Information Security Ppt

Financing Catalogue For Security Underwriting Agreement Share Allocation Process Clipart PDF
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. Presenting financing catalogue for security underwriting agreement share allocation process clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like in case undersubscription, in case of oversubscription. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
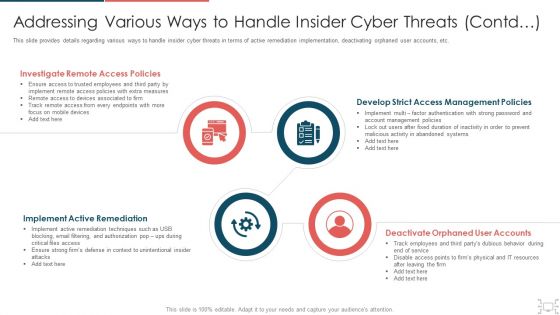
cyber security administration in organization addressing various ways to handle insider cyber active template pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting cyber security administration in organization addressing various ways to handle insider cyber active template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like investigate, access, policies, remediation, implement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
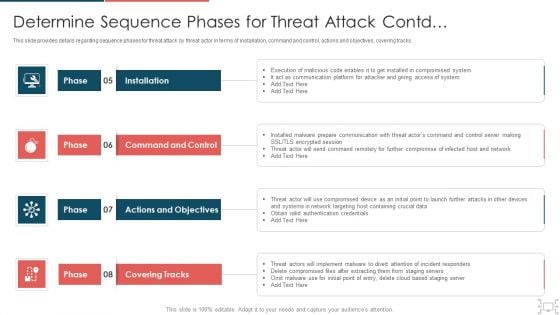
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
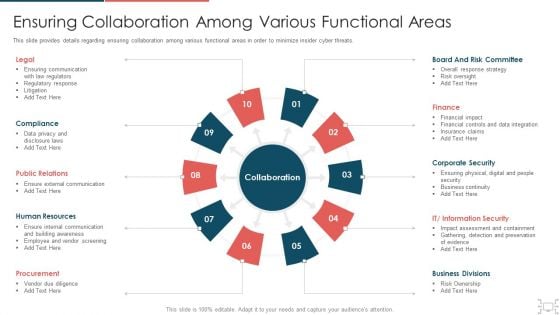
cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
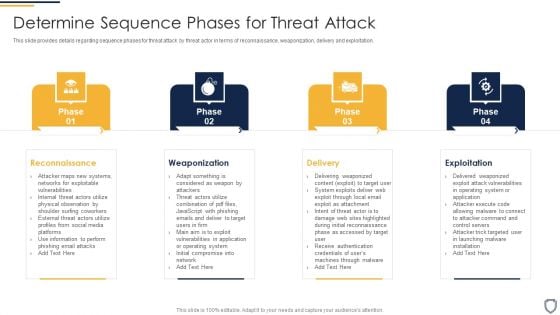
Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Ideas PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting corporate security and risk management determine sequence phases for threat attack ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
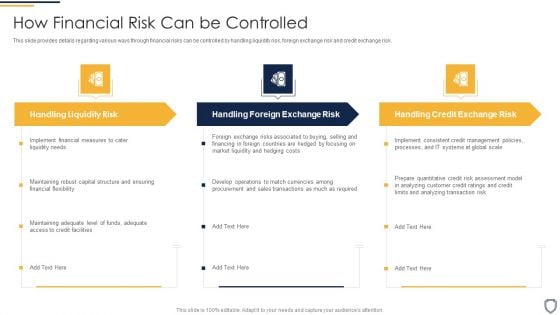
Corporate Security And Risk Management How Financial Risk Can Be Controlled Infographics PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting corporate security and risk management how financial risk can be controlled infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Various Types Of Workplace Violence And Threats Designs PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Presenting corporate security and risk management various types of workplace violence and threats designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like threats or threatening behavior, physical assault, property damage, stalking, harassment or intimidation . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
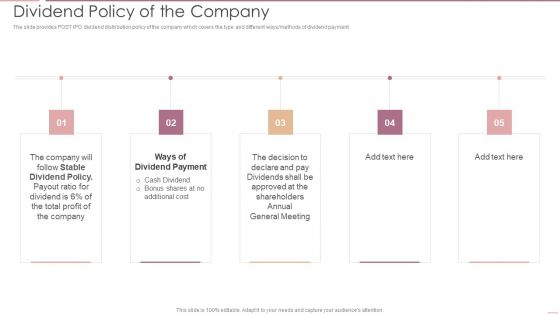
Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF
The slide provides POST IPO dividend distribution policy of the company which covers the type and different ways methods of dividend payment.Presenting Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Stable Dividend, Dividend Payment, General Meeting In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Investment Banking Security Underwriting Pitchbook Key Objectives Of The IPO Issue Slides PDF
The slide provides the companys objectives behind issuing IPO. Key objectives include future expansion, option of alternative currency, cash out option, paying off debts etc. Presenting Investment Banking Security Underwriting Pitchbook Key Objectives Of The IPO Issue Slides PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Expansion, Alternative Currency, Paying Debts In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
