Safety First
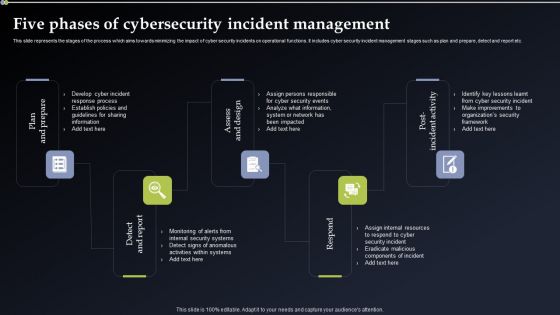
Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. There are so many reasons you need a Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
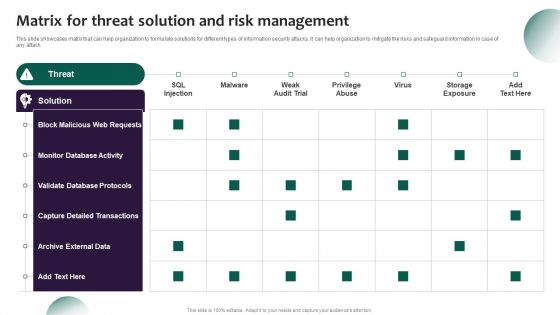
Information Systems Security And Risk Management Plan Matrix For Threat Solution And Risk Management Microsoft PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. There are so many reasons you need a Information Systems Security And Risk Management Plan Matrix For Threat Solution And Risk Management Microsoft PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementing Cybersecurity Awareness Program To Prevent Attacks Comparative Assessment Of Security Graphics PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. There are so many reasons you need a Implementing Cybersecurity Awareness Program To Prevent Attacks Comparative Assessment Of Security Graphics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Want to ace your presentation in front of a live audience Our Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
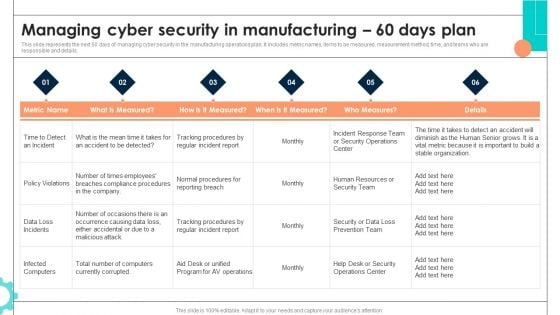
Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
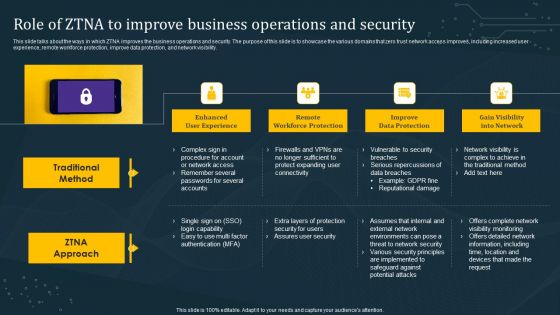
Role Of ZTNA To Improve Business Operations And Security Slides PDF
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. There are so many reasons you need a Role Of ZTNA To Improve Business Operations And Security Slides PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF
This template covers first step for LinkedIn marketing such as update company profile and position the company account according to the target audience. This is a Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Profiles Position, Target Audience, Account According. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
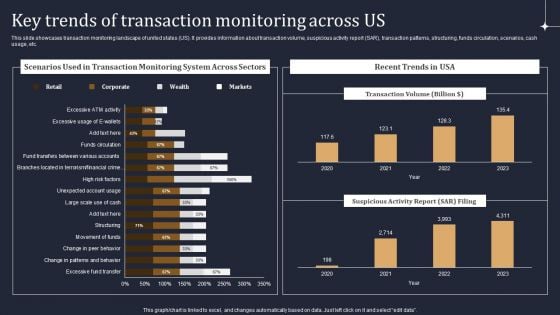
KYC Transaction Monitoring System Business Security Key Trends Of Transaction Monitoring Across Us Diagrams PDF
This slide showcases transaction monitoring landscape of united states US. It provides information about transaction volume, suspicious activity report SAR, transaction patterns, structuring, funds circulation, scenarios, cash usage, etc. There are so many reasons you need a KYC Transaction Monitoring System Business Security Key Trends Of Transaction Monitoring Across Us Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Planning Sales Campaign To Improve Analyzing Multiple Sales Tactics For Securing New Leads Demonstration PDF
