Information Security Program
Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf
Pitch your topic with ease and precision using this Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf This layout presents information on Futuristic Approach, Data Driven Decisions, Exposed Assets It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the comparative analysis of cybersecurity KPIs for small businesses which helps an organization to carefully choose, select the best metric to track performance. It include details such as goal oriented, actionable, easy to understand, etc.
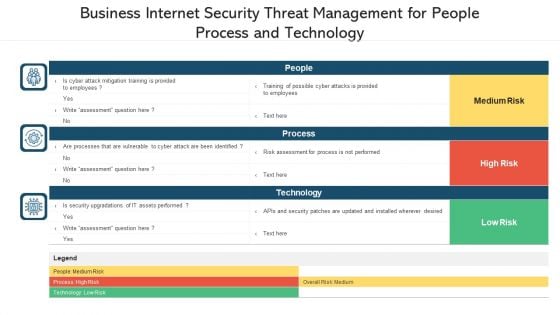
Business Internet Security Threat Management For People Process And Technology Ppt PowerPoint Presentation File Inspiration PDF
Pitch your topic with ease and precision using this business internet security threat management for people process and technology ppt powerpoint presentation file inspiration pdf. This layout presents information on people, process, technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
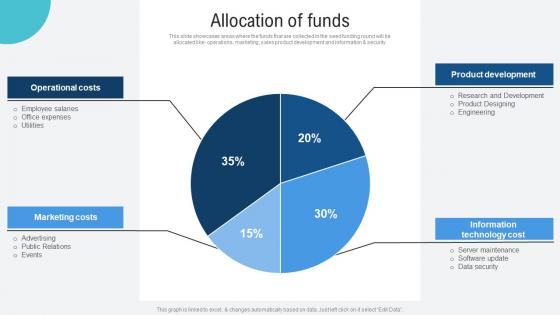
Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security. If you are looking for a format to display your unique thoughts, then the professionally designed Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security.
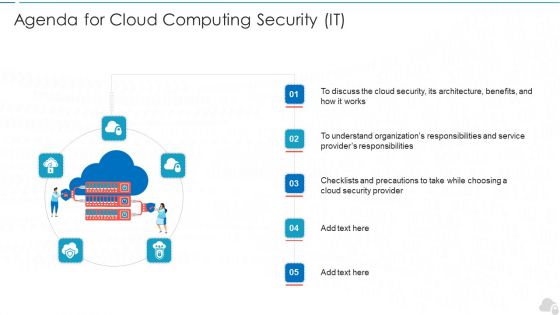
Agenda For Cloud Computing Security IT Ppt Infographic Template Inspiration PDF
Presenting agenda for cloud computing security it ppt infographic template inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cloud security, service, architecture, organizations, responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends Best, Smart Home Security, Systems Consumer Technology, Association Consumer Technology, Association Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enhanced Protection Corporate Event Administration Security And Operational Tasks Maintenance Checklist Slides PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration security and operational tasks maintenance checklist slides pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
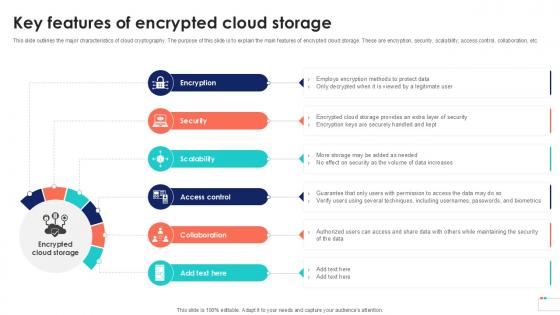
Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. This Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.
