Network Security

Success Key Security PowerPoint Template 0510
key to success 3d Develop plans with our Success Key Security PowerPoint Template 0510. Download without worries with our money back guaranteee.

Time Bomb Security PowerPoint Template 0910
time bomb with dynamite and timer on the computer chip Enthuse your audience with our Time Bomb Security PowerPoint Template 0910. You will come out on top.
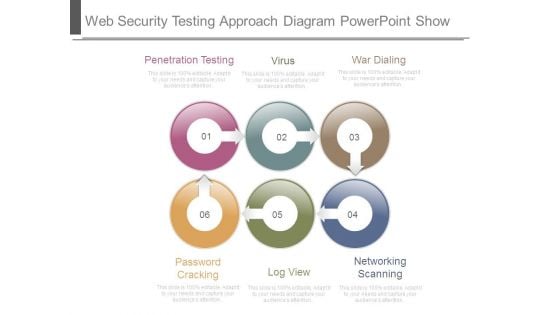
Web Security Testing Approach Diagram Powerpoint Show
This is a web security testing approach diagram powerpoint show. This is a six stage process. The stages in this process are penetration testing, virus, war dialing, password cracking, log view, networking scanning.

Protect Your Money Security PowerPoint Template 1110
protect your credit card with new device. isolated. with path Fight fires with our Protect Your Money Security PowerPoint Template 1110. Try us out and see what a difference our templates make.

Information Architecture Security Architecture Ppt Slides
This is an information architecture security architecture ppt slides. This is a four stage process. The stages in this process are business, marketing, security.

Accessing The Data Security PowerPoint Template 1010
3d illustration of a large brass key and lock protruding from a simple pie chart Help develop a solution with our Accessing The Data Security PowerPoint Template 1010. Just download, type and present.

Unlock Your Potential Security PowerPoint Template 1110
A safe lock dial with the words Unlock Your Potential on it Our Unlock Your Potential Security PowerPoint Template 1110 ensure your credentials are established. Your abilities will be acknowledged by all.
Private Database Security PowerPoint Icon C
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Chase dreams with our Private Database Security PowerPoint Icon C. You will come out on top.
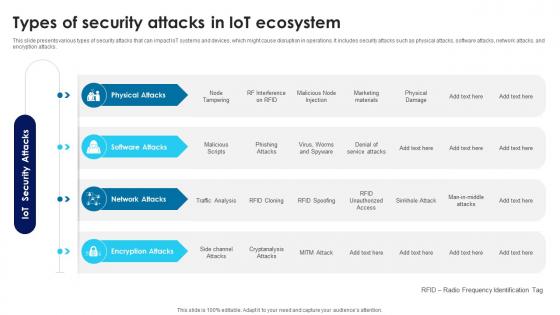
Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V
This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks.

