Safety Icons
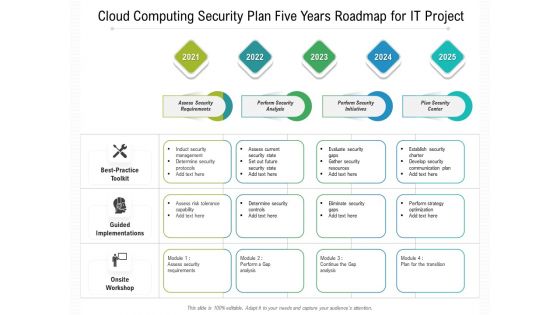
Cloud Computing Security Plan Five Years Roadmap For IT Project Slides
Presenting the cloud computing security plan five years roadmap for it project slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
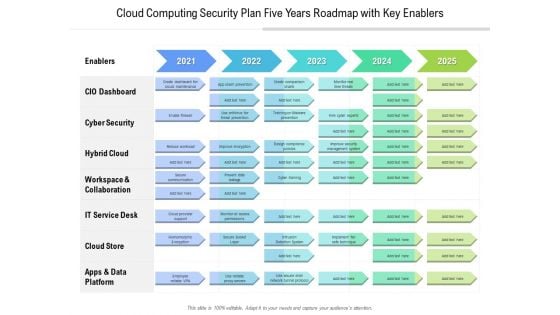
Cloud Computing Security Plan Five Years Roadmap With Key Enablers Designs
Presenting our jaw dropping cloud computing security plan five years roadmap with key enablers designs. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
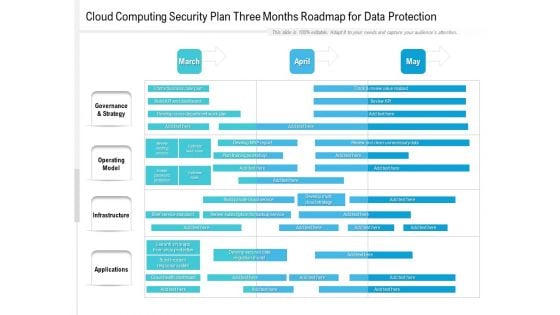
Cloud Computing Security Plan Three Months Roadmap For Data Protection Structure
Presenting the cloud computing security plan three months roadmap for data protection structure. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
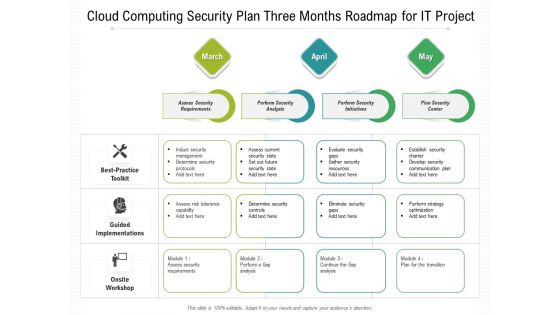
Cloud Computing Security Plan Three Months Roadmap For IT Project Pictures
Presenting our jaw dropping cloud computing security plan three months roadmap for it project pictures. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
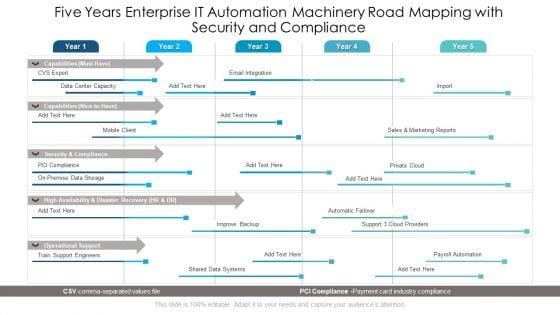
Five Years Enterprise IT Automation Machinery Road Mapping With Security And Compliance Ideas
Presenting the five years enterprise it automation machinery road mapping with security and compliance ideas. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
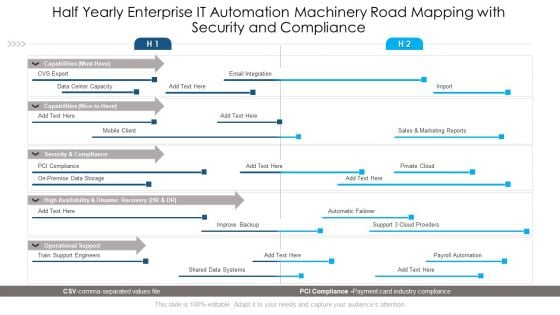
Half Yearly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Inspiration
Introducing our half yearly enterprise it automation machinery road mapping with security and compliance inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
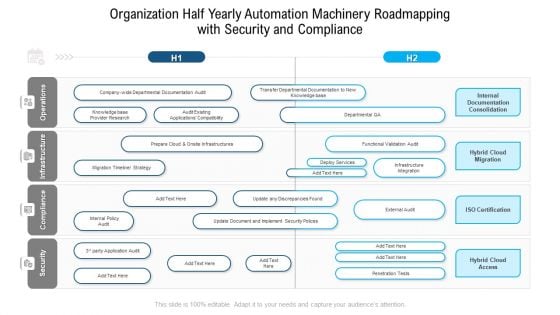
Organization Half Yearly Automation Machinery Roadmapping With Security And Compliance Background
Presenting our jaw dropping organization half yearly automation machinery roadmapping with security and compliance background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
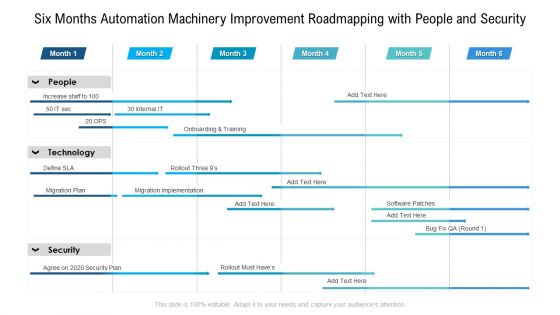
Six Months Automation Machinery Improvement Roadmapping With People And Security Brochure
Presenting the six months automation machinery improvement roadmapping with people and security brochure. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Three Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Sample
Presenting our jaw dropping three months enterprise it automation machinery road mapping with security and compliance sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
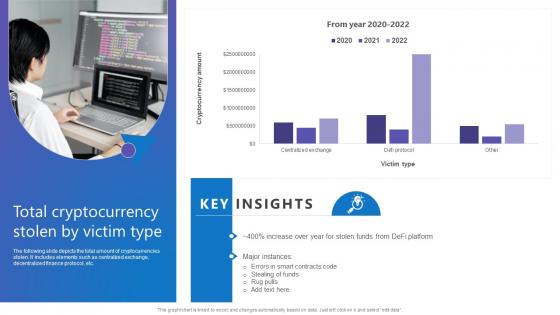
Total Cryptocurrency Stolen Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc. There are so many reasons you need a Total Cryptocurrency Stolen Comprehensive Guide To Blockchain Digital Security Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc.