This slide provides glimpse about employing different techniques that can help the business in new lead generation. It includes techniques such as social media marketing, cold calling, email marketing, their impact, etc. There are so many reasons you need a Planning Sales Campaign To Improve Analyzing Multiple Sales Tactics For Securing New Leads Demonstration PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
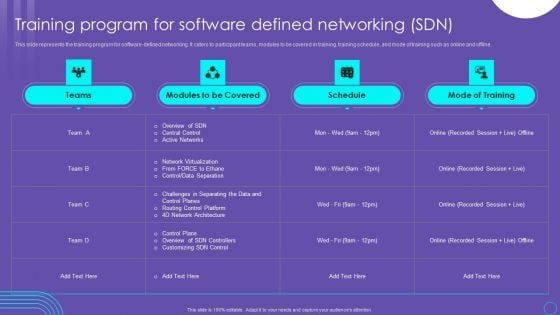
SDN Security Architecture Training Program For Software Defined Networking SDN Mockup PDF
This slide represents the training program for software defined networking. It caters to participant teams, modules to be covered in training, training schedule, and mode of training such as online and offline. There are so many reasons you need a SDN Security Architecture Training Program For Software Defined Networking SDN Mockup PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF
The following slide will assist an IT company to show the investors or audience a complete view of its competitive landscape based on elements like leaders by category, company, their market capitalization and revenue. There are so many reasons you need a Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. There are so many reasons you need a CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
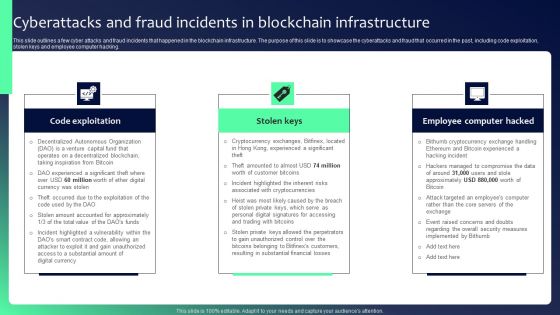
Blockchain Security Solutions Deployment Cyberattacks And Fraud Incidents In Blockchain Clipart PDF
This slide outlines a few cyber attacks and fraud incidents that happened in the blockchain infrastructure. The purpose of this slide is to showcase the cyberattacks and fraud that occurred in the past, including code exploitation, stolen keys and employee computer hacking. There are so many reasons you need a Blockchain Security Solutions Deployment Cyberattacks And Fraud Incidents In Blockchain Clipart PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
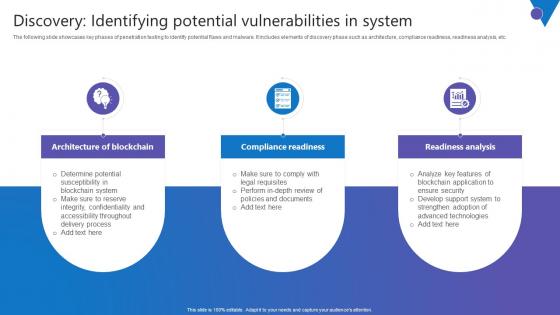
Discovery Identifying Potential Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc. There are so many reasons you need a Discovery Identifying Potential Comprehensive Guide To Blockchain Digital Security Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc.
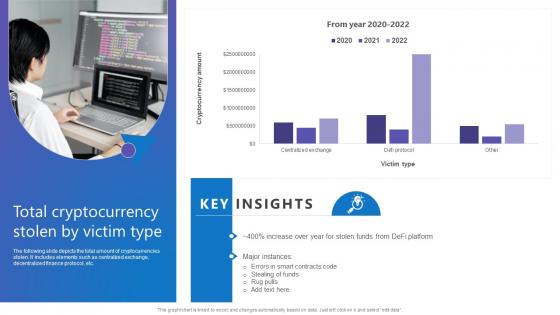
Total Cryptocurrency Stolen Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc. There are so many reasons you need a Total Cryptocurrency Stolen Comprehensive Guide To Blockchain Digital Security Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc.
