Network Security

Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF bundle. Topics like Implement Information, Data Encryption, Implement Advanced can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF.
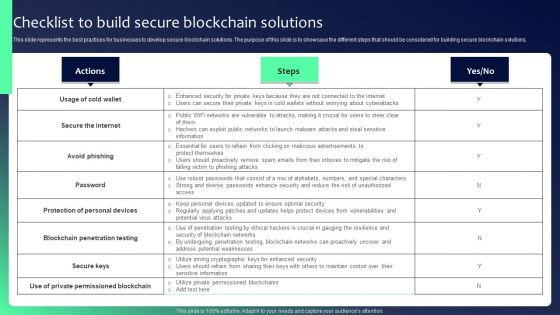
Blockchain Security Solutions Deployment Checklist To Build Secure Blockchain Diagrams PDF
This slide represents the best practices for businesses to develop secure blockchain solutions. The purpose of this slide is to showcase the different steps that should be considered for building secure blockchain solutions. Want to ace your presentation in front of a live audience Our Blockchain Security Solutions Deployment Checklist To Build Secure Blockchain Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
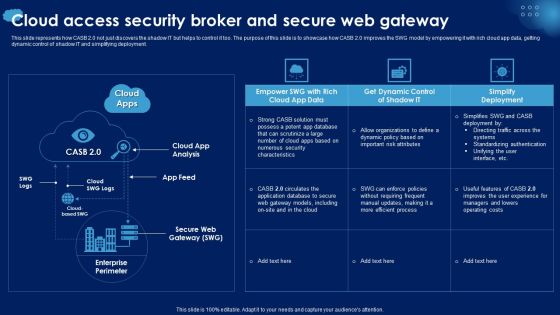
Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
Agenda For Secure Access Service Edge Cloud Security Model Ppt Outline Maker PDF
Find a pre designed and impeccable Agenda For Secure Access Service Edge Cloud Security Model Ppt Outline Maker PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
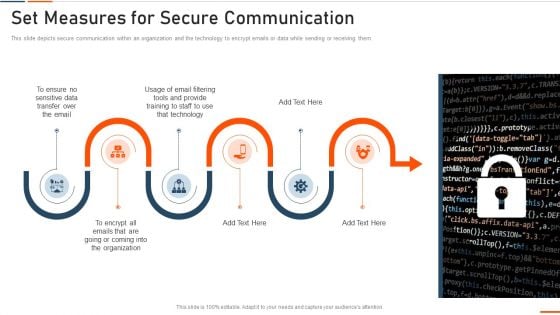
Information Technology Security Set Measures For Secure Communication Ppt Professional Portrait PDF
This is a information technology security set measures for secure communication ppt professional portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, transfer, technology, training, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
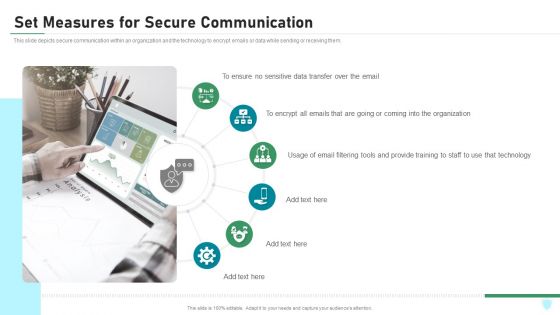
Set Measures For Secure Communication IT Security IT Ppt Styles Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Presenting set measures for secure communication it security it ppt styles background designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data transfer, organization, technology, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
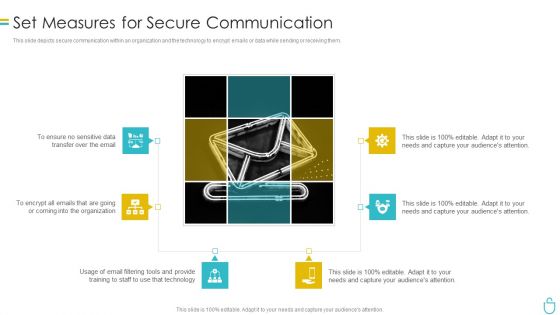
Information Security Set Measures For Secure Communication Ppt Outline Slide Download PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a information security set measures for secure communication ppt outline slide download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
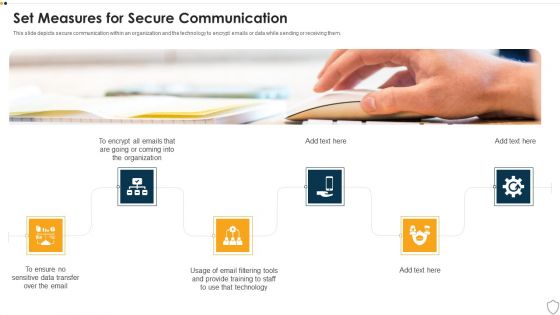
