Process Safety
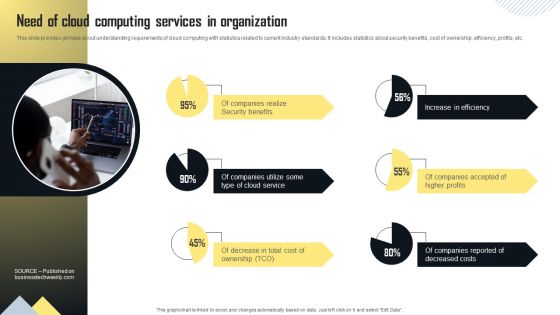
Need Of Cloud Computing Services In Organization Information PDF
This slide provides glimpse about understanding requirements of cloud computing with statistics related to current industry standards. It includes statistics about security benefits, cost of ownership, efficiency, profits, etc. Do you know about Slidesgeeks Need Of Cloud Computing Services In Organization Information PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF
This slide shows program for insider threat awareness training. It provides information such as program, details, system requirements, duration, fee or charge, etc. Showcasing this set of slides titled Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF. The topics addressed in these templates are Indicators Insider Threat, Protection Confidential Data, Insider Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
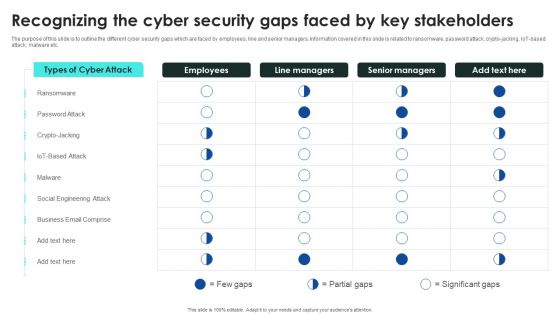
Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
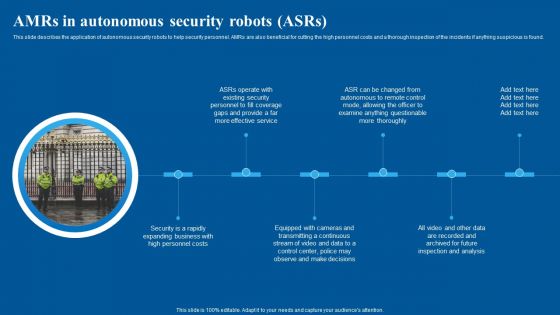
Amrs In Autonomous Security Robots Asrs Inspiration PDF
This slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Boost your pitch with our creative Amrs In Autonomous Security Robots Asrs Inspiration PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Information Technology Functions Management Table Of Content Ppt Model Files PDF
This is a information technology functions management table of content ppt model files pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to infrastructure, asset management process, inventory and condition assessment, deterioration modeling, optimization and decision making, performance and cost functions, interdependence, resiliency and security, contract and workflow management, commissioning new facilities, capital budgeting, metrics and dashboard. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF
This slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
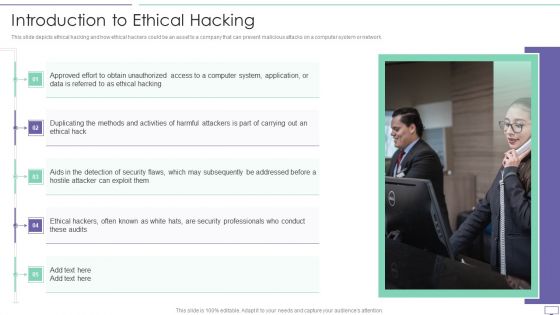
IT Security Hacker Introduction To Ethical Hacking Graphics PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network.This is a IT Security Hacker Introduction To Ethical Hacking Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Approved Effort, Data Is Referred, Ethical Hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
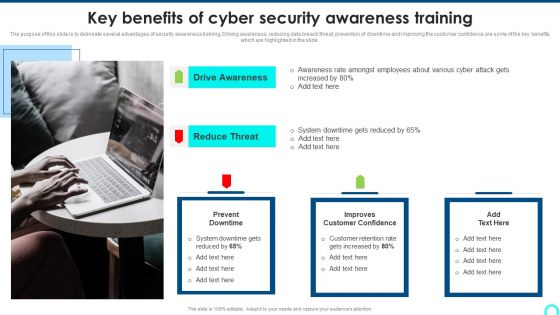
Key Benefits Of Cyber Security Awareness Training Background PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide.This is a Key Benefits Of Cyber Security Awareness Training Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drive Awareness, Reduce Threat, Amongst Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
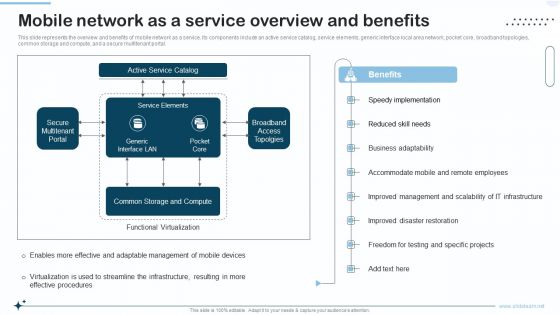
