Information Security Ppt
Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF
Showcasing this set of slides titled Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF. The topics addressed in these templates are Cyber Security, Risk Management, Icon, IT Risk, Control Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security For Cloud Based Systems Management Icon For IT Project Rules PDF
Persuade your audience using this Security For Cloud Based Systems Management Icon For IT Project Rules PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Management, IT Project. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon For Internet Of Things Application In Safety And Security Cameras Designs PDF
Showcasing this set of slides titled Icon For Internet Of Things Application In Safety And Security Cameras Designs PDF. The topics addressed in these templates are Internet Of Things, Application In Safety, Security Cameras. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Emergency Strategic Action Plan Analysis Icon For System Security Designs PDF
Showcasing this set of slides titled emergency strategic action plan analysis icon for system security designs pdf. The topics addressed in these templates are emergency strategic action plan analysis icon for system security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Construction Site Security Checklist To Ensure Systematic Progress Of Project Professional Pdf
Following slide shows the checklist for construction site safety to ensure orderly project progress which will assist in attaining overall growth. It includes parameters such as does work area is safe for employees, does employees have proper training of equipment, etc. Showcasing this set of slides titled Construction Site Security Checklist To Ensure Systematic Progress Of Project Professional Pdf. The topics addressed in these templates are Checklist Parameters, Comment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the checklist for construction site safety to ensure orderly project progress which will assist in attaining overall growth. It includes parameters such as does work area is safe for employees, does employees have proper training of equipment, etc.
Icon Of Wireless Network Security System For WIFI Networks With Smart Lock Sample PDF
Persuade your audience using this icon of wireless network security system for wifi networks with smart lock sample pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including icon of wireless network security system for wifi networks with smart lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon Of Wireless Network Security System With WIFI Lock Elements PDF
Persuade your audience using this icon of wireless network security system with wifi lock elements pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including icon of wireless network security system with wifi lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
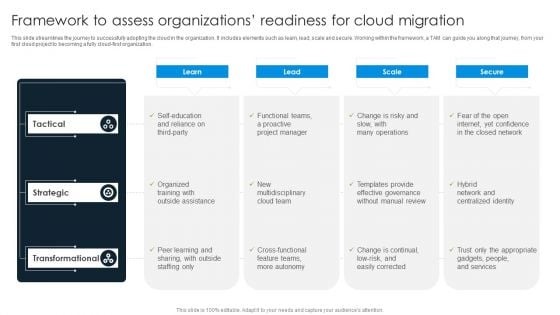
Framework To Assess Organizations Readiness For Cloud Migration Information PDF
This slide streamlines the journey to successfully adopting the cloud in the organization. It includes elements such as learn, lead, scale and secure. Working within the framework, a TAM can guide you along that journey, from your first cloud project to becoming a fully cloud-first organization. Pitch your topic with ease and precision using this Framework To Assess Organizations Readiness For Cloud Migration Information PDF. This layout presents information on Tactical, Strategic, Transformational. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
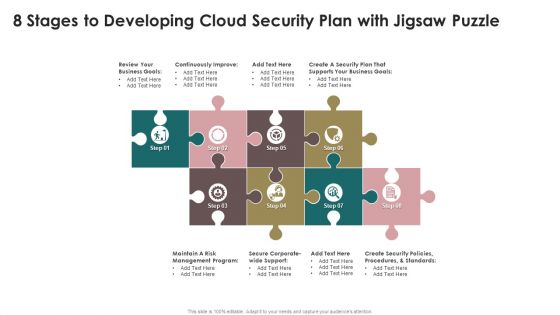
8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF
Persuade your audience using this 8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Security Plan, Management Program. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
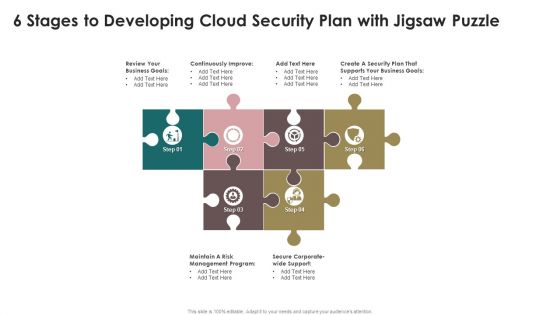
6 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Brochure PDF
Persuade your audience using this 6 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Security Plan, Business Goals. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Bring Your Own Device Security Policy Check In Organizations Icon Summary PDF
Persuade your audience using this Bring Your Own Device Security Policy Check In Organizations Icon Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Bring Your Own, Device Security Policy, Check Organizations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

About Us For Our Firewall Solutions Company Cloud Security Firewall Proposal
This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry-leading organizations, and history.Elevate your presentations with our intuitive About Us For Our Firewall Solutions Company Cloud Security Firewall Proposal template. Whether you are delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression. This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry-leading organizations, and history.