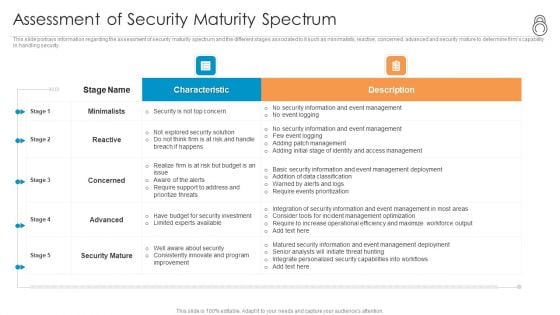
Enhanced Protection Corporate Event Administration Assessment Of Security Maturity Spectrum Background PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration assessment of security maturity spectrum background pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Table Of Contents For IT Security IT Cont Tracking Ppt Infographics Graphics Example PDF
Presenting table of contents for it security it cont tracking ppt infographics graphics example pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cyber security, implementation, communication, administrative, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Remote Access Control Mockup PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Remote Access Control. Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control mockup pdf bundle. Topics like security management plan steps in detail remote access control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Risk Assessment And Analysis Summary PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis summary pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Topics PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail remote access control topics pdf. Use them to share invaluable insights on requirement, security, implementation cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Define Access Control Measures For Employees IT Security IT Ppt Professional Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a define access control measures for employees it security it ppt professional icon pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, access data, networks, responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
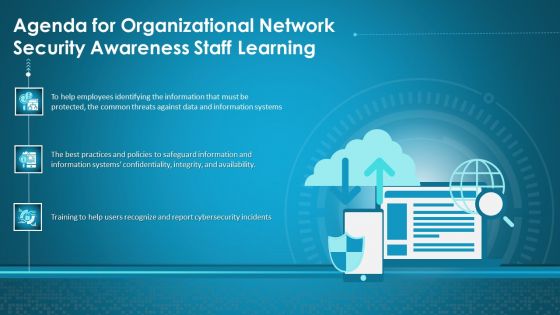
Agenda For Organizational Network Security Awareness Staff Learning Ppt Styles Master Slide PDF
Deliver an awe-inspiring pitch with this creative agenda for organizational network security awareness staff learning ppt styles master slide pdf bundle. Topics like employees identifying, cybersecurity incidents, information systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financing Catalogue For Security Underwriting Agreement Investment Bank Underwriting Overview Slides PDF
The slide provides the key points related to underwriting agreement between the company and the investment bank. Key points covered in the slide includes type of offering, underwriting fee, number of banks involved in the deal etc. This is a financing catalogue for security underwriting agreement investment bank underwriting overview slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like underwriting fee, syndicate or selling group, type of offering. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
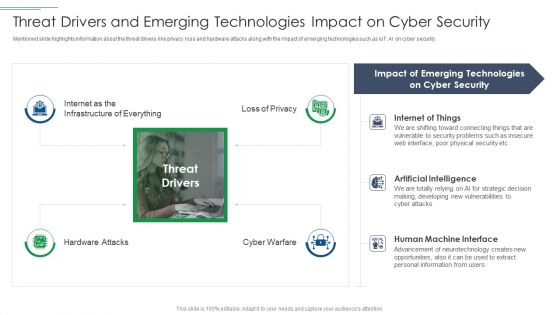