IT Security Set Measures For Secure Communication Ppt Infographic Template Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a it security set measures for secure communication ppt infographic template background designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, training, organization, data transfer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Set Measures For Secure Communication Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a info security set measures for secure communication ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, organization, email filtering tools, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Companys Data Safety Recognition Impact Of Security Awareness Training Demonstration PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative companys data safety recognition impact of security awareness training demonstration pdf bundle. Topics like system misconfiguration, inadvertent disclosure, network intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
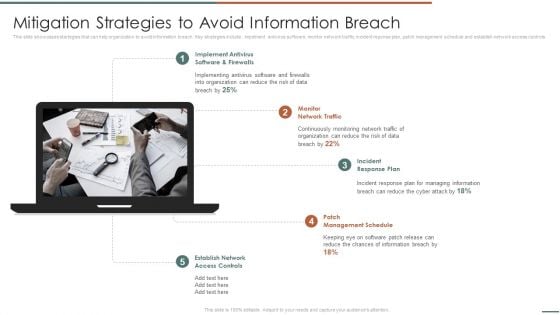
Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Computing Wifi Safety Upload Social Network Ppt Slides Graphics
This power point icon template has been designed with graphic of cloud computing, wifi and social network. These icons can be used for data upload safety features and social networking. Use these icons for social network and technology related presentations.
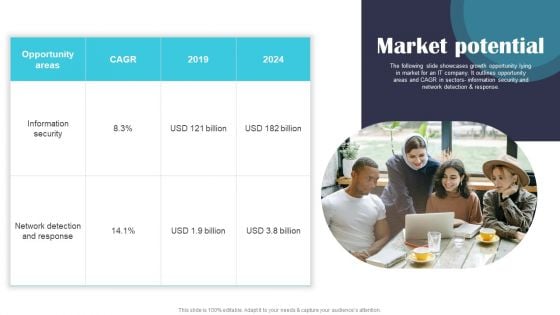
Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF
The following slide showcases growth opportunity lying in market for an IT company. It outlines opportunity areas and CAGR in sectors information security and network detection and response. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Network Access Computer PowerPoint Templates And PowerPoint Backgrounds 0411
Microsoft PowerPoint Template and Background with network access of computer Clip the wings of failure with our Network Access Computer PowerPoint Templates And PowerPoint Backgrounds 0411. You will come out on top.

Network Access Computer PowerPoint Themes And PowerPoint Slides 0411
Microsoft PowerPoint Theme and Slide with network access of computer Put in our Network Access Computer PowerPoint Themes And PowerPoint Slides 0411 as the catalyst. Churn out new equations with your ideas.
