Safety First
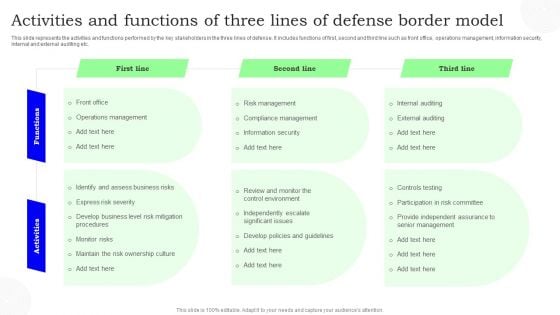
Activities And Functions Of Three Lines Of Defense Border Model Slides PDF
This slide represents the activities and functions performed by the key stakeholders in the three lines of defense. It includes functions of first, second and third line such as front office, operations management, information security, internal and external auditing etc. Showcasing this set of slides titled Activities And Functions Of Three Lines Of Defense Border Model Slides PDF. The topics addressed in these templates are First Line, Second Line, Third Line. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF
There are so many reasons you need a Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Rescue Statistics PowerPoint Icon C
3d illustration of a multi-segment colorful bar chart placed inside of a large red and white lifesaver on a reflective surface Be the early bird with our Rescue Statistics PowerPoint Icon C. Be the first on the block with your thoughts.

Table Of Contents For Integrating Data Privacy System To Enhance Securitys Sample PDF
There are so many reasons you need a Table Of Contents For Integrating Data Privacy System To Enhance Securitys Sample PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Security Control Techniques For Real Estate Project Organizational Chart For Construction Site Designs PDF
There are so many reasons you need a Security Control Techniques For Real Estate Project Organizational Chart For Construction Site Designs PDF. The first reason is you canot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Healthcare Management Overview Trends Stats And Operational Areas Developing New Healthcare Policies And Procedures Background PDF
The following slide showcases different type of healthcare policies. Patient care, health and safety, information management, drug handling and management are the major policies which are outlined in the slide. There are so many reasons you need a Healthcare Management Overview Trends Stats And Operational Areas Developing New Healthcare Policies And Procedures Background PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
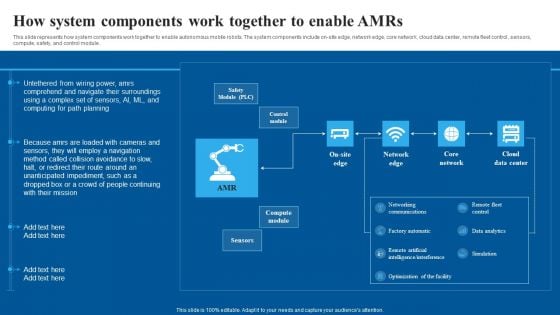
How System Components Work Together To Enable Amrs Mockup PDF
This slide represents how system components work together to enable autonomous mobile robots. The system components include on-site edge, network edge, core network, cloud data center, remote fleet control, sensors, compute, safety, and control module. There are so many reasons you need a How System Components Work Together To Enable Amrs Mockup PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
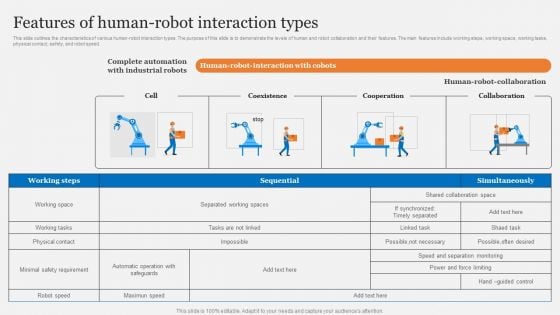
Cobots Usecases In Different Sectors Features Of Human Robot Interaction Types Designs PDF
This slide outlines the characteristics of various human-robot interaction types. The purpose of this slide is to demonstrate the levels of human and robot collaboration and their features. The main features include working steps, working space, working tasks, physical contact, safety, and robot speed. There are so many reasons you need a Cobots Usecases In Different Sectors Features Of Human Robot Interaction Types Designs PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

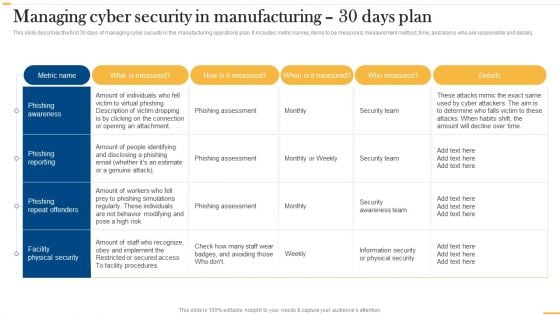
Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF from Slidegeeks today. This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
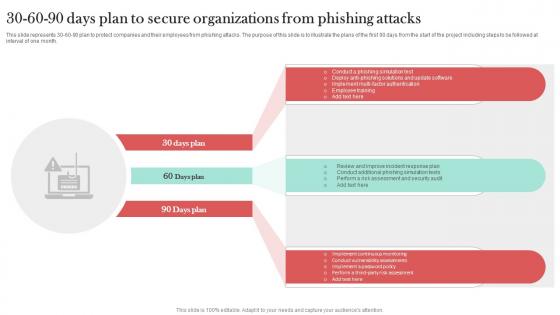
30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT
This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.

