Iot Security
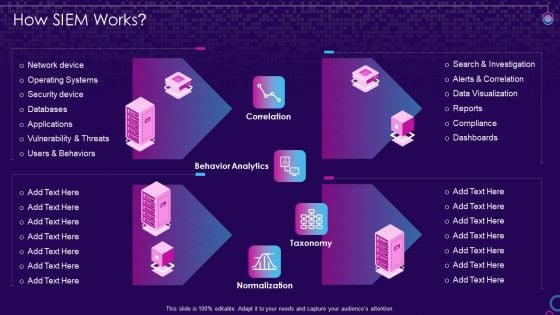
SIEM Services How SIEM Works Ppt Microsoft PDF
Deliver an awe inspiring pitch with this creative siem services how siem works ppt microsoft pdf bundle. Topics like network device, operating systems, security device, vulnerability and threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Management Elements Shown Through Three Gears Ppt PowerPoint Presentation Icon Files PDF
Presenting it management elements shown through three gears ppt powerpoint presentation icon files pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
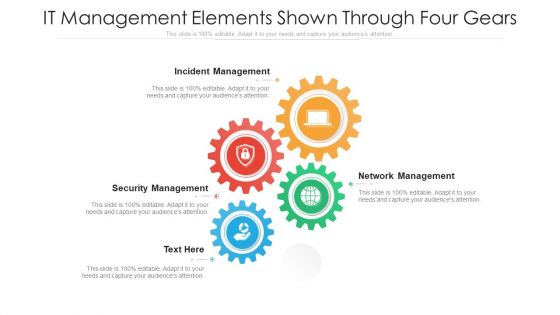
IT Management Elements Shown Through Four Gears Ppt PowerPoint Presentation Gallery Clipart Images PDF
Presenting it management elements shown through four gears ppt powerpoint presentation gallery clipart images pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
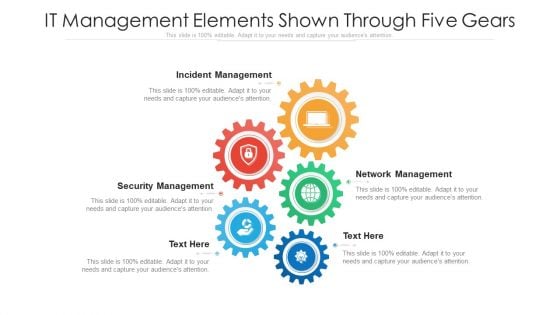
IT Management Elements Shown Through Five Gears Ppt PowerPoint Presentation File Portfolio PDF
Presenting it management elements shown through five gears ppt powerpoint presentation file portfolio pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
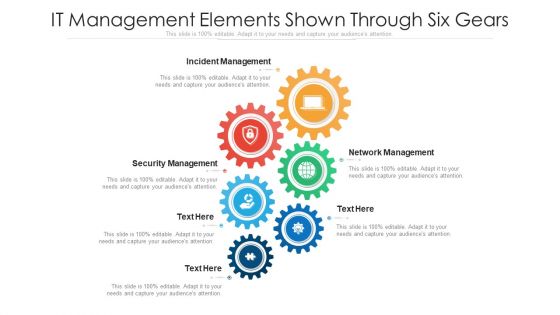
IT Management Elements Shown Through Six Gears Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting it management elements shown through six gears ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Management Elements Shown Through Seven Gears Ppt PowerPoint Presentation Gallery Example PDF
Presenting it management elements shown through seven gears ppt powerpoint presentation gallery example pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Metering Management Diagram Good Ppt Example
This is a smart metering management diagram good ppt example. This is a eight stage process. The stages in this process are reporting, customer information system, billing system, asset management, network information system, security manager, dc persistency, monitoring and control, meter data management.

Kubernetes Containers Architecture Overview Table Of Content Ppt Summary Layout Ideas PDF
Presenting this set of slides with name kubernetes containers architecture overview table of content ppt summary layout ideas pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.