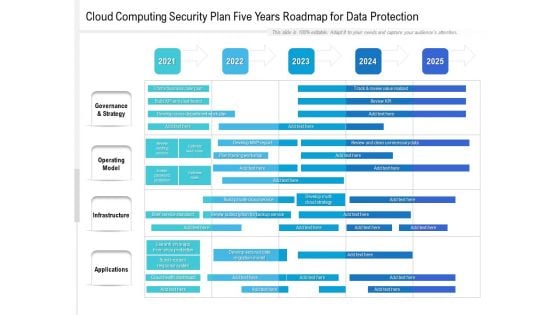
Cloud Computing Security Plan Five Years Roadmap For Data Protection Template
Introducing our cloud computing security plan five years roadmap for data protection template. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
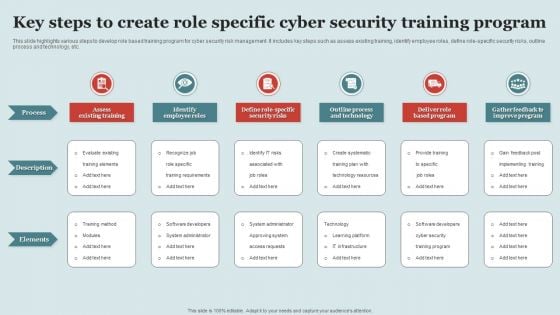
Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
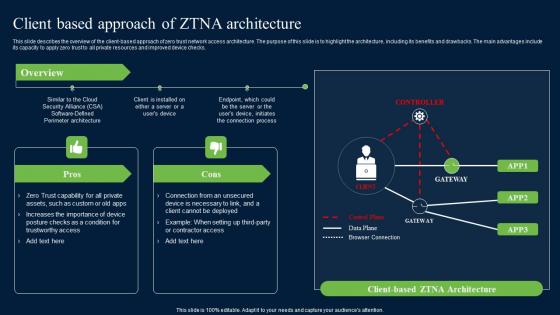
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.

Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF
This slide shows solutions to various challenges faced by organizations to provide cloud security. These challenges are data breaches, lack of expertise, insider threats and unsecured APIs. Showcasing this set of slides titled Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF. The topics addressed in these templates are Solutions To Overcome, Various Security For Cloud, Based Systems Challenges . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
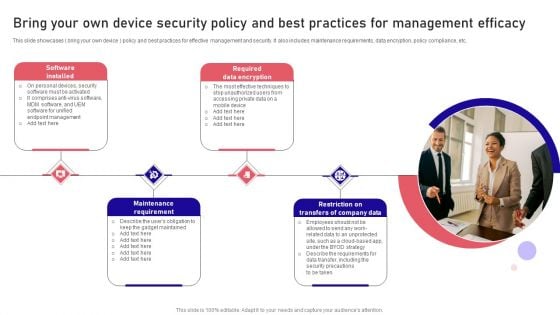
Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF
This slide showcases bring your own device policy and best practices for effective management and security. It also includes maintenance requirements, data encryption, policy compliance, etc. Persuade your audience using this Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Software Installed, Maintenance Requirement, Encryption . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
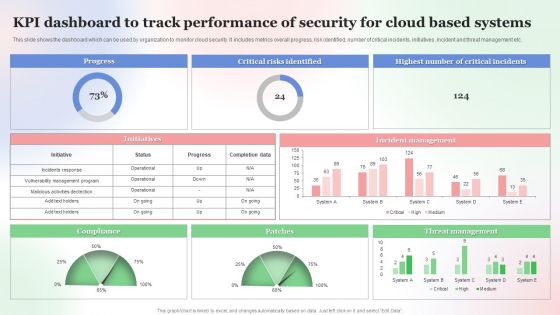
KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF
This slide shows the dashboard which can be used by organization to monitor cloud security. It includes metrics overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Showcasing this set of slides titled KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF. The topics addressed in these templates are Kpi Dashboard To Track, Performance Of Security, Cloud Based Systems . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
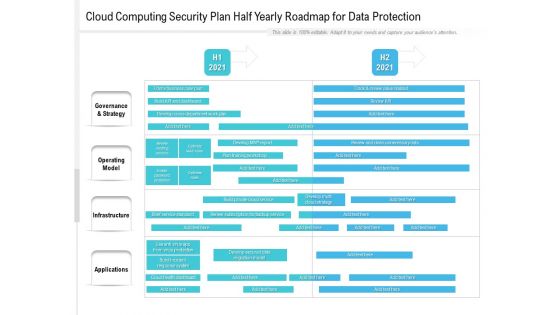
Cloud Computing Security Plan Half Yearly Roadmap For Data Protection Formats
Presenting our innovatively structured cloud computing security plan half yearly roadmap for data protection formats Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
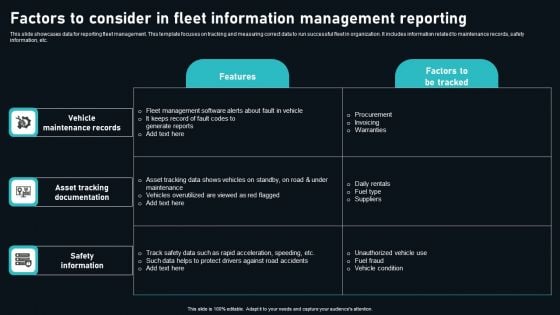