Overview Of Platform Tokenization In Data Security PPT Sample
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Find a pre-designed and impeccable Overview Of Platform Tokenization In Data Security PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc.
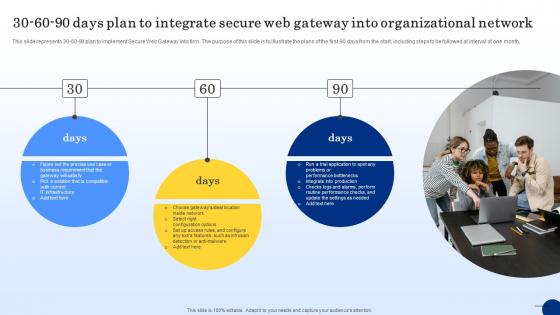
30 60 90 Days Plan To Integrate Secure Web Threat Protection System
This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Integrate Secure Web Threat Protection System. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
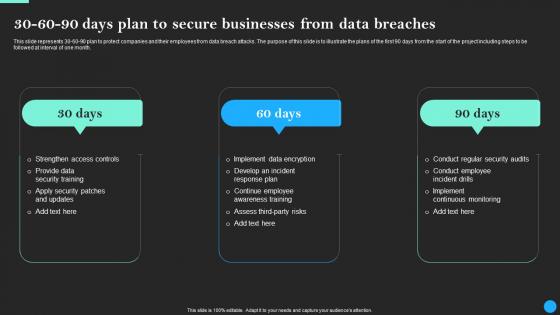
30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
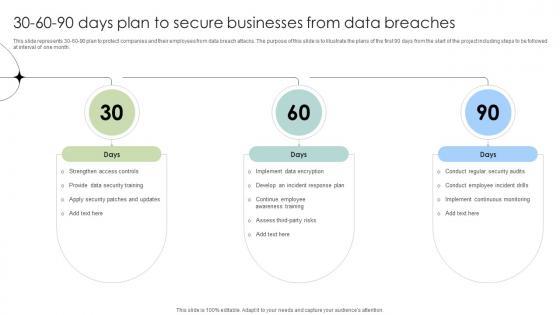
30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
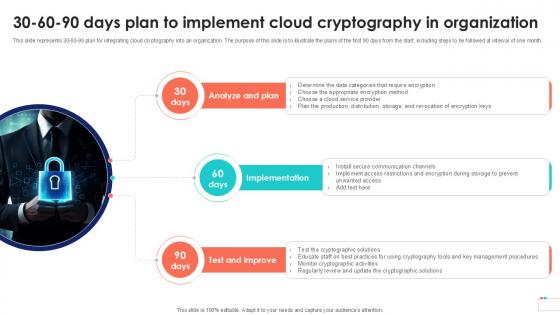
30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample
This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
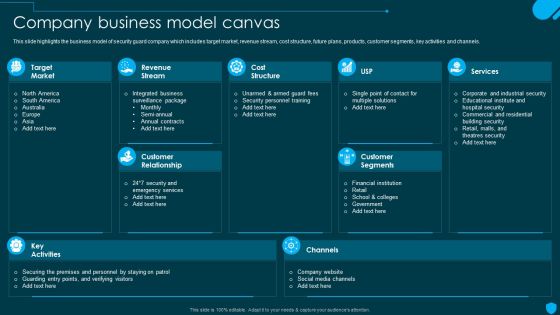
Security And Human Resource Services Business Profile Company Business Model Brochure PDF
This slide highlights the business model of security guard company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. There are so many reasons you need a Security And Human Resource Services Business Profile Company Business Model Brochure PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Web Access Control Solution 30 60 90 Days Plan To Integrate Secure Web Gateway Into Organizational
This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution 30 60 90 Days Plan To Integrate Secure Web Gateway Into Organizational will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Slidegeeks is here to make your presentations a breeze with Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Do Not Waste Saving On Poker PowerPoint Templates Ppt Backgrounds For Slides 0713
Brace yourself, arm your thoughts. Prepare for the hustle with our Do Not Waste Saving On Poker PowerPoint Templates PPT Backgrounds For Slides. Generate ecstasy with our Finance PowerPoint Templates. Your thoughts will delight your audience. Delight them with our Money PowerPoint Templates. Your audience will be ecstatic. Attract first time buyers with our Do Not Waste Saving On Poker PowerPoint Templates Ppt Backgrounds For Slides 0713. They will be your customers for life.

