Information Security
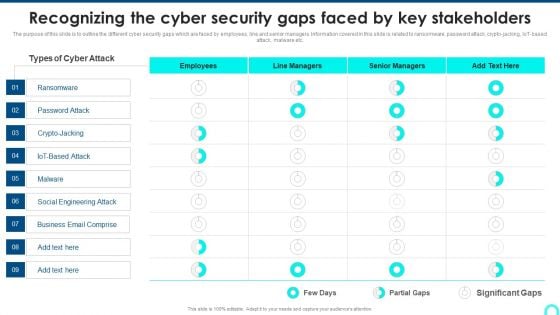
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Deliver and pitch your topic in the best possible manner with this Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF. Use them to share invaluable insights on Ransomware, Engineering Attack, Email Comprise and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Saas Cloud Security Analysis With KPI Dashboard Ppt PowerPoint Presentation Icon Slides PDF
The following slide highlights the assessment of Software as a security to meet safety standards. It includes key elements such as critical incidents, risk analysis, number of open tasks etc. Pitch your topic with ease and precision using this Saas Cloud Security Analysis With KPI Dashboard Ppt PowerPoint Presentation Icon Slides PDF. This layout presents information on Quarterly Incident Severity, Incident Risk Analysis, Critical Incidents. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Proposal For Enterprise Security System About Us One Pager Sample Example Document
Purpose of the following slide is to show the information about the origination as it displays the Company introduction, company background etc. Presenting you an exemplary Proposal For Enterprise Security System About Us One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System About Us One Pager Sample Example Document brilliant piece now.

About Us For Home Security Equipment Installation Proposal One Pager Sample Example Document
Purpose of the following slide is to show the information about the origination as it displays the Company introduction, company background etc. Presenting you an exemplary About Us For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this About Us For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Cyber Security Project Evaluation Plan To Safeguard Business Operation Designs PDF
This slide signifies the cyber security project evaluation plan for safeguarding organisation operations. It covers information regarding to the stages like initiation, planning, execution, implement and monitor. Persuade your audience using this Cyber Security Project Evaluation Plan To Safeguard Business Operation Designs PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Planning, Execution, Implement, Initiation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
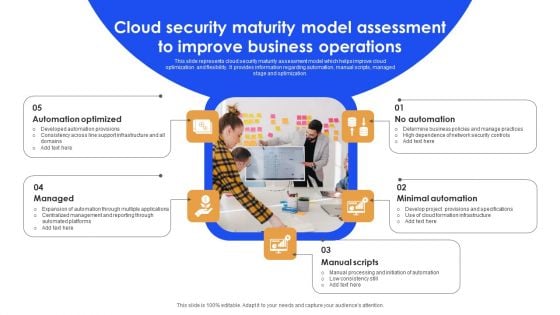
Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF
This slide represents cloud security maturity assessment model which helps improve cloud optimization and flexibility. It provides information regarding automation, manual scripts, managed stage and optimization. Persuade your audience using this Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Automation Optimized, Minimal Automation, Manual Scripts. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
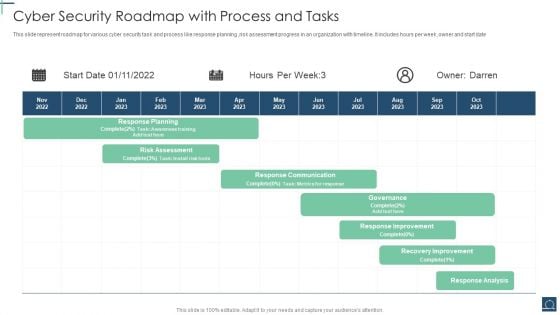
Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF
This slide represent roadmap for various cyber security task and process like response planning ,risk assessment progress in an organization with timeline. It includes hours per week ,owner and start date. Pitch your topic with ease and precision using this Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF. This layout presents information on Response Planning, Risk Assessment, Response Communication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
