Information Security Program
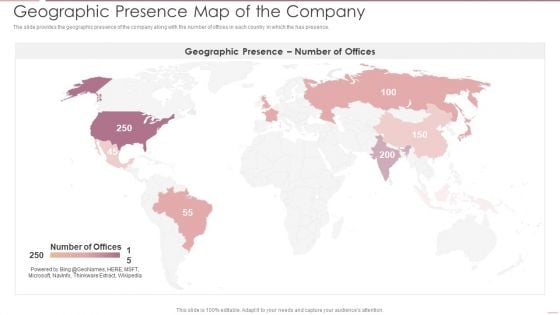
Investment Banking Security Underwriting Pitchbook Geographic Presence Map Of The Company Designs PDF
The slide provides the geographic presence of the company along with the number of offices in each country in which the has presence.This is a Investment Banking Security Underwriting Pitchbook Geographic Presence Map Of The Company Designs PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Geographic Presence, Map Company You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Investment Bank Underwriting Overview Topics PDF
The slide provides the key points related to underwriting agreement between the company and the investment bank. Key points covered in the slide includes type of offering, underwriting fee, number of banks involved in the deal etc. This is a Investment Banking Security Underwriting Pitchbook Investment Bank Underwriting Overview Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Investment Banks, Firm Commitment, Underwriting Fee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
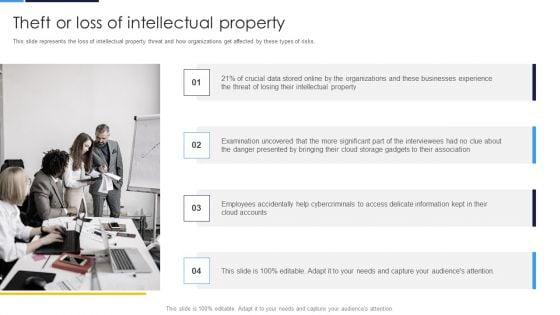
Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks.This is a Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intellectual Property, Examination Uncovered, Danger Presented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF
This template covers first step for LinkedIn marketing such as update company profile and position the company account according to the target audience. This is a Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Profiles Position, Target Audience, Account According. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Facebook And Instagram Advertising Audit The Company Profile Mockup PDF
This template covers Facebook and Instagram marketing strategy. All these sections on Facebook, Instagram pages add an important value to the business. This is a Security And Performance Digital Marketing Facebook And Instagram Advertising Audit The Company Profile Mockup PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Conducting Events, Regularly Post, Corporate Announcements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF
This template depicts that Facebook Ads needs three parts to run such as a campaign, ad set, and ad. All these parts are called campaign structure and help run ads the way the company wants and reach the right prospects.his is a Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Powerful Consisting, Features Campaigns, Define Creative. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
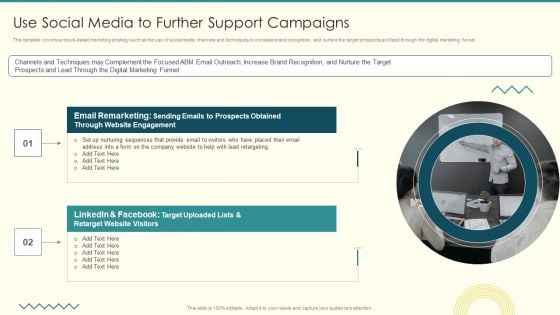
Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF
This template covers account-based marketing strategy such as the use of social media channels and techniques to increase brand recognition, and nurture the target prospects and lead through the digital marketing funnel.This is a Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Prospects Obtained, Nurturing Sequences, Channels Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Picture Of Trade Secret Security Merits Ppt PowerPoint Presentation Model Shapes PDF
Pitch your topic with ease and precision using this picture of trade secret security merits ppt powerpoint presentation model shapes pdf. This layout presents information on trade secret doe not require registration cost, they have immediate effect, they do not require compliance with official procedures such as disclosure of information to any government authority, they are not limited with time unless patents are not revealed to the public. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
