Safety First

Key With Puzzle Piece Finance PowerPoint Templates And PowerPoint Themes 1012
Key With Puzzle Piece Finance PowerPoint Templates And PowerPoint Themes 1012-Aesthetically designed to make a great first impression this template highlights the concept of key and lock. It consists of golden keys tied with the puzzle. It indicates fasten, bar, bolt, lock up, padlock, secure, fix in place, lodge, wedge, confine, secure brace, clench, stiffen, tighten, link, clasp, intertwine, join, unite, interlink, clinch and interlock. Explain the process by which you intend to right it. Show them how you can save the day.-Key With Puzzle Piece Finance PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Golden Key With Puzzle Piece On Chain, Business, Symbol, Puzzles Or Jigsaws, Success, Design Experience a defining event with our Key With Puzzle Piece Finance PowerPoint Templates And PowerPoint Themes 1012. Change direction for the better.
Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps Icons PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Mapping. Presenting operational efficiency execution strategy improve quality operational process improvement plan steps icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, applications, graphic software, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
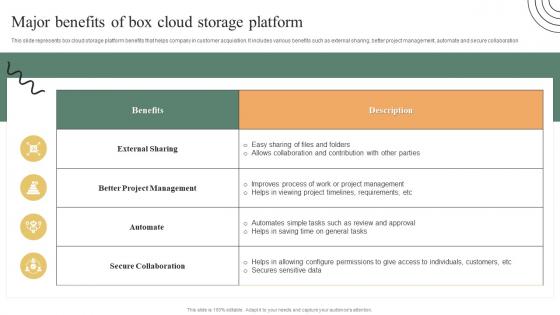
Major Benefits Of Box Cloud Storage Platform Ultimate Guide To Adopt Box Diagrams PDF
This slide represents box cloud storage platform benefits that helps company in customer acquisition. It includes various benefits such as external sharing, better project management, automate and secure collaboration. Slidegeeks is here to make your presentations a breeze with Major Benefits Of Box Cloud Storage Platform Ultimate Guide To Adopt Box Diagrams PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents box cloud storage platform benefits that helps company in customer acquisition. It includes various benefits such as external sharing, better project management, automate and secure collaboration.
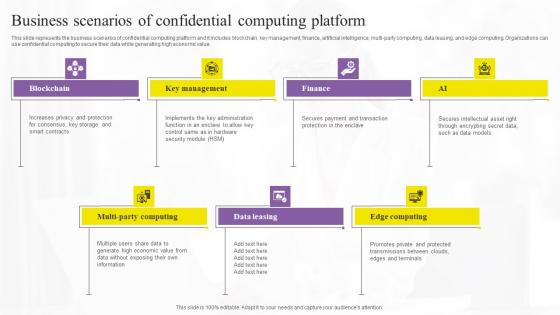
Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
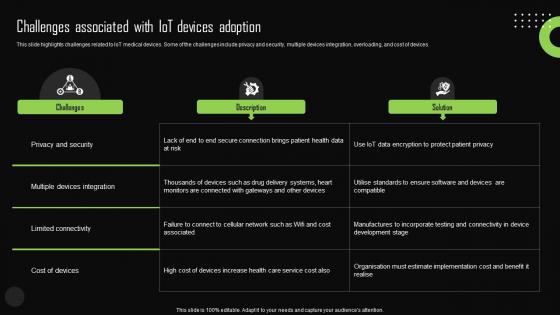
Challenges Associated With Iot Devices Adoption Iot Device Management Slides Pdf
This slide highlights challenges related to IoT medical devices. Some of the challenges include privacy and security, multiple devices integration, overloading, and cost of devices. Slidegeeks is here to make your presentations a breeze with Challenges Associated With Iot Devices Adoption Iot Device Management Slides Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights challenges related to IoT medical devices. Some of the challenges include privacy and security, multiple devices integration, overloading, and cost of devices.