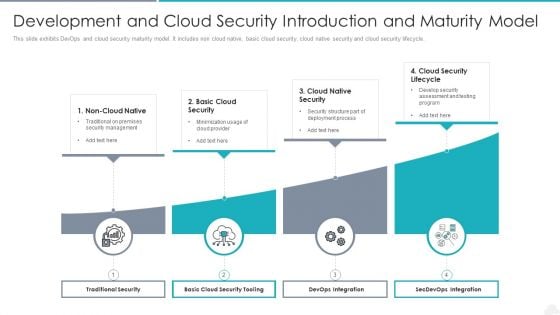
Development And Cloud Security Introduction And Maturity Model Graphics PDF
Presenting development and cloud security introduction and maturity model graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including traditional security, devops integration, secdevops integration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
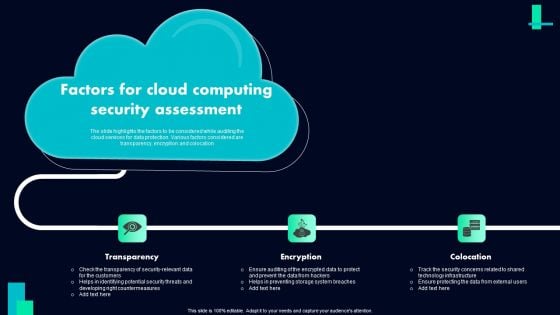
Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF
Presenting Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Factors For, Cloud Computing, Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
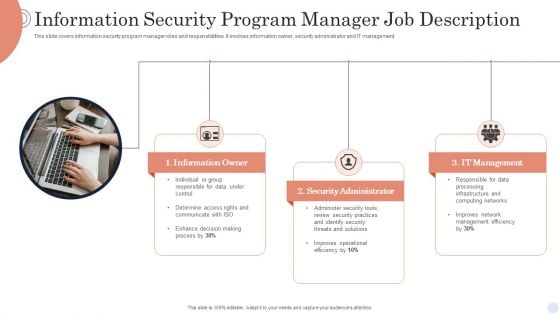
Information Security Program Manager Job Description Background PDF
This slide covers information security program manager roles and responsibilities. It involves information owner, security administrator and IT management. Presenting Information Security Program Manager Job Description Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Owner, Security Administrator, It Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
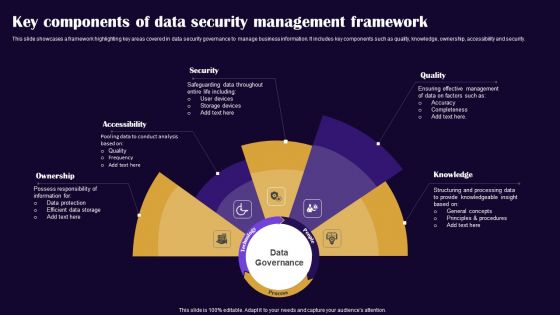
Key Components Of Data Security Management Framework Pictures PDF
This slide showcases a framework highlighting key areas covered in data security governance to manage business information. It includes key components such as quality, knowledge, ownership, accessibility and security. Presenting Key Components Of Data Security Management Framework Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Ownership, Accessibility, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Levels Of Security Concerns In Cloud Network Download PDF
The slide showcases levels of security concerns that measure user and device authentication. The elements are virtual machine security , network security , interface security , privacy concerns etc. Presenting Levels Of Security Concerns In Cloud Network Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Virtual Machine Security, Interface Security, Network Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
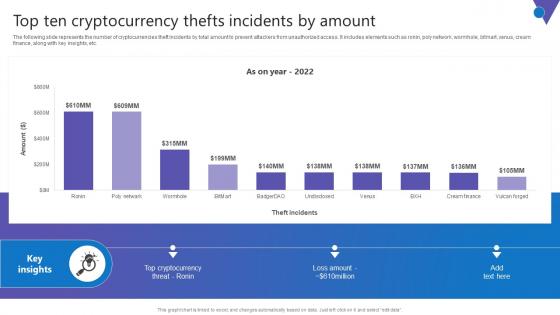
Top Ten Cryptocurrency Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as ronin, poly network, wormhole, bitmart, venus, cream finance, along with key insights, etc. Want to ace your presentation in front of a live audience Our Top Ten Cryptocurrency Comprehensive Guide To Blockchain Digital Security Clipart Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as ronin, poly network, wormhole, bitmart, venus, cream finance, along with key insights, etc.
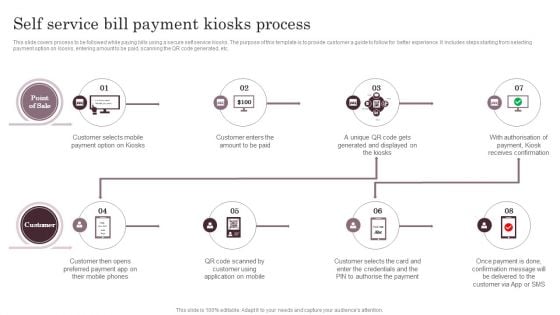
Omnichannel Services Solution In Financial Sector Self Service Bill Payment Kiosks Process Download PDF
This slide covers process to be followed while paying bills using a secure self service kiosks. The purpose of this template is to provide customer a guide to follow for better experience. It includes steps starting from selecting payment option on kiosks, entering amount to be paid, scanning the QR code generated, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Omnichannel Services Solution In Financial Sector Self Service Bill Payment Kiosks Process Download PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Omnichannel Services Solution In Financial Sector Self Service Bill Payment Kiosks Process Download PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
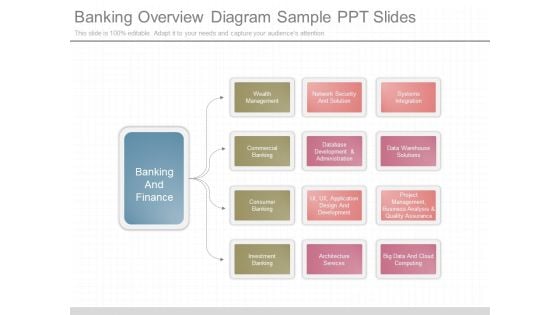
Banking Overview Diagram Sample Ppt Slides
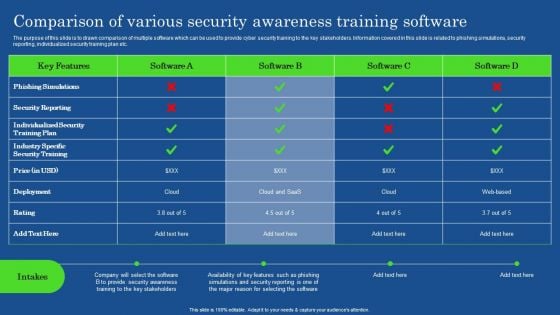
Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
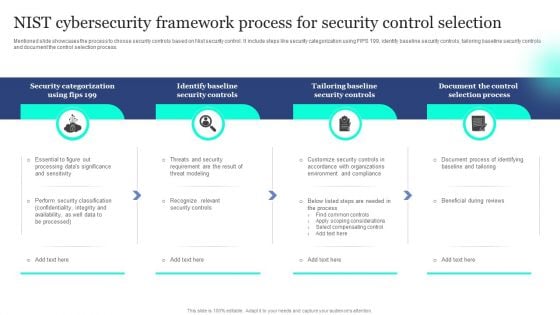
NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
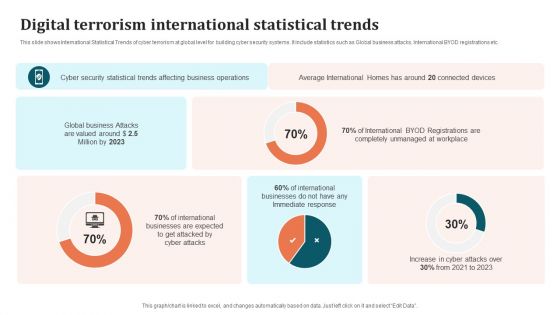
Digital Terrorism International Statistical Trends Brochure PDF
This slide shows International Statistical Trends of cyber terrorism at global level for building cyber security systems. It include statistics such as Global business attacks, International BYOD registrations etc. Showcasing this set of slides titled Digital Terrorism International Statistical Trends Brochure PDF. The topics addressed in these templates are International Businesses, Cyber Security Statistical Trends, Business Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
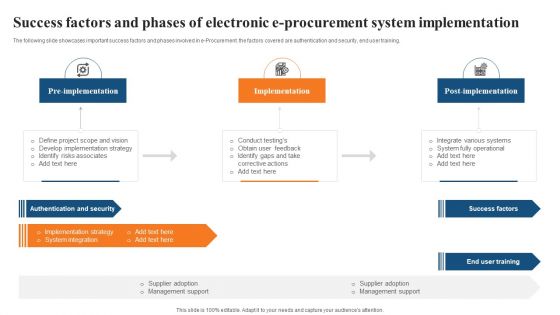
Success Factors And Phases Of Electronic E Procurement System Implementation Formats PDF

Cloud Based Email Security Market Report Industry Trends Ppt Styles Diagrams PDF
Major trends of the E mail security industry are shown in this slide. This is a cloud based email security market report industry trends ppt styles diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security system, artificial intelligence, supply chain security, security adaptive approach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
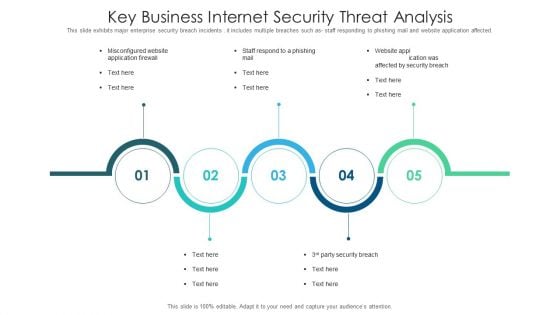
Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
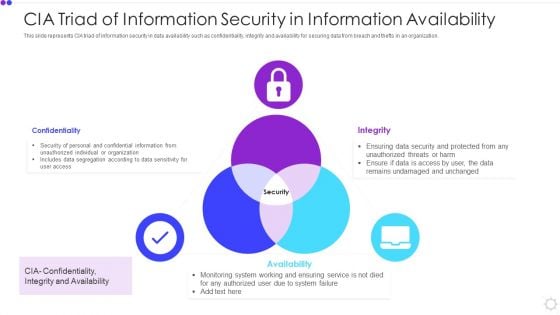
Cia Triad Of Information Security In Information Availability Microsoft PDF
This slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting cia triad of information security in information availability microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including confidentiality, integrity, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
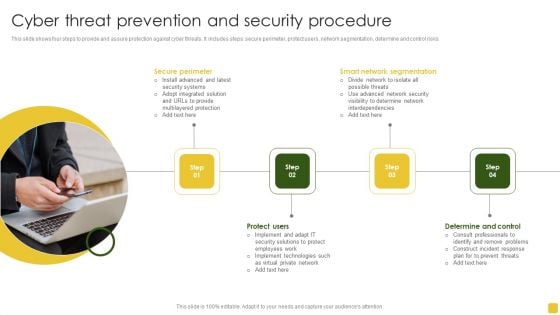
Cyber Threat Prevention And Security Procedure Elements PDF
This slide shows four steps to provide and assure protection against cyber threats. It includes steps secure perimeter, protect users, network segmentation, determine and control risks. Presenting Cyber Threat Prevention And Security Procedure Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Control, Smart Network Segmentation, Secure Perimeter. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
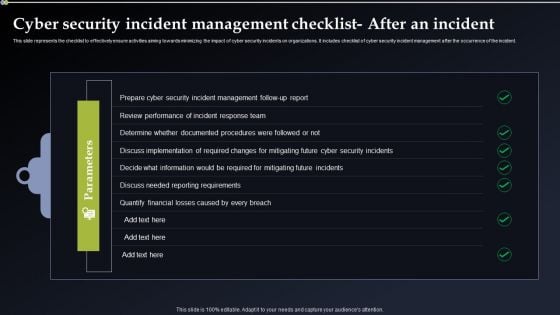
Cyber Security Incident Management Checklist After An Incident Designs PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. If you are looking for a format to display your unique thoughts, then the professionally designed Cyber Security Incident Management Checklist After An Incident Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cyber Security Incident Management Checklist After An Incident Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
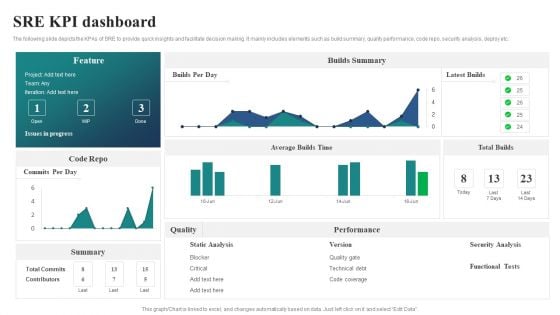
SRE KPI Dashboard Ppt PowerPoint Presentation File Slide Portrait PDF
The following slide depicts the KPAs of SRE to provide quick insights and facilitate decision making. It mainly includes elements such as build summary, quality performance, code repo, security analysis, deploy etc. Showcasing this set of slides titled SRE KPI Dashboard Ppt PowerPoint Presentation File Slide Portrait PDF. The topics addressed in these templates are Builds Summary, Latest Builds, Total Builds. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
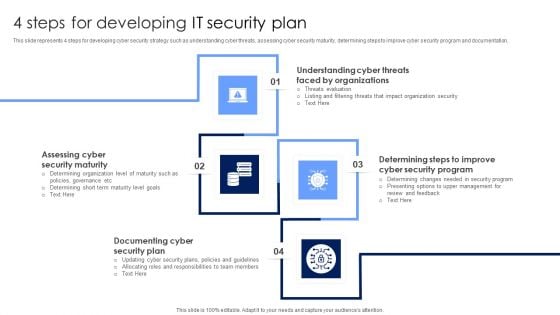
4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
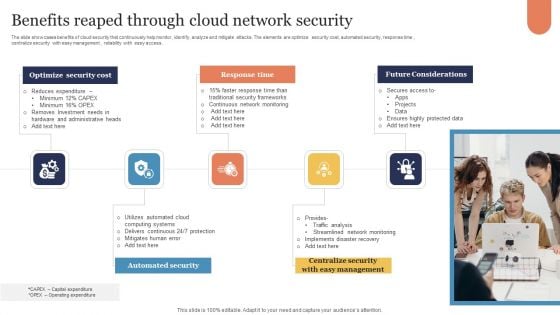
Benefits Reaped Through Cloud Network Security Sample PDF
The slide showcases benefits of cloud security that continuously help monitor, identify, analyze and mitigate attacks. The elements are optimize security cost, automated security, response time , centralize security with easy management , reliability with easy access . Presenting Benefits Reaped Through Cloud Network Security Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Optimize Security Cost, Response Time, Future Considerations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
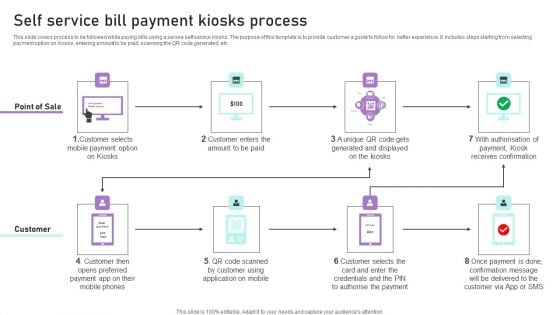
Self Service Bill Payment Kiosks Process Ppt Slides Format PDF
This slide covers process to be followed while paying bills using a secure self service kiosks. The purpose of this template is to provide customer a guide to follow for better experience. It includes steps starting from selecting payment option on kiosks, entering amount to be paid, scanning the QR code generated, etc. Are you searching for a Self Service Bill Payment Kiosks Process Ppt Slides Format PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Self Service Bill Payment Kiosks Process Ppt Slides Format PDF from Slidegeeks today.

Redis Cache Data Structure IT Secure Server Configuration With Server Configuration Lock Diagrams PDF
This slide describes the secure server configuration with server configuration lock, which guarantees only users have access. Presenting redis cache data structure it secure server configuration with server configuration lock diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like securing, programmer, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
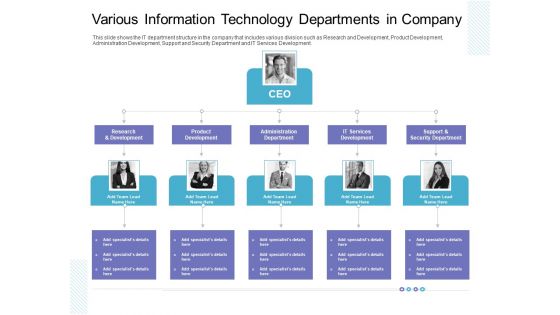
Various Information Technology Departments In Company Slides PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development. This is a various information technology departments in company slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like product development, administration department, research and development, support and security department. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
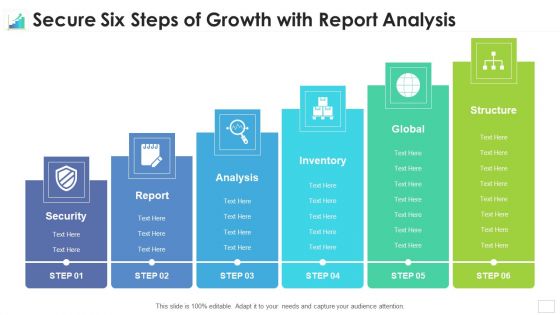
Secure Six Steps Of Growth With Report Analysis Template PDF
Presenting secure six steps of growth with report analysis template pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including inventory, analysis, global. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
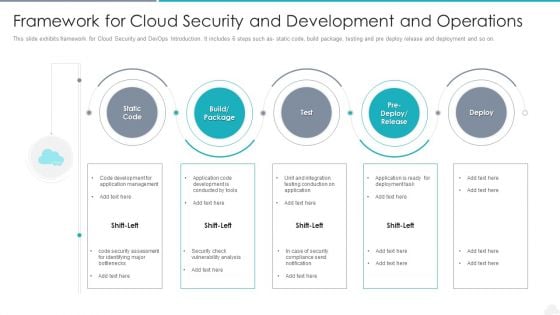
Framework For Cloud Security And Development And Operations Elements PDF
Presenting framework for cloud security and development and operations elements pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including management, application, development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Functional Technology Security Challenges And Solutions To Overcome Topics PDF
Presenting functional technology security challenges and solutions to overcome topics pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including challenges, solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
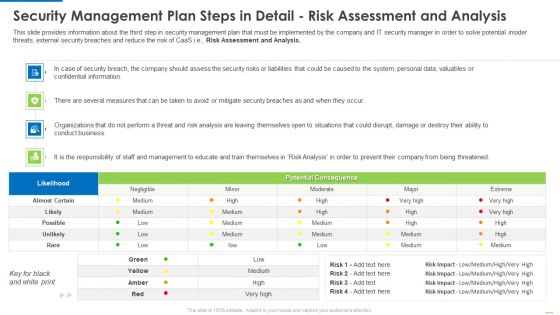