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
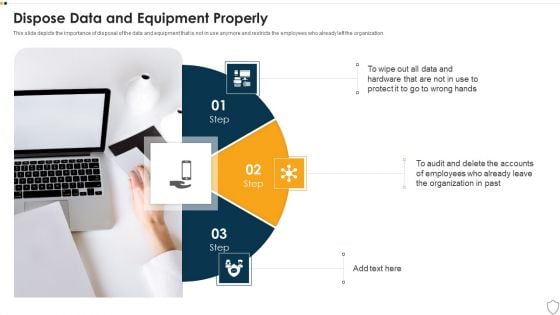
IT Security Dispose Data And Equipment Properly Ppt Portfolio Good PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. This is a it security dispose data and equipment properly ppt portfolio good pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dispose data and equipment properly. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
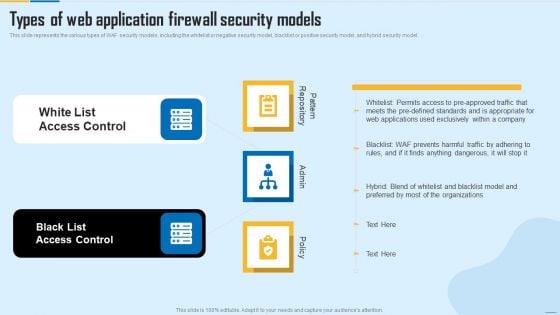
Types Of Web Application Firewall Security Models WAF Platform Themes PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting Types Of Web Application Firewall Security Models WAF Platform Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like White List Access Control, Black List Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
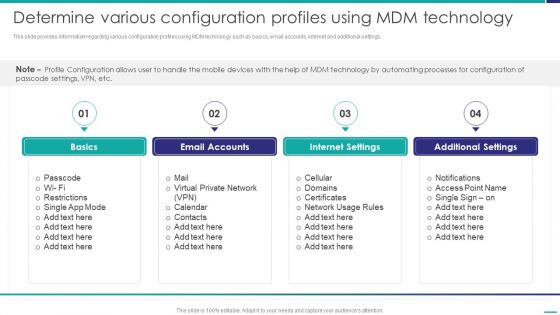
Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF
This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Presenting Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Restrictions, Internet Settings, Additional Settings. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
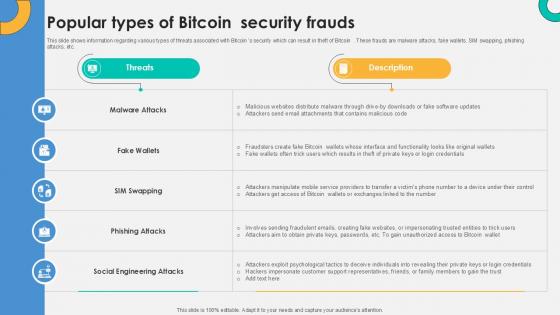
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.
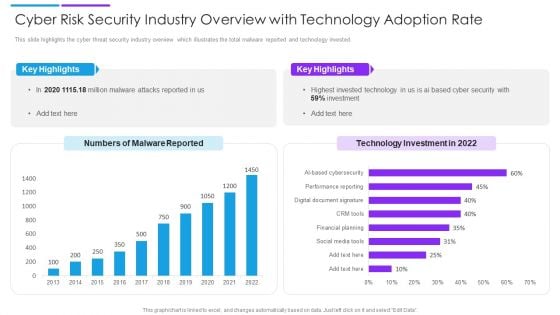
Cyber Risk Security Industry Overview With Technology Adoption Rate Slides PDF
This slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Pitch your topic with ease and precision using this cyber risk security industry overview with technology adoption rate slides pdf. This layout presents information on key highlights, technology investment, malware reported. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents For Cloud Computing Security IT Monitoring Ppt Styles Introduction PDF
Presenting table of contents for cloud computing security it monitoring ppt styles introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, business, implement, roadmap, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
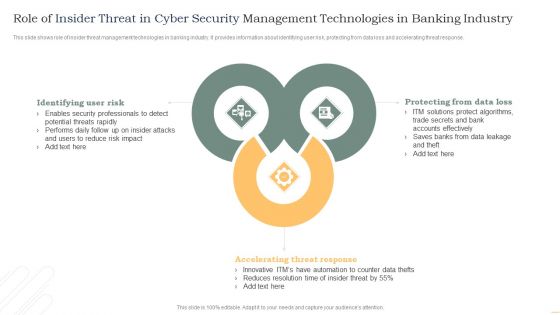
Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF
This slide shows role of insider threat management technologies in banking industry. It provides information about identifying user risk, protecting from data loss and accelerating threat response. Presenting Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Identifying User Risk, Accelerating Threat Response, Protecting Data Loss. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
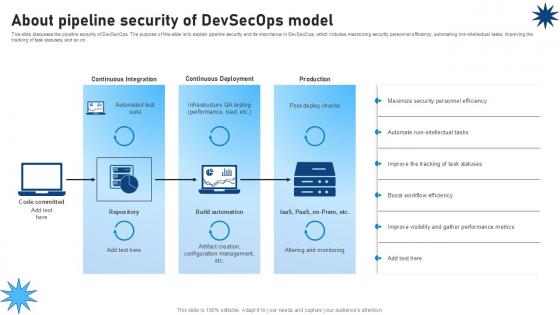
About Pipeline Security Of Devsecops Model Role Of Devsecops Ppt Powerpoint
This slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on. This About Pipeline Security Of Devsecops Model Role Of Devsecops Ppt Powerpoint from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on.