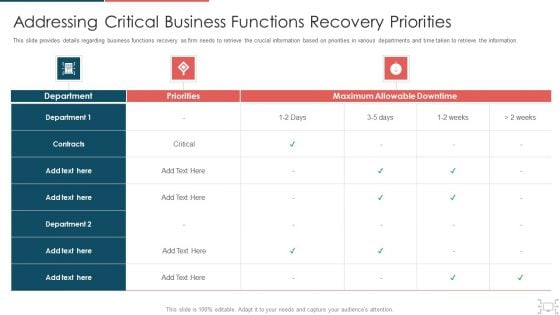
Cyber Security Administration In Organization Addressing Critical Business Functions Recovery Download PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing critical business functions recovery download pdf. Use them to share invaluable insights on addressing critical business functions recovery priorities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
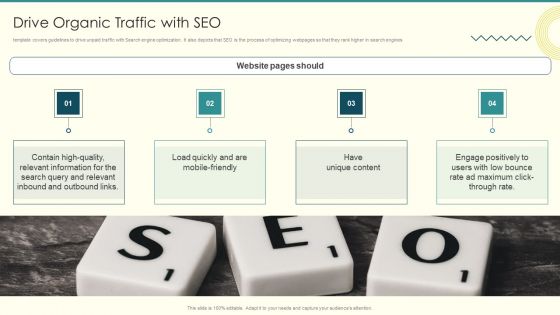
Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF
template covers guidelines to drive unpaid traffic with Search engine optimization. It also depicts that SEO is the process of optimizing webpages so that they rank higher in search engines.Presenting Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Relevant Information, Inbound Outbound, Engage Positively. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan How To Handle Financial Crisis At Workplace Themes PDF
This slide covers information regarding how firm can handle financial crisis by safeguarding financial stability in terms of abundant cash requirements, overhead analysis, currency hedging, etc. Presenting developing firm security strategy plan how to handle financial crisis at workplace themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like abundant cash requirement, key financial statements, overheads analysis, currency hedging, preparing aged debtors trial balance on monthly basis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF
This slide exhibits the different types of managed security services such as risk management, virtual CISO and security awareness education. It also provides information about the multiple offerings of each service. Persuade your audience using this Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Offerings, Security Awareness Education, Virtual CISO. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Handling Several Food Ingredients Quality Food Security Excellence Ppt Styles Template PDF
This slide provides information regarding handling of food ingredients quality for various kinds of ingredients such as liquid, dry ingredient and oil. Presenting handling several food ingredients quality food security excellence ppt styles template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like liquid ingredients, dry ingredients, oil. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Functioning Centre Current Challenges Faced By Firm While Implementing Secops Topics PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting security functioning centre current challenges faced by firm while implementing secops topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget, pool of talent and expertise, tools. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. Presenting Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Smart Home Services, Acquired Bluestone Security, System Product Catalogue, Launched Different CCTV, 2010 To 2022. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ensuring Mobile Device Compliance And Policy Enforcement Mobile Device Security Management Slides PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Presenting Ensuring Mobile Device Compliance And Policy Enforcement Mobile Device Security Management Slides PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Automated Device, Enforcement Automation, Device Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
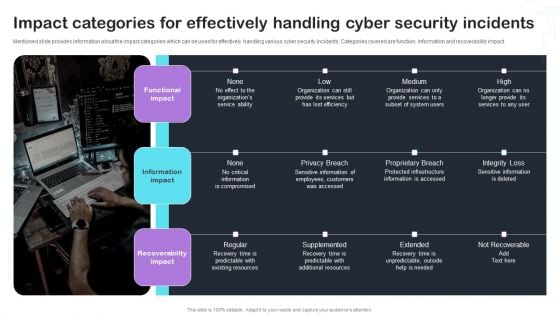
Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. This Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
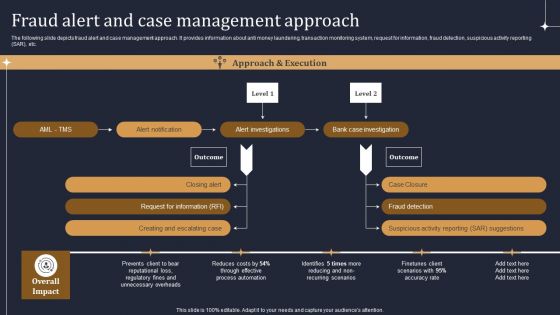
KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF
The following slide depicts fraud alert and case management approach. It provides information about anti money laundering, transaction monitoring system, request for information, fraud detection, suspicious activity reporting SAR, etc. The KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
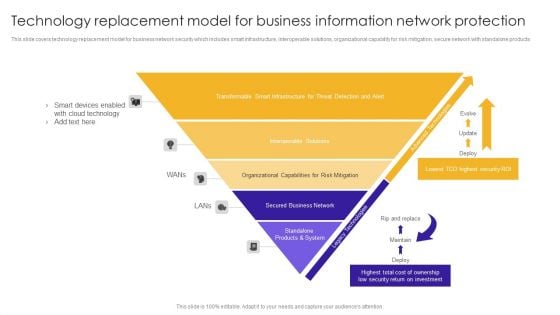
Technology Replacement Model For Business Information Network Protection Structure PDF
This slide covers technology replacement model for business network security which includes smart infrastructure, interoperable solutions, organizational capability for risk mitigation, secure network with standalone products.Showcasing this set of slides titled Technology Replacement Model For Business Information Network Protection Structure PDF. The topics addressed in these templates are Smart Devices, Cloud Technology, Transformable Smart. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Find highly impressive Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V
The slide determines the attributes on the basis of major trends in the Defense market. The purpose of this slide is to aware about the different areas where Defense is reshaping the market. It capture the information related to upcoming trends offered in the industry. This Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide determines the attributes on the basis of major trends in the Defense market. The purpose of this slide is to aware about the different areas where Defense is reshaping the market. It capture the information related to upcoming trends offered in the industry..

Ensuring Erp Data Security And Compliance Erp And Digital Transformation For Maximizing DT SS V
This slide presents various strategies to ensure data security and compliance issues. It includes robust access controls, data encryption, compliance with regulations, data backup and recovery, and employee training on security.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Ensuring Erp Data Security And Compliance Erp And Digital Transformation For Maximizing DT SS V from Slidegeeks and deliver a wonderful presentation. This slide presents various strategies to ensure data security and compliance issues. It includes robust access controls, data encryption, compliance with regulations, data backup and recovery, and employee training on security.
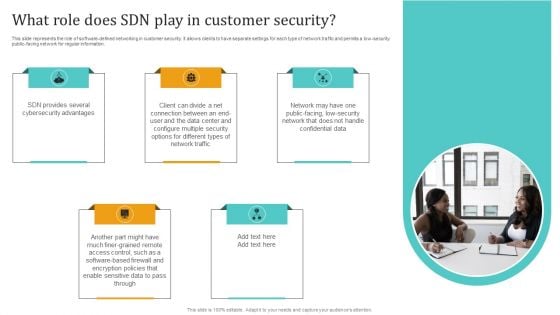
Empowering Network Agility Through SDN What Role Does SDN Play In Customer Security Professional PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. This Empowering Network Agility Through SDN What Role Does SDN Play In Customer Security Professional PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Infrastructure Strategies IT Infrastructure Optimization Ppt Icon Information PDF
Deliver an awe inspiring pitch with this creative infrastructure strategies it infrastructure optimization ppt icon information pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
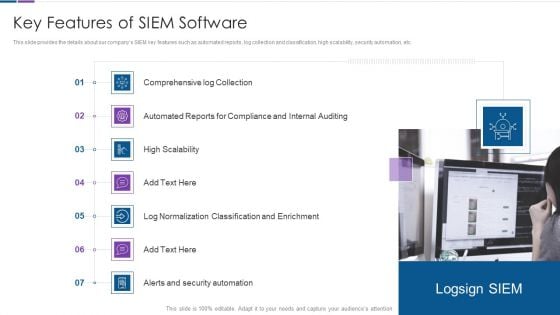
Real Time Assessment Of Security Threats Key Features Of SIEM Software Inspiration PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Presenting real time assessment of security threats key features of siem software inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like compliance and internal auditing, high scalability, classification and enrichment, security automation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
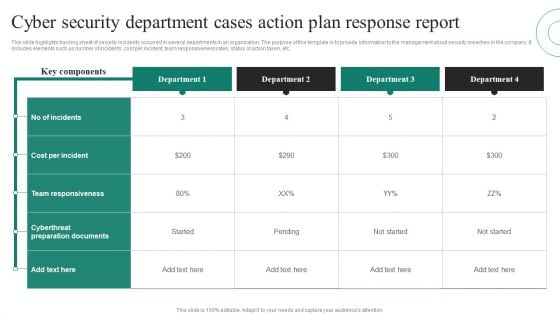
Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF
This slide highlights tracking sheet of security incidents occurred in several departments in an organization. The purpose of this template is to provide information to the management about security breaches in the company. It includes elements such as number of incidents, cost per incident, team responsiveness rates, status of action taken, etc. Pitch your topic with ease and precision using this Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF. This layout presents information on Key Components, Cost Per Incident, Team Responsiveness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
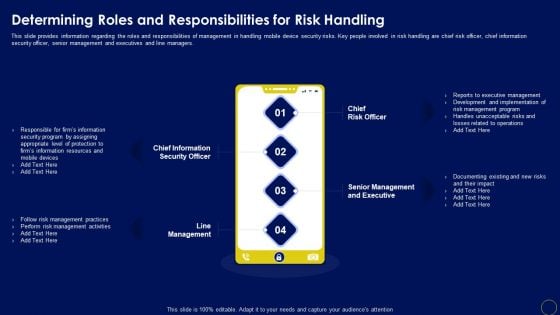
Determining Roles And Responsibilities For Risk Handling Business Mobile Device Security Management Graphics PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Boost your pitch with our creative Determining Roles And Responsibilities For Risk Handling Business Mobile Device Security Management Graphics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Complete Beginners Guide Multisignature Wallets To Enhance Wallet Security Fin SS V
This slide shows details regarding Multisignature wallets which can be used by Bitcoin holders to improve the security of accounts. It includes information about features and traction authorization. Slidegeeks has constructed Complete Beginners Guide Multisignature Wallets To Enhance Wallet Security Fin SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide shows details regarding Multisignature wallets which can be used by Bitcoin holders to improve the security of accounts. It includes information about features and traction authorization.
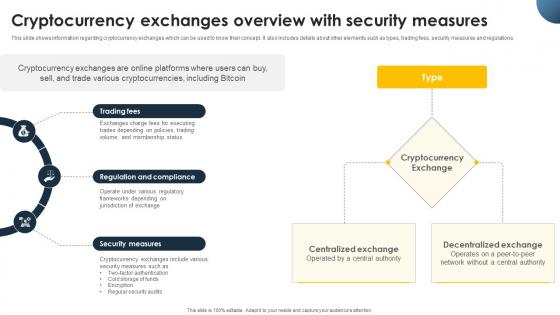
Complete Beginners Guide Cryptocurrency Exchanges Overview With Security Fin SS V
This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Complete Beginners Guide Cryptocurrency Exchanges Overview With Security Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information regarding cryptocurrency exchanges which can be used to know their concept. It also includes details about other elements such as types, trading fees, security measures and regulations.

Organization Impact Metrics Strategic Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Presenting organization impact metrics strategic hacking prevention awareness training for it security graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like organization, policy violations, data loss incidents, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
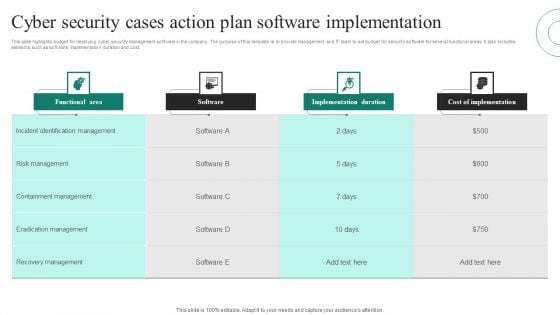
Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF
This slide highlights budget for deploying cyber security management software in the company. The purpose of this template is to provide management and IT team to set budget for security software for several functional areas. It also includes elements such as software, implementation duration and cost. Pitch your topic with ease and precision using this Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF. This layout presents information on Functional Area, Software, Implementation Duration, Cost Implementation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V
The slide depicts risk assessment for the cybersecurity industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability. It covers potential hazards associated with data beaches, phishing attacks, malware, regulatory compliance, and IoT security issues. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V from Slidegeeks and deliver a wonderful presentation. The slide depicts risk assessment for the cybersecurity industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability. It covers potential hazards associated with data beaches, phishing attacks, malware, regulatory compliance, and IoT security issues.

Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
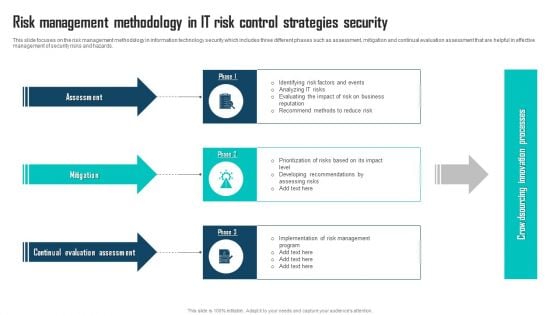
Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF
This slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Showcasing this set of slides titled Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF. The topics addressed in these templates are Assessment, Mitigation, Continual Evaluation Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
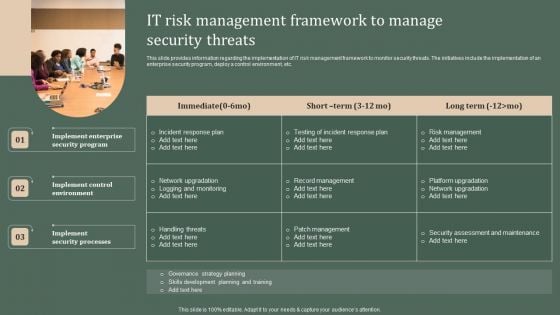
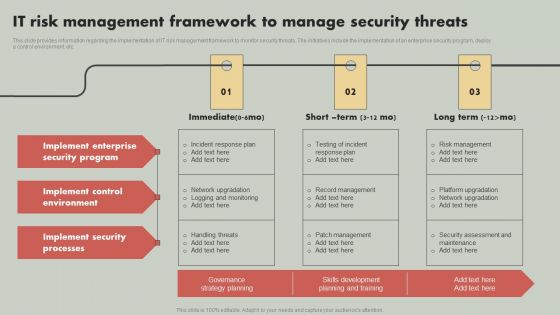
Deploying Corporate Aligned IT Strategy IT Risk Management Framework To Manage Security Threats Pictures PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Create an editable Deploying Corporate Aligned IT Strategy IT Risk Management Framework To Manage Security Threats Pictures PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Deploying Corporate Aligned IT Strategy IT Risk Management Framework To Manage Security Threats Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
IT Reducing Costs And Management Tips IT Risk Management Framework To Manage Security Threats Mockup PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Reducing Costs And Management Tips IT Risk Management Framework To Manage Security Threats Mockup PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Reducing Costs And Management Tips IT Risk Management Framework To Manage Security Threats Mockup PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
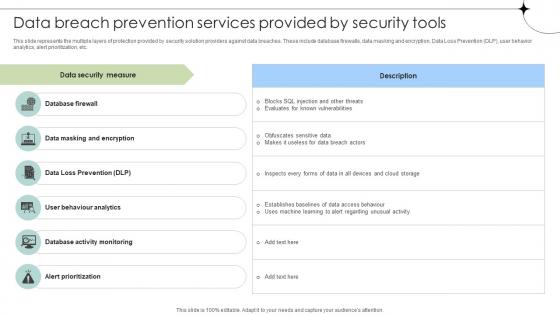
Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc.
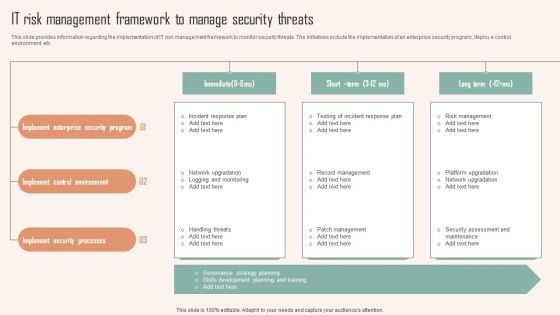
IT Risk Management Framework To Manage Security Threats Ppt PowerPoint Presentation File Outline PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Are you searching for a IT Risk Management Framework To Manage Security Threats Ppt PowerPoint Presentation File Outline PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT Risk Management Framework To Manage Security Threats Ppt PowerPoint Presentation File Outline PDF from Slidegeeks today.
