Information Security

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

MDM Strategies At Office Mobile Device Management For Android Platform Introduction PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Presenting MDM Strategies At Office Mobile Device Management For Android Platform Introduction PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Application Control, Mandatary Installed, Theft Protection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
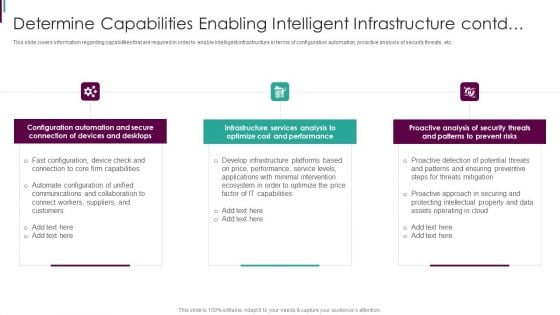
Developing Business Analytics Framework Determine Capabilities Infrastructure Contd Portrait PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. Presenting Developing Business Analytics Framework Determine Capabilities Infrastructure Contd Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Configuration Automation, Connection Devices, Infrastructure Services In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
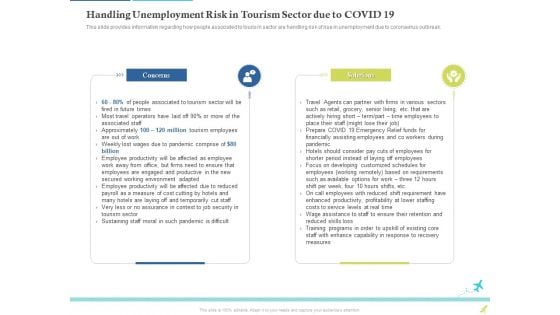
Rebuilding Travel Industry After COVID 19 Handling Unemployment Risk In Tourism Sector Due To COVID 19 Template PDF
This slide provides information regarding how people associated to tourism sector are handling risk of rise in unemployment due to coronavirus outbreak. Presenting rebuilding travel industry after COVID 19 handling unemployment risk in tourism sector due to covid 19 template pdf. to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like concerns, solutions, sustaining staff moral in such pandemic is difficult, very less or no assurance in context to job security in tourism sector. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Benefits Of ISO 27001 Certification Summary PDF
This slide displays various organizational benefits after getting ISO 27001 certification. Benefits included are information confidentiality, low operational cost, increase in the trust of valuable partners and customers and competitive advantage.Presenting Benefits Of ISO 27001 Certification Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Security Breaches, Competitive Advantage, Recognized Standard. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
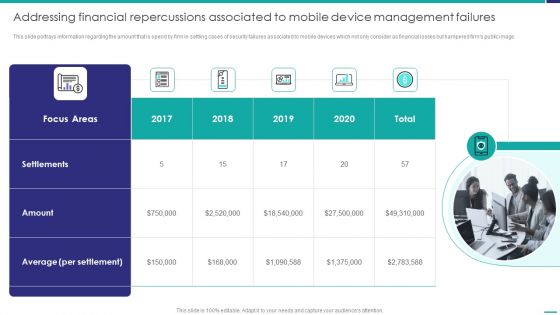
Addressing Financial Repercussions Associated To Mobile Device Management Failures Background PDF
This slide portrays information regarding the amount that is spend by firm in settling cases of security failures associated to mobile devices which not only consider as financial losses but hampered firms public image. Presenting Addressing Financial Repercussions Associated To Mobile Device Management Failures Background PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Settlements, Focus Areas, Per Settlement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Problem Statement Paubox Capital Funding Pitch Deck Graphics Pdf
This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file sharing options and spam and viruses overwhelming email systems. Explore a selection of the finest Problem Statement Paubox Capital Funding Pitch Deck Graphics Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Problem Statement Paubox Capital Funding Pitch Deck Graphics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file sharing options and spam and viruses overwhelming email systems.
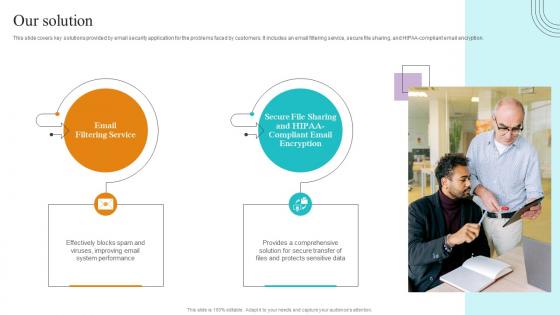
Our Solution Paubox Capital Funding Pitch Deck Summary Pdf
This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA compliant email encryption. Welcome to our selection of the Our Solution Paubox Capital Funding Pitch Deck Summary Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA compliant email encryption.

