Network Security
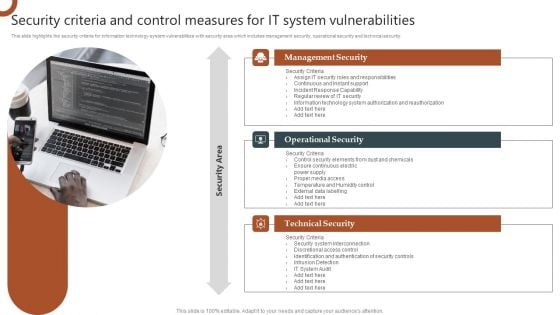
Organizations Risk Management And IT Security Security Criteria And Control Measures For IT System Vulnerabilities Diagrams PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizations Risk Management And IT Security Security Criteria And Control Measures For IT System Vulnerabilities Diagrams PDF can be your best option for delivering a presentation. Represent everything in detail using Organizations Risk Management And IT Security Security Criteria And Control Measures For IT System Vulnerabilities Diagrams PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
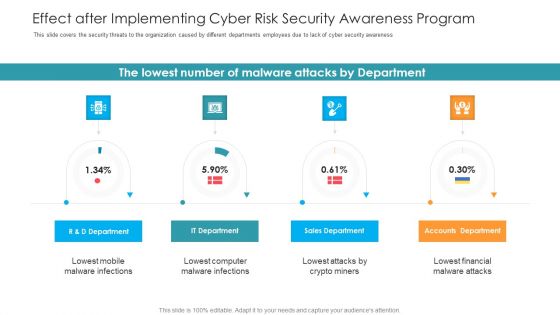
Effect After Implementing Cyber Risk Security Awareness Program Hacking Prevention Awareness Training For IT Security Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative effect after implementing cyber risk security awareness program hacking prevention awareness training for it security information pdf bundle. Topics like accounts department, sales department, it department, r and d department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Remote Summary PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management plan steps in detail remote summary pdf bundle. Topics like requirement for additional, remote access control, control security status can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
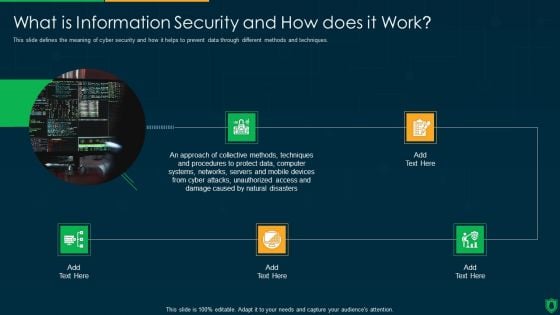
Info Security What Is Information Security And How Does It Work Ppt PowerPoint Presentation File Clipart PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a info security what is information security and how does it work ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collective methods, techniques and procedures, protect data, computer systems, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Malicious Icons PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with malicious icons pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
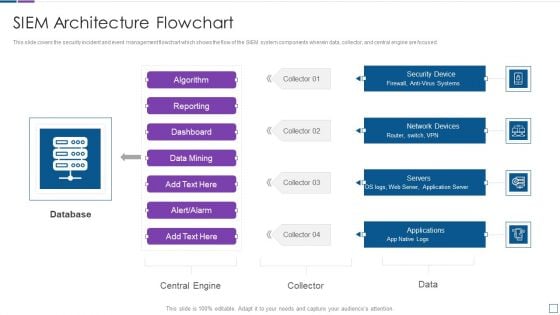
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
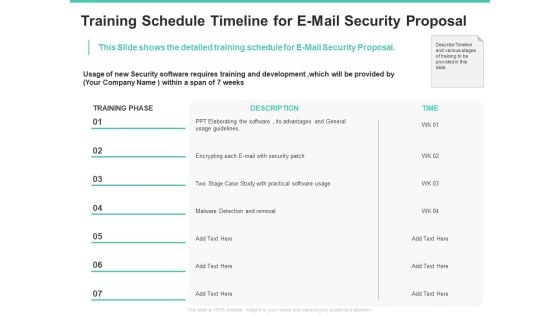
Email Security Encryption And Data Loss Prevention Training Schedule Timeline For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed training schedule for E-Mail Security Proposal. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention training schedule timeline for e mail security proposal diagrams pdf bundle. Topics like case study, security, development, timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
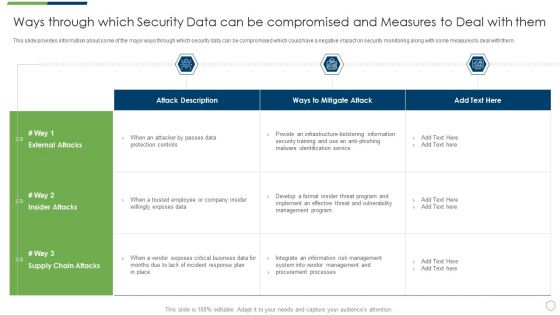
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ways Through Which Security Data Themes PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach ways through which security data themes pdf bundle. Topics like ways through which security data can be compromised and measures to deal with them can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
