Information Security

Damage Security Insurance Proposal Next Step For Liability Insurance Proposal Ppt Summary Outline PDF
Presenting damage security insurance proposal next step for liability insurance proposal ppt summary outline pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like next step. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Our Major Clients For Liability Insurance Proposal Ppt Inspiration Backgrounds PDF
Presenting damage security insurance proposal our major clients for liability insurance proposal ppt inspiration backgrounds pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like major clients liability insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Monitoring Plan Professional PDF
Presenting way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan professional pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like monitoring all systems, monitoring network traffic, monitoring user activity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
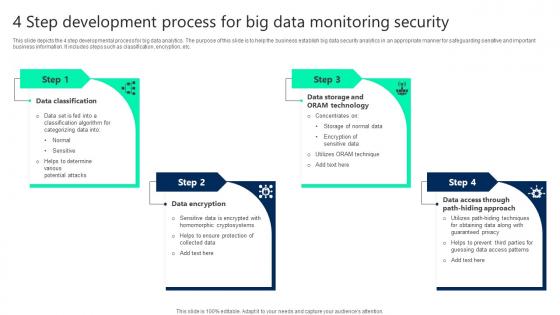
4 Step Development Process For Big Data Monitoring Security Demonstration pdf
This slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc. Showcasing this set of slides titled 4 Step Development Process For Big Data Monitoring Security Demonstration pdf. The topics addressed in these templates are Data Classification, Data Access, Data Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc.
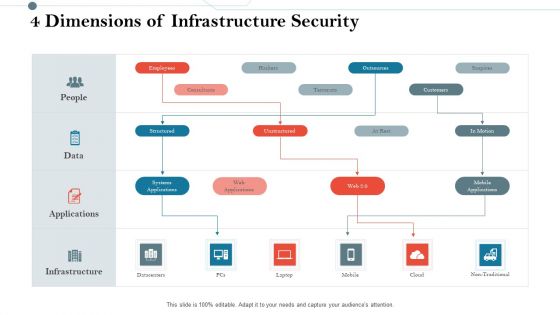
Construction Management Services And Action Plan 4 Dimensions Of Infrastructure Security Rules PDF
Presenting construction management services and action plan 4 dimensions of infrastructure security rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
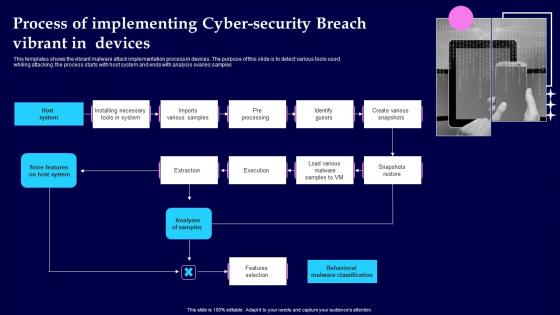
Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf
This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples Pitch your topic with ease and precision using this Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf This layout presents information on Analyses Of Samples, Features Selection, Pre Processing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples

Cyber Security For Your Organization Budget For Effective Cybersecurity Management Ppt Ideas Objects PDF
Presenting this set of slides with name cyber security for your organization budget for effective cybersecurity management ppt ideas objects pdf. This is a one stage process. The stages in this process are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