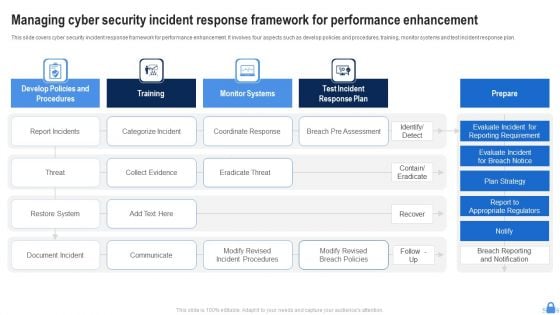
Managing Cyber Security Incident Response Framework For Performance Enhancement Formats PDF
This slide covers cyber security incident response framework for performance enhancement. It involves four aspects such as develop policies and procedures, training, monitor systems and test incident response plan. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response Framework For Performance Enhancement Formats PDF. This layout presents information on Report Incidents, Threat, Restore System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Steps Involved In Mobile Device Management Deployment Business Mobile Device Security Topics PDF
This slide provides information regarding key steps involved in deploying mobile device management system. Get a simple yet stunning designed Key Steps Involved In Mobile Device Management Deployment Business Mobile Device Security Topics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Key Steps Involved In Mobile Device Management Deployment Business Mobile Device Security Topics PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
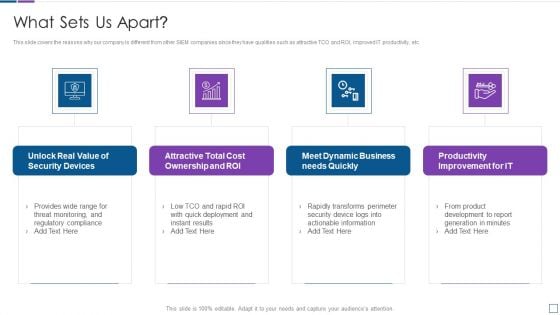
Real Time Assessment Of Security Threats What Sets Us Apart Microsoft PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting real time assessment of security threats what sets us apart microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, cost ownership and roi, dynamic business, productivity improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Existing Channel Development Strategy Infographics PDF
This slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Presenting Smart Home Security Solutions Company Profile Existing Channel Development Strategy Infographics PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Direct To Home, Incentive Scheme Hubs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
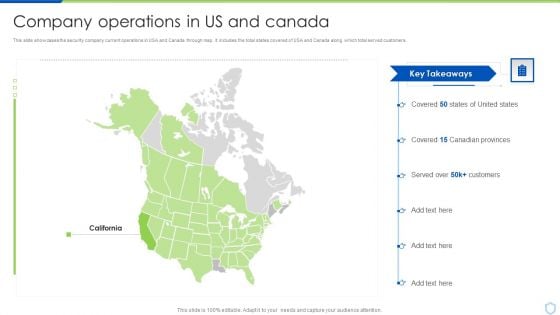
Security And Surveillance Company Profile Company Operations In US And Canada Demonstration PDF
This slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers.Presenting Security And Surveillance Company Profile Company Operations In US And Canada Demonstration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Canadian Provinces, Covered, Key Takeaways. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
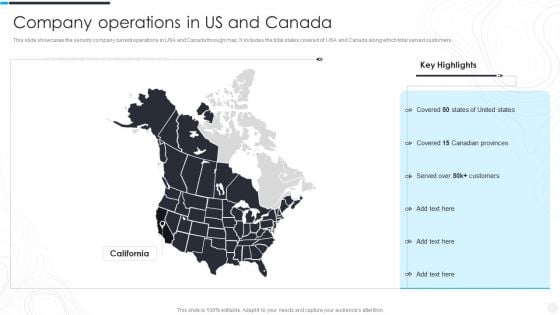
Security Camera System Company Profile Company Operations In US And Canada Mockup PDF
This slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers.Presenting Security Camera System Company Profile Company Operations In US And Canada Mockup PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Key Highlights, Customers, Canadian Provinces. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
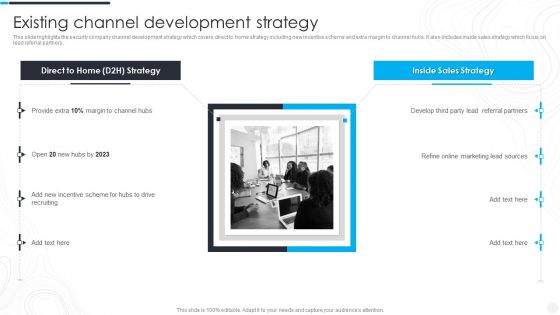
Security Camera System Company Profile Existing Channel Development Strategy Designs PDF
This slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Presenting Security Camera System Company Profile Existing Channel Development Strategy Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Referral Partners, Incentive Scheme, Marketing Lead. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF

Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.