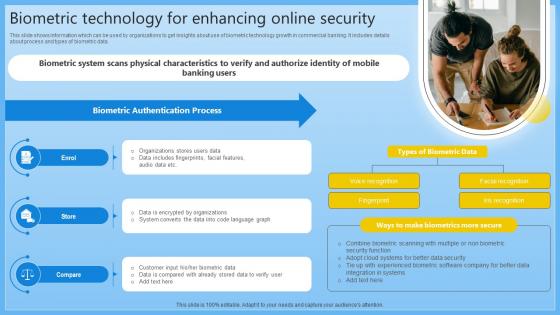
Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.
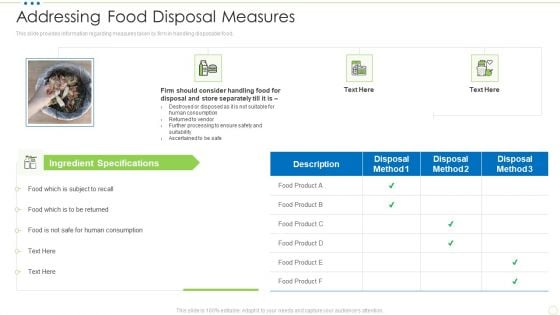
Addressing Food Disposal Measures Food Security Excellence Ppt Layouts Graphics Example PDF
This slide provides information regarding measures taken by firm in handling disposable food. Deliver an awe inspiring pitch with this creative addressing food disposal measures food security excellence ppt layouts graphics example pdf. Topics like addressing food disposal measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Impact Analysis For Effective Threat Management Slides PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative corporate security and risk management impact analysis for effective threat management slides pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
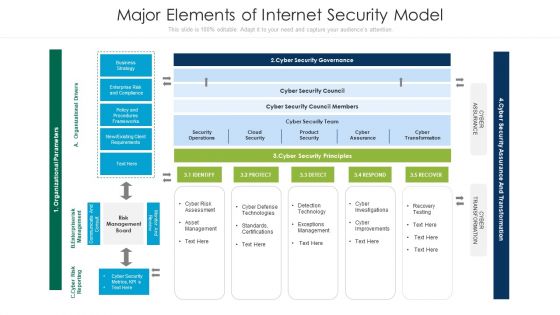
Major Elements Of Internet Security Model Ppt PowerPoint Presentation Slides Mockup PDF
Pitch your topic with ease and precision using this major elements of internet security model ppt powerpoint presentation slides mockup pdf. This layout presents information on business strategy, enterprise risk and compliance, policy and procedures frameworks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF
Pitch your topic with ease and precision using this Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF. This layout presents information on Compliance Trend, Risk Status, Risk Severity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
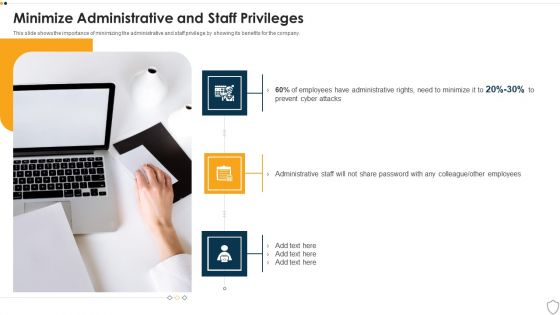
IT Security Minimize Administrative And Staff Privileges Ppt Inspiration Summary PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. This is a it security minimize administrative and staff privileges ppt inspiration summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimize administrative and staff privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact On Food Demand And Food Security Due To Covid Crisis Ppt Pictures Layout PDF
This template covers Impact On Food Demand And Food Security such as demand of food has affected due to reduction in income and purchasing capacity. It also covers the impact of school closure on childrens who are dependent on school meal programs. This is a impact on food demand and food security due to covid crisis ppt pictures layout pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management strategy, price, source, services, production. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Internet Security Threat Analysis Plan With Icons Ppt PowerPoint Presentation Ideas Influencers PDF
Pitch your topic with ease and precision using this internet security threat analysis plan with icons ppt powerpoint presentation ideas influencers pdf. This layout presents information on inspect, preliminary assessment, extended assessment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security Camera System Company Profile Market Positioning With Technology Icons PDF