Client Testimonials Paubox Capital Funding Pitch Deck Professional Pdf
This slide covers customer reviews about the email security company. It includes positive feedback related to user friendly secure email software, helpful and professional team, seamless integration with Gmail. Get a simple yet stunning designed Client Testimonials Paubox Capital Funding Pitch Deck Professional Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Client Testimonials Paubox Capital Funding Pitch Deck Professional Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers customer reviews about the email security company. It includes positive feedback related to user friendly secure email software, helpful and professional team, seamless integration with Gmail.
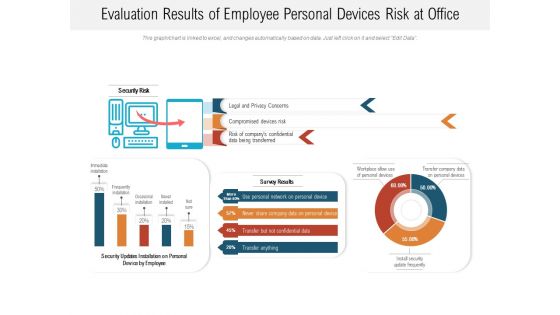
Evaluation Results Of Employee Personal Devices Risk At Office Ppt PowerPoint Presentation File Infographics PDF
Showcasing this set of slides titled evaluation results of employee personal devices risk at office ppt powerpoint presentation file infographics pdf. The topics addressed in these templates are security risk, devices risk, personal device. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
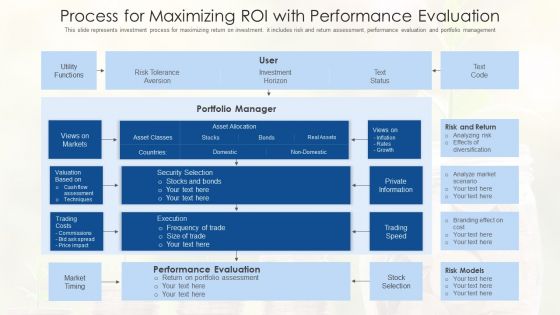
Process For Maximizing Roi With Performance Evaluation Ppt PowerPoint Presentation Model Background Images PDF
Showcasing this set of slides titled process for maximizing roi with performance evaluation ppt powerpoint presentation model background images pdf. The topics addressed in these templates are security selection, stocks and bonds, performance evaluation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Global Educative And Training Events For Skill Development Summary PDF
Showcasing this set of slides titled Global Educative And Training Events For Skill Development Summary PDF. The topics addressed in these templates are Leadership Program, Security Training, Melbourne Australia. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Zero Trust Model Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Find highly impressive Zero Trust Model Comparison Between Zero Trust Model SDP And VPN on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Comparison Between Zero Trust Model SDP And VPN for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