Factors To Consider In Fleet Information Management Reporting Topics PDF
This slide showcases data for reporting fleet management. This template focuses on tracking and measuring correct data to run successful fleet in organization. It includes information related to maintenance records, safety information, etc. Pitch your topic with ease and precision using this Factors To Consider In Fleet Information Management Reporting Topics PDF. This layout presents information on Vehicle Maintenance Records, Asset Tracking Documentation, Safety Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
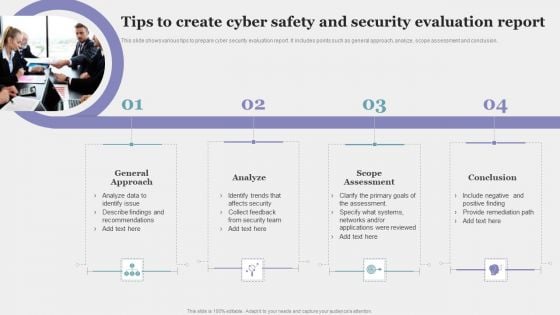
Tips To Create Cyber Safety And Security Evaluation Report Pictures PDF
This slide shows various tips to prepare cyber security evaluation report. It includes points such as general approach, analyze, scope assessment and conclusion. Persuade your audience using this Tips To Create Cyber Safety And Security Evaluation Report Pictures PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including General Approach, Analyze, Scope Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Awareness Campaign Roadmap With Goal And Target Audience Mockup PDF
This slide shows timeline for campaign to raise security awareness . It covers target audience, goal, phase 1 and 2. Persuade your audience using this Security Awareness Campaign Roadmap With Goal And Target Audience Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Target Audience, Goal, awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
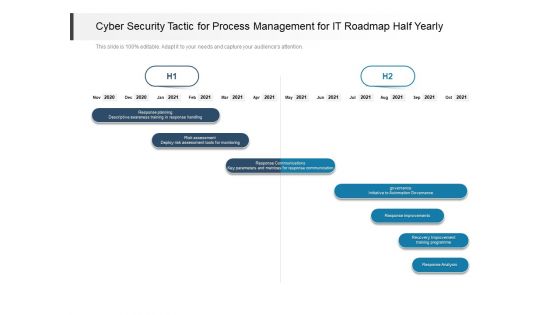
Cyber Security Tactic For Process Management For IT Roadmap Half Yearly Topics
Introducing our cyber security tactic for process management for it roadmap half yearly topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
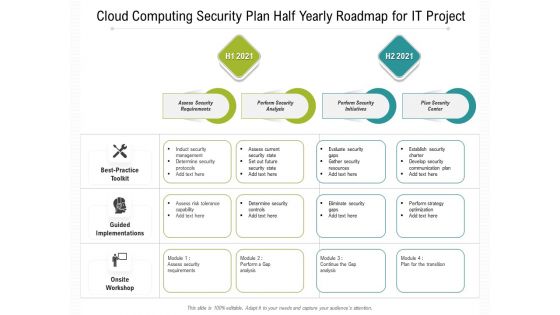
Cloud Computing Security Plan Half Yearly Roadmap For IT Project Introduction
Introducing our cloud computing security plan half yearly roadmap for it project introduction. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
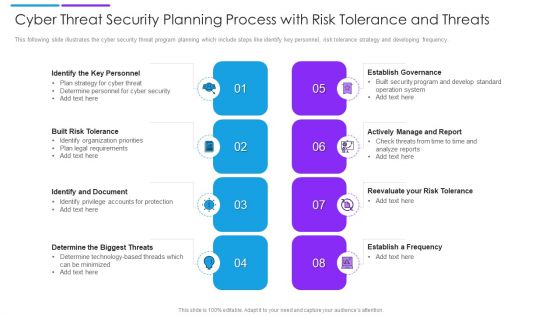
Cyber Threat Security Planning Process With Risk Tolerance And Threats Formats PDF