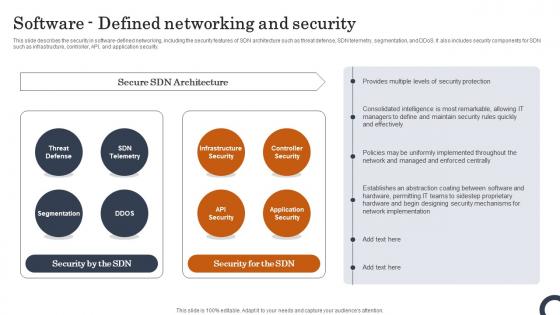
Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Do you know about Slidesgeeks Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.
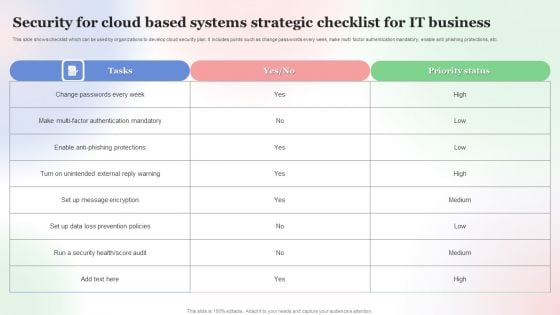
Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF
This slide shows checklist which can be used by organizations to develop cloud security plan. It includes points such as change passwords every week, make multi factor authentication mandatory, enable anti phishing protections, etc. Pitch your topic with ease and precision using this Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF. This layout presents information on Security For Cloud Based, Systems Strategic Checklist, For IT Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
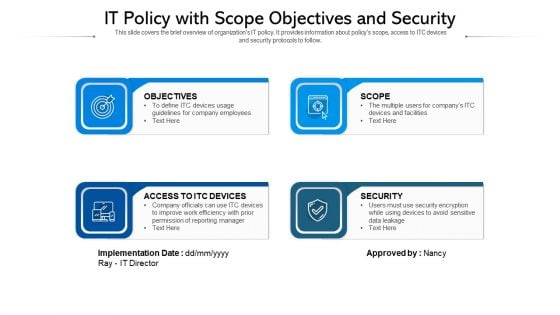
IT Policy With Scope Objectives And Security Ppt PowerPoint Presentation Infographics Show PDF
This slide covers the brief overview of organizations IT policy. It provides information about policys scope, access to ITC devices and security protocols to follow. Persuade your audience using this IT policy with scope objectives and security ppt powerpoint presentation infographics show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including objectives, access to itc devices, security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
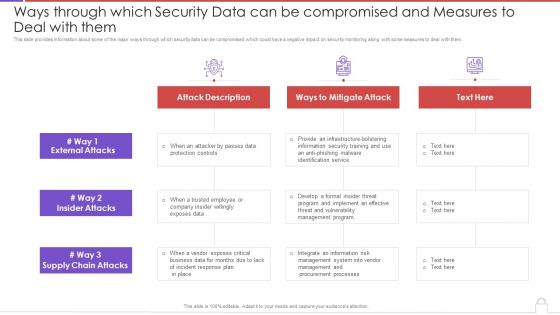
Ways Through Which Security Data Can Be Compromised And Measures To Deal With Them Professional PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative ways through which security data can be compromised and measures to deal with them professional pdf bundle. Topics like attack description, supply chain attacks, external attacks, insider attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Use Case Of Splunk Big Data For Security Intelligence Elements Pdf
Following slide showcases uses of splunk big data for security management. The purpose of this slide is to help businesses in investigating threats and improving compliance. It includes elements such as security monitoring, incident reporting, etc. Showcasing this set of slides titled Use Case Of Splunk Big Data For Security Intelligence Elements Pdf The topics addressed in these templates are Security Monitoring, Compliance, Threat Intelligence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide showcases uses of splunk big data for security management. The purpose of this slide is to help businesses in investigating threats and improving compliance. It includes elements such as security monitoring, incident reporting, etc.