Naas Integrated Solution IT Mobile Network As A Service Overview And Benefits Formats PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. Deliver and pitch your topic in the best possible manner with this Naas Integrated Solution IT Mobile Network As A Service Overview And Benefits Formats PDF. Use them to share invaluable insights on Management, Employees, Implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
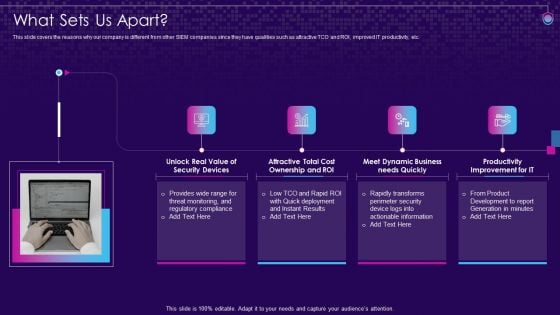
SIEM Services What Sets Us Apart Ppt Infographic Template Backgrounds PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting siem services what sets us apart ppt infographic template backgrounds pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, ownership, dynamic business, improvement it. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
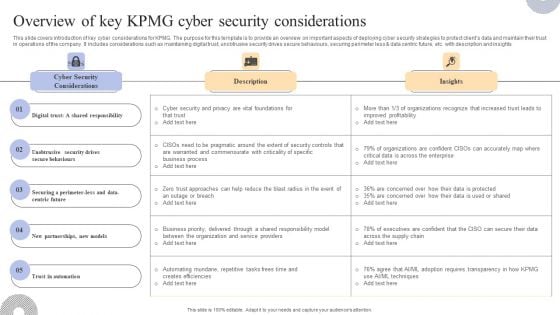
Overview Of Key KPMG Cyber Security Considerations Inspiration PDF
This slide covers an introduction to KPMG company ESG strategy to improve reporting to stakeholders. The purpose of this template is to provide overview on introducing ESG strategy, benefits along with reporting insights. It includes benefits such as helping organization assess and improve sustainable performance, establishing strong reputation and trust, attracting investors and customers, etc. Welcome to our selection of the Overview Of Key KPMG Cyber Security Considerations Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
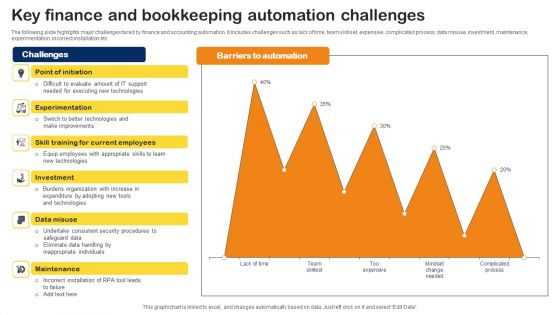
Key Finance And Bookkeeping Automation Challenges Professional PDF
The following slide highlights major challenges faced by finance and accounting automation. It includes challenges such as lack of time, team skillset, expensive, complicated process, data misuse, investment, maintenance, experimentation, incorrect installation etc. Showcasing this set of slides titled Key Finance And Bookkeeping Automation Challenges Professional PDF. The topics addressed in these templates are Burdens Organization, Investment, Consistent Security Procedures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
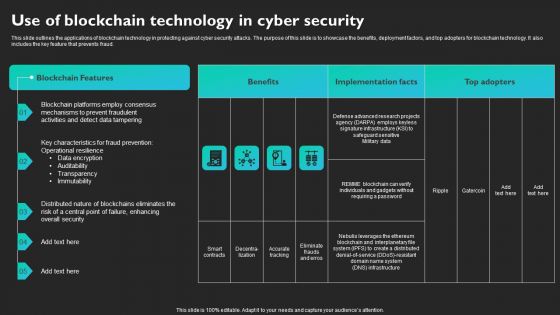
Use Of Blockchain Technology In Cyber Security Slides PDF
This slide outlines the applications of blockchain technology in protecting against cyber security attacks. The purpose of this slide is to showcase the benefits, deployment factors, and top adopters for blockchain technology. It also includes the key feature that prevents fraud. Find a pre-designed and impeccable Use Of Blockchain Technology In Cyber Security Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
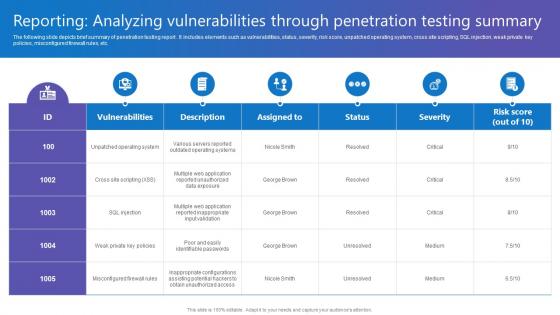
Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf
The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc. Do you know about Slidesgeeks Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc.