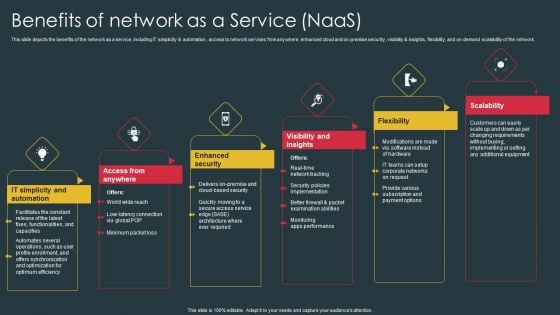
Managed Network Services Benefits Of Network As A Service Naas Mockup PDF
This slide depicts the benefits of the network as a service, including IT simplicity and automation, access to network services from anywhere, enhanced cloud and on-premise security, visibility and insights, flexibility, and on-demand scalability of the network. Boost your pitch with our creative Managed Network Services Benefits Of Network As A Service Naas Mockup PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Steps To Boost Home Safety And Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the process to be followed by smart homeowners to increase security. Major steps covered are determining data captured, utilizing security features, keeping networks separate, providing access to authorized people, monitoring energy usage and taking precautions. Create an editable Steps To Boost Home Safety And Security Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps To Boost Home Safety And Security Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the process to be followed by smart homeowners to increase security. Major steps covered are determining data captured, utilizing security features, keeping networks separate, providing access to authorized people, monitoring energy usage and taking precautions.

Online Attack Network Credit Card Ppt PowerPoint Presentation Complete Deck
Improve your presentation delivery using this online attack network credit card ppt powerpoint presentation complete deck. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
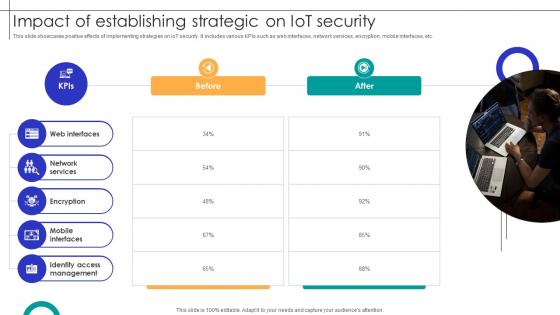
Impact Of Establishing Strategic On IOT Security Streamlining Production Ppt Presentation
This slide showcases positive effects of implementing strategies on IoT security. It includes various KPIs such as web interfaces, network services, encryption, mobile interfaces, etc. Retrieve professionally designed Impact Of Establishing Strategic On IOT Security Streamlining Production Ppt Presentation to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases positive effects of implementing strategies on IoT security. It includes various KPIs such as web interfaces, network services, encryption, mobile interfaces, etc.

About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology.
Various Strategies To Ensure Food Safety Food Security Excellence Ppt Icon Slide PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety food security excellence ppt icon slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Plan Strategy Make New Network Concept
Knock On The Door To Success With Our Business Plan Strategy Make New Network Concept Powerpoint Templates. Be Assured Of Gaining Entry. Give Them A Dose Of Your Ability. It Will Go Down Well With Our Leadership Powerpoint Templates.
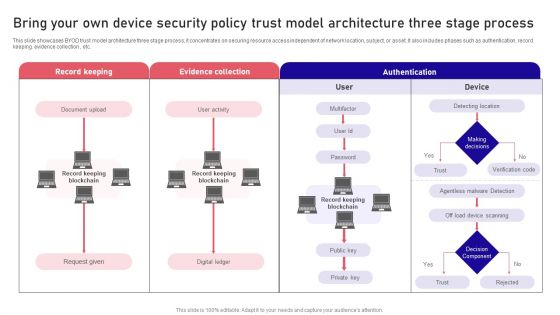
