Information Security
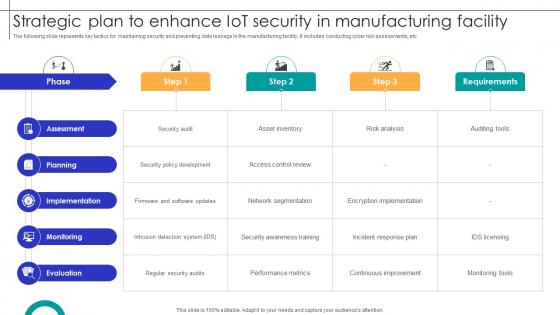
Strategic Plan To Enhance IOT Security In Manufacturing Facility Streamlining Production Ppt Sample
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Strategic Plan To Enhance IOT Security In Manufacturing Facility Streamlining Production Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
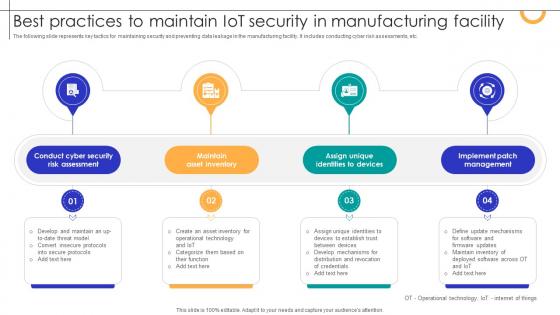
Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template today and make your presentation stand out from the rest The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
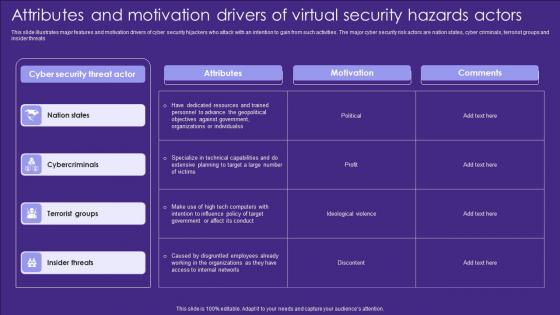
Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf
This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats Showcasing this set of slides titled Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf. The topics addressed in these templates are Attributes, Motivation, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats
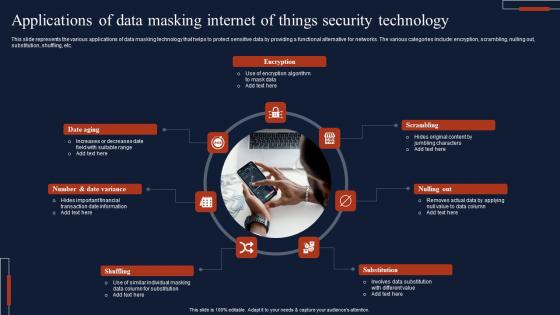
Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc.

Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf
This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Create an editable Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc.
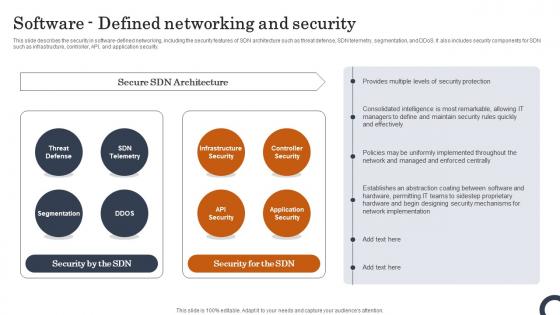
Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Do you know about Slidesgeeks Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.

Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Our Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V
The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as. The Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as.