Copy Right Security PowerPoint Template 1110
3d illustration of a brass metallic key and keyring sitting in front of a large chrome metallic copyright symbol on a dark gray reflective surface Our Copy Right Security PowerPoint Template 1110 give expression to your drive. They emit the essence of your determination.
Private Database Security PowerPoint Icon Cc
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Correct wrongs with our Private Database Security PowerPoint Icon Cc. Download without worries with our money back guaranteee.
Private Database Security PowerPoint Icon F
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Acquire the endorsement of the audience. The use of our Private Database Security PowerPoint Icon F will go in your favour.
Private Database Security PowerPoint Icon R
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Aim for the skies with our Private Database Security PowerPoint Icon R. You will come out on top.
Private Database Security PowerPoint Icon S
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Our Private Database Security PowerPoint Icon S have fantastic ability. They will have an astounding effect on the audience.
Computer Cyber Security Icon Infographics PDF
Presenting Computer Cyber Security Icon Infographics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Computer Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
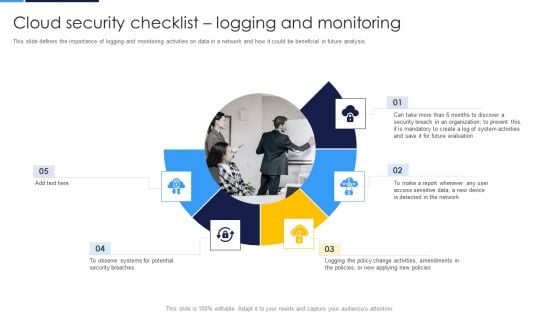
Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
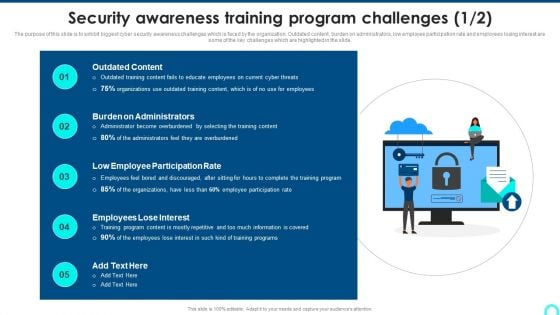
Security Awareness Training Program Challenges Rules PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Presenting Security Awareness Training Program Challenges Rules PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Outdated Content, Burden On Administrators, Employee Participation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Privacy Security Ppt PowerPoint Presentation Show Outline
Presenting this set of slides with name privacy security ppt powerpoint presentation show outline. This is a four stage process. The stages in this process are technology, marketing, planning, business, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
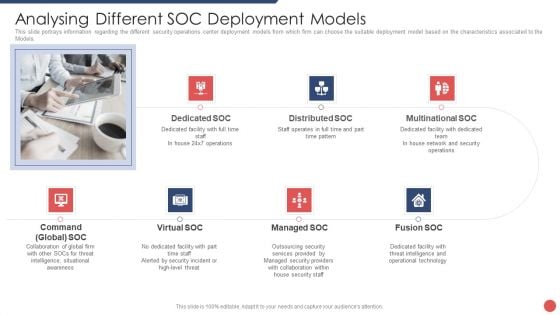
Security Functioning Centre Analysing Different SOC Deployment Models Template PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the Models. This is a security functioning centre analysing different soc deployment models template pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like distributed, network, security operations, operational technology, threat intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
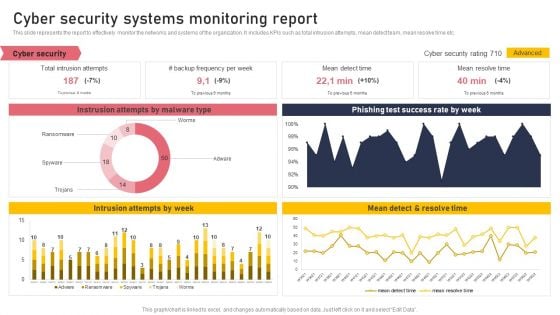
Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Boost your pitch with our creative Cyber Security Systems Monitoring Report Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
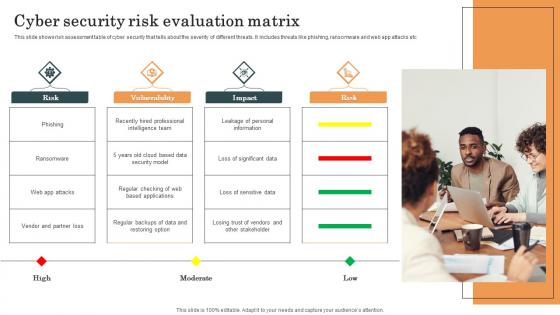
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.
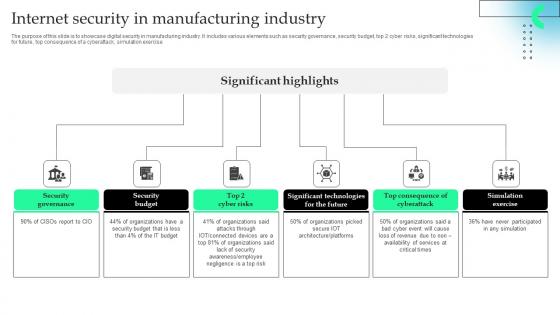
Internet Security In Manufacturing Industry Professional Pdf
The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.Pitch your topic with ease and precision using this Internet Security In Manufacturing Industry Professional Pdf This layout presents information on Security Governance, Security Budget, Significant Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.

