Information Security
Case Competition Inflated Fuel Price In Logistics Firm Risks Involved And Mitigation Strategies Rules PDF
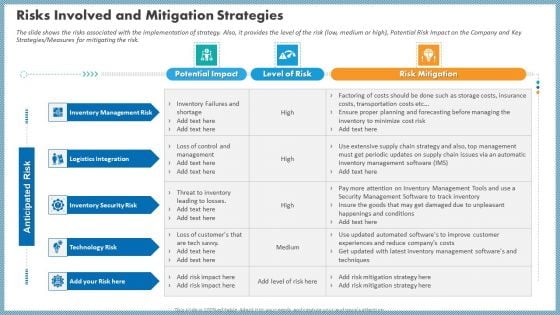
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies Measures for mitigating the risk. Presenting case competition inflated fuel price in logistics firm risks involved and mitigation strategies rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like management risk, logistics integration, inventory security risk, potential impact, level of risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
SIEM Traditional SIEM Deployment Model Ppt Model Shapes PDF
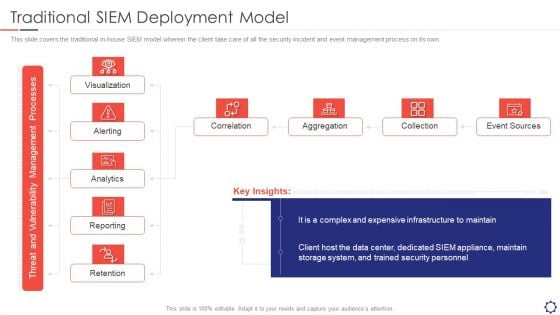
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Presenting siem traditional siem deployment model ppt model shapes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like visualization, alerting, analytics, reporting, retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Analysis Brochure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring analysis brochure pdf bundle. Topics like cybersecurity monitoring plan steps in detail review and risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Systems Graphics PDF
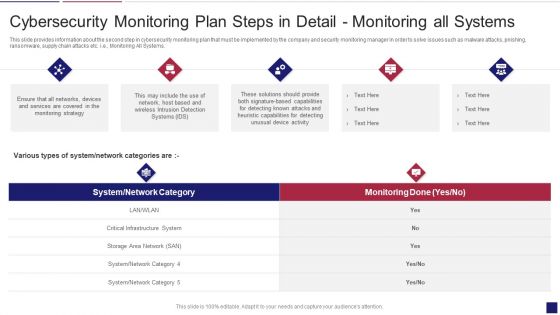
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring All Systems. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring systems graphics pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Timing Clipart PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring timing clipart pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Monitoring Plan Steps In Detail Providing Resilient And Synchronized Timing Background PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring plan steps in detail providing resilient and synchronized timing background pdf. Use them to share invaluable insights on monitoring and analysis, incident response, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ukraine Vs Russia Examining War Timeline Highlighting Major Events Occurred Cont Sample PDF
This slide provides information regarding Russia Ukraine war timeline highlighting major events occurred in FY2022 and FY2021 in terms of initiation of military training by Russian soldiers, security assistance to Ukraine by US, etc. . Deliver an awe inspiring pitch with this creative Ukraine Vs Russia Examining War Timeline Highlighting Major Events Occurred Cont Sample PDF bundle. Topics like US Tracked Unusual Russian, Russia Initiated Military Maneuvers, Controlled Crimea editable template. It is available for immediate download depending on the needs and requirements of the user.
