. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
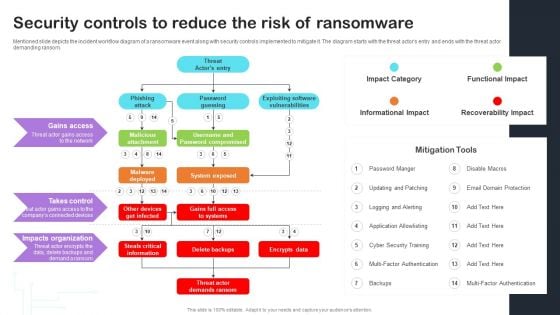
Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Take your projects to the next level with our ultimate collection of Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

SDN Security Architecture Comparison Between Software Defined Networking And SD WAN Structure PDF
This slide depicts the comparison between software defined networking and an SD WAN, which is an internet traffic distribution system that uses SDN ideas to dynamically find the most efficient path for traffic to and from branch locations and data center sites across WANs. Make sure to capture your audiences attention in your business displays with our gratis customizable SDN Security Architecture Comparison Between Software Defined Networking And SD WAN Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF
Slidegeeks has constructed Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF
Slidegeeks is here to make your presentations a breeze with Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
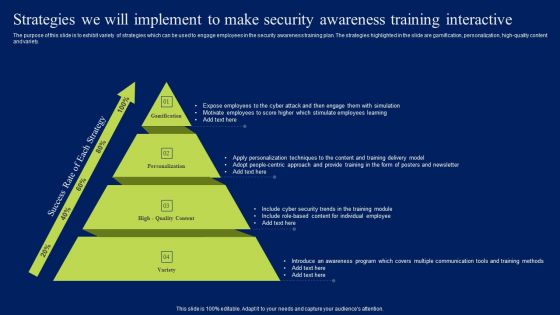
Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Slidegeeks is here to make your presentations a breeze with Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
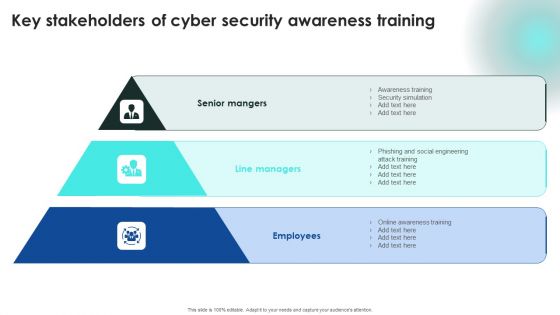
Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
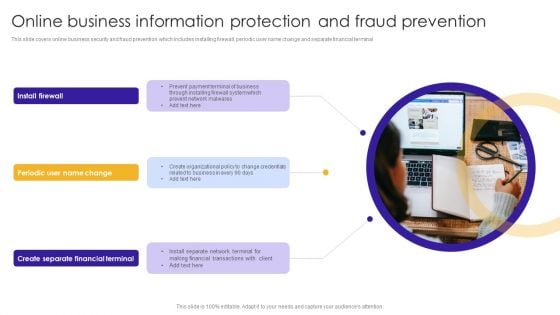
Online Business Information Protection And Fraud Prevention Topics PDF
This slide covers online business security and fraud prevention which includes installing firewall, periodic user name change and separate financial terminal. Persuade your audience using this Online Business Information Protection And Fraud Prevention Topics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Create Separate, Financial Terminal, Prevent Network. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Control Techniques For Real Estate Project Key Goals Of Construction Site Safety Program Professional PDF
This slide indicates the major focus areas for the construction site safety program. It also includes details of multiple program goals such as setting up safety department, identifying hazards and conduct impact, setting up control measures to prevent hazards, and impart safety training. Boost your pitch with our creative Security Control Techniques For Real Estate Project Key Goals Of Construction Site Safety Program Professional PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you donot have to invest time in any additional work. Just grab the template now and use them.