Cyber Security Strategic Agenda Checklist Mockup Pdf
This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status. Showcasing this set of slides titled Cyber Security Strategic Agenda Checklist Mockup Pdf. The topics addressed in these templates are Cyber Security, Strategic Agenda Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status.
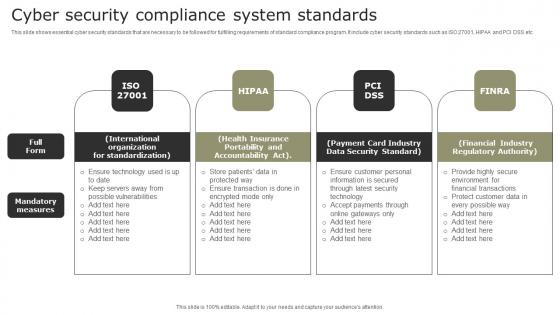
Cyber Security Compliance System Standards Demonstration Pdf
This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc. Showcasing this set of slides titled Cyber Security Compliance System Standards Demonstration Pdf. The topics addressed in these templates are International Organization, Health Insurance, Payment Card Industry. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc.
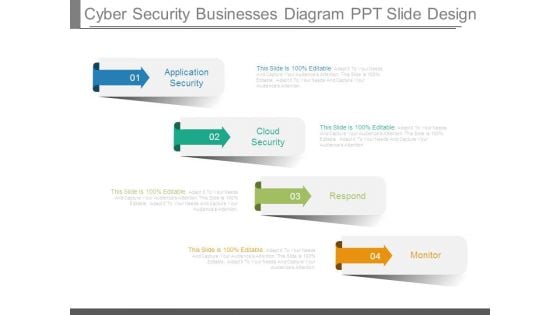
Cyber Security Businesses Diagram Ppt Slide Design
This is a cyber security businesses diagram ppt slide design. This is a four stage process. The stages in this process are application security, cloud security, respond, monitor.
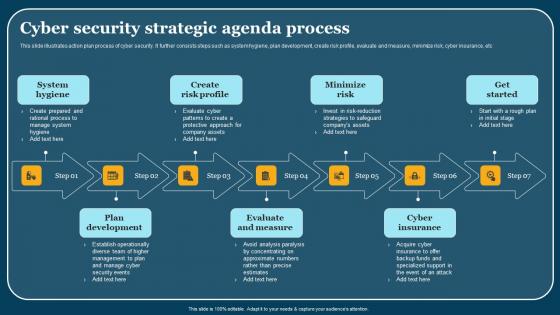
Cyber Security Strategic Agenda Process Demonstration Pdf
This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc. Showcasing this set of slides titled Cyber Security Strategic Agenda Process Demonstration Pdf. The topics addressed in these templates are System Hygiene, Plan Development, Evaluate And Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc.
Big Data Monitoring Security Icon Download pdf
Pitch your topic with ease and precision using this Big Data Monitoring Security Icon Download pdf. This layout presents information on Big Data Monitoring, Security Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Big Data Monitoring Security Icon Download pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Construction Worker Security Checklist Icon Portrait Pdf
Pitch your topic with ease and precision using this Construction Worker Security Checklist Icon Portrait Pdf. This layout presents information on Construction Worker, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Construction Worker Security Checklist Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Food Quality Security Checklist Icon Guidelines Pdf
Pitch your topic with ease and precision using this Food Quality Security Checklist Icon Guidelines Pdf. This layout presents information on Food Quality, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Food Quality Security Checklist Icon Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Data Security Compliance System Icon Clipart Pdf
Pitch your topic with ease and precision using this Data Security Compliance System Icon Clipart Pdf. This layout presents information on Data Security, Compliance System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Security Compliance System Icon Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Ppt PowerPoint Presentation Slides Cpb
This is a cyber security ppt powerpoint presentation slides cpb. This is a three stage process. The stages in this process are cyber security.
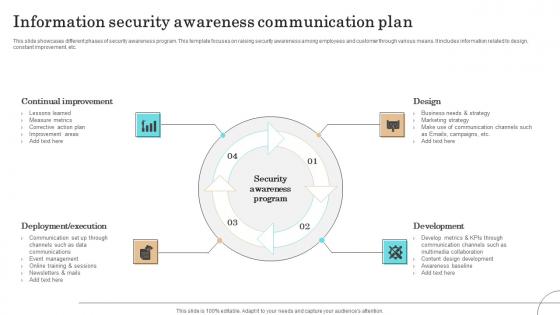
Information Security Awareness Communication Plan Formats Pdf
This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.Pitch your topic with ease and precision using this Information Security Awareness Communication Plan Formats Pdf This layout presents information on Continual Improvement, Deployment Execution, Communication It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.