Wireless Banking To Improve Popular Mobile Banking Apps Available In Market Fin SS V
This slide shows details about best mobile banking apps based on different types of features such as customer service, security, money management, account management, etc. which can be used by customers while selecting banking apps. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Wireless Banking To Improve Popular Mobile Banking Apps Available In Market Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows details about best mobile banking apps based on different types of features such as customer service, security, money management, account management, etc. which can be used by customers while selecting banking apps.
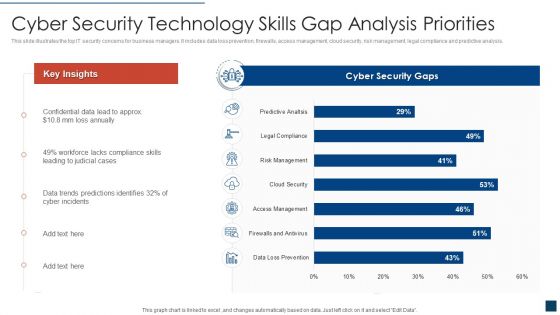
Cyber Security Technology Skills Gap Analysis Priorities Clipart PDF
This slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Showcasing this set of slides titled cyber security technology skills gap analysis priorities clipart pdf. The topics addressed in these templates are cyber security technology skills gap analysis priorities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Operations Team Roles And Responsibilities Infographics PDF
This slide exhibits key roles on the SecOps team with their roles and responsibilities that manage cybersecurity threats and attacks. It includes a security investigator, advanced security analyst, SOC manager, and security manager. Presenting Security Operations Team Roles And Responsibilities Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Skills Required, Determine, Develop Mitigation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
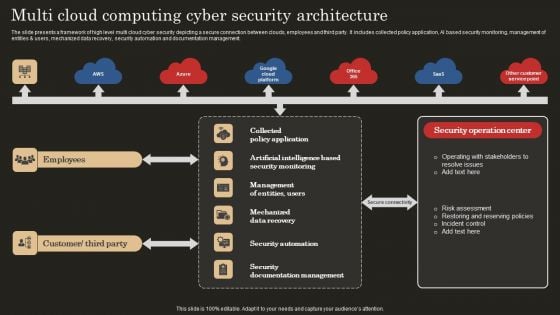
Multi Cloud Computing Cyber Security Architecture Microsoft PDF
The slide presents a framework of high level multi cloud cyber security depicting a secure connection between clouds, employees and third party. It includes collected policy application, AI based security monitoring, management of entities and users, mechanized data recovery, security automation and documentation management. Showcasing this set of slides titled Multi Cloud Computing Cyber Security Architecture Microsoft PDF. The topics addressed in these templates are Mechanized Data Recovery, Security Automation, Employees. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
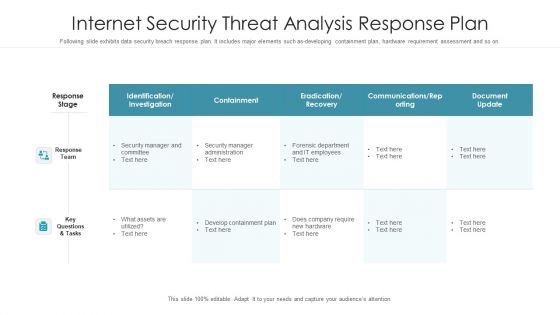
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Securities Analyst Resume In One Pager PDF Document PPT Template
Presenting you a fantastic Securities Analyst Resume In One Pager PDF Document PPT Template. This one-pager document is crafted on hours of research and professional design efforts to ensure you have the best resource. It is completely editable and its design allow you to rehash its elements to suit your needs. Get this Securities Analyst Resume In One Pager PDF Document PPT Template Download now.
Timeline Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary Timeline Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.
