Network Security
Agenda 5G Network Functional Architecture Infographics PDF
Get a simple yet stunning designed Agenda 5G Network Functional Architecture Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Agenda 5G Network Functional Architecture Infographics PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Agenda 5G Network Structure Template PDF
Get a simple yet stunning designed Agenda 5G Network Structure Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Agenda 5G Network Structure Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
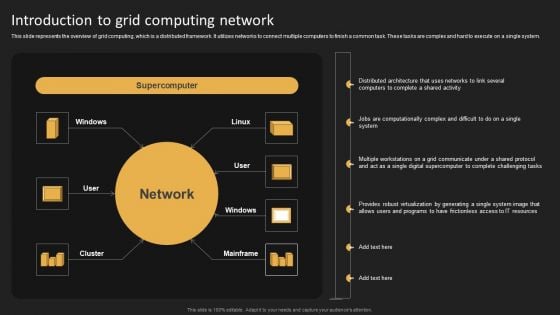
Introduction To Grid Computing Network Graphics PDF
This slide represents the overview of grid computing, which is a distributed framework. It utilizes networks to connect multiple computers to finish a common task. These tasks are complex and hard to execute on a single system. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Introduction To Grid Computing Network Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Introduction To Grid Computing Network Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
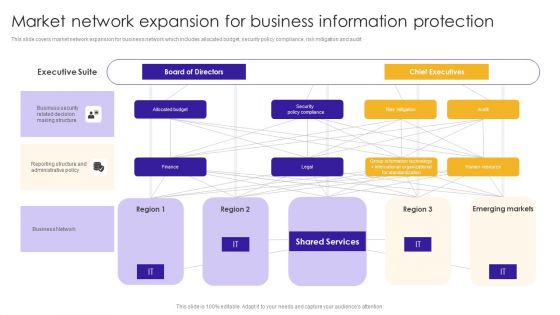
Market Network Expansion For Business Information Protection Sample PDF
This slide covers market network expansion for business network which includes allocated budget, security policy compliance, risk mitigation and audit. Showcasing this set of slides titled Market Network Expansion For Business Information Protection Sample PDF. The topics addressed in these templates are Business Security, Related Decision, Making Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
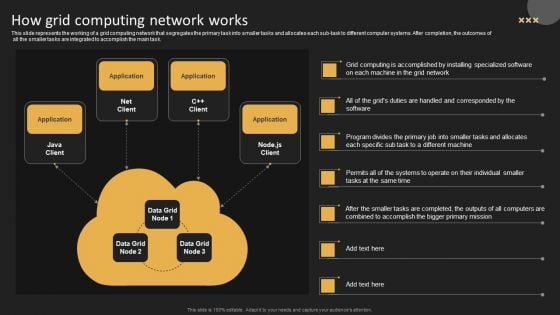
How Grid Computing Network Works Themes PDF
This slide represents the working of a grid computing network that segregates the primary task into smaller tasks and allocates each sub-task to different computer systems. After completion, the outcomes of all the smaller tasks are integrated to accomplish the main task. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our How Grid Computing Network Works Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into How Grid Computing Network Works Themes PDF
AGENDA 5G Network Operations Diagrams PDF
Do you have an important presentation coming up. Are you looking for something that will make your presentation stand out from the rest. Look no further than AGENDA 5G Network Operations Diagrams PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait. Grab AGENDA 5G Network Operations Diagrams PDF today and make your presentation stand out from the rest.