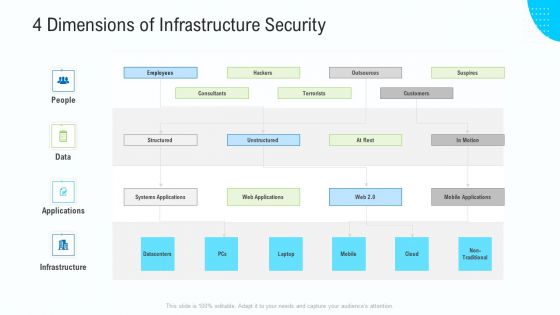
Business Activities Assessment Examples 4 Dimensions Of Infrastructure Security Professional PDF
Presenting business activities assessment examples 4 dimensions of infrastructure security professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
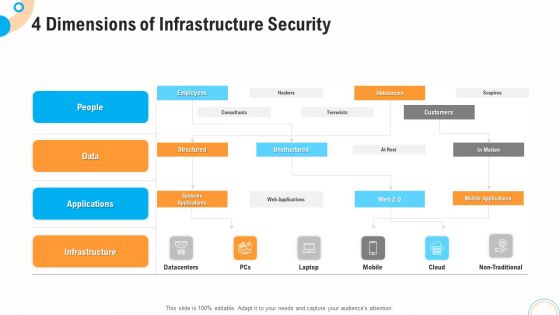
Fiscal And Operational Assessment 4 Dimensions Of Infrastructure Security Guidelines PDF
Presenting fiscal and operational assessment 4 dimensions of infrastructure security guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
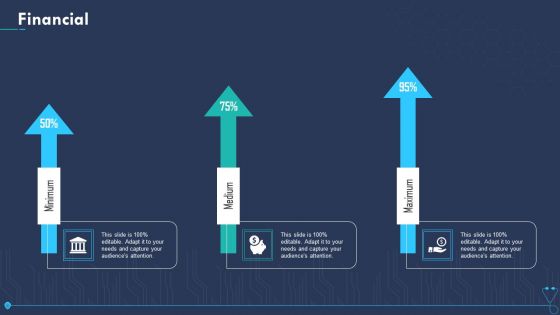
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Financial Elements PDF
Presenting case competition overpower the obstacle of cyber security in medicare financial elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
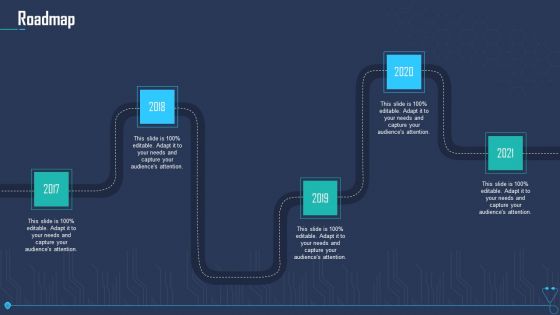
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Roadmap Inspiration PDF
Presenting case competition overpower the obstacle of cyber security in medicare roadmap inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap, 2017 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
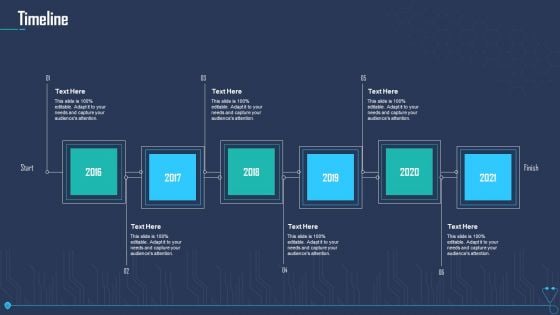
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Timeline Sample PDF
Presenting case competition overpower the obstacle of cyber security in medicare timeline sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Essential Elements To Be Included In A Security Management Plan Slides PDF
Presenting Essential elements to be included in a security management plan slides pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like program management, preparedness, recovery, training, response. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Guidelines To Create An Advanced Security Management Plan 30 60 90 Days Plan Rules PDF
Presenting guidelines to create an advanced security management plan 30 60 90 days plan rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Adopting Access Controls Demonstration PDF
Presenting security management plan steps in detail adopting access controls demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like logical access controls, control implementation, physical access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
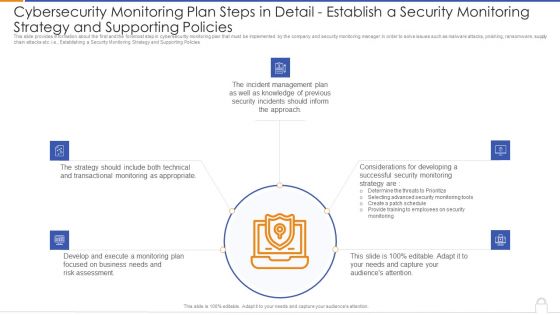
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Supporting Policies Microsoft PDF