Security Management Plan Steps In Detail Risk Assessment And Analysis Diagrams PDF
Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis diagrams pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Risk Management Process For Organization Template PDF
This slide displays flow diagram to illustrate cybersecurity risk management process to ensure continuous monitoring. It includes components such as threats, vulnerabilities, impacts, intelligence, etc. Showcasing this set of slides titled IT Security Risk Management Process For Organization Template PDF. The topics addressed in these templates are Organization, Cyber Intelligence, Continuous Monitoring, Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
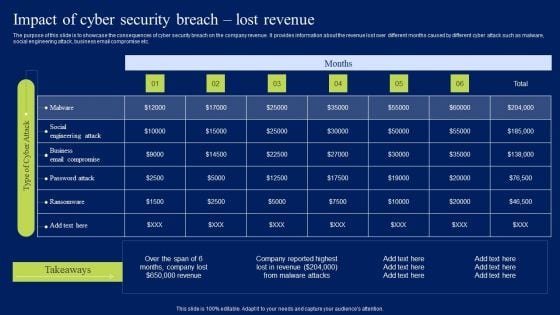
Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. If you are looking for a format to display your unique thoughts, then the professionally designed Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
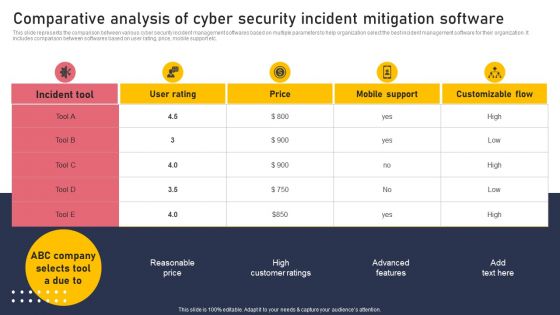
Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
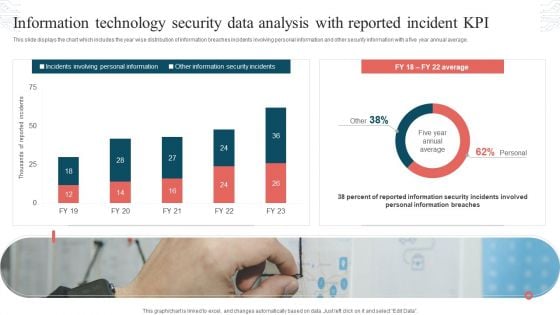
Information Technology Security Data Analysis With Reported Incident KPI Download PDF
This slide displays the chart which includes the year wise distribution of information breaches incidents involving personal information and other security information with a five year annual average. Showcasing this set of slides titled Information Technology Security Data Analysis With Reported Incident KPI Download PDF. The topics addressed in these templates are Incidents Involving, Personal Information, Other Information, Security Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
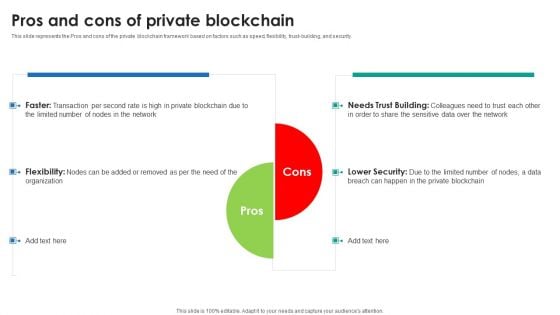
P2P Ledger Pros And Cons Of Private Blockchain Diagrams PDF
This slide represents the Pros and cons of the private blockchain framework based on factors such as speed, flexibility, trust-building, and security.Find a pre-designed and impeccable P2P Ledger Pros And Cons Of Private Blockchain Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
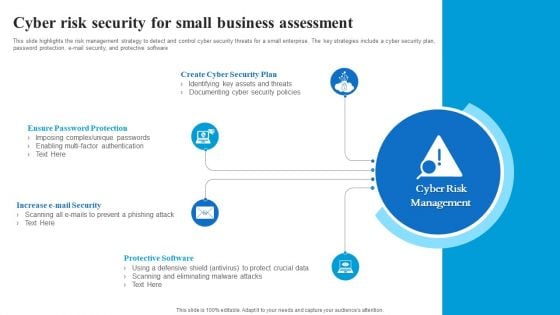
Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
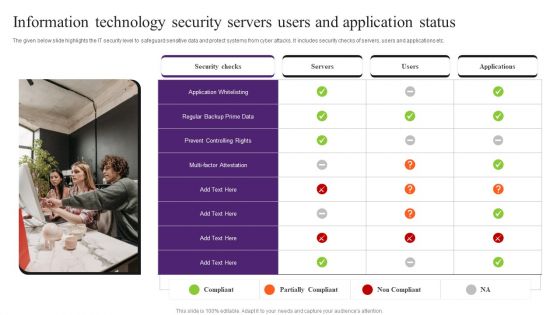
Information Technology Security Servers Users And Application Status Pictures PDF
The given below slide highlights the IT security level to safeguard sensitive data and protect systems from cyber attacks. It includes security checks of servers, users and applications etc. Presenting Information Technology Security Servers Users And Application Status Pictures PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Application Whitelisting, Security Checks, Information Technology Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
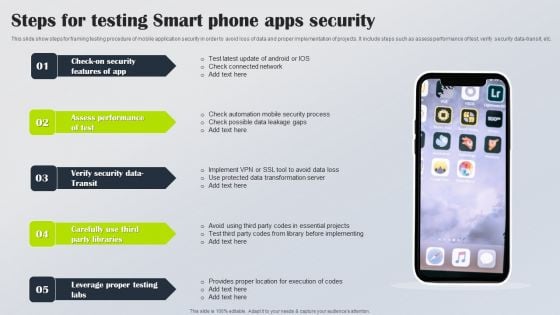
Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
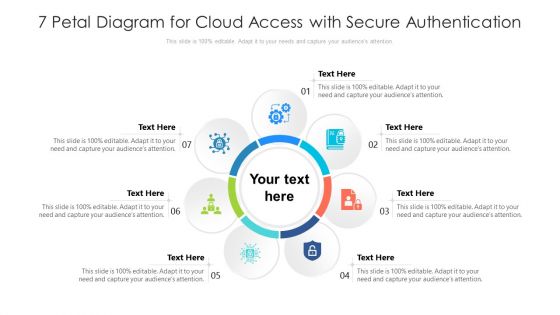
7 Petal Diagram For Cloud Access With Secure Authentication Ppt PowerPoint Presentation File Designs PDF
Persuade your audience using this 7 petal diagram for cloud access with secure authentication ppt powerpoint presentation file designs pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including 7 petal diagram for cloud access with secure authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
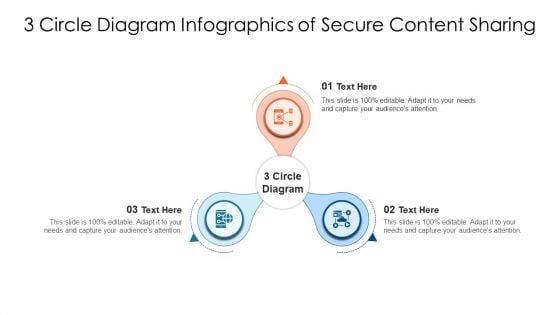
3 Circle Diagram Infographics Of Secure Content Sharing Ppt PowerPoint Presentation File Professional PDF
Persuade your audience using this 3 circle diagram infographics of secure content sharing ppt powerpoint presentation file professional pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including 3 circle diagram infographics of secure content sharing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
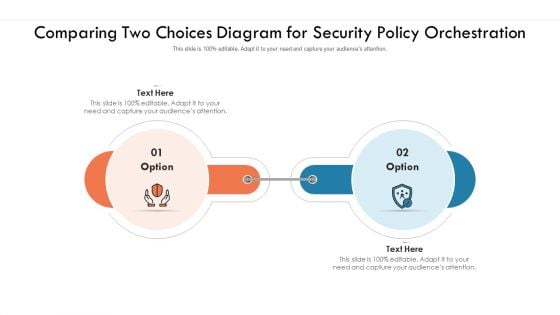
Comparing Two Choices Diagram For Security Policy Orchestration Ppt PowerPoint Presentation Gallery Design Templates PDF
Persuade your audience using this comparing two choices diagram for security policy orchestration ppt powerpoint presentation gallery design templates pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including comparing two choices diagram for security policy orchestration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
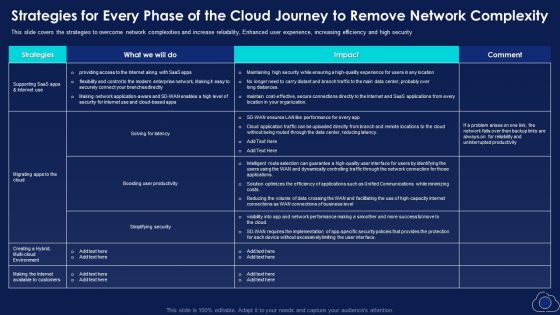
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security. Deliver an awe inspiring pitch with this creative Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF bundle. Topics like Productivity, Simplifying Security, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
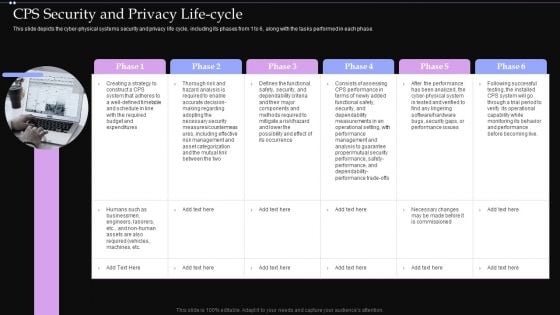
CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
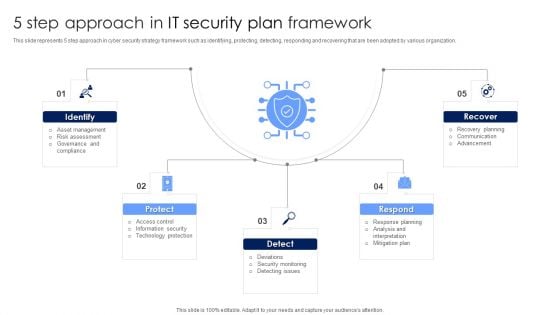
5 Step Approach In IT Security Plan Framework Designs PDF
This slide represents 5 step approach in cyber security strategy framework such as identifying, protecting, detecting, responding and recovering that are been adopted by various organization. Presenting 5 Step Approach In IT Security Plan Framework Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
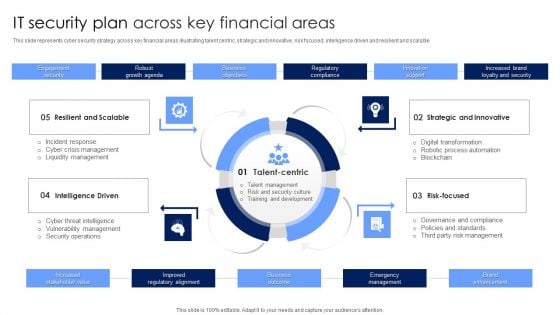