Zero Trust Network Access Roadmap To Implement Zero Trust Network Access Model
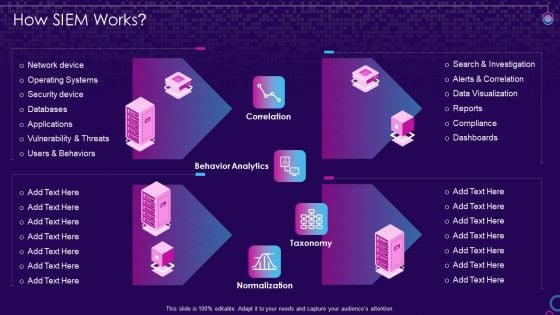
SIEM Services How SIEM Works Ppt Microsoft PDF
Deliver an awe inspiring pitch with this creative siem services how siem works ppt microsoft pdf bundle. Topics like network device, operating systems, security device, vulnerability and threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Login For Income Statement Powerpoint Template
Our above slide display graphics of log in page on mobile phone with money flowing out of tap. Download this diagram slide to display security measures for money saving account. Adjust the above diagram in your business presentations to visually support your content.
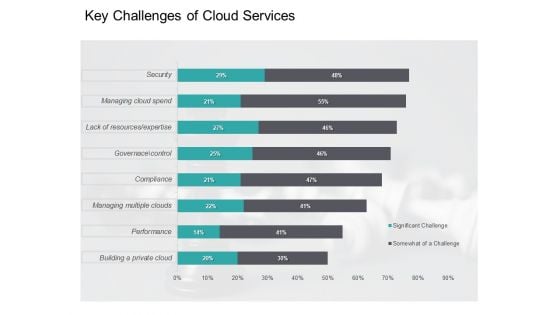
Cloud Based Marketing Key Challenges Of Cloud Services Ppt PowerPoint Presentation Styles Graphics Template PDF
Deliver an awe-inspiring pitch with this creative cloud based marketing key challenges of cloud services ppt powerpoint presentation styles graphics template pdf bundle. Topics like building private cloud, performance, managing multiple clouds, compliance, governance, control, lack resources, expertise, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
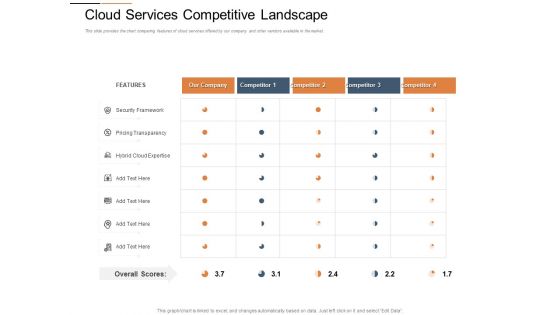
Cloud Services Best Practices Marketing Plan Agenda Cloud Services Competitive Landscape Guidelines PDF
Deliver an awe inspiring pitch with this creative cloud services best practices marketing plan agenda cloud services competitive landscape guidelines pdf bundle. Topics like security framework, pricing transparency, hybrid cloud expertise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
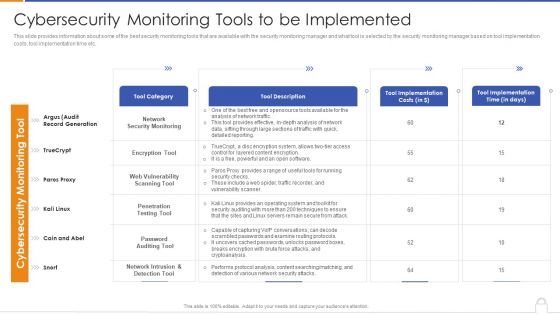
Cybersecurity Monitoring Tools To Be Implemented Topics PDF
Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring tools to be implemented topics pdf. Use them to share invaluable insights on security monitoring, password auditing tool, tool implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Housing Mortgage Additional Benefits For Home Loan Proposal Ppt Slides Background PDF
Deliver an awe inspiring pitch with this creative housing mortgage additional benefits for home loan proposal ppt slides background pdf bundle. Topics like credit cards, easy security investment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Installation Cost Of Smart Home Systems Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various systems installed in smart homes. Major smart systems covered are smart lighting systems, thermostats, smart locks, smart doorbells, security systems, motion sensors, smoke detection sensors, water sensors, alarm systems, security cameras, smart speakers, smart displays, smart plugs, robot vacuums, HVAC system, medical alert system. Are you searching for a Installation Cost Of Smart Home Systems Utilizing Smart Appliances IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Installation Cost Of Smart Home Systems Utilizing Smart Appliances IoT SS V from Slidegeeks today. This slide provides an overview of the various systems installed in smart homes. Major smart systems covered are smart lighting systems, thermostats, smart locks, smart doorbells, security systems, motion sensors, smoke detection sensors, water sensors, alarm systems, security cameras, smart speakers, smart displays, smart plugs, robot vacuums, HVAC system, medical alert system.