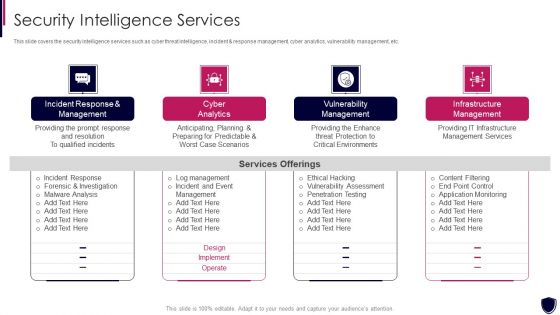
Enhancing Cyber Safety With Vulnerability Administration Security Intelligence Services Portrait PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting enhancing cyber safety with vulnerability administration security intelligence services portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
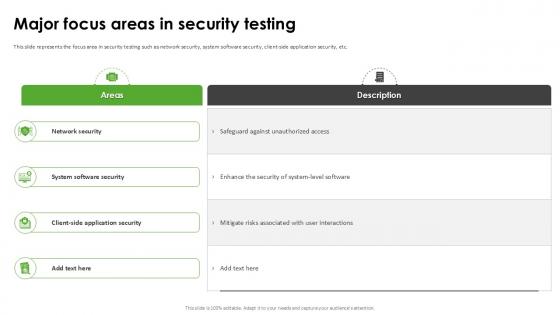
Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example
This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc.
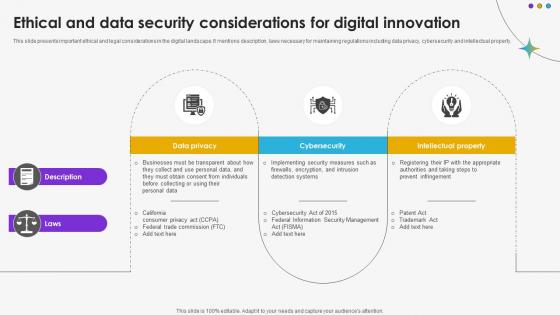
Ethical And Data Security Considerations For Digital Innovation DT SS V
This slide presents important ethical and legal considerations in the digital landscape. It mentions description, laws necessary for maintaining regulations including data privacy, cybersecurity and intellectual property.Find a pre-designed and impeccable Ethical And Data Security Considerations For Digital Innovation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents important ethical and legal considerations in the digital landscape. It mentions description, laws necessary for maintaining regulations including data privacy, cybersecurity and intellectual property.
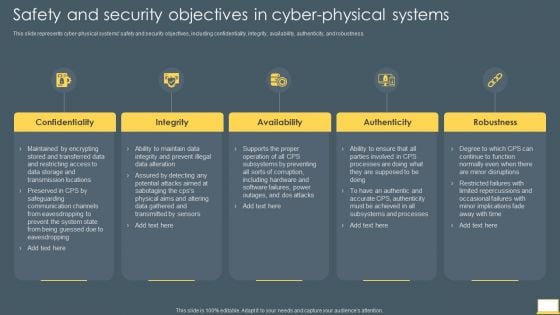
Cyber Intelligent Computing System Safety And Security Objectives In Cyber Physical Systems Ideas PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Presenting Cyber Intelligent Computing System Safety And Security Objectives In Cyber Physical Systems Ideas PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Availability, Authenticity, Robustness, Integrity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
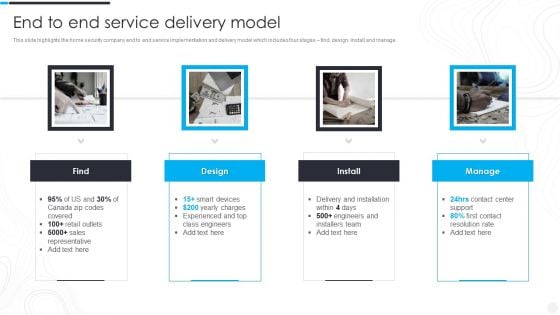
Security Camera System Company Profile End To End Service Delivery Model Clipart PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage.Presenting Security Camera System Company Profile End To End Service Delivery Model Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Charges Experienced, Sales Representative, Delivery And Installation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
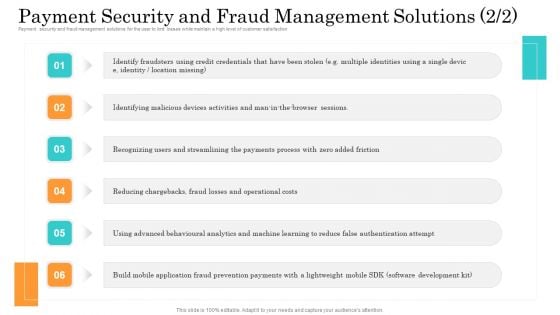
Online Payment Service Payment Security And Fraud Management Solutions Portrait PDF
Payment security and fraud management solutions for the user to limit losses while maintain a high level of customer satisfaction. Presenting online payment service payment security and fraud management solutions portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like operational costs, behavioural analytics, mobile application. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