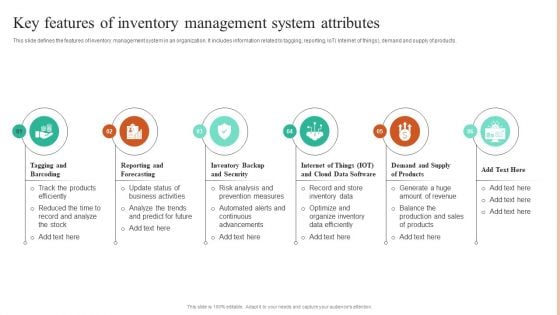
Key Features Of Inventory Management System Attributes Brochure PDF
This slide defines the features of inventory management system in an organization. It includes information related to tagging, reporting, IoT Internet of things, demand and supply of products. Persuade your audience using this Key Features Of Inventory Management System Attributes Brochure PDF. This PPT design covers Six stages, thus making it a great tool to use. It also caters to a variety of topics including Tagging and Barcoding, Reporting and Forecasting, Inventory Backup and Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
Zero Trust Network Access Performance Tracking Dashboard
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Want to ace your presentation in front of a live audience Our Zero Trust Network Access Performance Tracking Dashboard can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
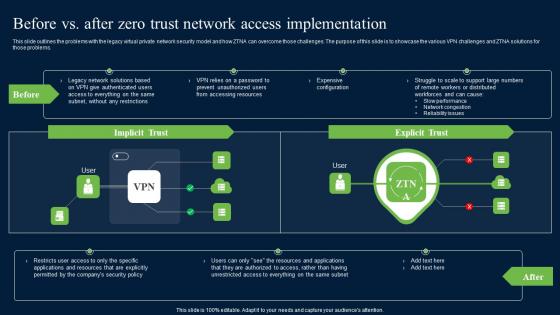
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

A47 Roadmap To Implement Zero Trust Network Access Model
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Find a pre-designed and impeccable A47 Roadmap To Implement Zero Trust Network Access Model. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

A51 Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Want to ace your presentation in front of a live audience Our A51 Zero Trust Network Access Implementation Challenges can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on

Zero Trust Network Access Implementation Challenges Mockup Pdf
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Get a simple yet stunning designed Zero Trust Network Access Implementation Challenges Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Network Access Implementation Challenges Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Zero Trust Model Roadmap To Implement Zero Trust Network Access Model
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Find a pre-designed and impeccable Zero Trust Model Roadmap To Implement Zero Trust Network Access Model. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Zero Trust Model Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Model Zero Trust Network Access Implementation Challenges from Slidegeeks and deliver a wonderful presentation. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Zero Trust Network Access Implementation Challenges Software Defined Perimeter SDP
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Network Access Implementation Challenges Software Defined Perimeter SDP from Slidegeeks and deliver a wonderful presentation. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Zero Trust Network Access Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Access Step 3 Assess The Environment and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Zero Trust Network Access Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Network Access Difference Between ZTNA And Software Defined Perimeter from Slidegeeks and deliver a wonderful presentation. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
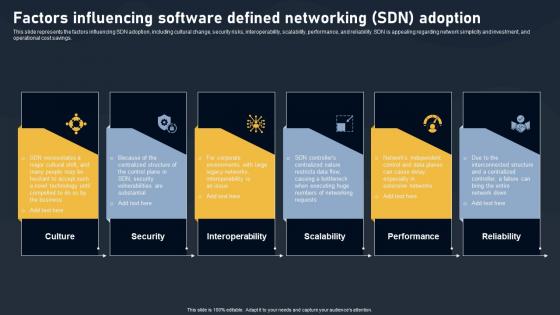
Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.Slidegeeks has constructed Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Why Invest With Us Digital Payment Platform Pitch Deck
This slide mentions the various reasons why potential investors should be investing with the company. Key reasons strong product offering, ROI for investors, security and privacy, AI integrated technology, investment option, growing user base. Explore a selection of the finest Why Invest With Us Digital Payment Platform Pitch Deck here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Why Invest With Us Digital Payment Platform Pitch Deck to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide mentions the various reasons why potential investors should be investing with the company. Key reasons strong product offering, ROI for investors, security and privacy, AI integrated technology, investment option, growing user base.
