Information Security

Multiple AML Technology Integration Challenges Mapping Out The Anti Money Fin SS V
The following slide presents various challenges faced during AML and technology integration that hinders the operational process. The different challenges are data security concerns, integrity complexity, cost constraints, and regulatory challenges. Do you know about Slidesgeeks Multiple AML Technology Integration Challenges Mapping Out The Anti Money Fin SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide presents various challenges faced during AML and technology integration that hinders the operational process. The different challenges are data security concerns, integrity complexity, cost constraints, and regulatory challenges.
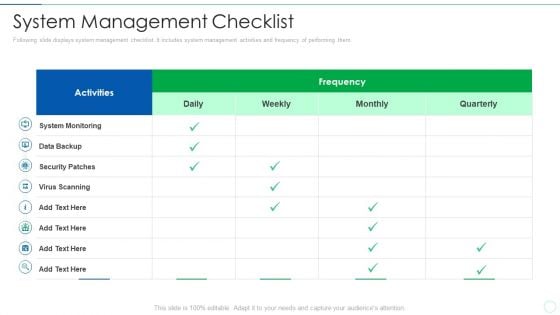
Effective IT Risk Management Process System Management Checklist Brochure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this effective it risk management process system management checklist brochure pdf. Use them to share invaluable insights on security patches, data backup, system monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

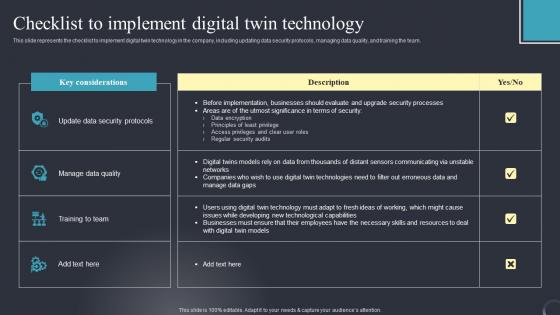
Checklist To Implement Digital Twin Digital Twins For Enhanced Industrial Infographics Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. Present like a pro with Checklist To Implement Digital Twin Digital Twins For Enhanced Industrial Infographics Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team.
Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team.
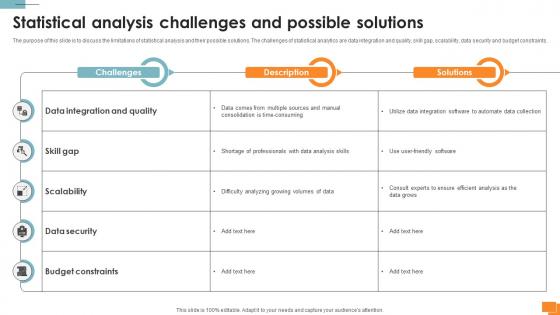
Statistical Tools For Evidence Statistical Analysis Challenges And Possible Solutions
The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints. Take your projects to the next level with our ultimate collection of Statistical Tools For Evidence Statistical Analysis Challenges And Possible Solutions. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Drone Technology Powerpoint Ppt Template Bundles
This Drone Technology Powerpoint Ppt Template Bundles is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This UAV Technology, Aerial Robotics, Drone Innovation, Unmanned Aerial Vehicle Tech, Autonomous Drone Systems-slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence. Explore our engaging PPT on Drone Technology, involving how drones are transforming industries like security and agriculture. Learn about their evolving role in surveillance, disaster response, etc. Get glimpse into future of unmanned aerial systems and their potential impact.
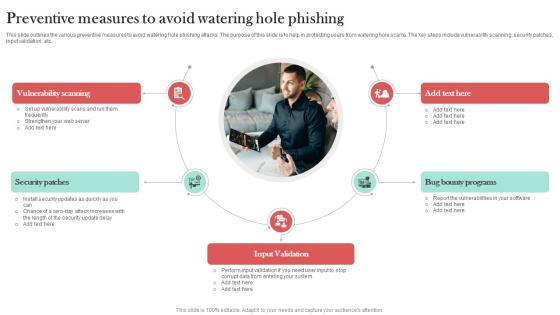
Preventive Measures To Avoid Watering Man In The Middle Phishing IT
This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Present like a pro with Preventive Measures To Avoid Watering Man In The Middle Phishing IT. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc.
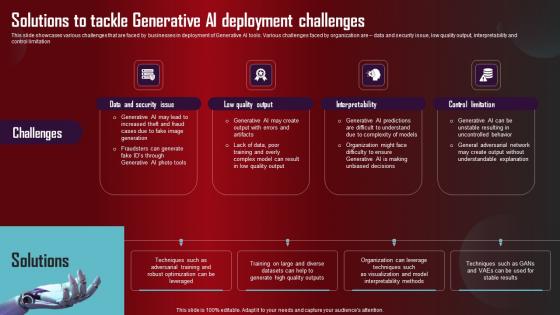
Solutions To Tackle Generative AI Role Of Generative AI Tools Across Portrait Pdf
This slide showcases various challenges that are faced by businesses in deployment of Generative AI tools. Various challenges faced by organization are data and security issue, low quality output, interpretability and control limitation Present like a pro with Solutions To Tackle Generative AI Role Of Generative AI Tools Across Portrait Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases various challenges that are faced by businesses in deployment of Generative AI tools. Various challenges faced by organization are data and security issue, low quality output, interpretability and control limitation.