SIEM Services Benchmarking With Security Operations Maturity Model Ppt File Grid PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting siem services benchmarking with security operations maturity model ppt file grid pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like decrease response time, quickly identify threats, improve visibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
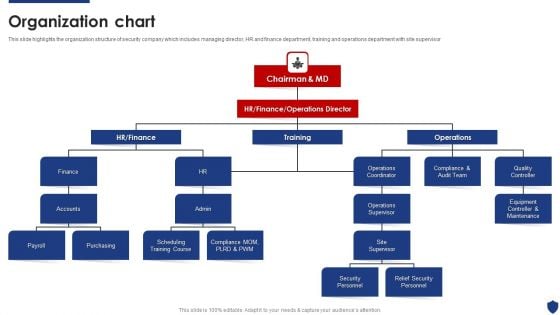
Security Officer Service Company Profile Organization Chart Ppt PowerPoint Presentation File Designs Download PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. Presenting Security Officer Service Company Profile Organization Chart Ppt PowerPoint Presentation File Designs Download PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Finance, Accounts, Payroll, Purchasing, Operations Supervisor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
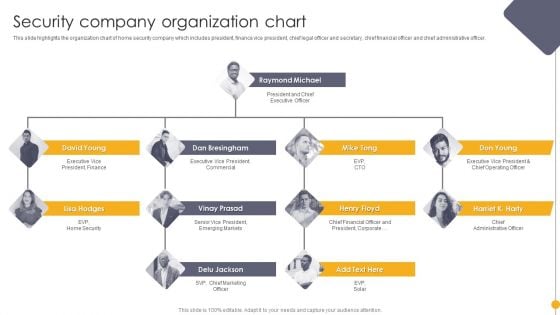
Portable Home Safety Systems Company Profile Security Company Organization Chart Demonstration PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. Presenting Portable Home Safety Systems Company Profile Security Company Organization Chart Demonstration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Chief Financial, Executive Vice President, Chief Operating Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Mission Vision And Core Values Professional PDF
This slide highlights the security company long term and short term objectives which includes trust, collaboration, service, and innovation as base of core values. Presenting Manpower Corporate Security Business Profile Mission Vision And Core Values Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Mission, Vision, Core Values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
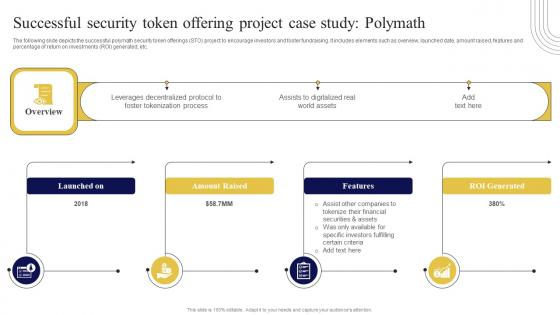
Successful Security Token Offering Project Case Exploring Investment Opportunities Summary Pdf
The following slide depicts the successful polymath security token offerings STO project to encourage investors and foster fundraising. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. This Successful Security Token Offering Project Case Exploring Investment Opportunities Summary Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide depicts the successful polymath security token offerings STO project to encourage investors and foster fundraising. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc.