Presenting Security Camera System Company Profile Market Positioning With Technology Icons PDF to provide visual cues and insights. Share and navigate important information on One stage that need your due attention. This template can be used to pitch topics like Transformative, Security Experience, Service Capabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
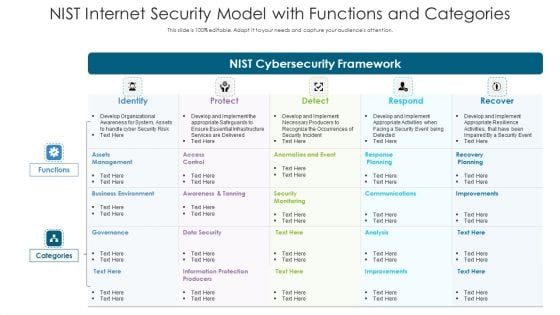
NIST Internet Security Model With Functions And Categories Ppt PowerPoint Presentation Model Show PDF
Showcasing this set of slides titled NIST internet security model with functions and categories ppt powerpoint presentation model show pdf. The topics addressed in these templates are assets management, recovery planning, information protection producers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
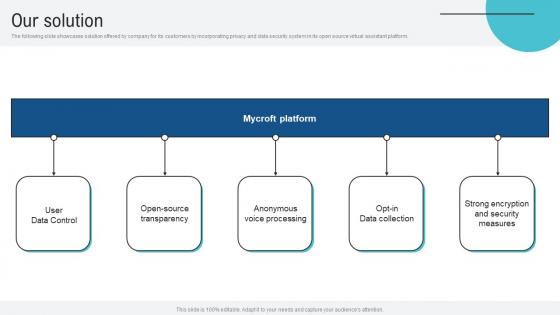
Our Solution Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf
The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform. This Our Solution Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform.

Construction Management Services And Action Plan Interdependence Resiliency And Security Portrait PDF
Presenting construction management services and action plan interdependence resiliency and security portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, dimensions of infrastructure security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
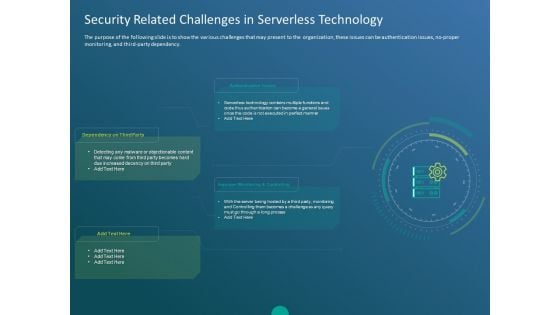
Functioning Of Serverless Computing Security Related Challenges In Serverless Technology Graphics PDF
The purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency. This is a functioning of serverless computing security related challenges in serverless technology graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication issues, dependency third party, improper monitoring and controlling. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
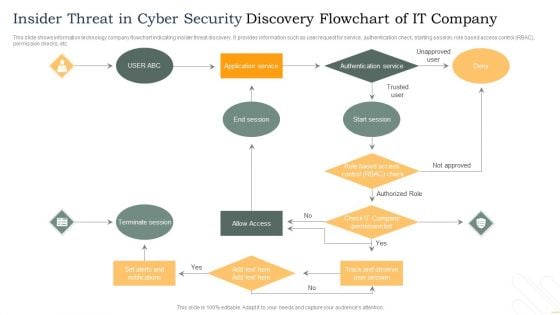
Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
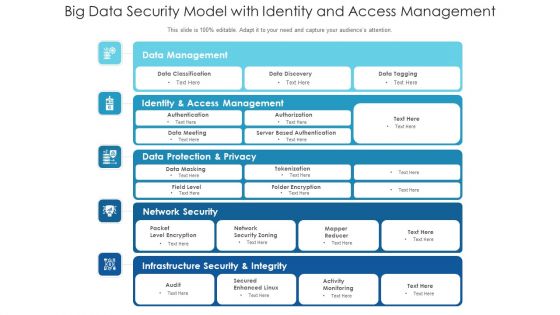
Big Data Security Model With Identity And Access Management Ppt PowerPoint Presentation Inspiration Good PDF
Pitch your topic with ease and precision using this big data security model with identity and access management ppt powerpoint presentation inspiration good pdf. This layout presents information on identity and access management, data protection and privacy, infrastructure security and integrity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Organizational Security Solutions Budget For Effective Secops System Management Rules PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this organizational security solutions budget for effective secops system management rules pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Process Integration Budget For Effective Secops System Management Brochure PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security and process integration budget for effective secops system management brochure pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