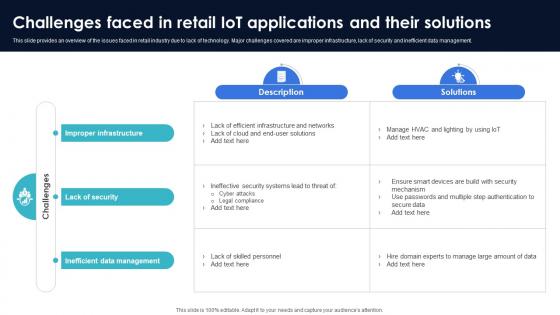
Optimization Of IoT Remote Monitoring Challenges Faced In Retail IoT Applications And Their IoT SS V
This slide provides an overview of the issues faced in retail industry due to lack of technology. Major challenges covered are improper infrastructure, lack of security and inefficient data management. Make sure to capture your audiences attention in your business displays with our gratis customizable Optimization Of IoT Remote Monitoring Challenges Faced In Retail IoT Applications And Their IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide provides an overview of the issues faced in retail industry due to lack of technology. Major challenges covered are improper infrastructure, lack of security and inefficient data management.
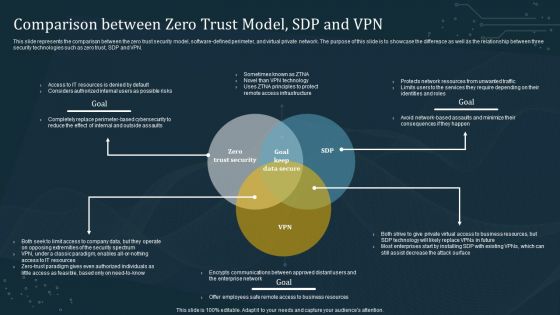
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
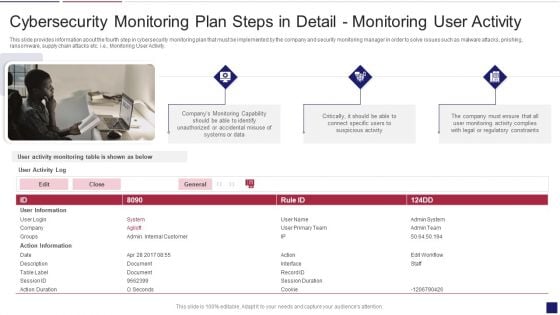
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.
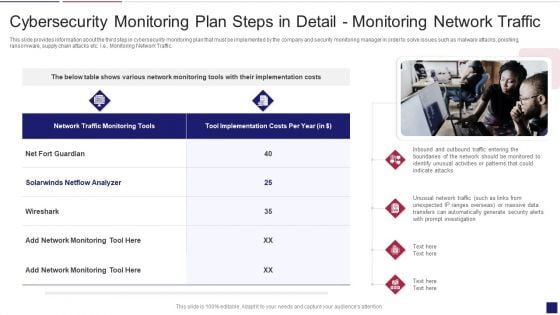
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
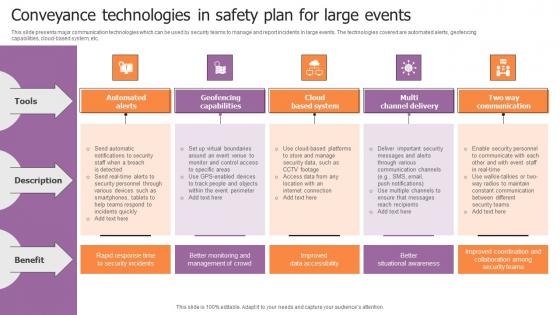
Conveyance Technologies In Safety Plan For Large Events Brochure Pdf
This slide presents major communication technologies which can be used by security teams to manage and report incidents in large events. The technologies covered are automated alerts, geofencing capabilities, cloud-based system, etc. Showcasing this set of slides titled Conveyance Technologies In Safety Plan For Large Events Brochure Pdf. The topics addressed in these templates are Automated Alerts, Geofencing Capabilities, Cloud Based System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents major communication technologies which can be used by security teams to manage and report incidents in large events. The technologies covered are automated alerts, geofencing capabilities, cloud-based system, etc.