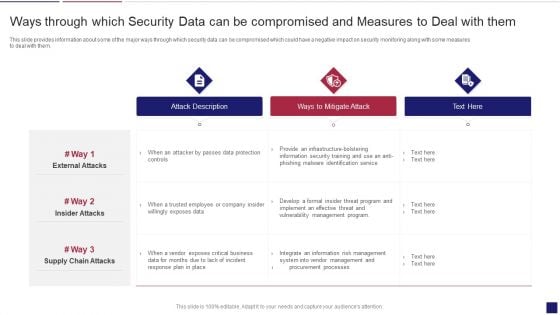
Continuous Development Evaluation Plan Eliminate Cyber Attacks Ways Through Which Security Clipart PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks ways through which security clipart pdf bundle. Topics like attack description, ways to mitigate attack, external attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Setting Scenario For Security Control Sample PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting effective it risk management process setting scenario for security control sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like technical controls, management controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Mobile Device Security Management In Organization Tips Inspiration PDF
Presenting Table Of Contents For Mobile Device Security Management In Organization Tips Inspiration PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Current Scenario, Determine Current, Determine Various. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
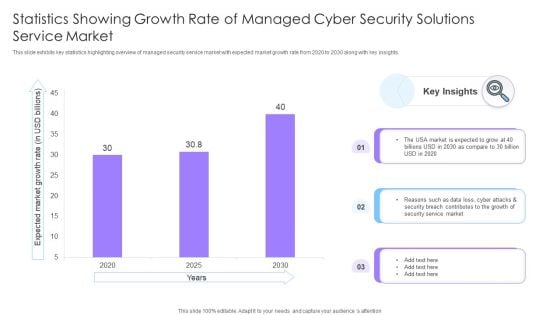
Statistics Showing Growth Rate Of Managed Cyber Security Solutions Service Market Ppt Show Inspiration PDF
This slide exhibits key statistics highlighting overview of managed security service market with expected market growth rate from 2020 to 2030 along with key insights. Pitch your topic with ease and precision using this Statistics Showing Growth Rate Of Managed Cyber Security Solutions Service Market Ppt Show Inspiration PDF. This layout presents information on Statistics Showing Growth, Cyber Security, Solutions Service Market. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
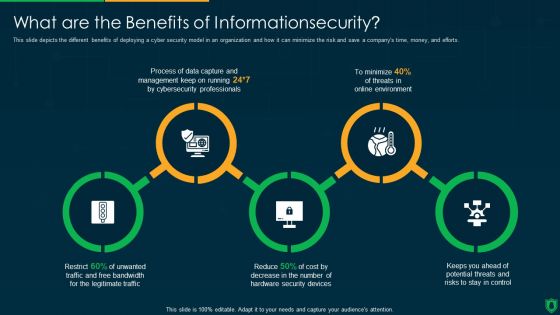
Info Security What Are The Benefits Of Informationsecurity Ppt PowerPoint Presentation Gallery Inspiration PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting info security what are the benefits of informationsecurity ppt powerpoint presentation gallery inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like data capture, threats online environment, security devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
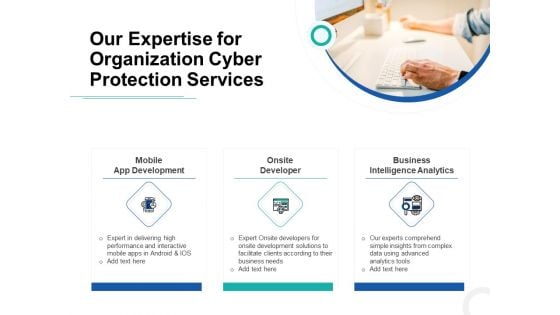
Develop Corporate Cyber Security Risk Mitigation Plan Our Expertise For Organization Cyber Protection Services Background PDF
Presenting develop corporate cyber security risk mitigation plan our expertise for organization cyber protection services background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like mobile app development, onsite developer, business intelligence analytic. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