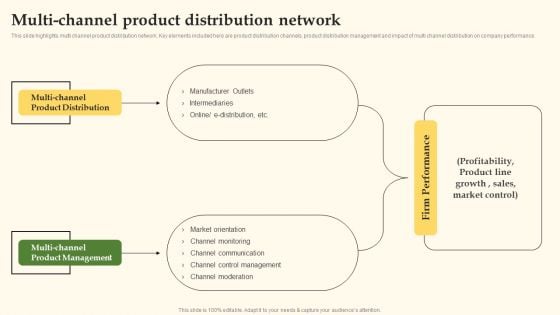
Multi Channel Product Distribution Network Template PDF
This slide highlights multi channel product distribution network. Key elements included here are product distribution channels, product distribution management and impact of multi channel distribution on company performance. Welcome to our selection of the Multi Channel Product Distribution Network Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
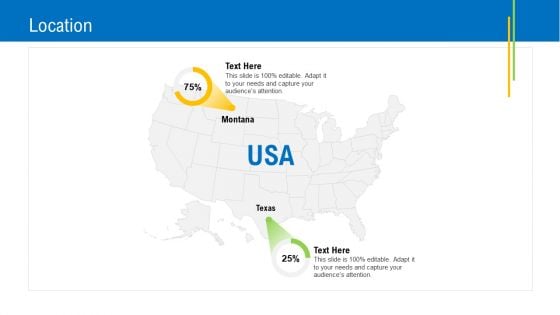
Viable Logistics Network Management Location Brochure PDF
Presenting viable logistics network management location brochure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like location. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Cognitive Sensor Network Information PDF
Find a pre designed and impeccable Agenda For Cognitive Sensor Network Information PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
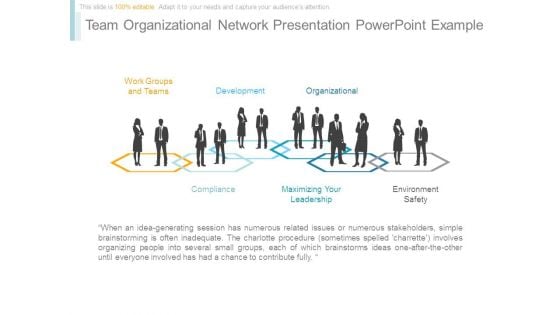
Team Organizational Network Presentation Powerpoint Example
This is a team organizational network presentation powerpoint example. This is a six stage process. The stages in this process are work groups and teams, development, organizational, compliance, maximizing your leadership, environment safety.
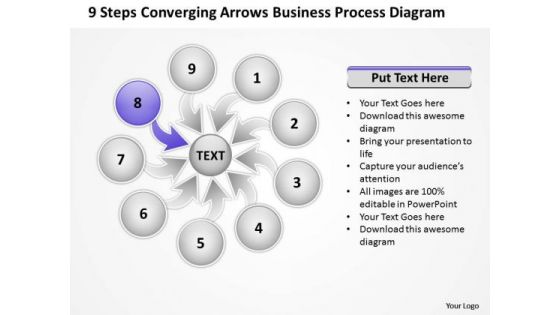
PowerPoint Templates Process Diagram Circular Flow Network
We present our powerpoint templates process diagram Circular Flow Network.Download our Circle Charts PowerPoint Templates because it can illustrate your chain of ideas focusing on that aspect or resource in order to enhance the quality of your product. Download our Arrows PowerPoint Templates because this diagram helps you to develop your marketing strategy and communicate your enthusiasm and motivation to raise the bar. Use our Shapes PowerPoint Templates because it Creates a winner with your passion and dream. Use our Business PowerPoint Templates because it helps you to explain your plans in all earnest to your colleagues and raise the bar for all. Present our Flow Charts PowerPoint Templates because they highlight the depth of your thought process.Use these PowerPoint slides for presentations relating to 9, abstract, arrows, blank, business, central, centralized, chart, circle, circular, circulation, concept, conceptual, converging, design, diagram, empty, executive, icon, idea, illustration, management, map, mapping, mba, model, numbers, organization, outwards, pointing, procedure, process, radial, radiating, relationship, resource, sequence, sequential, seven, square, strategy, template. The prominent colors used in the PowerPoint template are Purple, Gray, Black. Presenters tell us our powerpoint templates process diagram Circular Flow Network are Playful. The feedback we get is that our central PowerPoint templates and PPT Slides are Exuberant. Presenters tell us our powerpoint templates process diagram Circular Flow Network are Efficacious. You can be sure our central PowerPoint templates and PPT Slides are Delightful. People tell us our powerpoint templates process diagram Circular Flow Network are Vintage. PowerPoint presentation experts tell us our central PowerPoint templates and PPT Slides are Royal. Half the effort for double the rewards. Our PowerPoint Templates Process Diagram Circular Flow Network deliver exponential returns.
