Information Security
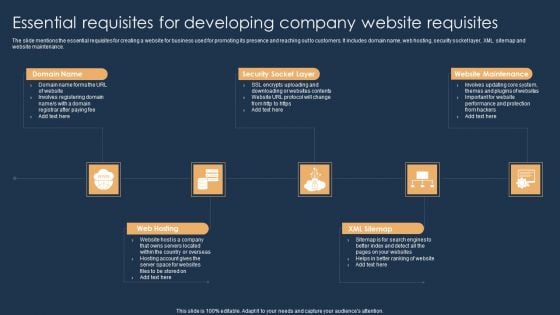
Essential Requisites For Developing Company Website Requisites Sample PDF
The slide mentions the essential requisites for creating a website for business used for promoting its presence and reaching out to customers. It includes domain name, web hosting, security socket layer, XML sitemap and website maintenance. Persuade your audience using this Essential Requisites For Developing Company Website Requisites Sample PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Web Hosting, Security Socket Layer, Website Maintenance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Address Challenges Associated With Legacy Systems DT SS V
This slide addresses the challenges associated with legacy systems and how it impact digital transformation of SMEs. It includes outdated technology, security vulnerabilities and lack of flexibility.Find a pre-designed and impeccable Address Challenges Associated With Legacy Systems DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide addresses the challenges associated with legacy systems and how it impact digital transformation of SMEs. It includes outdated technology, security vulnerabilities and lack of flexibility.
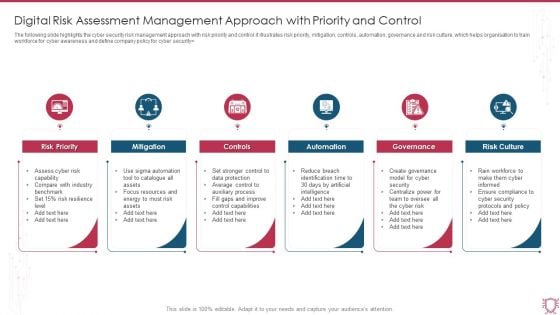
Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF
The following slide highlights the cyber security risk management approach with risk priority and control it illustrates risk priority, mitigation, controls, automation, governance and risk culture, which helps organisation to train workforce for cyber awareness and define company policy for cyber security. Persuade your audience using this Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Priority, Mitigation, Controls, Automation, Governance, Risk Culture. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps To Create Virtual Communication And Engagement Policy Themes PDF
This slide mentions the steps to create digital communication policy for organizations. It includes establishing governance, dictating security protocol, defining channels and setting standards for responsiveness. Persuade your audience using this Steps To Create Virtual Communication And Engagement Policy Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Dictate Security Protocol, Establish Governance, Define Channels. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
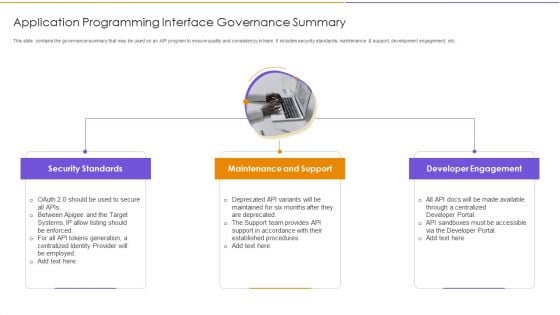
Application Programming Interface Governance Summary Pictures PDF
This slide contains the governance summary that may be used on an API program to ensure quality and consistency in team. It includes security standards, maintenance and support, development engagement, etc. Persuade your audience using this Application Programming Interface Governance Summary Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Maintenance And Support, Developer Engagement, Security Standards. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
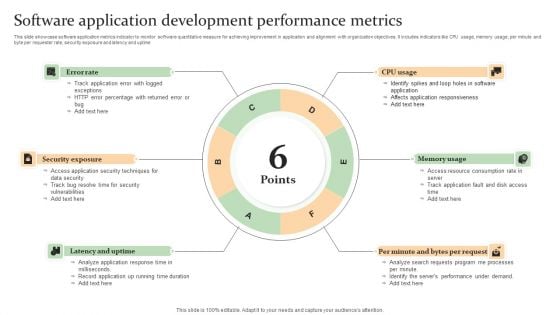
Software Application Development Performance Metrics Mockup PDF
This slide showcase software application metrics indicator to monitor software quantitative measure for achieving improvement in application and alignment with organization objectives. It includes indicators like CPU usage, memory usage, per minute and byte per requester rate, security exposure and latency and uptime Persuade your audience using this Software Application Development Performance Metrics Mockup PDF. This PPT design covers Six stages, thus making it a great tool to use. It also caters to a variety of topics including Latency And Uptime, Memory Usage, Security Exposure . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
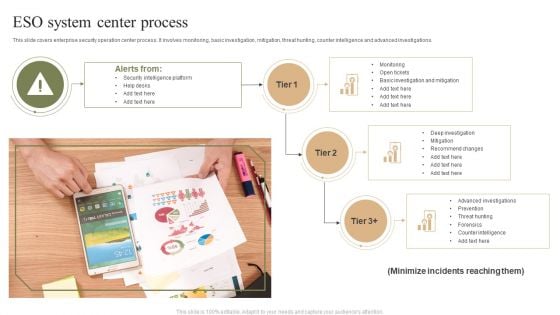
ESO System Center Process Ppt PowerPoint Presentation Gallery Brochure PDF
This slide covers enterprise security operation center process. It involves monitoring, basic investigation, mitigation, threat hunting, counter intelligence and advanced investigations. Persuade your audience using this ESO System Center Process Ppt PowerPoint Presentation Gallery Brochure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Intelligence Platform, Help Desks, Deep Investigation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
