Iot Security
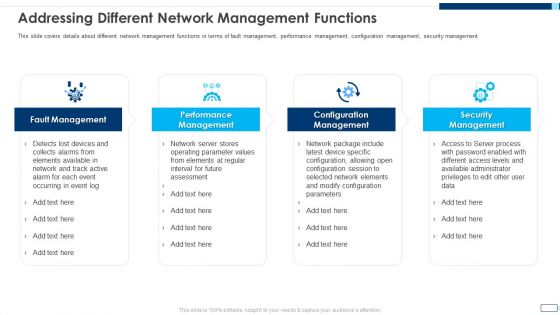
Evolving BI Infrastructure Addressing Different Network Management Functions Rules PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a evolving bi infrastructure addressing different network management functions rules pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fault management, performance management, configuration management, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
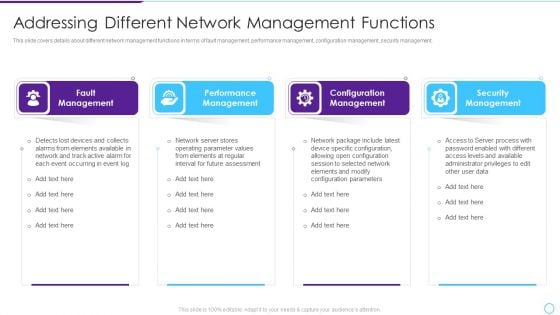
Intelligent Infrastructure Addressing Different Network Management Functions Background PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. Presenting Intelligent Infrastructure Addressing Different Network Management Functions Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Fault Management, Performance Management, Configuration Management, Security Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
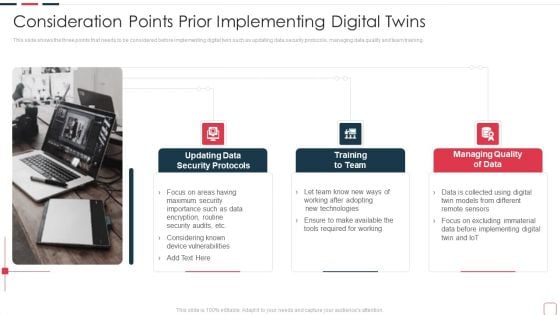
Price Benefit Internet Things Digital Twins Execution After Covid Consideration Points Prior Ideas PDF
This slide shows the three points that needs to be considered before implementing digital twin such as updating data security protocols, managing data quality and team training. This is a price benefit internet things digital twins execution after covid consideration points prior ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security protocol, training team, managing quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
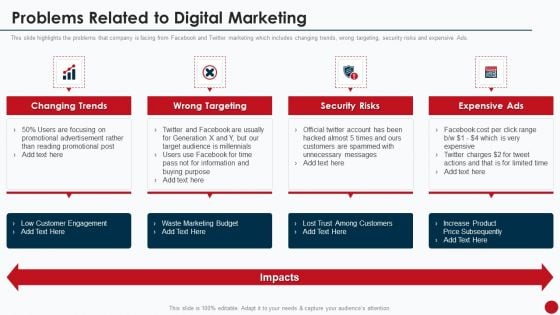
Marketing Manual For Product Promotion On Youtube Channel Problems Related To Digital Marketing Introduction PDF
This slide highlights the problems that company is facing from Facebook and Twitter marketing which includes changing trends, wrong targeting, security risks and expensive Ads.Presenting Marketing Manual For Product Promotion On Youtube Channel Problems Related To Digital Marketing Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Changing Trends, Security Risks, Among Customers In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
5G Network Technology Assessing Contribution Of 5G To Global Economy Ppt Icon Slideshow PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Deliver an awe inspiring pitch with this creative 5g network technology assessing contribution of 5g to global economy ppt icon slideshow pdf bundle. Topics like infrastructure, digital security and safety, regional specific content and services, enabling people to manage digitalization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
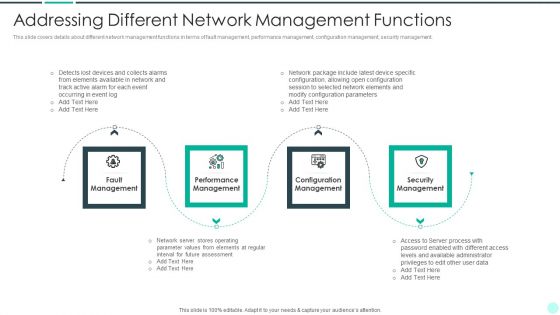
Executing Advance Data Analytics At Workspace Addressing Different Network Rules PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a executing advance data analytics at workspace addressing different network rules pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, performance, security, elements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
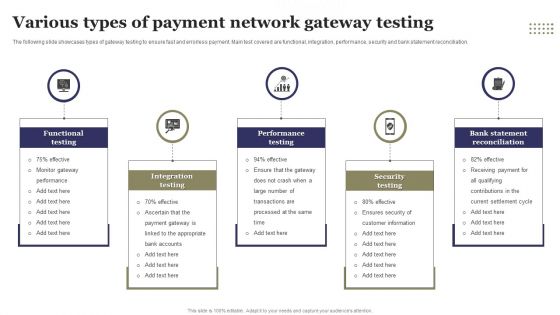
Various Types Of Payment Network Gateway Testing Ppt File Objects PDF
The following slide showcases types of gateway testing to ensure fast and errorless payment. Main test covered are functional, integration, performance, security and bank statement reconciliation. Persuade your audience using this Various Types Of Payment Network Gateway Testing Ppt File Objects PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Functional Testing, Integration Testing, Performance Testing, Security Testing . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