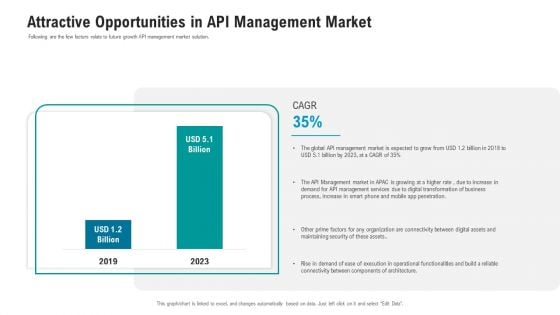
API Ecosystem Attractive Opportunities In API Management Market Infographics PDF
Following are the few factors relate to future growth API management market solution. Deliver an awe inspiring pitch with this creative api ecosystem attractive opportunities in api management market infographics pdf bundle. Topics like management market, services, process, organization, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
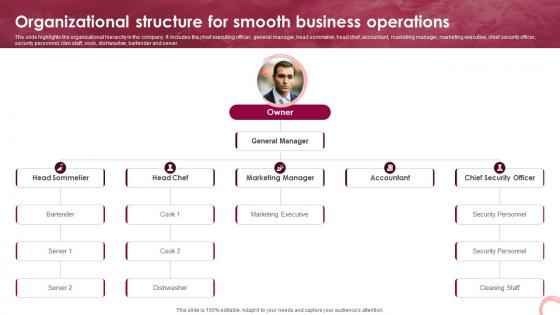
Wine Lounge Business Plan Organizational Structure For Smooth Business Operations BP SS V
The slide highlights the organizational hierarchy in the company. It includes the chief executing officer, general manager, head sommelier, head chef, accountant, marketing manager, marketing executive, chief security officer, security personnel, clen staff, cook, dishwasher, bartender and server. Are you searching for a Wine Lounge Business Plan Organizational Structure For Smooth Business Operations BP SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wine Lounge Business Plan Organizational Structure For Smooth Business Operations BP SS V from Slidegeeks today. The slide highlights the organizational hierarchy in the company. It includes the chief executing officer, general manager, head sommelier, head chef, accountant, marketing manager, marketing executive, chief security officer, security personnel, clen staff, cook, dishwasher, bartender and server.
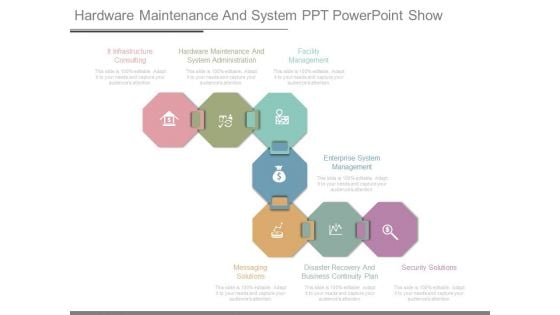
Hardware Maintenance And System Ppt Powerpoint Show
This is a hardware maintenance and system ppt powerpoint show. This is a seven stage process. The stages in this process are it infrastructure consulting, hardware maintenance and system administration, facility management, enterprise system management, messaging solutions, disaster recovery and business continuity plan, security solutions.
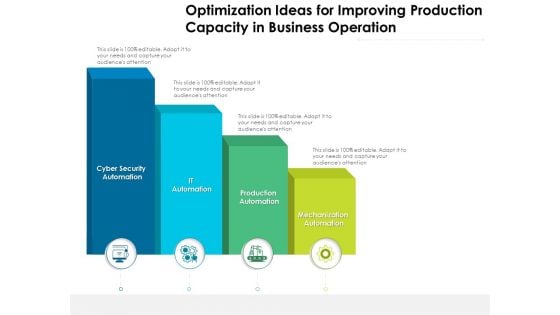
Optimization Ideas For Improving Production Capacity In Business Operation Ppt PowerPoint Presentation Outline Visual Aids PDF
Presenting this set of slides with name optimization ideas for improving production capacity in business operation ppt powerpoint presentation outline visual aids pdf. This is a four stage process. The stages in this process are mechanization automation, production automation, it automation, cyber security automation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Agile Best Practices For Effective Team Agile Kanban Methodology Chart With Stories Introduction PDF
Deliver an awe inspiring pitch with this creative agile best practices for effective team agile kanban methodology chart with stories introduction pdf bundle. Topics like security integration, product development, automation processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
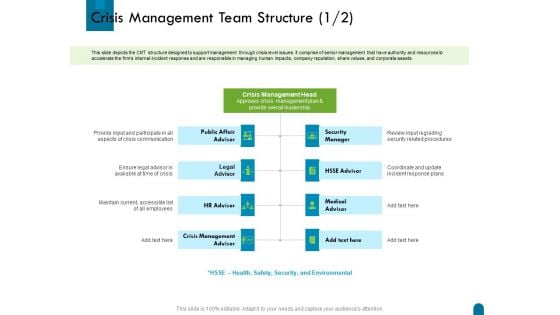
Crisis Management Team Structure Ppt Infographic Template Background Images PDF
