Process Safety
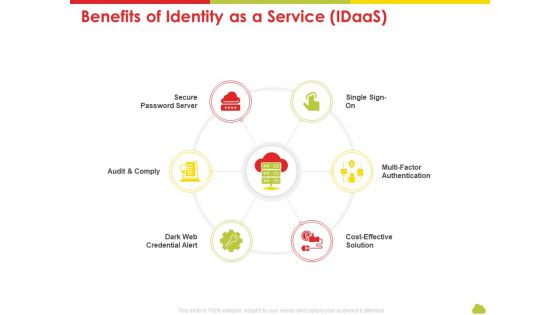
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Benefits Of Identity As A Service Idaas Brochure PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan benefits of identity as a service idaas brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dark web credential alert, cost effective solution, multi factor authentication, secure password server, audit and comply. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
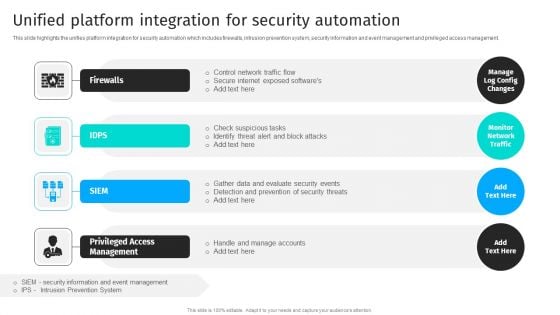
Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management.The Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
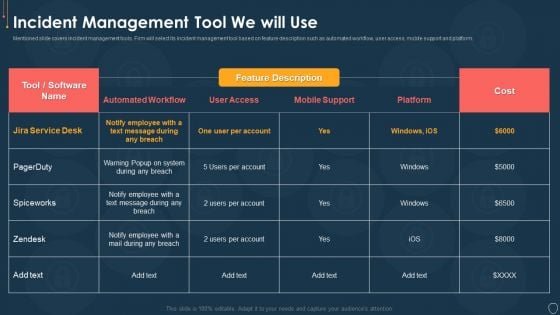
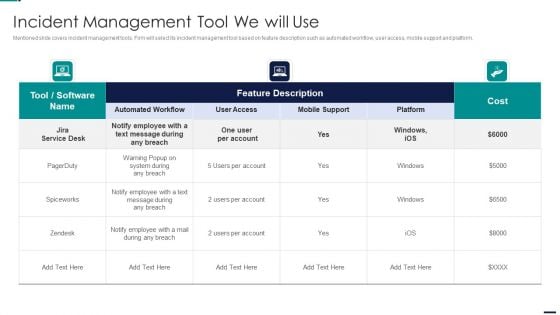
Cyber Security Risk Management Plan Incident Management Tool We Will Use Mockup PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative cyber security risk management plan incident management tool we will use mockup pdf bundle. Topics like incident management tool we will use can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Based Email Security Market Report Industry Trends Ppt Styles Diagrams PDF
Major trends of the E mail security industry are shown in this slide. This is a cloud based email security market report industry trends ppt styles diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security system, artificial intelligence, supply chain security, security adaptive approach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
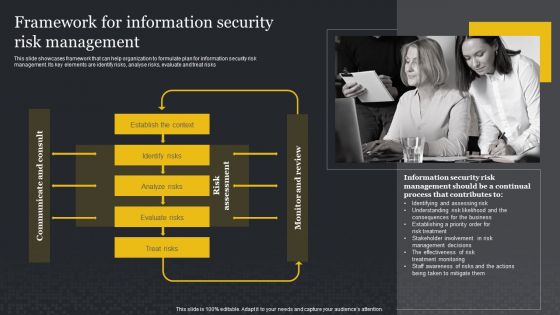
Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks. Presenting this PowerPoint presentation, titled Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Health Protection Plan For Secured Life Vector Icon Ppt PowerPoint Presentation Slides Examples PDF
Pitch your topic with ease and precision using this health protection plan for secured life vector icon ppt powerpoint presentation slides examples pdf. This layout presents information on health protection plan for secured life vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Protection Vector Showing Secured Bitcoin With Dollar Symbol Ppt PowerPoint Presentation Infographic Template Icon PDF
Showcasing this set of slides titled protection vector showing secured bitcoin with dollar symbol ppt powerpoint presentation infographic template icon pdf. The topics addressed in these templates are protection vector showing secured bitcoin with dollar symbol. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Of Business Website Vector Icon Ppt PowerPoint Presentation Pictures Infographics PDF