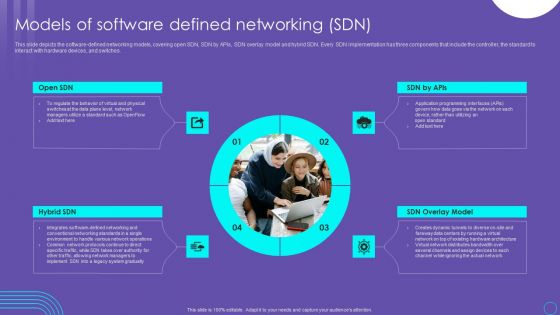
SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF
This slide depicts the software defined networking models, covering open SDN, SDN by APIs, SDN overlay model and hybrid SDN. Every SDN implementation has three components that include the controller, the standard to interact with hardware devices, and switches. Do you know about Slidesgeeks SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
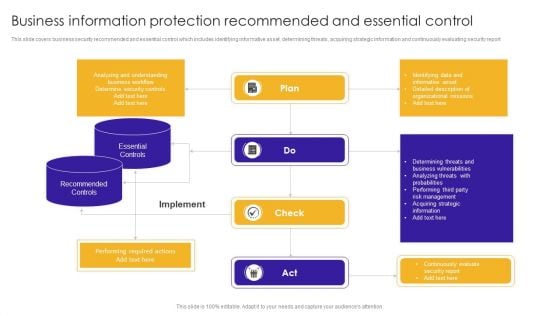
Business Information Protection Recommended And Essential Control Background PDF
This slide covers business security recommended and essential control which includes identifying informative asset, determining threats, acquiring strategic information and continuously evaluating security report. Showcasing this set of slides titled Business Information Protection Recommended And Essential Control Background PDF. The topics addressed in these templates are Determining Threats, Business Vulnerabilities, Risk Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
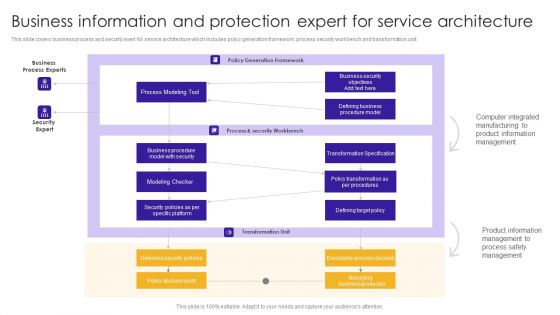
Business Information And Protection Expert For Service Architecture Demonstration PDF
This slide covers business process and security exert for service architecture which includes policy generation framework, process security workbench and transformation unit.Showcasing this set of slides titled Business Information And Protection Expert For Service Architecture Demonstration PDF. The topics addressed in these templates are Business Process, Computer Integrated, Product Information. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Book Under House Conceptually Security PowerPoint Templates And PowerPoint Themes 1012
Book Under House Conceptually Security PowerPoint Templates And PowerPoint Themes 1012-The above template displays a diagram of a 3d house and colorful books under it. This image represents the concept of education. The ideas and plans are on your finger tips. Now imprint them on the minds of your audience via our slides. This image has been conceived to enable you to emphatically communicate your ideas in your educational security PPT presentations on school education, teaching, school subjects etc.-Book Under House Conceptually Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Books under the house, education, future, real estate, security, success Cater for the fallout from any mishap. Create an actionable plan with our Book Under House Conceptually Security PowerPoint Templates And PowerPoint Themes 1012.
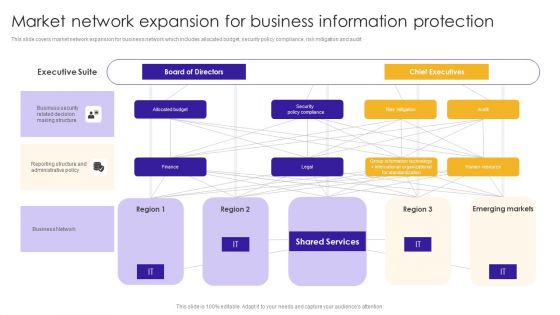
Market Network Expansion For Business Information Protection Sample PDF
This slide covers market network expansion for business network which includes allocated budget, security policy compliance, risk mitigation and audit. Showcasing this set of slides titled Market Network Expansion For Business Information Protection Sample PDF. The topics addressed in these templates are Business Security, Related Decision, Making Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
