Information Security Roadmap

Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. This Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges.
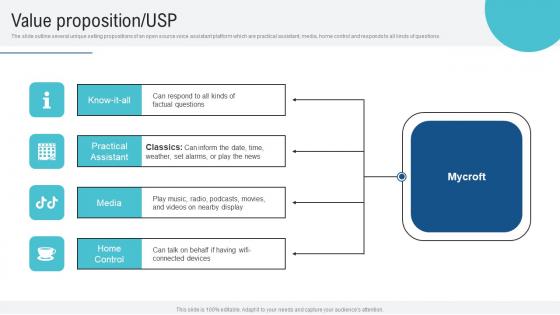
Value Proposition USP Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The slide outline several unique selling propositions of an open source voice assistant platform which are practical assistant, media, home control and responds to all kinds of questions. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Value Proposition USP Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide outline several unique selling propositions of an open source voice assistant platform which are practical assistant, media, home control and responds to all kinds of questions.
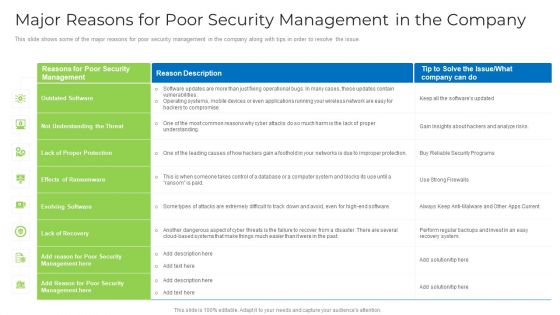
Major Reasons For Poor Security Management In The Company Download PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company download pdf bundle. Topics like applications, operating systems, network, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
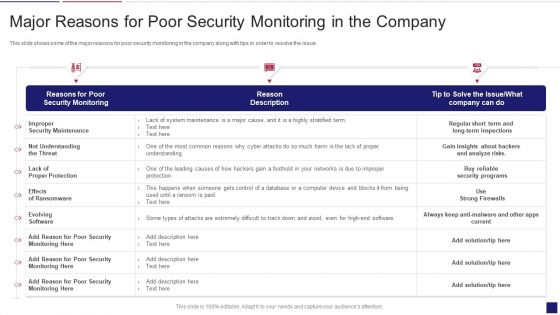
Continuous Development Evaluation Plan Eliminate Cyber Attacks Major Reasons For Poor Security Topics PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks major reasons for poor security topics pdf bundle. Topics like improper security maintenance, evolving software, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
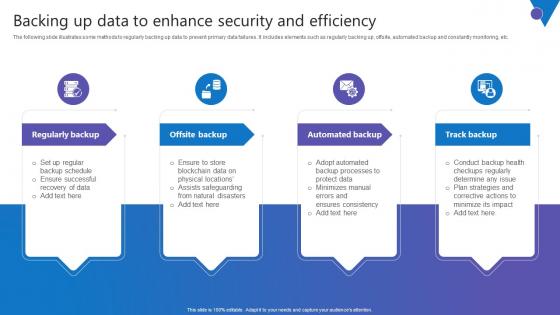
Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf
The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf. The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc.
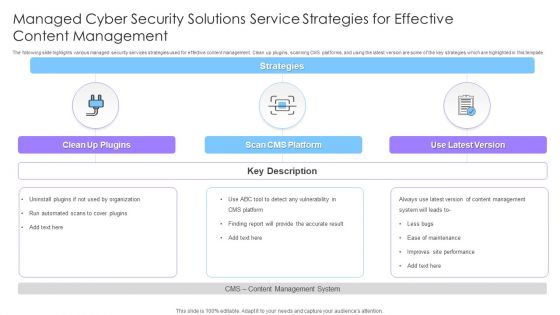
Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF
The following slide highlights various managed security services strategies used for effective content management. Clean up plugins, scanning CMS platforms, and using the latest version are some of the key strategies which are highlighted in this template. Persuade your audience using this Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Managed Cyber Security, Solutions Service Strategies, Effective Content Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Internet Security Threat Analysis Plan With Key Trends Ppt PowerPoint Presentation Summary Mockup PDF
Showcasing this set of slides titled internet security threat analysis plan with key trends ppt powerpoint presentation summary mockup pdf. The topics addressed in these templates are internet security threat analysis plan with key trends. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
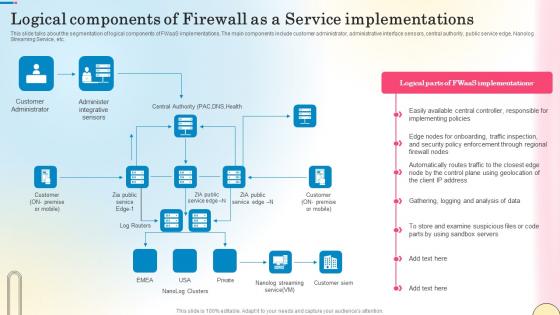
Logical Components Of Firewall As A Service Network Security Designs Pdf
This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Logical Components Of Firewall As A Service Network Security Designs Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Logical Components Of Firewall As A Service Network Security Designs Pdf. This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc.
Security And Safety Measures For Hotels Across Hospitality Sector Icons PDF
This slide outlines safety measures for various hotels across hospitality sector. It involves measures such as surveillance cameras, cybersecurity, mobile room keys and providing staff training.Presenting Security And Safety Measures For Hotels Across Hospitality Sector Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cybersecurity, Security And Ensure, Staff Training This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF
This slide signifies increasing cyber security and IT through problem management process. It includes stages like detection, define, investigate, identify resolutions, implement and follow up. Presenting Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Problem Detection, Define, Investigate, Identify Resolutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the action plan timeline for security guard service proposal as it displays steps of the process such as training and evaluating etc. Presenting you an exemplary Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
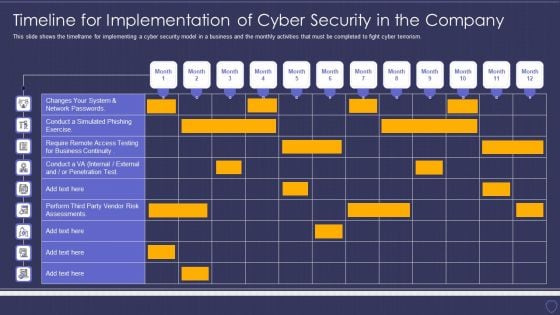
Global Cyber Terrorism Incidents On The Rise IT Timeline For Implementation Of Cyber Security Download PDF
This slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it timeline for implementation of cyber security download pdf. Use them to share invaluable insights on business, network, perform and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Action Plan Timeline Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the action plan timeline for security guard service proposal as it displays steps of the process such as training and evaluating etc. Presenting you an exemplary Action Plan Timeline Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.