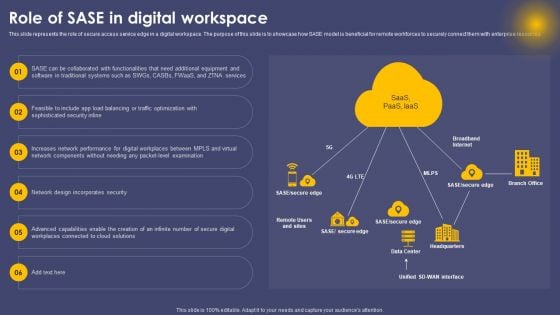
Role Of SASE In Digital Workspace Ppt Professional PDF
This slide represents the role of secure access service edge in a digital workspace. The purpose of this slide is to showcase how SASE model is beneficial for remote workforces to securely connect them with enterprise resources. There are so many reasons you need a Role Of SASE In Digital Workspace Ppt Professional PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
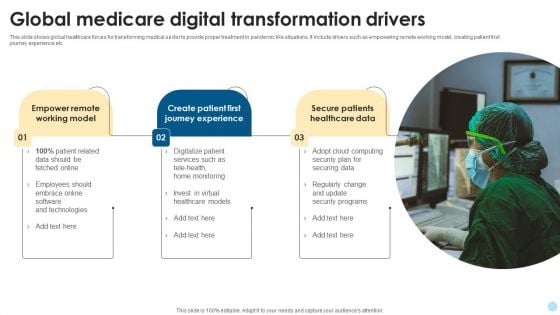
Global Medicare Digital Transformation Drivers Mockup PDF
This slide shows global healthcare forces for transforming medical sector to provide proper treatment in pandemic like situations. It include drivers such as empowering remote working model, creating patient first journey experience etc. Showcasing this set of slides titled Global Medicare Digital Transformation Drivers Mockup PDF. The topics addressed in these templates are Digitalize Patient Services, Security Programs, Securing Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
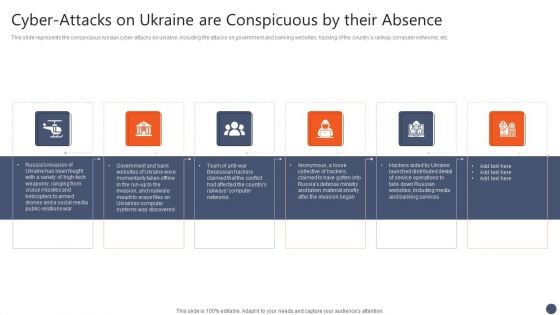
Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF
This slide represents the conspicuous russian cyber attacks on ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
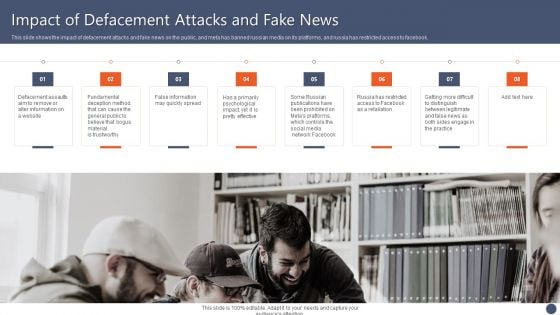
Series Of Cyber Security Attacks Against Ukraine 2022 Impact Of Defacement Attacks And Fake News Topics PDF
This slide shows the impact of defacement attacks and fake news on the public, and meta has banned russian media on its platforms, and russia has restricted access to facebook. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Impact Of Defacement Attacks And Fake News Topics PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Comparative Analysis Of Various Banks To Secure Best Funding Offer Opening Retail Store In Untapped Themes PDF
The following slide showcases the comparison of different banks offering term loans to businesses. The comparison is drawn on the basis of interest rate, processing fees and equated monthly installment EMI. There are so many reasons you need a Comparative Analysis Of Various Banks To Secure Best Funding Offer Opening Retail Store In Untapped Themes PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
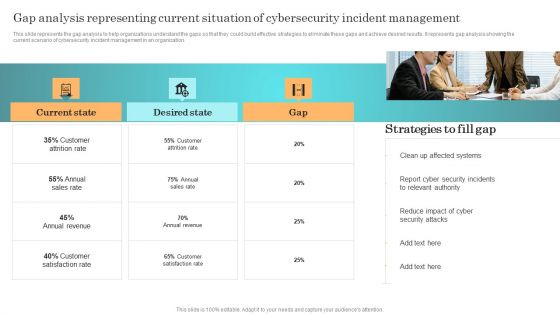
Incident Response Techniques Deployement Gap Analysis Representing Current Situation Of Cybersecurity Designs PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. There are so many reasons you need a Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Key Drivers For SASE Adoption Ppt Styles Visual Aids PDF
This slide outlines the critical drivers for secure access service edge adoption. This slide aims to demonstrate the key drivers that boost SASE adoption among different organizations, including cloud adoption, increased flexibility and agility, cost-effective network traffic management, etc. There are so many reasons you need a Key Drivers For SASE Adoption Ppt Styles Visual Aids PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
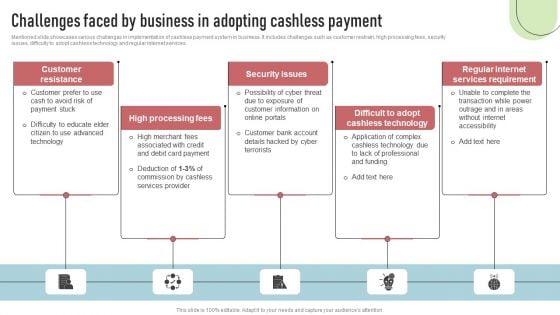
Cashless Payment Strategies To Enhance Business Performance Challenges Faced By Business In Adopting Microsoft PDF