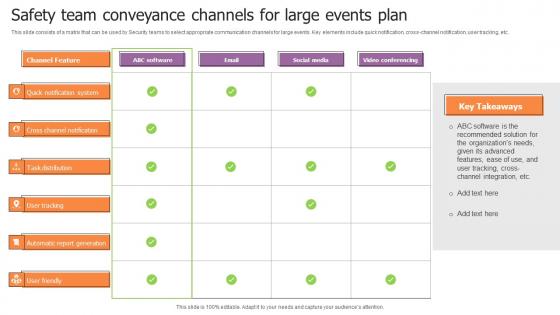
Safety Team Conveyance Channels For Large Events Plan Brochure Pdf
This slide consists of a matrix that can be used by Security teams to select appropriate communication channels for large events. Key elements include quick notification, cross-channel notification, user tracking, etc. Showcasing this set of slides titled Safety Team Conveyance Channels For Large Events Plan Brochure Pdf. The topics addressed in these templates are Channel Feature, Software, Email, Social Media. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide consists of a matrix that can be used by Security teams to select appropriate communication channels for large events. Key elements include quick notification, cross-channel notification, user tracking, etc.

Incident Conveyance Plan Timeline For Safety Teams In Large Events Inspiration Pdf
The following slide presents an Incident communication plan timeline to be followed by security teams in case of breach or mishappening in large events. Key elements covered are incident communicated by attendee or staff, incident verified, action plan developed, etc. Showcasing this set of slides titled Incident Conveyance Plan Timeline For Safety Teams In Large Events Inspiration Pdf. The topics addressed in these templates are Operations Resume, Treatment Validation . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide presents an Incident communication plan timeline to be followed by security teams in case of breach or mishappening in large events. Key elements covered are incident communicated by attendee or staff, incident verified, action plan developed, etc.
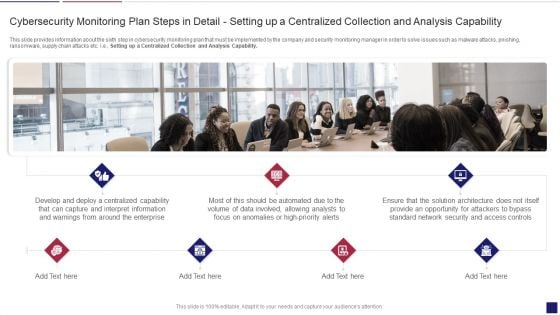
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
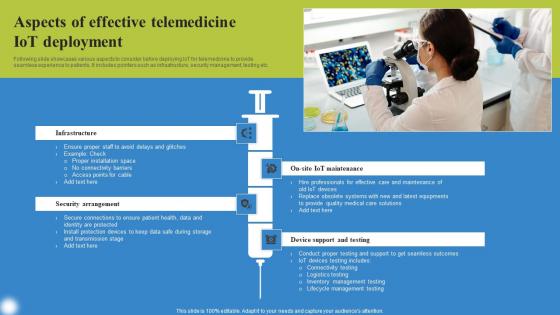
Aspects Of Effective Telemedicine Deploying IoT Solutions For Enhanced Healthcare Portrait Pdf
Following slide showcases various aspects to consider before deploying IoT for telemedicine to provide seamless experience to patients. It includes pointers such as infrastructure, security management, testing etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Aspects Of Effective Telemedicine Deploying IoT Solutions For Enhanced Healthcare Portrait Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Following slide showcases various aspects to consider before deploying IoT for telemedicine to provide seamless experience to patients. It includes pointers such as infrastructure, security management, testing etc.
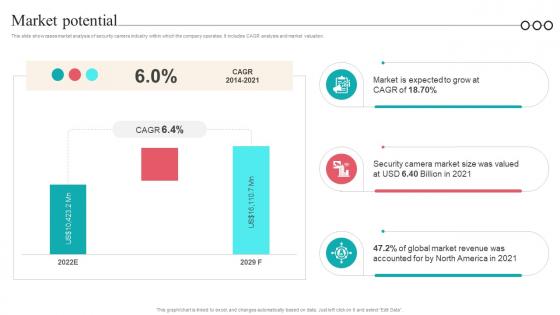
Market Potential Camera Management Platform Investor Funding Elevator Pitch Deck
This slide showcases market analysis of security camera industry within which the company operates. It includes CAGR analysis and market valuation. If you are looking for a format to display your unique thoughts, then the professionally designed Market Potential Camera Management Platform Investor Funding Elevator Pitch Deck is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Market Potential Camera Management Platform Investor Funding Elevator Pitch Deck and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases market analysis of security camera industry within which the company operates. It includes CAGR analysis and market valuation.
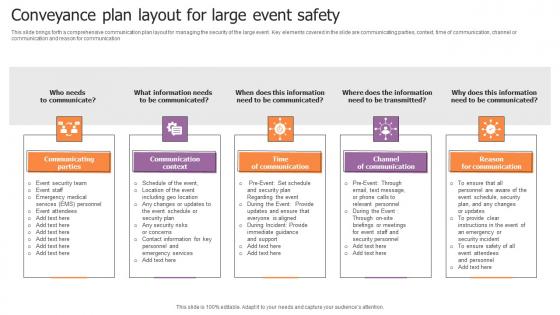
Conveyance Plan Layout For Large Event Safety Themes Pdf
This slide brings forth a comprehensive communication plan layout for managing the security of the large event. Key elements covered in the slide are communicating parties, context, time of communication, channel or communication and reason for communication. Showcasing this set of slides titled Conveyance Plan Layout For Large Event Safety Themes Pdf. The topics addressed in these templates are Communicating Parties, Communication Context, Time Of Communication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth a comprehensive communication plan layout for managing the security of the large event. Key elements covered in the slide are communicating parties, context, time of communication, channel or communication and reason for communication.