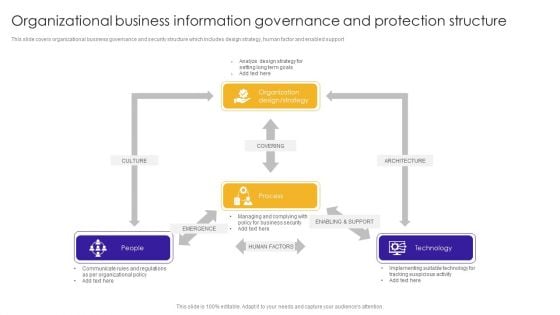
Organizational Business Information Governance And Protection Structure Guidelines PDF
This slide covers organizational business governance and security structure which includes design strategy, human factor and enabled support. Showcasing this set of slides titled Organizational Business Information Governance And Protection Structure Guidelines PDF. The topics addressed in these templates are Communicate Rules, Organizational Policy, Business Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
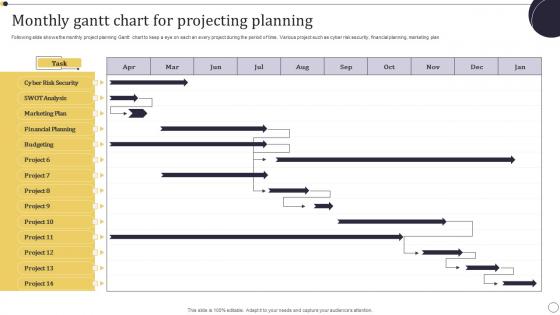
Monthly Gantt Chart For Projecting Planning Information Pdf
Following slide shows the monthly project planning Gantt chart to keep a eye on each an every project during the period of time. Various project such as cyber risk security, financial planning, marketing plan Showcasing this set of slides titled Monthly Gantt Chart For Projecting Planning Information Pdf. The topics addressed in these templates are Marketing Plan, Financial Planning, Cyber Risk Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the monthly project planning Gantt chart to keep a eye on each an every project during the period of time. Various project such as cyber risk security, financial planning, marketing plan
International Organization Standardization 270001 Security Domains That Will Be Addressed By Isms Icons PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a international organization standardization 270001 security domains that will be addressed by isms icons pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization of information security, human resources security, asset management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.This is a IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Incidents, Security Attacks, Common Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
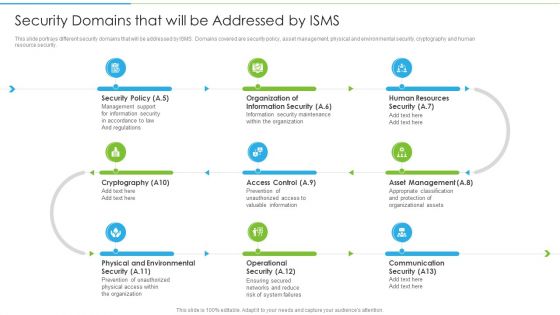
Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policy, Organization Information, Human Resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
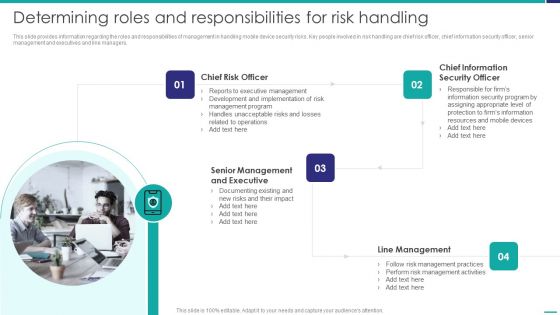
Determining Roles And Responsibilities For Risk Handling Mobile Device Security Management Designs PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. This is a Determining Roles And Responsibilities For Risk Handling Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Executive Management, Development Implementation, Management Program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
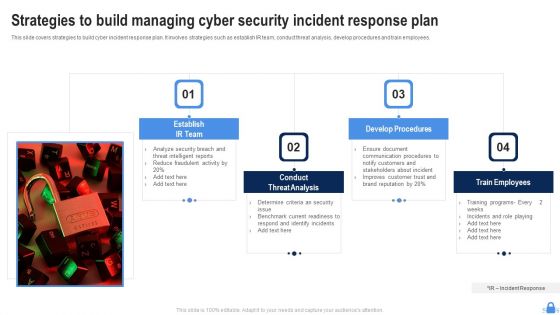
Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF
This slide covers strategies to build cyber incident response plan. It involves strategies such as establish IR team, conduct threat analysis, develop procedures and train employees. Persuade your audience using this Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Establish IR Team, Conduct Threat Analysis, Develop Procedures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
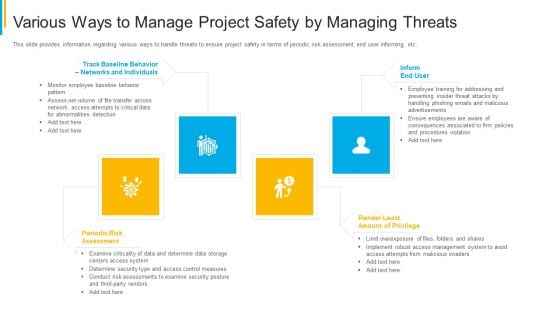
Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