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
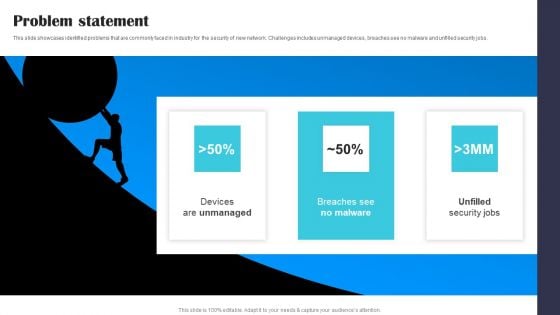
Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF
This slide showcases identified problems that are commonly faced in industry for the security of new network. Challenges includes unmanaged devices, breaches see no malware and unfilled security jobs. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
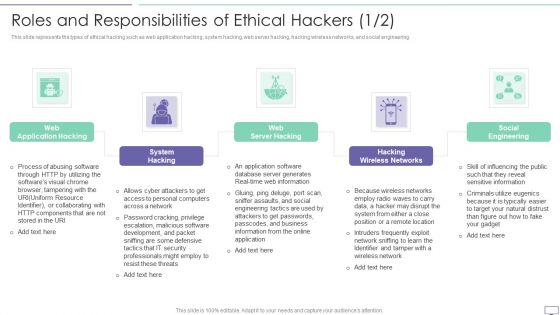
IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
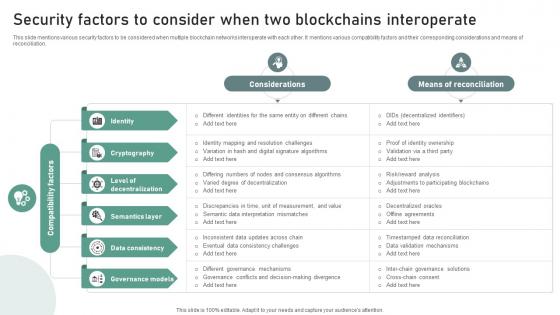
Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V
This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Create an editable Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation.
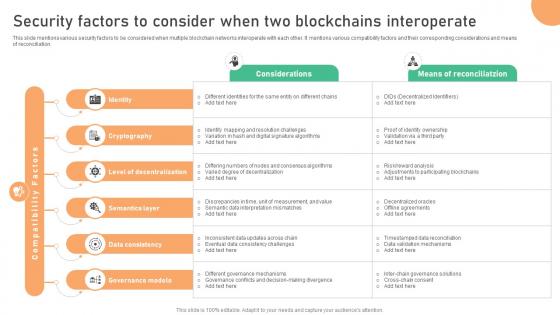
Seamless Integration The Power Security Factors To Consider When Two Blockchains BCT SS V
This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Seamless Integration The Power Security Factors To Consider When Two Blockchains BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation.

Understanding Various Blockchain Security Factors To Consider When Two Blockchains BCT SS V
This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Want to ace your presentation in front of a live audience Our Understanding Various Blockchain Security Factors To Consider When Two Blockchains BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation.
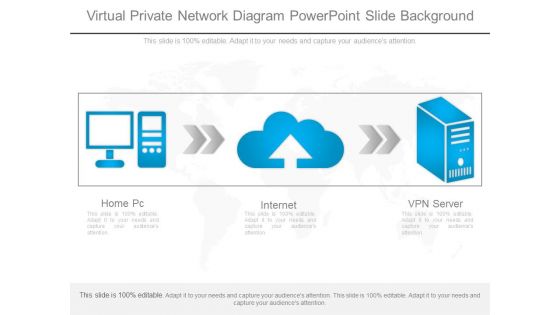
Virtual Private Network Diagram Powerpoint Slide Background
This is a virtual private network diagram powerpoint slide background. This is a three stage process. The stages in this process are home pc, internet, vpn server.
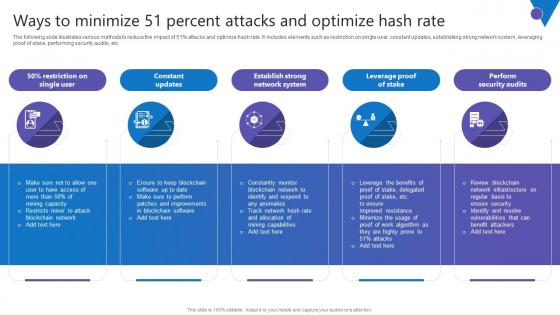
Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Present like a pro with Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc.

Multicultural Communication Network Strategic Plan Download Pdf
Pitch your topic with ease and precision using this Multicultural Communication Network Strategic Plan Download Pdf. This layout presents information on Multicultural Communication, Network Strategic Plan. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Multicultural Communication Network Strategic Plan Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Branch Network Transformation Techniques Icon Diagrams Pdf
Showcasing this set of slides titled Branch Network Transformation Techniques Icon Diagrams Pdf. The topics addressed in these templates are Branch Network Transformation, Techniques Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Branch Network Transformation Techniques Icon Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Network Access Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Network Access Overview Of Zero Trust Solution Categories for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.