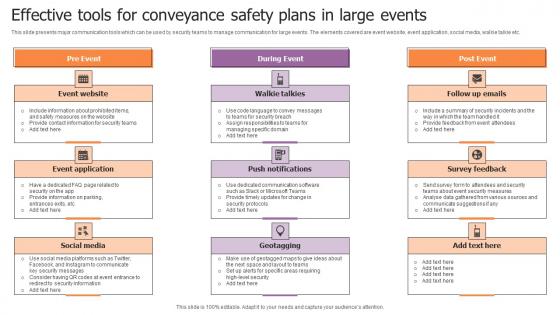
Effective Tools For Conveyance Safety Plans In Large Events Sample Pdf
This slide presents major communication tools which can be used by security teams to manage communication for large events. The elements covered are event website, event application, social media, walkie talkie etc. Showcasing this set of slides titled Effective Tools For Conveyance Safety Plans In Large Events Sample Pdf. The topics addressed in these templates are Event Website, Walkie Talkies, Push Notifications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents major communication tools which can be used by security teams to manage communication for large events. The elements covered are event website, event application, social media, walkie talkie etc.
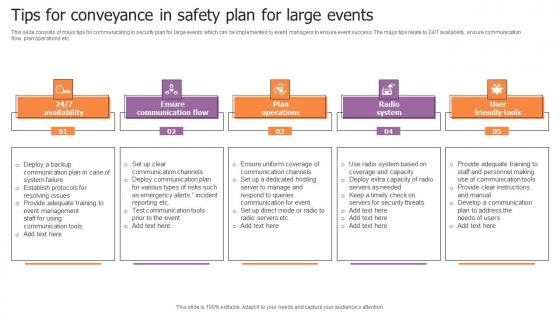
Tips For Conveyance In Safety Plan For Large Events Sample Pdf
This slide consists of major tips for communicating in security plan for large events which can be implemented by event managers to ensure event success. The major tips relate to 247 availability, ensure communication flow, plan operations etc. Showcasing this set of slides titled Tips For Conveyance In Safety Plan For Large Events Sample Pdf. The topics addressed in these templates are Ensure Communication Flow, Plan Operations, Radio System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide consists of major tips for communicating in security plan for large events which can be implemented by event managers to ensure event success. The major tips relate to 247 availability, ensure communication flow, plan operations etc.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
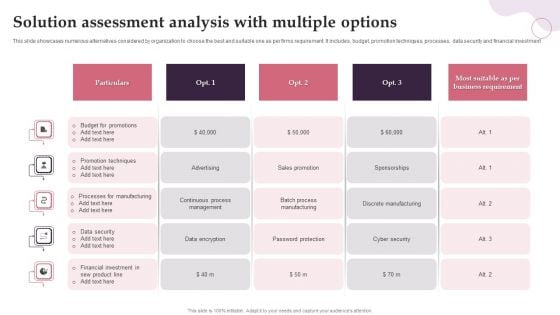
Solution Assessment Analysis With Multiple Options Sample PDF
This slide showcases numerous alternatives considered by organization to choose the best and suitable one as per firms requirement. It includes, budget, promotion techniques, processes, data security and financial investment. Showcasing this set of slides titled Solution Assessment Analysis With Multiple Options Sample PDF. The topics addressed in these templates are Budget, Manufacturing, Promotion Techniques. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Understanding The Kubernetes Components Through Diagram Table Of Contents Ppt Ideas Graphic Images
Presenting this set of slides with name understanding the kubernetes components through diagram table of contents ppt ideas graphic images. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Understanding The Kubernetes Concepts And Architecture Table Of Contents Ppt Summary Inspiration PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture table of contents ppt summary inspiration pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
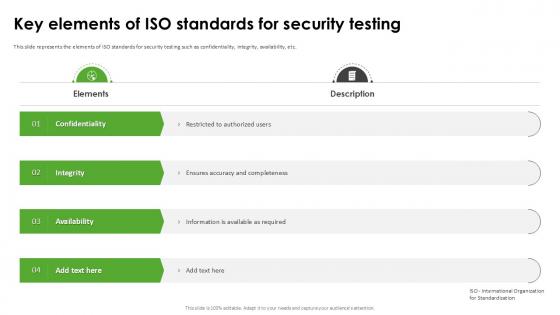
Key Elements Of Iso Standards Harnessing The World Of Ethical Ppt Presentation
This slide represents the elements of ISO standards for security testing such as confidentiality, integrity, availability, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Elements Of Iso Standards Harnessing The World Of Ethical Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the elements of ISO standards for security testing such as confidentiality, integrity, availability, etc.