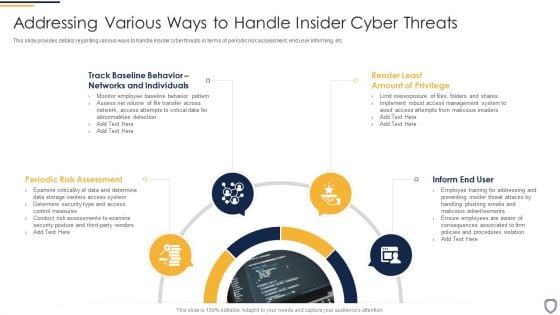
Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Infographics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a corporate security and risk management addressing various ways to handle insider cyber threats infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, inform end user, render least amount of privilege, track baseline behavior networks and individuals . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
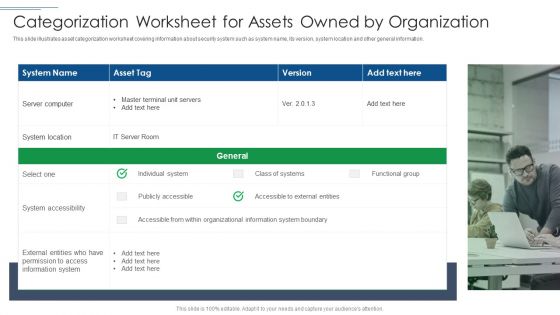
IT Security Risk Management Approach Introduction Categorization Worksheet For Assets Owned By Organization Portrait PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting IT Security Risk Management Approach Introduction Categorization Worksheet For Assets Owned By Organization Portrait PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like System Location, System Accessibility, Information System. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Golden Key With Puzzle Piece On Chain Security PowerPoint Templates And PowerPoint Themes 1012
Golden Key With Puzzle Piece On Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template consists an image of two golden keys attached to a jigsaw puzzle piece. This image refers the concept of solution. It portrays the concept of finance, house, insurance, interest, investment, jigsaw, key, mortgage, problem, prosperity, puzzle, service, solution, success etc. This image has been conceived to enable you to emphatically communicate your ideas in your Business PPT presentations. Deliver amazing presentations to mesmerize your audience.-Golden Key With Puzzle Piece On Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Golden Key With Puzzle, Security, Business, Chains, Symbol, Process and flows You will rarely find fault with our Golden Key With Puzzle Piece On Chain Security PowerPoint Templates And PowerPoint Themes 1012. They are designed by a fastidious team.

Develop Corporate Cyber Security Risk Mitigation Plan Awards And Recognition Organization Protection Services Clipart PDF
This is a develop corporate cyber security risk mitigation plan awards and recognition organization protection services clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like best cyber security, service provider, global leader, cyber security service, 2018, 2019. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
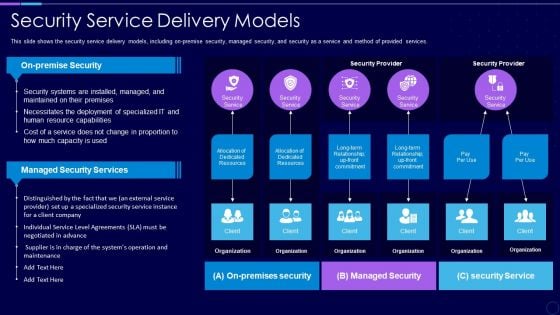
Everything As A Service Xaas For Cloud Computing IT Security Service Delivery Models Diagrams PDF
This slide shows the security service delivery models, including on-premise security, managed security, and security as a service and method of provided services. This is a everything as a service xaas for cloud computing it security service delivery models diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deployment, resource capabilities, security systems, security service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
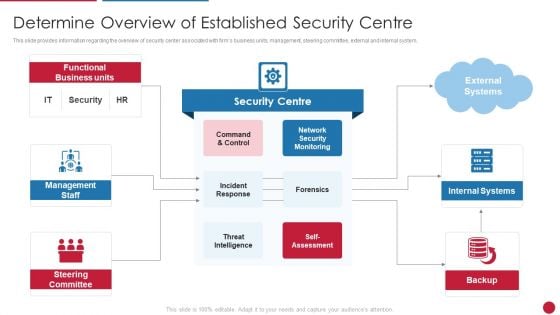
Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security Monitoring, Internal Systems, Steering Committee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
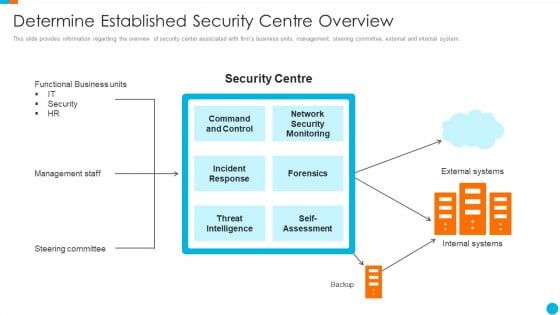
Upgrading Total Project Safety IT Determine Established Security Centre Overview Sample PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a upgrading total project safety it determine established security centre overview sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response, forensics, threat intelligence, command and control, network security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Market Trends Inspiration PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a modern security observation plan to eradicate cybersecurity risk and data breach current market trends inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization of sensitive data, outsourcing, general data protection laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
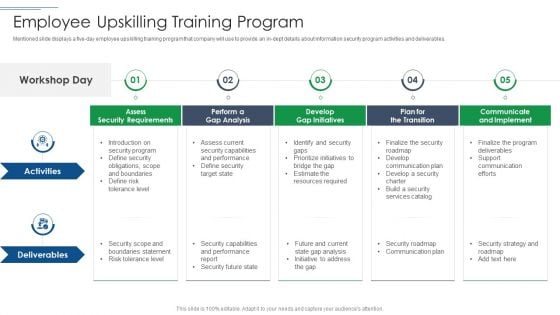
IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables. This is a IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Develop Gap Initiatives, Communicate And Implement, Assess Security Requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Process Integration How Firm Handle Insider Threats Template PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security and process integration how firm handle insider threats template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan How Firm Handle Various Insider Threats At Workplace Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a developing firm security strategy plan how firm handle various insider threats at workplace elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
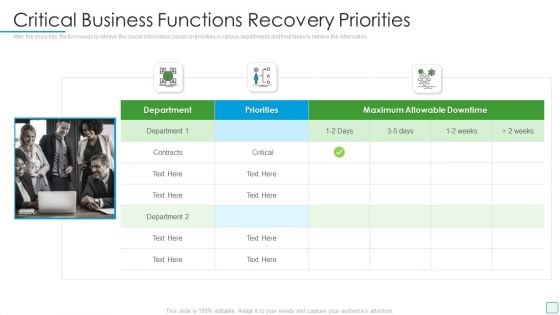
Developing Firm Security Strategy Plan Critical Business Functions Recovery Priorities Infographics PDF
After the crisis hits, the firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. This is a developing firm security strategy plan critical business functions recovery priorities infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical business functions recovery priorities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Addressing Critical Business Functions Recovery Priorities Guidelines PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. This is a corporate security and risk management addressing critical business functions recovery priorities guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like addressing critical business functions recovery priorities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Professional PDF
This is a security management plan steps in detail data backup and data loss recovery plan professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security tools, categories of application, data backup frequency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
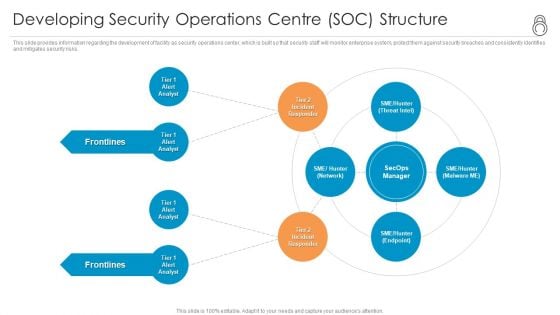