Iot Device Monitoring Applications Best Practices Iot Device Management Infographics Pdf
This slide showcases best practices to monitor IoT device health and improve decision making process. Some of the best practices such as establish system metrics, improve data reporting, set up notifications, and ensure security. Slidegeeks is here to make your presentations a breeze with Iot Device Monitoring Applications Best Practices Iot Device Management Infographics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases best practices to monitor IoT device health and improve decision making process. Some of the best practices such as establish system metrics, improve data reporting, set up notifications, and ensure security.
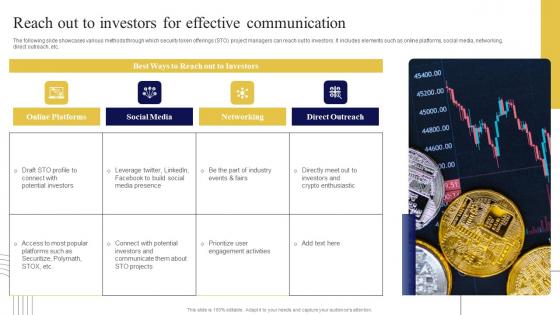
Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf
The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc. Slidegeeks is here to make your presentations a breeze with Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc.
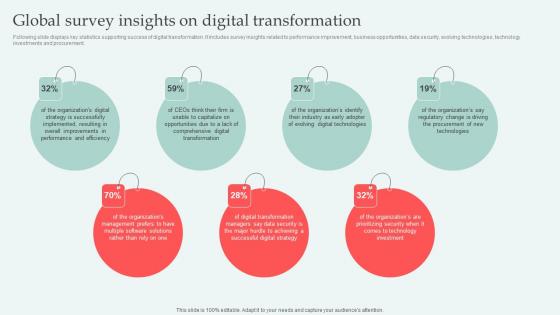
Global Survey Insights Digital Approaches To Increase Business Growth Formats Pdf
Following slide displays key statistics supporting success of digital transformation. It includes survey insights related to performance improvement, business opportunities, data security, evolving technologies, technology investments and procurement. Slidegeeks is here to make your presentations a breeze with Global Survey Insights Digital Approaches To Increase Business Growth Formats Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Following slide displays key statistics supporting success of digital transformation. It includes survey insights related to performance improvement, business opportunities, data security, evolving technologies, technology investments and procurement.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Slidegeeks is here to make your presentations a breeze with Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security

Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V
The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc. There are so many reasons you need a Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc.

Optimization Of IoT Remote Monitoring Types Of Smart Home Automation System Devices IoT SS V
This slide provides an overview of smart home devices. Major devices covered are smart thermostats, locks, doorbells, security, motion smoke detection, water, alarm, lighting, speakers, displays, plugs, vacuum and HVAC systems. Slidegeeks is here to make your presentations a breeze with Optimization Of IoT Remote Monitoring Types Of Smart Home Automation System Devices IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides an overview of smart home devices. Major devices covered are smart thermostats, locks, doorbells, security, motion smoke detection, water, alarm, lighting, speakers, displays, plugs, vacuum and HVAC systems.
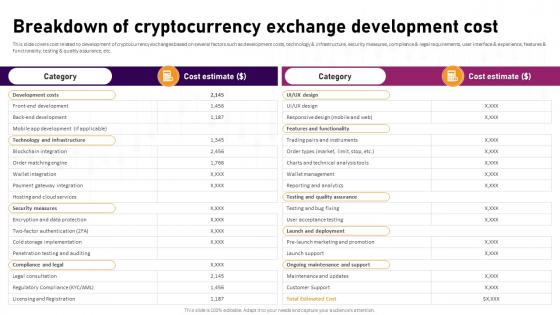
Breakdown Of Cryptocurrency Exchange Complete Roadmap To Blockchain BCT SS V
This slide covers cost related to development of cryptocurrency exchanges based on several factors such as development costs, technology and infrastructure, security measures, compliance and legal requirements, user interface and experience, features and functionality, testing and quality assurance, etc. There are so many reasons you need a Breakdown Of Cryptocurrency Exchange Complete Roadmap To Blockchain BCT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide covers cost related to development of cryptocurrency exchanges based on several factors such as development costs, technology and infrastructure, security measures, compliance and legal requirements, user interface and experience, features and functionality, testing and quality assurance, etc.
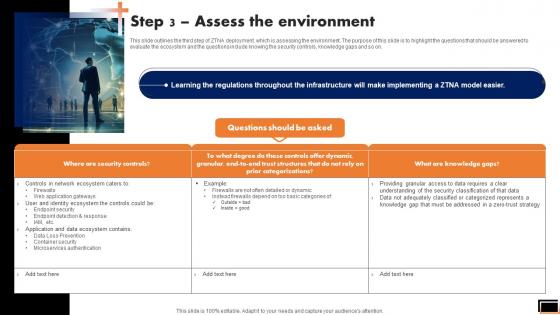
Step 3 Assess The Environment Software Defined Perimeter SDP
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. There are so many reasons you need a Step 3 Assess The Environment Software Defined Perimeter SDP. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

A52 Zero Trust Network Access System Use Cases
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. There are so many reasons you need a A52 Zero Trust Network Access System Use Cases. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.

Major Disadvantages Of Using A Hot Wallet Cryptocurrency Management With Blockchain
This slide highlights the disadvantages of using hot wallets in transactions of cryptocurrency. The purpose of this slide is to outline the negatives such as security risks, malware attaches, limited storage, etc.There are so many reasons you need a Major Disadvantages Of Using A Hot Wallet Cryptocurrency Management With Blockchain. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide highlights the disadvantages of using hot wallets in transactions of cryptocurrency. The purpose of this slide is to outline the negatives such as security risks, malware attaches, limited storage, etc.