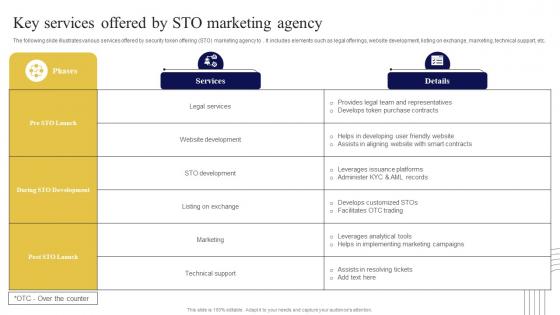
Key Services Offered By STO Exploring Investment Opportunities Topics Pdf
The following slide illustrates various services offered by security token offering STO marketing agency to. It includes elements such as legal offerings, website development, listing on exchange, marketing, technical support, etc. Slidegeeks has constructed Key Services Offered By STO Exploring Investment Opportunities Topics Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide illustrates various services offered by security token offering STO marketing agency to. It includes elements such as legal offerings, website development, listing on exchange, marketing, technical support, etc.
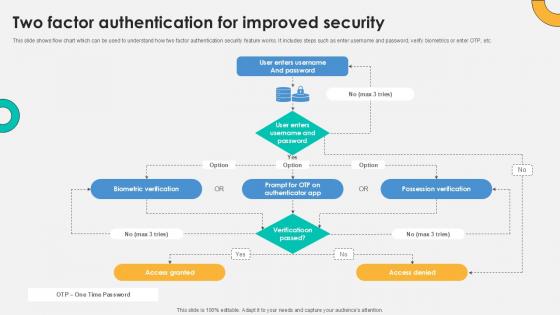
Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
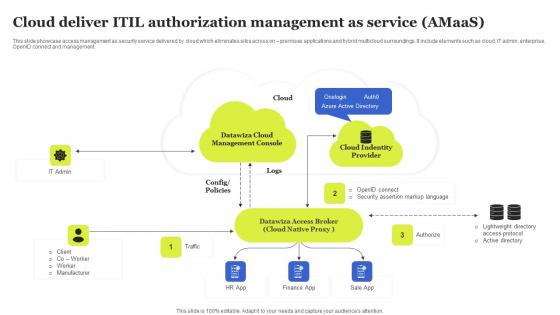
Cloud Deliver ITIL Authorization Management As Service Amaas Sample Pdf
This slide showcase access management as security service delivered by cloud which eliminates silos across on premises applications and hybrid multicloud surroundings. It include elements such as cloud, IT admin, enterprise, OpenID connect and management. Showcasing this set of slides titled Cloud Deliver ITIL Authorization Management As Service Amaas Sample Pdf The topics addressed in these templates are Management Console, Datawiza Access, Cloud Identity All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase access management as security service delivered by cloud which eliminates silos across on premises applications and hybrid multicloud surroundings. It include elements such as cloud, IT admin, enterprise, OpenID connect and management.
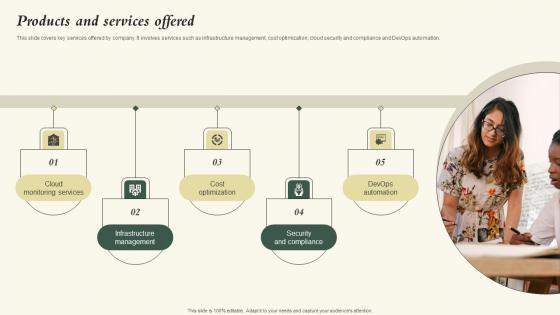
Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf
This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation.

Services Offered Camera Management Platform Investor Funding Elevator Pitch Deck
This slide mentions various features offered by security platform to its users. Key features include cloud recording, snapshotting, object counting, movement heatmaps, sudden light alert, counting people etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Services Offered Camera Management Platform Investor Funding Elevator Pitch Deck to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide mentions various features offered by security platform to its users. Key features include cloud recording, snapshotting, object counting, movement heatmaps, sudden light alert, counting people etc.
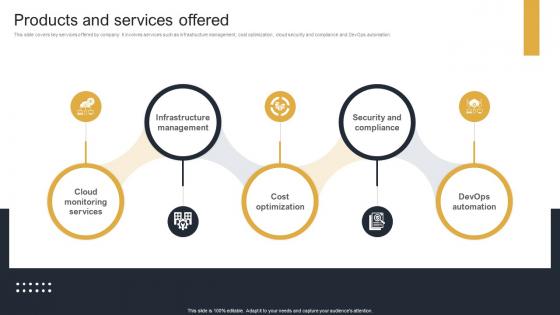
Products And Services Offered Cloud Monitoring And Management Pitch Deck
This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Cloud Monitoring And Management Pitch Deck to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation.