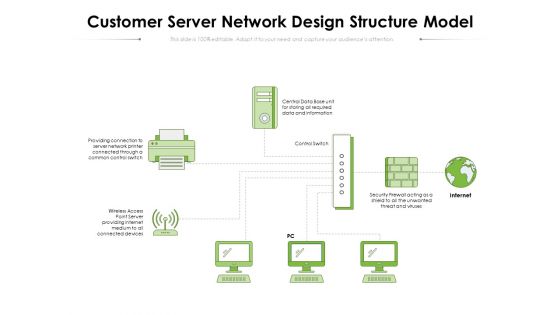
Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf today and make your presentation stand out from the rest This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
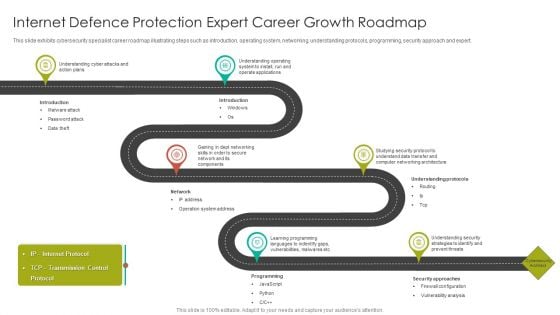
Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
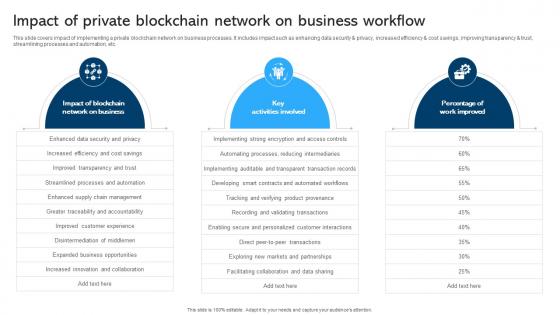
Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V
This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc.
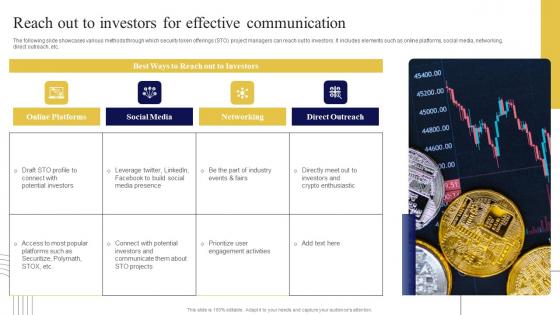
Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf
The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc. Slidegeeks is here to make your presentations a breeze with Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc.

Mobile Cloud Computing Challenges And Solutions Application Areas Of Mobile Cloud Computing
The given slide highlights the various challenges associated with mobile cloud computing along with desired solutions and impacts. The issues include less network bandwidth, network connectivity, and security concern. Retrieve professionally designed Mobile Cloud Computing Challenges And Solutions Application Areas Of Mobile Cloud Computing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The given slide highlights the various challenges associated with mobile cloud computing along with desired solutions and impacts. The issues include less network bandwidth, network connectivity, and security concern

Components Of SCM Connectivity Integration And Coordination Ppt PowerPoint Presentation File Pictures PDF
Persuade your audience using this components of scm connectivity integration and coordination ppt powerpoint presentation file pictures pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including transport connectivity, commercial integration, customs and security integration, regulatory integration, planning and funding integration, work practices integration, information system integration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Career With Cisco Certified Network Associate CCNA Professional PDF
This slide covers details about Cisco Certified Network Associate CCNA certification including career with CCNA, salary expectations, job responsibilities etc. Deliver and pitch your topic in the best possible manner with this Career With Cisco Certified Network Associate CCNA Professional PDF. Use them to share invaluable insights on Network Fundamentals, Security Fundamentals, Automation Programmability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
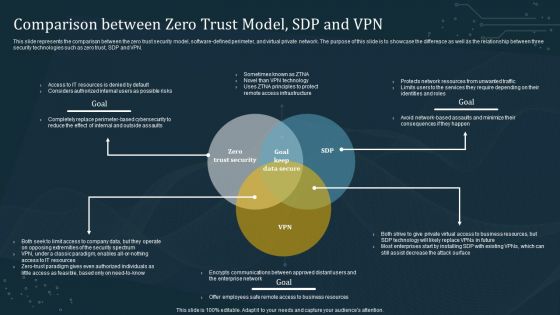
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
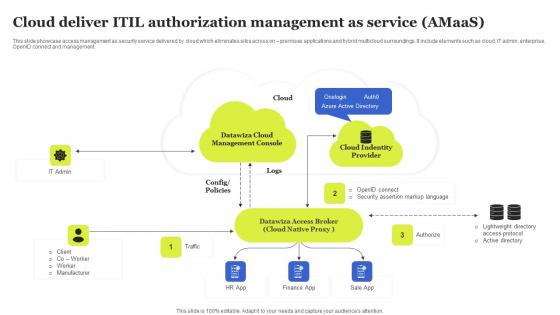
Cloud Deliver ITIL Authorization Management As Service Amaas Sample Pdf
This slide showcase access management as security service delivered by cloud which eliminates silos across on premises applications and hybrid multicloud surroundings. It include elements such as cloud, IT admin, enterprise, OpenID connect and management. Showcasing this set of slides titled Cloud Deliver ITIL Authorization Management As Service Amaas Sample Pdf The topics addressed in these templates are Management Console, Datawiza Access, Cloud Identity All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase access management as security service delivered by cloud which eliminates silos across on premises applications and hybrid multicloud surroundings. It include elements such as cloud, IT admin, enterprise, OpenID connect and management.