Picture Editing Company Outline Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in- app permissions. Welcome to our selection of the Picture Editing Company Outline Canva Security Processes And Systems Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
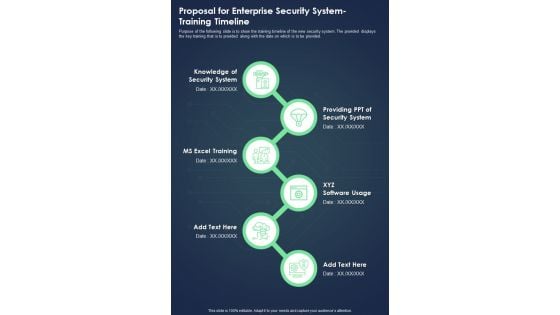
Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document brilliant piece now.
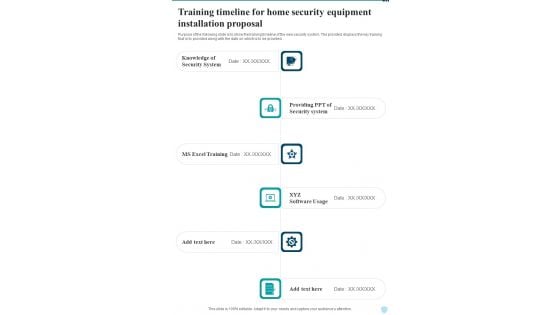
Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V
The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V from Slidegeeks and deliver a wonderful presentation. The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry.

Unlocking Potential IoTs Application Overview Of IoT Based Smart Home Security IoT SS V
This slide briefly introduces IoT devices in smart home security with features. It also showcases the components of IoT security systems, such as hardware, software, and communication protocols. Slidegeeks is here to make your presentations a breeze with Unlocking Potential IoTs Application Overview Of IoT Based Smart Home Security IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide briefly introduces IoT devices in smart home security with features. It also showcases the components of IoT security systems, such as hardware, software, and communication protocols.

CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Presenting this PowerPoint presentation, titled CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
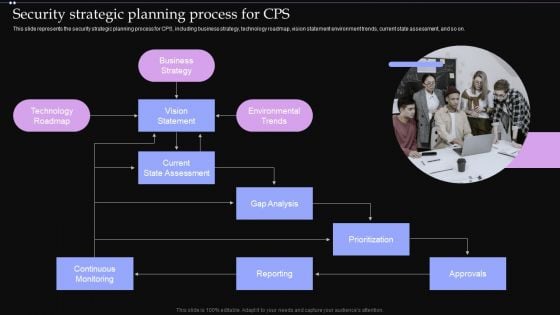
Security Strategic Planning Process For CPS Ppt PowerPoint Presentation File Pictures PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Strategic Planning Process For CPS Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Security Strategic Planning Process For CPS Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Money House Captital Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Money House Captital Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Money PowerPoint Templates because It will get your audience in sync. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Download our Sales PowerPoint Templates because Your audience will believe you are the cats whiskers. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence.Use these PowerPoint slides for presentations relating to money house, money, business, sales, signs, success. The prominent colors used in the PowerPoint template are Green, Yellow, Black. PowerPoint presentation experts tell us our Money House Captital Security PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides will make the presenter successul in his career/life. You can be sure our Money House Captital Security PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. PowerPoint presentation experts tell us our signs PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Presenters tell us our Money House Captital Security PowerPoint Templates PPT Backgrounds For Slides 0113 will impress their bosses and teams. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides will make you look like a winner. Inform your audience with our Money House Captital Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Make sure your presentation gets the attention it deserves.
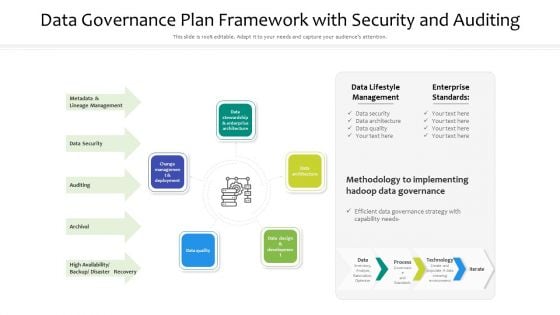
Data Governance Plan Framework With Security And Auditing Ppt PowerPoint Presentation File Template PDF
Presenting data governance plan framework with security and auditing ppt powerpoint presentation file template pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including data architecture, data quality, change management and deployment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Timeline Proposal For Security Guard Services One Pager Sample Example Document
Presenting you an exemplary Timeline Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.

Action Plan Timeline For Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Action Plan Timeline For Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline For Security Services Proposal One Pager Sample Example Document brilliant piece now.
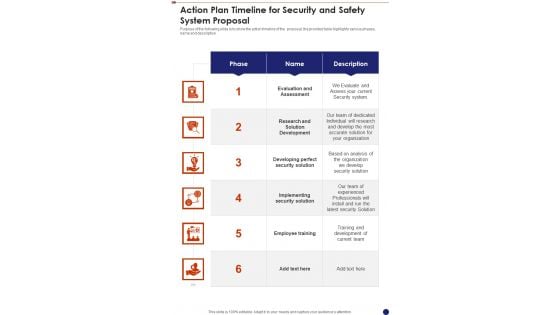
Action Plan Timeline For Security And Safety System Proposal One Pager Sample Example Document
Presenting you an exemplary Action Plan Timeline For Security And Safety System Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline For Security And Safety System Proposal One Pager Sample Example Document brilliant piece now.
Timeline Security And Safety System Proposal One Pager Sample Example Document
Presenting you an exemplary Timeline Security And Safety System Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline Security And Safety System Proposal One Pager Sample Example Document brilliant piece now.