Technical Support For Network Evolution Powerpoint Slides
This is a technical support for network evolution powerpoint slides. This is a four stage process. The stages in this process are technical support for network evolution, network operation and maintenance, network trend, planning and design.
Icon Showcasing Network Infrastructure Analysis Elements Pdf
Showcasing this set of slides titled Icon Showcasing Network Infrastructure Analysis Elements Pdf The topics addressed in these templates are Icon Showcasing Network, Infrastructure Analysis All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Icon Showcasing Network Infrastructure Analysis Elements Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Network Resource Planning Template Powerpoint Slides Designs
This is a network resource planning template powerpoint slides designs. This is a four stage process. The stages in this process are network, dynamic inventory, network synchronization, operational planning.
Business Diagram Correct Wrong And Security Icons For Antivirus Software Presentation Template
This business slide displays correct wrong and security icons. Download this slide to depict antivirus and software protection related concepts. It will make your presentation look professional and keep your audience mesmerized.

Agenda Wide Area Network Services Topics Pdf
Find a pre-designed and impeccable Agenda Wide Area Network Services Topics Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda Wide Area Network Services Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Global Internet Security Solution By Dsl PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Global Internet Security Solution By Dsl PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Earth PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime. Download and present our Network Diagrams PowerPoint Templates because You are well armed with penetrative ideas. Our PowerPoint Templates and Slides will provide the gunpowder you need. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Present our Globe PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Download our Computer PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate.Use these PowerPoint slides for presentations relating to Green computer mouse is connected to a green globe, earth, computer, globe, signs, network diagrams,. The prominent colors used in the PowerPoint template are Green, White, Black. Put your audience in a conducive mood. Conduct changes with our Global Internet Security Solution By Dsl PowerPoint Templates Ppt Backgrounds For Slides 0313.

Multi Level Network Marketing Revenue Download Pdf
The following slide provides the working model of network marketing strategy which helps business in creating effective product promotion. Key components are lead generation, recruitment, training and development. Showcasing this set of slides titled Multi Level Network Marketing Revenue Download Pdf. The topics addressed in these templates are Affiliate Marketing, Levels Of Sales, Commission. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides the working model of network marketing strategy which helps business in creating effective product promotion. Key components are lead generation, recruitment, training and development.
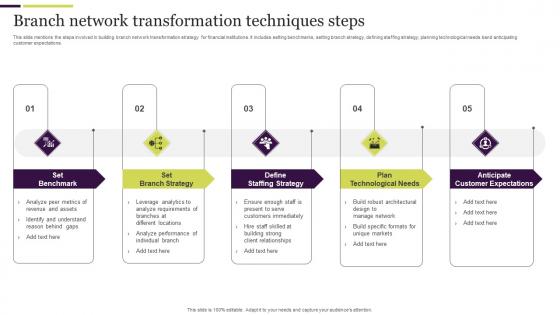
Branch Network Transformation Techniques Steps Ideas Pdf
This slide mentions the steps involved in building branch network transformation strategy for financial institutions. It includes setting benchmarks, setting branch strategy, defining staffing strategy, planning technological needs band anticipating customer expectations. Pitch your topic with ease and precision using this Branch Network Transformation Techniques Steps Ideas Pdf. This layout presents information on Plan Technological Needs, Anticipate Customer Expectations, Set Benchmark. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide mentions the steps involved in building branch network transformation strategy for financial institutions. It includes setting benchmarks, setting branch strategy, defining staffing strategy, planning technological needs band anticipating customer expectations.