This following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Persuade your audience using this cyber threat security planning process with risk tolerance and threats formats pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including establish governance, actively manage and report, built risk tolerance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon For Comparative Analysis Of Cloud And Traditional Computing It Security Rules PDF
Showcasing this set of slides titled Icon For Comparative Analysis Of Cloud And Traditional Computing It Security Rules PDF. The topics addressed in these templates are Icon Comparative Analysis Cloud, Traditional Computing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
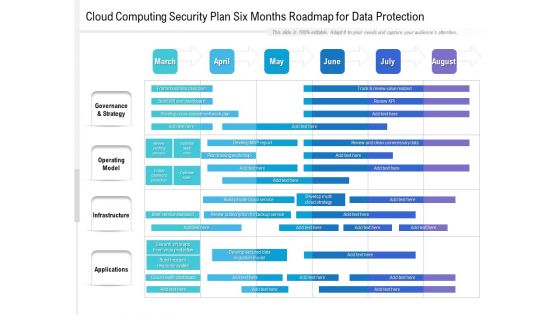
Cloud Computing Security Plan Six Months Roadmap For Data Protection Themes
Presenting our jaw dropping cloud computing security plan six months roadmap for data protection themes. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
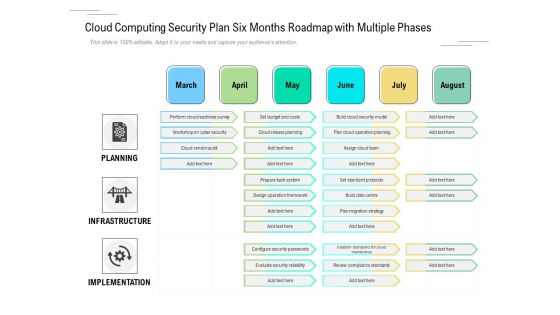
Cloud Computing Security Plan Six Months Roadmap With Multiple Phases Themes
Introducing our cloud computing security plan six months roadmap with multiple phases themes. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
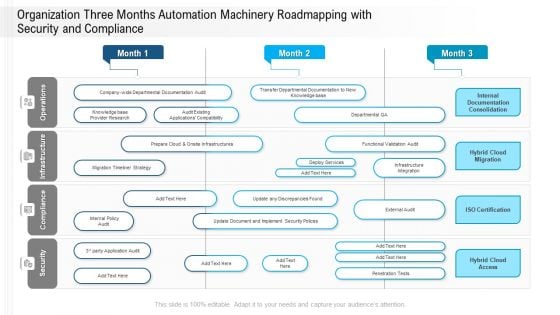
Organization Three Months Automation Machinery Roadmapping With Security And Compliance Rules
Introducing our organization three months automation machinery roadmapping with security and compliance rules. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
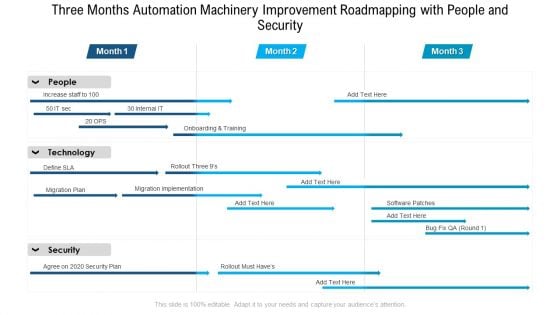
Three Months Automation Machinery Improvement Roadmapping With People And Security Designs
Introducing our three months automation machinery improvement roadmapping with people and security designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
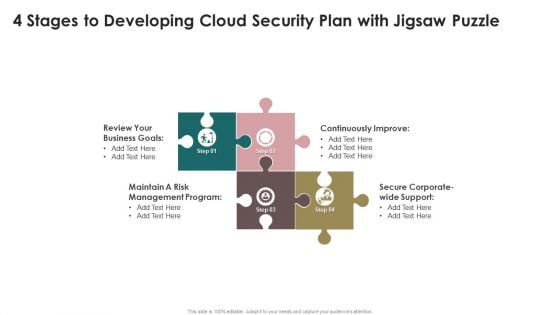
4 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Graphics PDF
Persuade your audience using this 4 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Management Program, Continuously Improve. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
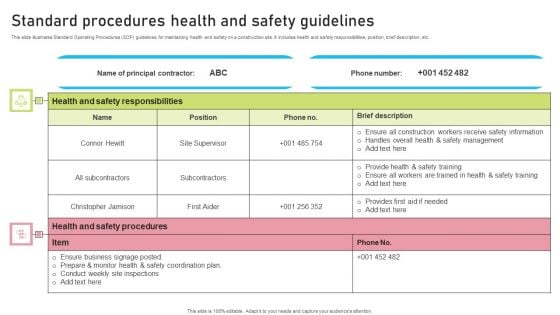
Standard Procedures Health And Safety Guidelines Information PDF
This slide illustrates Standard Operating Procedures SOP guidelines for maintaining health and safety on a construction site. It includes health and safety responsibilities, position, brief description, etc. Showcasing this set of slides titled Standard Procedures Health And Safety Guidelines Information PDF. The topics addressed in these templates are Contractor, Phone Number, Guidelines. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