Weighted Scoring Evaluation Model For Vendor Selection Themes PDF
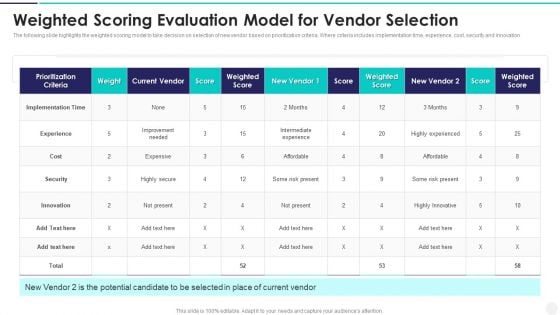
The following slide highlights the weighted scoring model to take decision on selection of new vendor based on prioritization criteria. Where criteria includes implementation time, experience, cost, security and innovation Pitch your topic with ease and precision using this Weighted Scoring Evaluation Model For Vendor Selection Themes PDF This layout presents information on Improvement Needed, Intermediate Experience, Highly Experienced It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
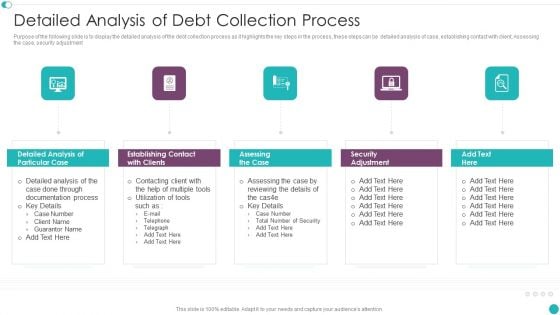
Credit Management And Recovery Policies Detailed Analysis Of Debt Collection Process Sample PDF
Purpose of the following slide is to display the detailed analysis of the debt collection process as it highlights the key steps in the process, these steps can be detailed analysis of case, establishing contact with client, Assessing the case, security adjustment. Presenting Credit Management And Recovery Policies Detailed Analysis Of Debt Collection Process Sample PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Detailed Analysis, Establishing Contact, Assessing Case. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

VID Managing End User Computing In The Company Infographics PDF
This slide represents how we will manage to end user computing and it includes to adopt centralized application deployment, preparation for changing job roles, know users and so on.Presenting VID Managing End User Computing In The Company Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Implications, Application Performance, Endeavor And Metrics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
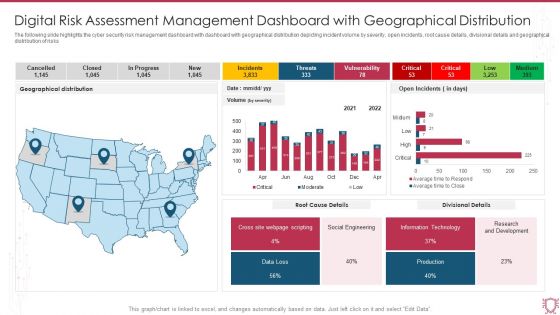
Digital Risk Assessment Management Dashboard With Geographical Distribution Clipart PDF
The following slide highlights the cyber security risk management dashboard with dashboard with geographical distribution depicting incident volume by severity, open incidents, root cause details, divisional details and geographical distribution of risks. Pitch your topic with ease and precision using this Digital Risk Assessment Management Dashboard With Geographical Distribution Clipart PDF. This layout presents information on Geographical Distribution, Root Cause Details, Divisional Details, Social Engineering. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Virtualization Managing End User Computing In The Company Topics PDF
This slide represents how we will manage to end user computing and it includes to adopt centralized application deployment, preparation for changing job roles, know users and so on.Presenting Computer Virtualization Managing End User Computing In The Company Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Security Implications, Storage Consumption, Experience Server. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
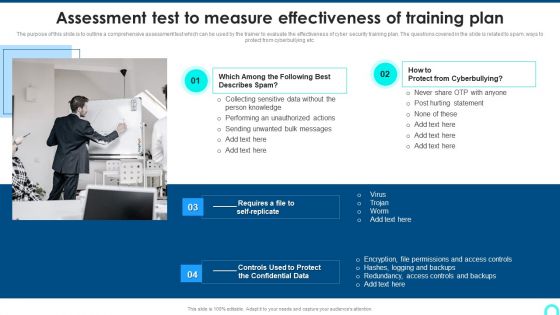
Assessment Test To Measure Effectiveness Of Training Plan Professional PDF
purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Presenting Assessment Test To Measure Effectiveness Of Training Plan Professional PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Collecting Sensitive, Performing Unauthorized, Hurting Statement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

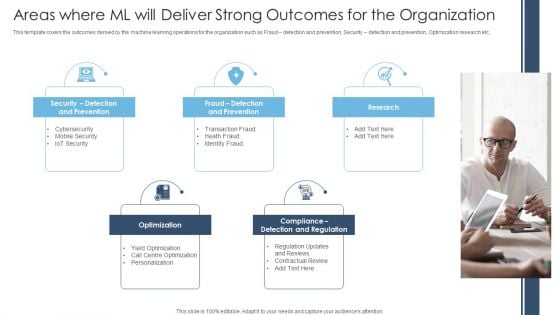