Timeline For Implementing Efficient Application Security Testing
This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Are you searching for a Timeline For Implementing Efficient Application Security Testing that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Timeline For Implementing Efficient Application Security Testing from Slidegeeks today. This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc.
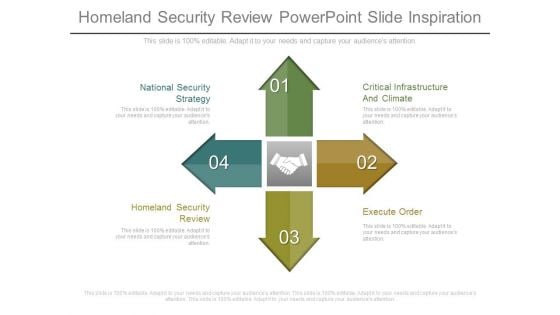
Homeland Security Review Powerpoint Slide Inspiration
This is a homeland security review powerpoint slide inspiration. This is a four stage process. The stages in this process are national security strategy, critical infrastructure and climate, homeland security review, execute order.
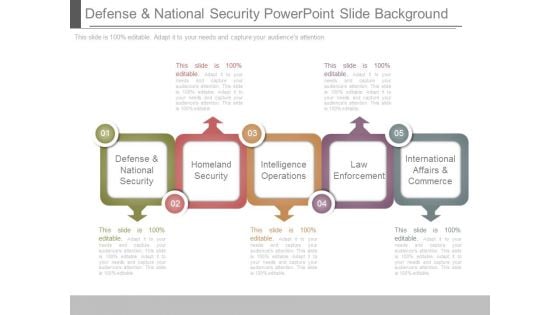
Defense And National Security Powerpoint Slide Background
This is a defense and national security powerpoint slide background. This is a five stage process. The stages in this process are defense and national security, homeland security, intelligence operations, law enforcement, international affairs and commerce.