Presenting cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like transactional monitoring, develop and execute, incident management plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Employee Awareness Training Budget For Fy2022 Inspiration PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Presenting desktop security management employee awareness training budget for fy2022 inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like opportunities, threats, weaknesses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
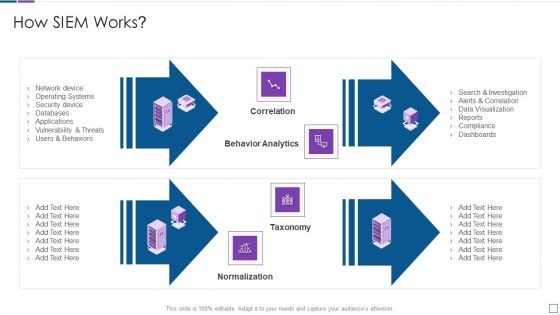
Real Time Assessment Of Security Threats How SIEM Works Inspiration PDF
Presenting real time assessment of security threats how siem works inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like correlation, behavior analytics, taxonomy, normalization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
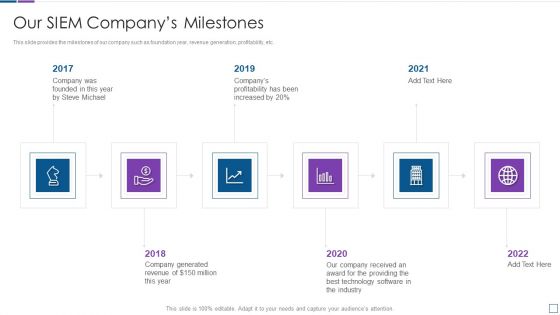
Real Time Assessment Of Security Threats Our SIEM Companys Milestones Slides PDF
This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. Presenting real time assessment of security threats our siem companys milestones slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like our siem companys milestones. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
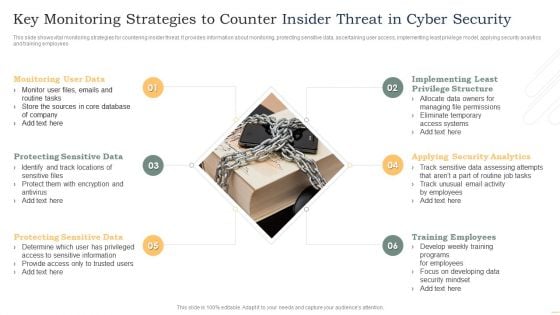
Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
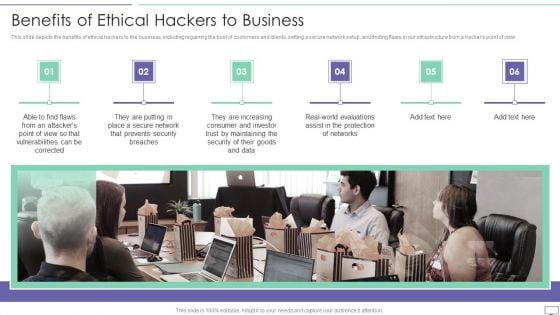
IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view.Presenting IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Consumer And Investor, Assist In The Protection, Prevents Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
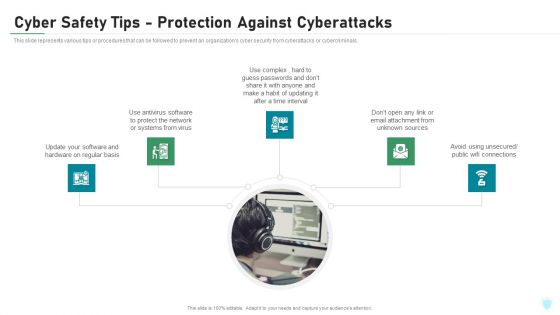
Cyber Safety Tips Protection Against Cyberattacks IT Security IT Ppt File Aids PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Presenting cyber safety tips protection against cyberattacks it security it ppt file aids pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cyber safety tips protection against cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Website And Social Media IT Security Audit With Risk Level Ppt Styles Pictures PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Presenting Website And Social Media IT Security Audit With Risk Level Ppt Styles Pictures PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Current Value, Risk, Risk Level. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. There are so many reasons you need a Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
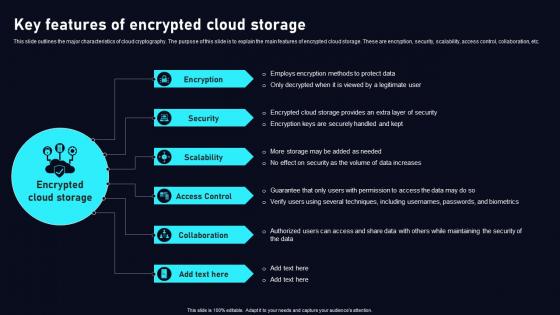
Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.