How Blockchain Is Reshaping Benefits Of Implementing Blockchain In Healthcare BCT SS V
This slide highlights the positives of integrating blockchain technology within the healthcare industry. It includes improving data security, enhanced interoperability, increased efficiency, improved clinical research and empowered patients. Slidegeeks is here to make your presentations a breeze with How Blockchain Is Reshaping Benefits Of Implementing Blockchain In Healthcare BCT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights the positives of integrating blockchain technology within the healthcare industry. It includes improving data security, enhanced interoperability, increased efficiency, improved clinical research and empowered patients.

The Digital Project Managers Significance Of Digital Tools In Project Management
The purpose of the mentioned slide is to illustrate the importance of incorporating digital solutions in project management. It includes advantages such as efficiency and automation, centralized information, task monitoring, and security and access control. There are so many reasons you need a The Digital Project Managers Significance Of Digital Tools In Project Management. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of the mentioned slide is to illustrate the importance of incorporating digital solutions in project management. It includes advantages such as efficiency and automation, centralized information, task monitoring, and security and access control.

Benefits Of Various Digital Wallet Payment Modes In Depth Guide To Digital Wallets Fin SS V
The following slide exhibits the multiple advantages of e-wallet modes of transaction that benefit individuals and businesses. Key benefits are contactless payments, better customer experience, enhanced security, discounts and offers, etc. There are so many reasons you need a Benefits Of Various Digital Wallet Payment Modes In Depth Guide To Digital Wallets Fin SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide exhibits the multiple advantages of e-wallet modes of transaction that benefit individuals and businesses. Key benefits are contactless payments, better customer experience, enhanced security, discounts and offers, etc.
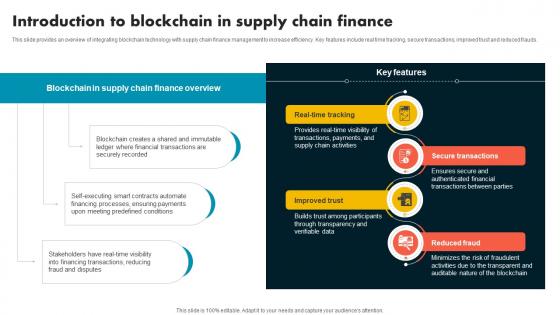
Introduction To Blockchain In Supply Chain Finance Supply Chain Evolution Harnessing The Power BCT SS V
This slide provides an overview of integrating blockchain technology with supply chain finance management to increase efficiency. Key features include real time tracking, secure transactions, improved trust and reduced frauds. Slidegeeks is here to make your presentations a breeze with Introduction To Blockchain In Supply Chain Finance Supply Chain Evolution Harnessing The Power BCT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides an overview of integrating blockchain technology with supply chain finance management to increase efficiency. Key features include real time tracking, secure transactions, improved trust and reduced frauds.
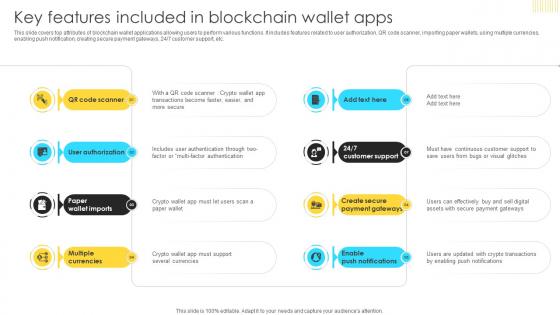
Mastering Blockchain Wallets Key Features Included In Blockchain Wallet Apps BCT SS V
This slide covers top attributes of blockchain wallet applications allowing users to perform various functions. It includes features related to user authorization, QR code scanner, importing paper wallets, using multiple currencies, enabling push notification, creating secure payment gateways, 24 or 7 customer support, etc. There are so many reasons you need a Mastering Blockchain Wallets Key Features Included In Blockchain Wallet Apps BCT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide covers top attributes of blockchain wallet applications allowing users to perform various functions. It includes features related to user authorization, QR code scanner, importing paper wallets, using multiple currencies, enabling push notification, creating secure payment gateways, 24 or 7 customer support, etc.
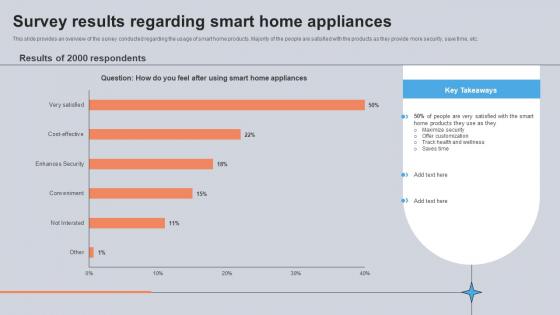