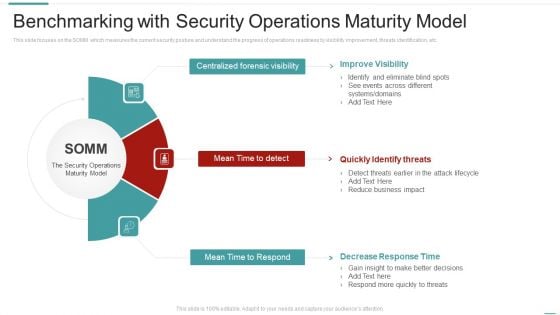
Risk Recognition Automation Benchmarking With Security Operations Maturity Model Ppt Pictures Infographic Template PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting risk recognition automation benchmarking with security operations maturity model ppt pictures infographic template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improve visibility, quickly identify threats, decrease response time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Staff Recruiting Criteria And Training Centre Designs PDF
This slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Presenting Security Agency Business Profile Staff Recruiting Criteria And Training Centre Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Selection Criteria, Authorized Training Centre. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mobile Device Management For Android Platform Business Mobile Device Security Management Graphics PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Slidegeeks is here to make your presentations a breeze with Mobile Device Management For Android Platform Business Mobile Device Security Management Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
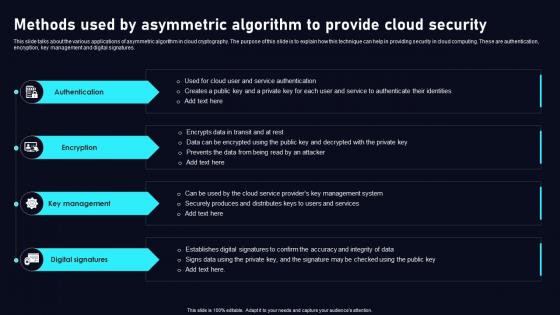
Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
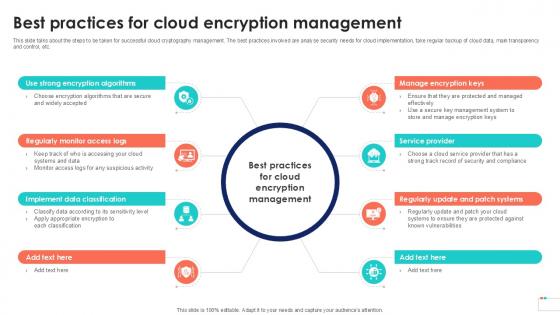
Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template today and make your presentation stand out from the rest This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.
Icons Slide For Global Data Security Industry Report IR SS V
Introducing our well designed Icons Slide For Global Data Security Industry Report IR SS V set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
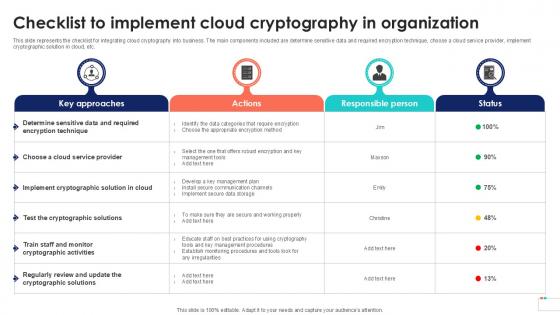
Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.

Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.

Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising sixteen slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V
The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa. Explore a selection of the finest Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa.

Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf
Are you searching for a Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf from Slidegeeks today. Our Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
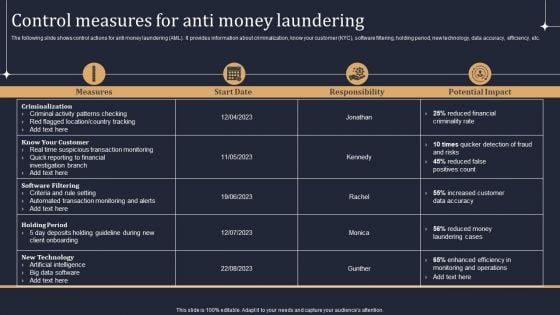
KYC Transaction Monitoring System Business Security Control Measures For Anti Money Laundering Ideas PDF
The following slide shows control actions for anti money laundering AML. It provides information about criminalization, know your customer KYC, software filtering, holding period, new technology, data accuracy, efficiency, etc. The following slide shows control actions for anti money laundering AML. It provides information about criminalization, know your customer KYC, software filtering, holding period, new technology, data accuracy, efficiency, etc. This modern and well arranged KYC Transaction Monitoring System Business Security Control Measures For Anti Money Laundering Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
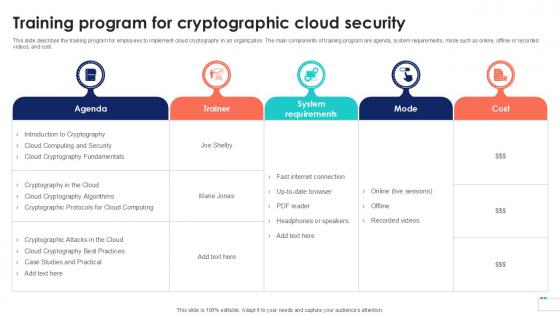
Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.