Evolution Of Security Testing Harnessing The World Of Ethical Ppt Presentation
This slide showcases the evolution of security testing from late 1960 when the inception of security testing was unclear to universal practice for all sizes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Evolution Of Security Testing Harnessing The World Of Ethical Ppt Presentation With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Evolution Of Security Testing Harnessing The World Of Ethical Ppt Presentation today and make your presentation stand out from the rest This slide showcases the evolution of security testing from late 1960 when the inception of security testing was unclear to universal practice for all sizes.
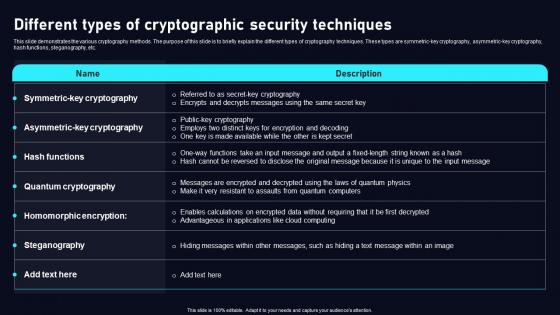
Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf
This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric key cryptography, asymmetric key cryptography, hash functions, steganography, etc. Slidegeeks has constructed Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric key cryptography, asymmetric key cryptography, hash functions, steganography, etc.
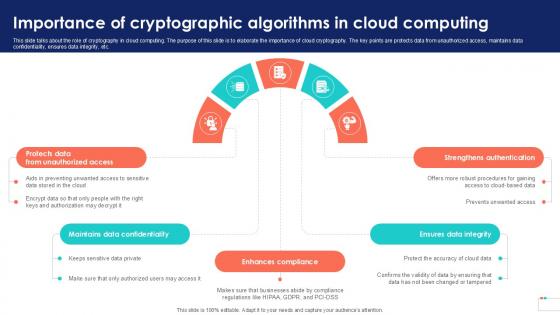
Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Presenting this PowerPoint presentation, titled Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.

What Are Benefits Of Using Data Security In Cloud Computing Ppt Template
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit What Are Benefits Of Using Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.

What Is The Cyber Security Role Web Designing User Engagement Rules PDF
Boost your pitch with our creative What Is The Cyber Security Role Web Designing User Engagement Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.
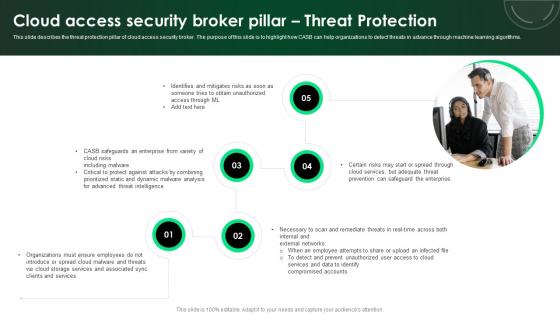
CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Retrieve professionally designed CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms.

Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf
This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Presenting this PowerPoint presentation, titled Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc.

Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V
The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.
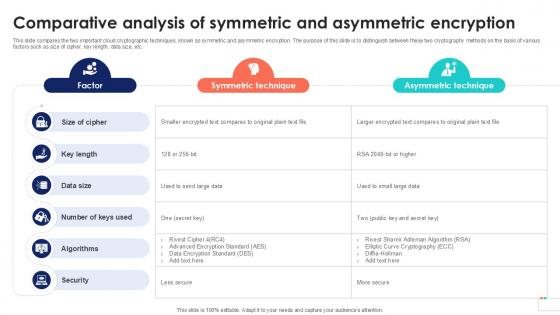
Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
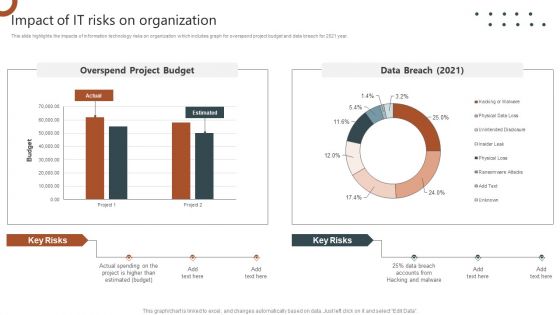
Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF
This slide highlights the impacts of information technology risks on organization which includes graph for overspend project budget and data breach for 2021 year. Explore a selection of the finest Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
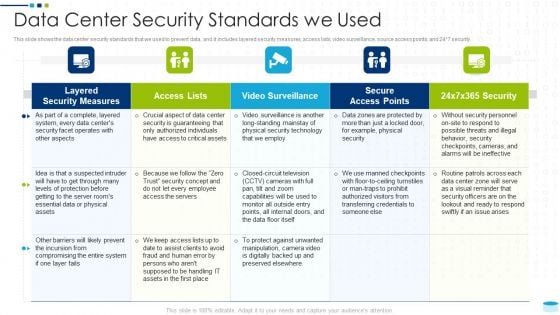
Data Center Infrastructure Management IT Data Center Security Standards We Used Professional PDF
This slide shows the data center security standards that we used to prevent data, and it includes layered security measures, access lists, video surveillance, source access points, and 24 7 security. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it data center security standards we used professional pdf. Use them to share invaluable insights on layered security measures, access lists, video surveillance, secure access points, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF
This slide showcases blockchain technology for anti money laundering AML and transaction monitoring. It provides information about transaction subsets, input data, monitoring, analysis, alerts, record, red flags, Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF.