Survey Results Regarding Smart Home Appliances Utilizing Smart Appliances IoT SS V
This slide provides an overview of the survey conducted regarding the usage of smart home products. Majority of the people are satisfied with the products as they provide more security, save time, etc. There are so many reasons you need a Survey Results Regarding Smart Home Appliances Utilizing Smart Appliances IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provides an overview of the survey conducted regarding the usage of smart home products. Majority of the people are satisfied with the products as they provide more security, save time, etc.
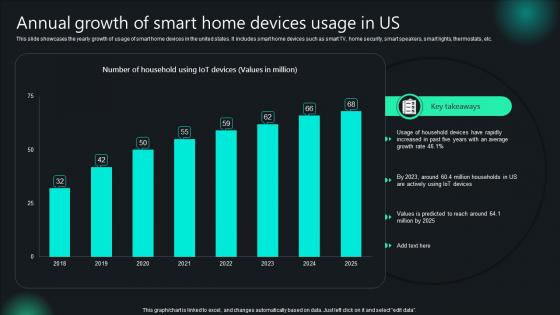
Unlocking Potential IoTs Application Annual Growth Of Smart Home Devices Usage In Us IoT SS V
This slide showcases the yearly growth of usage of smart home devices in the united states. It includes smart home devices such as smart TV, home security, smart speakers, smart lights, thermostats, etc. Slidegeeks is here to make your presentations a breeze with Unlocking Potential IoTs Application Annual Growth Of Smart Home Devices Usage In Us IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases the yearly growth of usage of smart home devices in the united states. It includes smart home devices such as smart TV, home security, smart speakers, smart lights, thermostats, etc.
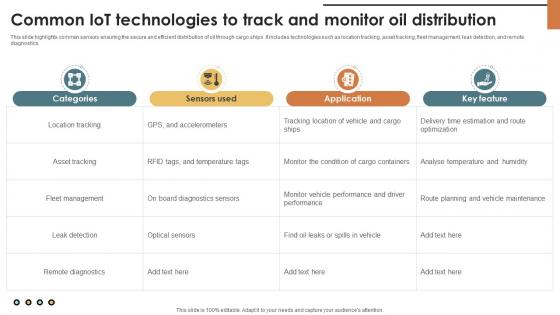
IoT Solutions For Oil And Common IoT Technologies To Track And Monitor IoT SS V
This slide highlights common sensors ensuring the secure and efficient distribution of oil through cargo ships. It includes technologies such as location tracking, asset tracking, fleet management, leak detection, and remote diagnostics. There are so many reasons you need a IoT Solutions For Oil And Common IoT Technologies To Track And Monitor IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide highlights common sensors ensuring the secure and efficient distribution of oil through cargo ships. It includes technologies such as location tracking, asset tracking, fleet management, leak detection, and remote diagnostics.
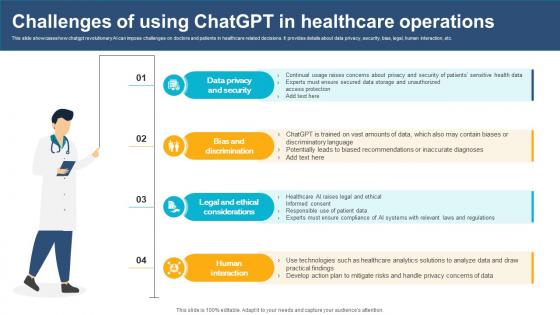
Challenges Of Using ChatGPT In Healthcare Operations ChatGPT And Healthcare Innovation Enhancing AI SS V
This slide showcases how chatgpt revolutionary AI can impose challenges on doctors and patients in healthcare related decisions. It provides details about data privacy, security, bias, legal, human interaction, etc. There are so many reasons you need a Challenges Of Using ChatGPT In Healthcare Operations ChatGPT And Healthcare Innovation Enhancing AI SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases how chatgpt revolutionary AI can impose challenges on doctors and patients in healthcare related decisions. It provides details about data privacy, security, bias, legal, human interaction, etc.
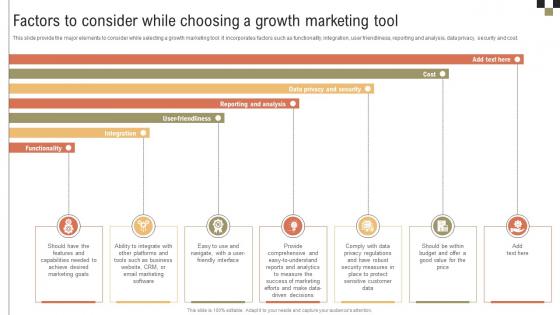
A Comprehensive Guide On Growth Factors To Consider While Choosing A Growth Marketing MKT SS V
This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost. There are so many reasons you need a A Comprehensive Guide On Growth Factors To Consider While Choosing A Growth Marketing MKT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost.

Related And Unrelated Business Steps For Successful Business Diversification Strategy SS V
This slide showcases process that can help organization to formulate business diversification strategy. Its key steps are establish supportive corporate centre, select capable division managers, performance measures, secure competitive advantage, align corporate culture and set incentives. There are so many reasons you need a Related And Unrelated Business Steps For Successful Business Diversification Strategy SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases process that can help organization to formulate business diversification strategy. Its key steps are establish supportive corporate centre, select capable division managers, performance measures, secure competitive advantage, align corporate culture and set incentives.

