Iot Security
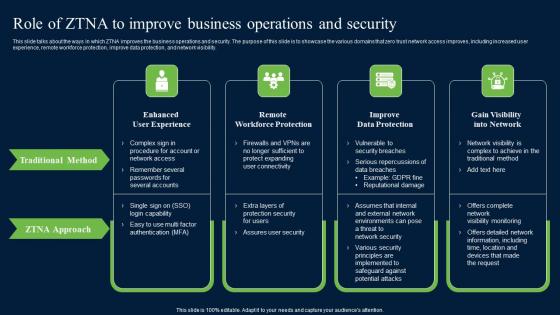
Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
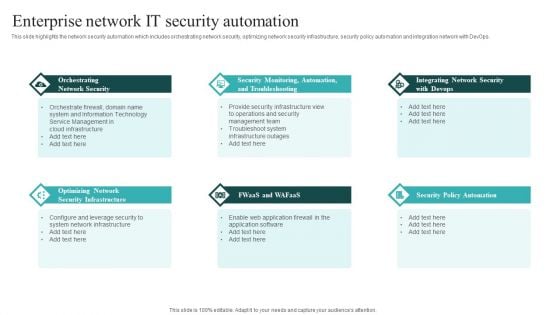
IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
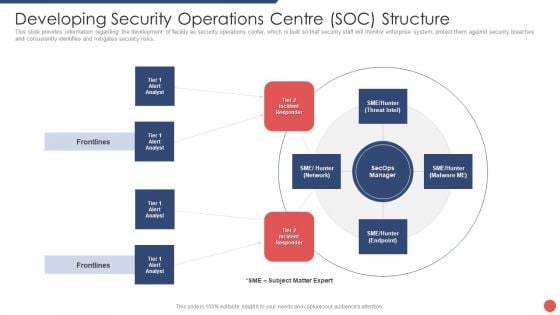
Security Functioning Centre Developing Security Operations Centre SOC Structure Guidelines PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Deliver and pitch your topic in the best possible manner with this security functioning centre developing security operations centre soc structure guidelines pdf. Use them to share invaluable insights on incident responder, analyst, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
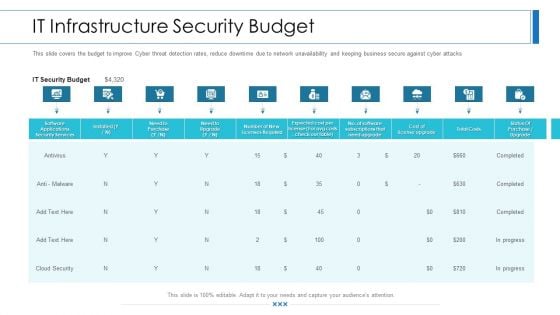
Workforce Security Realization Coaching Plan IT Infrastructure Security Budget Background PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan it infrastructure security budget background pdf bundle. Topics like software applications security services, business, it security budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Infrastructure Security Budget Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe inspiring pitch with this creative it infrastructure security budget hacking prevention awareness training for it security graphics pdf bundle. Topics like security, services, costs, cloud security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
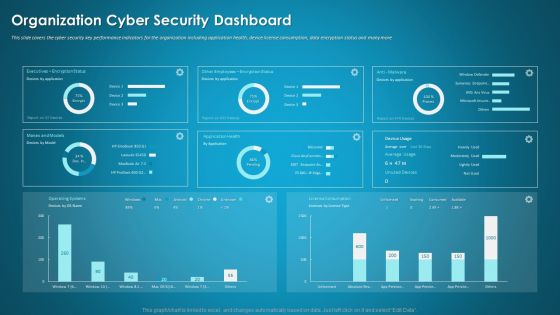
Organizational Network Security Awareness Staff Learning Organization Cyber Security Dashboard Elements PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization cyber security dashboard elements pdf. Use them to share invaluable insights on organization cyber security dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
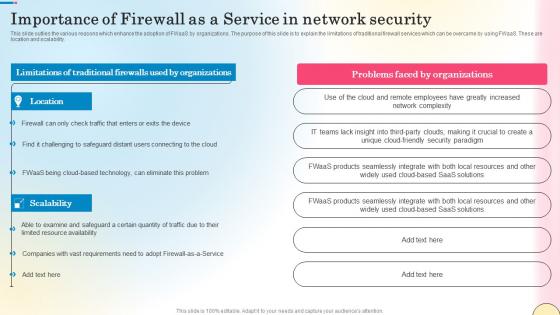
Importance Of Firewall As A Service In Network Security Network Security Designs Pdf
This slide outlies the various reasons which enhance the adoption of FWaaS by organizations. The purpose of this slide is to explain the limitations of traditional firewall services which can be overcame by using FWaaS. These are location and scalability. The Importance Of Firewall As A Service In Network Security Network Security Designs Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlies the various reasons which enhance the adoption of FWaaS by organizations. The purpose of this slide is to explain the limitations of traditional firewall services which can be overcame by using FWaaS. These are location and scalability.

Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, iot-based attack, malware etc. Do you know about Slidesgeeks Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
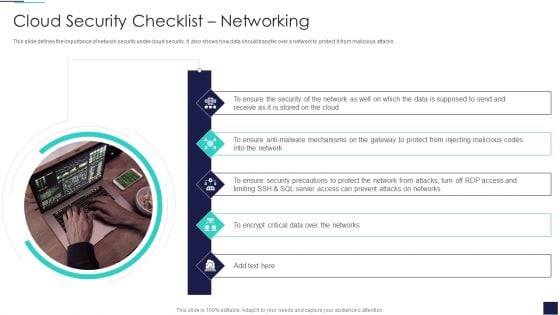
Cloud Information Security Cloud Security Checklist Networking Ppt Infographics Deck PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. This is a Cloud Information Security Cloud Security Checklist Networking Ppt Infographics Deck PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ensure Security, Data Supposed, Encrypt Critical. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
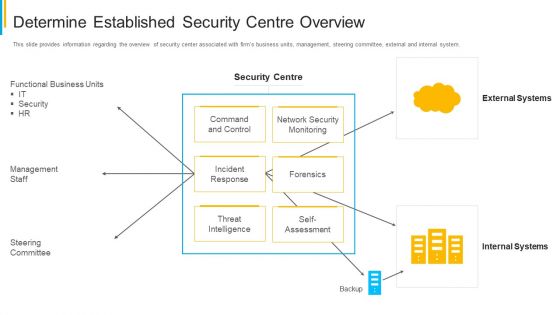
Project Security Administration IT Determine Established Security Centre Overview Infographics PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this project security administration it determine established security centre overview infographics pdf. Use them to share invaluable insights on functional business units, management staff, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

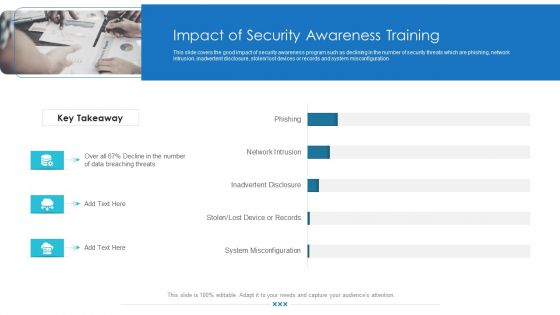
Organizational Network Security Awareness Staff Learning Impact Of Security Awareness Training Microsoft PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning impact of security awareness training microsoft pdf bundle. Topics like impact of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
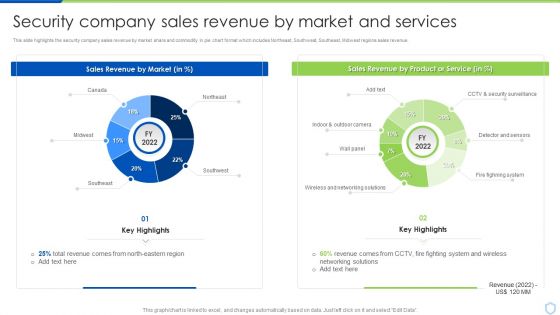
Security And Surveillance Company Profile Security Company Sales Revenue Clipart PDF
This slide highlights the security company sales revenue by market share and commodity in pie chart format which includes Northeast, Southwest, Southeast, Midwest regions sales revenue.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Security Company Sales Revenue Clipart PDF bundle. Topics like Sales Revenue, Security Surveillance, Networking Solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
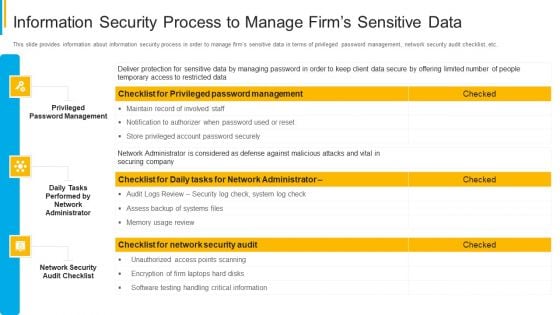
Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
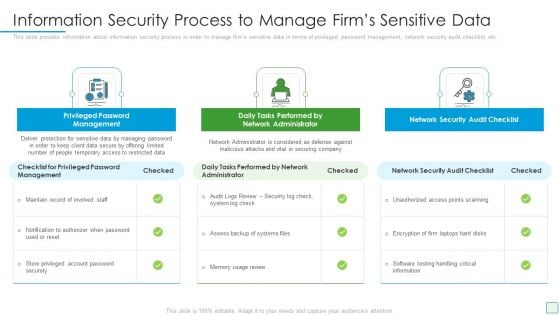
Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Introduction PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. This is a developing firm security strategy plan information security process to manage firms sensitive data introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
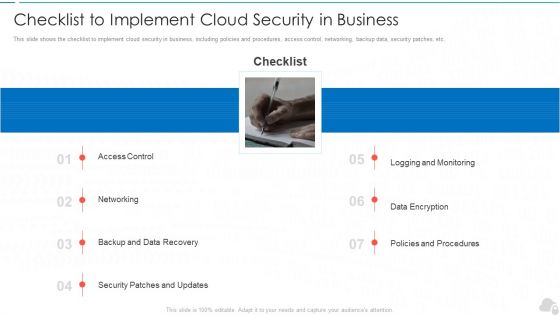
Checklist To Implement Cloud Security In Business Cloud Computing Security IT Ppt Infographic Template Example File