IT Security Plan Across Key Financial Areas Portrait PDF
This slide represents cyber security strategy across key financial areas illustrating talent centric, strategic and innovative, risk focused, intelligence driven and resilient and scalable. Presenting IT Security Plan Across Key Financial Areas Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strategic And Innovative, Risk Focused, Intelligence Driven. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
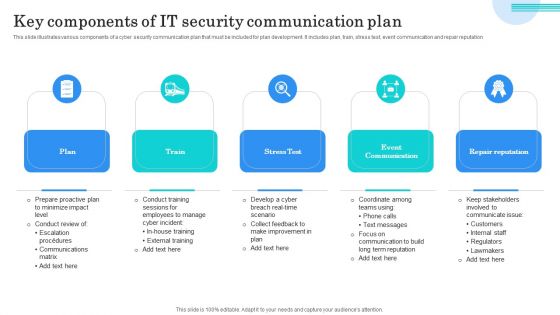
Key Components Of IT Security Communication Plan Mockup PDF
This slide illustrates various components of a cyber security communication plan that must be included for plan development. It includes plan, train, stress test, event communication and repair reputation. Presenting Key Components Of IT Security Communication Plan Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Plan, Train, Stress Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
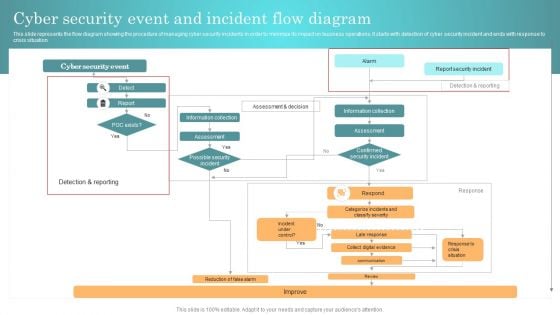
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Incident Response Techniques Deployement Five Phases Of Cybersecurity Incident Management Formats PDF
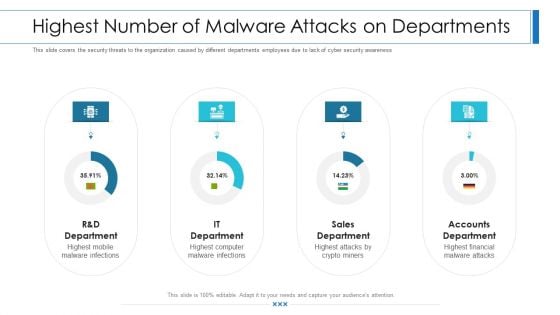
Workforce Security Realization Coaching Plan Highest Number Of Malware Attacks On Departments Professional PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan highest number of malware attacks on departments professional pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
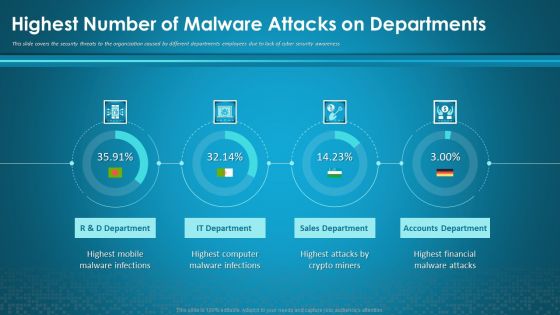
Organizational Network Security Awareness Staff Learning Highest Number Of Malware Attacks On Departments Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning highest number of malware attacks on departments information pdf. Use them to share invaluable insights on sales department, accounts department, financial, computer, mobile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
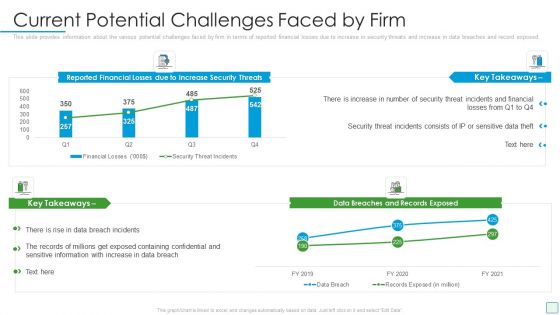
Developing Firm Security Strategy Plan Current Potential Challenges Faced By Firm Designs PDF
This slide provides information about the various potential challenges faced by firm in terms of reported financial losses due to increase in security threats and increase in data breaches and record exposed. Deliver an awe inspiring pitch with this creative developing firm security strategy plan current potential challenges faced by firm designs pdf bundle. Topics like security, financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
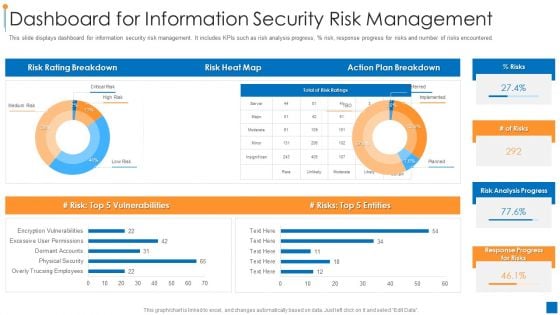
International Organization Standardization 270001 Dashboard For Information Security Risk Management Pictures PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, parcent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative international organization standardization 270001 dashboard for information security risk management pictures pdf bundle. Topics like dashboard for information security risk management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
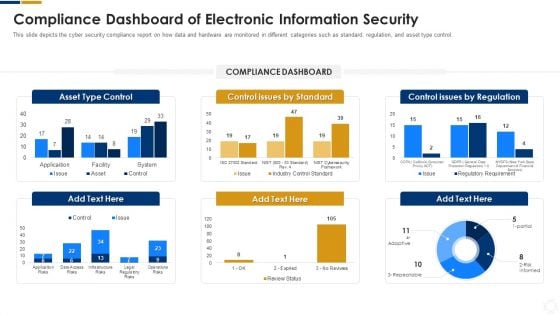
Cybersecurity Compliance Dashboard Of Electronic Information Security Ppt Outline Graphic Tips PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative cybersecurity compliance dashboard of electronic information security ppt outline graphic tips pdf bundle. Topics like compliance dashboard of electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
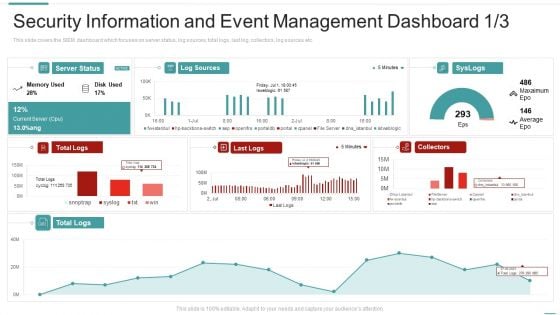
Risk Recognition Automation Security Information And Event Management Dashboard Ppt Model Elements PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard ppt model elements pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
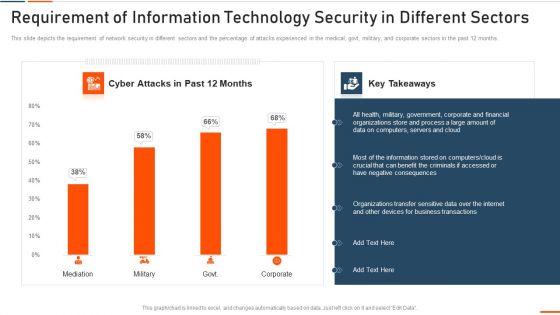
Requirement Of Information Technology Security In Different Sectors Ppt Ideas Shapes PDF
This slide depicts the requirement of network security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with requirement of information technology security in different sectors ppt ideas shapes pdf bundle. Topics like requirement of information technology security in different sectors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
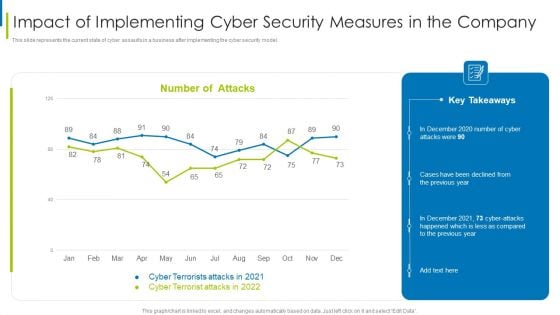
Cyber Terrorism Assault Impact Of Implementing Cyber Security Measures In The Company Professional PDF
This slide represents the current state of cyber assaults in a business after implementing the cyber security model.Deliver an awe inspiring pitch with this creative cyber terrorism assault impact of implementing cyber security measures in the company professional pdf bundle. Topics like impact of implementing cyber security measures in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF
This slide shows the various types of cloud security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF. This layout presents information on Quarterly Comparison Of Security, Cloud Based Systems Threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
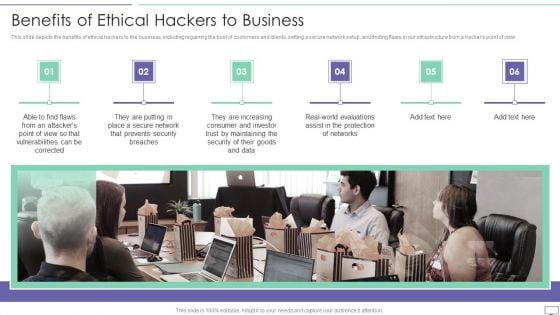
IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view.Presenting IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Consumer And Investor, Assist In The Protection, Prevents Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
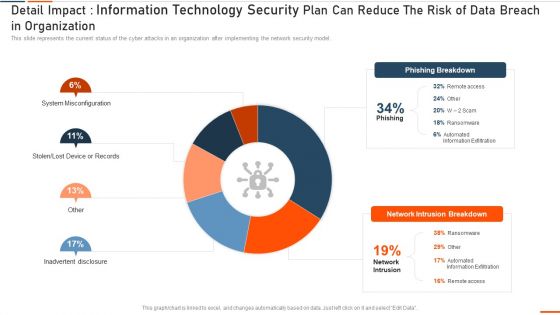
Detail Impact Information Technology Security Plan Can Reduce Ppt Show Slide Download PDF
This slide represents the current status of the cyber attacks in an organization after implementing the network security model. Deliver an awe inspiring pitch with this creative it security detail impact detail impact information technology security plan can reduce ppt show slide download pdf bundle. Topics like detail impact information technology security plan can reduce the risk of data breach in organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
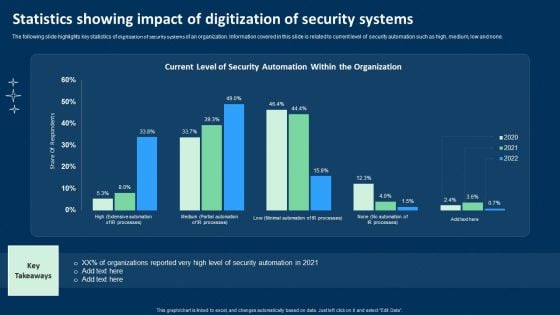
Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF
The following slide highlights key statistics of digitization of security systems of an organization. Information covered in this slide is related to current level of security automation such as high, medium, low and none. Showcasing this set of slides titled Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF. The topics addressed in these templates are Current Level, Security Automation, Organization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Threat Intelligence Cyber Security Ppt PowerPoint Presentation Infographic Template Diagrams Cpb Pdf
Presenting this set of slides with name threat intelligence cyber security ppt powerpoint presentation infographic template diagrams cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like threat intelligence cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Environments Best Suited For Efficient And Secure Supply Chains Diagrams PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver and pitch your topic in the best possible manner with environments best suited for efficient and secure supply chains diagrams pdf. Use them to share invaluable insights on operations strategy, inventory investment, efficient supply chains, responsible supply chains and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
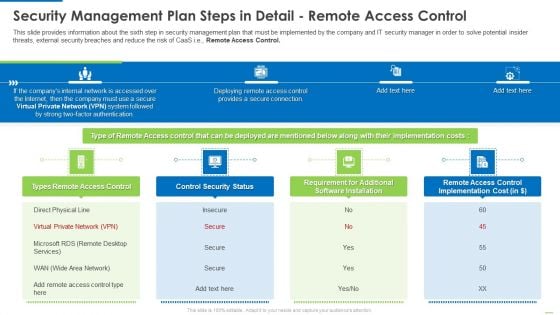
Security Management Plan Steps In Detail Remote Access Control Diagrams PDF
This is a security management plan steps in detail remote access control diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control security status, requirement for additional software installation, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Executing Security Management Plan To Minimize Threats Diagrams PDF
This is a agenda for executing security management plan to minimize threats diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizational, protect, risks, reduce, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver and pitch your topic in the best possible manner with this ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF. Use them to share invaluable insights on Assessing Information, Occurrence Identification, Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
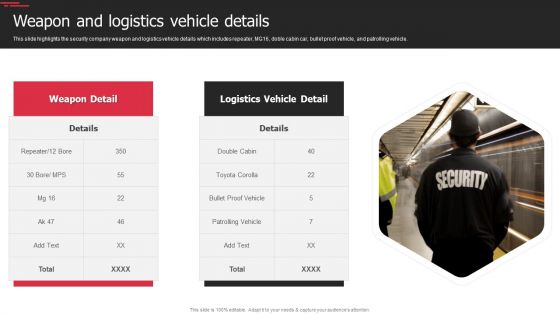
Security Agency Business Profile Weapon And Logistics Vehicle Details Diagrams PDF
This slide highlights the security company weapon and logistics vehicle details which includes repeater, MG16, doble cabin car, bullet proof vehicle, and patrolling vehicle. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Weapon And Logistics Vehicle Details Diagrams PDF bundle. Topics like Weapon, Logistics Vehicle Details can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
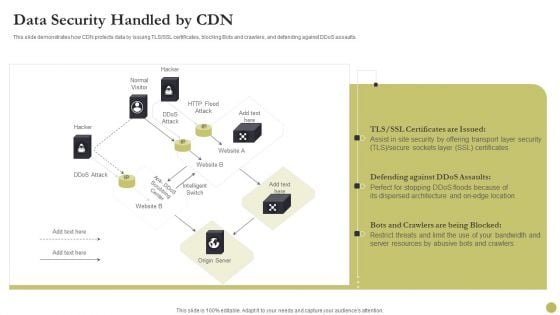
Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver and pitch your topic in the best possible manner with this Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF. Use them to share invaluable insights on Security, Location, Server Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
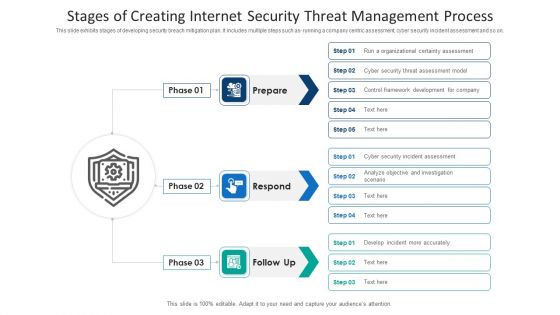
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
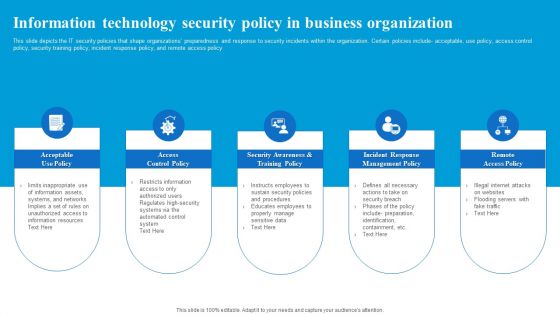
Information Technology Security Policy In Business Organization Download PDF
This slide depicts the IT security policies that shape organizations preparedness and response to security incidents within the organization. Certain policies include acceptable, use policy, access control policy, security training policy, incident response policy, and remote access policy. Presenting Information Technology Security Policy In Business Organization Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Access Control Policy, Acceptable Use Policy, Remote Access Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
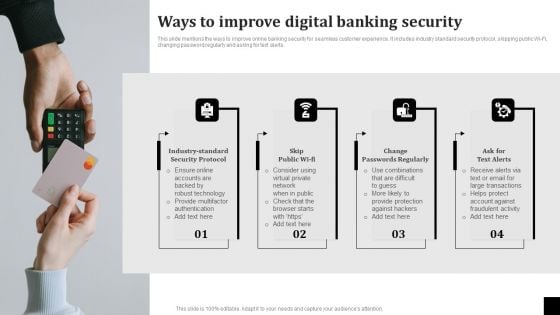
Ways To Improve Digital Banking Security Elements PDF
This slide mentions the ways to improve online banking security for seamless customer experience. It includes industry standard security protocol, skipping public Wi-Fi, changing password regularly and asking for text alerts. Presenting Ways To Improve Digital Banking Security Elements PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Industry Standard Security Protocol, Skip Public Wifi, Change Passwords Regularly. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Operations Team Roles And Responsibilities Infographics PDF