Bridging Blockchains A Deep Understanding Two Way Peg In Sidechain BCT SS V
This slide provides an overview of two way peg approach in sidechain technology used for blockchain interoperability. Features include asset transfer, secure asset utilization, data and asset movement and connectivity. Slidegeeks is here to make your presentations a breeze with Bridging Blockchains A Deep Understanding Two Way Peg In Sidechain BCT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides an overview of two way peg approach in sidechain technology used for blockchain interoperability. Features include asset transfer, secure asset utilization, data and asset movement and connectivity.

Blockchain Technology Used IoT Fleet Monitoring Ppt Example IoT SS V
This slide provides an overview of the blockchain technology used in logistics for monitoring and communication . It also includes the benefits that it allows device communication, enhances security and provides authorization access. There are so many reasons you need a Blockchain Technology Used IoT Fleet Monitoring Ppt Example IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provides an overview of the blockchain technology used in logistics for monitoring and communication . It also includes the benefits that it allows device communication, enhances security and provides authorization access.
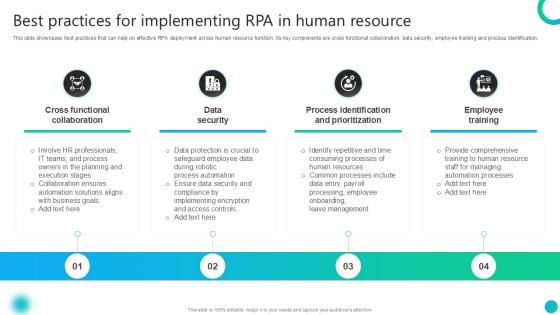
Best Practices For Implementing RPA In Human Resource PPT PowerPoint AI SS V
This slide showcases best practices that can help on effective RPA deployment across human resource function. Its key components are cross functional collaboration, data security, employee training and process identification. Slidegeeks is here to make your presentations a breeze with Best Practices For Implementing RPA In Human Resource PPT PowerPoint AI SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases best practices that can help on effective RPA deployment across human resource function. Its key components are cross functional collaboration, data security, employee training and process identification.
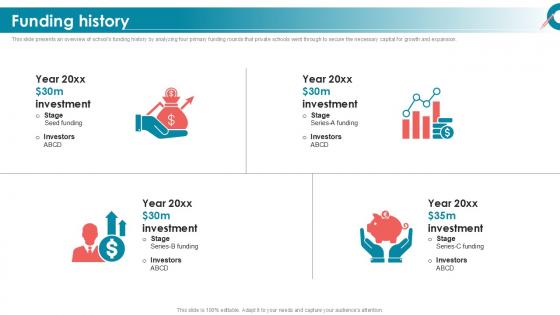
Funding History Private School Investor Funding Elevator Pitch Deck PPT Slides
This slide presents an overview of schools funding history by analyzing four primary funding rounds that private schools went through to secure the necessary capital for growth and expansion. Slidegeeks is here to make your presentations a breeze with Funding History Private School Investor Funding Elevator Pitch Deck PPT Slides With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide presents an overview of schools funding history by analyzing four primary funding rounds that private schools went through to secure the necessary capital for growth and expansion.