Security Operations Management Sample Presentation Images
This is a security operations management sample presentation images. This is a five stage process. The stages in this process are compliance and validation, security organization, device control, security operations, patch management.
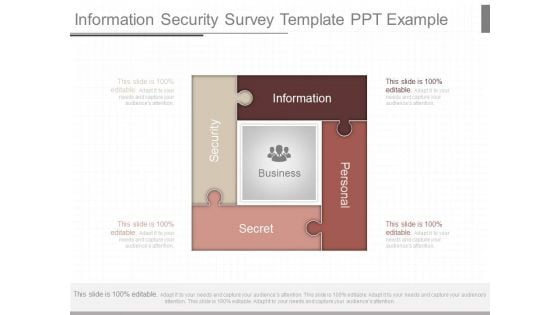
Information Security Survey Template Ppt Example
This is a information security survey template ppt example. This is a four stage process. The stages in this process are information, security, personal, secret.
Enterprise Security Strategy Sample Diagram Ppt Design
This is a enterprise security strategy sample diagram ppt design. This is a five stage process. The stages in this process are security strategy, governance, drivers, compliance, capability.
Big Data Security Model Ppt Presentations
This is a big data security model ppt presentations. This is a three stage process. The stages in this process are security model, confidentiality, availability, integrity.
Strategy Of Proactive Security Process Ppt Presentation
This is a strategy of proactive security process ppt presentation. This is a three stage process. The stages in this process are environment scanning, pear networking, result, threat detection, incident response, cyber incident.
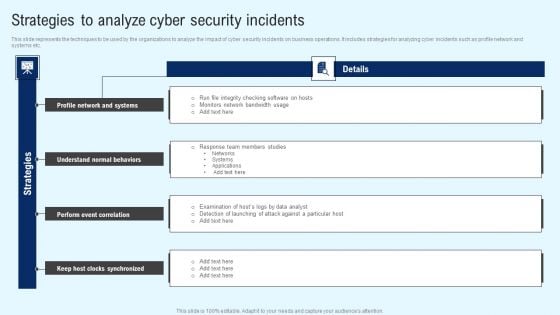
Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks has constructed Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Cover Letter For Cloud Security Firewall Proposal
Take your presentations to the next level with our Cover Letter For Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights. Cover Letter, Cloud Security Firewall Proposal
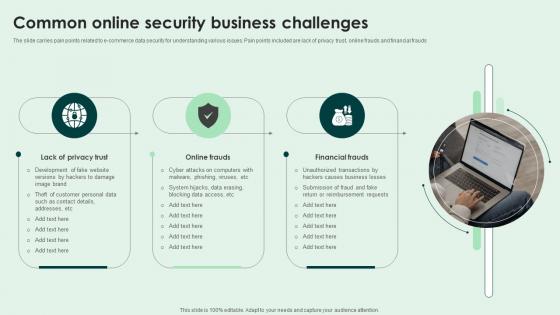
Common Online Security Business Challenges Guidelines Pdf
Showcasing this set of slides titled Common Online Security Business Challenges Guidelines Pdf. The topics addressed in these templates are Lack Of Privacy Trust, Online Frauds, Financial Frauds. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Common Online Security Business Challenges Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
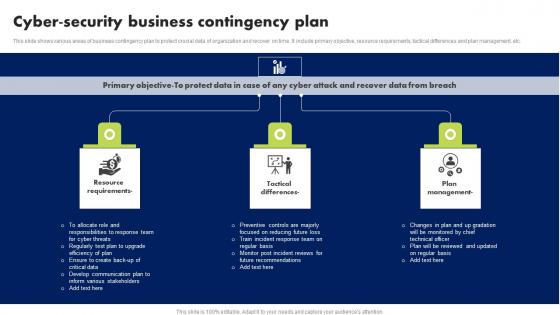
Cyber Security Business Contingency Plan Brochure Pdf
This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc. Showcasing this set of slides titled Cyber Security Business Contingency Plan Brochure Pdf. The topics addressed in these templates are Resource Requirements, Tactical Differences, Plan Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc.

Gantt Chart For Cloud Security Firewall Proposal
Power up your presentations with our Gantt Chart For Cloud Security Firewall Proposal single-slide PPT template. Our visually-stunning template will help you deliver your message with confidence. With easy-to-use editing options and fully customizable features, you can create polished and captivating presentations in no time. Say goodbye to boring slides and hello to impactful presentations with our top-quality template. Download now and get ready to wow your audience. singles Our Gantt Chart For Cloud Security Firewall Proposal are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
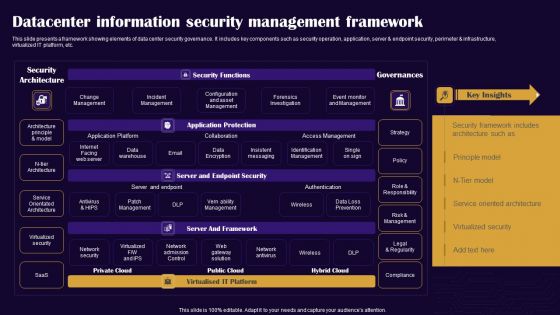
Datacenter Information Security Management Framework Professional PDF
This slide presents a framework showing elements of data center security governance. It includes key components such as security operation, application, server and endpoint security, perimeter and infrastructure, virtualized IT platform, etc. Pitch your topic with ease and precision using this Datacenter Information Security Management Framework Professional PDF. This layout presents information on Security Architecture, Security Functions, Governances. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
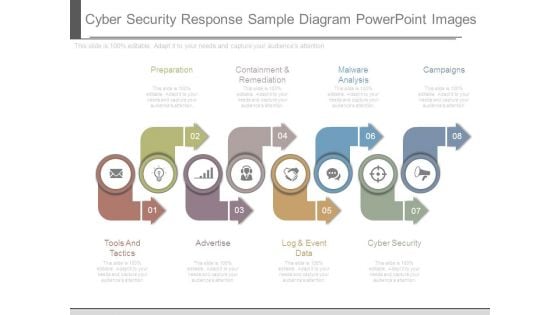
Cyber Security Response Sample Diagram Powerpoint Images
This is a cyber security response sample diagram powerpoint images. This is a eight stage process. The stages in this process are preparation, containment and remediation, malware analysis, campaigns, cyber security, log and event data, advertise, tools and tactics.