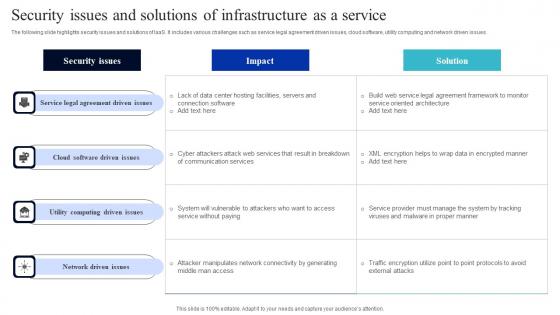
Security Issues And Solutions Of Infrastructure As A Service Summary Pdf
The following slide highlights security issues and solutions of IaaS. It includes various challenges such as service legal agreement driven issues, cloud software, utility computing and network driven issues. Showcasing this set of slides titled Security Issues And Solutions Of Infrastructure As A Service Summary Pdf. The topics addressed in these templates are Cloud Software, Utility Computing, Network Driven Issues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights security issues and solutions of IaaS. It includes various challenges such as service legal agreement driven issues, cloud software, utility computing and network driven issues.
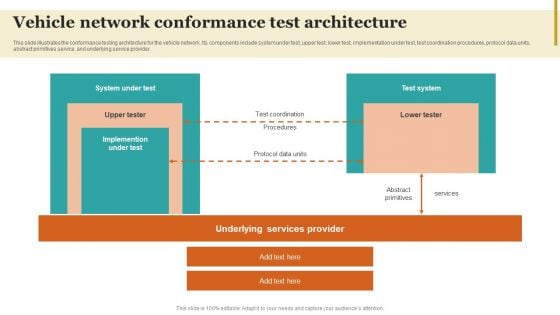
Vehicle Network Conformance Test Architecture Formats PDF
This slide illustrates the conformance testing architecture for the vehicle network. Its components include system under test, upper test, lower test, implementation under test, test coordination procedures, protocol data units, abstract primitives service, and underlying service provider. Retrieve professionally designed Vehicle Network Conformance Test Architecture Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
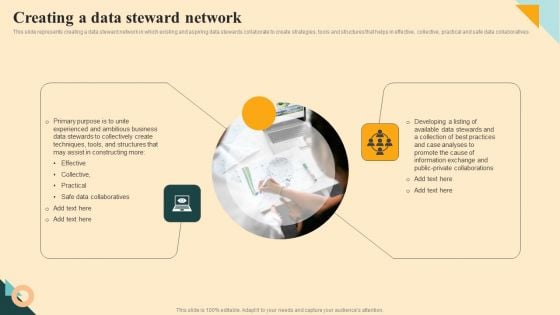
Creating A Data Steward Network Inspiration PDF
This slide represents creating a data steward network in which existing and aspiring data stewards collaborate to create strategies, tools and structures that helps in effective, collective, practical and safe data collaboratives. This Creating A Data Steward Network Inspiration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
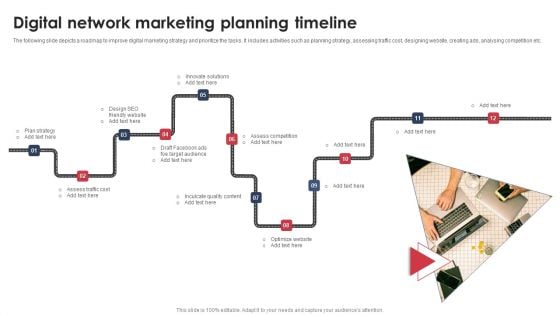
Digital Network Marketing Planning Timeline Diagrams PDF
The following slide depicts a roadmap to improve digital marketing strategy and prioritize the tasks. It includes activities such as planning strategy, assessing traffic cost, designing website, creating ads, analysing competition etc. Persuade your audience using this Digital Network Marketing Planning Timeline Diagrams PDF. This PPT design covers twelve stages, thus making it a great tool to use. It also caters to a variety of topics including Innovate Solutions, Target Audience, Inculcate Quality Content. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Ppt Templates Social Network Branding PowerPoint Slides
PPT_templates_Social_network_Branding_PowerPoint_Slides-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! These PowerPoint presentation slides can be used to represent themes relating to --Activity, answer, background, black, blank, boxes, brainteaser, challenge, clue, crossword, down, empty, game, hobby, illustration, leisure, pastime, problem, puzzle, question, quiz, raster, rectangle, solution, spelling, square, template, tile, unfinished, up, vocabulary, white, word-PPT_templates_Social_network_Branding_PowerPoint_Slides Audit your thoughts with our Ppt Templates Social Network Branding PowerPoint Slides. They will authenticate their excellence.