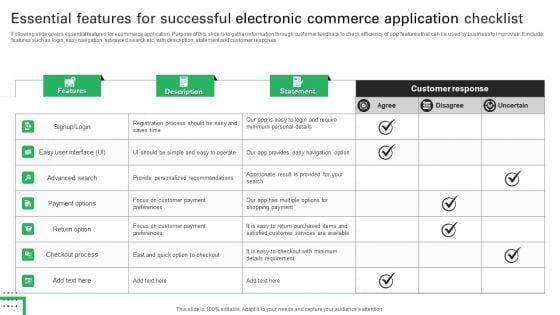
Essential Features For Successful Electronic Commerce Application Checklist Information PDF
Following slide covers essential features for ecommerce application. Purpose of this slide is to gather information through customer feedback to check efficiency of app features that can be used by business to improvise. It include features such as login, easy navigation, advanced search etc. with description, statement and customer response. Showcasing this set of slides titled Essential Features For Successful Electronic Commerce Application Checklist Information PDF. The topics addressed in these templates are Personalized Recommendations, Customer Response, Return Purchased . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
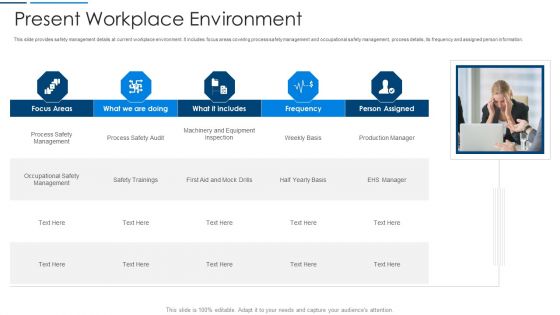
Information Technology Transformation Organization Present Workplace Environment Topics PDF
This slide provides safety management details at current workplace environment. It includes focus areas covering process safety management and occupational safety management, process details, its frequency and assigned person information. Deliver and pitch your topic in the best possible manner with this information technology transformation organization present workplace environment topics pdf. Use them to share invaluable insights on management, production manager, equipment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
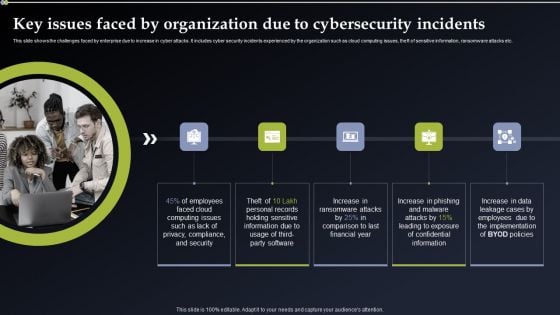
Deploying Cyber Security Incident Response Administration Key Issues Faced By Organization Due Brochure PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Key Issues Faced By Organization Due Brochure PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Key Issues Faced By Organization Due Brochure PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
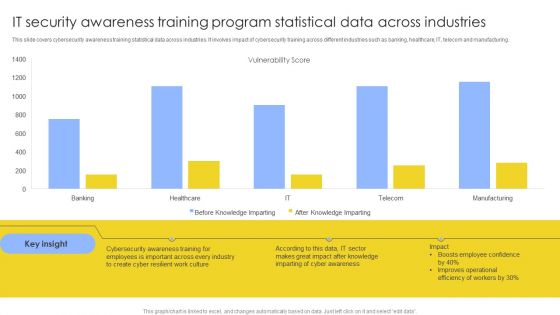
IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF
This slide covers cybersecurity awareness training statistical data across industries. It involves impact of cybersecurity training across different industries such as banking, healthcare, IT, telecom and manufacturing. Showcasing this set of slides titled IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF. The topics addressed in these templates are Vulnerability Score, Cyber Awareness, Improves Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Comparative Assessment Of Fleet Information Management Software Icons PDF
This slide showcases different tools used for fleet management. This template focuses on creating more efficient driving routes, tracking vehicle inventory and providing cost management analysis. It includes information related to live webinars, safety management, etc. Showcasing this set of slides titled Comparative Assessment Of Fleet Information Management Software Icons PDF. The topics addressed in these templates are Live Webinars, Activity Tracking, Audit Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
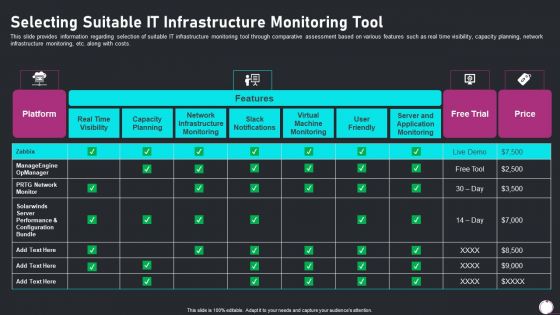
Information Technology Transformation Playbook Selecting Suitable It Infrastructure Slides PDF
This slide provides information regarding selection of suitable IT infrastructure monitoring tool through comparative assessment based on various features such as real time visibility, capacity planning, network infrastructure monitoring, etc. along with costs. Deliver an awe inspiring pitch with this creative information technology transformation playbook selecting suitable it infrastructure slides pdf bundle. Topics like selecting suitable it infrastructure monitoring tool can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
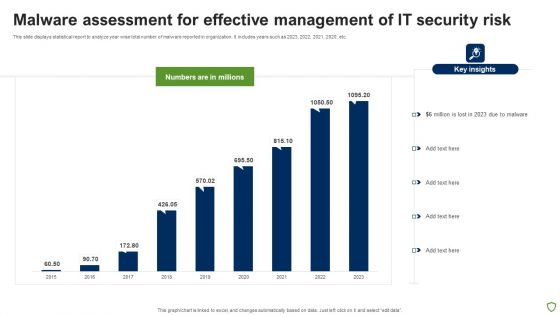
Malware Assessment For Effective Management Of IT Security Risk Portrait PDF
This slide displays statistical report to analyze year wise total number of malware reported in organization. It includes years such as 2023, 2022, 2021, 2020, etc. Showcasing this set of slides titled Malware Assessment For Effective Management Of IT Security Risk Portrait PDF. The topics addressed in these templates are Malware Assessment For Effective, Management IT Security Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
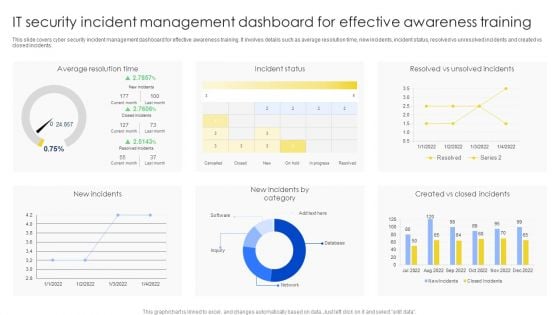
IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF
This slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
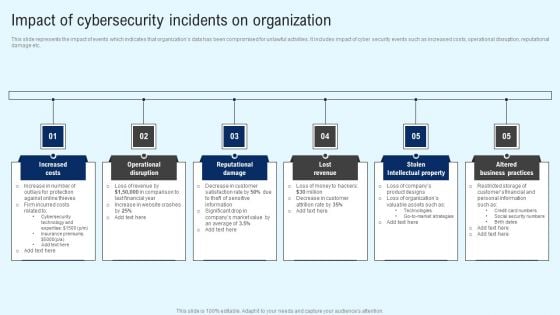
Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Get a simple yet stunning designed Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