Optimize Service Delivery With Enhanced Areas Where ML Will Deliver Strong Outcomes For The Organization Ideas PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc.Presenting Optimize Service Delivery With Enhanced Areas Where ML Will Deliver Strong Outcomes For The Organization Ideas PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Detection And Prevention, Optimization, Centre Optimization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
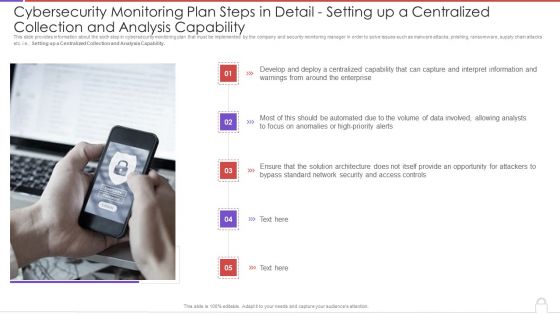
Cybersecurity Monitoring Plan Steps In Detail Setting Up A Centralized Collection And Elements PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Setting up a Centralized Collection and Analysis Capability. This is a cybersecurity monitoring plan steps in detail setting up a centralized collection and elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interpret information, high priority alerts, analysts, access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Program Presentation Crisis Management Team Structure Manager Ppt Gallery Visual Aids PDF
The CMT generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting program presentation crisis management team structure manager ppt gallery visual aids pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security manager, crisis management, HR advisor, crisis management team structure. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
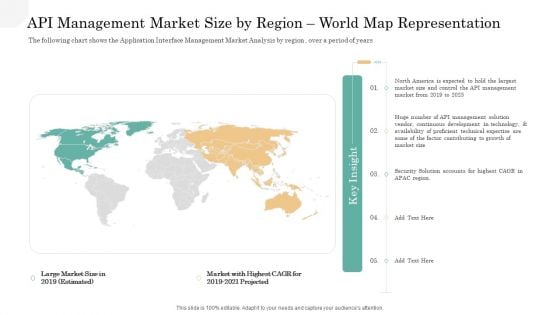
API Management Market API Management Market Size By Region World Map Representation Guidelines PDF
The following chart shows the Application Interface Management Market Analysis by region , over a period of years. Presenting api management market api management market size by region world map representation guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, technical, security solution accounts, market with highest cagr for 2019 2021 projected. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
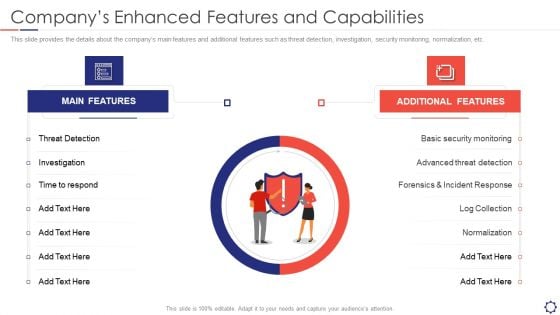
SIEM Companys Enhanced Features And Capabilities Ppt Inspiration Layout Ideas PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Presenting siem companys enhanced features and capabilities ppt inspiration layout ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like main features, additional features. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Devops Engineer Capabilities Top Skills Essential For Devops Engineer Ppt Model Design Ideas PDF
This slide provides the glimpse about the top skills which a DevOps engineer must have such as communication and collaboration, soft skills, security skills, automation skills, etc. Presenting devops engineer capabilities top skills essential for devops engineer ppt model design ideas pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like top skills essential for devops engineer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
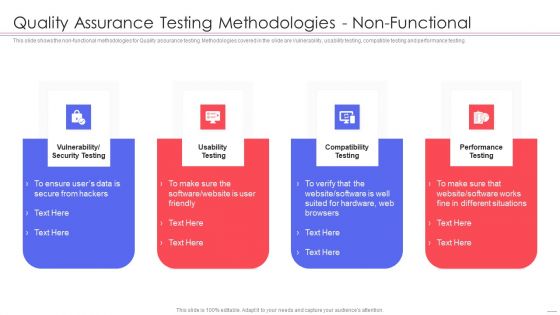
Agile QA Procedure Quality Assurance Testing Methodologies Non Functional Download PDF
This slide shows the non-functional methodologies for Quality assurance testing. Methodologies covered in the slide are Vulnerability, usability testing, compatible testing and performance testing. Presenting agile qa procedure quality assurance testing methodologies non functional download pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like vulnerability security testing, compatibility testing, performance testing. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Recognition Automation Companys Enhanced Features And Capabilities Ppt Gallery Model PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Presenting risk recognition automation companys enhanced features and capabilities ppt gallery model pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like main features, additional features. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