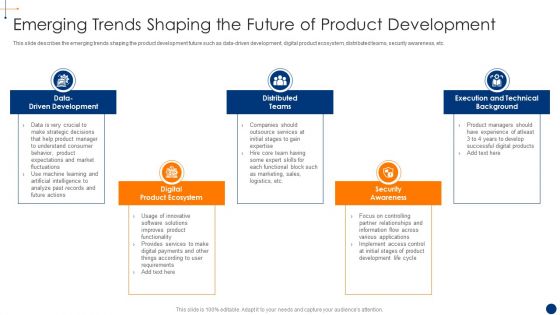
New Product Development Process Optimization Emerging Trends Shaping Clipart PDF
This slide describes the emerging trends shaping the product development future such as data-driven development, digital product ecosystem, distributed teams, security awareness, etc. This is a new product development process optimization emerging trends shaping clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data driven development, digital product ecosystem, security awareness, distributed teams. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Satisfying Consumers Through Strategic Product Building Plan Emerging Trends Shaping Information PDF
This slide describes the emerging trends shaping the product development future such as data-driven development, digital product ecosystem, distributed teams, security awareness, etc. Presenting satisfying consumers through strategic product building plan emerging trends shaping information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data driven development, digital product ecosystem, distributed teams, security awareness, execution and technical background. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
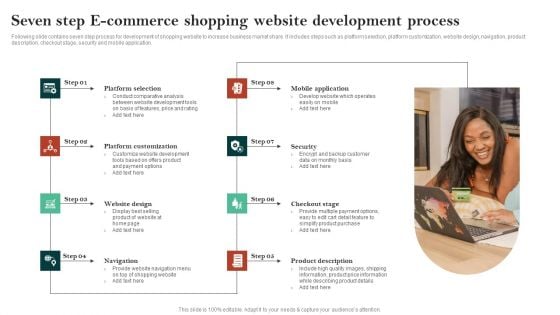
Seven Step E Commerce Shopping Website Development Process Guidelines PDF
Following slide contains seven step process for development of shopping website to increase business market share. It includes steps such as platform selection, platform customization, website design, navigation, product description, checkout stage, security and mobile application. Presenting Seven Step E Commerce Shopping Website Development Process Guidelines PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Platform Selection, Mobile Application, Security, Checkout Stage, Product Description. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Formulating Product Development Action Plan To Enhance Client Experience Emerging Trends Shaping Infographics PDF
This slide describes the emerging trends shaping the product development future such as data-driven development, digital product ecosystem, distributed teams, security awareness, etc. This is a formulating product development action plan to enhance client experience emerging trends shaping infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data driven development, digital product ecosystem, distributed teams, security awareness, execution and technical background. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
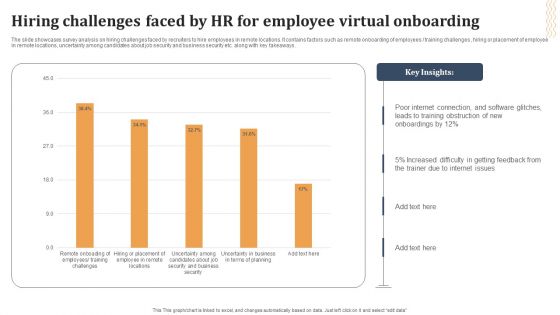
Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF
The slide showcases survey analysis on hiring challenges faced by recruiters to hire employees in remote locations. It contains factors such as remote onboarding of employees training challenges , hiring or placement of employee in remote locations, uncertainty among candidates about job security and business security etc. along with key takeaways. Showcasing this set of slides titled Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF. The topics addressed in these templates are Internet Connection, Software Glitches, Internet Issues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