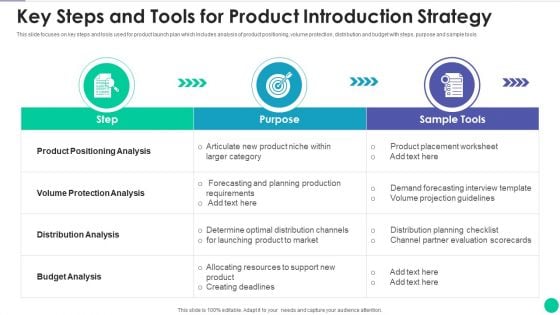
Key Steps And Tools For Product Introduction Strategy Information PDF
This slide focuses on key steps and tools used for product launch plan which includes analysis of product positioning, volume protection, distribution and budget with steps, purpose and sample tools Pitch your topic with ease and precision using this key steps and tools for product introduction strategy information pdf. This layout presents information on key steps and tools for product introduction strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Prevention Of Information Social Engineering Attack Prevention Techniques Infographics PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. There are so many reasons you need a Prevention Of Information Social Engineering Attack Prevention Techniques Infographics PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF
This slide describes the different methods used by blockchain technology to prevent data from fraud and stealing. The purpose of this slide is to showcase the various techniques and technologies used in blockchain technology to prevent fraud and data theft. Get a simple yet stunning designed Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings. Get a simple yet stunning designed Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings.
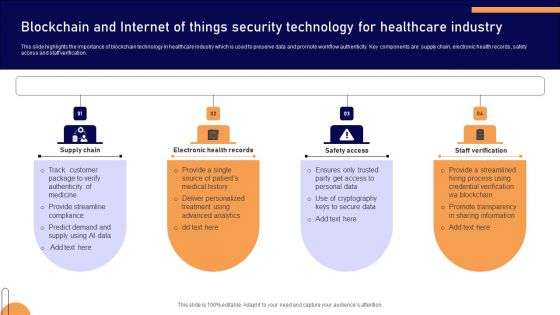
Blockchain And Internet Of Things Security Technology For Healthcare Industry Mockup PDF
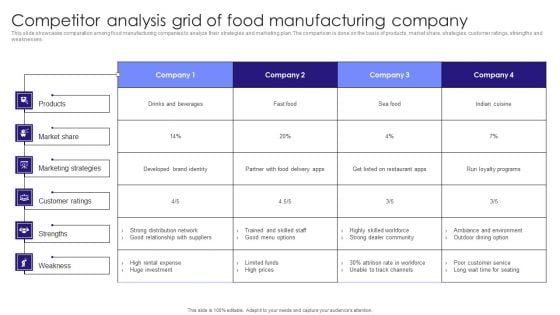
Competitor Analysis Grid Of Food Manufacturing Company Information PDF
This slide showcases comparation among food manufacturing companies to analyze their strategies and marketing plan. The comparison is done on the basis of products, market share, strategies, customer ratings, strengths and weaknesses.Pitch your topic with ease and precision using this Competitor Analysis Grid Of Food Manufacturing Company Information PDF. This layout presents information on Marketing Strategies, Customer Ratings, Distribution Network. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
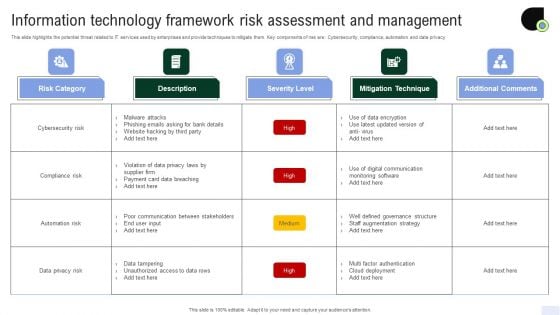
Information Technology Framework Risk Assessment And Management Diagrams PDF
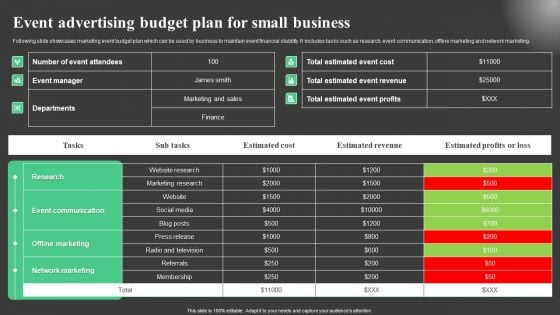
Event Advertising Budget Plan For Small Business Information PDF