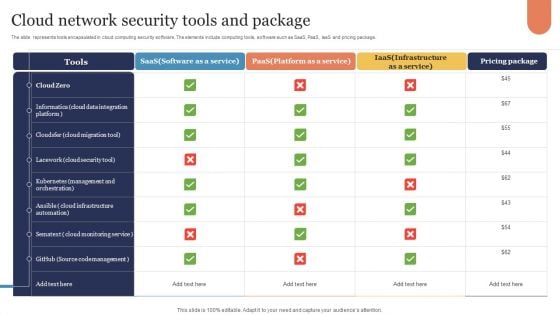
Cloud Network Security Tools And Package Graphics PDF
The slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Showcasing this set of slides titled Cloud Network Security Tools And Package Graphics PDF. The topics addressed in these templates are Saas, Paas, Iaas. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
RCA Action Plan For Business Cyber Security Icons PDF
This slide shows root cause analysis action plan to identify and provide strategies for overcoming cyber security threats. It include root cause, action plan and outcomes, etc. Showcasing this set of slides titled RCA Action Plan For Business Cyber Security Icons PDF Elements. The topics addressed in these templates are Root Cause, Action Plan, Outcomes. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
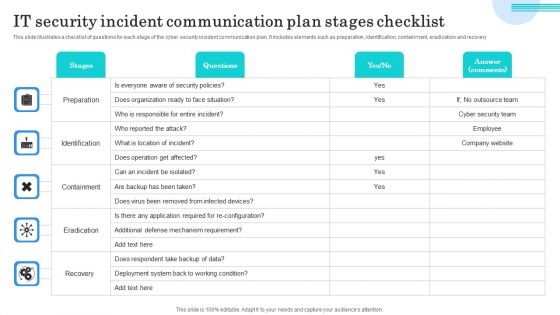
IT Security Incident Communication Plan Stages Checklist Topics PDF
This slide illustrates a checklist of questions for each stage of the cyber security incident communication plan. It includes elements such as preparation, identification, containment, eradication and recovery. Showcasing this set of slides titled IT Security Incident Communication Plan Stages Checklist Topics PDF. The topics addressed in these templates are Preparation, Identification, Containment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Shift Capital Fundraising Pitch Deck Shifts Operational Technology And Financial Service Challenges Icons PDF
The following slide provides information about the operational technology and financial services challenges that are faced by Shift such as pricing challenges, distributed workforce challenges, merchandizing and marketing challenges, payment and security challenges, fraud prevention etc. This is a shift capital fundraising pitch deck shifts operational technology and financial service challenges icons pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like operations technology, financial services technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Computer Security Incident Handling Dashboard Incident Tracking Ppt Gallery Infographics PDF
Presenting this set of slides with name computer security incident handling dashboard incident tracking ppt gallery infographics pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, user application hardening, daily backup of important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Implementation Framework Dashboard Incident Tracking Ppt Styles Topics PDF
Presenting this set of slides with name cyber security implementation framework dashboard incident tracking ppt styles topics pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Essential Contingency Plan Strategies Ppt Portfolio Introduction PDF
Presenting this set of slides with name cyber security implementation framework essential contingency plan strategies ppt portfolio introduction pdf. The topics discussed in these slides are contingency considerations, contingency solutions, vendors coordination, system backups. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Contents Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Information PDF