Web App Firewall Services IT Security Use Cases Of Web Application Firewall Deployment Brochure PDF
This slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. Presenting web app firewall services it security use cases of web application firewall deployment brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network, application, performance, material. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
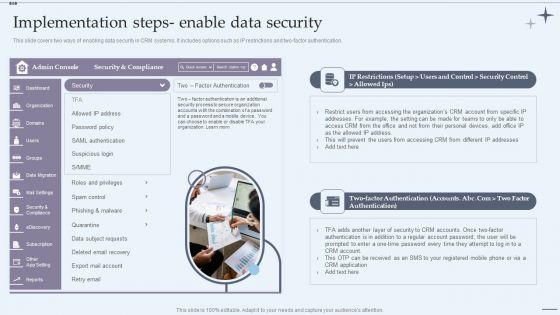
CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Presenting CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Marketing Executive, Marketing Intern, Sales Executive. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V
The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects. This Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
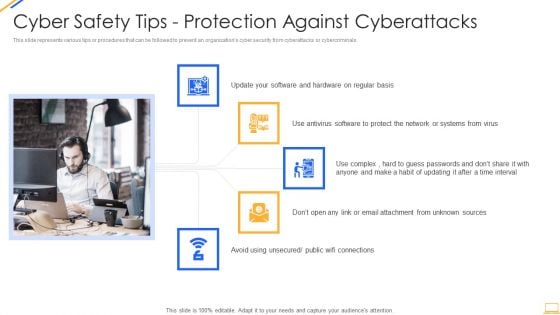
Desktop Security Management Cyber Safety Tips Protection Against Cyberattacks Download PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Presenting desktop security management cyber safety tips protection against cyberattacks download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like systems, network, sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
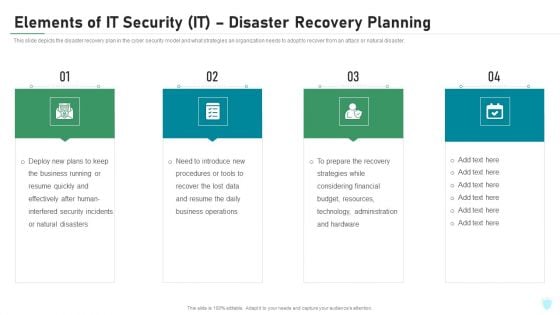
Elements Of IT Security IT Disaster Recovery Planning Ppt Styles Influencers PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting elements of it security it disaster recovery planning ppt styles influencers pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like effectively, business, technology, budget, resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Network Security Using Firewall As A Service Table Of Contents Designs Pdf
This slide demonstrates the flow of traffic within a network secured with firewall. The purpose of this slide is to illustrate the meaning of good and bad traffic. This slide also highlights the factors which are used to analyze the nature of data packets. This Network Security Using Firewall As A Service Table Of Contents Designs Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the flow of traffic within a network secured with firewall. The purpose of this slide is to illustrate the meaning of good and bad traffic. This slide also highlights the factors which are used to analyze the nature of data packets.