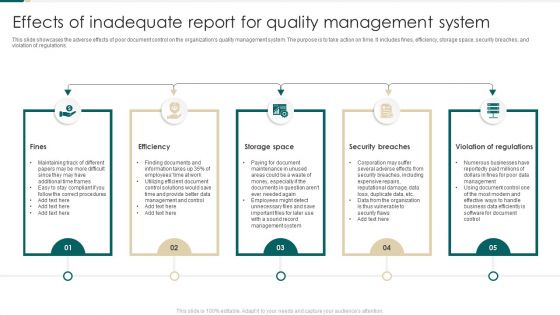
Effects Of Inadequate Report For Quality Management System Clipart PDF
This slide showcases the adverse effects of poor document control on the organizations quality management system. The purpose is to take action on time. It includes fines, efficiency, storage space, security breaches, and violation of regulations. Persuade your audience using this Effects Of Inadequate Report For Quality Management System Clipart PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Storage Space, Security Breaches, Violation Of Regulations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Why System Integration Deployment Is Required For Business Slides PDF
This slide covers need to implement system integration in business. It involves reasons such as streamlining and automation, productivity and efficiency, cost effectiveness and security aspects. Persuade your audience using this Why System Integration Deployment Is Required For Business Slides PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Streamlining And Automation, Cost Effectiveness Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Working Areas Of Telecom Cost Management Portrait PDF
This slide shows areas to deploy telecom expense management initiative that ensure financial and operational efficiency in business. It includes various disciplines such as design, optimization, inventory, financial , security management etc. Persuade your audience using this Working Areas Of Telecom Cost Management Portrait PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Management, Contract Management, Financial Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
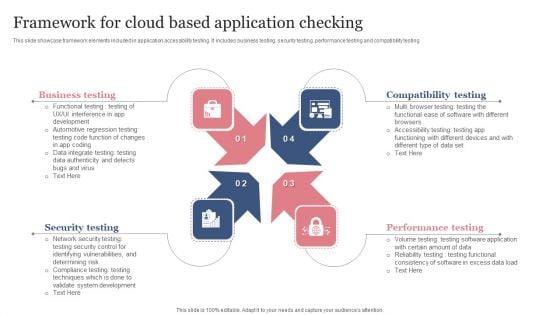
Framework For Cloud Based Application Checking Structure PDF
This slide showcase framework elements included in application accessibility testing. It includes business testing, security testing, performance testing and compatibility testing. Persuade your audience using this Framework For Cloud Based Application Checking Structure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Compatibility Testing, Performance Testing, Security Testing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
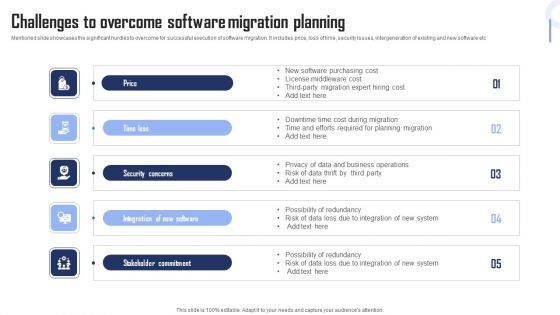
Challenges To Overcome Software Migration Planning Professional PDF
Mentioned slide showcases the significant hurdles to overcome for successful execution of software migration. It includes price, loss of time, security issues, intergeneration of existing and new software etc Persuade your audience using this Challenges To Overcome Software Migration Planning Professional PDF This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Concerns, Stakeholder Commitment, Planning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
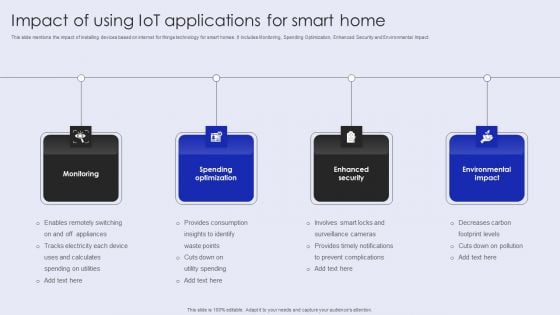
Impact Of Using Iot Applications For Smart Home Template PDF
This slide mentions the impact of installing devices based on internet for things technology for smart homes. It includes Monitoring, Spending Optimization, Enhanced Security and Environmental Impact. Persuade your audience using this Impact Of Using Iot Applications For Smart Home Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Spending Optimization, Enhanced Security, Environmental Impact. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Difficulties And Resolutions In Web Application Development Mockup PDF
This slide presents solutions to challenges faced during web application development helpful in streamlining process, increasing accuracy and making customer experience better. It includes user interface and user experience, scalability, performance and security that are highly important aspects to focus upon. Present the topic in a bit more detail with this Difficulties And Resolutions In Web Application Development Mockup PDF. Use it as a tool for discussion and navigation on Scalability, Performance, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.