Best Data Security Software 30 60 90 Days Plan For Company Online Database Security Proposal Sample PDF
Presenting this set of slides with name best data security software 30 60 90 days plan for company online database security proposal sample pdf. This is a three stage process. The stages in this process are 30 60 90 days plan, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
What Are The Benefits Of A Cloud Security System Cloud Computing Security IT Ppt Icon Clipart Images PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. Deliver an awe inspiring pitch with this creative what are the benefits of a cloud security system cloud computing security it ppt icon clipart images pdf bundle. Topics like efficient recovery, openness, no hardware required, ddos protection, efficient data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Topics That Fall Under The Umbrella Of Cloud Security Cloud Computing Security IT Ppt Model Example Introduction PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. Presenting topics that fall under the umbrella of cloud security cloud computing security it ppt model example introduction pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data centre security, threat prevention, access control, threat detection, threat mitigation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
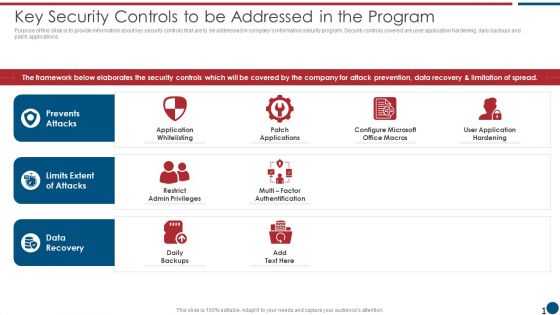
Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF bundle. Topics like Prevents Attacks, Limits Extent, Data Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
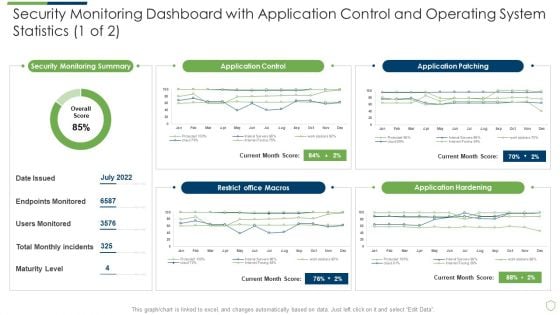
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Application Slides PDF
Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with application slides pdf. Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
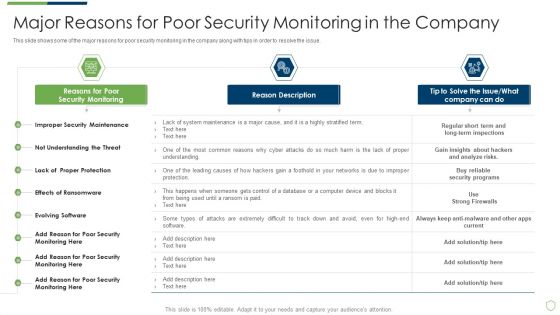
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security What Are The Benefits Of A Cloud Security System Ppt Gallery Infographic Template PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. This is a Cloud Information Security What Are The Benefits Of A Cloud Security System Ppt Gallery Infographic Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Efficient Recovery, DDOS Protection, Efficient Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
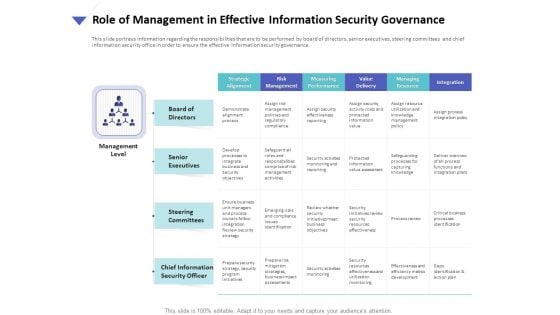
Strategies To Mitigate Cyber Security Risks Role Of Management In Effective Information Security Governance Ppt Model File Formats PDF
Presenting this set of slides with name strategies to mitigate cyber security risks role of management in effective information security governance ppt model file formats pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Content Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Elements PDF