Showcasing this set of slides titled security of business website vector icon ppt powerpoint presentation pictures infographics pdf. The topics addressed in these templates are security of business website vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Measures To Prevent Accident At Workplace Ppt PowerPoint Presentation Pictures Display PDF
Showcasing this set of slides titled security measures to prevent accident at workplace ppt powerpoint presentation pictures display pdf. The topics addressed in these templates are security measures to prevent accident at workplace. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
App Design Model Icon For Security Optimization Ppt PowerPoint Presentation Inspiration PDF
Showcasing this set of slides titled app design model icon for security optimization ppt powerpoint presentation inspiration pdf. The topics addressed in these templates are app design model icon for security optimization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Saas Cloud Security Action Plan Icon Ppt PowerPoint Presentation File Templates PDF
Showcasing this set of slides titled Saas Cloud Security Action Plan Icon Ppt PowerPoint Presentation File Templates PDF. The topics addressed in these templates are Saas Cloud Security, Action Plan, Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF
Pitch your topic with ease and precision using this Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF. This layout presents information on Virus Cyber Security, Attack Warning, Web Browser Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDFbundle. Topics like Cost, Employee, Mobile Support, Automated Workflow, User Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Risk Management KPI Dashboard With Loss Events Brochure PDF
Following slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Risk Management KPI Dashboard With Loss Events Brochure PDF bundle. Topics like Key Risk Indicators, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mobile Device Management For Ios Platform Mobile Device Security Management Mockup PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Deliver an awe inspiring pitch with this creative Mobile Device Management For Ios Platform Mobile Device Security Management Mockup PDF bundle. Topics like Device Enrollment, Theft Protection, Remote Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
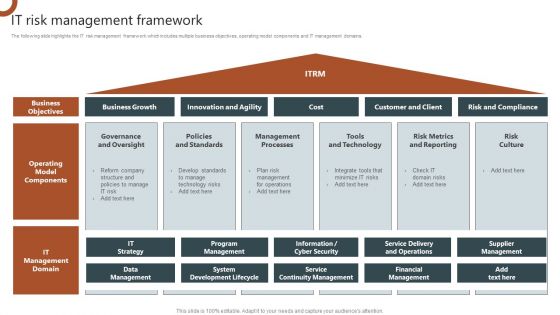
IT Risk Management Framework Organizations Risk Management And IT Security Ideas PDF
The following slide highlights the IT risk management framework which includes multiple business objectives, operating model components and IT management domains. There are so many reasons you need a IT Risk Management Framework Organizations Risk Management And IT Security Ideas PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
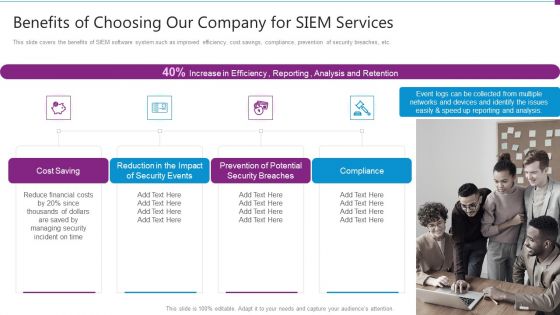