Team Network For Our Goal Powerpoint Slides
This PowerPoint template has been designed with graphics of team network. Download this PPT slide to display teamwork to achieve goals. This diagram may be used for goal planning related topics.
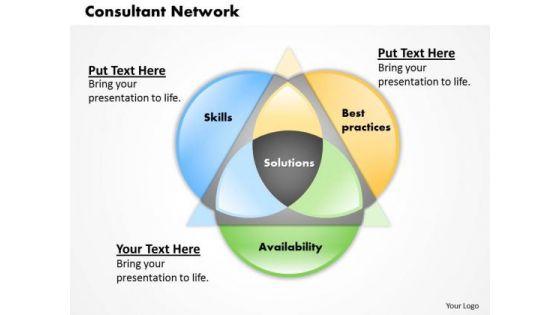
Business Framework Consultant Network PowerPoint Presentation
This business framework template displays consultant network. This image slide has been crafted to depict strategic planning. Use this image slide, in your presentations to express views on marketing, technology and business. This image slide will help you make outstanding presentations.
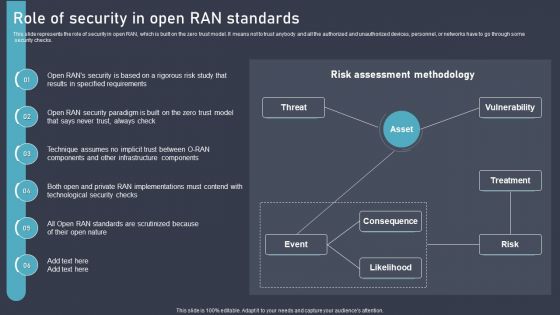
O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Retrieve professionally designed O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
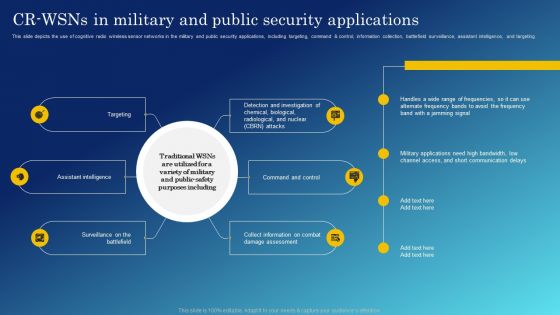
Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF
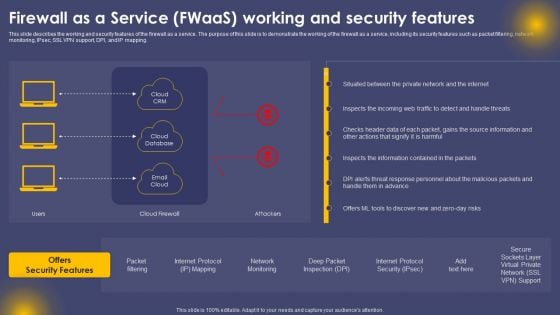
Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF
This slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Create an editable Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
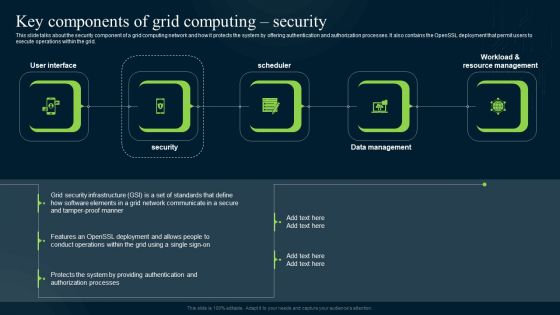
Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Explore a selection of the finest Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
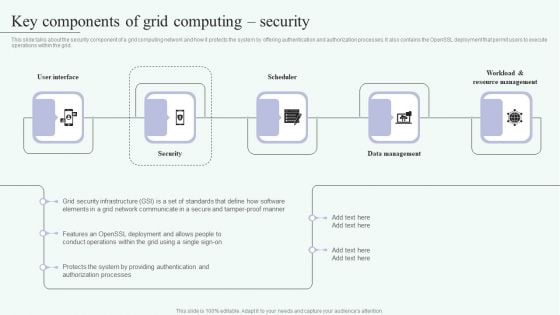
Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
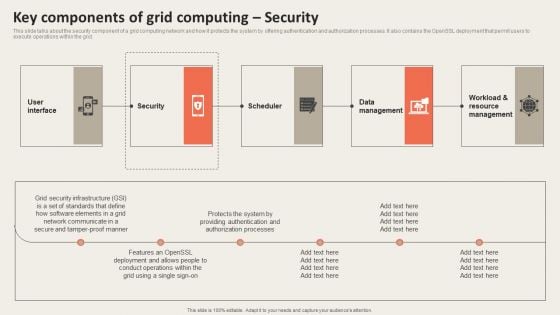
Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. This modern and well arranged Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Co2 Network Laptop Data Upload Ppt Slides Graphics
This power point icon template has been crafted with graphic of CO2, network and laptop with data icons. These icons can be used for data upload and networking related topics. Use these icons for social network and technology related presentation.