Deliver an awe-inspiring pitch with this creative crisis management team structure ppt infographic template background images pdf bundle. Topics like public affair advisor, legal advisor, hr advisor, crisis management advisor, security manager, medical advisor can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agile Kanban Methodology Chart With Stories Microsoft PDF
Deliver an awe inspiring pitch with this creative agile kanban methodology chart with stories microsoft pdf bundle. Topics like security integration, automation processes, product development can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Feedback From Employees On Retaining Talent With Key Notes Template PDF
Deliver an awe inspiring pitch with this creative feedback from employees on retaining talent with key notes template pdf bundle. Topics like satisfaction with existing job, fair work compensation, employment security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
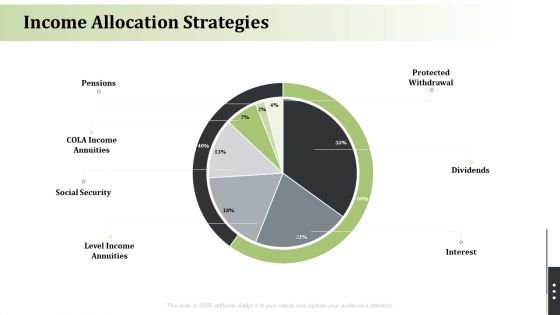
Pension Alimony Income Allocation Strategies Portrait PDF
Deliver an awe inspiring pitch with this creative pension alimony income allocation strategies portrait pdf bundle. Topics like income, security social, interest can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
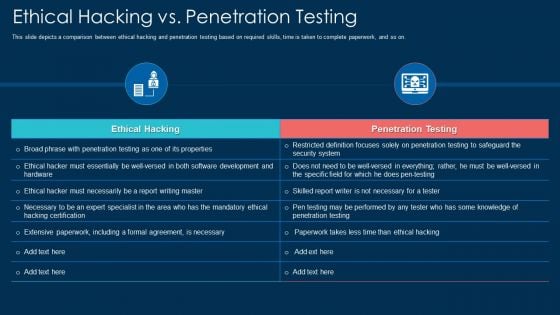
Ethical Hacking Vs Penetration Testing Ppt Tips PDF
This slide depicts a comparison between ethical hacking and penetration testing based on required skills, time is taken to complete paperwork, and so on. Deliver an awe inspiring pitch with this creative NAMEEEEE bundle. Topics like development, security system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
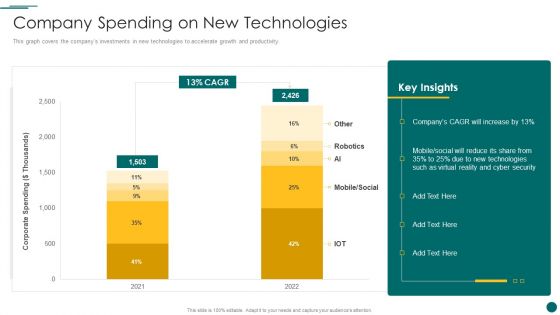
Organization Reinvention Company Spending On New Technologies Microsoft PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Reinvention Company Spending On New Technologies Microsoft PDF bundle. Topics like Social, Technologies, Cyber Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
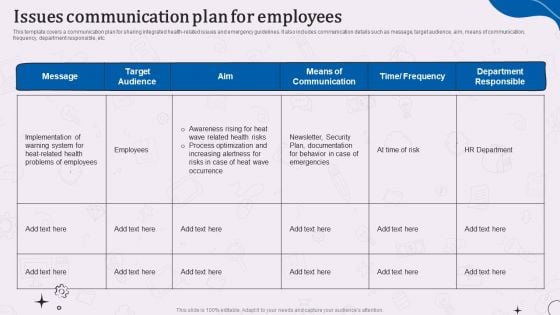
Types Of Corporate Communication Techniques Issues Communication Plan For Employees Microsoft PDF
Deliver and pitch your topic in the best possible manner with this Types Of Corporate Communication Techniques Issues Communication Plan For Employees Microsoft PDF. Use them to share invaluable insights on Implementation, Target Audience, Security Plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Vendor Management To Handle Purchase Vendor Risk Management And Audit Checklist Clipart PDF
Deliver and pitch your topic in the best possible manner with this Vendor Management To Handle Purchase Vendor Risk Management And Audit Checklist Clipart PDF. Use them to share invaluable insights on Lawsuits Termination, Renewal Requirements, Proper Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
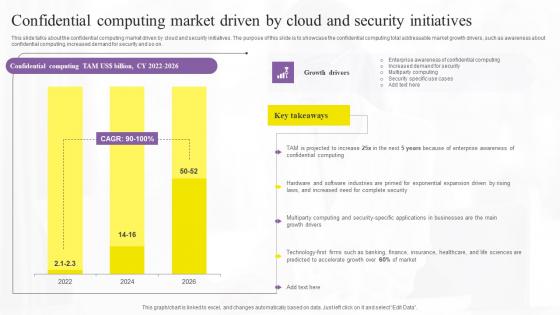
Confidential Computing Market Driven Confidential Computing Technologies Rules Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. This modern and well-arranged Confidential Computing Market Driven Confidential Computing Technologies Rules Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.