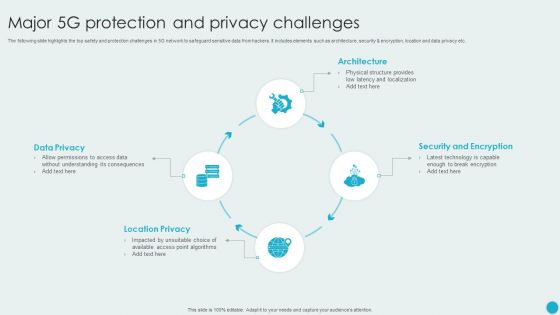
Major 5G Protection And Privacy Challenges Themes PDF
The following slide highlights the top safety and protection challenges in 5G network to safeguard sensitive data from hackers. It includes elements such as architecture, security and encryption, location and data privacy etc. Presenting Major 5G Protection And Privacy Challenges Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Privacy, Location Privacy, Security And Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
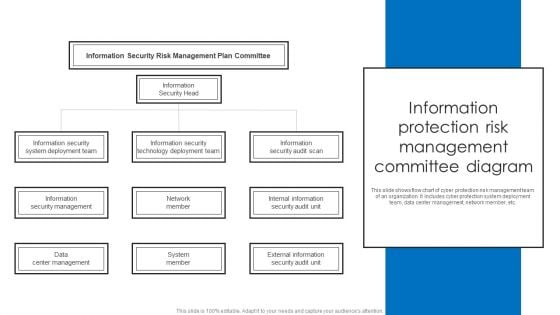
Information Protection Risk Management Committee Diagram Information PDF
This slide shows flow chart of cyber protection risk management team of an organization. It includes cyber protection system deployment team, data center management, network member, etc. Persuade your audience using this Information Protection Risk Management Committee Diagram Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security Head, Information Security Audit Scan, Network Member. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Portable Home Safety Systems Company Profile Our Expertise Ppt Summary Graphics Example PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. This is a Portable Home Safety Systems Company Profile Our Expertise Ppt Summary Graphics Example PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Integrated Control, Voice Assistant, Internet Protocol, RFID Based. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration SIEM Logging Sources Microsoft PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Presenting enhancing cyber safety with vulnerability administration siem logging sources microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, network devices, servers, applications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
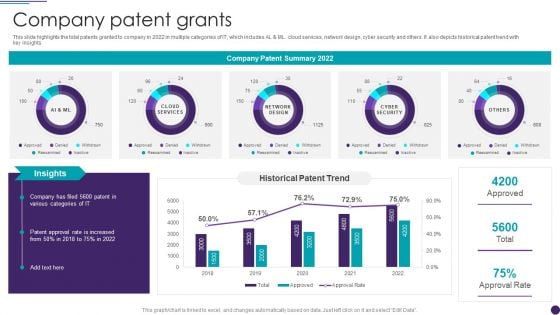
IT Services Business Profile Company Patent Grants Infographics PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative IT Services Business Profile Company Patent Grants Infographics PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
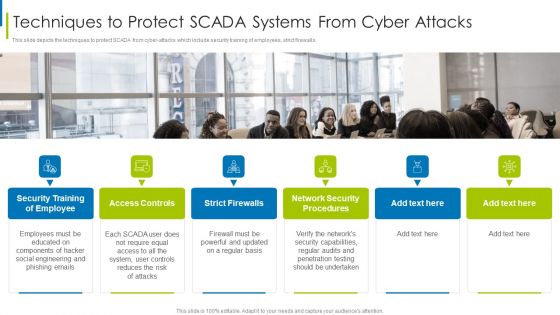
Cyber Terrorism Assault Techniques To Protect SCADA Systems From Cyber Attacks Demonstration PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls.Presenting cyber terrorism assault techniques to protect scada systems from cyber attacks demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like access controls, strict firewalls, network security procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Cost Management Model Components Clipart PDF
This slide shows cloud cost optimization components to make coordination between complex operations of cloud system. It include elements like orchestration, cloud network security and compliance setup etc. Presenting Cloud Cost Management Model Components Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Orchestration Automation, Cloud Network Security, Compliance Governance Setup. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

SIEM Logging Sources Ppt Portfolio Master Slide PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a siem logging sources ppt portfolio master slide pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
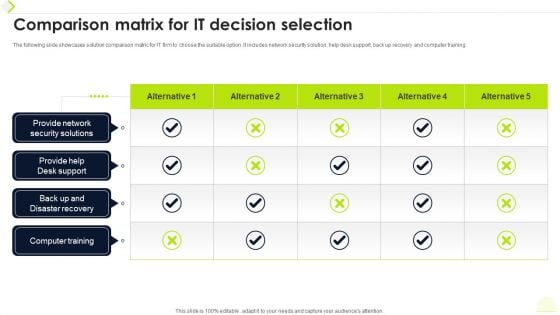