How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Get a simple yet stunning designed How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc.
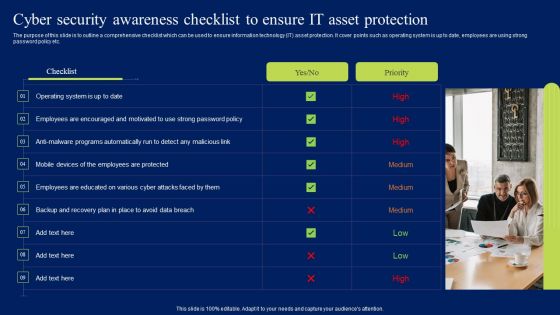
Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
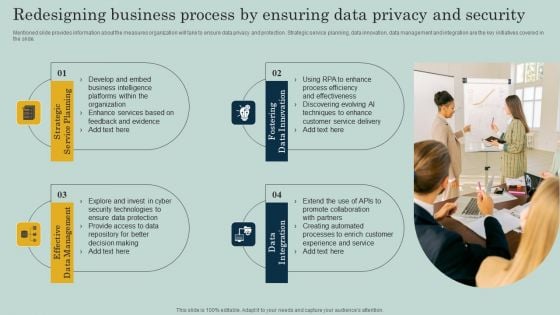
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Create an editable Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.
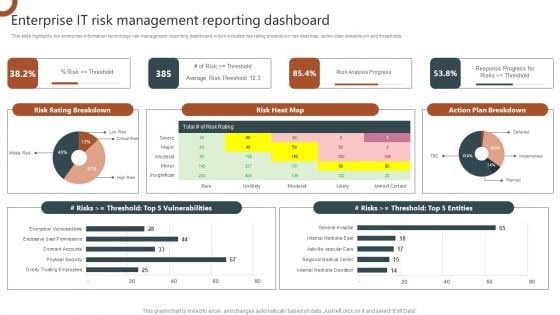
Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF
This slide highlights the enterprise information technology risk management reporting dashboard which includes risk rating breakdown risk heat map, action plan breakdown and thresholds. This Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
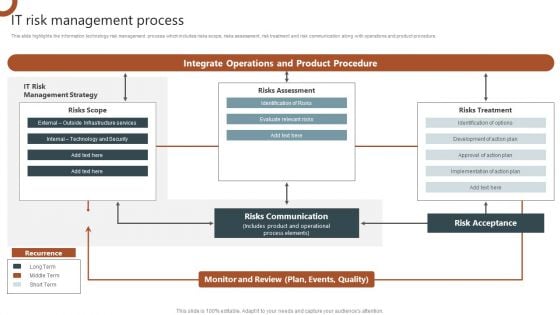
IT Risk Management Process Organizations Risk Management And IT Security Slides PDF
This slide highlights the information technology risk management process which includes risks scope, risks assessment, risk treatment and risk communication along with operations and product procedure. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Risk Management Process Organizations Risk Management And IT Security Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Risk Management Process Organizations Risk Management And IT Security Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
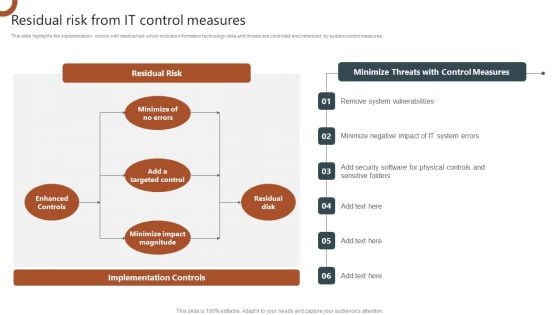
Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF
This slide highlights the implementation control with residual risk which includes information technology risks and threats are controlled and minimized by system control measures. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF today and make your presentation stand out from the rest.
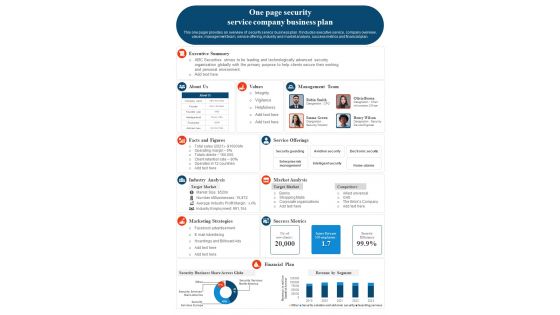
One Page Security Service Company Business Plan PDF Document PPT Template
Presenting you an exemplary One Page Security Service Company Business Plan PDF Document PPT Template. Our one-pager template comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Security Service Company Business Plan PDF Document PPT Template Download now. Our One Page Security Service Company Business Plan PDF Document PPT Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
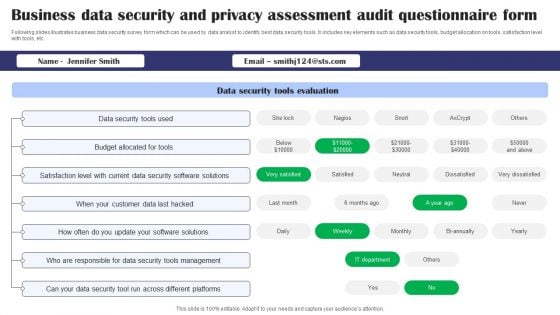
Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS
Following slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Showcasing this set of slides titled Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS. The topics addressed in these templates are Data Security Tools Evaluation, Data Security Tools Used, Budget Allocated For Tools, Data Security Software Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
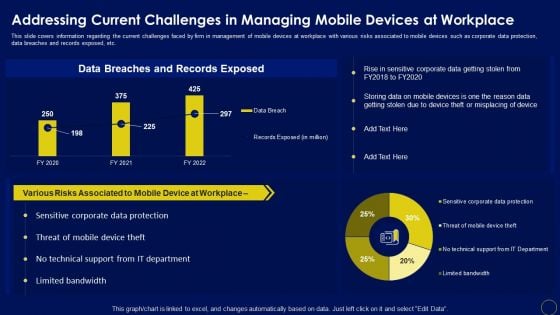
Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
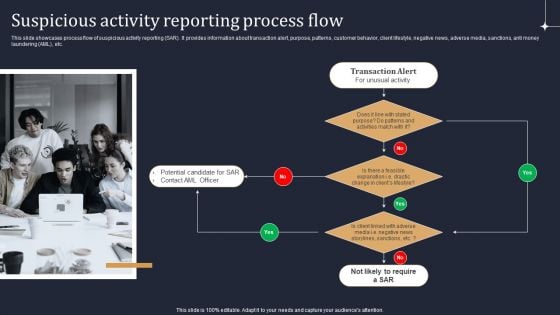
KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF
This slide showcases process flow of suspicious activity reporting SAR. It provides information about transaction alert, purpose, patterns, customer behavior, client lifestyle, negative news, adverse media, sanctions, anti money laundering AML, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF today and make your presentation stand out from the rest.
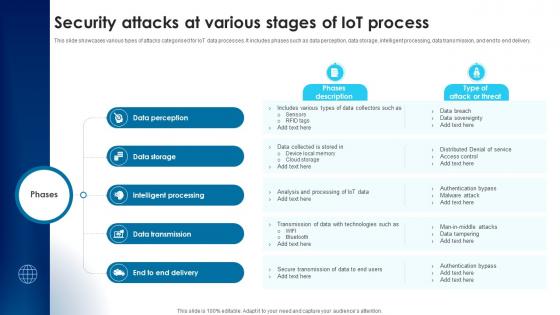
Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V
This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery. Create an editable Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery.

KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF
This slide showcases assessing impact on major operations and workflows. It provides information about customer understanding, knowledge, data management, financial risk management, customer relationship management, client onboarding, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF.
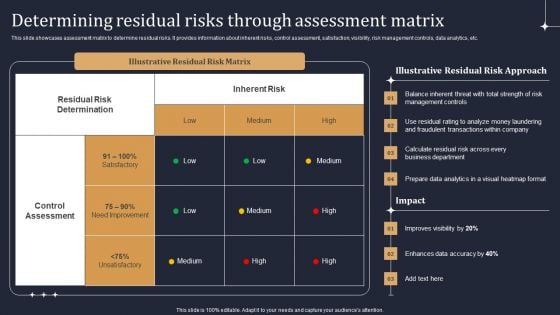
KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
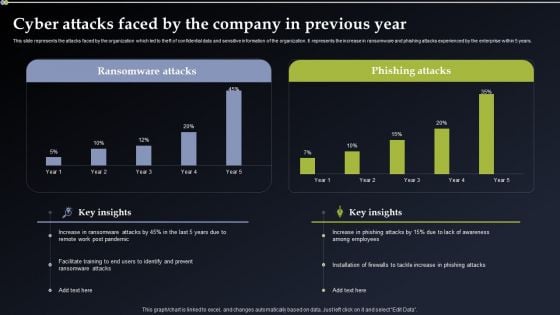
Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF
This slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V
The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry.
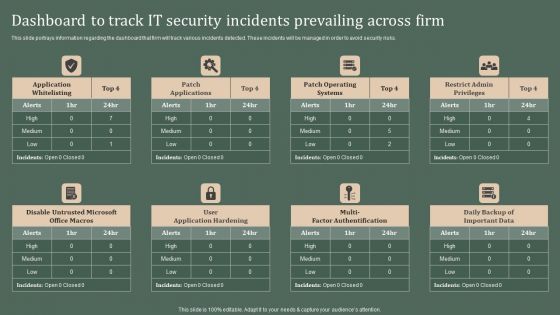
Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Organizations Risk Management And IT Security Need Of IT Risk Management Portrait PDF
The following slide highlights the importance of information risk management which includes safer environment, reduce unexpected events, financial benefits, saves time and effort, and improves security. Present like a pro with Organizations Risk Management And IT Security Need Of IT Risk Management Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
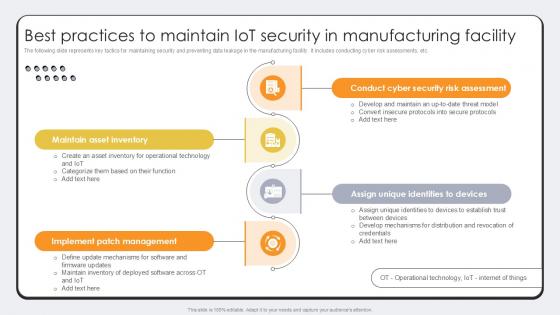
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
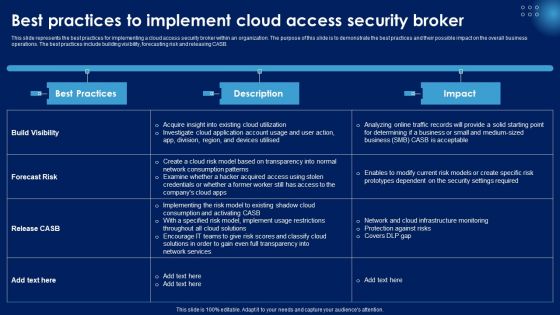
Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
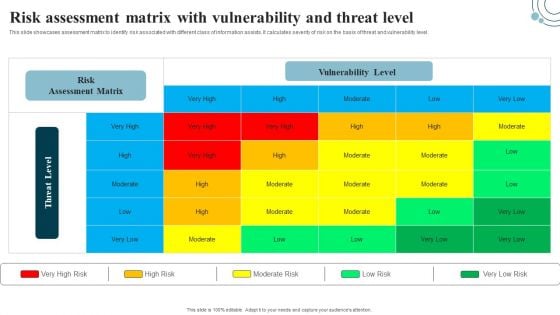
Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is here to make your presentations a breeze with Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