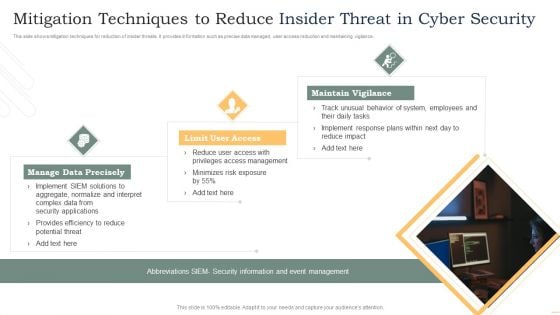
Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Process Of Disaster Recovery Planning IT Security IT Ppt Outline Example Introduction PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a process of disaster recovery planning it security it ppt outline example introduction pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data collection, plan testing, approval, perform risk analysis, prioritize procedures and operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Theft Or Loss Of Intellectual Property Cloud Computing Security IT Ppt Styles Visual Aids PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks. This is a theft or loss of intellectual property cloud computing security it ppt styles visual aids pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, cloud accounts, intellectual property. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Table Of Contents Ppt Professional Graphic Tips PDF
Presenting security functioning centre table of contents ppt professional graphic tips pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like dashboard, impact analysis, incident management, security operations centre, technologies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
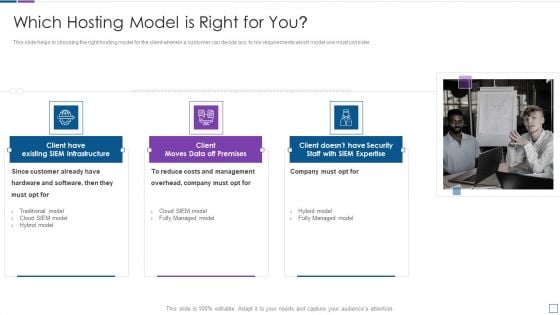
Real Time Assessment Of Security Threats Which Hosting Model Is Right For You Clipart PDF
This slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. This is a real time assessment of security threats which hosting model is right for you clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs and management, company, hardware and software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Addressing Various Threats Affecting IT Project Safety Designs PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Presenting project security administration it addressing various threats affecting it project safety designs pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like general it threats, criminal it threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
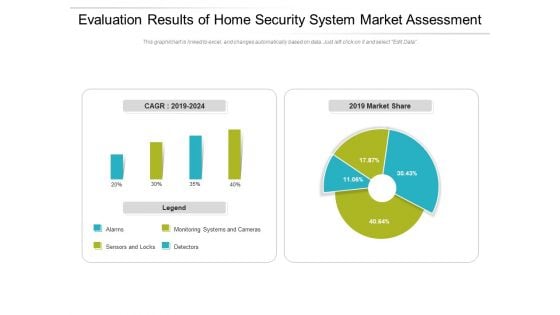
Evaluation Results Of Home Security System Market Assessment Ppt PowerPoint Presentation Gallery Deck PDF
Pitch your topic with ease and precision using this evaluation results of home security system market assessment ppt powerpoint presentation gallery deck pdf. This layout presents information on monitoring, market, detectors. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Internet Security Risk Assessment Report For Business Ppt PowerPoint Presentation Gallery Graphics Example PDF