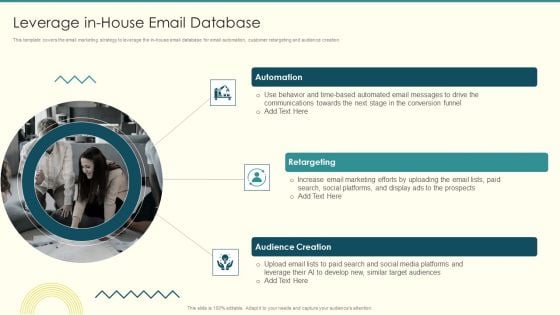
Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF
This template covers the email marketing strategy to leverage the in house email database for email automation, customer retargeting and audience creation. Presenting Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Communications Towards, Automated Messages, Social Platforms. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Optimize Onpage SEO Include Title Tag And Meta Descriptions Formats PDF
This template covers search engine optimization guidelines to optimal title length for title tag and to write meta description displayed on the SERPs . Presenting Security And Performance Digital Marketing Optimize Onpage SEO Include Title Tag And Meta Descriptions Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Currently Limited, Typically Displays, Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
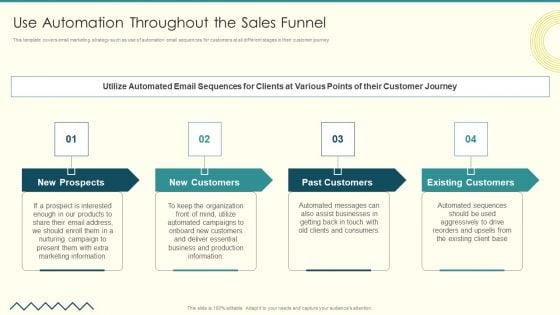
Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF
This template covers email marketing strategy such as use of automation email sequences for customers at all different stages in their customer journey . Presenting Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Past Customers, Existing Customers, Assist Businesses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
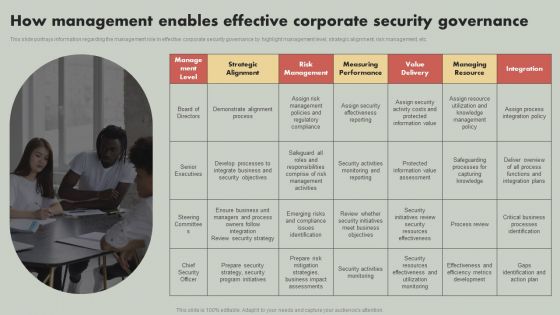
IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Get a simple yet stunning designed IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
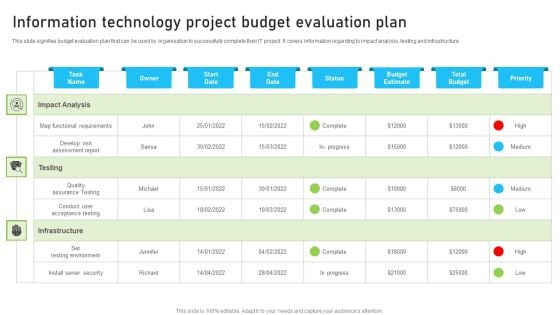
Information Technology Project Budget Evaluation Plan Pictures PDF
This slide signifies the project key performance indicator dashboard to evaluate financial budget evaluation. It covers information regarding to allocated and used budget. Pitch your topic with ease and precision using this Information Technology Project Budget Evaluation Plan Pictures PDF. This layout presents information on Develop Risk Assessment Report, Environment, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Internet Defence Protection Certification Roadmap For Career Advancement Information PDF
This slide represents cybersecurity certification roadmap illustrating certificates such as CompTIA ITFplus, CompTIA Aplus, CompTIA Network plus etc for professional growth.Pitch your topic with ease and precision using this Internet Defence Protection Certification Roadmap For Career Advancement Information PDF. This layout presents information on Intermediate Level, Information Security, Data Specialist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Get a simple yet stunning designed CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc.