Deliver and pitch your topic in the best possible manner with this table of contents modern security observation plan to eradicate cybersecurity risk and data breach information pdf. Use them to share invaluable insights on essential elements of security, compromised and measures, performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
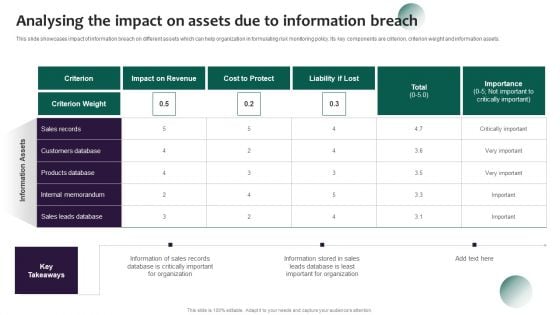
Information Systems Security And Risk Management Plan Analysing The Impact On Assets Due To Information Breach Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. This Information Systems Security And Risk Management Plan Analysing The Impact On Assets Due To Information Breach Introduction PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Table Of Contents For Risk Based Procedures To IT Security Wd Ppt PowerPoint Presentation File Professional PDF
This is a Table Of Contents For Risk Based Procedures To IT Security Wd Ppt PowerPoint Presentation File Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Global Market, IoT Products, Companies Digitization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
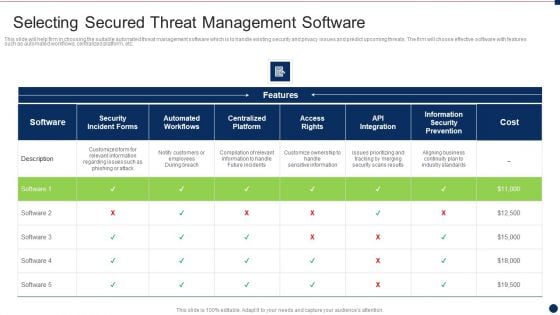
Threat Management At Workplace Selecting Secured Threat Management Software Information PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace selecting secured threat management software information pdf. Use them to share invaluable insights on customize ownership to handle sensitive information, compilation of relevant information to handle future incidents, aligning business continuity plan to industry standards and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
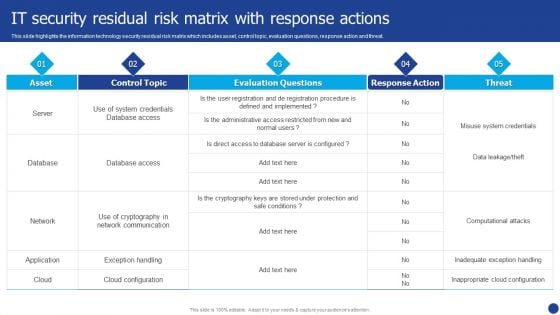
Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
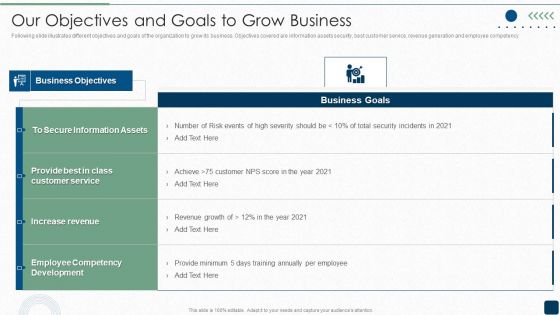
Our Objectives And Goals To Grow Business Elements PDF
Following slide illustrates different objectives and goals of the organization to grow its business. Objectives covered are information assets security, best customer service, revenue generation and employee competency.Deliver an awe inspiring pitch with this creative Our Objectives And Goals To Grow Business Elements PDF bundle. Topics like Information Assets, Increase Revenue, Competency Development can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
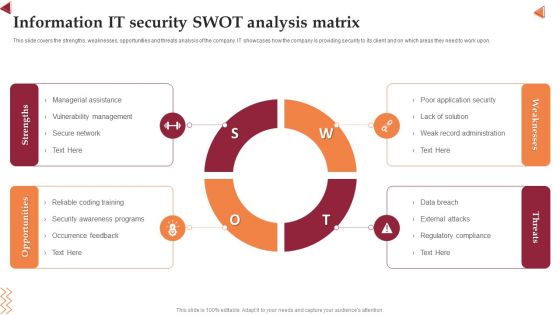
Information IT Security Swot Analysis Matrix Clipart PDF
This slide covers the strengths, weaknesses, opportunities and threats analysis of the company. IT showcases how the company is providing security to its client and on which areas they need to work upon. Persuade your audience using this Information IT Security Swot Analysis Matrix Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Opportunities, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Conducting Cyber Security Gap Analysis Of Organization Formats PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Boost your pitch with our creative Conducting Cyber Security Gap Analysis Of Organization Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Corporate Digital Transformation Roadmap Budget Allocation For Digital Icons PDF