Software Defined Perimeter SDP Roadmap To Implement Zero Trust Network Access Model
This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the business existing security model, etc. Boost your pitch with our creative Software Defined Perimeter SDP Roadmap To Implement Zero Trust Network Access Model. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the business existing security model, etc.

Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck
This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches.
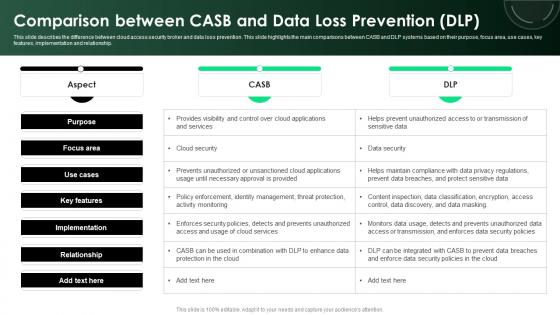
CASB 2 0 IT Comparison Between CASB And Data Loss Prevention DLP
This slide describes the difference between cloud access security broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship. Take your projects to the next level with our ultimate collection of CASB 2 0 IT Comparison Between CASB And Data Loss Prevention DLP. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide describes the difference between cloud access security broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship.

Exit Strategy Email And Data Protection Platform Capital Funding Pitch Deck PPT Template
This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering. Present like a pro with Exit Strategy Email And Data Protection Platform Capital Funding Pitch Deck PPT Template. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering.

Roadmap For Cloud Data Client Side Encryption PPT Presentation
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc. The Roadmap For Cloud Data Client Side Encryption PPT Presentation is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc.
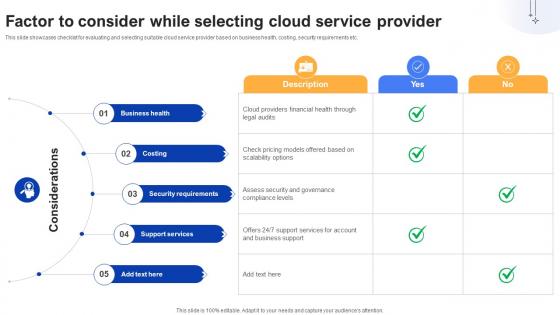
Effective Data Migration Factor To Consider While Selecting Cloud Service
This slide showcases checklist for evaluating and selecting suitable cloud service provider based on business health, costing, security requirements etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Effective Data Migration Factor To Consider While Selecting Cloud Service to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases checklist for evaluating and selecting suitable cloud service provider based on business health, costing, security requirements etc.
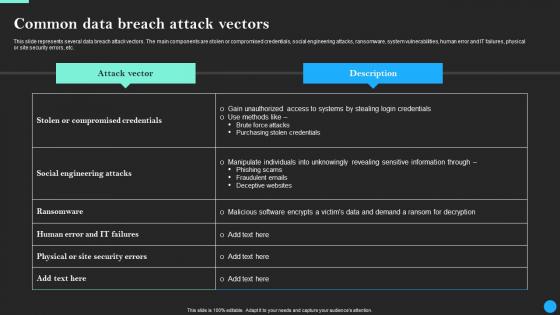
Common Data Breach Attack Vectors Data Breach Prevention Clipart Pdf
This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Present like a pro with Common Data Breach Attack Vectors Data Breach Prevention Clipart Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc.

Common Data Breach Attack Vectors Data Fortification Strengthening Defenses
This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Present like a pro with Common Data Breach Attack Vectors Data Fortification Strengthening Defenses. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc.
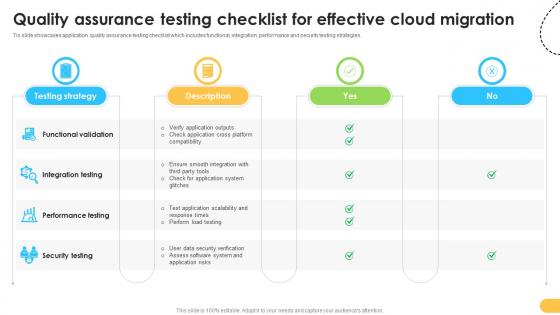
Quality Assurance Testing Checklist For Effective Data Migration From On Premises
Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies. The Quality Assurance Testing Checklist For Effective Data Migration From On Premises is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies.
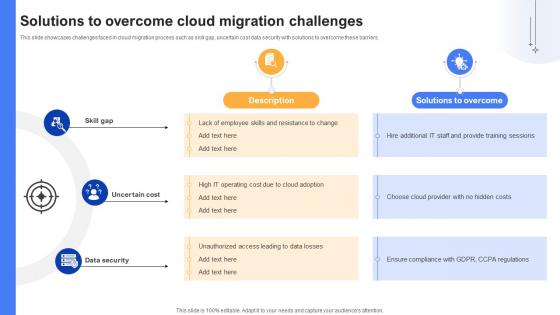
Effective Data Migration Solutions To Overcome Cloud Migration Challenges
This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Effective Data Migration Solutions To Overcome Cloud Migration Challenges for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers.