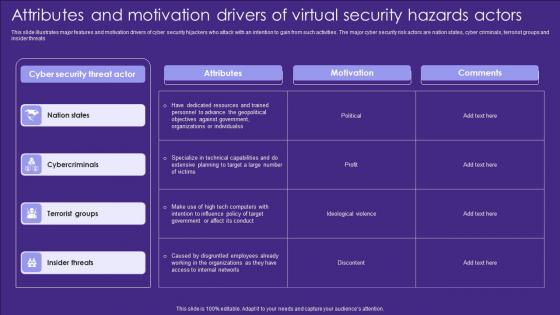
Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf
This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats Showcasing this set of slides titled Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf. The topics addressed in these templates are Attributes, Motivation, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats
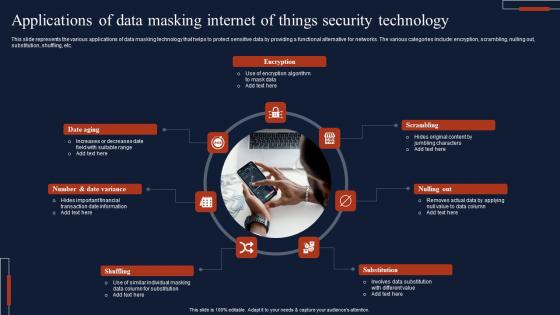
Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc.

Effective IT Risk Management Process Budget For Information Topics PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver and pitch your topic in the best possible manner with this effective it risk management process budget for information topics pdf. Use them to share invaluable insights on incident management, risk management, asset management, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.

Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V
The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts. Get a simple yet stunning designed Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts.
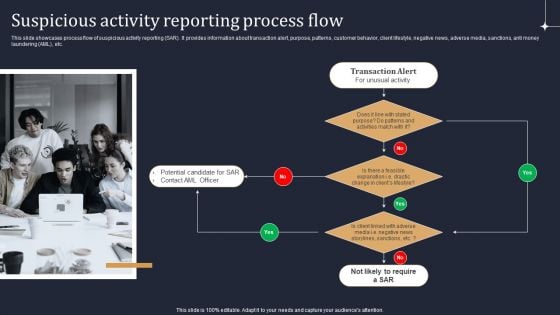
KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF
This slide showcases process flow of suspicious activity reporting SAR. It provides information about transaction alert, purpose, patterns, customer behavior, client lifestyle, negative news, adverse media, sanctions, anti money laundering AML, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
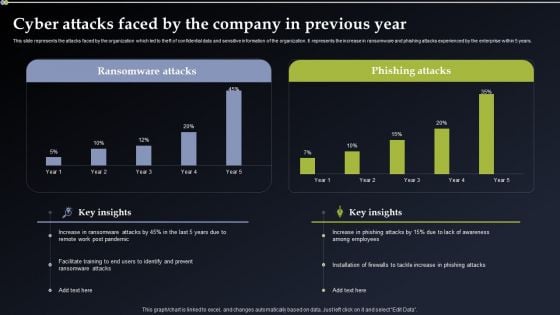
Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF
The following slide highlights key responsibilities of the digitization of security systems team with the position level and requirements. The various positions mentioned in the slide are security engineer, senior security engineer, distinguished security engineer and digitization of security systems manager. Showcasing this set of slides titled Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF. The topics addressed in these templates are Security Engineer, Senior Security Engineer, Security Automation Manager. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
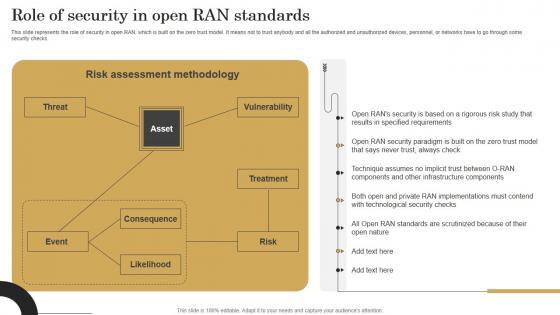
Role Of Security In Open Ran Standards Revolutionizing Mobile Networks Ideas PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Role Of Security In Open Ran Standards Revolutionizing Mobile Networks Ideas PDF from Slidegeeks and deliver a wonderful presentation. This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks.

Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V
This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Get a simple yet stunning designed Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.
Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf
Showcasing this set of slides titled Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf The topics addressed in these templates are Blockchain Internet, Things Security, Technology For Business All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Image For Personal Biometrics Internet Of Things Security Technology Summary Pdf
Showcasing this set of slides titled Image For Personal Biometrics Internet Of Things Security Technology Summary Pdf The topics addressed in these templates are Image For Personal, Biometrics Internet, Security Technology All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Image For Personal Biometrics Internet Of Things Security Technology Summary Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Of Things Security Technology Image For Mobile Application Download Pdf
Showcasing this set of slides titled Internet Of Things Security Technology Image For Mobile Application Download Pdf The topics addressed in these templates are Internet Of Things, Security Technology, Image For Mobile Application All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Internet Of Things Security Technology Image For Mobile Application Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Get a simple yet stunning designed How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc.

Data Processing Maturity Model With Information Architecture Background PDF
Persuade your audience using this data processing maturity model with information architecture background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including data services, data management, security management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Accountability And Responsibility Of The Employees Information PDF
This slide covers the RACI matrix of an organization based on different departments such as facilities, plant, HR, security, project, etc.Deliver and pitch your topic in the best possible manner with this Accountability And Responsibility Of The Employees Information PDF. Use them to share invaluable insights on Identify A Minimum, Review Quotes Contractor Selection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Get a simple yet stunning designed CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB.
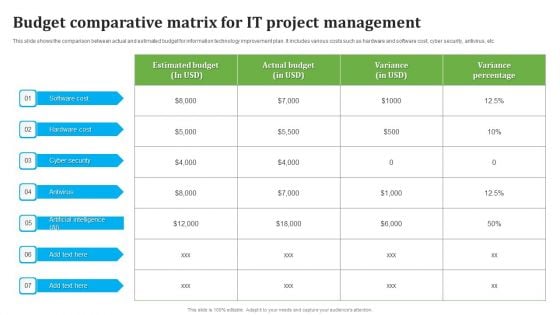
Budget Comparative Matrix For IT Project Management Information PDF
This slide shows the comparison between actual and estimated budget for information technology improvement plan. It includes various costs such as hardware and software cost, cyber security, antivirus, etc. Showcasing this set of slides titled Budget Comparative Matrix For IT Project Management Information PDF. The topics addressed in these templates are Budget Comparative Matrix, IT Project Management . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Task Completion Status Report With Project Details Information PDF
Following slide showcases work completion report which can be used by project manager to evaluate the success or failure of a project. It provides information about project name, objective, manager, sponsor, start and finish date, total hours taken etc. Showcasing this set of slides titled Task Completion Status Report With Project Details Information PDF. The topics addressed in these templates areCyber Security, Sarah Taylor, Networks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
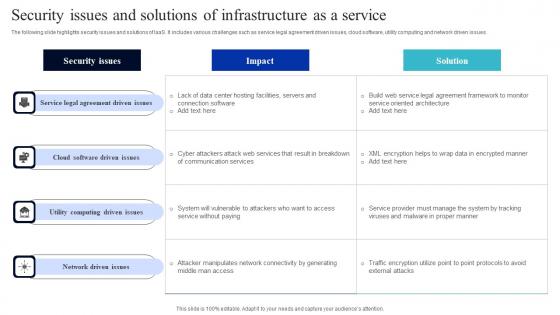
Security Issues And Solutions Of Infrastructure As A Service Summary Pdf
The following slide highlights security issues and solutions of IaaS. It includes various challenges such as service legal agreement driven issues, cloud software, utility computing and network driven issues. Showcasing this set of slides titled Security Issues And Solutions Of Infrastructure As A Service Summary Pdf. The topics addressed in these templates are Cloud Software, Utility Computing, Network Driven Issues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights security issues and solutions of IaaS. It includes various challenges such as service legal agreement driven issues, cloud software, utility computing and network driven issues.