Deliver an awe inspiring pitch with this creative table of content cyber security and phishing awareness training hacking prevention awareness training for it security elements pdf bundle. Topics like training, awareness, strategies, communication, plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Impact Of Critical Security Concerns Issues On Overall Firms Performance Pictures PDF
This slide provides information about the several situations that will result in increase of potential security threats in the organization and addressing various major security concerns at workplace. Deliver an awe inspiring pitch with this creative developing firm security strategy plan impact of critical security concerns issues on overall firms performance pictures pdf bundle. Topics like loss in sales, customer dissatisfaction, tarnished reputation, decrease in customer loyalty, increase in expenses can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
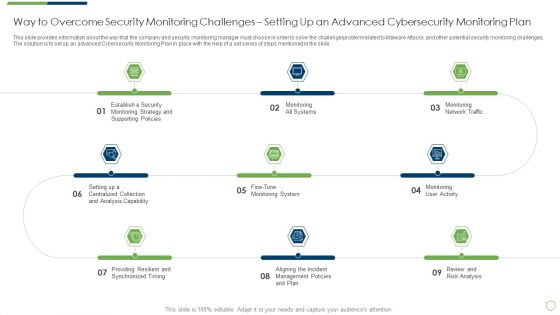
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
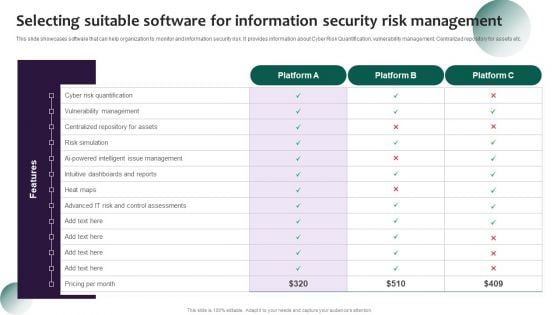
Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF
This slide showcases software that can help organization to monitor and information security risk. It provides information about Cyber Risk Quantification, vulnerability management, Centralized repository for assets etc. Get a simple yet stunning designed Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Uniformed Security We Provide The Following Services For Your Convenience In Security Guard Services Proposal Formats PDF
Deliver an awe inspiring pitch with this creative uniformed security we provide the following services for your convenience in security guard services proposal formats pdf bundle. Topics like training, strategies, policies, management, investigative can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Real Time Assessment Of Security Threats Table Of Contents Real Time Assessment Of Security Threats Mockup PDF
Deliver an awe inspiring pitch with this creative real time assessment of security threats table of contents real time assessment of security threats mockup pdf bundle. Topics like company overview, challenges and solutions, services offered, siem hosting models, siem architecture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Hacking Prevention Awareness Training For IT Security Icons Slide Hacking Prevention Awareness Training For IT Security Information PDF
Introducing our well designed hacking prevention awareness training for it security icons slide hacking prevention awareness training for it security information pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Real Time Assessment Of Security Threats Icons Slide For Real Time Assessment Of Security Threats Sample PDF
Presenting our innovatively structured real time assessment of security threats icons slide for real time assessment of security threats sample pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
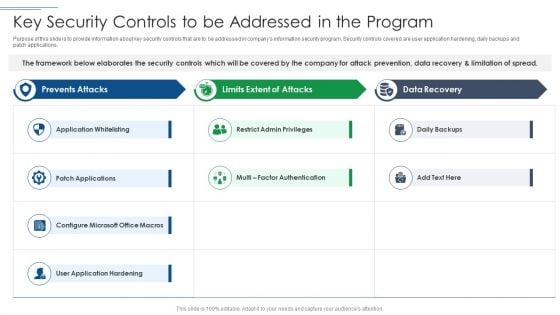
IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF. Use them to share invaluable insights on Application Whitelisting, Patch Applications, User Application Hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
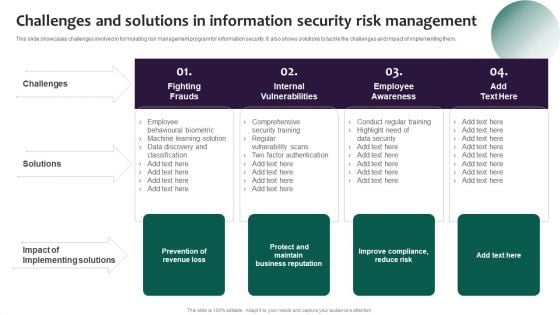
Information Systems Security And Risk Management Plan Challenges And Solutions In Information Security Risk Management Summary PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Systems Security And Risk Management Plan Challenges And Solutions In Information Security Risk Management Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Systems Security And Risk Management Plan Challenges And Solutions In Information Security Risk Management Summary PDF

Agenda For Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Sample PDF
Presenting agenda for cyber security and phishing awareness training hacking prevention awareness training for it security sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like safeguard, integrity, cybersecurity, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

30 60 90 Days Plan To Implement Cloud Security In Business Cloud Computing Security IT Ppt Gallery Master Slide PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. This is a 30 60 90 days plan to implement cloud security in business cloud computing security it ppt gallery master slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performed, analyze, cloud services, data access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
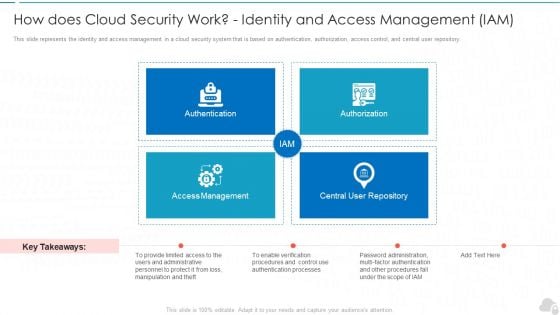
How Does Cloud Security Work Identity And Access Management Iam Cloud Computing Security IT Ppt Infographics Picture PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting how does cloud security work identity and access management iam cloud computing security it ppt infographics picture pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like authentication, authorization, access management, central user repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
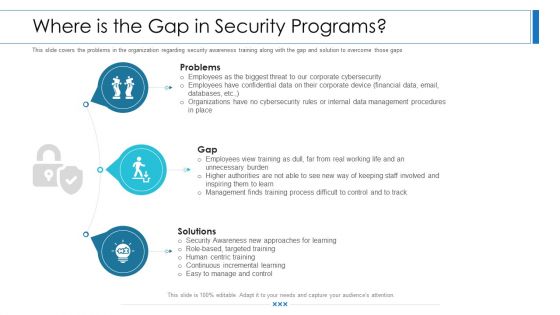
Workforce Security Realization Coaching Plan Where Is The Gap In Security Programs Ppt Show Master Slide PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a workforce security realization coaching plan where is the gap in security programs ppt show master slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
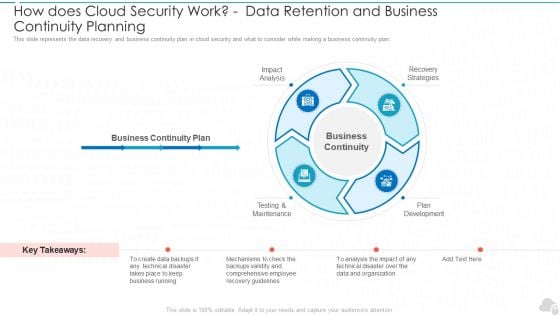
How Does Cloud Security Work Data Retention And Business Continuity Planning Cloud Computing Security IT Ppt Slides Demonstration PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a how does cloud security work data retention and business continuity planning cloud computing security it ppt slides demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis, testing and maintenance, plan development, recovery strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Boost your pitch with our creative Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Best Data Security