Key Facts Data Management Company Investor Funding Pitch Deck
The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of rightsizing savings, reverted deploys, effective cost per resource, production incidents by application or team and number of security lapses. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Key Facts Data Management Company Investor Funding Pitch Deck and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of rightsizing savings, reverted deploys, effective cost per resource, production incidents by application or team and number of security lapses.
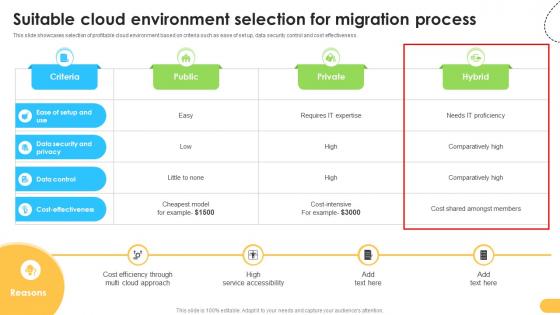
Suitable Cloud Environment Selection For Data Migration From On Premises
This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Suitable Cloud Environment Selection For Data Migration From On Premises to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Suitable Cloud Environment Selection For Data Migration From On Premises. This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness.
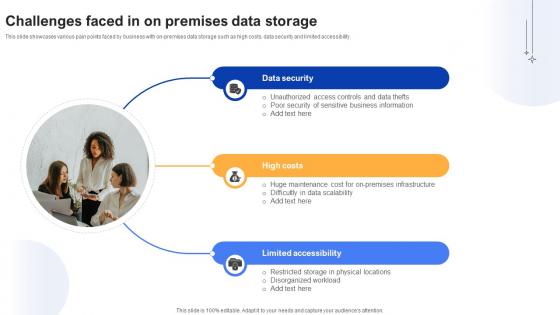
Effective Data Migration Challenges Faced In On Premises Data Storage
This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Effective Data Migration Challenges Faced In On Premises Data Storage a try. Our experts have put a lot of knowledge and effort into creating this impeccable Effective Data Migration Challenges Faced In On Premises Data Storage. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility.
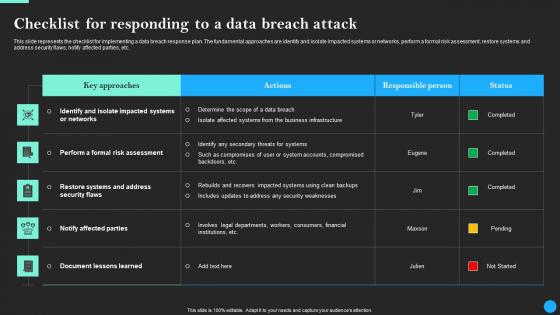
Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.

Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.

Challenges Faced In On Premises Data Storage Data Migration From On Premises
This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Challenges Faced In On Premises Data Storage Data Migration From On Premises a try. Our experts have put a lot of knowledge and effort into creating this impeccable Challenges Faced In On Premises Data Storage Data Migration From On Premises. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility.
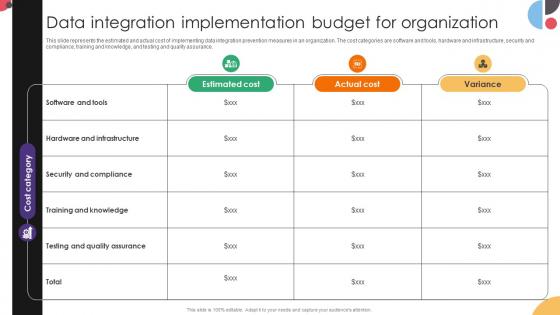
Data Integration Implementation Budget For Organization Data Integration Strategies For Business
This slide represents the estimated and actual cost of implementing data integration prevention measures in an organization. The cost categories are software and tools, hardware and infrastructure, security and compliance, training and knowledge, and testing and quality assurance. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Integration Implementation Budget For Organization Data Integration Strategies For Business and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the estimated and actual cost of implementing data integration prevention measures in an organization. The cost categories are software and tools, hardware and infrastructure, security and compliance, training and knowledge, and testing and quality assurance.