Training Timeline For Security And Safety System Proposal One Pager Sample Example Document
Presenting you an exemplary Training Timeline For Security And Safety System Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Training Timeline For Security And Safety System Proposal One Pager Sample Example Document brilliant piece now.
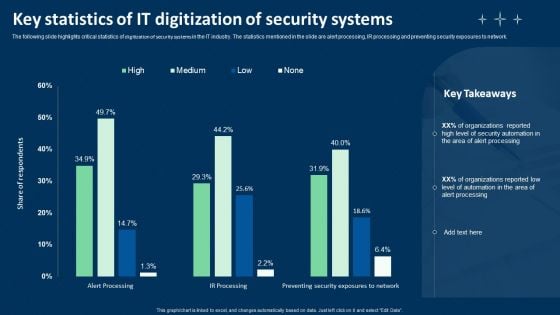
Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure, Code Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Proposal For Enterprise Security System Timeline One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Timeline One Pager Sample Example Document brilliant piece now.
Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document
Presenting you an exemplary Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. There are so many reasons you need a Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
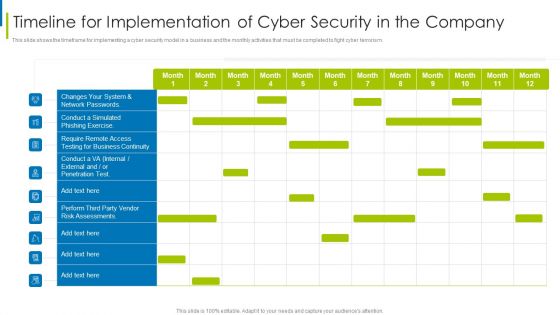
Cyber Terrorism Assault Timeline For Implementation Of Cyber Security In The Company Sample PDF
This slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism.Deliver an awe inspiring pitch with this creative cyber terrorism assault timeline for implementation of cyber security in the company sample pdf bundle. Topics like require remote access, testing for business continuity, risk assessments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Icons Slide Inspiration PDF
Introducing our well designed Executing security management program to mitigate threats and safeguard confidential organizational data icons slide inspiration pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
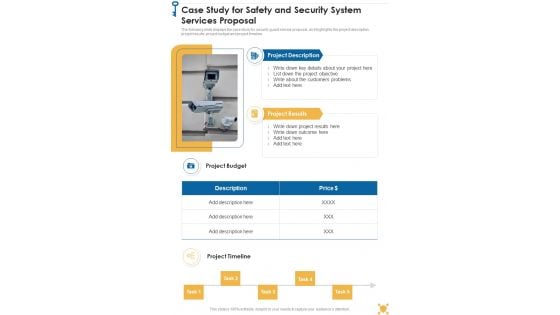
Case Study For Safety And Security System Services Proposal One Pager Sample Example Document
The following slide displays the case study for security guard service proposal, as it highlights the project description, project results, project budget and project timeline. Presenting you an exemplary Case Study For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
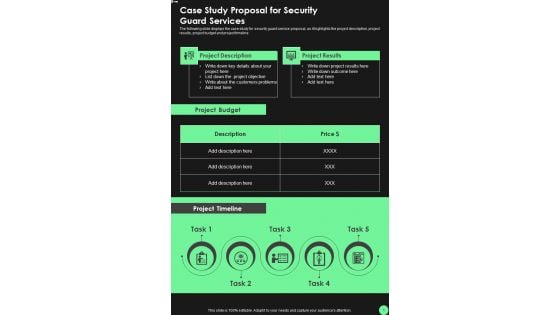
Case Study Proposal For Security Guard Services One Pager Sample Example Document
The following slide displays the case study for security guard service proposal, as it highlights the project description, project results, project budget and project timeline. Presenting you an exemplary Case Study Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.

Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Proposal For Enterprise Security System Case Study One Pager Sample Example Document
The following slide displays the case study for security system proposal, as it highlights the project description, project results, project budget and project timeline. Presenting you an exemplary Proposal For Enterprise Security System Case Study One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Case Study One Pager Sample Example Document brilliant piece now.
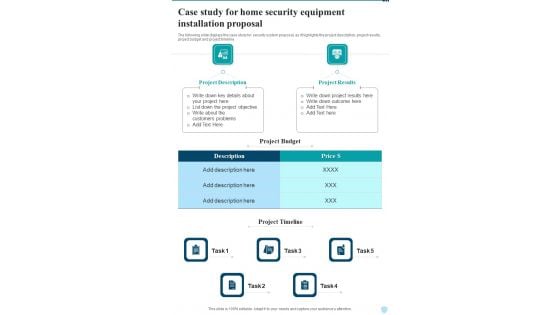
Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the case study for security system proposal, as it highlights the project description, project results, project budget and project timeline Presenting you an exemplary Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF
The following slide exhibits four practices for selecting managed security service provider. Expertise, cost, business requirements and testimonials are some of the practices which will help the organization in selecting trusted security providers. Persuade your audience using this Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Expertise, Cost, Business Requirements, Testimonials. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings. Get a simple yet stunning designed Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings.

Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure Code, Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
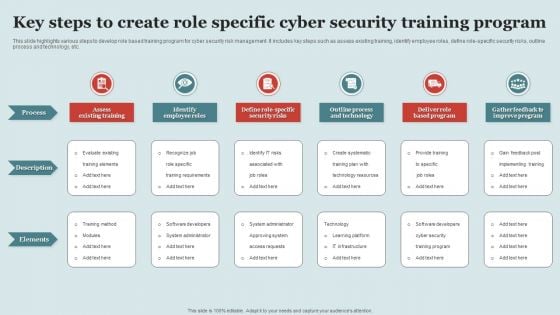
Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
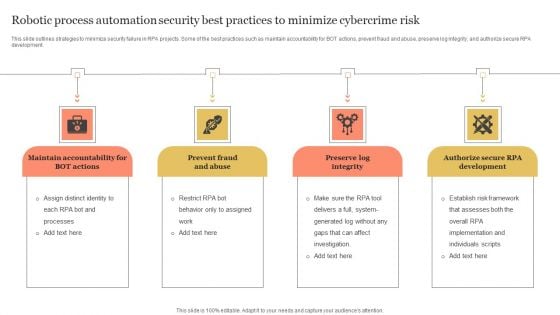
Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF
This slide outlines strategies to minimize security failure in RPA projects. Some of the best practices such as maintain accountability for BOT actions, prevent fraud and abuse, preserve log integrity, and authorize secure RPA development. Presenting Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Maintain Accountability, Prevent Fraud And Abuse, Preserve Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
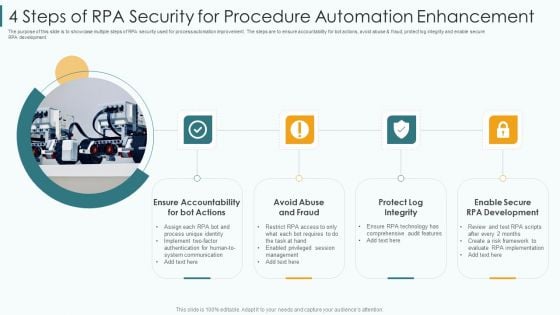
4 Steps Of RPA Security For Procedure Automation Enhancement Slides PDF
The purpose of this slide is to showcase multiple steps of RPA security used for process automation improvement. The steps are to ensure accountability for bot actions, avoid abuse and fraud, protect log integrity and enable secure RPA development. Presenting 4 steps of rpa security for procedure automation enhancement slides pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication, implement, requires. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
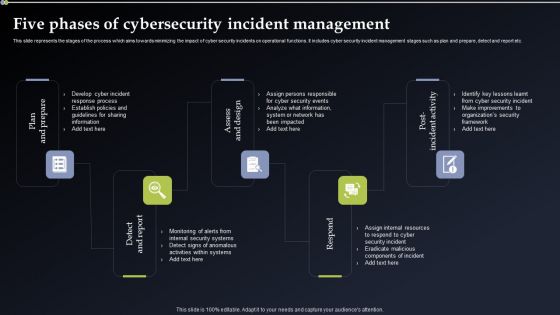
Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
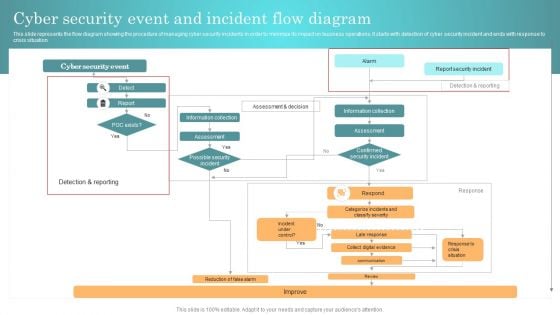
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
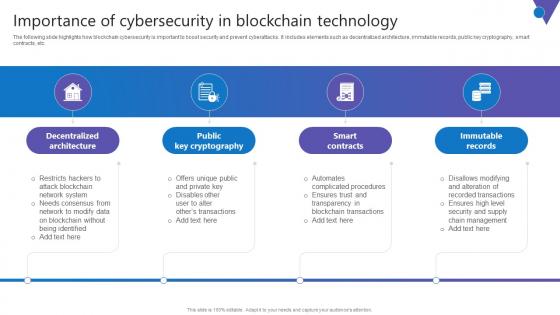
Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Find highly impressive Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc.
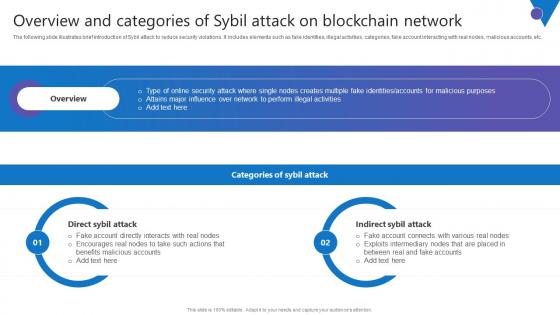
Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf
The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Are you searching for a Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf from Slidegeeks today. The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc.