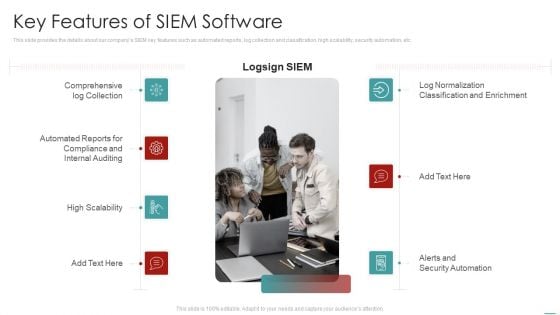
Risk Recognition Automation Key Features Of Siem Software Ppt Visuals PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Presenting risk recognition automation key features of siem software ppt visuals pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like key features of siem software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
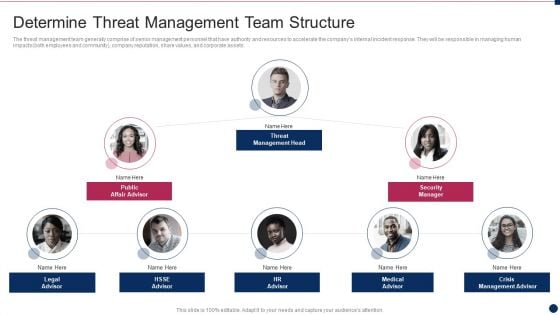
Threat Management At Workplace Determine Threat Management Team Structure Designs Pdf
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting threat management at workplace determine threat management team structure designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like threat management head, public affair advisor, security manager. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Quality Assurance Testing Methodologies Non Functional Icons PDF
This slide shows the non functional methodologies for Quality assurance testing. Methodologies covered in the slide are Vulnerability, usability testing, compatible testing and performance testing. Presenting quality assurance testing methodologies non functional icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like vulnerability security testing, usability testing, performance testing. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Electronic Playbook Digital Transformation Trends We Can Adopt Microsoft PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyperautomation, cyber security tools, usage of AI etc.Presenting electronic playbook digital transformation trends we can adopt microsoft pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like digital transformation trends we can adopt In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
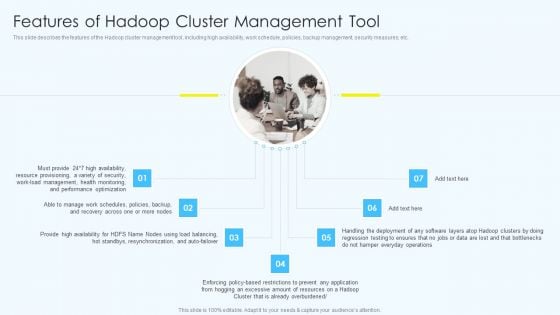
Apache Hadoop Software Deployment Features Of Hadoop Cluster Management Tool Elements PDF
This slide describes the features of the Hadoop cluster management tool, including high availability, work schedule, policies, backup management, security measures, etc.Presenting Apache Hadoop Software Deployment Features Of Hadoop Cluster Management Tool Elements PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Resource Provisioning, Health Monitoring, Performance Optimization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Areas Where ML Will Deliver Strong Outcomes For The Organization Icons PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc.Presenting Areas Where ML Will Deliver Strong Outcomes For The Organization Icons PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Detection And Prevention, Optimization, Detection And Regulation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Achieving Proactive From Reactive Areas Where Ml Will Deliver Strong Outcomes For Infographics PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc. Presenting Achieving Proactive From Reactive Areas Where Ml Will Deliver Strong Outcomes For Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Optimization, Research, Detection And Prevention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
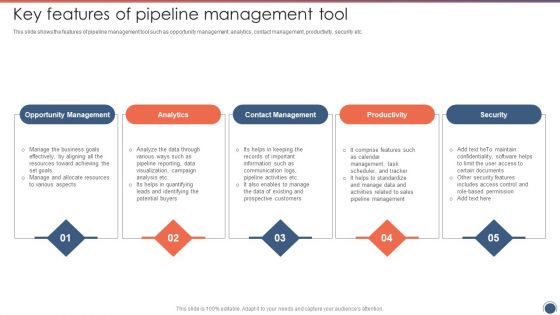
Key Features Of Pipeline Management Tool Sales Funnel Management Strategies To Increase Sales Microsoft PDF