Enhanced Protection Corporate Event Administration Developing Security Operations Centre SOC Structure Formats PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting enhanced protection corporate event administration developing security operations centre soc structure formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This is a Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Container Approach, Platform Approach, Critical Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Executing Security Management Plan To Minimize Threats Diagrams PDF
This is a agenda for executing security management plan to minimize threats diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizational, protect, risks, reduce, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Construction Engineering And Industrial Facility Management Interdependence Resiliency And Security Graphics PDF
This is a construction engineering and industrial facility management interdependence resiliency and security graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, 4 dimensions of infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Development Company Pitch Deck Problems Faced By Companies Security Introduction PDF
This is a it development company pitch deck problems faced by companies security introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poor network security, backup issues, software concerns, qualified experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
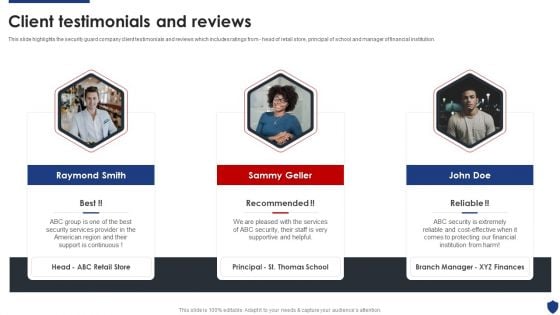
Security Officer Service Company Profile Client Testimonials And Reviews Sample PDF
This is a Security Officer Service Company Profile Client Testimonials And Reviews Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Our Financial, Support Continuous, Security Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
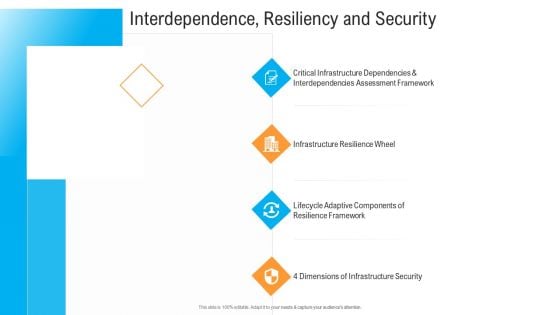
Civil Infrastructure Designing Services Management Interdependence Resiliency And Security Background PDF
This is a civil infrastructure designing services management interdependence resiliency and security background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interdependence, resiliency and security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
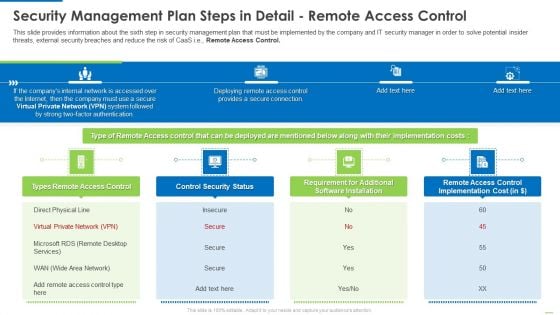
Security Management Plan Steps In Detail Remote Access Control Diagrams PDF
This is a security management plan steps in detail remote access control diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control security status, requirement for additional software installation, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Risk Assessment And Analysis Template PDF
This is a security management plan steps in detail risk assessment and analysis template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential consequence, security risks or liabilities, management to educate You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
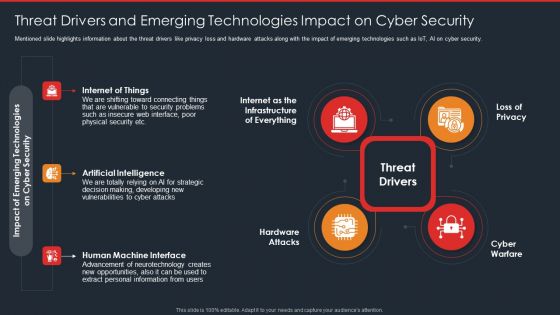