IT Security Ppt PowerPoint Presentation Complete Deck
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty one slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. There are so many reasons you need a IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
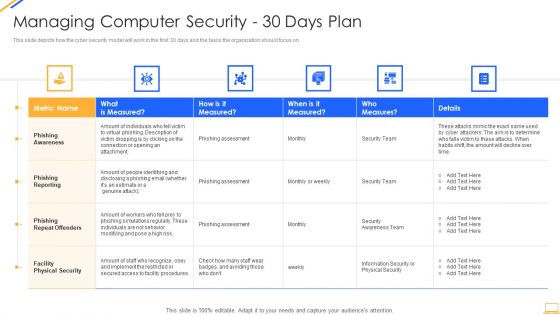
Desktop Security Management Managing Computer Security 30 Days Plan Designs PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 30 days plan designs pdf bundle. Topics like awareness, measured, risk, security, team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
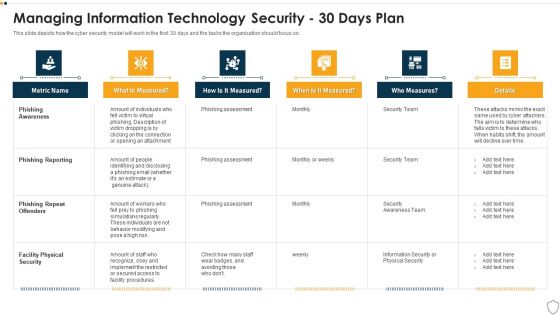
IT Security Managing Information Technology Security 30 Days Plan Themes PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 30 days plan themes pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Info Security Managing Information Security 30 Days Plan Ppt PowerPoint Presentation Icon Show PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative info security managing information security 30 days plan ppt powerpoint presentation icon show pdf bundle. Topics like phishing aware, phishing reporting, phishing repeat offenders, facility physical security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
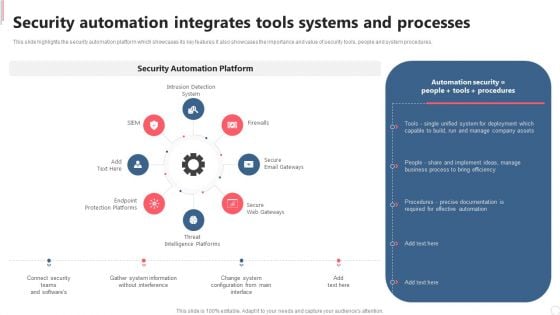
Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. There are so many reasons you need a Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
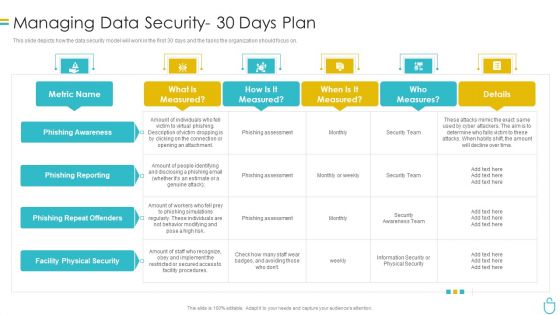
Information Security Managing Data Security 30 Days Plan Ppt Summary Slides PDF
This slide depicts how the data security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative information security managing data security 30 days plan ppt summary slides pdf bundle. Topics like risk, procedures, implement, metric can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
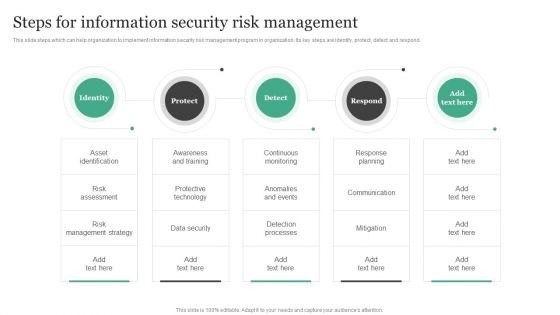
Steps For Information Security Risk Management Information Security Risk Administration Template PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond.There are so many reasons you need a Steps For Information Security Risk Management Information Security Risk Administration Template PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
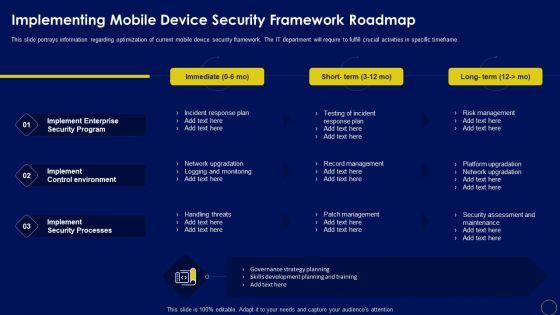
Implementing Mobile Device Security Framework Roadmap Business Mobile Device Security Sample PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. There are so many reasons you need a Implementing Mobile Device Security Framework Roadmap Business Mobile Device Security Sample PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