Software Statement Of Work And Contract For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software statement of work and contract for company online database security proposal themes pdf. This is a six stage process. The stages in this process are services rendered, mutual cooperation, terms of payment, plans cancellation, confidentiality, terms and termination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. This Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Want to ace your presentation in front of a live audience Our Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
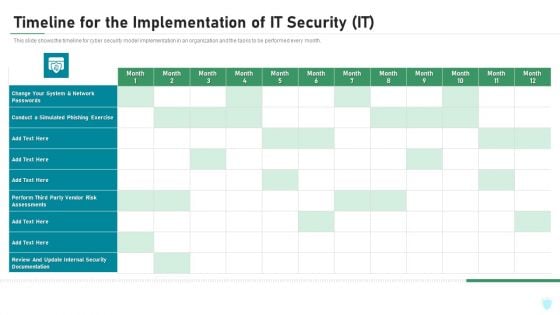
Timeline For The Implementation Of IT Security IT Ppt Inspiration Portrait PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of it security it ppt inspiration portrait pdf bundle. Topics like network, internal security, perform, phishing exercise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Protection Cyber Security Cyber Threat Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name it protection cyber security cyber threat ppt powerpoint presentation complete deck. The topics discussed in these slides are network protection, cyber security, cyber threat, laptop protected, security breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Padlock On Laptop Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Technology PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Internet PowerPoint Templates because It can Bubble and burst with your ideas. Use our Computer PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Download and present our Shapes PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Download our Network diagrams PowerPoint Templates because You should Press the right buttons with our PowerPoint Templates and Slides. They will take your ideas down the perfect channel.Use these PowerPoint slides for presentations relating to protect your computer, security concept, network diagrams, technology, computer, internet, shapes. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. PowerPoint presentation experts tell us our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our network PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. You can be sure our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our computer PowerPoint templates and PPT Slides are designed by a team of presentation professionals. Presenters tell us our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our security PowerPoint templates and PPT Slides are designed by a team of presentation professionals. Publicize your views with our Padlock On Laptop Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.
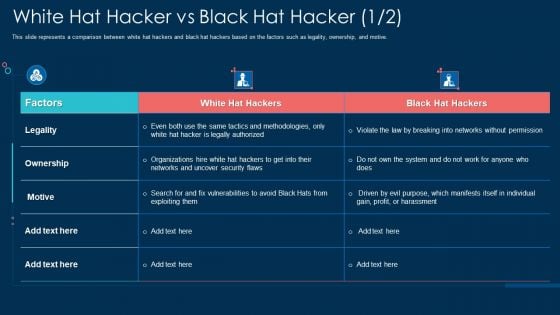
White Hat Hacker Vs Black Hat Hacker Security Ppt File Example PDF