Comparison Matrix For IT Decision Selection Ppt Inspiration Graphic Tips PDF
The following slide showcases solution comparison matric for IT firm to choose the suitable option. It includes network security solution, help desk support, back up recovery and computer training. Showcasing this set of slides titled Comparison Matrix For IT Decision Selection Ppt Inspiration Graphic Tips PDF. The topics addressed in these templates are Provide Network, Security Solutions, Provide Help, Desk Support. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
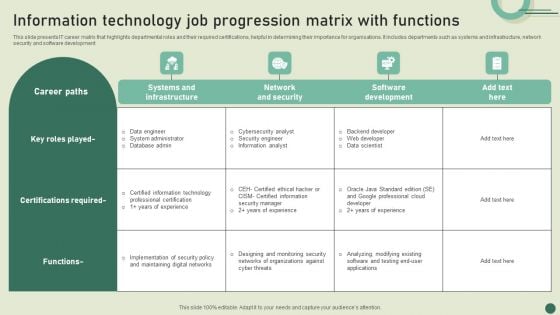
Information Technology Job Progression Matrix With Functions Graphics PDF
This slide presents IT career matrix that highlights departmental roles and their required certifications, helpful in determining their importance for organisations. It includes departments such as systems and infrastructure, network security and software development. Showcasing this set of slides titled Information Technology Job Progression Matrix With Functions Graphics PDF. The topics addressed in these templates are Systems And Infrastructure, Network Security, Software Development. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
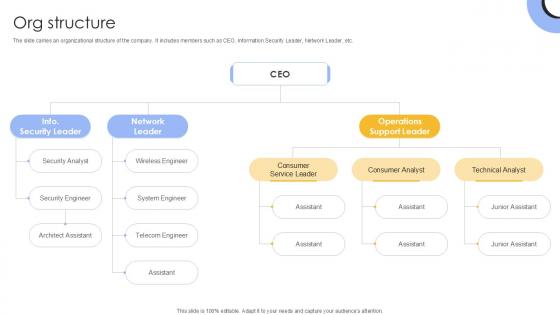
Org Structure Investment Company Investor Funding Elevator Ppt Presentation
The slide carries an organizational structure of the company. It includes members such as CEO, Information Security Leader, Network Leader, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Org Structure Investment Company Investor Funding Elevator Ppt Presentation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide carries an organizational structure of the company. It includes members such as CEO, Information Security Leader, Network Leader, etc.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
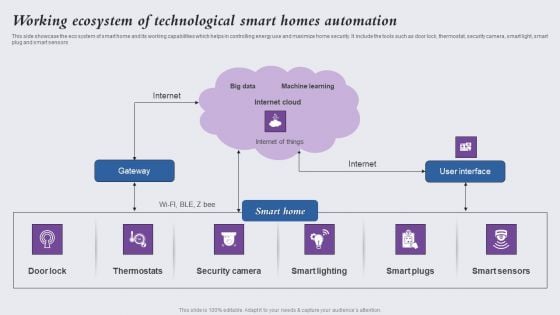
Working Ecosystem Of Technological Smart Homes Automation Elements PDF
This side showcase the eco system of smart home and its working capabilities which helps in controlling energy use and maximize home security. It include the tools such as door lock, thermostat, security camera, smart light, smart plug and smart sensors. Showcasing this set of slides titled Working Ecosystem Of Technological Smart Homes Automation Elements PDF. The topics addressed in these templates are Internet, Gateway, Thermostats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
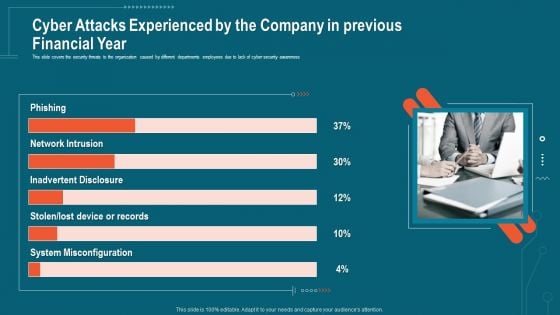
Companys Data Safety Recognition Cyber Attacks Experienced By The Company In Previous Financial Year Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. This is a companys data safety recognition cyber attacks experienced by the company in previous financial year sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system misconfiguration, inadvertent disclosure, network intrusion. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
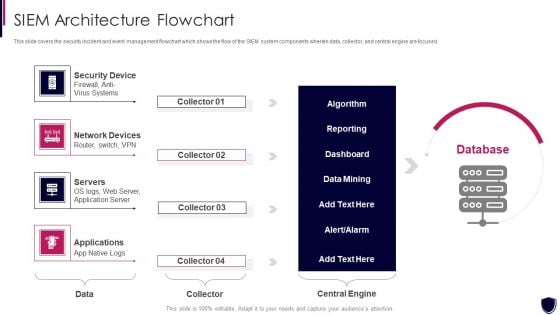
Enhancing Cyber Safety With Vulnerability Administration SIEM Architecture Flowchart Demonstration PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a enhancing cyber safety with vulnerability administration siem architecture flowchart demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
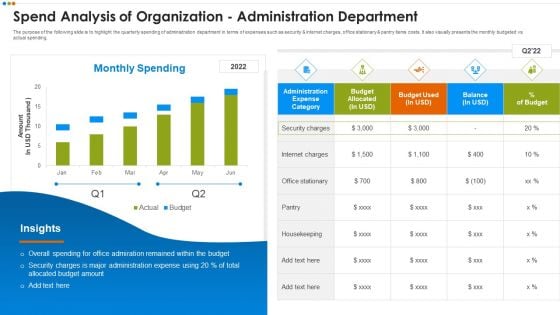
Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending.Deliver an awe inspiring pitch with this creative Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF bundle. Topics like Overall Spending, Admiration Remained, Security Administration Expense can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
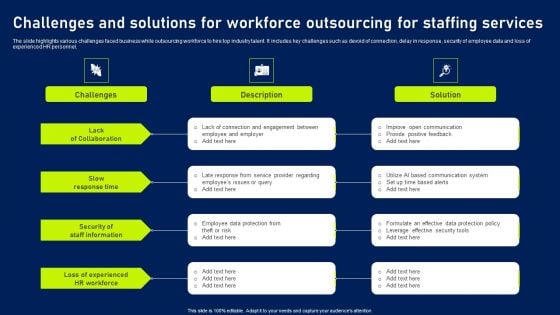
Challenges And Solutions For Workforce Outsourcing For Staffing Services Diagrams PDF
The slide highlights various challenges faced business while outsourcing workforce to hire top industry talent. It includes key challenges such as devoid of connection, delay in response, security of employee data and loss of experienced HR personnel. Presenting Challenges And Solutions For Workforce Outsourcing For Staffing Services Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Lack Collaboration, Slow Response Time, Security Staff Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
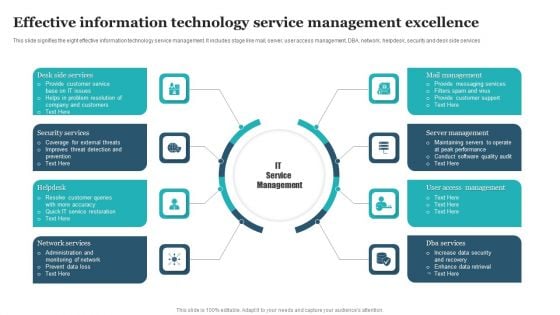
Effective Information Technology Service Management Excellence Rules PDF
This slide signifies the eight effective information technology service management. It includes stage like mail, server, user access management, DBA, network, helpdesk, security and desk side services. Presenting Effective Information Technology Service Management Excellence Rules PDF to dispense important information. This template comprises Eight stages. It also presents valuable insights into the topics including Desk Side Services, Mail Management, Security Services, Server Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Optimization Infrastructure Model Key Requirements Of Cloud Platform Download PDF
Following slide throw light on key specifications for both hardware and software requirements for building private cloud. It covers system support, cloud security, cloud network etc. Presenting Cloud Optimization Infrastructure Model Key Requirements Of Cloud Platform Download PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Service Management, Applications Portability, Cloud Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
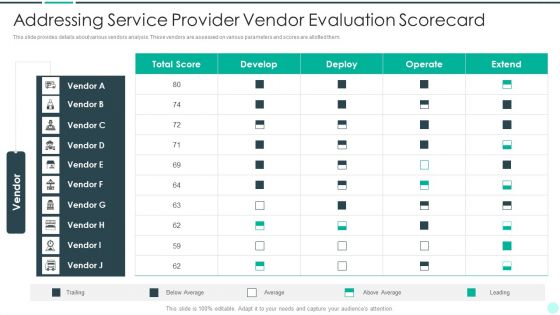
Executing Advance Data Analytics At Workspace Addressing Service Provider Vendor Formats PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a executing advance data analytics at workspace addressing service provider vendor formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fault management, performance management, configuration management, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
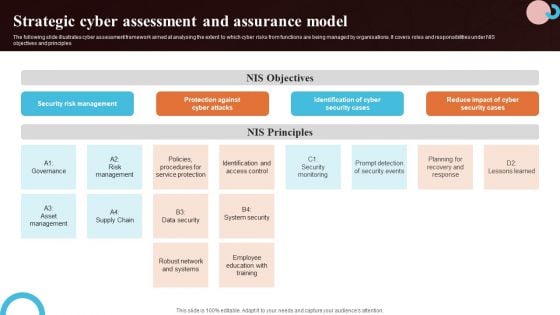
Strategic Cyber Assessment And Assurance Model Microsoft PDF
The following slide illustrates cyber assessment framework aimed at analysing the extent to which cyber risks from functions are being managed by organisations. It covers roles and responsibilities under NIS objectives and principles. Showcasing this set of slides titled Strategic Cyber Assessment And Assurance Model Microsoft PDF. The topics addressed in these templates are Security Cases, System Security, Network And Systems. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
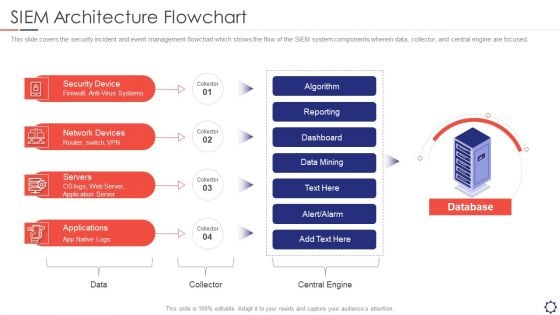
SIEM Architecture Flowchart Ppt Show Introduction PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a siem architecture flowchart ppt show introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
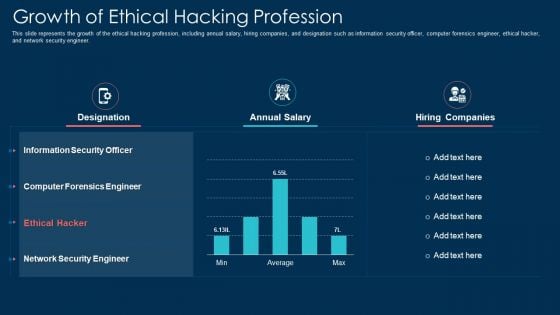