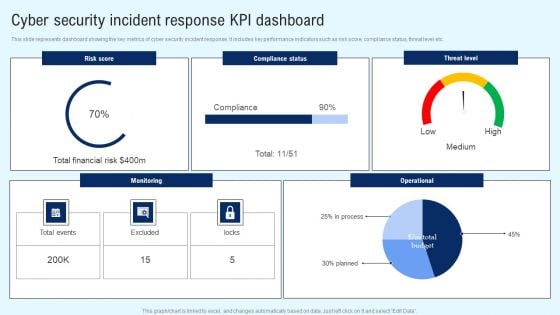
Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
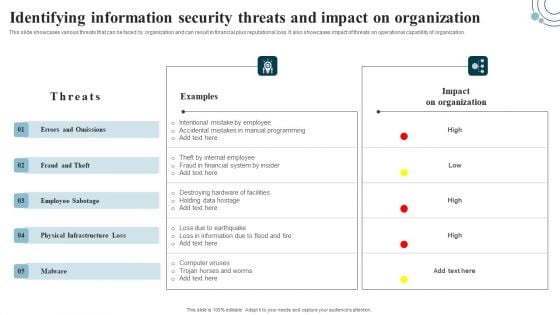
Developing IT Security Strategy Identifying Information Security Threats And Impact On Download PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. There are so many reasons you need a Developing IT Security Strategy Identifying Information Security Threats And Impact On Download PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
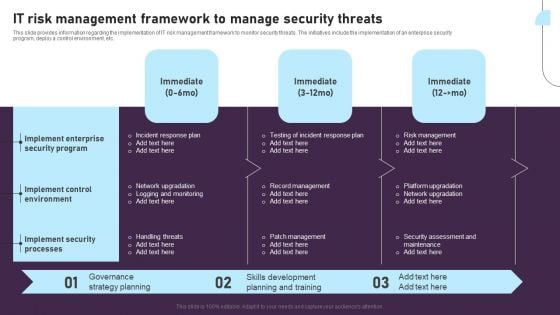
IT Risk Management Framework To Manage Security Threats Background PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. There are so many reasons you need a IT Risk Management Framework To Manage Security Threats Background PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
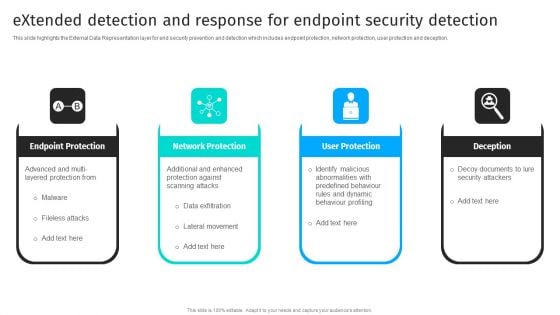
Extended Detection And Response For Endpoint Security Detection Information PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception.There are so many reasons you need a Extended Detection And Response For Endpoint Security Detection Information PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Measuring The Impact Of Security Awareness Training Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. There are so many reasons you need a Measuring The Impact Of Security Awareness Training Icons PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
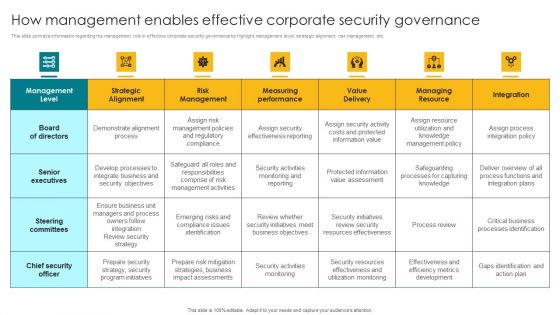
How Management Enables Effective Corporate Security Governance Designs PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. There are so many reasons you need a How Management Enables Effective Corporate Security Governance Designs PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
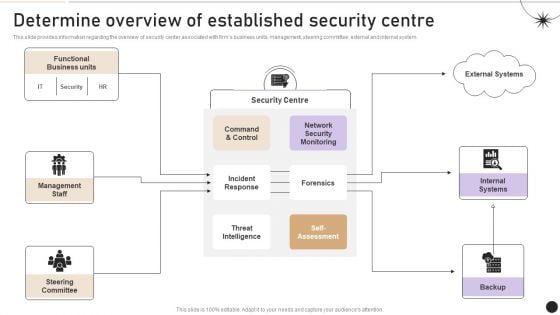
Determine Overview Of Established Security Centre Themes PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. There are so many reasons you need a Determine Overview Of Established Security Centre Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
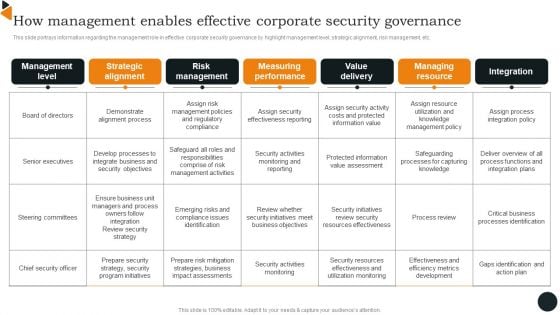
How Management Enables Effective Corporate Security Governance Brochure PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. There are so many reasons you need a How Management Enables Effective Corporate Security Governance Brochure PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