Execute Operational Procedure Plan Steps In Detail Process Mapping Background PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping.Deliver and pitch your topic in the best possible manner with this execute operational procedure plan steps in detail process mapping background pdf. Use them to share invaluable insights on workflow applications, process mapping, process improvement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Process Mapping Pictures PDF
This slide provides information about the first step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e, Process Mapping.Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail process mapping pictures pdf bundle. Topics like process mapping applications, workflow applications, process mapping can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Process Mapping Mockup PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping. Presenting operational process improvement plan steps in detail process mapping mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, graphic software, applications, accountability, productivity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
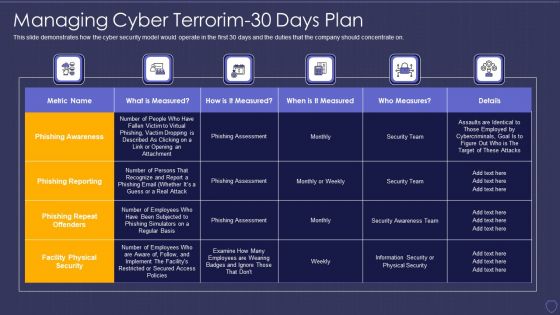
Global Cyber Terrorism Incidents On The Rise IT Managing Cyber Terrorim 30 Days Plan Information PDF
This slide demonstrates how the cyber security model would operate in the first 30 days and the duties that the company should concentrate on. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it managing cyber terrorim 30 days plan information pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Challenges Faced By Companies In Online Marketing Efficient Marketing Tactics Structure Pdf
Following slide outlines major challenges of ecommerce websites and potential solutions to overcome them. It include issues such as cyber security, online data verification, data management and customer experiences. There are so many reasons you need a Challenges Faced By Companies In Online Marketing Efficient Marketing Tactics Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide outlines major challenges of ecommerce websites and potential solutions to overcome them. It include issues such as cyber security, online data verification, data management and customer experiences.
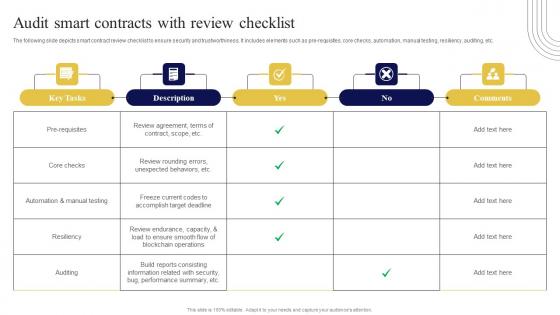
Audit Smart Contracts With Review Exploring Investment Opportunities Infographics Pdf
The following slide depicts smart contract review checklist to ensure security and trustworthiness. It includes elements such as pre-requisites, core checks, automation, manual testing, resiliency, auditing, etc. There are so many reasons you need a Audit Smart Contracts With Review Exploring Investment Opportunities Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide depicts smart contract review checklist to ensure security and trustworthiness. It includes elements such as pre-requisites, core checks, automation, manual testing, resiliency, auditing, etc.

Unlocking Potential IoTs Application Overview And Features Of IoT Connected Cars IoT SS V
This slide showcases a brief introduction to IoT-connected vehicles along with its feature. It incorporates internet connectivity, app-to-car connectivity, vehicle-to-vehicle communication, remote parking, and security. There are so many reasons you need a Unlocking Potential IoTs Application Overview And Features Of IoT Connected Cars IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases a brief introduction to IoT-connected vehicles along with its feature. It incorporates internet connectivity, app-to-car connectivity, vehicle-to-vehicle communication, remote parking, and security.