Challenges And Solutions In Web Application Development PPT Template SS
This slide presents solutions to challenges faced during web application development helpful in streamlining process, increasing accuracy and making customer experience better. It includes user interface and user experience, scalability, performance and security that are highly important aspects to focus upon. There are so many reasons you need a Challenges And Solutions In Web Application Development PPT Template SS. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide presents solutions to challenges faced during web application development helpful in streamlining process, increasing accuracy and making customer experience better. It includes user interface and user experience, scalability, performance and security that are highly important aspects to focus upon
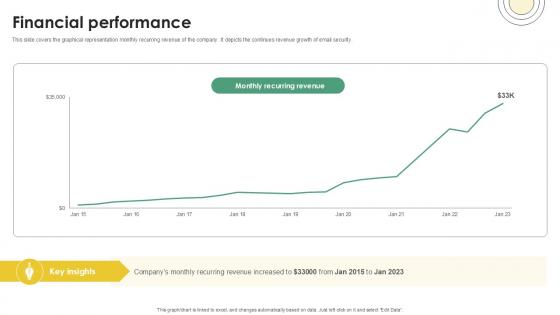
Financial Performance Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers the graphical representation monthly recurring revenue of the company. It depicts the continues revenue growth of email security. Slidegeeks is here to make your presentations a breeze with Financial Performance Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the graphical representation monthly recurring revenue of the company. It depicts the continues revenue growth of email security.
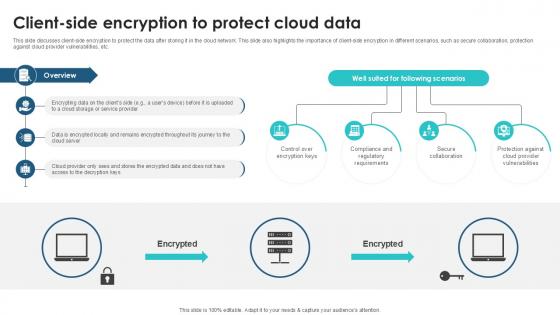
Client Side Encryption To Protect Client Side Encryption PPT Example
This slide discusses client-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client-side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc. There are so many reasons you need a Client Side Encryption To Protect Client Side Encryption PPT Example. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide discusses client-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client-side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc.
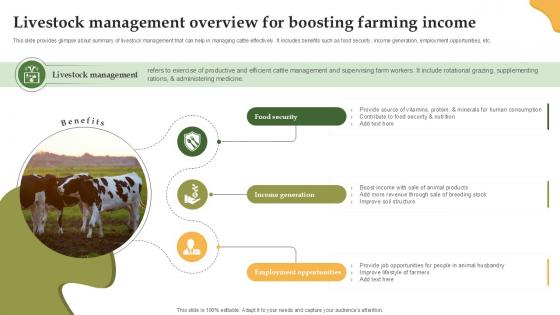
Livestock Management Overview Enhancing Productivity With Adoption PPT Slide
This slide provides glimpse about summary of livestock management that can help in managing cattle effectively. It includes benefits such as food security, income generation, employment opportunities, etc. Slidegeeks is here to make your presentations a breeze with Livestock Management Overview Enhancing Productivity With Adoption PPT Slide With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides glimpse about summary of livestock management that can help in managing cattle effectively. It includes benefits such as food security, income generation, employment opportunities, etc.

Best Practices To Create Winning Digital Account Opening Experience Mockup PDF
This slide covers top techniques to enhance customer experience in opening digital bank account. The purpose of this template is to provide an overview of action steps that should be taken to improve user experience. It includes techniques such as streamlining KYC checks, adopting a mobile first account opening, emphazing regulatory and security, etc along with action steps and impact of these techniques. Find a pre designed and impeccable Best Practices To Create Winning Digital Account Opening Experience Mockup PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
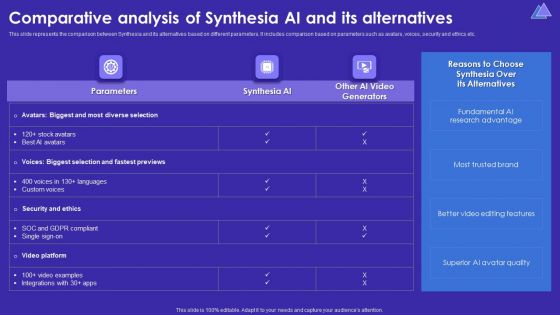
Comparative Analysis Of Synthesia AI And Its Alternatives Summary PDF
This slide represents the comparison between Synthesia and its alternatives based on different parameters. It includes comparison based on parameters such as avatars, voices, security and ethics etc. Slidegeeks is here to make your presentations a breeze with Comparative Analysis Of Synthesia AI And Its Alternatives Summary PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Strategic Ecommerce Plan For B2B Enterprises Key Challenges Faced By Businesses During B2b Payments Topics PDF