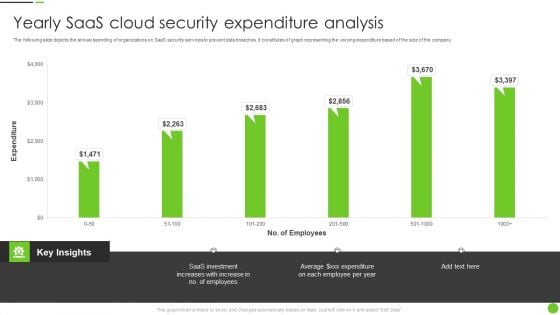
Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF
The following slide depicts the annual spending of organizations on SaaS security services to prevent data breaches. It constitutes of graph representing the varying expenditure based of the size of the company. Pitch your topic with ease and precision using this Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF. This layout presents information on Saas Investment, Employees. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
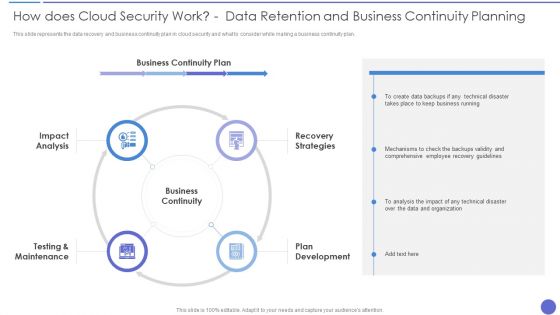
How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Presenting How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Continuity, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
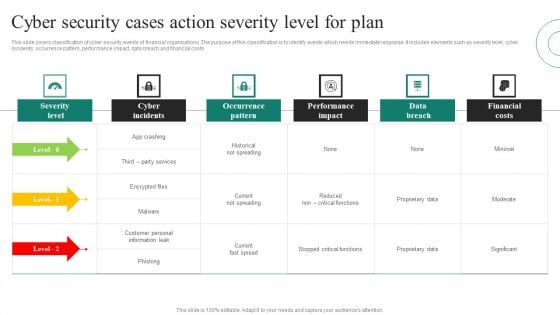
Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF
This slide covers classification of cyber security events of financial organizations. The purpose of this classification is to identify events which needs immediate response. It includes elements such as severity level, cyber incidents, occurrence pattern, performance impact, data breach and financial costs Pitch your topic with ease and precision using this Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF. This layout presents information on Severity Level, Cyber Incidents, Occurrence Pattern, Performance Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
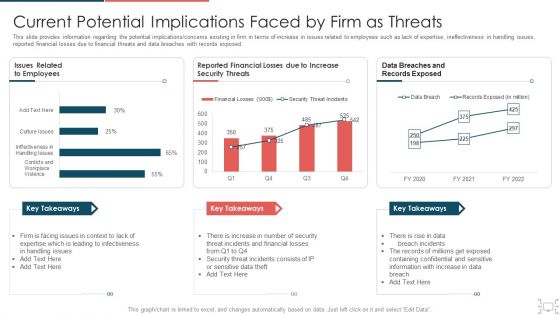
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
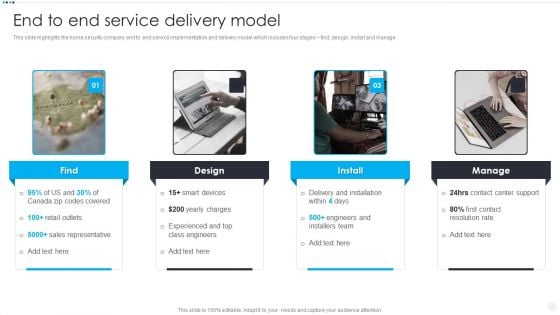
Smart Home Security Solutions Company Profile End To End Service Delivery Model Slides PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage. Presenting Smart Home Security Solutions Company Profile End To End Service Delivery Model Slides PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Delivery And Installation, Contact Center Support, Contact Resolution Rate, Engineers And Installers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
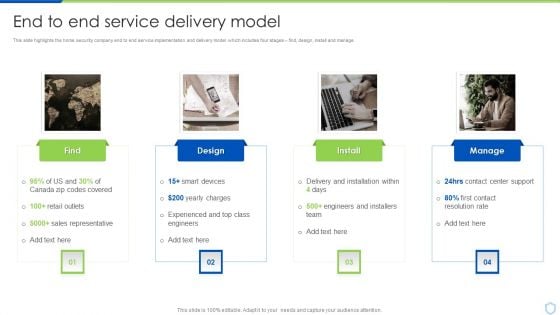
Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage.Presenting Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Sales Representative, Experienced Engineers, Engineers Installers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
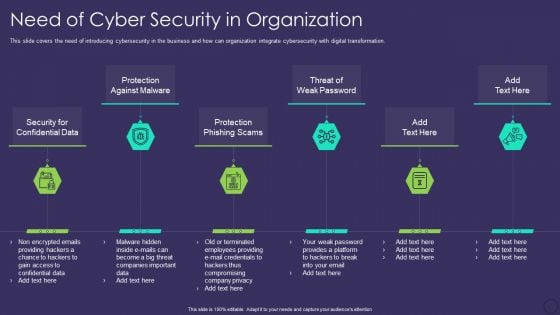
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