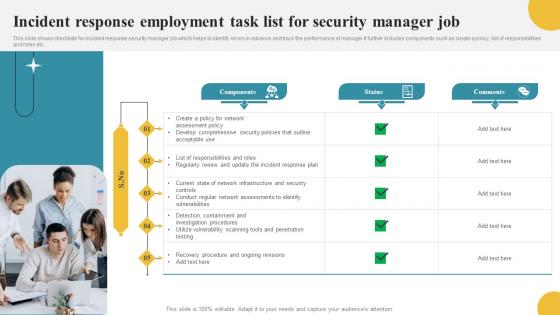
Incident Response Employment Task List For Security Manager Job Themes Pdf
This slide shows checklists for incident response security manager job which helps to identify errors in advance and track the performance of manager It further includes components such as create a policy, list of responsibilities and roles etc. Showcasing this set of slides titled Incident Response Employment Task List For Security Manager Job Themes Pdf The topics addressed in these templates are Components, Responsibilities And Roles, Response Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows checklists for incident response security manager job which helps to identify errors in advance and track the performance of manager It further includes components such as create a policy, list of responsibilities and roles etc.
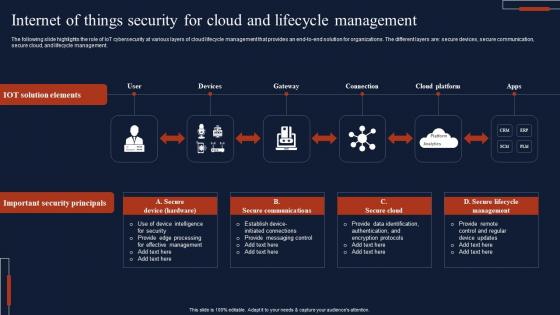
Internet Of Things Security For Cloud And Lifecycle Management Slides Pdf
The following slide highlights the role of IoT cybersecurity at various layers of cloud lifecycle management that provides an end-to-end solution for organizations. The different layers are secure devices, secure communication, secure cloud, and lifecycle management. Showcasing this set of slides titled Internet Of Things Security For Cloud And Lifecycle Management Slides Pdf The topics addressed in these templates are Important Security Principals, Secure Communications All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights the role of IoT cybersecurity at various layers of cloud lifecycle management that provides an end-to-end solution for organizations. The different layers are secure devices, secure communication, secure cloud, and lifecycle management.
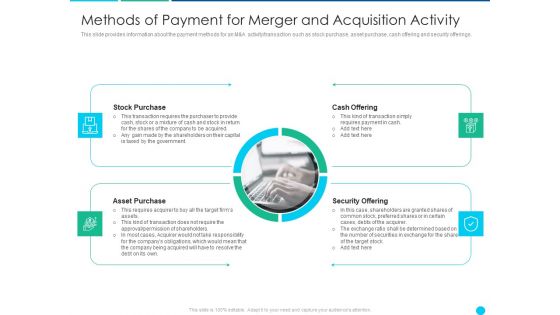
Methods Of Payment For Merger And Acquisition Activity Information PDF
Presenting methods of payment for merger and acquisition activity information pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like stock purchase, asset purchase, security offering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
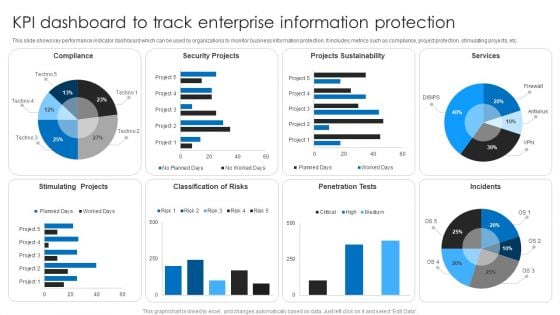
KPI Dashboard To Track Enterprise Information Protection Topics PDF
This slide shows key performance indicator dashboard which can be used by organizations to monitor business information protection. It includes metrics such as compliance, project protection, stimulating projects, etc. Showcasing this set of slides titled KPI Dashboard To Track Enterprise Information Protection Topics PDF. The topics addressed in these templates are Security Projects, Projects Sustainability, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Overview Of Key Insights On Cyber Security Trends Icon Microsoft PDF
Persuade your audience using this Overview Of Key Insights On Cyber Security Trends Icon Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Overview Of Key Insights, Cyber Security Trends Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Exploring Investment Opportunities With Security Token Table Of Contents Infographics Pdf