This slide exhibits key roles on the SecOps team with their roles and responsibilities that manage cybersecurity threats and attacks. It includes a security investigator, advanced security analyst, SOC manager, and security manager. Presenting Security Operations Team Roles And Responsibilities Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Skills Required, Determine, Develop Mitigation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
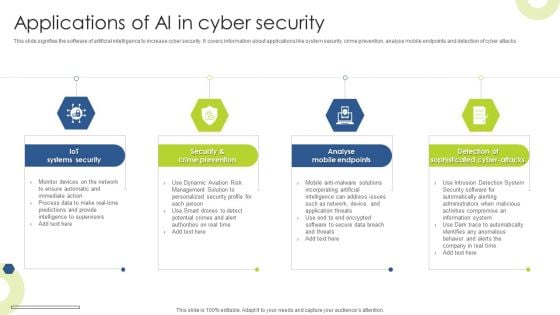
Applications Of AI In Cyber Security Infographics PDF
This slide signifies the software of artificial intelligence to increase cyber security. It covers information about applications like system security, crime prevention, analyse mobile endpoints and detection of cyber attacks Presenting Applications Of AI In Cyber Security Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Iot Systems Security, Crime Prevention, Analyse Mobile Endpoints. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Attacks Faced By Organization Mockup PDF
This slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. If you are looking for a format to display your unique thoughts, then the professionally designed Information Security Attacks Faced By Organization Mockup PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Security Attacks Faced By Organization Mockup PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Security In 5G Technology Architecture 5G Network Structure Pictures PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Retrieve professionally designed Security In 5G Technology Architecture 5G Network Structure Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
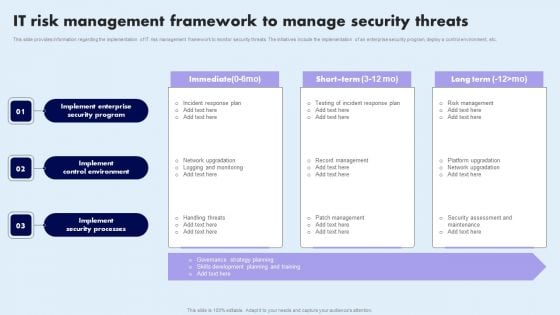
IT Risk Management Framework To Manage Security Threats Summary PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Retrieve professionally designed IT Risk Management Framework To Manage Security Threats Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
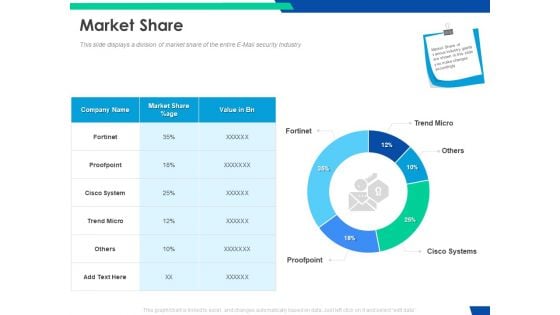
Cloud Based Email Security Market Report Market Share Ppt File Background PDF
This slide displays a division of market share of the entire E Mail security Industry. Deliver an awe inspiring pitch with this creative cloud based email security market report market share ppt file background pdf bundle. Topics like market share can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
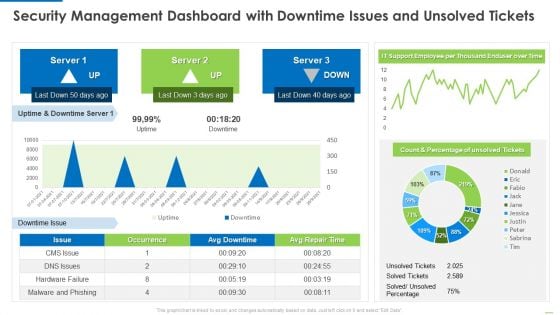
Security Management Dashboard With Downtime Issues And Unsolved Tickets Introduction PDF
Deliver an awe inspiring pitch with this creative Security management dashboard with downtime issues and unsolved tickets introduction pdf bundle. Topics like security management dashboard with downtime issues and unsolved tickets can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
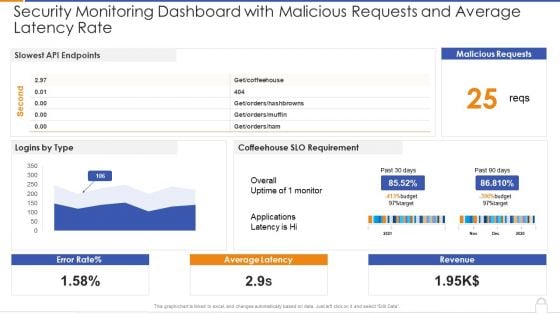
Security Monitoring Dashboard With Malicious Requests And Average Latency Rate Introduction PDF
Deliver an awe inspiring pitch with this creative security monitoring dashboard with malicious requests and average latency rate introduction pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
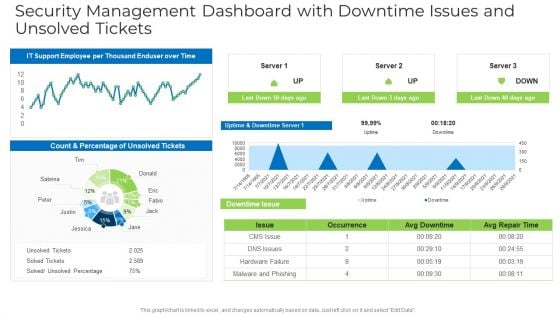
Security Management Dashboard With Downtime Issues And Unsolved Tickets Structure PDF
Deliver and pitch your topic in the best possible manner with this security management dashboard with downtime issues and unsolved tickets structure pdf. Use them to share invaluable insights on security management dashboard with downtime issues and unsolved tickets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Operating Designs PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard operating designs pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
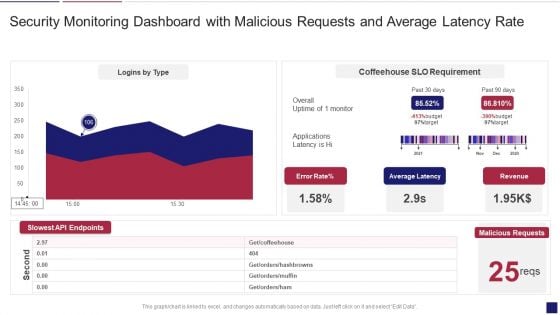
Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Rate Summary PDF
Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks security monitoring dashboard rate summary pdf. Use them to share invaluable insights on security monitoring dashboard with malicious requests and average latency rate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
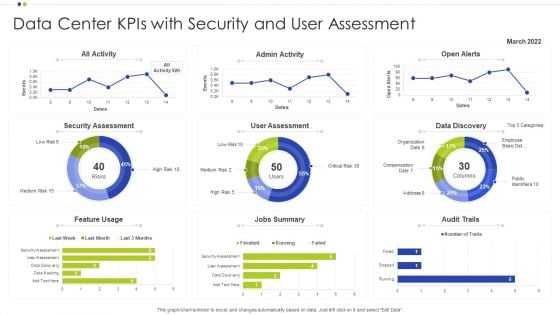
Data Center Kpis With Security And User Assessment Ppt Infographics Deck PDF
Showcasing this set of slides titled Data Center Kpis With Security And User Assessment Ppt Infographics Deck PDF. The topics addressed in these templates are Data Center, Data Discovery, Security Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
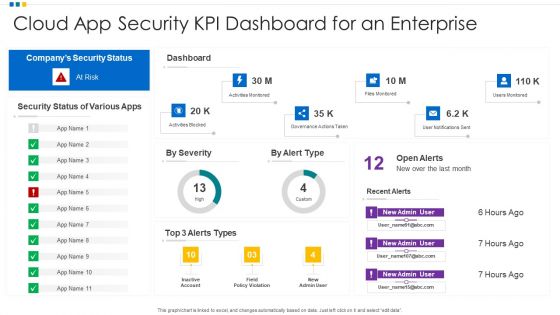
Cloud App Security KPI Dashboard For An Enterprise Ppt Model Template PDF
Showcasing this set of slides titled Cloud App Security KPI Dashboard For An Enterprise Ppt Model Template PDF. The topics addressed in these templates are Cloud App Security, KPI Dashboard, Enterprise. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
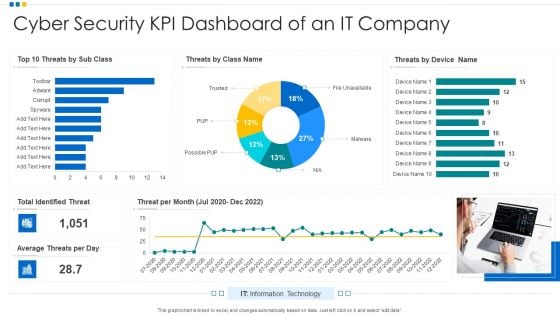