Growth Of Ethical Hacking Profession Ppt Infographic Template Templates PDF
This slide represents the growth of the ethical hacking profession, including annual salary, hiring companies, and designation such as information security officer, computer forensics engineer, ethical hacker, and network security engineer. Deliver and pitch your topic in the best possible manner with this growth of ethical hacking profession ppt infographic template templates pdf. Use them to share invaluable insights on growth of ethical hacking profession and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
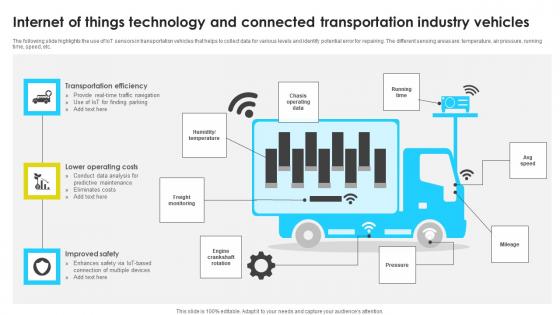
Internet Of Things Technology And Connected Transportation Industry Vehicles Information Pdf
The following slide highlights the use of IoT sensors in transportation vehicles that helps to collect data for various levels and identify potential error for repairing. The different sensing areas are temperature, air pressure, running time, speed, etc. Pitch your topic with ease and precision using this Internet Of Things Technology And Connected Transportation Industry Vehicles Information Pdf This layout presents information on Transportation Efficiency, Lower Operating Costs, Improved Safety It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide highlights the use of IoT sensors in transportation vehicles that helps to collect data for various levels and identify potential error for repairing. The different sensing areas are temperature, air pressure, running time, speed, etc.
Internet Of Things Advantages In Business Ppt PowerPoint Presentation Gallery Icon PDF
Presenting internet of things advantages in business ppt powerpoint presentation gallery icon pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including security system, operational expenditure, rich data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Internet Of Things In Transportation Industry For Supply Chain Management Icons Pdf
The below slide illustrates the IoT transportation advantage for effective supply chain management that leads to food safety promotion. The different benefits provided are tracking, monitoring, and analytics at various levels. Showcasing this set of slides titled Internet Of Things In Transportation Industry For Supply Chain Management Icons Pdf The topics addressed in these templates are Continuous Data Flow, Monitoring, Analytics, Tracking All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The below slide illustrates the IoT transportation advantage for effective supply chain management that leads to food safety promotion. The different benefits provided are tracking, monitoring, and analytics at various levels.
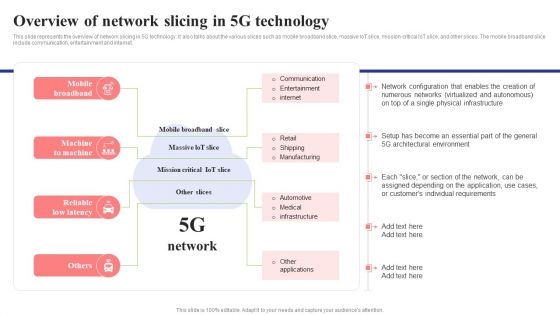
Overview Of Network Slicing In 5G Technology 5G Network Structure Graphics PDF
This slide represents the overview of network slicing in 5G technology. It also talks about the various slices such as mobile broadband slice, massive IoT slice, mission-critical IoT slice, and other slices. The mobile broadband slice include communication, entertainment and internet.This Overview Of Network Slicing In 5G Technology 5G Network Structure Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Overview Of Network Slicing In 5G Technology 5G Network Structure Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, Do not wait, grab the presentation templates today.