Scorecard To Check Cybersecurity And Digital Risk Preparedness Ppt Layouts Brochure PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this scorecard to check cybersecurity and digital risk preparedness ppt layouts brochure pdf. Use them to share invaluable insights on organization, management, measures, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
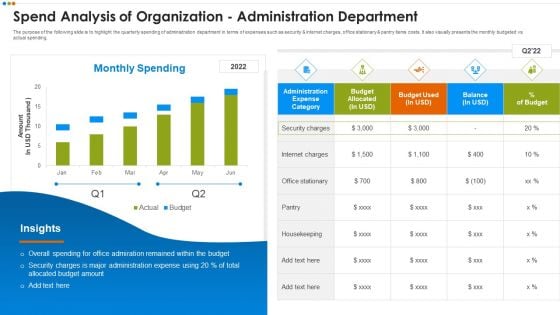
Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending.Deliver an awe inspiring pitch with this creative Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF bundle. Topics like Overall Spending, Admiration Remained, Security Administration Expense can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
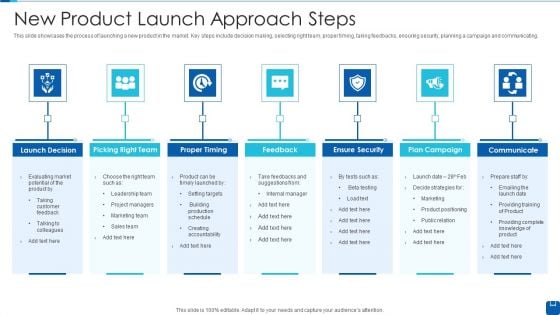
New Product Launch Approach Steps Infographics PDF
This slide showcases the process of launching a new product in the market. Key steps include decision making, selecting right team, proper timing, taking feedbacks, ensuring security, planning a campaign and communicating.Persuade your audience using this New Product Launch Approach Steps Infographics PDF This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Launch Decision, Picking Right Team, Ensure Security Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Negative Technology Effect On Manufacturing Business Ppt File Samples PDF
This slide showcases the negative impacts of manufacturing technology advancements in the business. The impacts includes environmental degradation, security vulnerability, high investment and many more. Persuade your audience using this Negative Technology Effect On Manufacturing Business Ppt File Samples PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Environmental Degradation, Security Vulnerabilities, Escalating Investment Requirements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
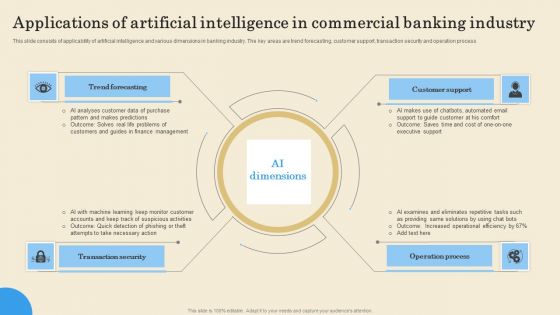
Applications Of Artificial Intelligence In Commercial Banking Industry Elements PDF
This slide consists of applicability of artificial intelligence and various dimensions in banking industry. The key areas are trend forecasting, customer support, transaction security and operation process. Persuade your audience using this Applications Of Artificial Intelligence In Commercial Banking Industry Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Trend Forecasting, Transaction Security, Operation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Assessment Tools And Techniques Ppt PowerPoint Presentation Gallery Picture PDF
The slide highlights various tools of cloud audit to guide and improve the vendors performance. Various tools and techniques included are cloud controls matrix, STAR questionnaire and CSA best practices. Persuade your audience using this Cloud Assessment Tools And Techniques Ppt PowerPoint Presentation Gallery Picture PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Controls Matrix, Security, Trust, Assurance, Risk Security Questionnaire. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key AI Trends Associated With Financial Sector Applications And Impact Themes Pdf
This slide represents key artificial intelligence tools related to financial sector. It includes huperautomation, AI-powered advisory, financial security and personalized offering. Find a pre-designed and impeccable Key AI Trends Associated With Financial Sector Applications And Impact Themes Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents key artificial intelligence tools related to financial sector. It includes huperautomation, AI-powered advisory, financial security and personalized offering.
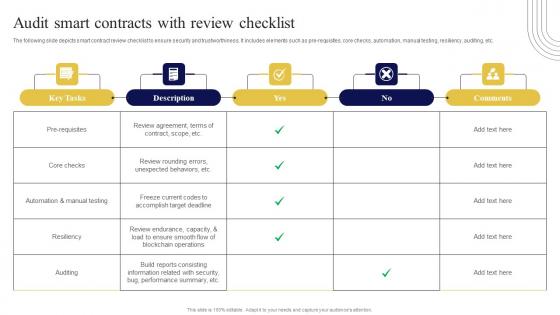
Audit Smart Contracts With Review Exploring Investment Opportunities Infographics Pdf
The following slide depicts smart contract review checklist to ensure security and trustworthiness. It includes elements such as pre-requisites, core checks, automation, manual testing, resiliency, auditing, etc. There are so many reasons you need a Audit Smart Contracts With Review Exploring Investment Opportunities Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide depicts smart contract review checklist to ensure security and trustworthiness. It includes elements such as pre-requisites, core checks, automation, manual testing, resiliency, auditing, etc.
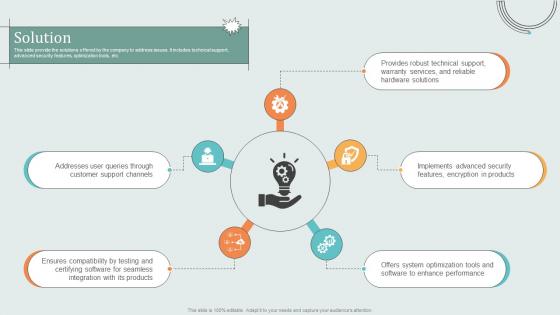
Solution Hardware Technology Provider Business Model BMC SS V
This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Hardware Technology Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc.