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Deliver an awe inspiring pitch with this creative checklist to implement cloud security in business cloud computing security it ppt infographic template example file bundle. Topics like networking, policies and procedures, logging and monitoring, data encryption, security patches and updates can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
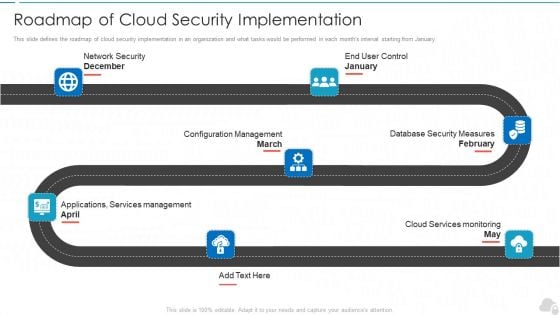
Roadmap Of Cloud Security Implementation Cloud Computing Security IT Ppt Outline Files PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. This is a roadmap of cloud security implementation cloud computing security it ppt outline files pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configuration management, database security measures, cloud services monitoring, applications, services management, network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Workforce Security Realization Coaching Plan Impact Of Security Awareness Training Pictures PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan impact of security awareness training pictures pdf bundle. Topics like impact of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
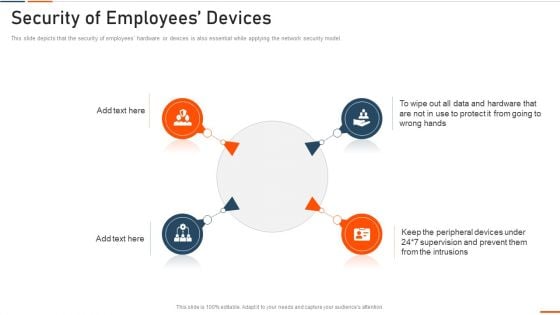
Information Technology Security Security Of Employees Devices Ppt File Portrait PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the network security model. Presenting information technology security security of employees devices ppt file portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Security Awareness Staff Learning IT Infrastructure Security Budget Slides PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning it infrastructure security budget slides pdf. Use them to share invaluable insights on it infrastructure security budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
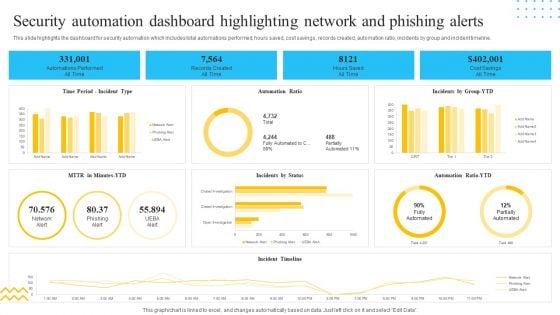
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF bundle. Topics like Records Created, All Time, Hours Saved, Cost Savings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
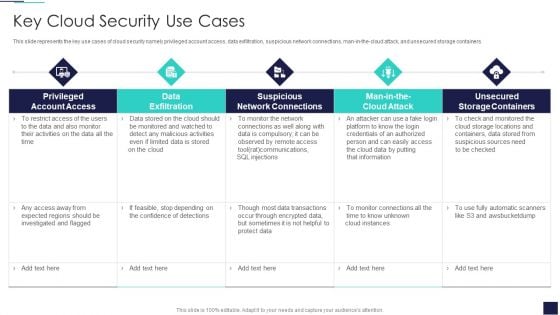
Cloud Information Security Key Cloud Security Use Cases Ppt Gallery Templates PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers. Deliver an awe inspiring pitch with this creative Cloud Information Security Key Cloud Security Use Cases Ppt Gallery Templates PDF bundle. Topics like Privileged Account, Data Exfiltration, Suspicious Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
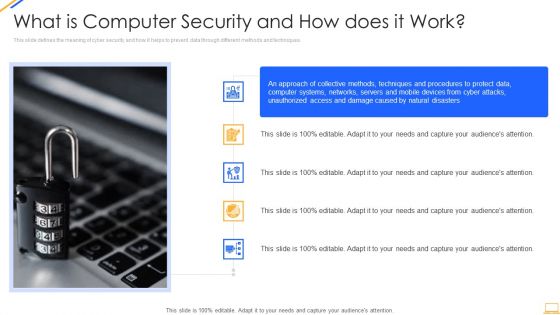
Desktop Security Management What Is Computer Security And How Does It Work Template PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Deliver an awe inspiring pitch with this creative desktop security management what is computer security and how does it work template pdf bundle. Topics like networks, systems, protect data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Global Cloud Based Email Security Market Hosted E Mail Security Portrait PDF