Pitch your topic with ease and precision using this internet security risk assessment report for business ppt powerpoint presentation gallery graphics example pdf. This layout presents information on process, unit, risk level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Internet Security Risk Assessment Report With Vulnerability And Impact Ppt PowerPoint Presentation Icon Backgrounds PDF
Pitch your topic with ease and precision using this internet security risk assessment report with vulnerability and impact ppt powerpoint presentation icon backgrounds pdf. This layout presents information on vulnerability, asset, impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF
Pitch your topic with ease and precision using this Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF. This layout presents information on Phishing Cyber Securit, Attack Unprotected, Web Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparative Assessment Of Security Problem Management Tools Ppt Model Influencers PDF
Pitch your topic with ease and precision using this Comparative Assessment Of Security Problem Management Tools Ppt Model Influencers PDF. This layout presents information on Customized Workflows, Threat Intelligence Integration, Real Time Alerts. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Intelligence With Data Governance And Security Ppt PowerPoint Presentation Infographics Example PDF
Pitch your topic with ease and precision using this business intelligence with data governance and security ppt powerpoint presentation infographics example pdf. This layout presents information on data governance, data discovery, data quality management, connected clouds, security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
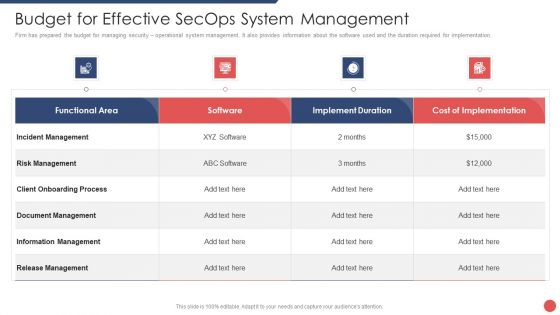
Security Functioning Centre Budget For Effective Secops System Management Formats PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security functioning centre budget for effective secops system management formats pdf. Use them to share invaluable insights on incident management, risk management, client onboarding process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V
This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing.
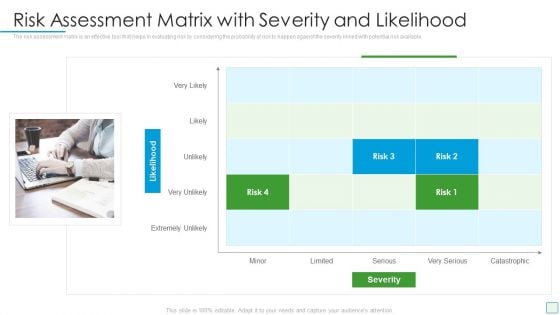
Developing Firm Security Strategy Plan Risk Assessment Matrix With Severity And Likelihood Portrait PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. This is a developing firm security strategy plan risk assessment matrix with severity and likelihood portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment matrix with severity and likelihood. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Develop Corporate Cyber Security Risk Mitigation Plan Organization Mission And Vision Statement Download PDF
Presenting develop corporate cyber security risk mitigation plan organization mission and vision statement download pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like vision, mission. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