Best Practices To Create Winning Digital Account Opening Experience Infographics PDF
This slide covers top techniques to enhance customer experience in opening digital bank account. The purpose of this template is to provide an overview of action steps that should be taken to improve user experience. It includes techniques such as streamlining KYC checks, adopting a mobile first account opening, emphazing regulatory and security, etc along with action steps and impact of these techniques. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices To Create Winning Digital Account Opening Experience Infographics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
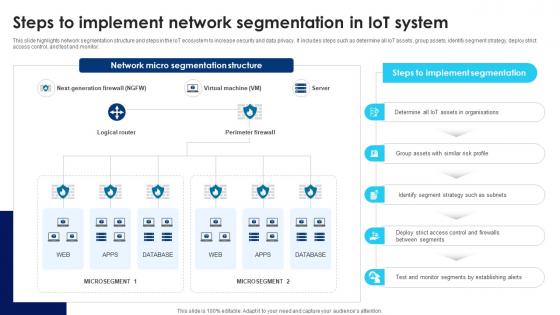
Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V
This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor.
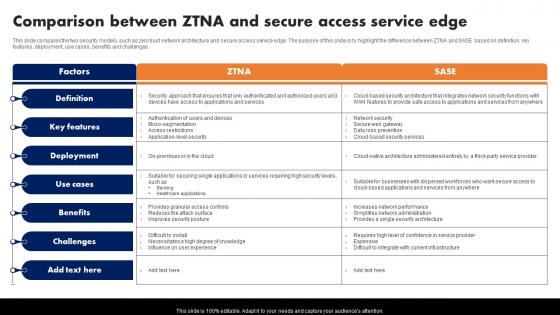
Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
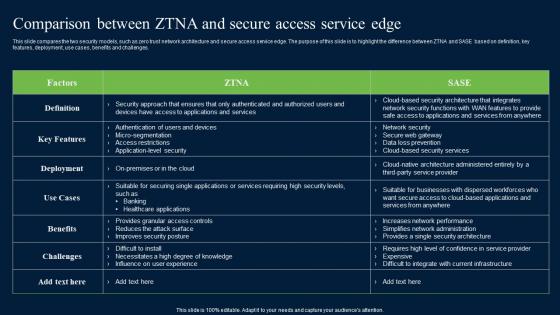
Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Current Trends Enhancing Performance Of Secure Web Gateway Web Threat Protection System
This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc. Slidegeeks is here to make your presentations a breeze with Current Trends Enhancing Performance Of Secure Web Gateway Web Threat Protection System With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.
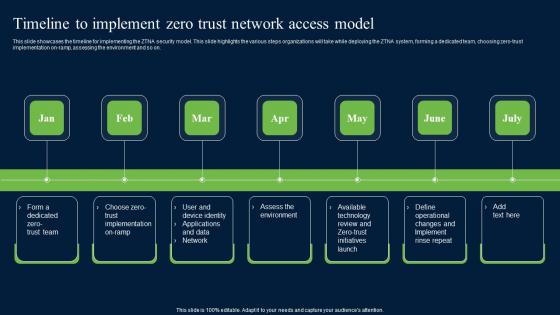
Timeline To Implement Zero Trust Network Security Themes Pdf
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Zero Trust Network Security Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
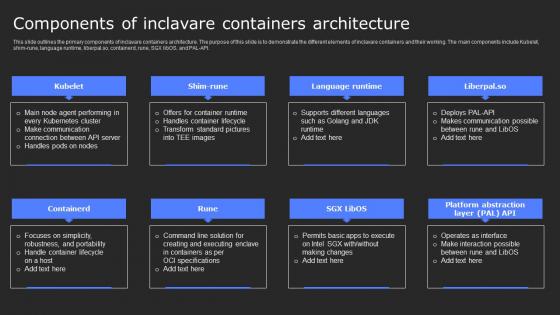
Components Of Inclavare Containers Secure Computing Framework Professional Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Slidegeeks is here to make your presentations a breeze with Components Of Inclavare Containers Secure Computing Framework Professional Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
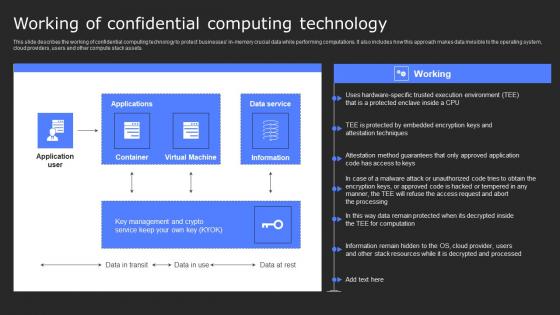
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
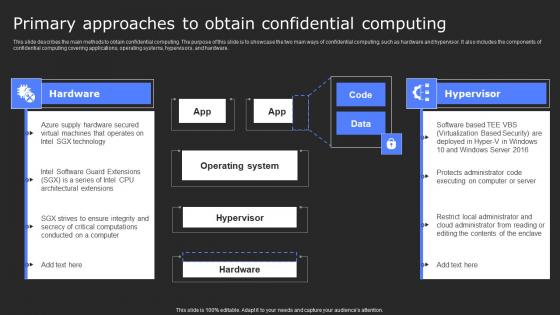
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
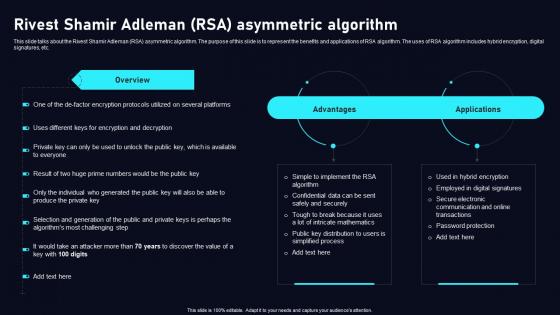
Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Slidegeeks is here to make your presentations a breeze with Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.
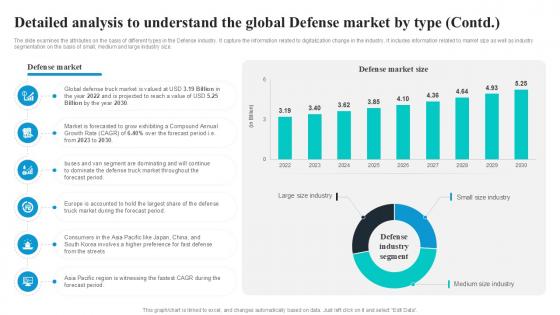
Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size. Slidegeeks is here to make your presentations a breeze with Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size.