Presenting this set of slides with name global cloud based email security market hosted e mail security portrait pdf. This is a two stage process. The stages in this process are cloud based e mail security system, no maintenance required from it personal, intercepts various miscellaneous contents before it reaches the network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
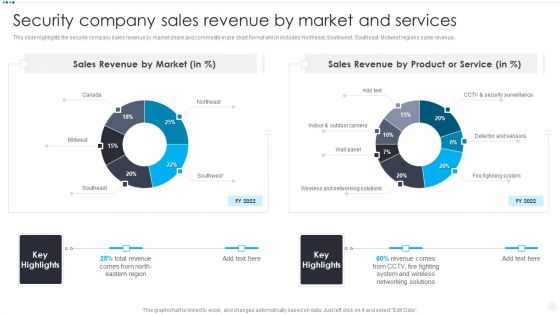
Smart Home Security Solutions Company Profile Security Company Sales Revenue By Market Themes PDF
This slide highlights the security company sales revenue by market share and commodity in pie chart format which includes Northeast, Southwest, Southeast, Midwest regions sales revenue. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Security Company Sales Revenue By Market Themes PDF bundle. Topics like Sales Revenue Market, Sales Revenue Product, Wireless And Networking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
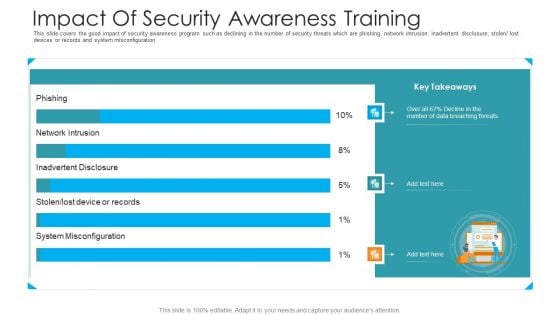
Impact Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Infographics PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe inspiring pitch with this creative impact of security awareness training hacking prevention awareness training for it security infographics pdf bundle. Topics like system misconfiguration, network intrusion breakdown, phishing breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
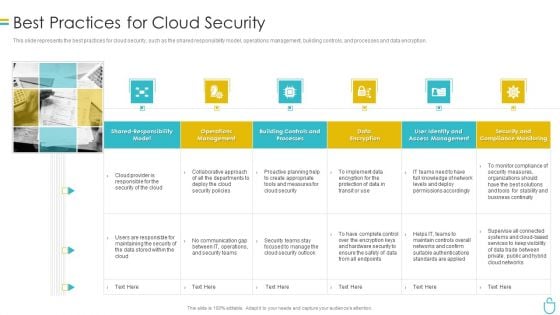
Information Security Best Practices For Cloud Security Ppt Ideas Deck PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting information security best practices for cloud security ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, measures, planning, teams, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Our Security Services And Solutions Slides PDF
This slide highlights the security company services which includes CCTV, mobile app and software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera. Presenting Smart Home Security Solutions Company Profile Our Security Services And Solutions Slides PDF to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like CCTV And Security, Wireless And Networking, Storage And Server, Fire Fighting System. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
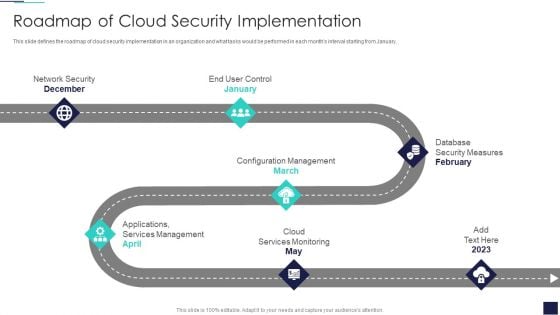