Implement General Data Protection Regulation DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.
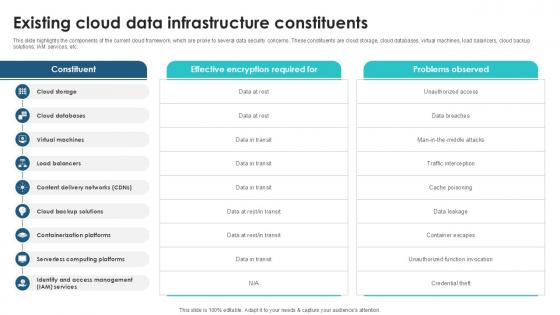
Existing Cloud Data Infrastructure Client Side Encryption PPT Sample
This slide highlights the components of the current cloud framework, which are prone to several data security concerns. These constituents are cloud storage, cloud databases, virtual machines, load balancers, cloud backup solutions, IAM services, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Existing Cloud Data Infrastructure Client Side Encryption PPT Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide highlights the components of the current cloud framework, which are prone to several data security concerns. These constituents are cloud storage, cloud databases, virtual machines, load balancers, cloud backup solutions, IAM services, etc.
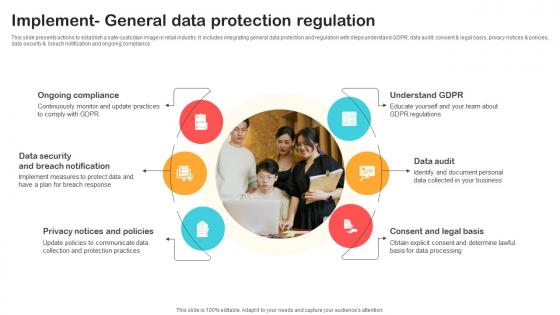
Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.
Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
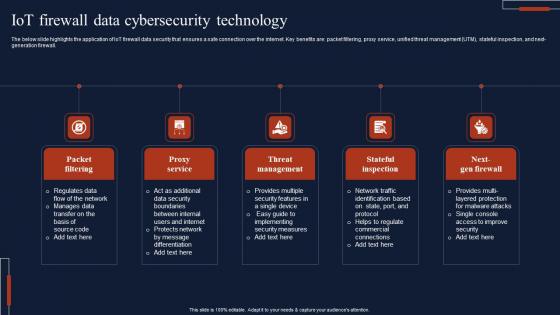
IOT Firewall Data Cybersecurity Technology Brochure Pdf
The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall. Showcasing this set of slides titled IOT Firewall Data Cybersecurity Technology Brochure Pdf The topics addressed in these templates are Packet Filtering, Proxy Service, Threat Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall.
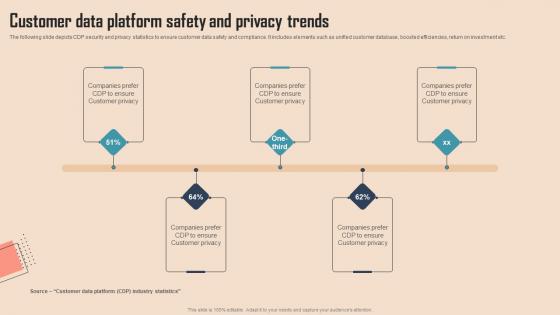
Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc.
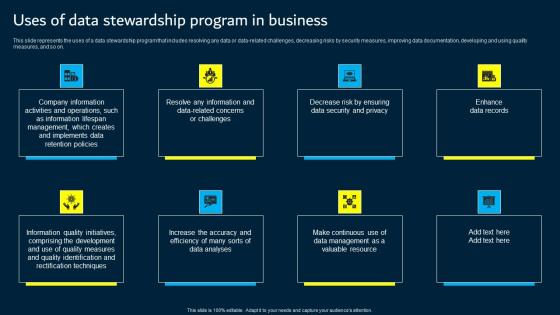
Uses Of Data Stewardship Program In Business Data Custodianship Structure Pdf
This slide represents the uses of a data stewardship program that includes resolving any data or data related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on. Do you know about Slidesgeeks Uses Of Data Stewardship Program In Business Data Custodianship Structure Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the uses of a data stewardship program that includes resolving any data or data related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on.
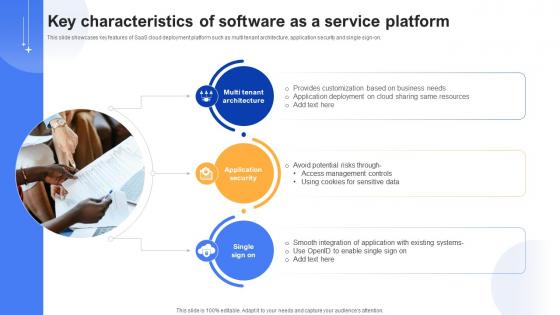
Effective Data Migration Key Characteristics Of Software As A Service Platform
This slide showcases key features of SaaS cloud deployment platform such as multi tenant architecture, application security and single sign-on. Are you searching for a Effective Data Migration Key Characteristics Of Software As A Service Platform that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Effective Data Migration Key Characteristics Of Software As A Service Platform from Slidegeeks today. This slide showcases key features of SaaS cloud deployment platform such as multi tenant architecture, application security and single sign-on.


 Continue with Email
Continue with Email

 Home
Home


