This slide shows the features of pipeline management tool such as opportunity management, analytics, contact management, productivity, security etc. Presenting Key Features Of Pipeline Management Tool Sales Funnel Management Strategies To Increase Sales Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Opportunity Management, Contact Management, Productivity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
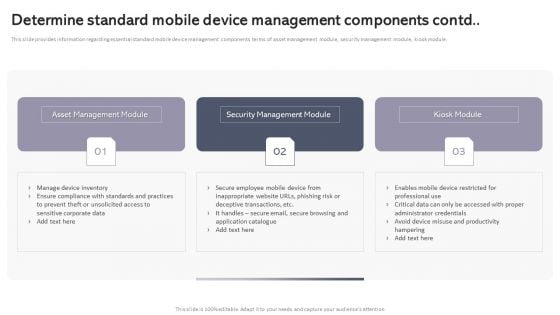
Workplace Portable Device Monitoring And Administration Determine Standard Mobile Device Management Components Contd Mockup PDF
This slide provides information regarding essential standard mobile device management components terms of asset management module, security management module, kiosk module. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Workplace Portable Device Monitoring And Administration Determine Standard Mobile Device Management Components Contd Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
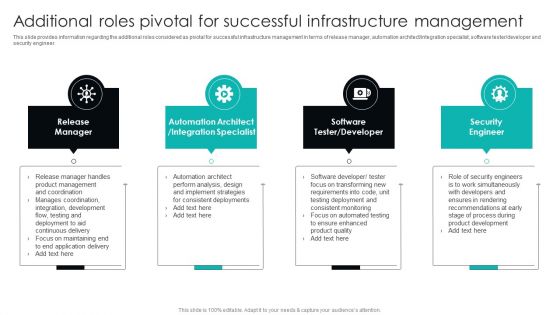
Additional Roles Pivotal For Successful Infrastructure Management Summary PDF
This slide provides information regarding the additional roles considered as pivotal for successful infrastructure management in terms of release manager, automation architect integration specialist, software tester developer and security engineer. Find a pre designed and impeccable Additional Roles Pivotal For Successful Infrastructure Management Summary PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
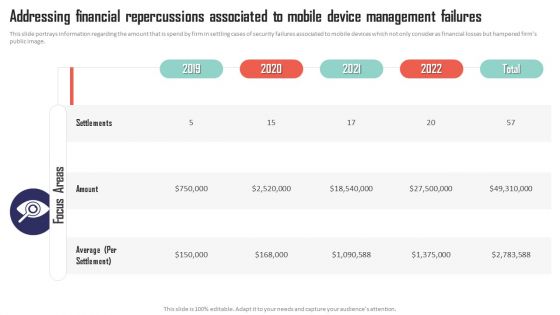
Addressing Financial Repercussions Associated To Mobile Device Management Failures Summary PDF
This slide portrays information regarding the amount that is spend by firm in settling cases of security failures associated to mobile devices which not only consider as financial losses but hampered firms public image. There are so many reasons you need a Addressing Financial Repercussions Associated To Mobile Device Management Failures Summary PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
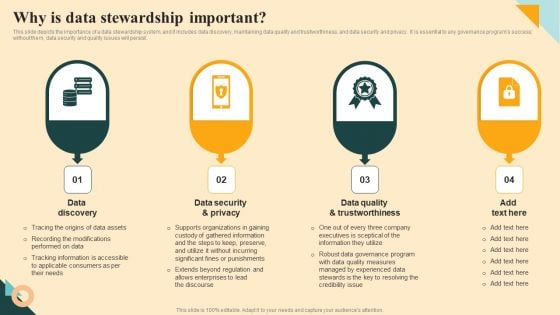
Why Is Data Stewardship Important Sample PDF
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. Slidegeeks has constructed Why Is Data Stewardship Important Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
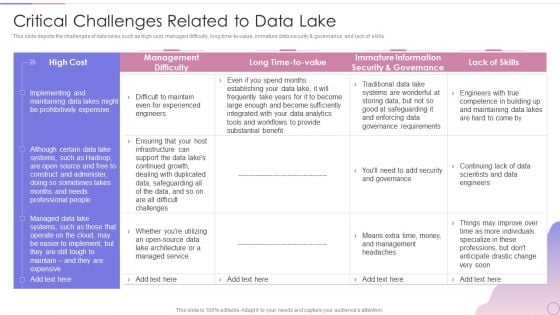
Data Lake Architecture Future Of Data Analysis Critical Challenges Related To Data Lake Mockup PDF
This slide depicts the challenges of data lakes such as high cost, managed difficulty, long time-to-value, immature data security governance, and lack of skills.Deliver an awe inspiring pitch with this creative Data Lake Architecture Future Of Data Analysis Critical Challenges Related To Data Lake Mockup PDF bundle. Topics like Governance Requirements, Maintaining Data, Construct And Administer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
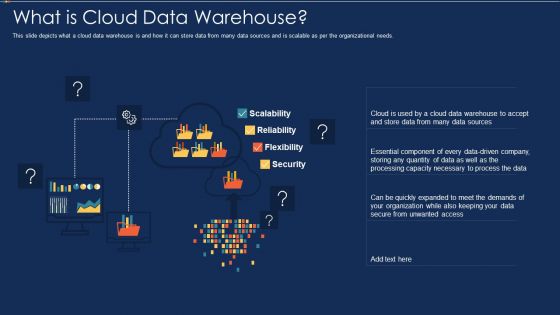
Data Warehousing IT What Is Cloud Data Warehouse Ppt Styles Background Designs PDF
This slide depicts what a cloud data warehouse is and how it can store data from many data sources and is scalable as per the organizational needs. Deliver and pitch your topic in the best possible manner with this data warehousing it what is cloud data warehouse ppt styles background designs pdf. Use them to share invaluable insights on scalability, reliability, flexibility, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
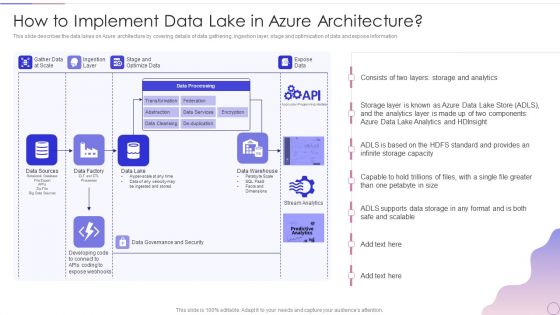
Data Lake Architecture Future Of Data Analysis How To Implement Data Lake In Azure Architecture Slides PDF