About Us For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the information about the organization as it displays the Company introduction, company background etc. Presenting you an exemplary About Us For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this About Us For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
Where Is The Gap In Security Programs Ppt Icon Layout Ideas PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps Presenting where is the gap in security programs ppt icon layout ideas pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like problems, gap, solution. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
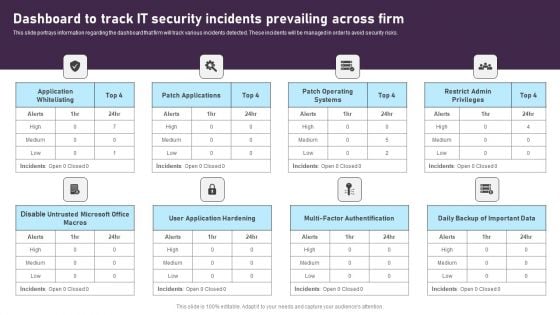
Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions.Presenting Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Management Training, Potential Mitigation, Already Developed In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Market Restraints Impacting The Global Security Industry PPT Template IR SS V
The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry. This modern and well-arranged Market Restraints Impacting The Global Security Industry PPT Template IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry.
Online Settlement Revolution Payment Security And Fraud Management Solutions Browser Icons PDF
Payment security and fraud management solutions for the user to limit losses while maintain a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions browser icons pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like costs, process, analytics, development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
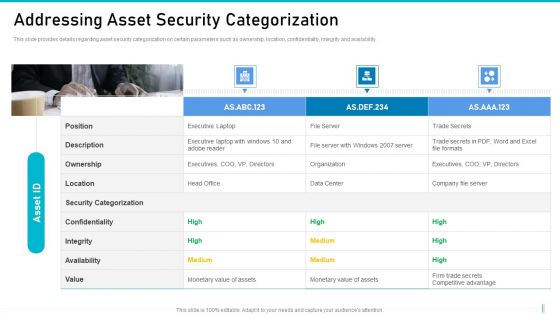
Risk Management For Organization Essential Assets Addressing Asset Security Categorization Diagrams PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Presenting risk management for organization essential assets addressing asset security categorization diagrams pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ownership, location, confidentiality, integrity, availability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
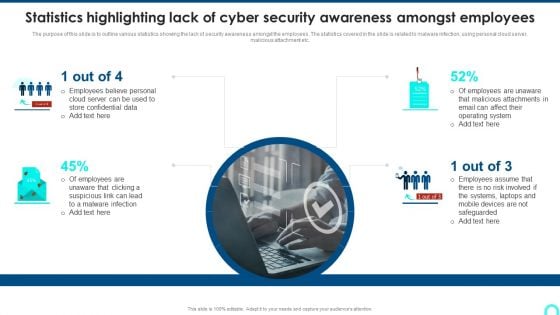
Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc.Presenting Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Employees Believe, Store Confidential, Malicious Attachments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

About Us Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the information about the organization as it displays the Company introduction, company background etc. Presenting you an exemplary About Us Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this About Us Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.