Cloud Information Security Roadmap Of Cloud Security Implementation Ppt Styles PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Cloud Information Security Roadmap Of Cloud Security Implementation Ppt Styles PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Network Security, Configuration Management, Cloud Services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
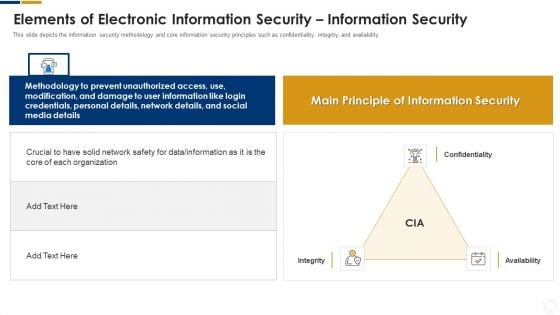
Cybersecurity Elements Of Electronic Information Security Information Security Ppt Pictures Slide PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a cybersecurity elements of electronic information security information security ppt pictures slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, network, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
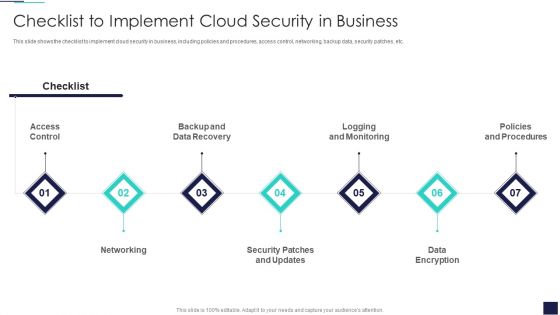
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
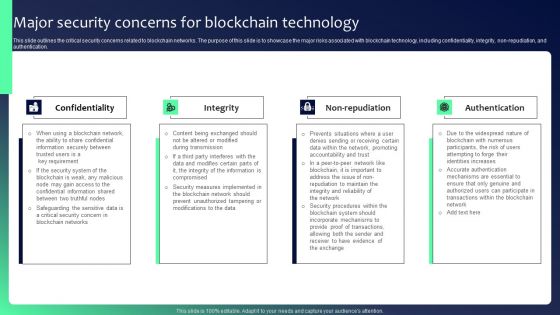
Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF
This slide outlines the critical security concerns related to blockchain networks. The purpose of this slide is to showcase the major risks associated with blockchain technology, including confidentiality, integrity, non-repudiation, and authentication. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF today and make your presentation stand out from the rest
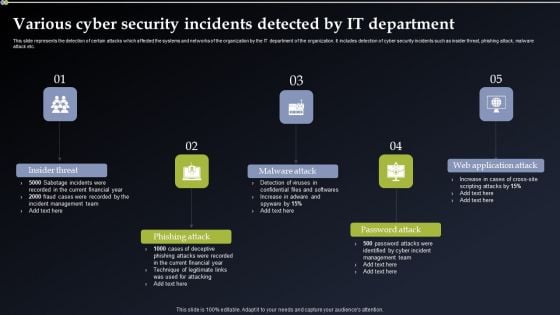
Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you searching for a Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF from Slidegeeks today.
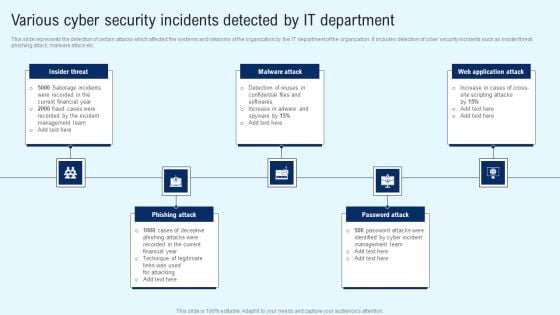
Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
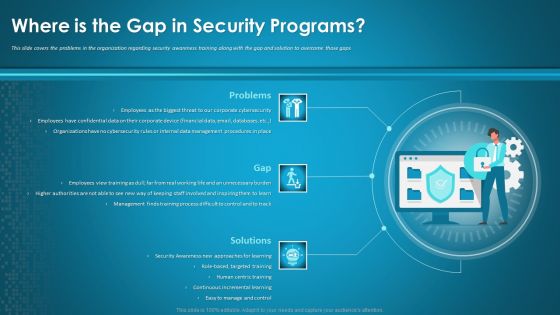
Organizational Network Security Awareness Staff Learning Where Is The Gap In Security Programs Template PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a organizational network security awareness staff learning where is the gap in security programs template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees, management, organizations, targeted training, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
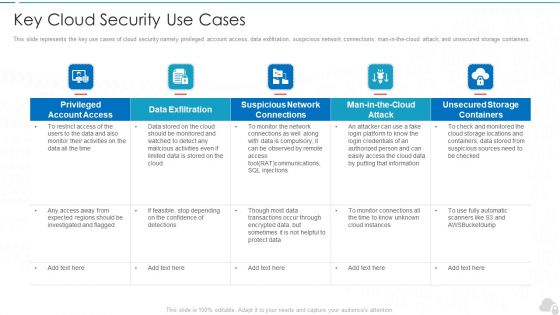
Key Cloud Security Use Cases Cloud Computing Security IT Ppt Visual Aids Ideas PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containe. Deliver an awe inspiring pitch with this creative key cloud security use cases cloud computing security it ppt visual aids ideas pdf bundle. Topics like privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, unsecured storage containers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
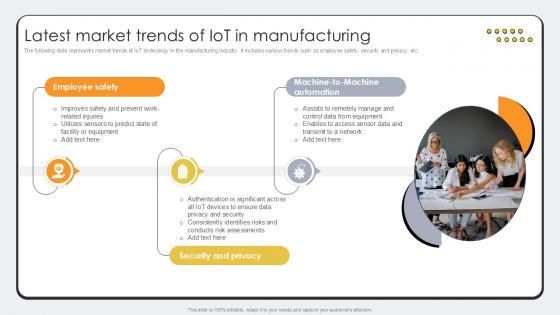
Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example
The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc. Presenting this PowerPoint presentation, titled Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc.