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Exploring Investment Opportunities With Security Token Table Of Contents Infographics Pdf from Slidegeeks and deliver a wonderful presentation. Our Exploring Investment Opportunities With Security Token Table Of Contents Infographics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
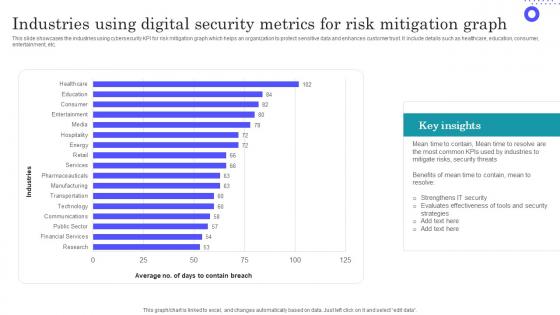
Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf
Showcasing this set of slides titled Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf The topics addressed in these templates are Evaluates Effectiveness, Most Common, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the industries using cybersecurity KPI for risk mitigation graph which helps an organization to protect sensitive data and enhances customer trust. It include details such as healthcare, education, consumer, entertainment, etc.
Security For Cloud Based Systems Icon For Data Protection Themes PDF
Showcasing this set of slides titled Security For Cloud Based Systems Icon For Data Protection Themes PDF. The topics addressed in these templates are Security For Cloud, Based Systems Icon, For Data Protection . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
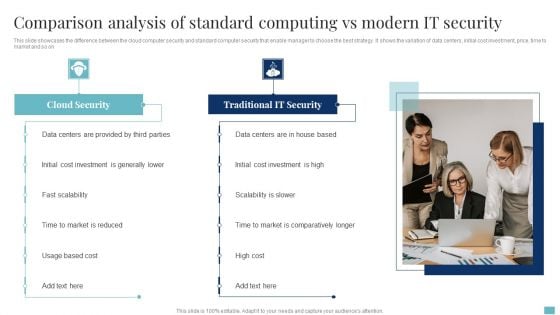
Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF
This slide showcases the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market and so on. Persuade your audience using this Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Data Centers, Cloud Security, Cost Investment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
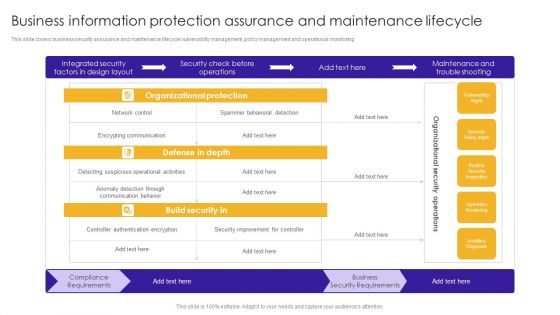
Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF
This slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring.Showcasing this set of slides titled Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF. The topics addressed in these templates are Encrypting Communication, Detecting Suspicious, Authentication Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Objectives Efficient Transportation Safety And Security Maritime Shipping Industry IR SS V
The slide covers objectives of the reports. It help companies in streamlining its operations towards achieving this goal and earn profits. It includes efficient transportation, safety and security, sustainability etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Objectives Efficient Transportation Safety And Security Maritime Shipping Industry IR SS V from Slidegeeks and deliver a wonderful presentation. The slide covers objectives of the reports. It help companies in streamlining its operations towards achieving this goal and earn profits. It includes efficient transportation, safety and security, sustainability etc.
Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf
This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc. Showcasing this set of slides titled Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf. The topics addressed in these templates are Analysis Progress, Resolution Progress, Threshold Limit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc.