House And Alarm Clock Security PowerPoint Templates Ppt Background For Slides 1112
We present our House And Alarm clock Security PowerPoint Templates PPT Background For Slides 1112.Use our Real estate PowerPoint Templates because,Stable ideas are the building blocks of a sucessful structure. Use our Business PowerPoint Templates because,This template can project the path to sucess that you have charted. Use our Money PowerPoint Templates because,You can Enlighten them with your brilliant understanding of mental health. Use our Finance PowerPoint Templates because, You can Refine them all as you take them through the numerous filtering stages of the funnel of your quality control process. Use our Clocks PowerPoint Templates because, This is Aesthetically designed to make a great first impression this template highlights .Use these PowerPoint slides for presentations relating to House and alarm clock, real estate, business, money, finance, clocks. The prominent colors used in the PowerPoint template are Green, White, Blue Get your fill of applause with our House And Alarm Clock Security PowerPoint Templates Ppt Background For Slides 1112. The claps will just continue to come.
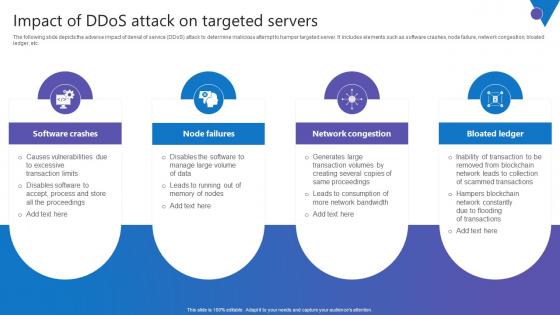
Impact Of DDoS Attack Comprehensive Guide To Blockchain Digital Security Sample Pdf
The following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc. Slidegeeks is here to make your presentations a breeze with Impact Of DDoS Attack Comprehensive Guide To Blockchain Digital Security Sample Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc.

Steps To Select Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Slidegeeks is here to make your presentations a breeze with Steps To Select Next Generation Secure Web Gateway Web Threat Protection System With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc.

Web Access Control Solution Architecture Of Citrix Secure Web Gateway Proxy Solution
This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Slidegeeks is here to make your presentations a breeze with Web Access Control Solution Architecture Of Citrix Secure Web Gateway Proxy Solution With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc.

Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. Slidegeeks is here to make your presentations a breeze with Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc.

CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
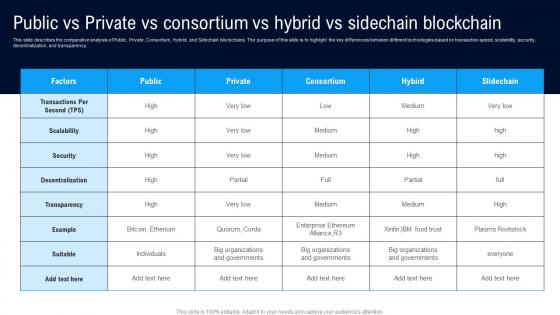
Public Vs Private Vs Consortium Vs Hybrid Different Architectures Of Blockchain Template Pdf
This slide describes the comparative analysis of Public, Private, Consortium, Hybrid, and Sidechain blockchains. The purpose of this slide is to highlight the key differences between different technologies based on transaction speed, scalability, security, decentralization, and transparency. Slidegeeks is here to make your presentations a breeze with Public Vs Private Vs Consortium Vs Hybrid Different Architectures Of Blockchain Template Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the comparative analysis of Public, Private, Consortium, Hybrid, and Sidechain blockchains. The purpose of this slide is to highlight the key differences between different technologies based on transaction speed, scalability, security, decentralization, and transparency.
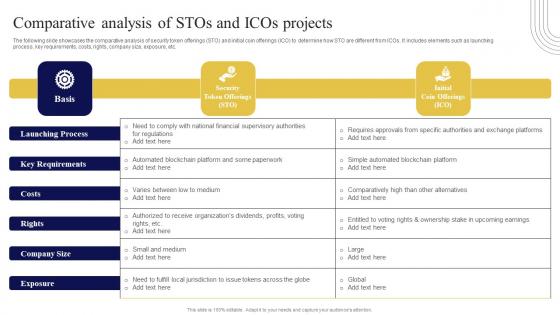
Comparative Analysis Of Stos And Icos Exploring Investment Opportunities Download Pdf
The following slide showcases the comparative analysis of security token offerings STO and initial coin offerings ICO to determine how STO are different from ICOs. It includes elements such as launching process, key requirements, costs, rights, company size, exposure, etc. Slidegeeks is here to make your presentations a breeze with Comparative Analysis Of Stos And Icos Exploring Investment Opportunities Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide showcases the comparative analysis of security token offerings STO and initial coin offerings ICO to determine how STO are different from ICOs. It includes elements such as launching process, key requirements, costs, rights, company size, exposure, etc.

Zero Trust Model Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Steps To Implement Zero Trust Network Access Model With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.


 Continue with Email
Continue with Email

 Home
Home


