CASB 2 0 IT Training Program For Cloud Access Security Broker
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Training Program For Cloud Access Security Broker was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Training Program For Cloud Access Security Broker. This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training.
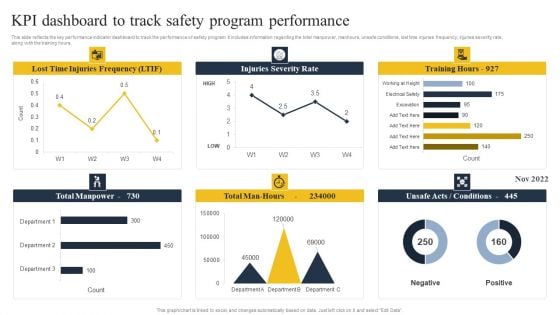
Security Control Techniques For Real Estate Project KPI Dashboard To Track Safety Program Performance Brochure PDF
This slide reflects the key performance indicator dashboard to track the performance of safety program. It includes information regarding the total manpower, manhours, unsafe conditions, lost time injuries frequency, injuries severity rate, along with the training hours. Create an editable Security Control Techniques For Real Estate Project KPI Dashboard To Track Safety Program Performance Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Control Techniques For Real Estate Project KPI Dashboard To Track Safety Program Performance Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
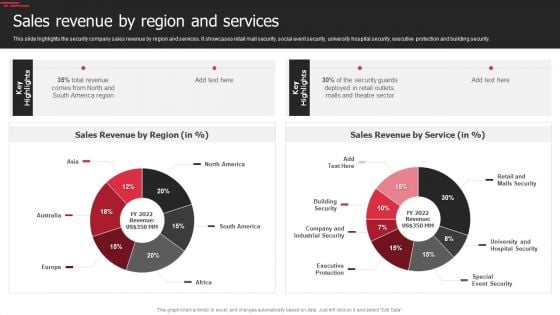
Security Agency Business Profile Sales Revenue By Region And Services Slides PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Sales Revenue By Region And Services Slides PDF. Use them to share invaluable insights on Revenue, Security, Executive Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
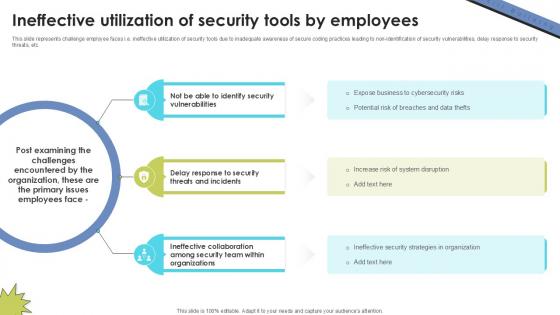
Ineffective Utilization Of Security Skill Building Plan For Application PPT Presentation DTE SS V
This slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non-identification of security vulnerabilities, delay response to security threats, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Ineffective Utilization Of Security Skill Building Plan For Application PPT Presentation DTE SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non-identification of security vulnerabilities, delay response to security threats, etc.

Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF
This slide showcases cyber security risk landscape which can benefit various users around the world to be proactive of potential outcomes. It includes information about target, purpose, possible outcome, social media phishing, system viruses, configuration and passcodes, allocated service denial, hacking devices and structured query language. Persuade your audience using this Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Landscape, Target, Purpose, Possible Outcome. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF
This slide showcases identifying inherent risk factors and measures. It provides information about customer base, products, services, delivery channels, jurisdictions, qualitative factors, location, customer risk rating, transparency, fund transfer, etc. Create an editable KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Get a simple yet stunning designed CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB.
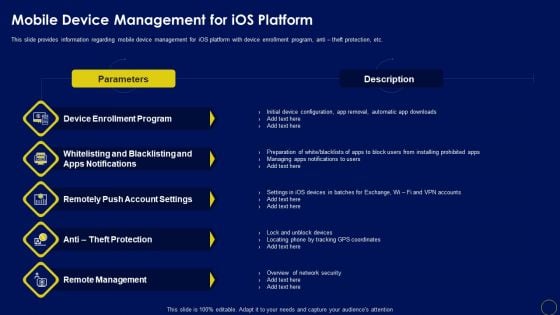
Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF today and make your presentation stand out from the rest.
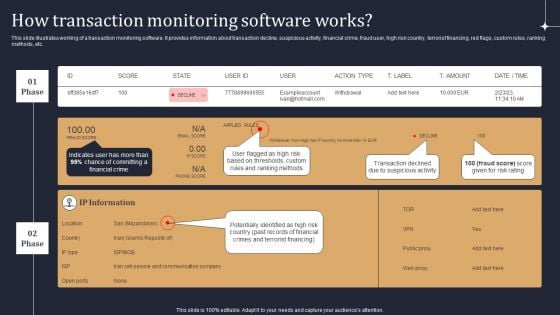
KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF
This slide illustrates working of a transaction monitoring software. It provides information about transaction decline, suspicious activity, financial crime, fraud user, high risk country, terrorist financing, red flags, custom rules, ranking methods, etc. Are you searching for a KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF from Slidegeeks today.

KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF
This slide showcases cryptocurrency transaction monitoring with alert status. It provides information about address, risk level, currencies, bitcoin, Ethereum, date added, deposits, case status, alerts, deposits, darknet, etc. This KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
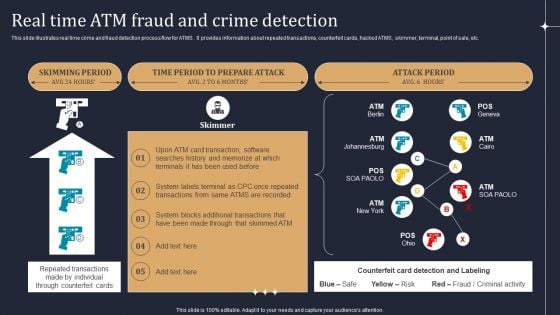
KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF
This slide covers information regarding how firm can handle financial crisis by safeguarding financial stability in terms of abundant cash requirements, overhead analysis, currency hedging, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF today and make your presentation stand out from the rest.
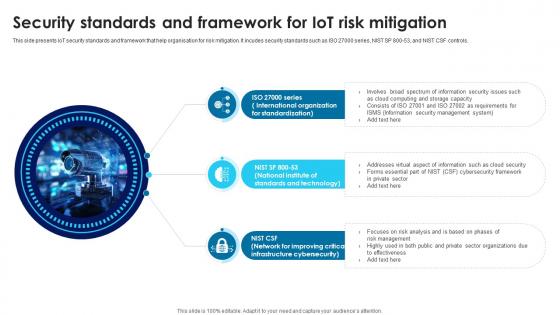
Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V
This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls. Present like a pro with Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls.

About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.


 Continue with Email
Continue with Email

 Home
Home


