Online Payment Techniques Challenges Faced By Business In Adopting Cashless
Mentioned slide showcases various challenges in implementation of cashless payment system in business. It includes challenges such as customer restrain, high processing fees, security issues, difficulty to adopt cashless technology and regular internet services. Explore a selection of the finest Online Payment Techniques Challenges Faced By Business In Adopting Cashless here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Online Payment Techniques Challenges Faced By Business In Adopting Cashless to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide showcases various challenges in implementation of cashless payment system in business. It includes challenges such as customer restrain, high processing fees, security issues, difficulty to adopt cashless technology and regular internet services.
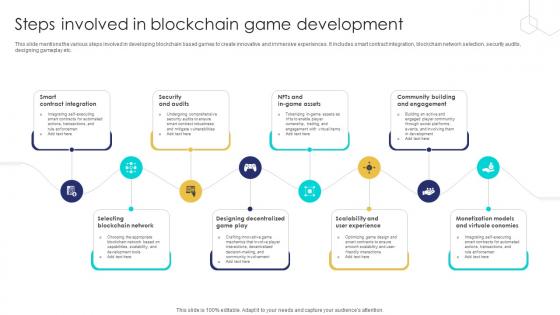
Unlocking The Potential Of Steps Involved In Blockchain Game Development BCT SS V
This slide mentions the various steps involved in developing blockchain based games to create innovative and immersive experiences. It includes smart contract integration, blockchain network selection, security audits, designing gameplay etc. Are you searching for a Unlocking The Potential Of Steps Involved In Blockchain Game Development BCT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Unlocking The Potential Of Steps Involved In Blockchain Game Development BCT SS V from Slidegeeks today. This slide mentions the various steps involved in developing blockchain based games to create innovative and immersive experiences. It includes smart contract integration, blockchain network selection, security audits, designing gameplay etc.
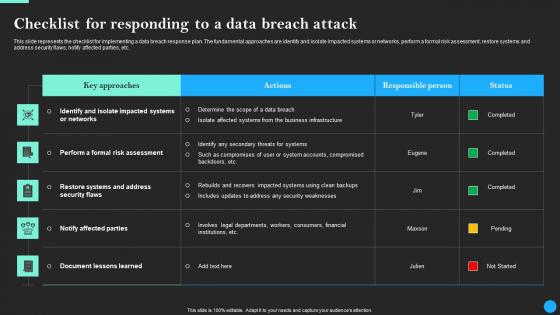
Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.

Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.

Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf
This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty.

Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Slidegeeks is here to make your presentations a breeze with Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security
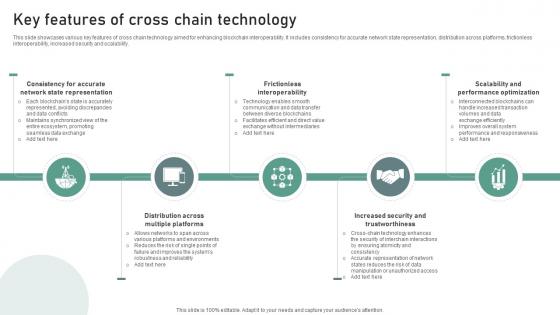
Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Slidegeeks has constructed Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.