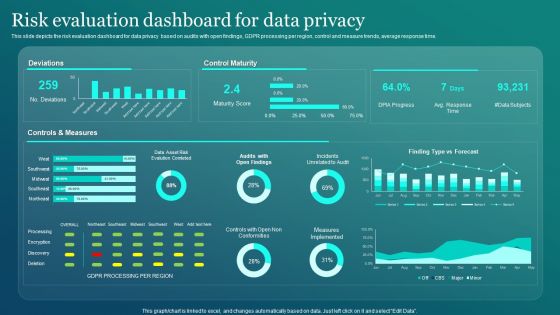
Information Security Risk Evaluation Dashboard For Data Privacy Introduction PDF
This slide depicts the risk evaluation dashboard for data privacy based on audits with open findings, GDPR processing per region, control and measure trends, average response time. There are so many reasons you need a Information Security Risk Evaluation Dashboard For Data Privacy Introduction PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Desktop Security Management Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Info Security Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty one slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Cloud Information Security Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Cloud Data Security Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Security Agency Business Profile Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the forty five slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
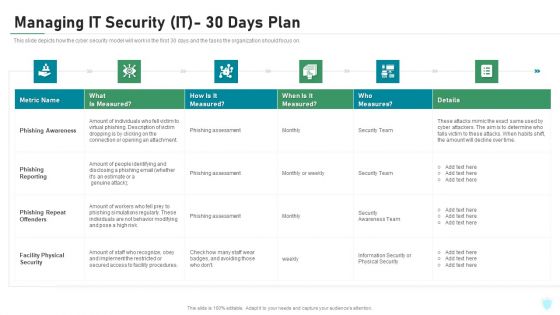
Managing IT Security IT 30 Days Plan Ppt Gallery Graphics Download PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this managing it security it 30 days plan ppt gallery graphics download pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Managing Electronic Information Security 30 Days Plan Ppt Layouts Design Ideas PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this cybersecurity managing electronic information security 30 days plan ppt layouts design ideas pdf. Use them to share invaluable insights on measured, metric, awareness, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
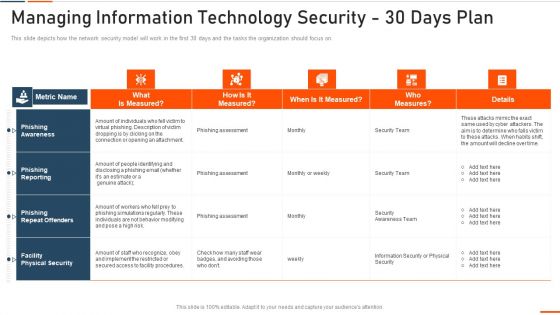
Managing Information Technology Security 30 Days Plan Ppt Professional Examples PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative managing information technology security 30 days plan ppt professional examples pdf bundle. Topics like managing information technology security 30 days plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
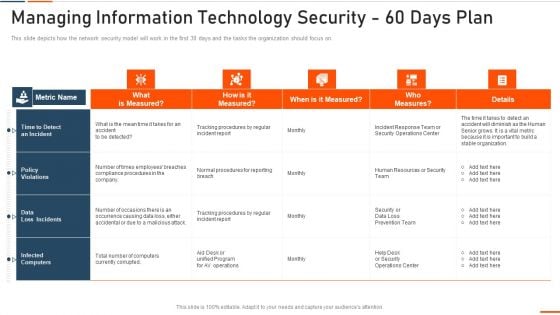
Managing Information Technology Security 60 Days Plan Ppt Ideas Graphics PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this managing information technology security 60 days plan ppt ideas graphics pdf . Use them to share invaluable insights on managing information technology security 60 days plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