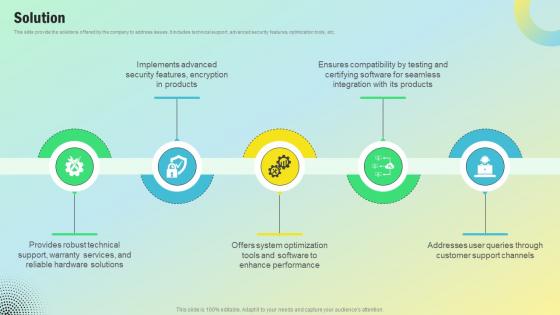
Solution Personal Computing Company Revenue Model BMC SS V
This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Personal Computing Company Revenue Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc.
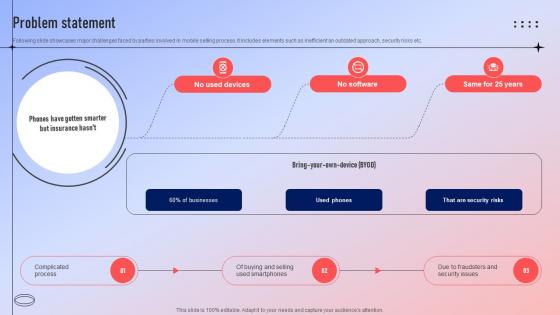
Problem Statement Fundraising Pitch Deck For Ecommerce Platform
Following slide showcases major challenges faced by parties involved in mobile selling process. It includes elements such as inefficient an outdated approach, security risks etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Problem Statement Fundraising Pitch Deck For Ecommerce Platform. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. Following slide showcases major challenges faced by parties involved in mobile selling process. It includes elements such as inefficient an outdated approach, security risks etc.
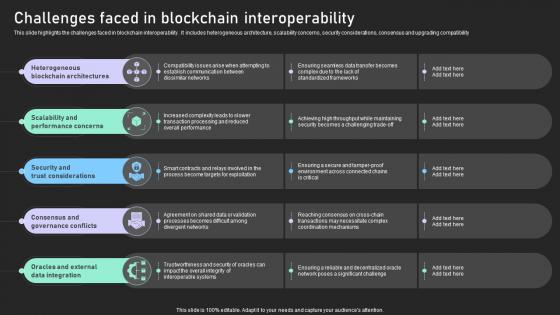
Understanding Various Blockchain Challenges Faced In Blockchain Interoperability BCT SS V
This slide highlights the challenges faced in blockchain interoperability . It includes heterogeneous architecture, scalability concerns, security considerations, consensus and upgrading compatibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Understanding Various Blockchain Challenges Faced In Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights the challenges faced in blockchain interoperability . It includes heterogeneous architecture, scalability concerns, security considerations, consensus and upgrading compatibility.

Post COVID Recovery Strategy Oil Gas Industry Strategizing The New Normal For Energy Industry Demonstration PDF
This slide provides the details of the new normal for energy industry which focuses on oil and gas sector such as volatility, risks, supply security, vulnerability, automation and digitalization, Behavioural change, etc. Deliver an awe inspiring pitch with this creative post covid recovery strategy oil gas industry strategizing the new normal for energy industry demonstration pdf bundle. Topics like preparing for volatility and risks, focus on security of supply, new sense of vulnerability, introduce automation and digitalization, considering implications of behavioural change can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Challenge And Solutions 1 Malware And Ransomware Attacks Ppt Model Objects PDF
This slide shows the problem that the company is facing related to malware and ransomware attacks on company softwares. Also, some solutions are provided to solve the problem. Deliver and pitch your topic in the best possible manner with this challenge and solutions 1 malware and ransomware attacks ppt model objects pdf. Use them to share invaluable insights on access management, security software and ensure, comprehensive security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Computerized Game Pitch Deck Rendering Unified Solutions To Handle Concerns Faced By Prospect Download PDF
This slide caters details about unified solutions to address concerns faced by clients in terms of game engine, security enhancement, revolutionary gameplay, absolute control. Deliver and pitch your topic in the best possible manner with this computerized game pitch deck rendering unified solutions to handle concerns faced by prospect download pdf. Use them to share invaluable insights on game engine, absolute control, security enhancement, revolutionary gameplay and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF. Use them to share invaluable insights on Goal, Security System, Reduce and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
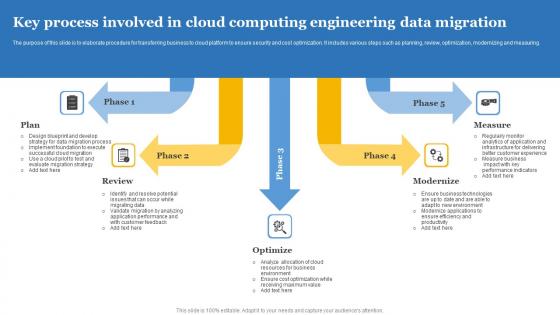
Key Process Involved In Cloud Computing Engineering Data Migration Mockup Pdf
The purpose of this slide is to elaborate procedure for transferring business to cloud platform to ensure security and cost optimization. It includes various steps such as planning, review, optimization, modernizing and measuring. Pitch your topic with ease and precision using this Key Process Involved In Cloud Computing Engineering Data Migration Mockup Pdf This layout presents information on Plan, Review, Optimize, Modernize, Measure It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to elaborate procedure for transferring business to cloud platform to ensure security and cost optimization. It includes various steps such as planning, review, optimization, modernizing and measuring.