Security And Surveillance Company Profile Our Security Services And Solutions Icons PDF
This slide highlights the security company services which includes CCTV, mobile app software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera.This is a Security And Surveillance Company Profile Our Security Services And Solutions Icons PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Networking Solution, Display Solutions, Occupancy Sensor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile Our Security Services And Solutions Topics PDF
This slide highlights the security company services which includes CCTV, mobile app software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera.Presenting Security Camera System Company Profile Our Security Services And Solutions Topics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Networking Solution, Display Solutions, Occupancy Sensor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
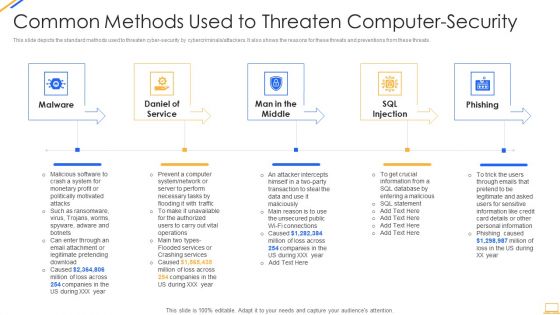
Desktop Security Management Common Methods Used To Threaten Computer Security Template PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a desktop security management common methods used to threaten computer security template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, services, network, database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
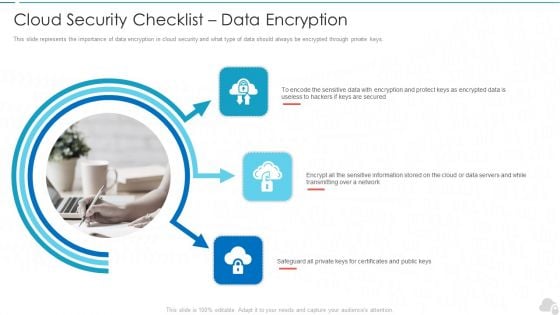
Cloud Security Checklist Data Encryption Cloud Computing Security IT Ppt Summary Tips PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a cloud security checklist data encryption cloud computing security it ppt summary tips pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like safeguard, data servers, network, encryption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
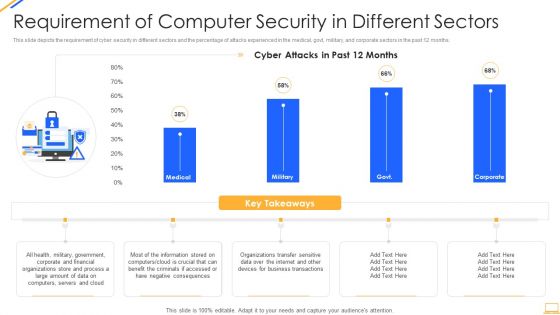
Desktop Security Management Requirement Of Computer Security In Different Sectors Sample PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this desktop security management requirement of computer security in different sectors sample pdf. Use them to share invaluable insights on information, organizations, financial, servers, internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
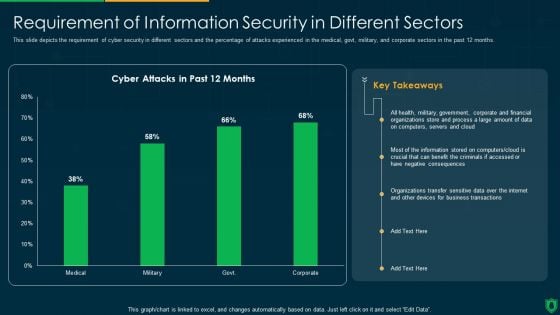
Info Security Requirement Of Information Security In Different Sectors Ppt PowerPoint Presentation File Grid PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative info security requirement of information security in different sectors ppt powerpoint presentation file grid pdf bundle. Topics like cyber attacks, past 12 months, organizations transfer, sensitive data over internet can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
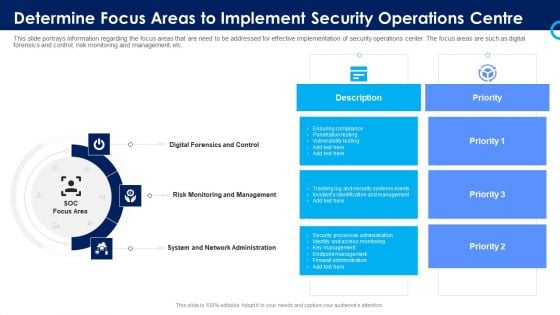
Organizational Security Solutions Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a organizational security solutions determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