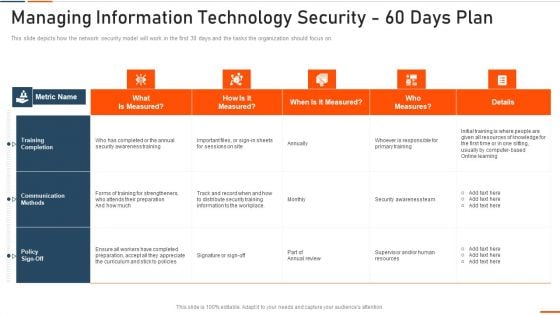
Managing Information Technology Security 60 Days Ppt Infographic Template Samples PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative managing information technology security 60 days ppt infographic template samples pdf bundle. Topics like managing information technology security 60 days plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner. There are so many reasons you need a Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF
The following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy,disaster recovery, password encryption, tasks, reviews etc. There are so many reasons you need a Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
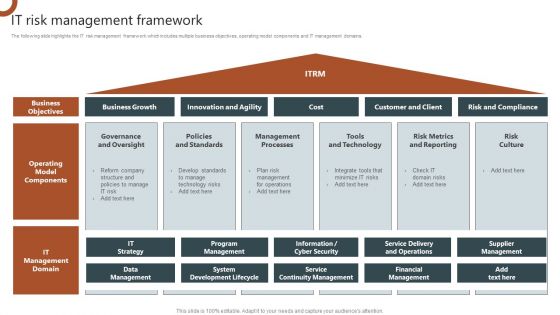
IT Risk Management Framework Organizations Risk Management And IT Security Ideas PDF
The following slide highlights the IT risk management framework which includes multiple business objectives, operating model components and IT management domains. There are so many reasons you need a IT Risk Management Framework Organizations Risk Management And IT Security Ideas PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
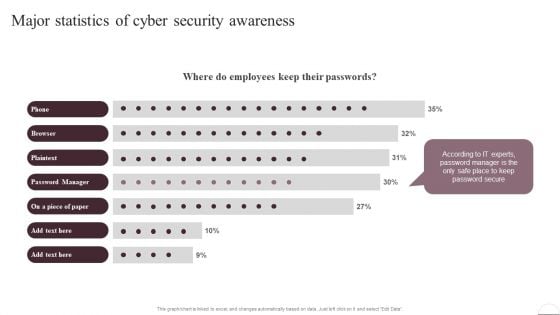
Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. There are so many reasons you need a Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Deploying Cyber Security Incident Response Administration Budget Allocation For Cyber Incident Microsoft PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Budget Allocation For Cyber Incident Microsoft PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
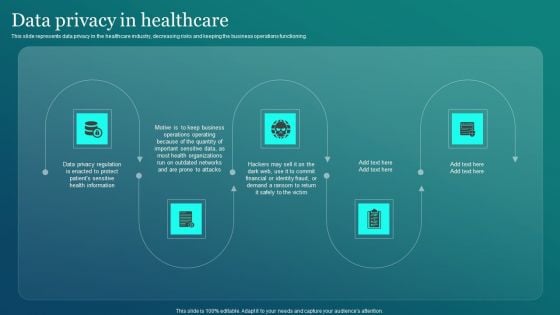
Information Security Data Privacy In Healthcare Ppt PowerPoint Presentation File Layouts PDF
This slide represents data privacy in the healthcare industry, decreasing risks and keeping the business operations functioning. There are so many reasons you need a Information Security Data Privacy In Healthcare Ppt PowerPoint Presentation File Layouts PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
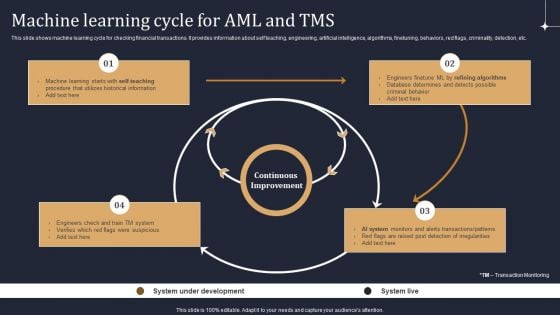
KYC Transaction Monitoring System Business Security Machine Learning Cycle For Aml And Tms Demonstration PDF