Security Information And Event Management Strategies For Financial Audit And Compliance Benefits Of Choosing Our Company Topics PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a security information and event management strategies for financial audit and compliance benefits of choosing our company topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, security breaches, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF
The following slide illustrates some SaaS security threats to enhance security practices and eliminate them. It includes elements such as phishing, account takeovers, lack of transparency etc. Showcasing this set of slides titled Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF. The topics addressed in these templates are Comprehending Risks, Phishing, Account Takeovers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
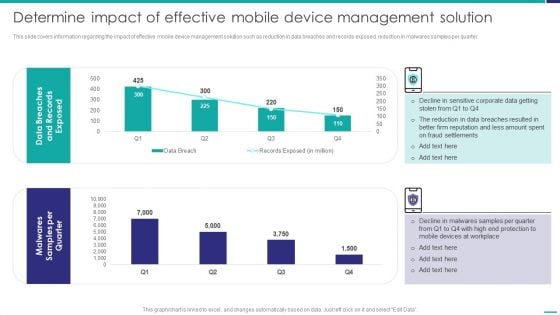
Determine Impact Of Effective Mobile Device Management Solution Mobile Device Security Management Graphics PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. Deliver an awe inspiring pitch with this creative Determine Impact Of Effective Mobile Device Management Solution Mobile Device Security Management Graphics PDF bundle. Topics like Fraud Settlements, Devices Workplace, Malwares Samples can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Customer Value Proposition Security Easy Management Energy Saving Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name customer value proposition security easy management energy saving ppt powerpoint presentation complete deck. The topics discussed in these slides are security, easy management, energy saving, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CIO Role In Digital Evolution Cloud Security Architect Skills Scope Structure PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational, technical, etc. Deliver and pitch your topic in the best possible manner with this CIO Role In Digital Evolution Cloud Security Architect Skills Scope Structure PDF. Use them to share invaluable insights on Architecture Strategy, Risk Management, Business Architecture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
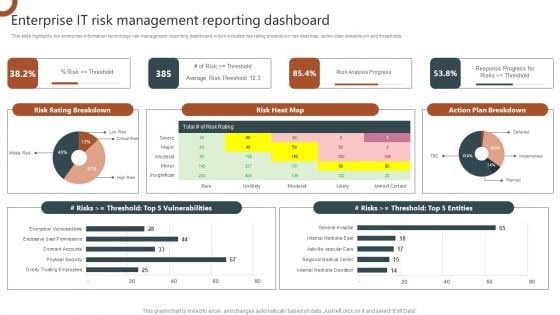
Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF
This slide highlights the enterprise information technology risk management reporting dashboard which includes risk rating breakdown risk heat map, action plan breakdown and thresholds. This Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
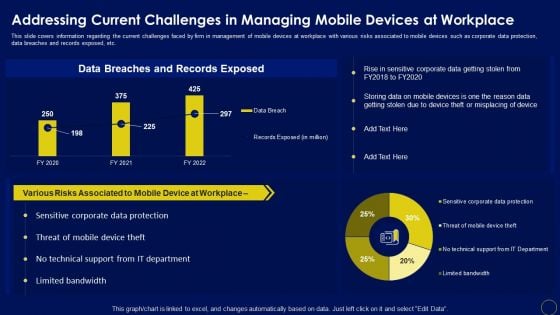
Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
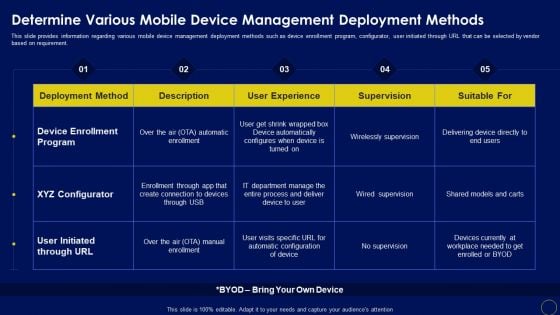
Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF.