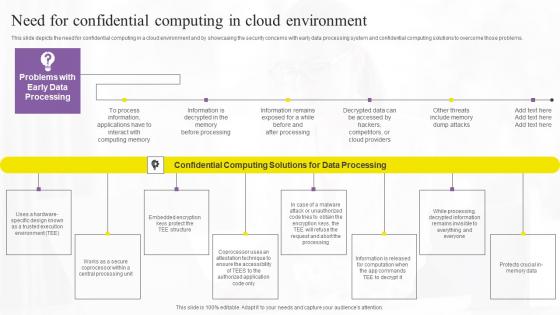
Need For Confidential Computing In Confidential Computing Technologies Structure Pdf
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. This Need For Confidential Computing In Confidential Computing Technologies Structure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems.

Key Drivers For Encouraging Adoption Of Complete Roadmap To Blockchain BCT SS V
This slide covers critical factors that encourages widespread adoption of blockchain technology across various industries. It includes drivers such as efficiency and cost savings, security and data integrity, disintermediation and decentralization, etc. This Key Drivers For Encouraging Adoption Of Complete Roadmap To Blockchain BCT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide covers critical factors that encourages widespread adoption of blockchain technology across various industries. It includes drivers such as efficiency and cost savings, security and data integrity, disintermediation and decentralization, etc.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Ppt Pictures File Formats PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness ppt pictures file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technologies, financial control procedures, operating system maintenance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
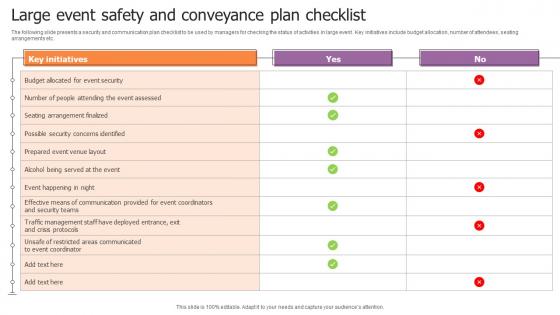
Large Event Safety And Conveyance Plan Checklist Portrait Pdf
The following slide presents a security and communication plan checklist to be used by managers for checking the status of activities in large event. Key initiatives include budget allocation, number of attendees, seating arrangements etc. Pitch your topic with ease and precision using this Large Event Safety And Conveyance Plan Checklist Portrait Pdf. This layout presents information on Key Initiatives, Safety And Conveyance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide presents a security and communication plan checklist to be used by managers for checking the status of activities in large event. Key initiatives include budget allocation, number of attendees, seating arrangements etc.
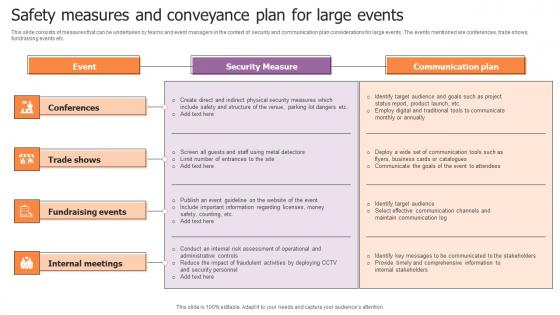
Safety Measures And Conveyance Plan For Large Events Designs Pdf
This slide consists of measures that can be undertaken by teams and event managers in the context of security and communication plan considerations for large events. The events mentioned are conferences, trade shows, fundraising events etc. Pitch your topic with ease and precision using this Safety Measures And Conveyance Plan For Large Events Designs Pdf. This layout presents information on Conferences, Trade Shows, Fundraising Events. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide consists of measures that can be undertaken by teams and event managers in the context of security and communication plan considerations for large events. The events mentioned are conferences, trade shows, fundraising events etc.
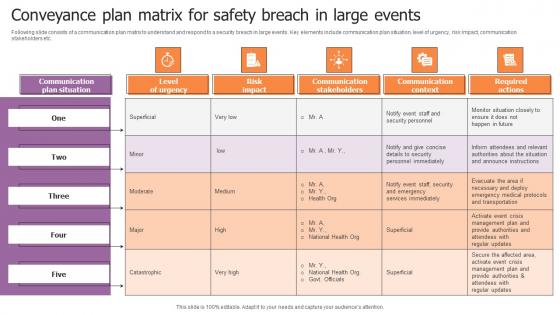
Conveyance Plan Matrix For Safety Breach In Large Events Diagrams Pdf
Following slide consists of a communication plan matrix to understand and respond to a security breach in large events. Key elements include communication plan situation, level of urgency, risk impact, communication stakeholders etc. Pitch your topic with ease and precision using this Conveyance Plan Matrix For Safety Breach In Large Events Diagrams Pdf. This layout presents information on Level Of Urgency, Risk Impact, Communication Stakeholders. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide consists of a communication plan matrix to understand and respond to a security breach in large events. Key elements include communication plan situation, level of urgency, risk impact, communication stakeholders etc.