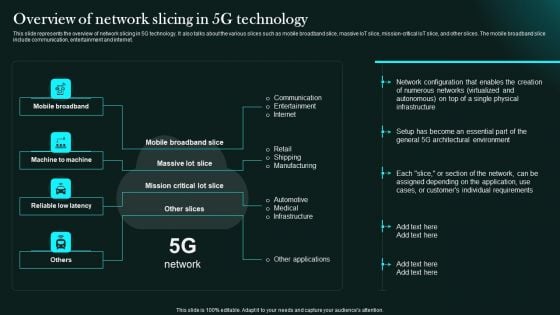
Overview Of Network Slicing In 5G Technology 5G Network Functional Architecture Pictures PDF
This slide represents the overview of network slicing in 5G technology. It also talks about the various slices such as mobile broadband slice, massive IoT slice, mission-critical IoT slice, and other slices. The mobile broadband slice include communication, entertainment and internet.Welcome to our selection of the Overview Of Network Slicing In 5G Technology 5G Network Functional Architecture Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

Overview Of Pneumatic Waste Collection Step By Step Guide For Electronic Ppt Template
This slide exhibits an overview of pneumatic pipes IoT technology that helps in intelligent waste collection scheduling from multiple inlet points. It includes key benefits such as enhanced logistics, health and safety, and cost efficiency. Slidegeeks has constructed Overview Of Pneumatic Waste Collection Step By Step Guide For Electronic Ppt Template after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide exhibits an overview of pneumatic pipes IoT technology that helps in intelligent waste collection scheduling from multiple inlet points. It includes key benefits such as enhanced logistics, health and safety, and cost efficiency.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access Roadmap To Implement Zero Trust Network Access Model
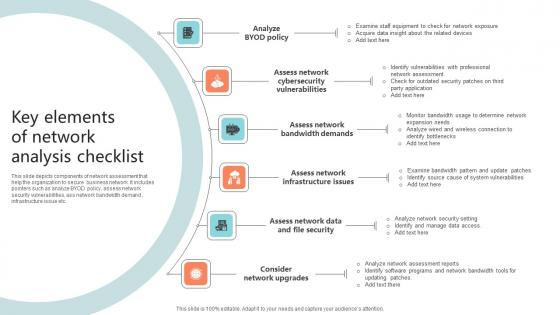
Key Elements Of Network Analysis Checklist Microsoft Pdf
This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.Pitch your topic with ease and precision using this Key Elements Of Network Analysis Checklist Microsoft Pdf This layout presents information on Cybersecurity Vulnerabilities, Bandwidth Demands, Assess Network It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.
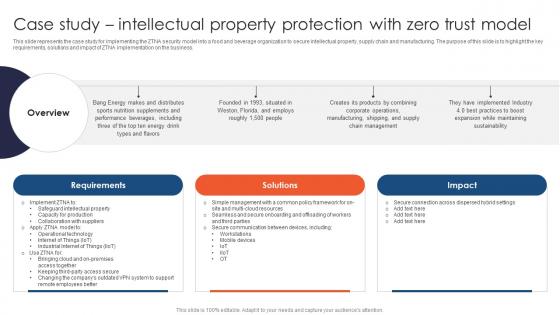
Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

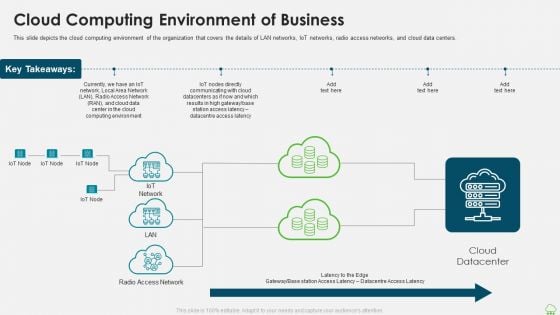
Concurrent Computing Cloud Computing Environment Of Business Ppt Infographics Inspiration PDF
This slide depicts the cloud computing environment of the organization that covers the details of LAN networks, IoT networks, radio access networks, and cloud data centers. Deliver an awe inspiring pitch with this creative concurrent computing cloud computing environment of business ppt infographics inspiration pdf bundle. Topics like communicating, datacentre, environment, computing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Distributed Computing IT Cloud Computing Environment Of Business Inspiration PDF
This slide depicts the cloud computing environment of the organization that covers the details of LAN networks, IoT networks, radio access networks, and cloud data centers. Deliver an awe inspiring pitch with this creative distributed computing it cloud computing environment of business inspiration pdf bundle. Topics like communicating, computing environment, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
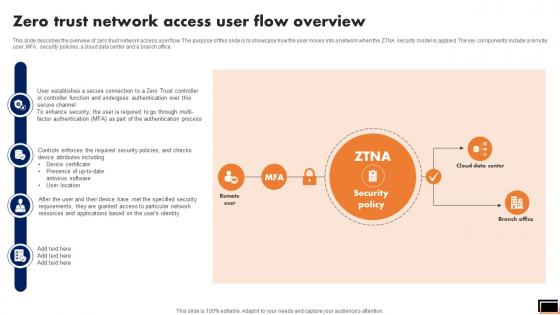
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Login For Income Statement Powerpoint Template
Our above slide display graphics of log in page on mobile phone with money flowing out of tap. Download this diagram slide to display security measures for money saving account. Adjust the above diagram in your business presentations to visually support your content.