Purpose of the following slide is to show the budget for digital transformation as it highlights the key components of the budget along with the total amount allocated for the entire process. Deliver and pitch your topic in the best possible manner with this Corporate Digital Transformation Roadmap Budget Allocation For Digital Icons PDF Use them to share invaluable insights on Improve Security, Upgrading Network, Most Impotent Technology Investment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
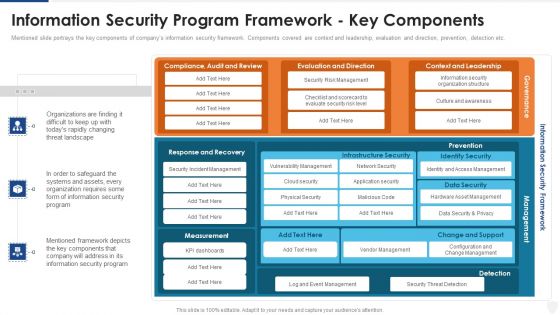
Information Security Program Framework Key Components Ppt Inspiration Ideas PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this information security program framework key components ppt inspiration ideas pdf. Use them to share invaluable insights on network security, application security, vendor management, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
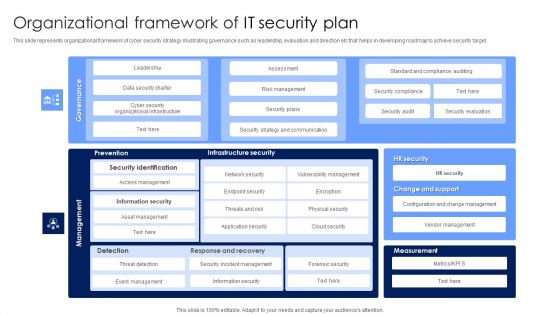
Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
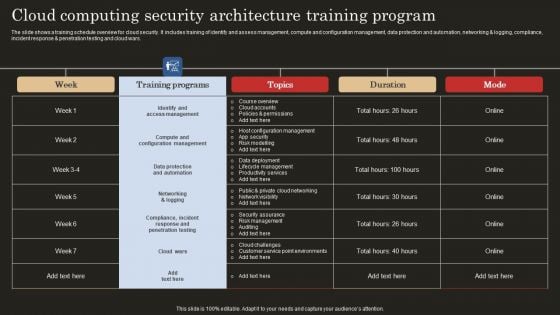
Cloud Computing Security Architecture Training Program Guidelines PDF
The slide shows a training schedule overview for cloud security. It includes training of identify and assess management, compute and configuration management, data protection and automation, networking and logging, compliance, incident response and penetration testing and cloud wars. Showcasing this set of slides titled Cloud Computing Security Architecture Training Program Guidelines PDF. The topics addressed in these templates are Identify Access Management, Compute Configuration Management, Data Protection Automation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
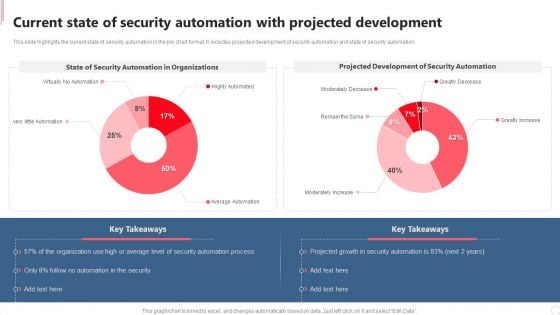
Current State Of Security Automation With Projected Development Rules PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed Current State Of Security Automation With Projected Development Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Current State Of Security Automation With Projected Development Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
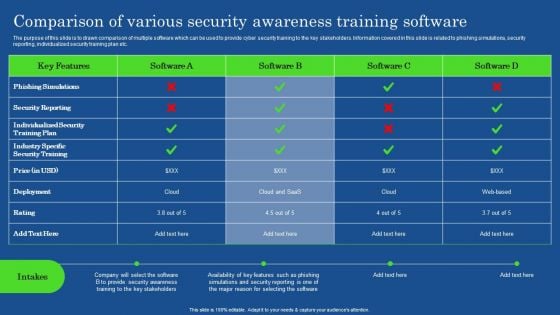
Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Adaptive Work Arrangements Guidelines To Successfully Develop Flexible Work Policy Pictures PDF
The following slide showcases important instructions related to the work from home WFH policy that can assist corporates to draft rules and regulations for remote employees. It contains information about security protocols, online meeting etiquette, expenditure, and team building activities. This modern and well arranged Implementing Adaptive Work Arrangements Guidelines To Successfully Develop Flexible Work Policy Pictures PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
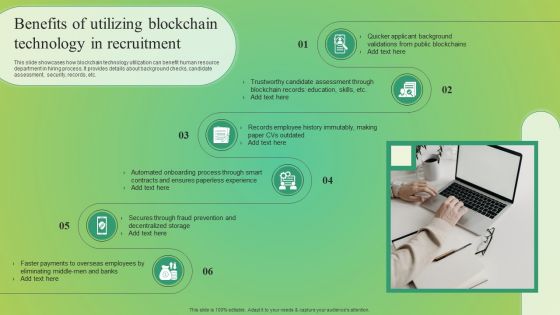
Benefits Of Utilizing Blockchain Technology In Recruitment Information PDF
This slide showcases how blockchain technology utilization can benefit human resource department in hiring process. It provides details about background checks, candidate assessment, security, records, etc. Boost your pitch with our creative Benefits Of Utilizing Blockchain Technology In Recruitment Information PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