Data Safety Initiatives Threat Drivers And Emerging Technologies Impact On Cyber Security Brochure PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a data safety initiatives threat drivers and emerging technologies impact on cyber security brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat drivers, loss privacy, cyber warfare, hardware attacks, artificial intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.This is a IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Update, Malicious Attachments, Connection Accurately. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Investigations by HR, Phishing Detection And Prevention, Risk Mitigation of Left Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
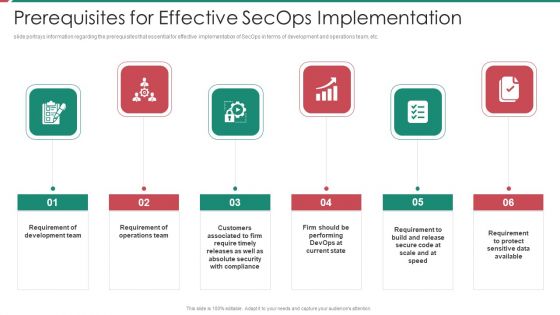
Security And Process Integration Prerequisites For Effective Secops Implementation Microsoft PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a security and process integration prerequisites for effective secops implementation microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
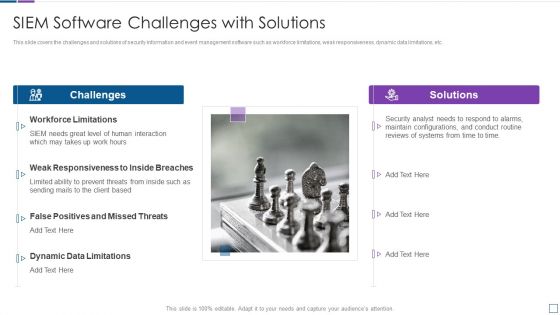
Real Time Assessment Of Security Threats SIEM Software Challenges With Solutions Inspiration PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a real time assessment of security threats siem software challenges with solutions inspiration pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions, workforce limitations, false positives and missed threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.This is a Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Integrate Access, Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
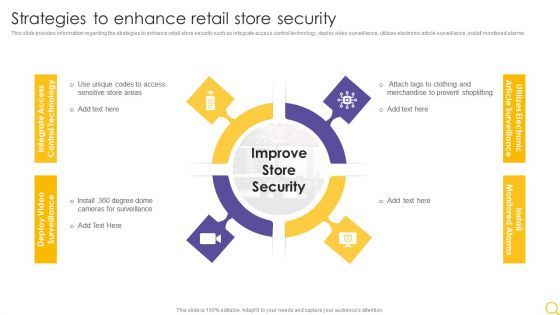
Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. This is a Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Article Surveillance, Install Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
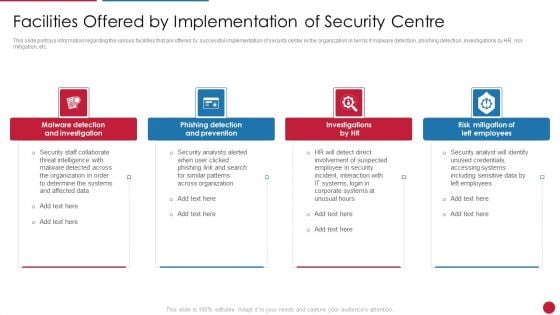
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Functioning Centre Various Metrics To Measure Secops System Performance Icons PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. This is a security functioning centre various metrics to measure secops system performance icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security analysts productivity, escalation breakdown, average time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
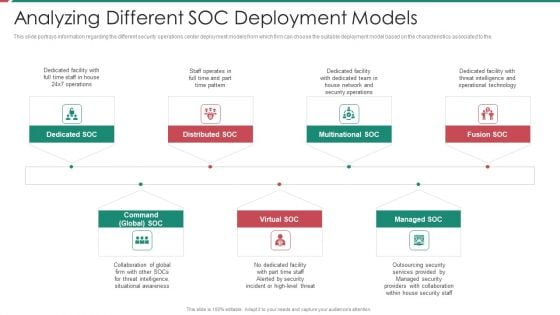
Security And Process Integration Analyzing Different SOC Deployment Models Diagrams PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a security and process integration analyzing different soc deployment models diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
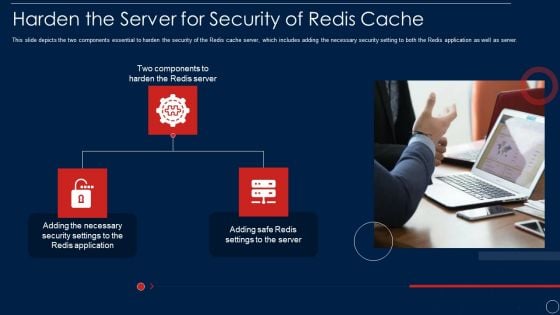
Redis Cache Data Structure IT Harden The Server For Security Of Redis Cache Template PDF
This slide depicts the two components essential to harden the security of the Redis cache server, which includes adding the necessary security setting to both the Redis application as well as server. This is a redis cache data structure it harden the server for security of redis cache template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like harden the server for security of redis cache. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