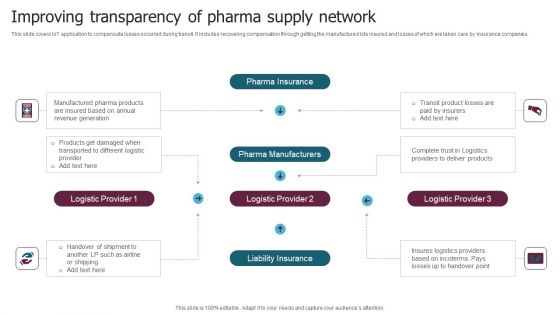
Improving Transparency Of Pharma Supply Network Slides PDF
This slide covers IoT application to compensate losses occurred during transit. It includes recovering compensation through getting the manufactured lots insured and losses of which are taken care by insurance companies. Pitch your topic with ease and precision using this Improving Transparency Of Pharma Supply Network Slides PDF. This layout presents information on Pharma Insurance, Pharma Manufacturers, Liability Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
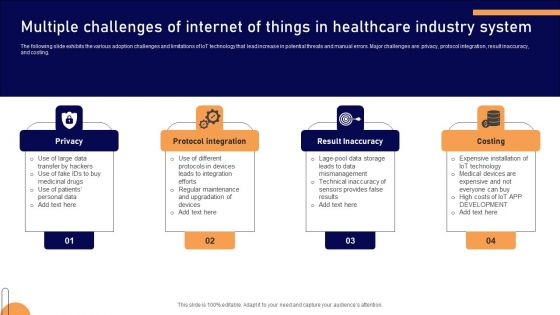
Multiple Challenges Of Internet Of Things In Healthcare Industry System Slides PDF
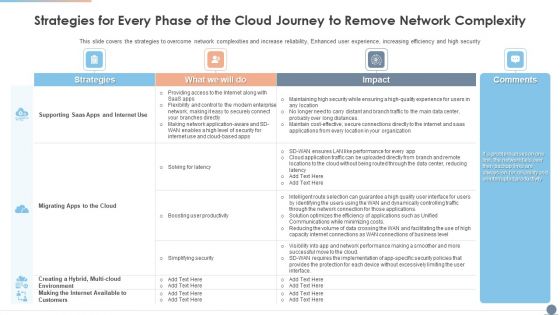
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Deliver and pitch your topic in the best possible manner with this Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF. Use them to share invaluable insights on Environment, Strategies, Productivity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
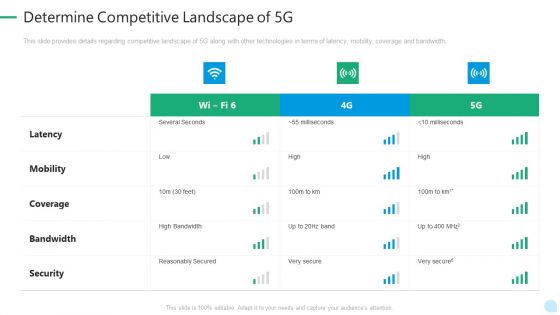
5G Network Technology Determine Competitive Landscape Of 5G Ppt Summary Visual Aids PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver and pitch your topic in the best possible manner with this 5g network technology determine competitive landscape of 5g ppt summary visual aids pdf. Use them to share invaluable insights on latency, mobility, coverage, bandwidth, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
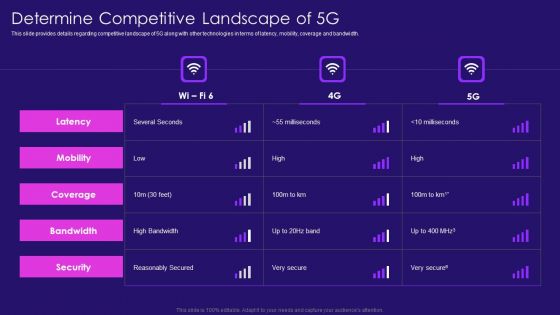
Determine Competitive Landscape Of 5G 5G Network Architecture Instructions Information PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver an awe inspiring pitch with this creative Determine Competitive Landscape Of 5G 5G Network Architecture Instructions Information PDF bundle. Topics like Bandwidth, Coverage, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
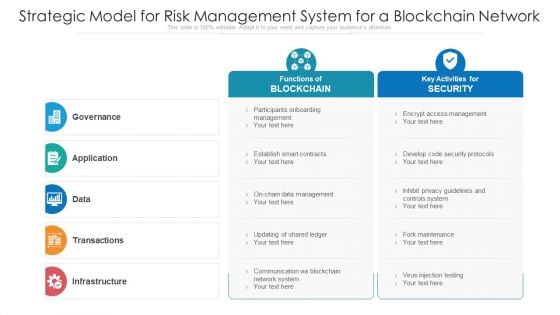
Strategic Model For Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Professional Example File PDF
Persuade your audience using this strategic model for risk management system for a blockchain network ppt powerpoint presentation professional example file pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Participants Onboarding Management, Encrypt Access Management, Develop Code Security Protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