Integrating Data Privacy System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides
Use this Integrating Data Privacy System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in sixty four slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
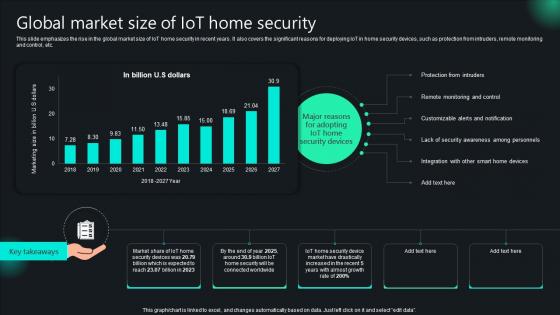
Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V
This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc. The Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Technology Trends Ppt PowerPoint Presentation Model Graphics Download Cpb
Presenting this set of slides with name cyber security technology trends ppt powerpoint presentation model graphics download cpb. This is an editable Powerpoint four stages graphic that deals with topics like cyber security technology trends to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
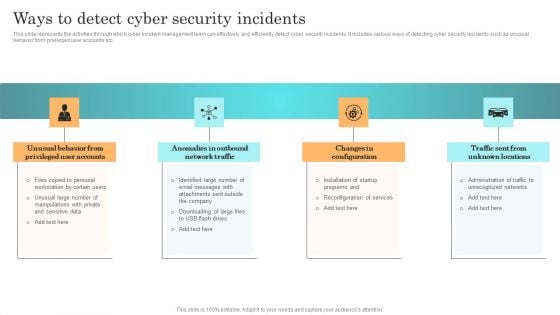
Incident Response Techniques Deployement Ways To Detect Cyber Security Incidents Infographics PDF
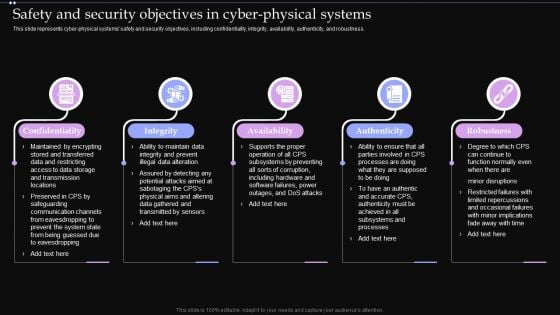
Safety And Security Objectives In Cyber Physical Systems Ppt PowerPoint Presentation File Example PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. The Safety And Security Objectives In Cyber Physical Systems Ppt PowerPoint Presentation File Example PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF
This slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. The Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
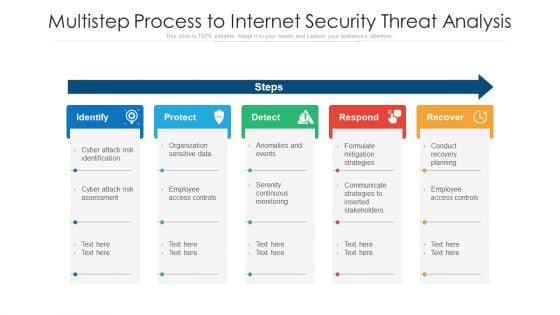
Multistep Process To Internet Security Threat Analysis Ppt PowerPoint Presentation Layouts Maker PDF
Presenting multistep process to internet security threat analysis ppt powerpoint presentation layouts maker pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identify, protect, detect, respond, recover. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
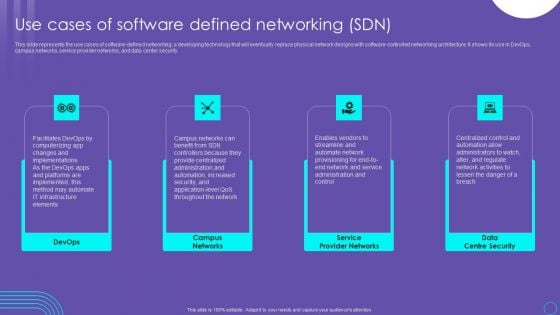
SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF
This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today


 Continue with Email
Continue with Email

 Home
Home


