A50 Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A50 Zero Trust Network Access Architecture Workflow for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
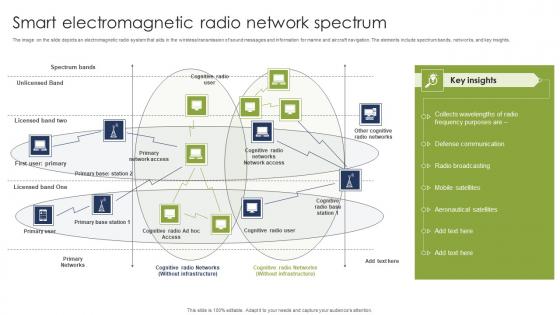
Smart Electromagnetic Radio Network Spectrum Designs Pdf
The image on the slide depicts an electromagnetic radio system that aids in the wireless transmission of sound messages and information for marine and aircraft navigation. The elements include spectrum bands, networks, and key insights. Showcasing this set of slides titled Smart Electromagnetic Radio Network Spectrum Designs Pdf. The topics addressed in these templates are Spectrum Bands, Unlicensed Band, Primary User. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The image on the slide depicts an electromagnetic radio system that aids in the wireless transmission of sound messages and information for marine and aircraft navigation. The elements include spectrum bands, networks, and key insights.
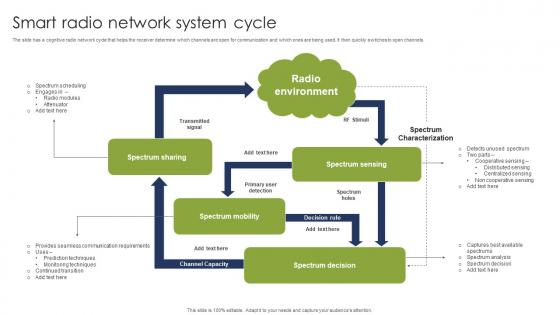
Smart Radio Network System Cycle Demonstration Pdf
The slide has a cognitive radio network cycle that helps the receiver determine which channels are open for communication and which ones are being used. It then quickly switches to open channels. Pitch your topic with ease and precision using this Smart Radio Network System Cycle Demonstration Pdf. This layout presents information on Radio Environment, Spectrum Sharing, Spectrum Sensing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide has a cognitive radio network cycle that helps the receiver determine which channels are open for communication and which ones are being used. It then quickly switches to open channels.
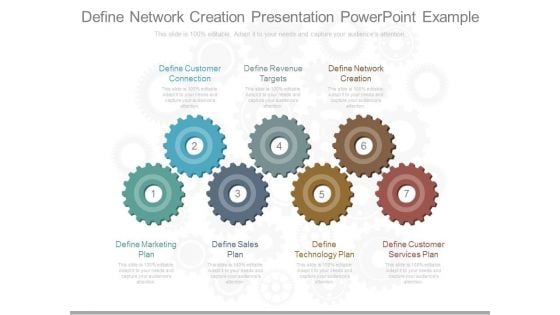
Define Network Creation Presentation Powerpoint Example
This is a define network creation presentation powerpoint example. This is a seven stage process. The stages in this process are define customer connection, define revenue targets, define network creation, define marketing plan, define technology plan, define customer services plan.\n\n\n\n
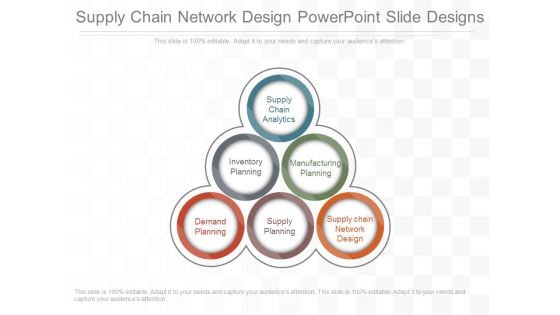
Supply Chain Network Design Powerpoint Slide Designs
This is a supply chain network design powerpoint slide designs. This is a six stage process. The stages in this process are supply chain analytics, inventory planning, manufacturing planning, demand planning, supply planning, supply chain network design.