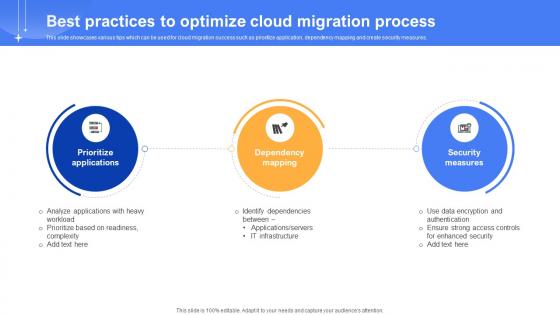
Best Practices To Optimize Cloud Migration Process Data Migration From On Premises
This slide showcases various tips which can be used for cloud migration success such as prioritize application, dependency mapping and create security measures. There are so many reasons you need a Best Practices To Optimize Cloud Migration Process Data Migration From On Premises. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases various tips which can be used for cloud migration success such as prioritize application, dependency mapping and create security measures.
Effective Data Migration Best Practices To Optimize Cloud Migration Process
This slide showcases various tips which can be used for cloud migration success such as prioritize application, dependency mapping and create security measures. There are so many reasons you need a Effective Data Migration Best Practices To Optimize Cloud Migration Process. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases various tips which can be used for cloud migration success such as prioritize application, dependency mapping and create security measures.
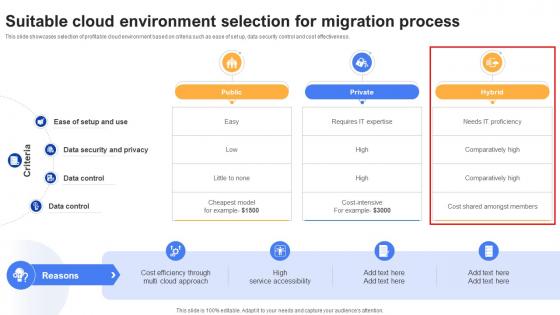
Effective Data Migration Suitable Cloud Environment Selection For Migration
This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness. There are so many reasons you need a Effective Data Migration Suitable Cloud Environment Selection For Migration. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness.

Blue Arrow With Word Wealth PowerPoint Templates And PowerPoint Themes 1012
The above template displays a diagram of word wealth and blue arrow pointing right. Aesthetically designed to make a great first impression this template symbolizes financial advice one would receive from an advisor when saving for a profitable future. This image has been conceived to enable you to emphatically communicate your ideas in your Business and Finance PPT presentations on investment, success and security. Our PPT images are so perfectly designed that it reveals the very basis of our PPT template to make your clients understand. Our Blue Arrow With Word Wealth PowerPoint Templates And PowerPoint Themes 1012 adhere to the ethics. They comply with all the conditions.
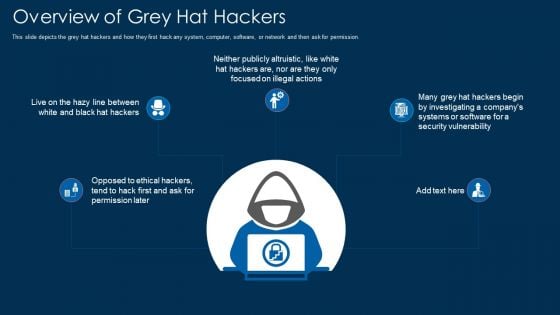
Overview Of Grey Hat Hackers Ppt Infographics Pictures PDF
This slide depicts the grey hat hackers and how they first hack any system, computer, software, or network and then ask for permission. This is a overview of grey hat hackers ppt infographics pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
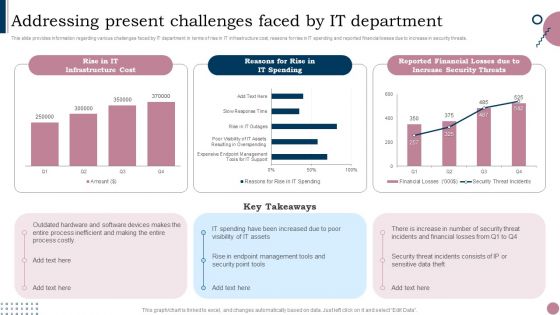
Cios Guide To Optimize Addressing Present Challenges Faced By IT Department Sample PDF
This slide provides information regarding various challenges faced by IT department in terms of rise in IT infrastructure cost, reasons for rise in IT spending and reported financial losses due to increase in security threats. There are so many reasons you need a Cios Guide To Optimize Addressing Present Challenges Faced By IT Department Sample PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