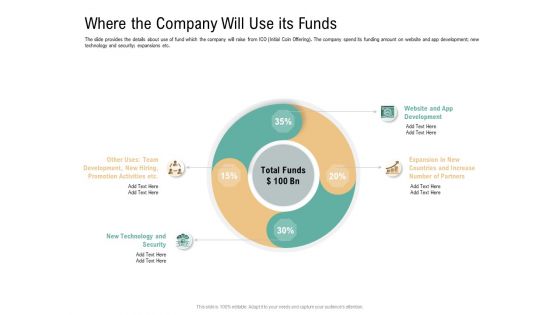
Where The Company Will Use Its Funds Virtual Currency Financing Pitch Deck Topics PDF
The slide provides the details about use of fund which the company will raise from ICO Initial Coin Offering. The company spend its funding amount on website and app development new technology and security expansions etc. Presenting where the company will use its funds virtual currency financing pitch deck topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like expansion in new countries and increase number of partners, website and app development, other uses team development, new hiring, promotion activities etc, new technology and security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Strategies For Conveyance Of Large Event Safety Plan Icons Pdf
This slide highlights major strategies to communicate effectively for large event security plans in order to ensure the safety of the business and enhance confidence among stakeholders. Key strategies are to inspect the venue, conduct a risk assessment, assess large-scale attacks, etc. Pitch your topic with ease and precision using this Strategies For Conveyance Of Large Event Safety Plan Icons Pdf. This layout presents information on Inspect The Venue, Conduct Risk Assessment, Crowd Controlling Measures. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights major strategies to communicate effectively for large event security plans in order to ensure the safety of the business and enhance confidence among stakeholders. Key strategies are to inspect the venue, conduct a risk assessment, assess large-scale attacks, etc.

Online Business Challenges And Best Practices Brochure Pdf
The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc. Pitch your topic with ease and precision using this Online Business Challenges And Best Practices Brochure Pdf. This layout presents information on Pain Points, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc.
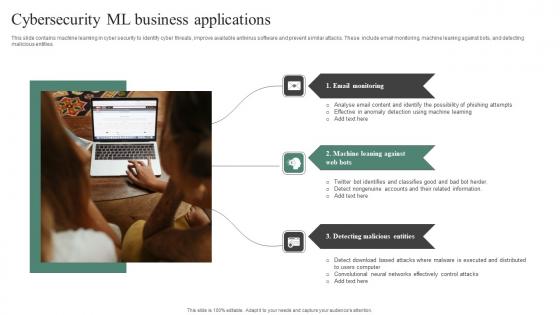
Cybersecurity ML Business Applications Sample Pdf
This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities. Pitch your topic with ease and precision using this Cybersecurity ML Business Applications Sample Pdf. This layout presents information on Email Monitoring, Machine Leaning, Detecting Malicious Entities. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities.

Cryptocurrency Ledger Public Blockchain Technology Infographics PDF
This slide depicts the public blockchain technology framework and how data is stored in the public blockchain, bitcoin, voting are few examples of the public blockchain. Presenting Cryptocurrency Ledger Public Blockchain Technology Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Network, Secure Method, Security Protocols Sincerely. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
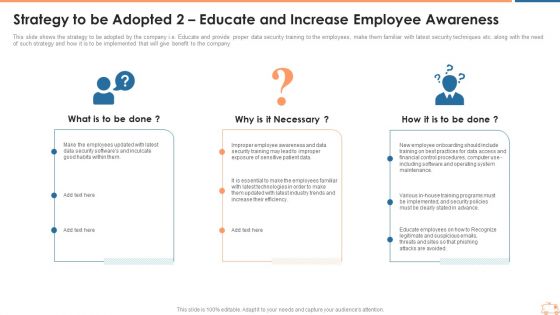
Strategy To Be Adopted 2 Educate And Increase Employee Awareness Inspiration PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 2 educate and increase employee awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
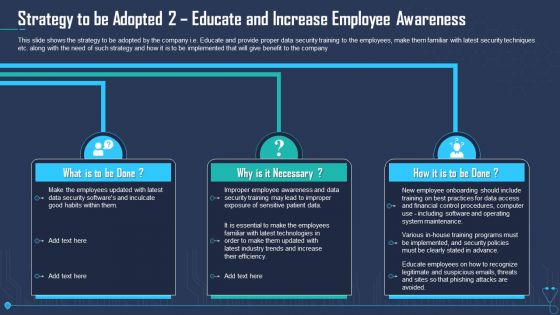
Strategy To Be Adopted 2 Educate And Increase Employee Awareness Infographics PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 2 educate and increase employee awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
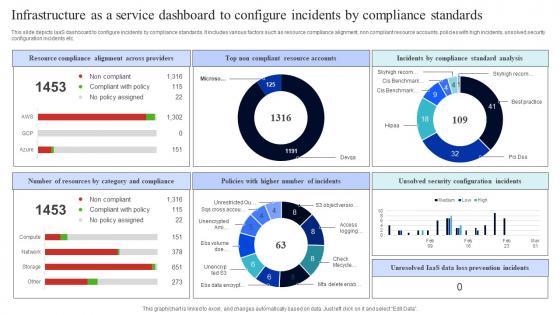
Infrastructure As A Service Dashboard To Configure Incidents By Compliance Standards Rules Pdf
This slide depicts IaaS dashboard to configure incidents by compliance standards. It includes various factors such as resource compliance alignment, non compliant resource accounts, policies with high incidents, unsolved security configuration incidents etc. Pitch your topic with ease and precision using this Infrastructure As A Service Dashboard To Configure Incidents By Compliance Standards Rules Pdf. This layout presents information on Resource Compliance Alignment, Across Providers, Top Non Compliant, Resource Accounts. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts IaaS dashboard to configure incidents by compliance standards. It includes various factors such as resource compliance alignment, non compliant resource accounts, policies with high incidents, unsolved security configuration incidents etc.