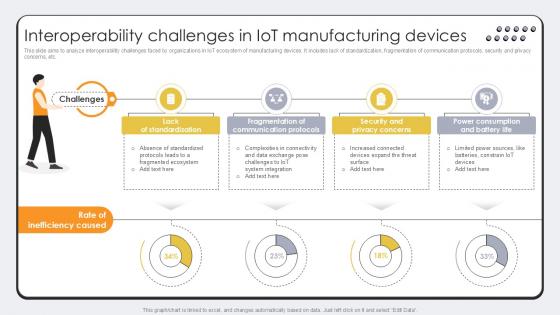
Interoperability Challenges In Revolutionizing Production IoT Ppt Sample
This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc. Slidegeeks has constructed Interoperability Challenges In Revolutionizing Production IoT Ppt Sample after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc.
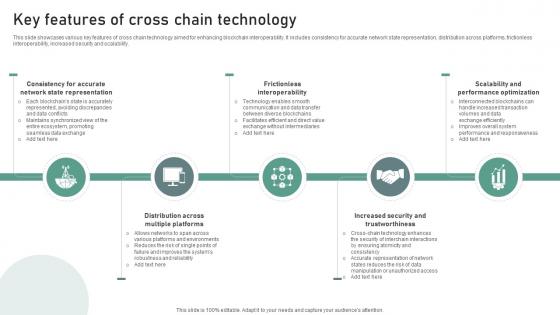
Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Slidegeeks has constructed Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.

Implement Effective Marketing Exploring Investment Opportunities Introduction Pdf
The following slide depicts various marketing techniques to ensure successful launch of security token offerings STO project. It includes elements such as public relations, social media, content, affiliate, email marketing, paid ads, etc. Are you searching for a Implement Effective Marketing Exploring Investment Opportunities Introduction Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implement Effective Marketing Exploring Investment Opportunities Introduction Pdf from Slidegeeks today. The following slide depicts various marketing techniques to ensure successful launch of security token offerings STO project. It includes elements such as public relations, social media, content, affiliate, email marketing, paid ads, etc.

Strategic Influencer Marketing Plan To Create Exploring Investment Opportunities Ideas Pdf
The following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc. Slidegeeks has constructed Strategic Influencer Marketing Plan To Create Exploring Investment Opportunities Ideas Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc.
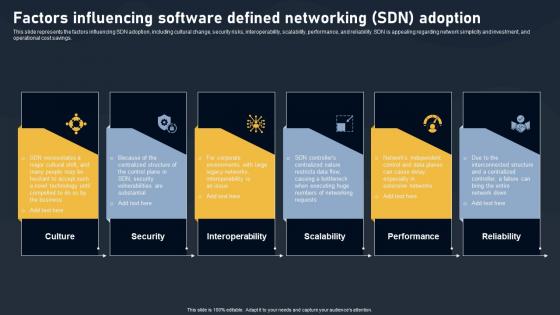
Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.Slidegeeks has constructed Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.
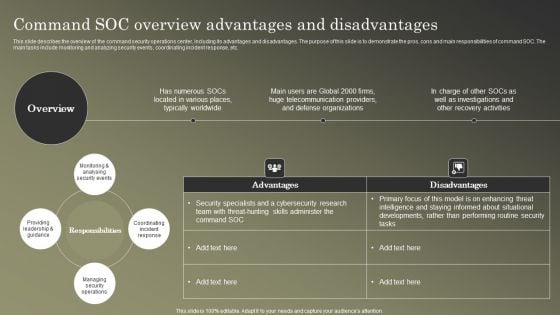
Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
This slide describes the overview of the command security operations center, including its advantages and disadvantages. The purpose of this slide is to demonstrate the pros, cons and main responsibilities of command SOC. The main tasks include monitoring and analyzing security events, coordinating incident response, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
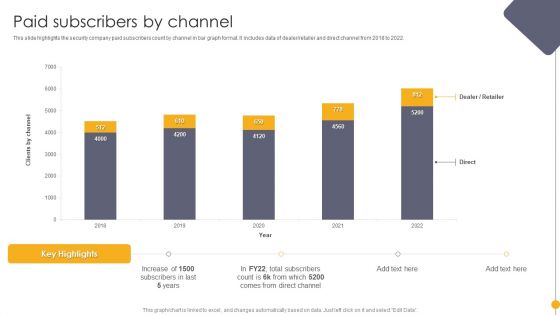
Portable Home Safety Systems Company Profile Paid Subscribers By Channel Demonstration PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer or retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Portable Home Safety Systems Company Profile Paid Subscribers By Channel Demonstration PDF bundle. Topics like Total Subscribers, Dealer, Retailer, Direct, 2018 To 2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Online Payment Techniques Challenges Faced By Business In Adopting Cashless
Mentioned slide showcases various challenges in implementation of cashless payment system in business. It includes challenges such as customer restrain, high processing fees, security issues, difficulty to adopt cashless technology and regular internet services. Explore a selection of the finest Online Payment Techniques Challenges Faced By Business In Adopting Cashless here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Online Payment Techniques Challenges Faced By Business In Adopting Cashless to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide showcases various challenges in implementation of cashless payment system in business. It includes challenges such as customer restrain, high processing fees, security issues, difficulty to adopt cashless technology and regular internet services.