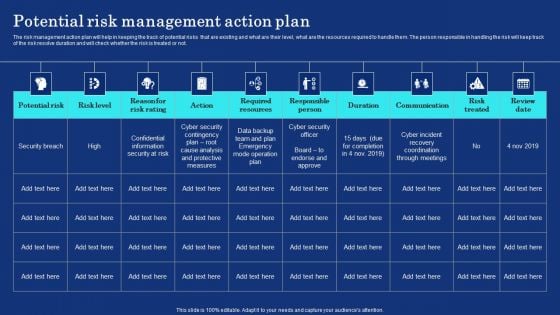
Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF can be your best option for delivering a presentation. Represent everything in detail using Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Business Security Problem And Threat Management Ppt PowerPoint Presentation Model Gridlines PDF
Pitch your topic with ease and precision using this business security problem and threat management ppt powerpoint presentation model gridlines pdf. This layout presents information on business security problem and threat management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Risk Prevention And Security Management Vector Icon Ppt PowerPoint Presentation File Background Images PDF
Showcasing this set of slides titled risk prevention and security management vector icon ppt powerpoint presentation file background images pdf. The topics addressed in these templates are risk prevention and security management vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
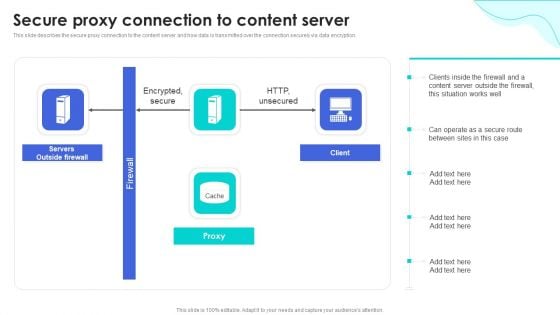
Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Find a pre-designed and impeccable Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents For Comprehensive Guide To Blockchain Digital Security Risk Management Download Pdf
Boost your pitch with our creative Table Of Contents For Comprehensive Guide To Blockchain Digital Security Risk Management Download Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Table Of Contents For Comprehensive Guide To Blockchain Digital Security Risk Management Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Corporate Security And Risk Management Determine Threat Management Team Structure Topics PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a corporate security and risk management determine threat management team structure topics pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
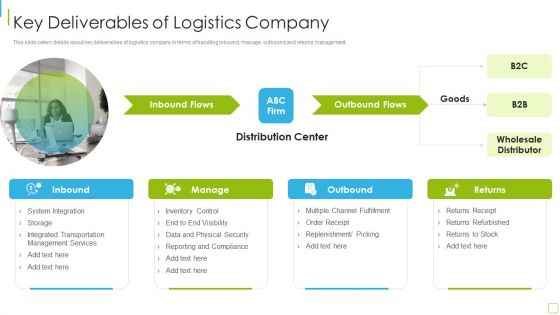
Performance Analysis Of New Product Development Key Deliverables Of Logistics Company Information PDF
This slide caters details about key deliverables of logistics company in terms of handling inbound, manage, outbound and returns management. Presenting performance analysis of new product development key deliverables of logistics company information pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like system integration, management services, inventory control, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Increase Cloud Security Threats Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name how to increase cloud security threats ppt powerpoint presentation complete deck. The topics discussed in these slides are security assessments, security threats, cloud computing security, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Corporate Security And Risk Management Cyber Threats Management Dashboard Ideas PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver and pitch your topic in the best possible manner with this corporate security and risk management cyber threats management dashboard ideas pdf. Use them to share invaluable insights on cyber threats management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
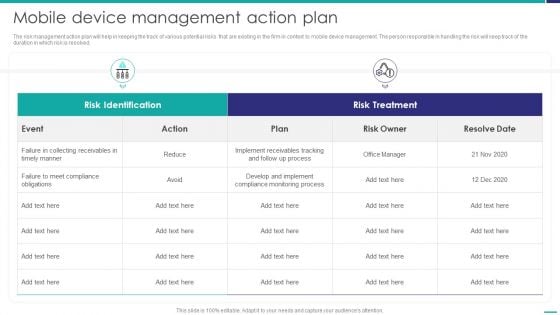
Mobile Device Management Action Plan Mobile Device Security Management Rules PDF
The risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.Deliver an awe inspiring pitch with this creative Mobile Device Management Action Plan Mobile Device Security Management Rules PDF bundle. Topics like Collecting Receivables, Compliance Obligations, Compliance Monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF
The risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
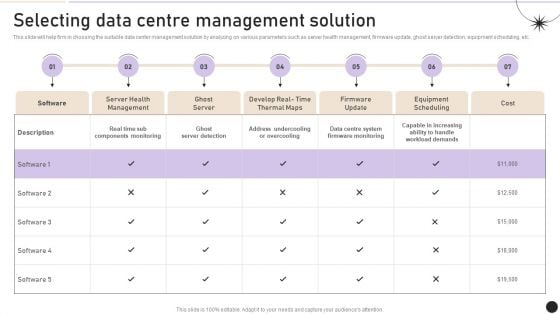
Selecting Data Centre Management Solution Workplace Security Management Program Information PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Selecting Data Centre Management Solution Workplace Security Management Program Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
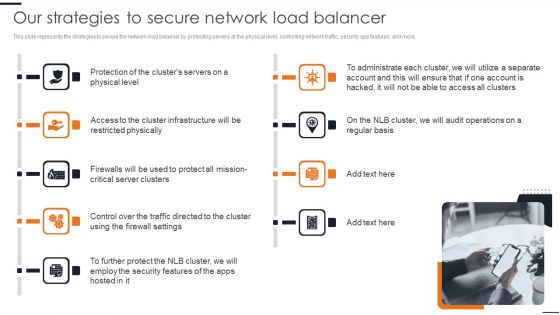
Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. This modern and well arranged Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. This Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
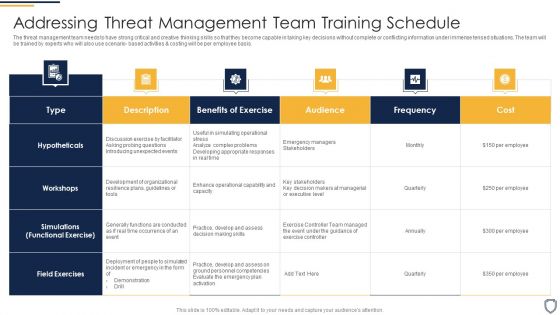
Corporate Security And Risk Management Addressing Threat Management Team Training Schedule Clipart PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative corporate security and risk management addressing threat management team training schedule clipart pdf bundle. Topics like benefits of exercise, audience, frequency, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
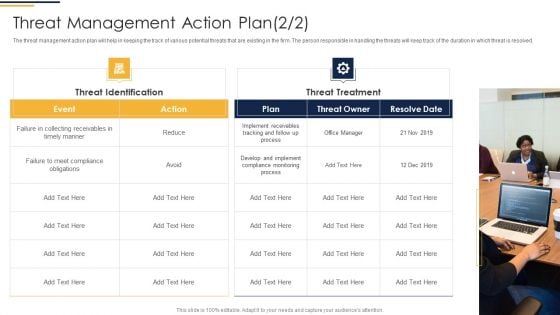
Corporate Security And Risk Management Threat Management Action Plan Introduction PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this corporate security and risk management threat management action plan introduction pdf. Use them to share invaluable insights on potential risk, risk level, action, duration, risk treated and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This is a Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Container Approach, Platform Approach, Critical Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Various Mobile Device Management Deployment Methods Mobile Device Security Management Summary PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. This is a Determine Various Mobile Device Management Deployment Methods Mobile Device Security Management Summary PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enrollment Program, Configurator, Automatic Enrollment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management Assistance To Mobile Device Security Management Professional PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. This is a Mobile Device Management Assistance To Mobile Device Security Management Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reducing Connection, Rendering Appropriate, Remote Configuration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
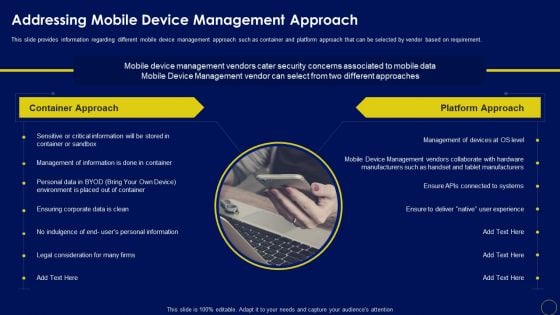
Addressing Mobile Device Management Business Mobile Device Security Management Download PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This modern and well-arranged Addressing Mobile Device Management Business Mobile Device Security Management Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. Present like a pro with Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
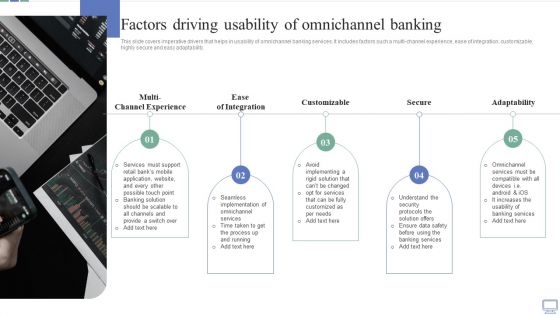