This slide describes the data lakes on Azure architecture by covering details of data gathering, ingestion layer, stage and optimization of data and expose information.Deliver an awe inspiring pitch with this creative Data Lake Architecture Future Of Data Analysis How To Implement Data Lake In Azure Architecture Slides PDF bundle. Topics like Data Processing, Storage And Analytics, Governance And Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Services Market Data Pricing Analytics Ppt PowerPoint Presentation Slides Template Cpb Pdf
Presenting this set of slides with name data services market data pricing analytics ppt powerpoint presentation slides template cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like data security financial services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V
This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals This Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals

CASB 2 0 IT Primary Types Of Reverse Proxy Server Deployment
This slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations. Present like a pro with CASB 2 0 IT Primary Types Of Reverse Proxy Server Deployment. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations.
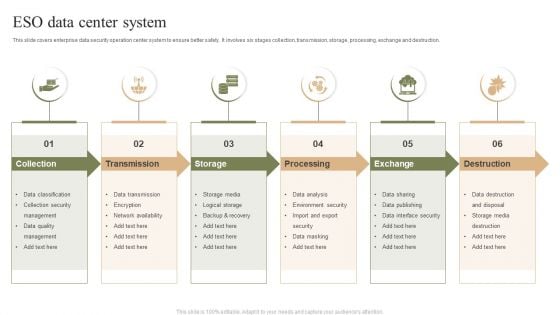
ESO Data Center System Ppt PowerPoint Presentation Gallery Grid PDF
This slide covers enterprise data security operation center system to ensure better safety. It involves six stages collection, transmission, storage, processing, exchange and destruction. Presenting ESO Data Center System Ppt PowerPoint Presentation Gallery Grid PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Collection, Transmission, Storage, Processing, Exchange. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Migration Project Risks With Mitigation Strategies Formats PDF
This slide showcases risks in implementing data migration projects that can cause data loss and security breachment. Its also outlines solutions to mitigate the hindrances and impact after the implementation. Showcasing this set of slides titled Data Migration Project Risks With Mitigation Strategies Formats PDF. The topics addressed in these templates are Mitigation Strategies, Impact, Risks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
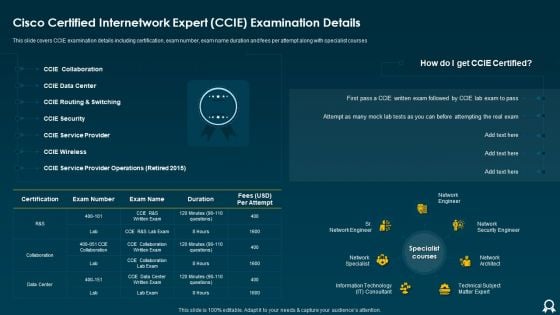
IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF
This slide covers CCIE examination details including certification, exam number, exam name duration and fees per attempt along with specialist courses. Deliver and pitch your topic in the best possible manner with this IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF. Use them to share invaluable insights on Data Center, Service Provider, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Professional Data Certification Program Comptia A Certification Courses Details Professional PDF
This slide covers certification details about CompTIA A such as who should take these certifications, courses offered in this certification etc. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Comptia A Certification Courses Details Professional PDF. Use them to share invaluable insights on Network Administrator, Systems Administrator, Security Administrator and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
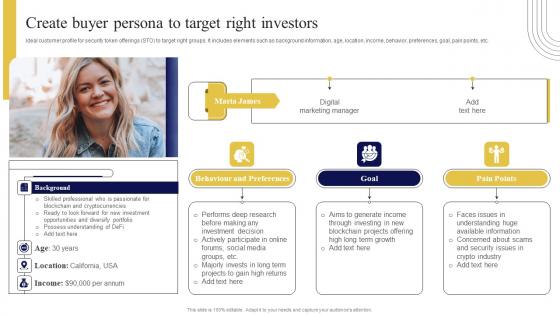
Create Buyer Persona To Target Right Exploring Investment Opportunities Mockup Pdf