Team With Social Media Network Powerpoint Slides
Our compelling template consists with graphics of team with social media network. This slide has been professionally designed to display team network and planning. This template offers an excellent background to build impressive presentation.
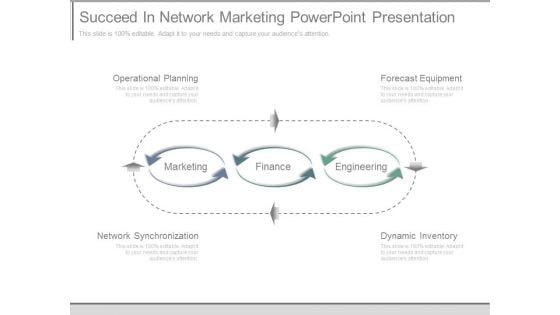
Succeed In Network Marketing Powerpoint Presentation
This is a succeed in network marketing powerpoint presentation. This is a three stage process. The stages in this process are operational planning, forecast equipment, marketing, finance, engineering, network synchronization, dynamic inventory.
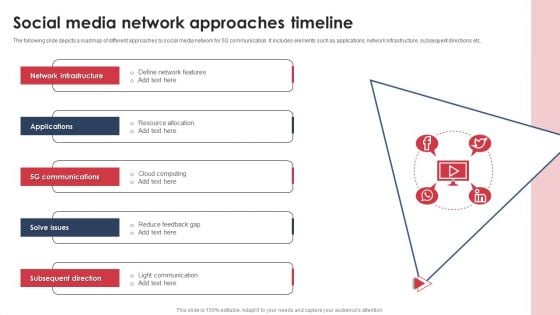
Social Media Network Approaches Timeline Microsoft PDF
The following slide depicts a roadmap of different approaches to social media network for 5G communication. It includes elements such as applications, network infrastructure, subsequent directions etc. Presenting Social Media Network Approaches Timeline Microsoft PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Network Infrastructure, Applications, 5G Communications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
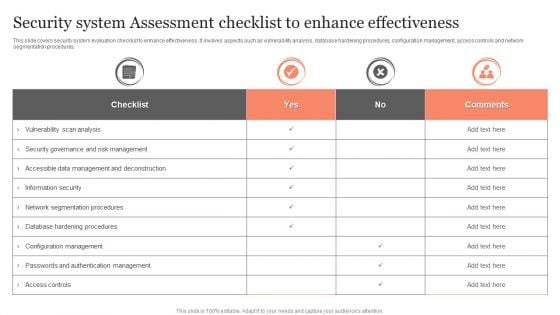
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

A49 Zero Trust Network Access Architecture Overview
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Create an editable A49 Zero Trust Network Access Architecture Overview that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. A49 Zero Trust Network Access Architecture Overview is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.
Business Diagram Consultant Network PowerPoint Ppt Presentation
Plan For All Contingencies With Our Business Diagram Consultant Network PowerPoint PPT Presentation Powerpoint Templates. Douse The Fire Before It Catches.
Cloud Services Network Server Icon Topics PDF
Showcasing this set of slides titled Cloud Services Network Server Icon Topics PDF. The topics addressed in these templates are Cloud Services, Network Server Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Digital Network Transformation Timeline Icon Clipart PDF
Showcasing this set of slides titled Digital Network Transformation Timeline Icon Clipart PDF. The topics addressed in these templates are Digital Network Transformation, Timeline Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Product Supply Chain Network Icon Structure PDF
Showcasing this set of slides titled Product Supply Chain Network Icon Structure PDF. The topics addressed in these templates are Chain Network Icon, Product Supply. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cloud Computing Network Building Icon Themes PDF
Persuade your audience using this Cloud Computing Network Building Icon Themes PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Computing, Network Building Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network Catastrophe Recovery Application Plan Portrait PDF
This slide defines another type of DR plan, which is a network disaster recovery plan. It also represents how processes will be created to get new hardware and contact IT professionals. This is a network catastrophe recovery application plan portrait pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network catastrophe recovery application plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