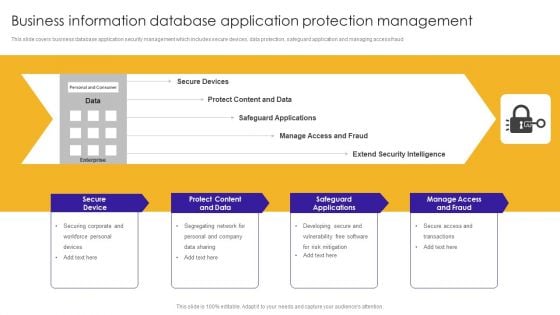
Business Information Database Application Protection Management Ideas PDF
This slide covers business database application security management which includes secure devices, data protection, safeguard application and managing access fraud.Showcasing this set of slides titled Business Information Database Application Protection Management Ideas PDF. The topics addressed in these templates are Safeguard Applications, Protect Content, Manage Access Fraud. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
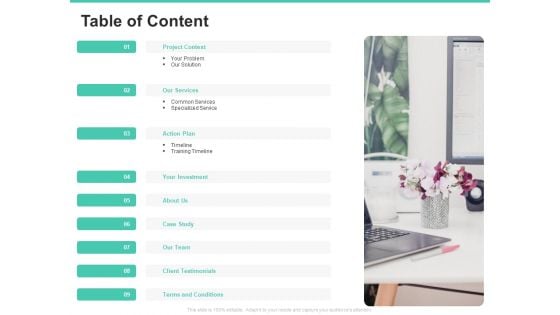
Email Security Encryption And Data Loss Prevention Table Of Content Slides PDF
Presenting email security encryption and data loss prevention table of content slides pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like project context, our services, action plan, investment, about us, case study, our team, client testimonials, terms and conditions. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample
This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample today and make your presentation stand out from the rest This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
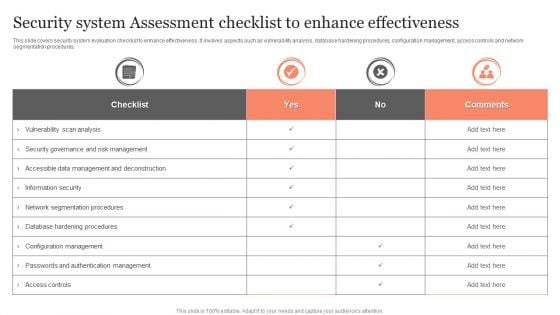
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
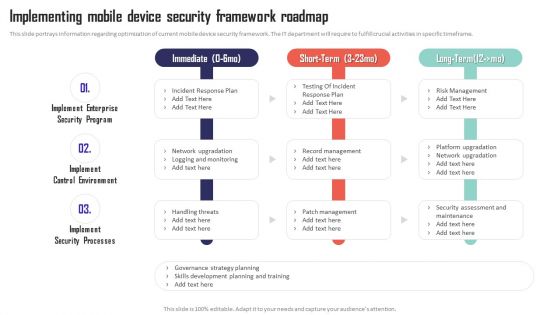
Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Get a simple yet stunning designed Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
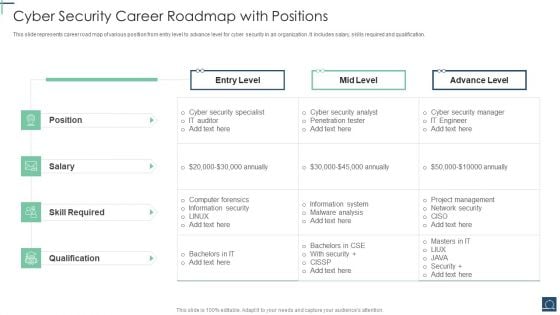
Cyber Security Career Roadmap With Positions Ppt PowerPoint Presentation File Portrait PDF
This slide represents career road map of various position from entry level to advance level for cyber security in an organization .It includes salary, skills required and qualification. Pitch your topic with ease and precision using this Cyber Security Career Roadmap With Positions Ppt PowerPoint Presentation File Portrait PDF. This layout presents information on Cyber Security Specialist, Skill Required, Advance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security Employee Awareness Training Budget For FY2022 Ppt Show Slide PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Presenting it security employee awareness training budget for fy2022 ppt show slide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like training, duration, budget, capability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