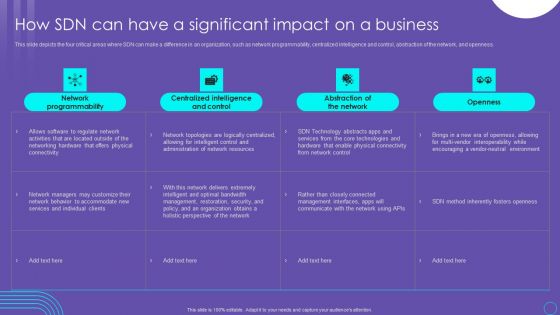
SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF
This slide depicts the four critical areas where SDN can make a difference in an organization, such as network programmability, centralized intelligence and control, abstraction of the network, and openness. Welcome to our selection of the SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Network Business Computer PowerPoint Background And Template 1210
Microsoft PowerPoint Template and Background with 3d illustration of a key unlocking a workstation Advertise the efficiency of your factory. Educate likely clients with our Network Business Computer PowerPoint Background And Template 1210.

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
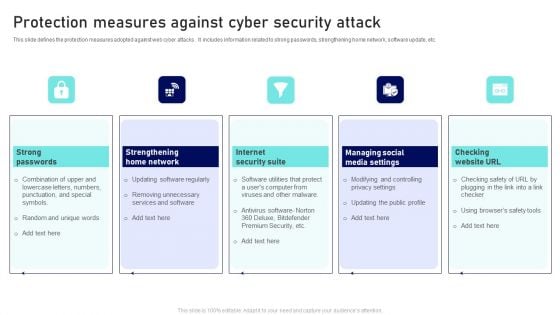
Protection Measures Against Cyber Security Attack Ppt Infographic Template Template PDF
This slide defines the protection measures adopted against web cyber attacks . It includes information related to strong passwords, strengthening home network, software update, etc. Presenting Protection Measures Against Cyber Security Attack Ppt Infographic Template Template PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Strong Passwords, Internet Security Suite, Checking Website URL. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access Roadmap To Implement Zero Trust Network Access Model
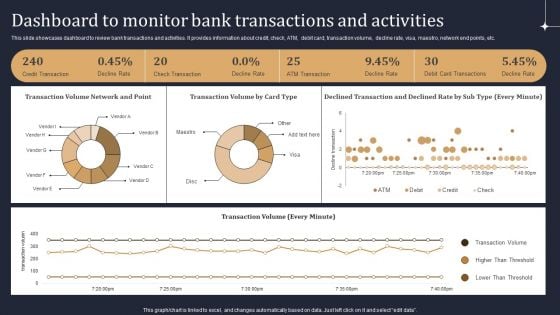
KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF
This slide showcases dashboard to review bank transactions and activities. It provides information about credit, check, ATM, debit card, transaction volume, decline rate, visa, maestro, network end points, etc. This KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
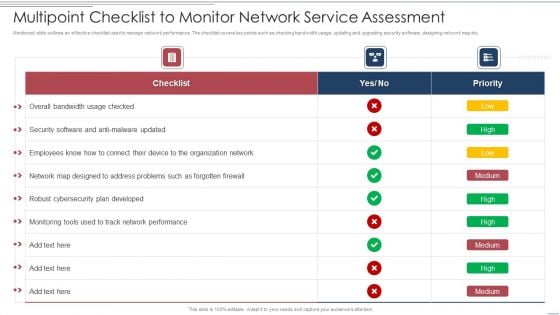
Multipoint Checklist To Monitor Network Service Assessment Structure PDF
Showcasing this set of slides titled Multipoint Checklist To Monitor Network Service Assessment Structure PDF. The topics addressed in these templates are Security, Developed, Organization Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
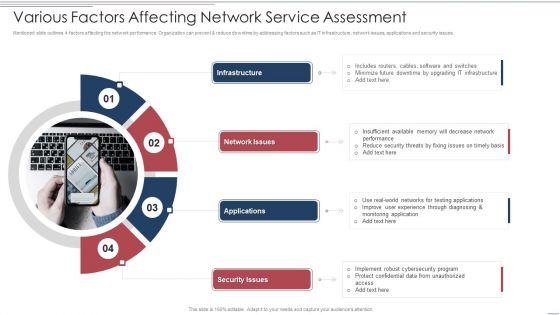