This slide represents a comparison between white hat hackers and black hat hackers based on the factors such as legality, ownership, and motive. Deliver and pitch your topic in the best possible manner with this white hat hacker vs black hat hacker security ppt file example pdf. Use them to share invaluable insights on ownership, networks, organizations, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
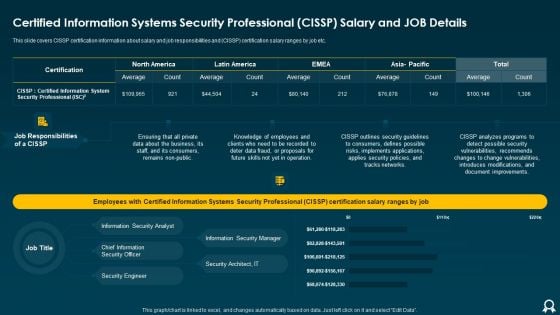
Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF bundle. Topics like Average, Tracks Networks, Applies Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Zero Trust Network Access Performance Tracking Dashboard Template PDF
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Find a pre-designed and impeccable Zero Trust Network Access Performance Tracking Dashboard Template PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
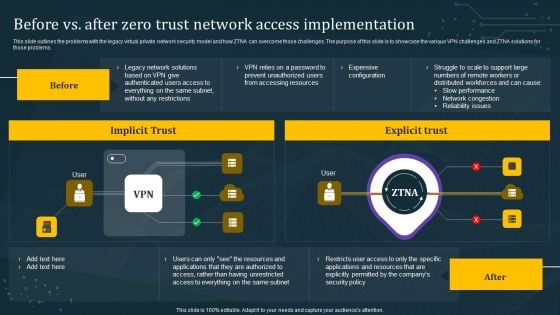
Before Vs After Zero Trust Network Access Implementation Background PDF
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Before Vs After Zero Trust Network Access Implementation Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
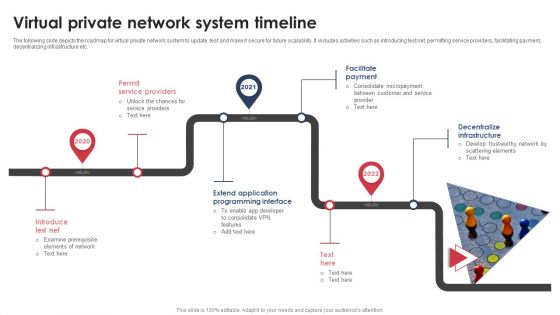
Virtual Private Network System Timeline Graphics PDF
The following slide depicts the roadmap for virtual private network system to update, test and make it secure for future scalability. It includes activities such as introducing test net, permitting service providers, facilitating payment, decentralizing infrastructure etc. Presenting Virtual Private Network System Timeline Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Permit Service Providers, Facilitate Payment, Decentralize Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
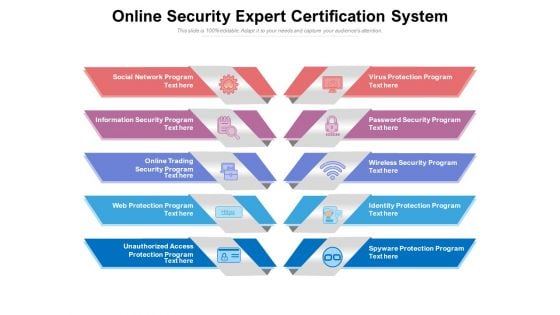
Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Info Security Employee Awareness Training Budget For FY2022 Ppt PowerPoint Presentation File Graphics Download PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative info security employee awareness training budget for fy2022 ppt powerpoint presentation file graphics download pdf bundle. Topics like build and maintain, secure network and system, protect cardholder data, maintain a vulnerability, management program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
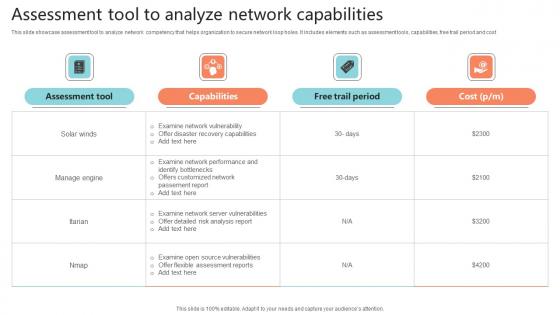
Assessment Tool To Analyze Network Capabilities Pictures Pdf
This slide showcase assessment tool to analyze network competency that helps organization to secure network loop holes. It includes elements such as assessment tools, capabilities, free trail period and cost.Showcasing this set of slides titled Assessment Tool To Analyze Network Capabilities Pictures Pdf The topics addressed in these templates are Examine Network, Flexible Assessment, Recovery Capabilities All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase assessment tool to analyze network competency that helps organization to secure network loop holes. It includes elements such as assessment tools, capabilities, free trail period and cost.

Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Data Breach Prevention Recognition Impact Of Security Awareness Training Sample PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative data breach prevention recognition impact of security awareness training sample pdf bundle. Topics like security awareness program, security threats, network intrusion, inadvertent disclosure, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
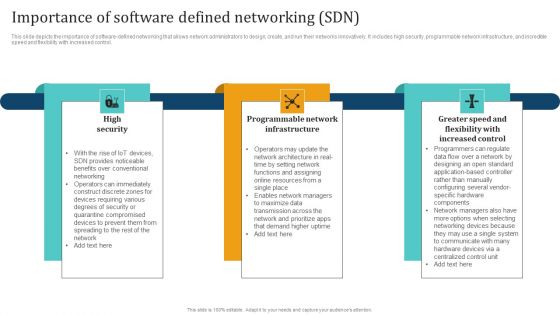
Empowering Network Agility Through SDN Importance Of Software Defined Networking SDN Mockup PDF
This slide depicts the importance of software defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Find highly impressive Empowering Network Agility Through SDN Importance Of Software Defined Networking SDN Mockup PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Empowering Network Agility Through SDN Importance Of Software Defined Networking SDN Mockup PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Laptop Under Umbrella Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Umbrellas PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake. Present our Security PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Download our Computer PowerPoint Templates because you can Set pulses racing with our PowerPoint Templates and Slides. They will raise the expectations of your team. Download and present our Network Diagrams PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Download and present our Signs PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time.Use these PowerPoint slides for presentations relating to Laptop computer under umbrella, umbrellas, security, computer, network diagrams, signs. The prominent colors used in the PowerPoint template are Red, Blue, Gray. Use our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. The feedback we get is that our security PowerPoint templates and PPT Slides are incredible easy to use. Customers tell us our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113 will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Customers tell us our network PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Presenters tell us our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Presenters tell us our computer PowerPoint templates and PPT Slides are designed by professionals Book you place at the top with our Laptop Under Umbrella Security PowerPoint Templates Ppt Backgrounds For Slides 0113. You will come out on top.
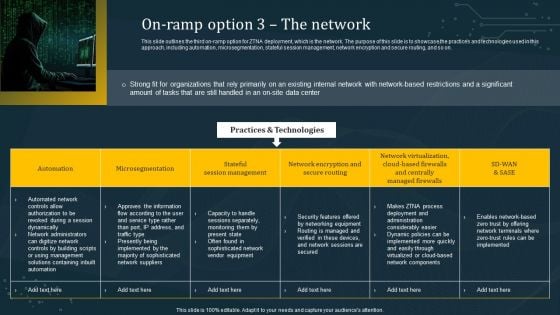
On Ramp Option 3 The Network Structure PDF