Companys Data Safety Recognition Communication Plan General Format Themes PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe-inspiring pitch with this creative companys data safety recognition communication plan general format themes pdf bundle. Topics like communication, description, frequency, audience can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Six Focus Areas To Be Prioritized In Healthcare Sector Ppt Outline Icon PDF
This slide covers the six areas which must be prioritized in healthcare sector such as virtual workforce, extraordinary scaling, security and compliance, power care operations, digital solutions, and technological roles. Presenting six focus areas to be prioritized in healthcare sector ppt outline icon pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like enable virtual workforce, scale extraordinary circumstances, establish elastic security and compliance, power care and operations with better insight, enable new digital and virtual care solutions, elevate role technology. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
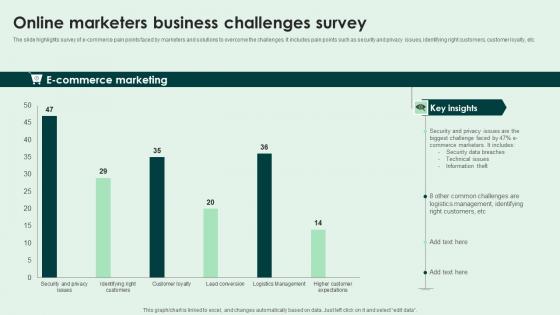
Online Marketers Business Challenges Survey Slides Pdf
The slide highlights survey of e-commerce pain points faced by marketers and solutions to overcome the challenges. It includes pain points such as security and privacy issues, identifying right customers, customer loyalty, etc. Pitch your topic with ease and precision using this Online Marketers Business Challenges Survey Slides Pdf. This layout presents information on E Commerce Marketing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide highlights survey of e-commerce pain points faced by marketers and solutions to overcome the challenges. It includes pain points such as security and privacy issues, identifying right customers, customer loyalty, etc.

Big Data Analysis Requirements Ppt Professional Format Ideas PDF
Deliver and pitch your topic in the best possible manner with this big data analysis requirements ppt professional format ideas pdf. Use them to share invaluable insights on data movement, existing skills, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Why Do You Need Data Management Themes PDF
Deliver and pitch your topic in the best possible manner with this why do you need data management themes pdf. Use them to share invaluable insights on minimize data movement, use existing skills, attend to data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
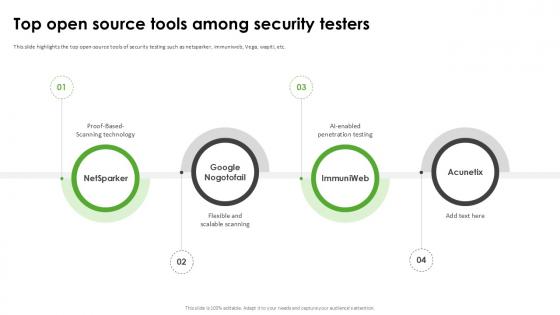
Top Open Source Tools Harnessing The World Of Ethical Ppt Slide
This slide highlights the top open-source tools of security testing such as netsparker, immuniweb, Vega, wapiti, etc. This Top Open Source Tools Harnessing The World Of Ethical Ppt Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the top open-source tools of security testing such as netsparker, immuniweb, Vega, wapiti, etc.
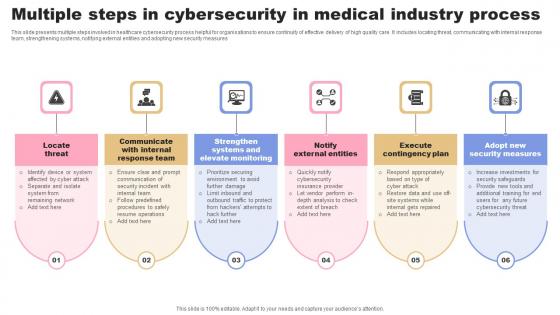
Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf
This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures Pitch your topic with ease and precision using this Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf This layout presents information on Locate Threat, Response Team, Elevate Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures

Debt Retrieval Techniques Detailed Analysis Of Debt Collection Process Ppt Pictures Layout Ideas PDF
Purpose of the following slide is to display the detailed analysis of the debt collection process as it highlights the key steps in the process, these steps can be detailed analysis of case, establishing contact with client, Assessing the case, security adjustment Presenting debt retrieval techniques detailed analysis of debt collection process ppt pictures layout ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like detailed analysis of particular case, establishing contact with clients, assessing the case, security adjustment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