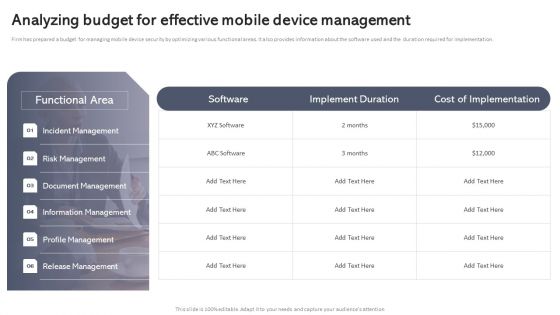
Workplace Portable Device Monitoring And Administration Analyzing Budget For Effective Mobile Device Management Demonstration PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. There are so many reasons you need a Workplace Portable Device Monitoring And Administration Analyzing Budget For Effective Mobile Device Management Demonstration PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
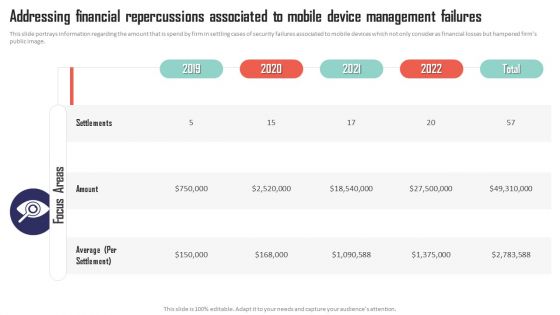
Addressing Financial Repercussions Associated To Mobile Device Management Failures Summary PDF
This slide portrays information regarding the amount that is spend by firm in settling cases of security failures associated to mobile devices which not only consider as financial losses but hampered firms public image. There are so many reasons you need a Addressing Financial Repercussions Associated To Mobile Device Management Failures Summary PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

1G To 5G Cellular Key Features And Disadvantages Of 5Th Generation Technology Guidelines PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. There are so many reasons you need a 1G To 5G Cellular Key Features And Disadvantages Of 5Th Generation Technology Guidelines PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
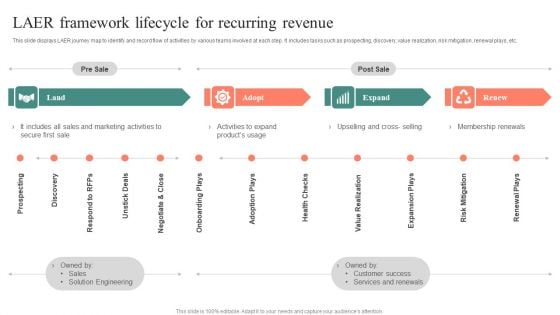
LAER Framework Lifecycle For Recurring Revenue Sample PDF
This slide displays LAER journey map to identify and record flow of activities by various teams involved at each step. It includes tasks such as prospecting, discovery, value realization, risk mitigation, renewal plays, etc. Persuade your audience using this LAER Framework Lifecycle For Recurring Revenue Sample PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Pre Sale, Post Sale, Secure First Sale. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Optimizing Online Stores Challenges Faced By Ecommerce Marketing Manager Demonstration PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. There are so many reasons you need a Optimizing Online Stores Challenges Faced By Ecommerce Marketing Manager Demonstration PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
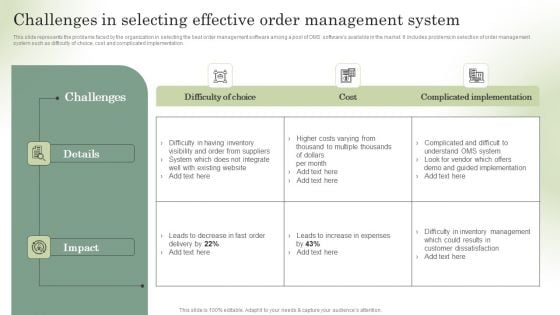
Optimizing Online Stores Challenges In Selecting Effective Order Management Graphics PDF
This slide represents the hurdles and business challenges faced by marketing manager of abc ecommerce firm in the current scenario. it includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. there are so many reasons you need a optimizing online stores challenges faced by ecommerce marketing manager demonstration pdf. the first reason is you cant spend time making everything from scratch, thus, slidegeeks has made presentation templates for you too. you can easily download these templates from our website easily.