Deploying Docker Container And Kubernetes Within Organization Table Of Contents Ppt PowerPoint Presentation Infographic Template Aids PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization table of contents ppt powerpoint presentation infographic template aids pdf. This is a six stage process. The stages in this process are introduction of kubernetes, kubernetes component, security measures in kubernetes, networking kubernetes, kubernetes development process, nodes kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
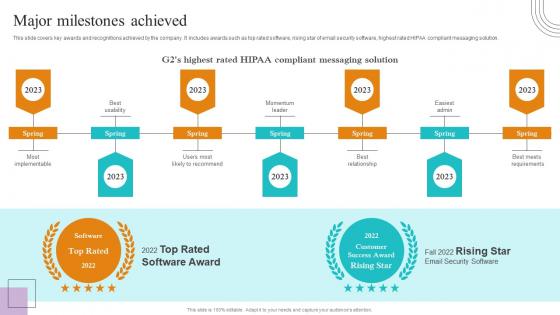
Major Milestones Achieved Paubox Capital Funding Pitch Deck Inspiration Pdf
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Milestones Achieved Paubox Capital Funding Pitch Deck Inspiration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.

Types Of Employee Incentives Offered By Company Elements Pdf
This slide showcase employee benefits provided by industry to motivate workers and provide job satisfaction to achieve work life goals. It include perks such as work, healthcare, financial security and lifestyle benefits. Showcasing this set of slides titled Types Of Employee Incentives Offered By Company Elements Pdf The topics addressed in these templates are Work Benefits, Healthcare Benefits, Lifestyle Benefits All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase employee benefits provided by industry to motivate workers and provide job satisfaction to achieve work life goals. It include perks such as work, healthcare, financial security and lifestyle benefits.

Key Business Challenges Of Fintech New Venture Infographics Pdf
This slide shows key business challenges of finetch startups that can be addresses and solved effectively through given solutions. It include challenge such as security issues and block chain technology integration etc. Showcasing this set of slides titled Key Business Challenges Of Fintech New Venture Infographics Pdf. The topics addressed in these templates are Challenges, Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows key business challenges of finetch startups that can be addresses and solved effectively through given solutions. It include challenge such as security issues and block chain technology integration etc.

Categories Of Issues And Risks In Cloud Computing PPT Slide SS
This slide presents issue categories and their solutions in cloud computing, helpful for businesses to take advantage of digital transformation. It includes challenges such as security issues, cost management, lack of resources and compliance. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Categories Of Issues And Risks In Cloud Computing PPT Slide SS to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide presents issue categories and their solutions in cloud computing, helpful for businesses to take advantage of digital transformation. It includes challenges such as security issues, cost management, lack of resources and compliance.
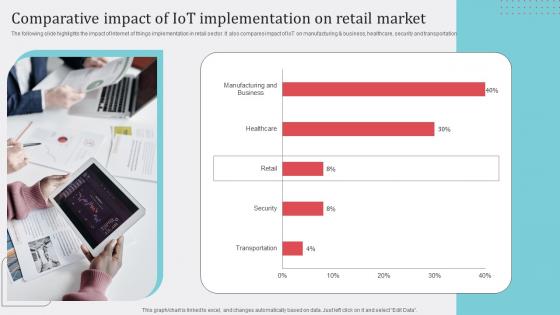
Comparative Impact IoT How Industrial IoT Is Changing Worldwide Microsoft Pdf
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation Boost your pitch with our creative Comparative Impact IoT How Industrial IoT Is Changing Worldwide Microsoft Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation

Exit Strategy Paubox Capital Funding Pitch Deck Clipart Pdf
This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering. Find highly impressive Exit Strategy Paubox Capital Funding Pitch Deck Clipart Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Exit Strategy Paubox Capital Funding Pitch Deck Clipart Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering.
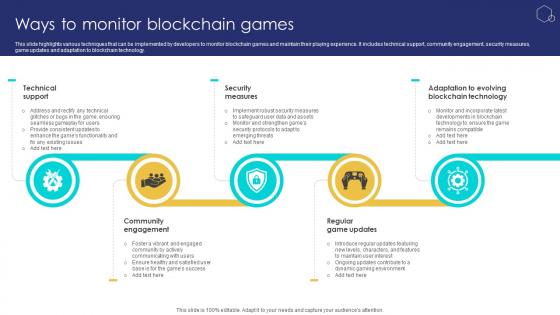
Unlocking The Potential Of Ways To Monitor Blockchain Games BCT SS V
This slide highlights various techniques that can be implemented by developers to monitor blockchain games and maintain their playing experience. It includes technical support, community engagement, security measures, game updates and adaptation to blockchain technology. Boost your pitch with our creative Unlocking The Potential Of Ways To Monitor Blockchain Games BCT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights various techniques that can be implemented by developers to monitor blockchain games and maintain their playing experience. It includes technical support, community engagement, security measures, game updates and adaptation to blockchain technology.