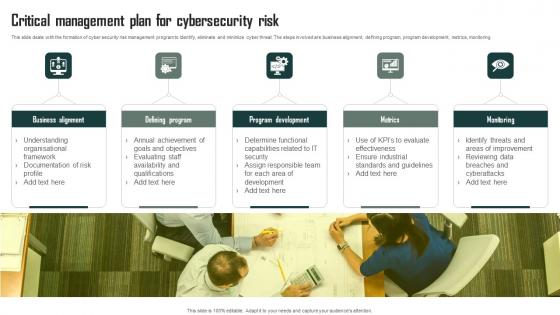
Critical Management Plan For Cybersecurity Risk Demonstration Pdf
This slide deals with the formation of cyber security risk management program to identify, eliminate and minimize cyber threat. The steps involved are business alignment, defining program, program development, metrics, monitoring Pitch your topic with ease and precision using this Critical Management Plan For Cybersecurity Risk Demonstration Pdf This layout presents information on Business Alignment, Defining Program, Program Development It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide deals with the formation of cyber security risk management program to identify, eliminate and minimize cyber threat. The steps involved are business alignment, defining program, program development, metrics, monitoring
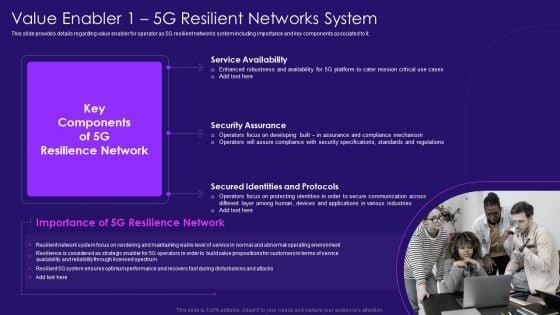
Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. Presenting Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Service Availability, Security Assurance, Secured Identities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
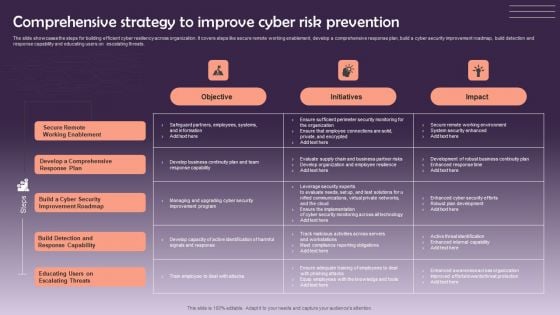
Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF
The slide showcases the steps for building efficient cyber resiliency across organization. It covers steps like secure remote working enablement, develop a comprehensive response plan, build a cyber security improvement roadmap, build detection and response capability and educating users on escalating threats. Pitch your topic with ease and precision using this Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF. This layout presents information on Objective, Initiatives, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
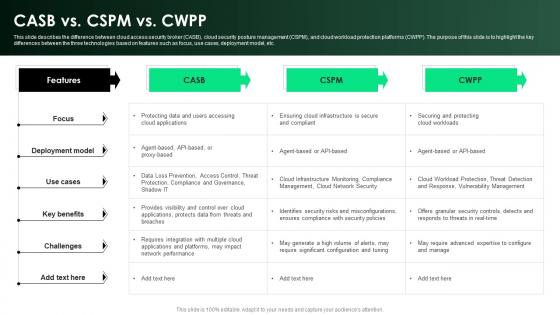
CASB 2 0 IT CASB Vs CSPM Vs CWPP Ppt Diagram Graph Charts
This slide describes the difference between cloud access security broker CASB , cloud security posture management CSPM , and cloud workload protection platforms CWPP . The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CASB 2 0 IT CASB Vs CSPM Vs CWPP Ppt Diagram Graph Charts and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the difference between cloud access security broker CASB , cloud security posture management CSPM , and cloud workload protection platforms CWPP . The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc.

Pitch Deck To Raise Capital From Product Pooled Funding Why Should Investors Choose Us Graphics PDF
This slide provides the key values which the company offers to its stakeholders. Key Values include Product quality, Reliability, Affordability, Security etc. Presenting pitch deck to raise capital from product pooled funding why should investors choose us graphics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like quality, reliable, affordable cost, secure, easy to work with. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
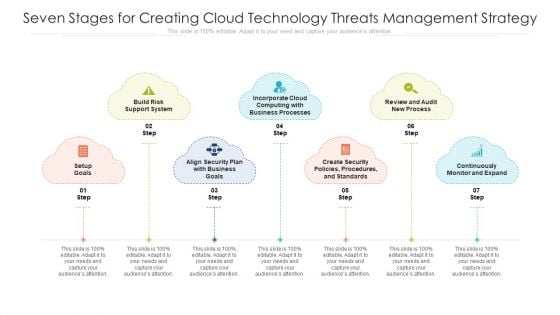
Seven Stages For Creating Cloud Technology Threats Management Strategy Ppt PowerPoint Presentation File Inspiration PDF
Presenting seven stages for creating cloud technology threats management strategy ppt powerpoint presentation file inspiration pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including business goals, security policies, continuously monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
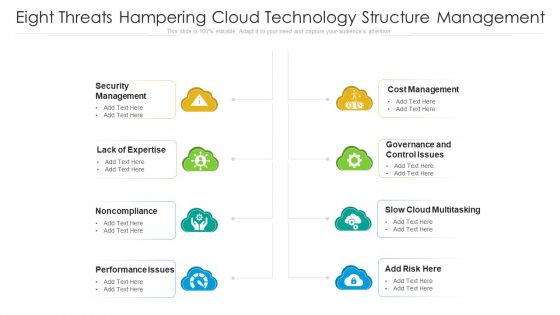
Eight Threats Hampering Cloud Technology Structure Management Ppt PowerPoint Presentation Gallery Slideshow PDF
Presenting eight threats hampering cloud technology structure management ppt powerpoint presentation gallery slideshow pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including performance issues, cost management, security management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