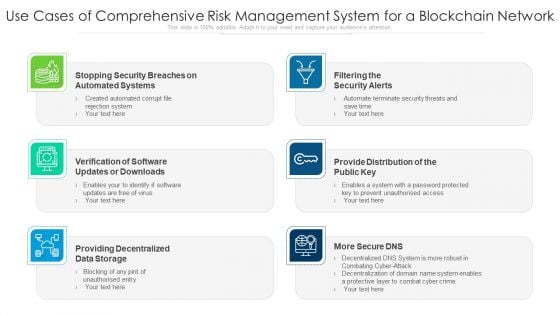
Use Cases Of Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Outline Background Designs PDF
Presenting use cases of comprehensive risk management system for a blockchain network ppt powerpoint presentation outline background designs pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including filtering the security alerts, provide distribution of the public key, providing decentralized data storage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
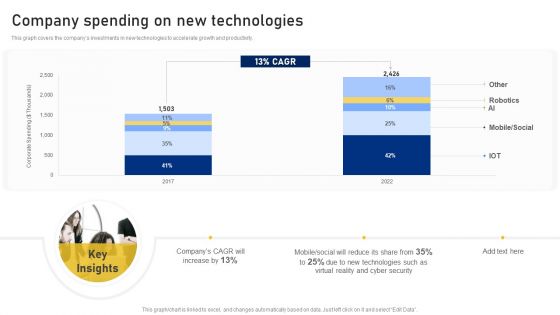
Reshaping Business In Digital Company Spending On New Technologies Clipart PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Reshaping Business In Digital Company Spending On New Technologies Clipart PDF bundle. Topics like Corporate Spending, New Technologies, Cyber Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
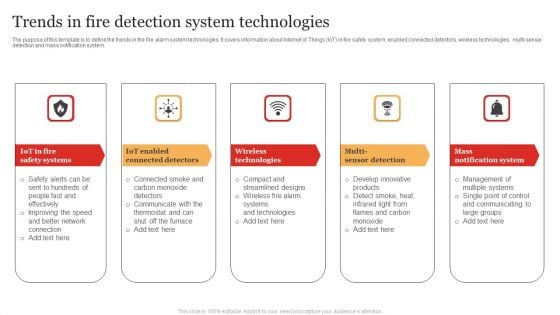
Trends In Fire Detection System Technologies Pictures PDF
The purpose of this template is to define the trends in the fire alarm system technologies. It covers information about Internet of Things IoT in fire safety system, enabled connected detectors, wireless technologies, multi sensor detection and mass notification system.Presenting Trends In Fire Detection System Technologies Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Safety Systems, Connected Detectors, Wireless Technologies. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
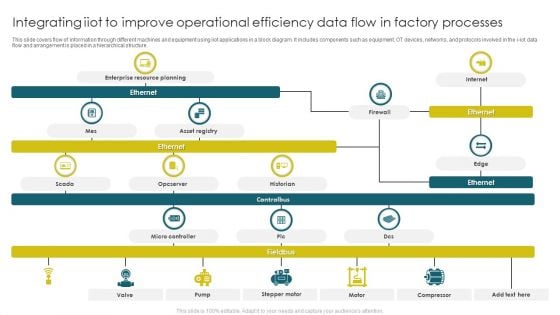
Integrating Iiot To Improve Operational Efficiency Data Flow In Factory Processes Brochure PDF
This slide covers flow of information through different machines and equipment using iiot applications in a block diagram. It includes components such as equipment, OT devices, networks, and protocols involved in the i iot data flow and arrangement is placed in a hierarchical structure. Showcasing this set of slides titled Integrating Iiot To Improve Operational Efficiency Data Flow In Factory Processes Brochure PDF. The topics addressed in these templates are Enterprise Resource Planning, Asset Registry, Micro Controller. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
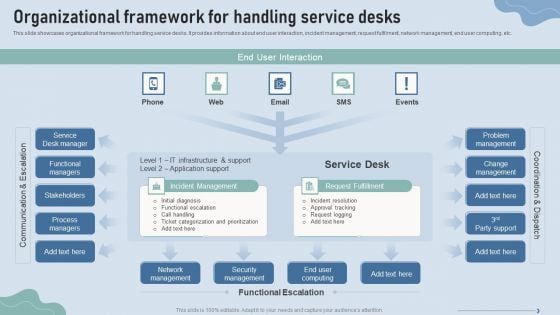
Improve IT Service Desk Organizational Framework For Handling Service Desks Background PDF