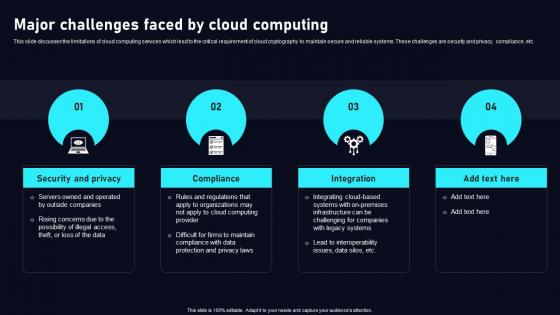
Major Challenges Faced By Cloud Data Security Using Cryptography Inspiration Pdf
This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc. QThere are so many reasons you need a Major Challenges Faced By Cloud Data Security Using Cryptography Inspiration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Comprehensive Guide For Website Development Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup This modern and well-arranged Comprehensive Guide For Website Development Best Practices For Web Security Management provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup
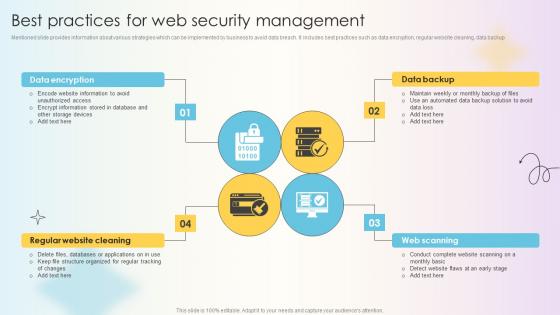
Managing Technical And Non Technical Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup Present like a pro with Managing Technical And Non Technical Best Practices For Web Security Management. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Take your projects to the next level with our ultimate collection of Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc.
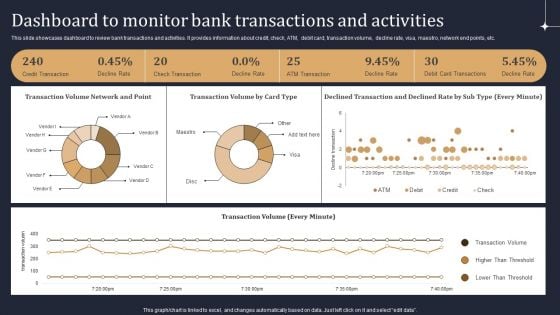
KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF
This slide showcases dashboard to review bank transactions and activities. It provides information about credit, check, ATM, debit card, transaction volume, decline rate, visa, maestro, network end points, etc. This KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Complete Beginners Guide Cold Wallets For Enhancing Bitcoin Security Fin SS V
This slide shows information regarding cold wallets which can be used by Bitcoin holders. It also includes types of cold crypto wallets which are hardware wallets and paper wallets. Slidegeeks is here to make your presentations a breeze with Complete Beginners Guide Cold Wallets For Enhancing Bitcoin Security Fin SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows information regarding cold wallets which can be used by Bitcoin holders. It also includes types of cold crypto wallets which are hardware wallets and paper wallets.
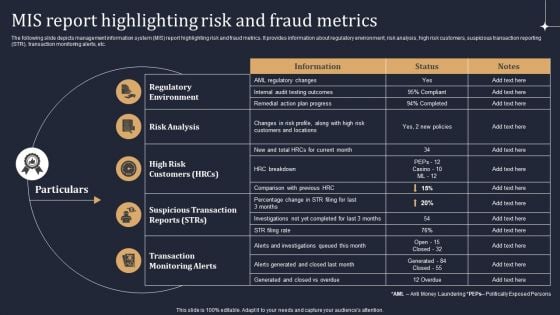
KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF
The following slide depicts management information system MIS report highlighting risk and fraud metrics. It provides information about regulatory environment, risk analysis, high risk customers, suspicious transaction reporting STR, transaction monitoring alerts, etc. Retrieve professionally designed KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V
The slide provides a comprehensive overview of the rules and regulations governing the cybersecurity industry. The slide aims to inform stakeholders regarding the laws in different countries such as USA, Europe, China And UK. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V The slide provides a comprehensive overview of the rules and regulations governing the cybersecurity industry. The slide aims to inform stakeholders regarding the laws in different countries such as USA, Europe, China And UK.