Zero Trust Network Access Implementation Challenges Mockup Pdf
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Get a simple yet stunning designed Zero Trust Network Access Implementation Challenges Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Network Access Implementation Challenges Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Monthly Restaurant Initial Funds Estimate Professional Pdf
The following slide exhibits startup budget for restaurant which include several cost such as security deposit, licence fee, renovation, rent, salary, marketing, etc. The slide also cover one time cost, recurring costs, low estimate, and high estimates. Showcasing this set of slides titled Monthly Restaurant Initial Funds Estimate Professional Pdf. The topics addressed in these templates are Expenses, Low Estimate, High Estimate. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide exhibits startup budget for restaurant which include several cost such as security deposit, licence fee, renovation, rent, salary, marketing, etc. The slide also cover one time cost, recurring costs, low estimate, and high estimates.
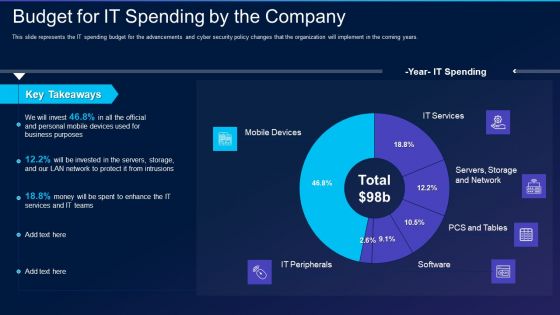
Cyber Exploitation IT Budget For IT Spending By The Company Professional PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years. Deliver an awe inspiring pitch with this creative cyber exploitation it budget for it spending by the company professional pdf bundle. Topics like mobile devices, it peripherals, it services, servers, storage and network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
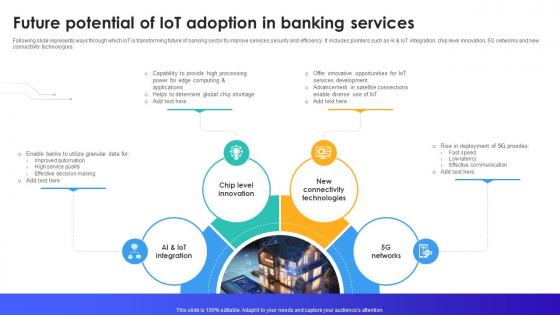
Future Potential Of IoT Adoption In Banking Services IoT In Banking For Digital Future IoT SS V
Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies. There are so many reasons you need a Future Potential Of IoT Adoption In Banking Services IoT In Banking For Digital Future IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies.
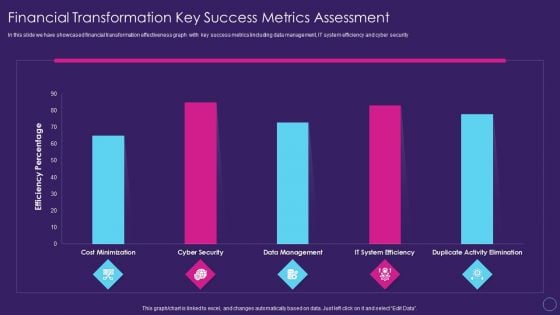
Financial Transformation Key Success Metrics Assessment Digital Transformation Toolkit Accounting Finance Introduction PDF
In this slide we have showcased financial transformation effectiveness graph with key success metrics lincluding data management, IT system efficiency and cyber security Deliver an awe inspiring pitch with this creative financial transformation key success metrics assessment digital transformation toolkit accounting finance introduction pdf bundle. Topics like financial transformation key success metrics assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
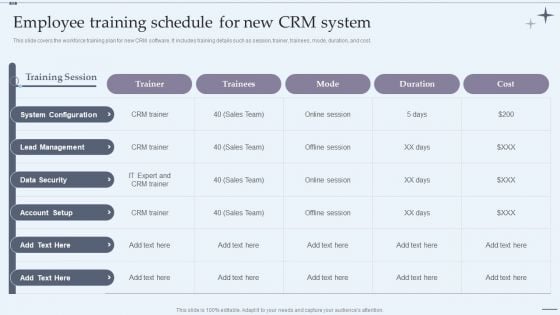
CRM System Implementation Stages Employee Training Schedule For New CRM System Mockup PDF
This slide covers the workforce training plan for new CRM software. It includes training details such as session, trainer, trainees, mode, duration, and cost. Deliver an awe inspiring pitch with this creative CRM System Implementation Stages Employee Training Schedule For New CRM System Mockup PDF bundle. Topics like System Configuration, Lead Management, Data Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