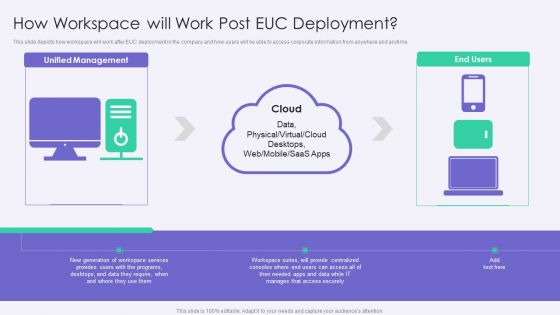
VID How Workspace Will Work Post EUC Deployment Template PDF
This slide depicts how workspace will work after EUC deployment in the company and how users will be able to access corporate information from anywhere and anytime.This is a VID How Workspace Will Work Post EUC Deployment Template PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Workspace Services, Access Securely, Provide Centralized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Service Marketing Fundraising What Business Challenges Are Faced By Prospect Icons PDF
This slide caters details about key business challenges are faced by prospects in context to services such as high IT cost, poor business agility, regulatory compliances, etc. Presenting service marketing fundraising what business challenges are faced by prospect icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like poor business agility, regulatory compliances, security threats, infrastructure silos. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
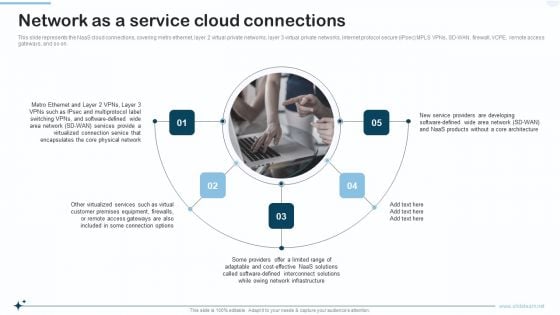
Naas Integrated Solution IT Network As A Service Cloud Connections Topics PDF
This slide represents the NaaS cloud connections, covering metro ethernet, layer 2 virtual private networks, layer 3 virtual private networks, internet protocol secure IPsec MPLS VPNs, SD-WAN, firewall, VCPE, remote access gateways, and so on. This is a Naas Integrated Solution IT Network As A Service Cloud Connections Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Services, Network, Equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
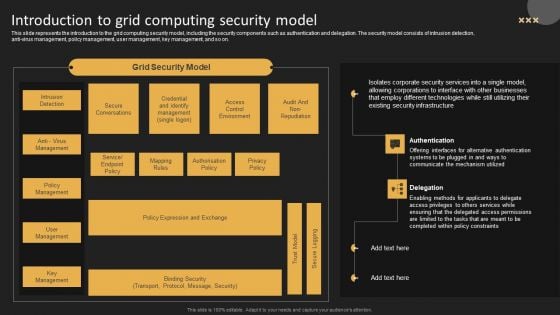
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Five Year Marketing Strategy Financial Portfolio Professional PDF
This slide illustrate five year plan to diversify financial portfolio, become debt free and generate enough emergency funds. It includes elements such as goals, process, success indicator and benefits. Pitch your topic with ease and precision using this Five Year Marketing Strategy Financial Portfolio Professional PDF. This layout presents information on Reduces Impact, Market Volatility, Financial Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
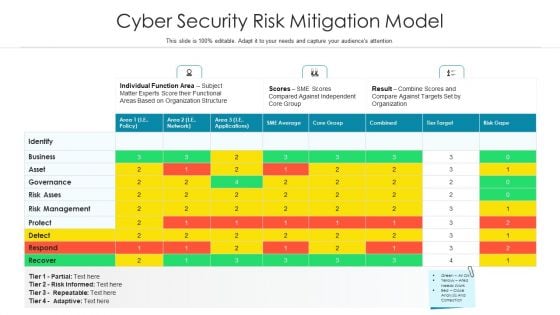
Cyber Security Risk Mitigation Model Ppt PowerPoint Presentation Infographics Sample PDF
Showcasing this set of slides titled cyber security risk mitigation model ppt powerpoint presentation infographics sample pdf. The topics addressed in these templates are risk management, functional areas based, subject matter experts score. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
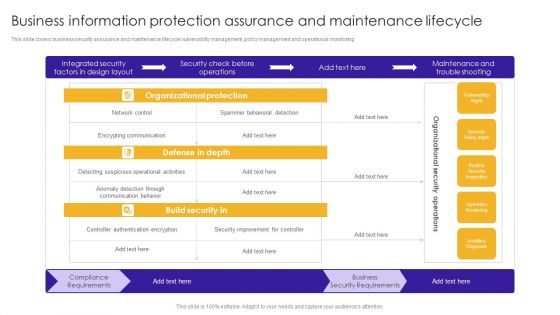
Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF
This slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring.Showcasing this set of slides titled Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF. The topics addressed in these templates are Encrypting Communication, Detecting Suspicious, Authentication Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
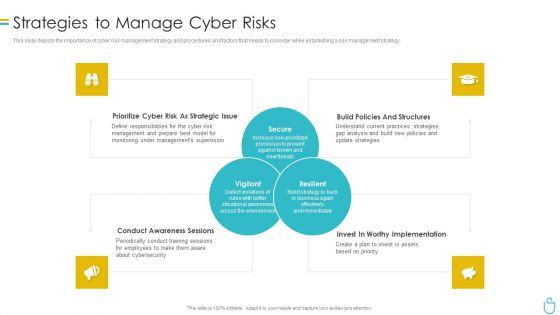