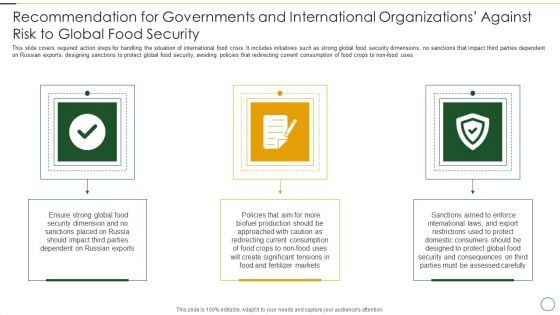
Recommendation For Governments And International Organizations Against Risk To Global Food Security Infographics PDF
This slide covers required action steps for handling the situation of international food crisis. It includes initiatives such as strong global food security dimensions, no sanctions that impact third parties dependent on Russian exports, designing sanctions to protect global food security, avoiding policies that redirecting current consumption of food crops to non food uses. Presenting recommendation for governments and international organizations against risk to global food security infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dependent on russian, ensure strong global, security dimension In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Types Of Security Testing Harnessing The World Of Ethical Ppt Sample
This slide represents the types of security testing such as penetration testing, application security testing, web application security testing, etc. Do you know about Slidesgeeks Various Types Of Security Testing Harnessing The World Of Ethical Ppt Sample These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the types of security testing such as penetration testing, application security testing, web application security testing, etc.

Impact Of Critical Security Concerns Issues On Overall Firms Performance Elements PDF
This slide provides information about the several situations that will result in increase of potential security threats in the organization and addressing various major security concerns at workplace. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Impact Of Critical Security Concerns Issues On Overall Firms Performance Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Impact Of Critical Security Concerns Issues On Overall Firms Performance Elements PDF today and make your presentation stand out from the rest.
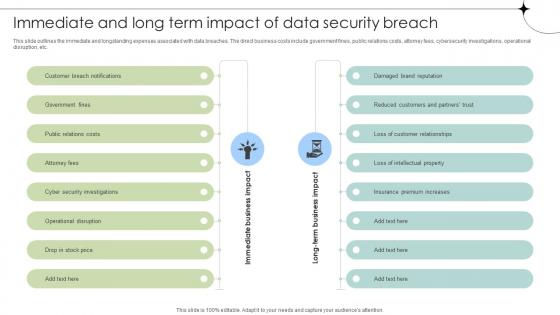
Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Are you searching for a Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses from Slidegeeks today. This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc.

Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Do you know about Slidesgeeks Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls.
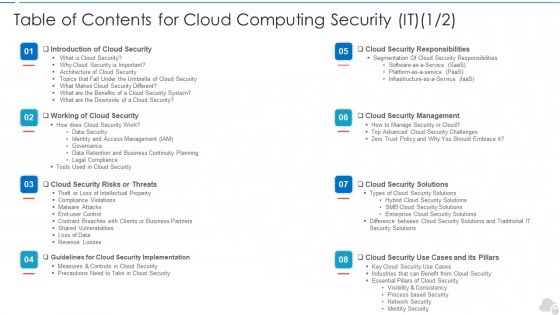
Table Of Contents For Cloud Computing Security IT Business Ppt File Inspiration PDF
Deliver an awe inspiring pitch with this creative table of contents for cloud computing security it business ppt file inspiration pdf bundle. Topics like cloud security implementation, cloud security responsibilities, cloud security management, cloud security solutions, cloud security risks or threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Get a simple yet stunning designed Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.

Different Types Of Cryptographic Data Security In Cloud Computing Ppt Example
This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric-key cryptography, asymmetric-key cryptography, hash functions, steganography, etc. This Different Types Of Cryptographic Data Security In Cloud Computing Ppt Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Different Types Of Cryptographic Data Security In Cloud Computing Ppt Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric-key cryptography, asymmetric-key cryptography, hash functions, steganography, etc.

Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides
This incisive,comprehensive Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides details important features of running a business. One learns about things like result areas,planning and strategic framework just a glance of this comprehensive deck of eighty five slides. Use this PPT template to present your unique perspective of business technicalities and experience the way a good presentation can give new meaning to similarly placed facts. Use this template to leave a roomful of people wondering at the expert you have gathered in closing a business deal. The completely editable and customisable nature of the presentation is a unique bonus. Download now. Our Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