Omnichannel Banking Services Platform Factors Driving Usability Of Omnichannel Banking Background PDF
This slide covers imperative drivers that helps in usability of omnichannel banking services. It includes factors such a multi channel experience, ease of integration, customizable, highly secure and easy adaptability. Get a simple yet stunning designed Omnichannel Banking Services Platform Factors Driving Usability Of Omnichannel Banking Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Omnichannel Banking Services Platform Factors Driving Usability Of Omnichannel Banking Background PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
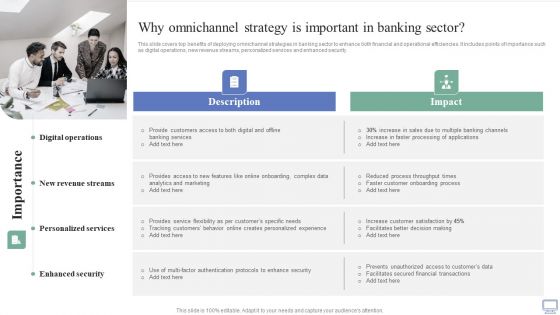
Omnichannel Banking Services Platform Why Omnichannel Strategy Is Important In Banking Sector Diagrams PDF
This slide covers top benefits of deploying omnichannel strategies in banking sector to enhance both financial and operational efficiencies. It includes points of importance such as digital operations, new revenue streams, personalized services and enhanced security. Are you searching for a Omnichannel Banking Services Platform Why Omnichannel Strategy Is Important In Banking Sector Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Omnichannel Banking Services Platform Why Omnichannel Strategy Is Important In Banking Sector Diagrams PDF from Slidegeeks today.
Email Security Encryption And Data Loss Prevention Client Testimonial Guidelines PDF
This Slide shows the testimonials of the previous clients who have worked with you. Presenting email security encryption and data loss prevention client testimonial guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like client testimonial. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
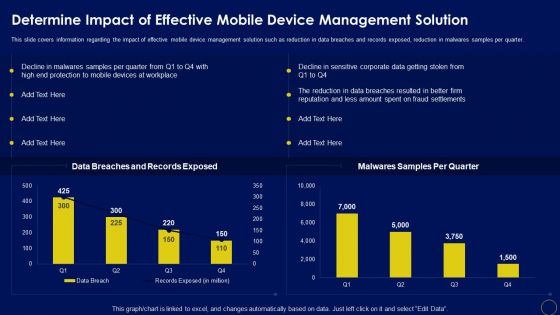
Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. The Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
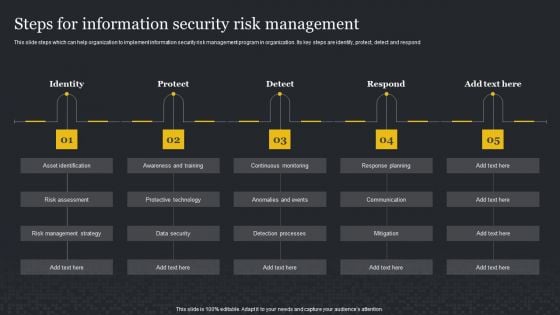
Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Create an editable Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
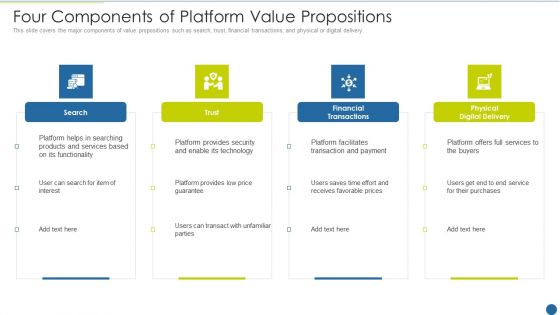
Expedite Multi Sided System Four Components Of Platform Value Propositions Infographics PDF
This is a expedite multi sided system four components of platform value propositions infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, security, services, prices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Security Management Strategy To Mitigate Risk Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This implementing security management strategy to mitigate risk ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fortytwo slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Table Of Contents For Cloud Information Security Ppt Slides Vector PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Cloud Information Security Ppt Slides Vector PDF. Use them to share invaluable insights on Cloud Management, Cloud Responsibilities, Shared Vulnerabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Ppt PowerPoint Presentation Complete Deck With Slides

IT Security Risk Management Approach Introduction Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fifty two slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.


 Continue with Email
Continue with Email

 Home
Home


