Information Security Strategies To Manage Cyber Risks Ppt Layouts Gridlines PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information security strategies to manage cyber risks ppt layouts gridlines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk, management, strategies, analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

QA Modification For Product Quality Development And Consumer Satisfaction Implement Code Quality Brochure PDF
This slide shows the details about Code Quality Measurements Approach for Effective QA Transformation along with details on Software Quality Indicators and Test Metrics such as Reliability, Security, Testability, Rate of Delivery etc. Presenting qa modification for product quality development and consumer satisfaction implement code quality brochure pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like reliability, performance efficiency, security, maintainability, rate of delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
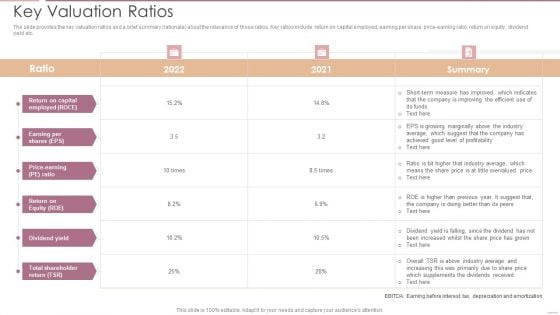
Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF
The slide provides the key valuation ratios and a brief summary rationale about the relevance of those ratios. Key ratios include return on capital employed, earning per share, price-earning ratio, return on equity, dividend yield etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF Use them to share invaluable insights on Measure Improved, Dividends Received, Total Shareholder and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
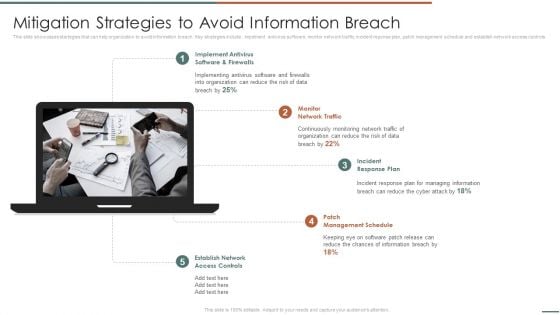
Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Various Types And Categories Of Internal Audit In The Company Contd Ppt Portfolio Ideas PDF
This slide provides information regarding the various types and categories of internal audit in the company in detail. Presenting various types and categories of internal audit in the company contd ppt portfolio ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, evaluate information, customer, processing, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
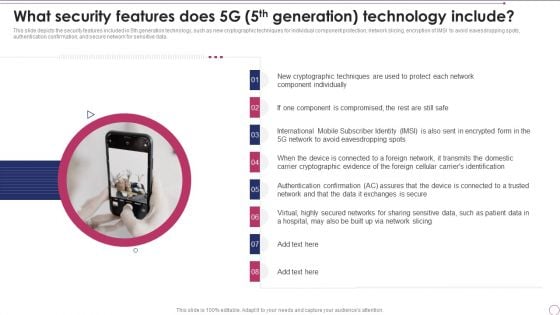
1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Presenting 1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Cryptographic Evidence, Domestic, Via Network Slicing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Track Record Of Our Company Themes PDF
This slide highlights our past track record as a data privacy provider company and outlines that we promise 100 percent client satisfaction. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Security Track Record Of Our Company Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
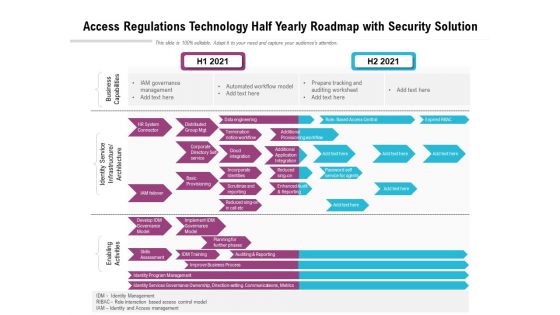
Access Regulations Technology Half Yearly Roadmap With Security Solution Guidelines
Presenting the access regulations technology half yearly roadmap with security solution guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
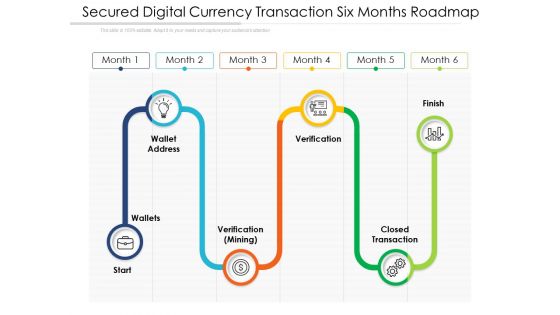
Secured Digital Currency Transaction Six Months Roadmap Guidelines
Presenting the secured digital currency transaction six months roadmap guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.


 Continue with Email
Continue with Email

 Home
Home


