Following slide showcases marketing event budget plan which can be used by business to maintain event financial stability. It includes tasks such as research, event communication, offline marketing and network marketing. Showcasing this set of slides titled Event Advertising Budget Plan For Small Business Information PDF. The topics addressed in these templates are Tasks, Estimated Cost, Estimated Revenue . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
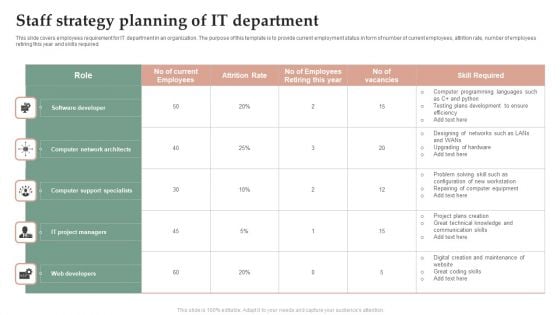
Staff Strategy Planning Of IT Department Information PDF
This slide covers employees requirement for IT department in an organization. The purpose of this template is to provide current employment status in form of number of current employees, attrition rate, number of employees retiring this year and skills required. Showcasing this set of slides titled Staff Strategy Planning Of IT Department Information PDF. The topics addressed in these templates are Software Developer, Computer Network Architects, Computer Support Specialists. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
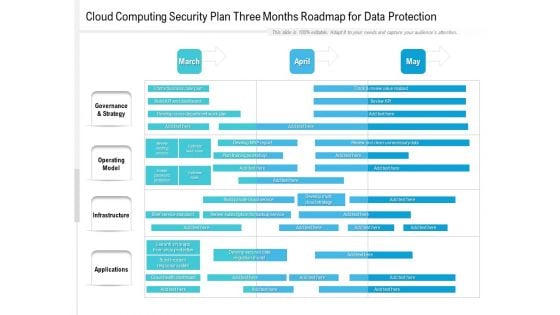
Cloud Computing Security Plan Three Months Roadmap For Data Protection Structure
Presenting the cloud computing security plan three months roadmap for data protection structure. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
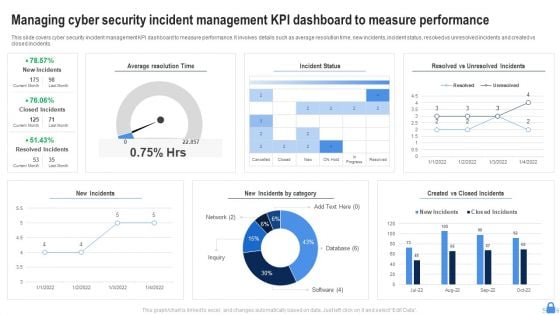
Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF
This slide covers cyber security incident management KPI dashboard to measure performance. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF
Get a simple yet stunning designed Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.
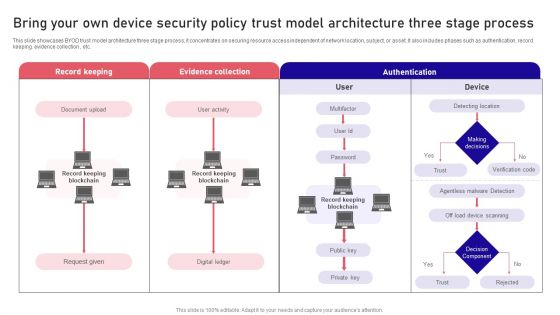
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V
This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc.
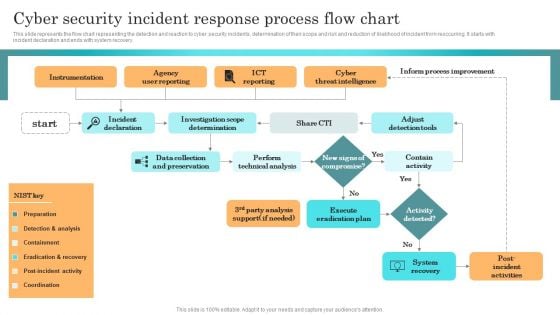
Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF from Slidegeeks and deliver a wonderful presentation.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF
This slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Persuade your audience using this IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Attack Vector, Examples, Objective Problem Identifier. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