Ideal customer profile for security token offerings STO to target right groups. It includes elements such as background information, age, location, income, behavior, preferences, goal, pain points, etc. Find highly impressive Create Buyer Persona To Target Right Exploring Investment Opportunities Mockup Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Create Buyer Persona To Target Right Exploring Investment Opportunities Mockup Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Ideal customer profile for security token offerings STO to target right groups. It includes elements such as background information, age, location, income, behavior, preferences, goal, pain points, etc.

R78 Solutions To Challenges Faced In Implementing Product Analytics Implementation Data Analytics V
This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solutions To Challenges Faced In R78 Solutions To Challenges Faced In Implementing Product Analytics Implementation Data Analytics V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality.

Companys Data Safety Recognition Organization Impact Metrics Behaviours Background PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people.Deliver and pitch your topic in the best possible manner with this companys data safety recognition organization impact metrics behaviours background pdf. Use them to share invaluable insights on organization impact metrics behaviours and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Breach Prevention Recognition Organization Impact Metrics Behaviours Pictures PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people.Deliver an awe-inspiring pitch with this creative data breach prevention recognition organization impact metrics behaviours pictures pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CASB 2 0 IT 30 60 90 Days Plan To Deploy CASB Model
This slide represents the 30-0-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days. Boost your pitch with our creative CASB 2 0 IT 30 60 90 Days Plan To Deploy CASB Model. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the 30-0-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days.

Need Of Implementing Ble Technique For Asset RFID Solutions For Asset Traceability Clipart Pdf
This slide covers key benefits of implementing Bluetooth low energy method in asset tracking and management. It involves advantages such as high return on investment, enhanced security and high broadcast capacity. The Need Of Implementing Ble Technique For Asset RFID Solutions For Asset Traceability Clipart Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers key benefits of implementing Bluetooth low energy method in asset tracking and management. It involves advantages such as high return on investment, enhanced security and high broadcast capacity.
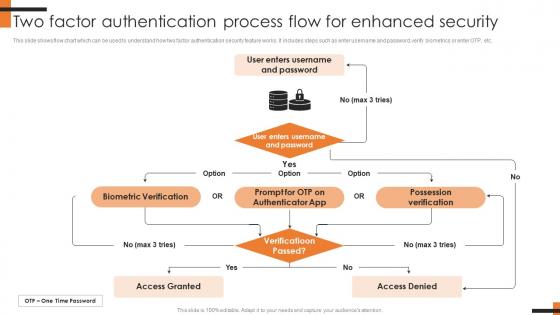
Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. The Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
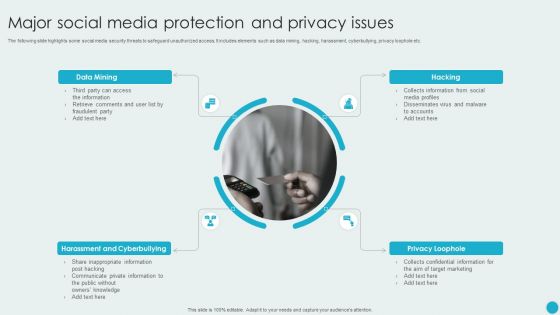
Major Social Media Protection And Privacy Issues Template PDF
The following slide highlights some social media security threats to safeguard unauthorized access. It includes elements such as data mining, hacking, harassment, cyberbullying, privacy loophole etc. Presenting Major Social Media Protection And Privacy Issues Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Mining, Harassment And Cyberbullying, Privacy Loophole. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

CASB 2 0 IT Reverse Proxy CASB Deployment Model
This slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit CASB 2 0 IT Reverse Proxy CASB Deployment Model and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers.