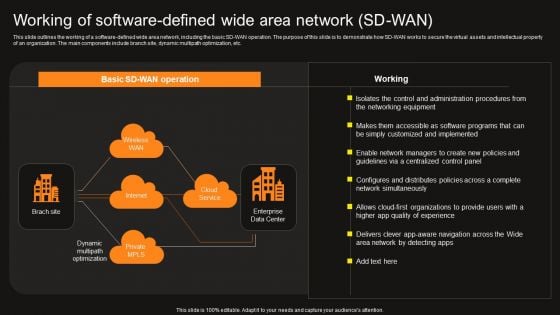
Virtual WAN Architecture Working Of Software Defined Wide Area Network SD WAN Elements PDF
This slide outlines the working of a software-defined wide area network, including the basic sd wan operation. the purpose of this slide is to demonstrate how sd wan works to secure the virtual assets and intellectual property of an organization the main components include branch site, dynamic multipath optimization, etc. There are so many reasons you need a Virtual WAN Architecture Working Of Software Defined Wide Area Network SD WAN Elements PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementing Effective Ecommerce Managemnet Platform Challenges Faced By Ecommerce Marketing Topics PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. There are so many reasons you need a Implementing Effective Ecommerce Managemnet Platform Challenges Faced By Ecommerce Marketing Topics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Technological Change Management Training Plan Introduction Of New Technology Ppt PowerPoint Presentation File Backgrounds PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. There are so many reasons you need a Technological Change Management Training Plan Introduction Of New Technology Ppt PowerPoint Presentation File Backgrounds PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
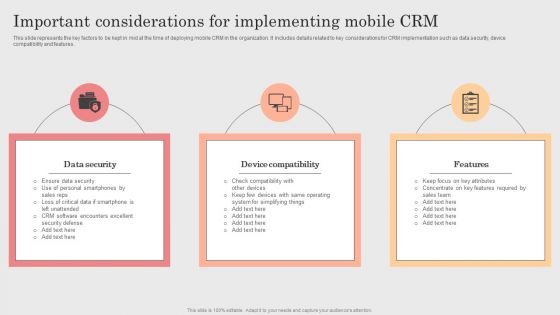
Integrating CRM Solution To Acquire Potential Customers Important Considerations For Implementing Mobile CRM Brochure PDF
This slide represents the key factors to be kept in mid at the time of deploying mobile CRM in the organization. It includes details related to key considerations for CRM implementation such as data security, device compatibility and features. There are so many reasons you need a Integrating CRM Solution To Acquire Potential Customers Important Considerations For Implementing Mobile CRM Brochure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
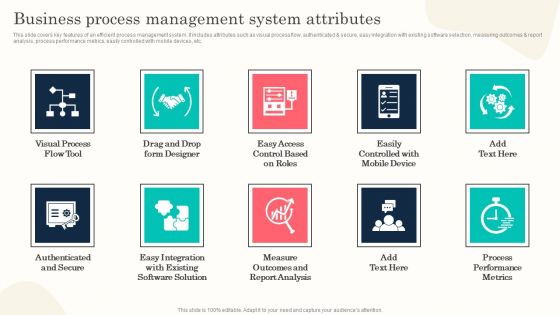
Business Process Management System Attributes Formats PDF
This slide covers key features of an efficient process management system. It includes attributes such as visual process flow, authenticated and secure, easy integration with existing software selection, measuring outcomes and report analysis, process performance metrics, easily controlled with mobile devices, etc. There are so many reasons you need a Business Process Management System Attributes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Effective Business Project Risk Mitigation Plan Project Risk Management Tracking Software Information PDF
This slide provides an overview of project management software used to monitor and track risks. It includes reviews, trials, pricing and features which are automatic risk alerts, a secure database, details reporting and customizable parameters. There are so many reasons you need a Effective Business Project Risk Mitigation Plan Project Risk Management Tracking Software Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
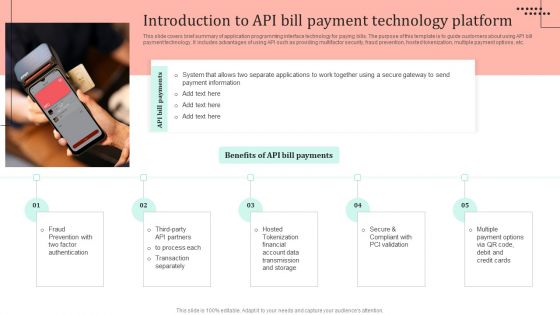
Omnichannel Strategy Implementation For Banking Solutions Introduction To API Bill Payment Technology Microsoft PDF