Various Factors Affecting Network Service Assessment Brochure PDF
Mentioned slide outlines 4 factors affecting the network performance. Organization can prevent and reduce downtime by addressing factors such as IT infrastructure, network issues, applications and security issues. Persuade your audience using this Various Factors Affecting Network Service Assessment Brochure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Infrastructure, Network Issues, Applications. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
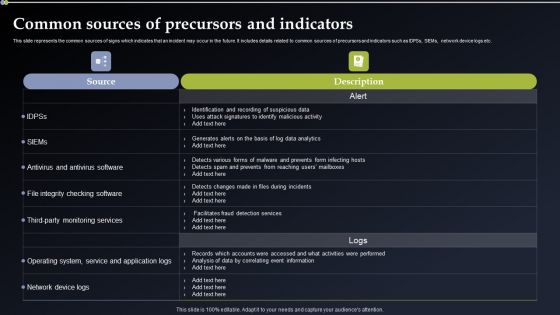
Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. This modern and well arranged Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.
1 Icon Of A Firewall To Separate The Internal Network From The External World Ppt Slides
This image slide displays icon of firewall. This image slide has been crafted with graphic of firewall icon to separate internal network from the external world. This image slide depicts security on network. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like networking and security. This image slide will enhance the quality of your presentations.
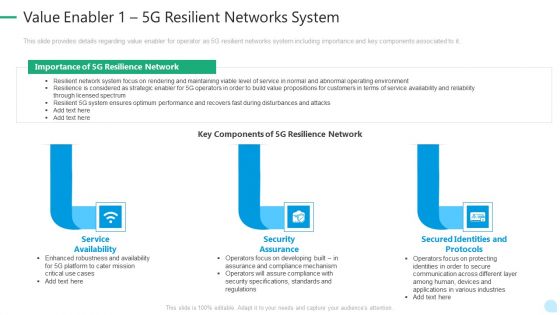
5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
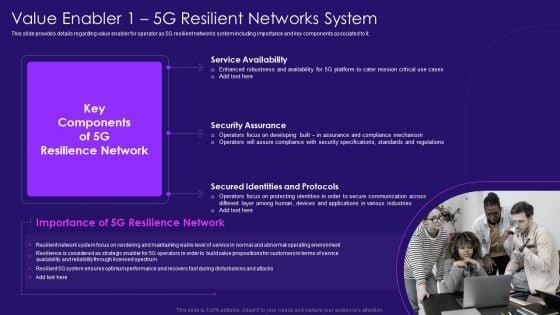
Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. Presenting Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Service Availability, Security Assurance, Secured Identities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

A47 Roadmap To Implement Zero Trust Network Access Model
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Find a pre-designed and impeccable A47 Roadmap To Implement Zero Trust Network Access Model. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Zero Trust Model On Ramp Option 3 The Network
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Presenting this PowerPoint presentation, titled Zero Trust Model On Ramp Option 3 The Network, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Model On Ramp Option 3 The Network. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Model On Ramp Option 3 The Network that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