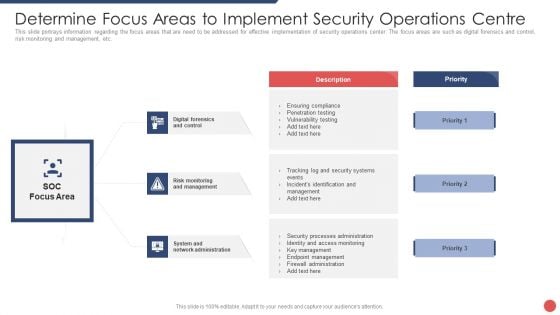
Security Functioning Centre Determine Focus Areas To Implement Security Operations Centre Demonstration PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security functioning centre determine focus areas to implement security operations centre demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk monitoring, management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
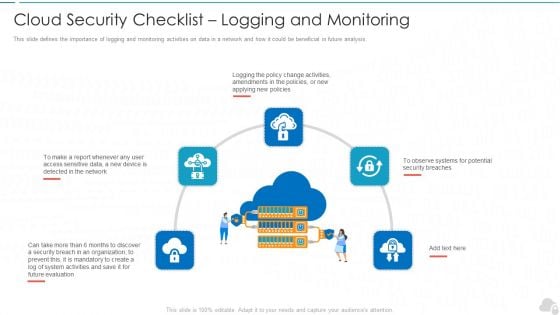
Cloud Security Checklist Logging And Monitoring Cloud Computing Security IT Ppt Show Example PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a cloud security checklist logging and monitoring cloud computing security it ppt show example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluation, organization, policies, potential, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
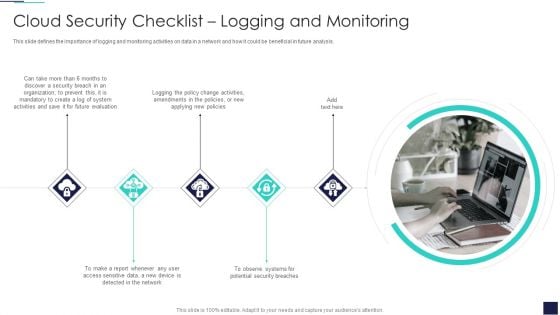
Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Presenting Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Evaluation, New Policies, Potential Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
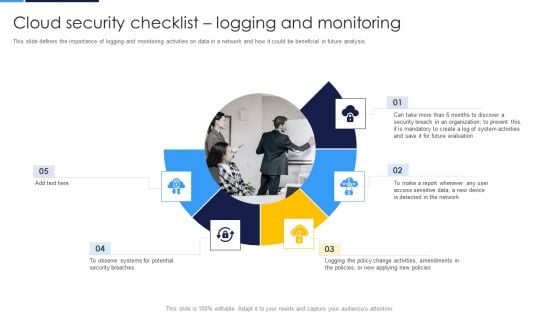
Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
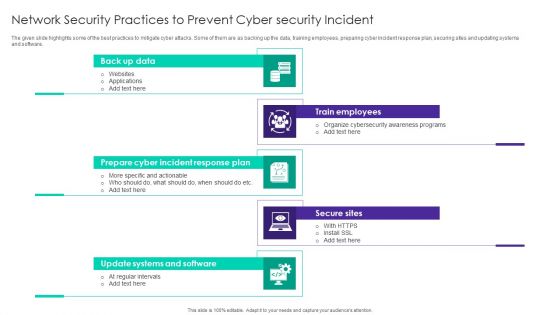
Network Security Practices To Prevent Cyber Security Incident Ppt Visual Aids Infographic Template PDF
The given slide highlights some of the best practices to mitigate cyber attacks. Some of them are as backing up the data, training employees, preparing cyber incident response plan, securing sites and updating systems and software. Persuade your audience using this Network Security Practices To Prevent Cyber Security Incident Ppt Visual Aids Infographic Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Back Up Data, Train Employees, Secure Sites, Prepare Cyber Incident. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Explore a selection of the finest CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
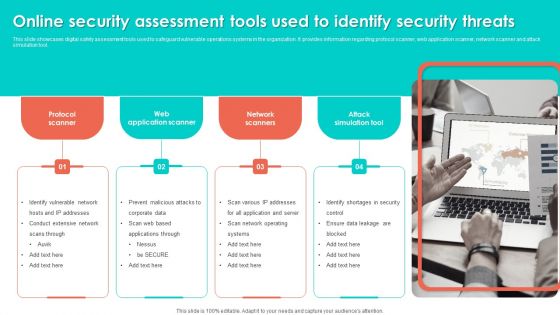
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
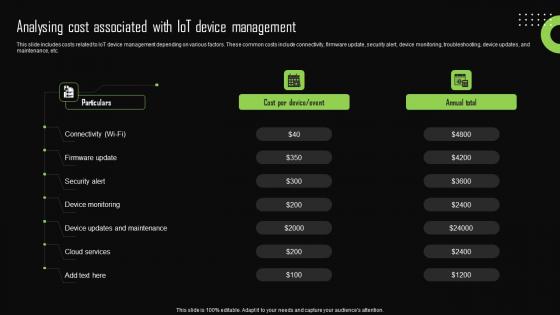
Analysing Cost Associated With Iot Devic Iot Device Management Template Pdf
This slide includes costs related to IoT device management depending on various factors. These common costs include connectivity, firmware update, security alert, device monitoring, troubleshooting, device updates, and maintenance, etc. Create an editable Analysing Cost Associated With Iot Devic Iot Device Management Template Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Analysing Cost Associated With Iot Devic Iot Device Management Template Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide includes costs related to IoT device management depending on various factors. These common costs include connectivity, firmware update, security alert, device monitoring, troubleshooting, device updates, and maintenance, etc.