This slide covers brief summary of application programming interface technology for paying bills. The purpose of this template is to guide customers about using API bill payment technology. It includes advantages of using API such as providing multifactor security, fraud prevention, hosted tokenization, multiple payment options, etc. There are so many reasons you need a Omnichannel Strategy Implementation For Banking Solutions Introduction To API Bill Payment Technology Microsoft PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
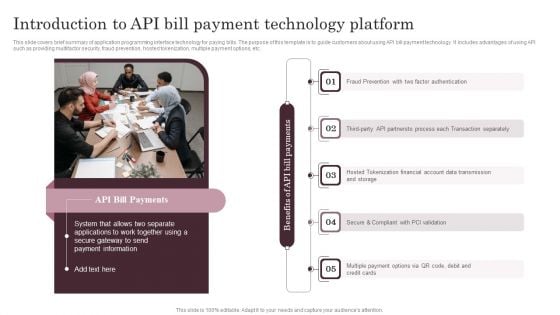
Introduction To API Bill Payment Technology Platform Elements PDF
This slide covers brief summary of application programming interface technology for paying bills. The purpose of this template is to guide customers about using API bill payment technology. It includes advantages of using API such as providing multifactor security, fraud prevention, hosted tokenization, multiple payment options, etc. There are so many reasons you need a Introduction To API Bill Payment Technology Platform Elements PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementation Of Digital Advancement Techniques Essential Personnel Required Pictures PDF
The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists. There are so many reasons you need a Implementation Of Digital Advancement Techniques Essential Personnel Required Pictures PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
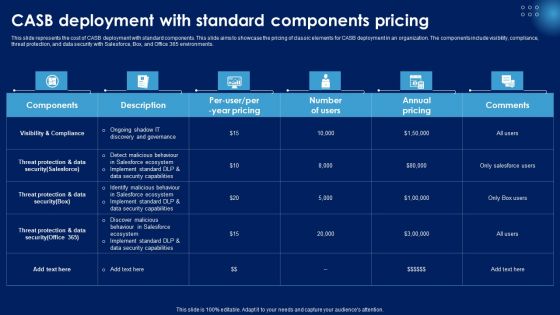
CASB Deployment With Standard Components Pricing Ppt PowerPoint Presentation File Example File PDF
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. There are so many reasons you need a CASB Deployment With Standard Components Pricing Ppt PowerPoint Presentation File Example File PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
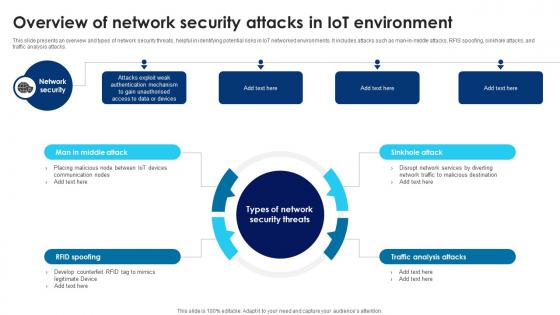
Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks. There are so many reasons you need a Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks.
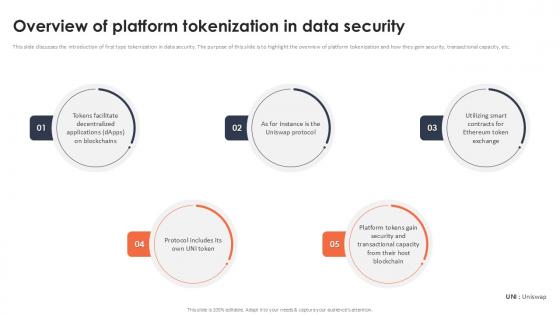
Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc.

Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V
This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery. There are so many reasons you need a Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery.
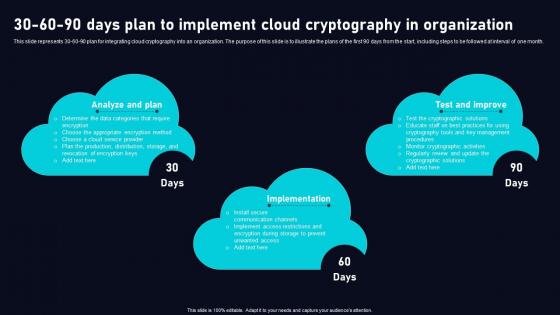
30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf
This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.

On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

Key Resources Security Service Provider Business Model BMC SS V
This slide covers the importance assets to operate business. It includes data centers, intellectual property, financial and human resources. Slidegeeks is here to make your presentations a breeze with Key Resources Security Service Provider Business Model BMC SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the importance assets to operate business. It includes data centers, intellectual property, financial and human resources.

Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. There are so many reasons you need a Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.


 Continue with Email
Continue with Email

 Home
Home


