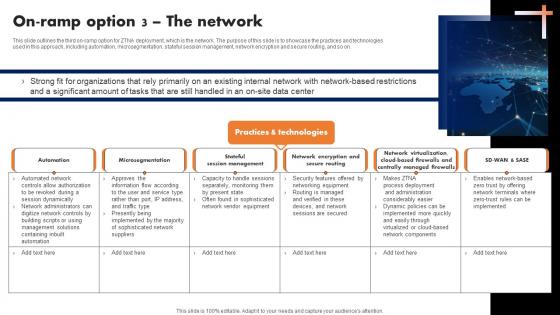
On Ramp Option 3 The Network Software Defined Perimeter SDP
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Software Defined Perimeter SDP from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
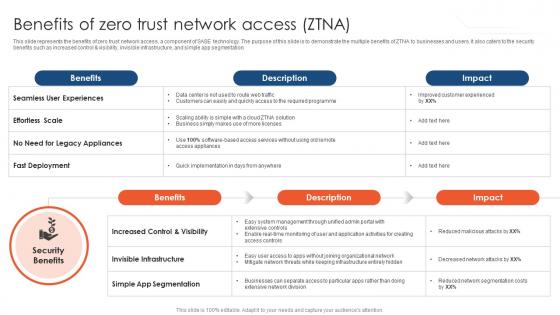
Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
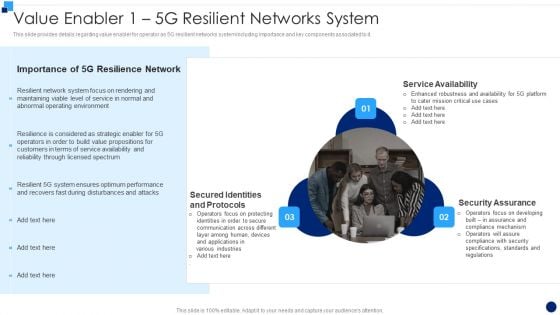
Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Assurance, Service Availability, Protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
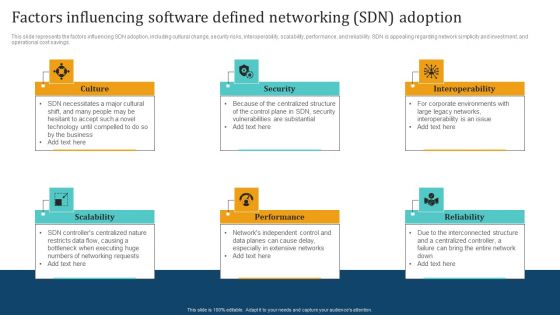
Empowering Network Agility Through SDN Factors Influencing Software Defined Networking SDN Adoption Slides PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Empowering Network Agility Through SDN Factors Influencing Software Defined Networking SDN Adoption Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Empowering Network Agility Through SDN Factors Influencing Software Defined Networking SDN Adoption Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
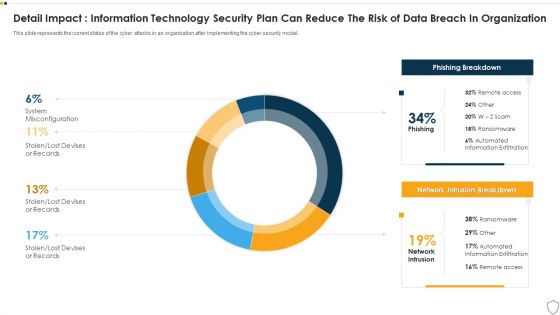
IT Security Detail Impact Information Technology Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Layouts Show PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this it security detail impact information technology security plan can reduce the risk of data breach in organization ppt layouts show pdf. Use them to share invaluable insights on detail impact information technology security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
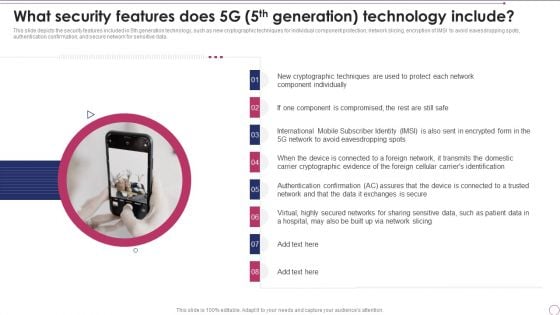
1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Presenting 1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Cryptographic Evidence, Domestic, Via Network Slicing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Mindmap Design For Network Marketing And Business Networking Ppt PowerPoint Presentation Show
This is a mindmap design for network marketing and business networking ppt powerpoint presentation show. This is a twelve stage process. The stages in this process are business, strategy, mind map, management, marketing.