This slide showcases organizational framework for handling service desks. It provides information about end user interaction, incident management, request fulfilment, network management, end user computing, etc. Deliver and pitch your topic in the best possible manner with this Improve IT Service Desk Organizational Framework For Handling Service Desks Background PDF. Use them to share invaluable insights on Security Management, Network Management, Incident Resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
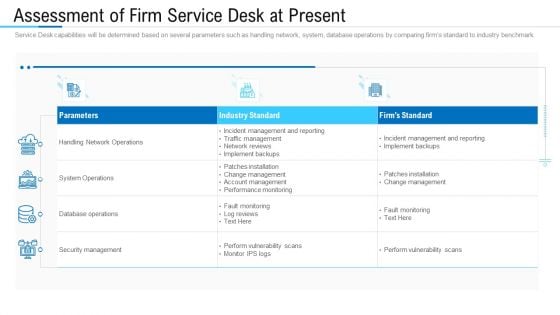
Information Technology Facility Flow Administration Assessment Of Firm Service Desk At Present Brochure PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver and pitch your topic in the best possible manner with this information technology facility flow administration assessment of firm service desk at present brochure pdf. Use them to share invaluable insights on network operations, security management, database operations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
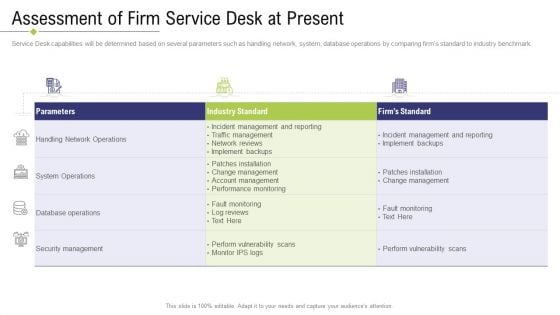
Technology Facility Maintenance And Provider Assessment Of Firm Service Desk At Present Brochure PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver an awe inspiring pitch with this creative technology facility maintenance and provider assessment of firm service desk at present brochure pdf bundle. Topics like system operations, security management, performance monitoring, network reviews, database operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Assessment Of Firm Service Desk At Present Ppt Professional Files PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver and pitch your topic in the best possible manner with this assessment of firm service desk at present ppt professional files pdf. Use them to share invaluable insights on database operations, security management, network operations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
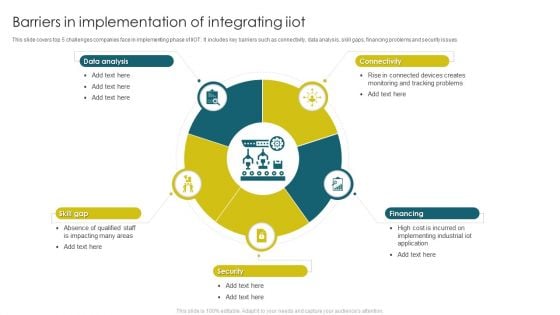
Barriers In Implementation Of Integrating Iiot Infographics PDF
This slide covers top 5 challenges companies face in implementing phase of IIOT. It includes key barriers such as connectivity, data analysis, skill gaps, financing problems and security issues. Presenting Barriers In Implementation Of Integrating Iiot Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Analysis, Connectivity, Financing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