Icon Showing Data Security Through Blockchain Technology In Supply Chain Rules PDF
Persuade your audience using this Icon Showing Data Security Through Blockchain Technology In Supply Chain Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Showing Data Security, Blockchain Technology Supply Chain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Best Messages App Android Security Update In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Best Messages App Android Security Update In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Best Messages App Android Security Update that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Best Messages App Android Security Update In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Top Rated Outdoor Security Lights that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
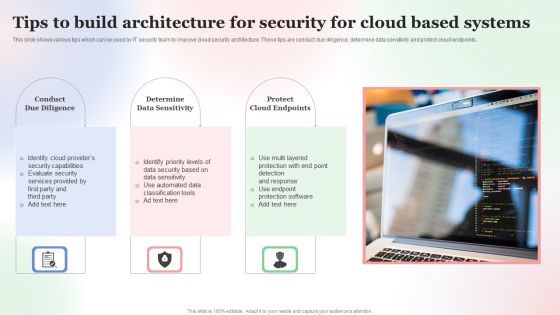
Tips To Build Architecture For Security For Cloud Based Systems Designs PDF
This slide shows various tips which can be used by IT security team to improve cloud security architecture. These tips are conduct due diligence, determine data sensitivity and protect cloud endpoints. Persuade your audience using this Tips To Build Architecture For Security For Cloud Based Systems Designs PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Tips To Build, Architecture For Security, Cloud Based Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Wireless Banking To Improve Mobile Banking Application Security Testing Tools Fin SS V
This slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. Get a simple yet stunning designed Wireless Banking To Improve Mobile Banking Application Security Testing Tools Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Wireless Banking To Improve Mobile Banking Application Security Testing Tools Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc.
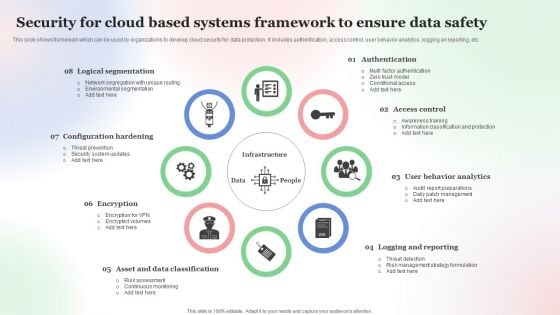
Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF
This slide shows framework which can be used by organizations to develop cloud security for data protection. It includes authentication, access control, user behavior analytics, logging an reporting, etc. Persuade your audience using this Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF. This PPT design covers Eight stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Framework, To Ensure Data Safety . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
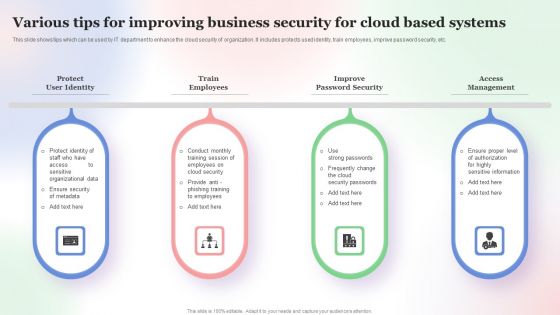
Various Tips For Improving Business Security For Cloud Based Systems Slides PDF
This slide shows tips which can be used by IT department to enhance the cloud security of organization. It includes protects used identity, train employees, improve password security, etc. Persuade your audience using this Various Tips For Improving Business Security For Cloud Based Systems Slides PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Various Tips For Improving, Business Security, Cloud Based Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
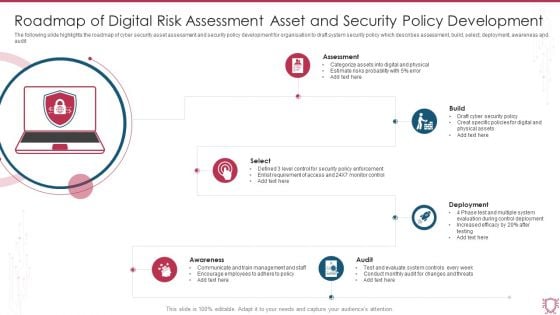
Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