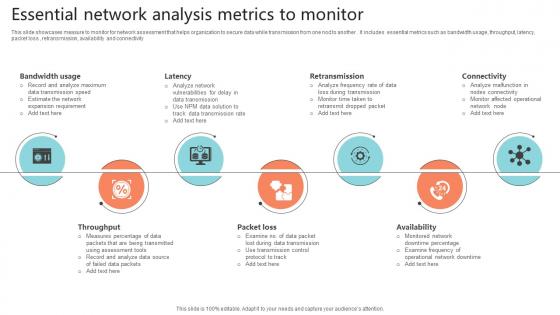
Essential Network Analysis Metrics To Monitor Portrait Pdf
This slide showcases measure to monitor for network assessment that helps organization to secure data while transmission from one nod to another . It includes essential metrics such as bandwidth usage, throughput, latency, packet loss , retransmission, availability and connectivity.Pitch your topic with ease and precision using this Essential Network Analysis Metrics To Monitor Portrait Pdf This layout presents information on Bandwidth Usage, Retransmission, Throughput It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases measure to monitor for network assessment that helps organization to secure data while transmission from one nod to another . It includes essential metrics such as bandwidth usage, throughput, latency, packet loss , retransmission, availability and connectivity
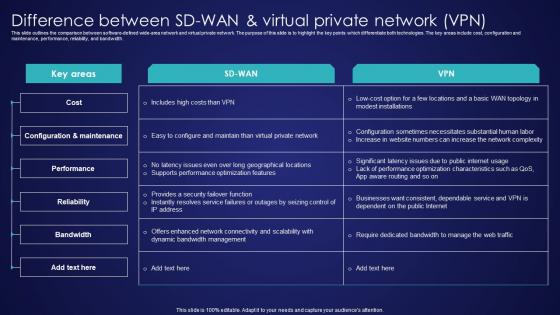
Difference Between SD Wan And Virtual Private Network Vpn Wide Area Network Services Template Pdf
This slide outlines the comparison between software-defined wide-area network and virtual private network. The purpose of this slide is to highlight the key points which differentiate both technologies. The key areas include cost, configuration and maintenance, performance, reliability, and bandwidth. Get a simple yet stunning designed Difference Between SD Wan And Virtual Private Network Vpn Wide Area Network Services Template Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Difference Between SD Wan And Virtual Private Network Vpn Wide Area Network Services Template Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the comparison between software-defined wide-area network and virtual private network. The purpose of this slide is to highlight the key points which differentiate both technologies. The key areas include cost, configuration and maintenance, performance, reliability, and bandwidth.
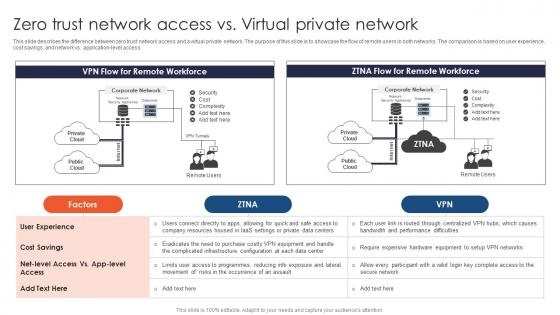
Zero Trust Network Access Vs Virtual Private Network Ppt File Example File
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Are you searching for a Zero Trust Network Access Vs Virtual Private Network Ppt File Example File that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Vs Virtual Private Network Ppt File Example File from Slidegeeks today. This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access.

Zero Trust Model Zero Trust Network Access Vs Virtual Private Network
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Slidegeeks has constructed Zero Trust Model Zero Trust Network Access Vs Virtual Private Network after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access

Zero Trust Network Access Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Working Of Zero Trust Network Access Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Working Of Zero Trust Network Access Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Working Of Zero Trust Network Access Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.


 Continue with Email
Continue with Email

 Home
Home


