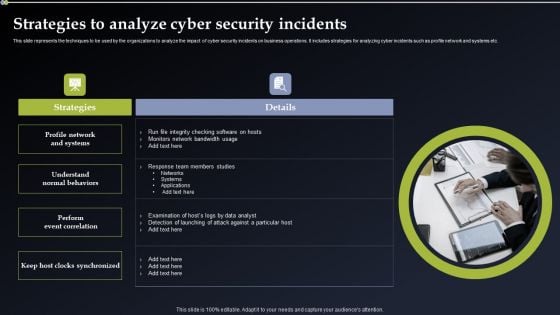
Deploying Cyber Security Incident Response Administration Strategies To Analyze Cyber Security Incidents Template PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Present like a pro with Deploying Cyber Security Incident Response Administration Strategies To Analyze Cyber Security Incidents Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
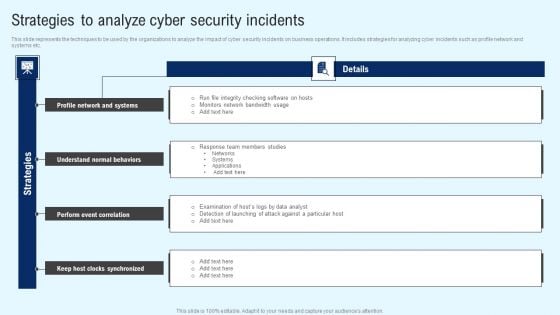
Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks has constructed Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
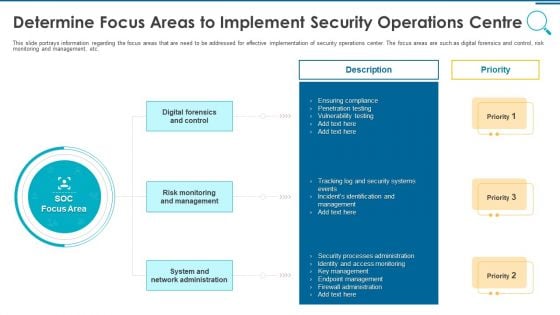
Information And Technology Security Operations Determine Focus Areas To Implement Security Operations Centre Download PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a information and technology security operations determine focus areas to implement security operations centre download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
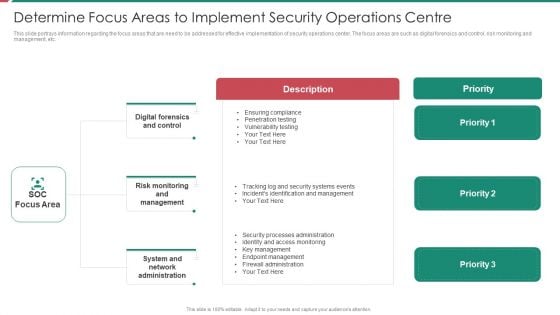
Security And Process Integration Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security and process integration determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Do you know about Slidesgeeks CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
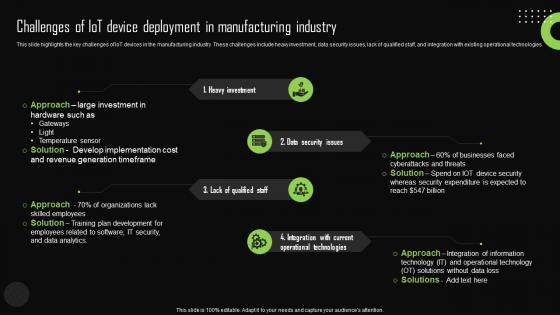
Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf
This slide highlights the key challenges of IoT devices in the manufacturing industry. These challenges include heavy investment, data security issues, lack of qualified staff, and integration with existing operational technologies. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf today and make your presentation stand out from the rest This slide highlights the key challenges of IoT devices in the manufacturing industry. These challenges include heavy investment, data security issues, lack of qualified staff, and integration with existing operational technologies.


 Continue with Email
Continue with Email

 Home
Home


