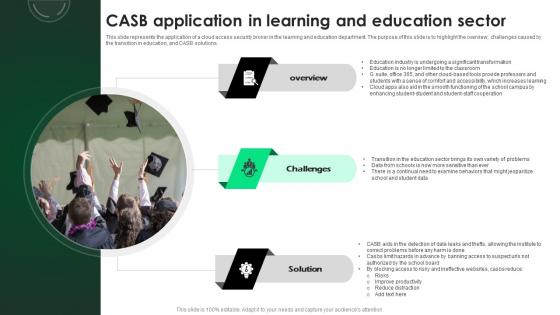
CASB 2 0 IT CASB Application In Learning And Education Sector
This slide represents the application of a cloud access security broker in the learning and education department. The purpose of this slide is to highlight the overview, challenges caused by the transition in education, and CASB solutions. Present like a pro with CASB 2 0 IT CASB Application In Learning And Education Sector. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the application of a cloud access security broker in the learning and education department. The purpose of this slide is to highlight the overview, challenges caused by the transition in education, and CASB solutions.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
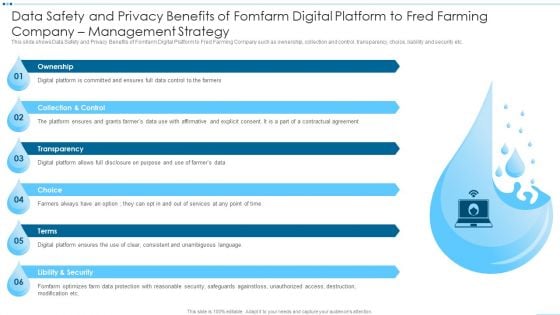
Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF
This slide shows Data Safety and Privacy Benefits of Fomfarm Digital Platform to Fred Farming Company such as ownership, collection and control, transparency, choice, liability and security etc. Deliver an awe inspiring pitch with this creative Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF bundle. Topics like Ownership, Collection And Control, Transparency, Choice can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
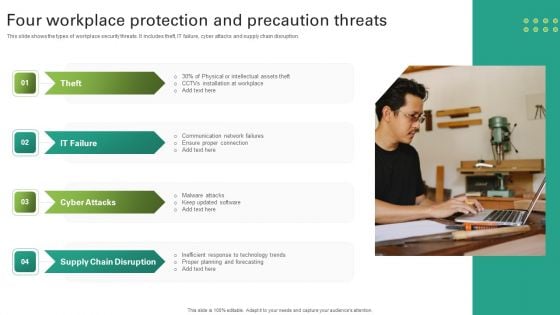
Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
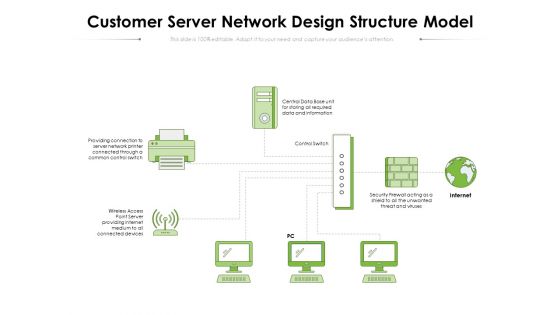
Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
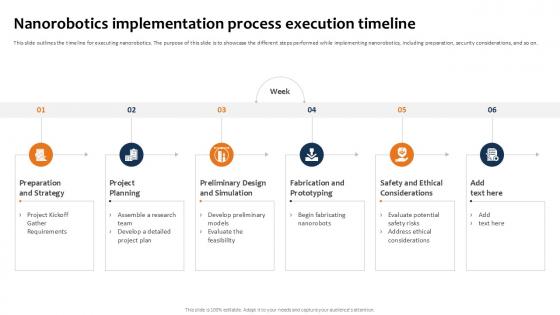
Nanorobotics Implementation Building The Future Of Robotic Ppt Slide
This slide outlines the timeline for executing nanorobotics. The purpose of this slide is to showcase the different steps performed while implementing nanorobotics, including preparation, security considerations, and so on.The Nanorobotics Implementation Building The Future Of Robotic Ppt Slide is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlines the timeline for executing nanorobotics. The purpose of this slide is to showcase the different steps performed while implementing nanorobotics, including preparation, security considerations, and so on.


 Continue with Email
Continue with Email

 Home
Home


