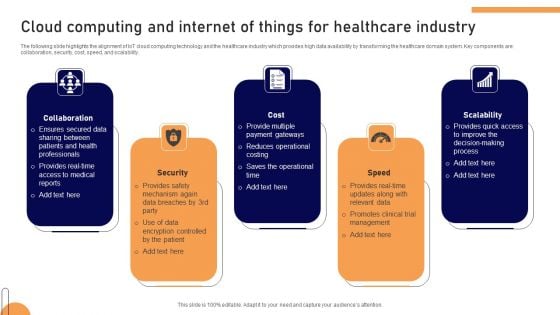
Cloud Computing And Internet Of Things For Healthcare Industry Ideas PDF
Networking Device Icon Circle Arrow Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name networking device icon circle arrow ppt powerpoint presentation complete deck. The topics discussed in these slides are technology, router device, circle, arrow, security shield. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Software Defined Perimeter SDP Roadmap To Implement Zero Trust Network Access Model
This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the business existing security model, etc. Boost your pitch with our creative Software Defined Perimeter SDP Roadmap To Implement Zero Trust Network Access Model. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the business existing security model, etc.
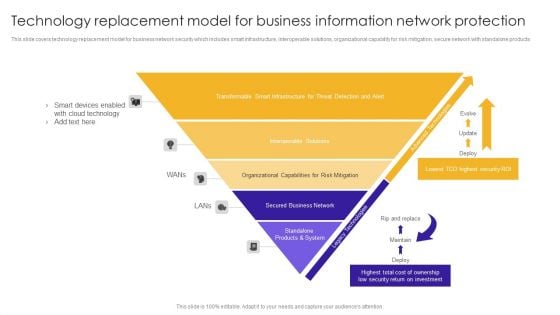
Technology Replacement Model For Business Information Network Protection Structure PDF
This slide covers technology replacement model for business network security which includes smart infrastructure, interoperable solutions, organizational capability for risk mitigation, secure network with standalone products.Showcasing this set of slides titled Technology Replacement Model For Business Information Network Protection Structure PDF. The topics addressed in these templates are Smart Devices, Cloud Technology, Transformable Smart. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Zero Trust Model Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Find highly impressive Zero Trust Model Comparison Between Zero Trust Model SDP And VPN on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Comparison Between Zero Trust Model SDP And VPN for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
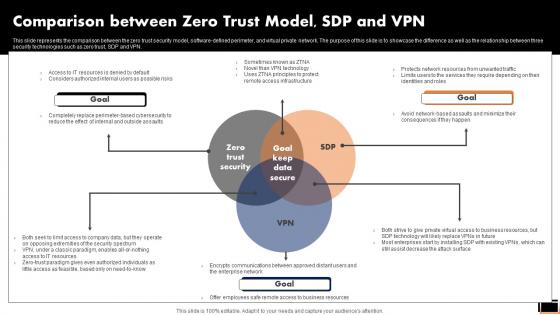
Comparison Between Zero Trust ModelSDP And Vpn Software Defined Perimeter SDP
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
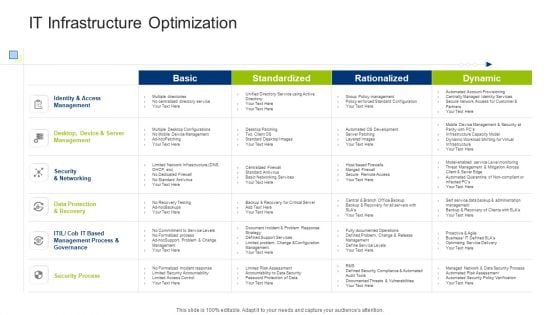
Infrastructure Building Administration IT Infrastructure Optimization Formats PDF
Deliver and pitch your topic in the best possible manner with this infrastructure building administration it infrastructure optimization formats pdf. Use them to share invaluable insights on identity and access management, security and networking, data protection and recovery and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