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you know about Slidesgeeks On Ramp Option 3 The Network Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
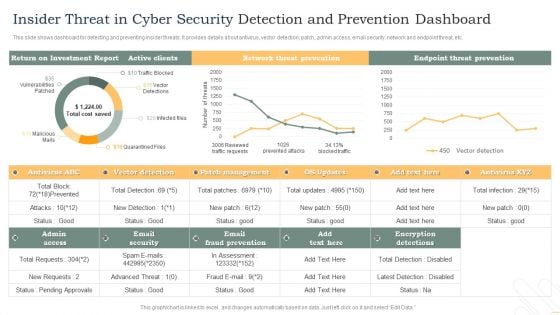
Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF
This slide shows dashboard for detecting and preventing insider threats. It provides details about antivirus, vector detection, patch, admin access, email security, network and endpoint threat, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF. This layout presents information on Active Clients, Network Threat Prevention, Endpoint Threat Prevention. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
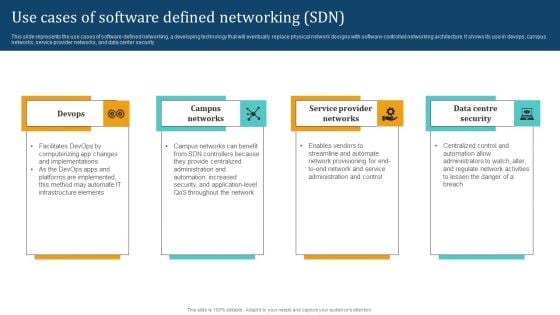
Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF
This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in devops, campus networks, service provider networks, and data center security. Presenting this PowerPoint presentation, titled Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
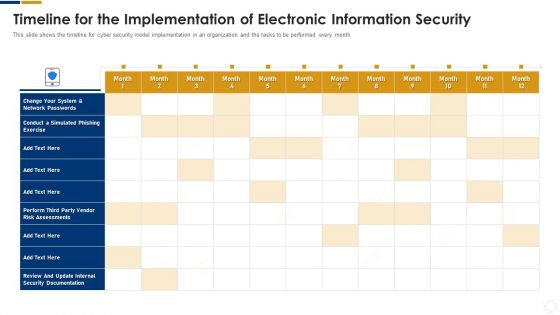
Cybersecurity Timeline For The Implementation Of Electronic Information Security Ppt Infographic Template Information PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative cybersecurity timeline for the implementation of electronic information security ppt infographic template information pdf bundle. Topics like security documentation, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
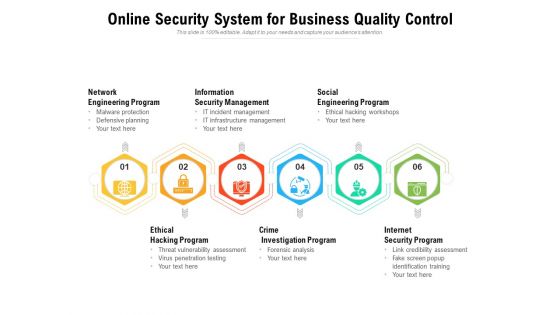
Online Security System For Business Quality Control Ppt PowerPoint Presentation Gallery Templates PDF
Presenting this set of slides with name online security system for business quality control ppt powerpoint presentation gallery templates pdf. This is a six stage process. The stages in this process are network engineering program, information security management, social engineering program, ethical hacking program, crime investigation program, internet security program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
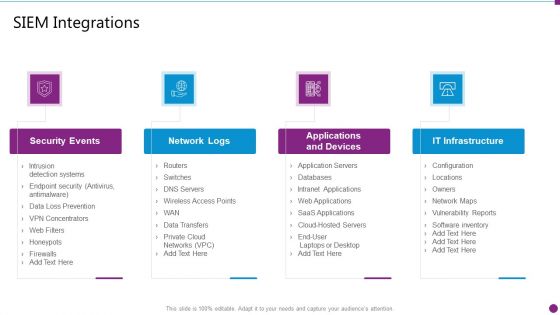
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Integrations Ideas PDF
This is a security information and event management strategies for financial audit and compliance siem integrations ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
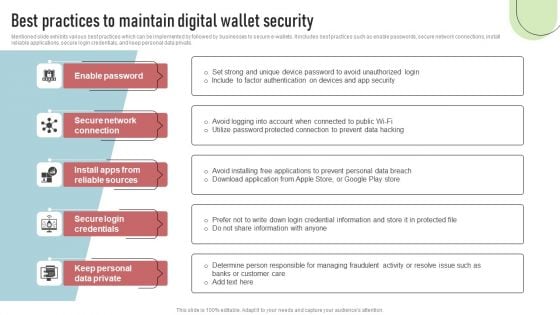
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
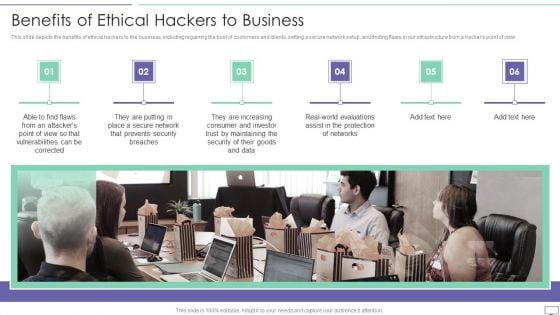
IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view.Presenting IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Consumer And Investor, Assist In The Protection, Prevents Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