This slide shows machine learning cycle for checking financial transactions. It provides information about self teaching, engineering, artificial intelligence, algorithms, finetuning, behaviors, red flags, criminality, detection, etc. There are so many reasons you need a KYC Transaction Monitoring System Business Security Machine Learning Cycle For Aml And Tms Demonstration PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Organizational Assets Security Management Strategy Critical Business Functions Recovery Priorities Template PDF
After the crisis hits, the firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. There are so many reasons you need a Organizational Assets Security Management Strategy Critical Business Functions Recovery Priorities Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
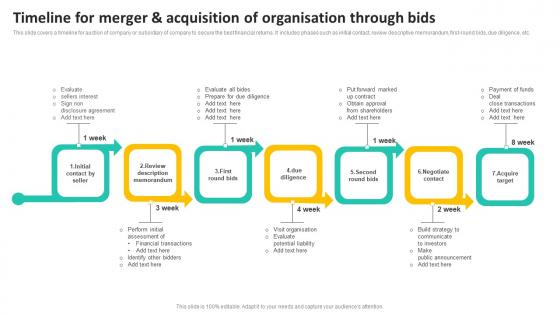
Timeline For Merger And Acquisition Of Organisation Through Bids Introduction Pdf
This slide covers a timeline for auction of company or subsidiary of company to secure the best financial returns. It includes phases such as initial contact, review descriptive memorandum, first round bids, due diligence, etc. Pitch your topic with ease and precision using this Timeline For Merger And Acquisition Of Organisation Through Bids Introduction Pdf. This layout presents information on Payment Of Funds, Financial Transactions, Potential Liability. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide covers a timeline for auction of company or subsidiary of company to secure the best financial returns. It includes phases such as initial contact, review descriptive memorandum, first round bids, due diligence, etc.

Email Security Encryption And Data Loss Prevention Proposal Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought-provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the twenty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Eliminating Information And Technology Security Challenges Experienced By Healthcare Sector Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought-provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fourty six slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Management To Enhance Project Security Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fourty nine slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Developing Firm Security Strategy Plan Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty two slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.


 Continue with Email
Continue with Email

 Home
Home


