Data Security In Cloud Computing Ppt Presentation

Cloud Security Implementation Strategy Ppt Template
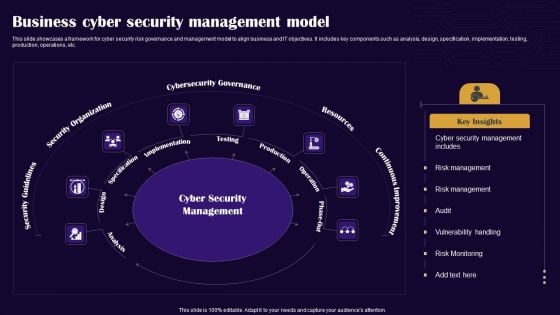
Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
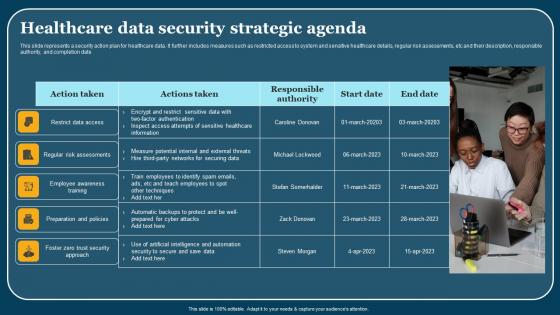
Healthcare Data Security Strategic Agenda Themes Pdf
This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date. Showcasing this set of slides titled Healthcare Data Security Strategic Agenda Themes Pdf. The topics addressed in these templates are Employee Awareness Training, Action Taken. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date.

Implementing Authentication In Application Security PPT Example
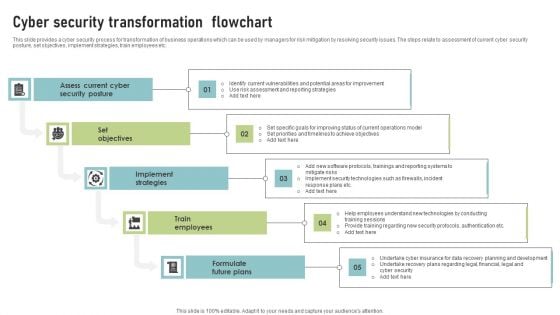
Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

What Is Cloud Security Guidelines PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Deliver an awe inspiring pitch with this creative What Is Cloud Security Guidelines PDF bundle. Topics like Computing Systems, Protocols, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Implementation Strategy Ppt Presentation

Mobile Application Security Testing PPT Sample

Cloud Native Application Security PPT Template
Web Acceleration Security Software Example Of Ppt
This is a web acceleration security software example of ppt. This is a four stage process. The stages in this process are web acceleration, security software, shopping carts, data services.
Data Security Challenges Template Powerpoint Templates
This is a data security challenges template powerpoint templates. This is a four stage process. The stages in this process are policy compliance, data management, data privacy, infrastructure security.

Internet Security Diagram Template Ppt Slide Styles
This is a internet security diagram template ppt slide styles. This is a five stage process. The stages in this process are search, protection, password, antivirus, firewall.


 Continue with Email
Continue with Email

 Home
Home


