Case Study For Security Camera Services One Pager Sample Example Document
This slide represents the case study highlighting the successful execution of a similar project in the past by the bidding company. It provides information about the business problem, solution, and results. Presenting you an exemplary Case Study For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study For Security Camera Services One Pager Sample Example Document brilliant piece now.

About Us For Security Camera Services One Pager Sample Example Document
This slide shows the brief history of the bidding company providing information about the foundation year, vision and mission statements, and core values. Presenting you an exemplary About Us For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this About Us For Security Camera Services One Pager Sample Example Document brilliant piece now.

Contact Us For Security Camera Services One Pager Sample Example Document
This slide depicts the contact information of the bidding company for the client covering details about the address, contact numbers, and email address. Presenting you an exemplary Contact Us For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Contact Us For Security Camera Services One Pager Sample Example Document brilliant piece now.
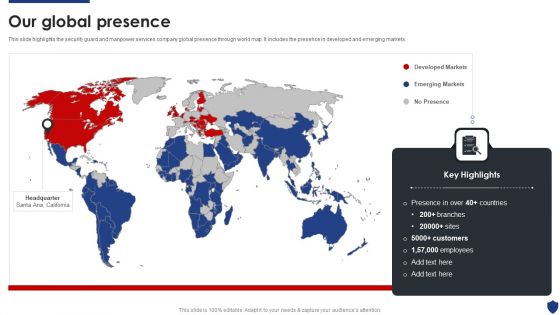
Security Officer Service Company Profile Our Global Presence Ppt PowerPoint Presentation Gallery Microsoft PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. Presenting Security Officer Service Company Profile Our Global Presence Ppt PowerPoint Presentation Gallery Microsoft PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Developed Markets, Emerging Markets, No Presence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
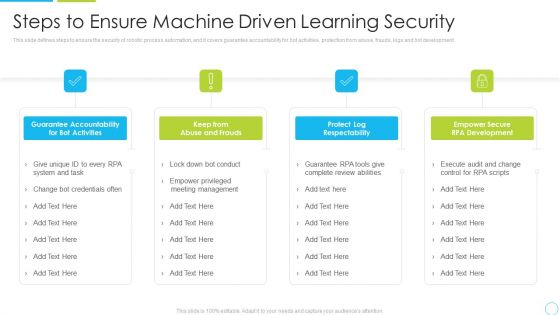
Steps To Ensure Machine Driven Learning Security Ppt Inspiration Structure PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. Presenting steps to ensure machine driven learning security ppt inspiration structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like system, management, development, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
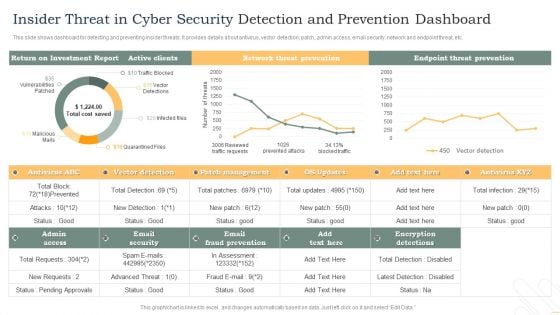
Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF
This slide shows dashboard for detecting and preventing insider threats. It provides details about antivirus, vector detection, patch, admin access, email security, network and endpoint threat, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF. This layout presents information on Active Clients, Network Threat Prevention, Endpoint Threat Prevention. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Workforce Security Realization Coaching Plan Different Training Formats For Different Organizational Levels Icons PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. Presenting workforce security realization coaching plan different training formats for different organizational levels icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like interactive protection simulation, cybersecurity for it online, automated security awareness platform. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile Existing Channel Development Strategy Formats PDF
This slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Presenting Security And Surveillance Company Profile Existing Channel Development Strategy Formats PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Motion Awareness, Flood Protection, Thermostat Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