Cyber Security KPI Dashboard Of An IT Company Ppt Show Introduction PDF
Showcasing this set of slides titled Cyber Security KPI Dashboard Of An IT Company Ppt Show Introduction PDF. The topics addressed in these templates are Cyber Security, KPI Dashboard, Average Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
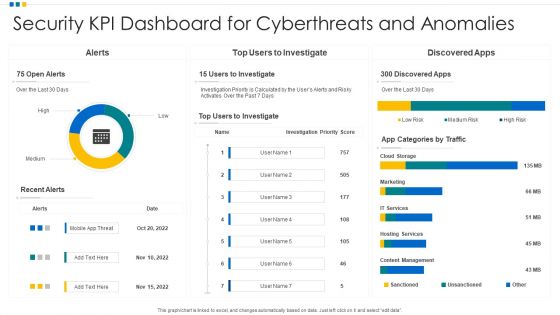
Security KPI Dashboard For Cyberthreats And Anomalies Ppt Professional Gridlines PDF
Showcasing this set of slides titled Security KPI Dashboard For Cyberthreats And Anomalies Ppt Professional Gridlines PDF. The topics addressed in these templates are Security KPI Dashboard, Cyberthreats And Anomalies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
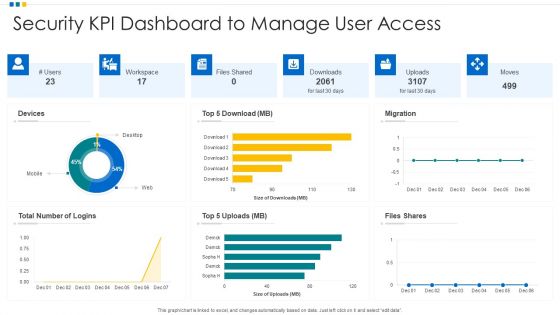
Security KPI Dashboard To Manage User Access Ppt Infographic Template Graphics Pictures PDF
Pitch your topic with ease and precision using this Security KPI Dashboard To Manage User Access Ppt Infographic Template Graphics Pictures PDF. This layout presents information on Devices, Security KPI Dashboard, Workspace. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security KPI Dashboard With Various Key Performance Indicators Ppt Portfolio Objects PDF
Showcasing this set of slides titled Security KPI Dashboard With Various Key Performance Indicators Ppt Portfolio Objects PDF. The topics addressed in these templates are Security Kpi Dashboard, Performance Indicators, Analyst Assigned. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
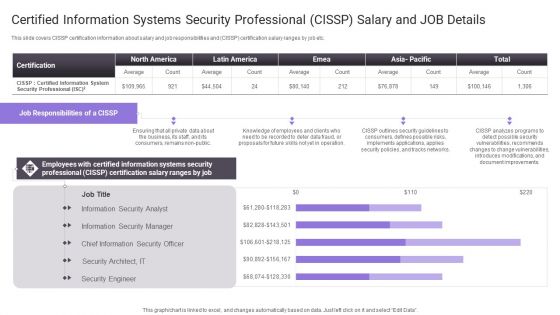
Certified Information Systems Security Professional Cissp Salary And Job Details Slides PDF
Deliver and pitch your topic in the best possible manner with this Certified Information Systems Security Professional Cissp Salary And Job Details Slides PDF. Use them to share invaluable insights on Document Improvements, Introduces Modifications, Information Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
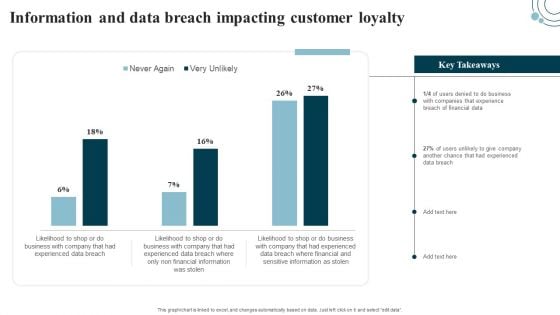
Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select edit data. Get a simple yet stunning designed Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Information Systems Security And Risk Management Plan Post It Notes Diagrams PDF
Get a simple yet stunning designed Information Systems Security And Risk Management Plan Post It Notes Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Systems Security And Risk Management Plan Post It Notes Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Table Of Contents For SDN Security Architecture Ppt PowerPoint Presentation File Diagrams PDF
Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Table Of Contents For SDN Security Architecture Ppt PowerPoint Presentation File Diagrams PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Table Of Contents For SDN Security Architecture Ppt PowerPoint Presentation File Diagrams PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
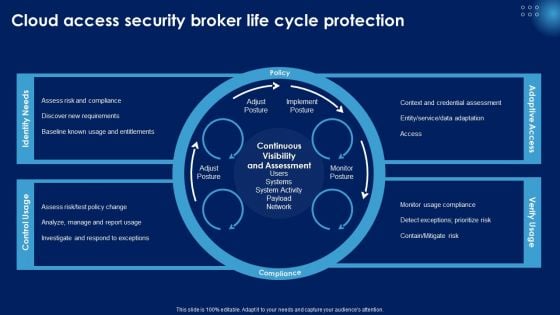
Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
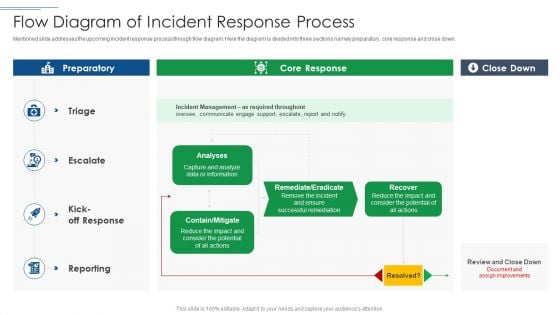
IT Security Risk Management Approach Introduction Flow Diagram Of Incident Response Process Demonstration PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Flow Diagram Of Incident Response Process Demonstration PDF bundle. Topics like Incident Management, Potential can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
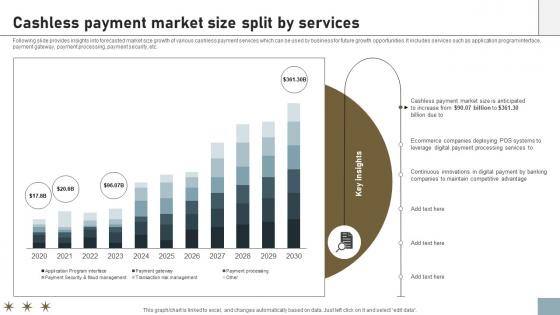
Online Payment Techniques For Providing Cashless Payment Market Size Split
Following slide provides insights into forecasted market size growth of various cashless payment services which can be used by business for future growth opportunities. It includes services such as application program interface, payment gateway, payment processing, payment security, etc. Take your projects to the next level with our ultimate collection of Online Payment Techniques For Providing Cashless Payment Market Size Split. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest Following slide provides insights into forecasted market size growth of various cashless payment services which can be used by business for future growth opportunities. It includes services such as application program interface, payment gateway, payment processing, payment security, etc.

Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF
The following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. This Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
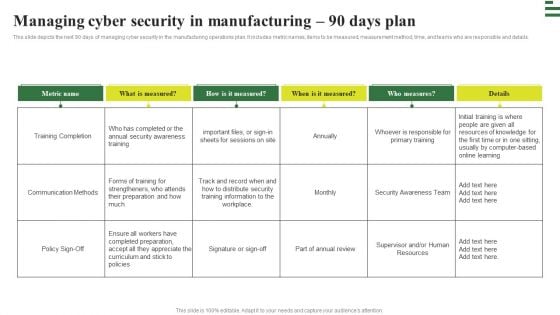
Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
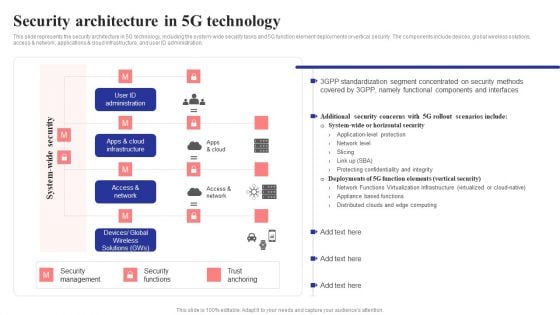
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.

Challenge And Solutions 2 Cloud Threats And Security Ppt Outline Design Inspiration PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt outline design inspiration pdf bundle. Topics like implement data encryption techniques to eliminate risk of infiltration, security and compliance risks are major considerations for the company, professional business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
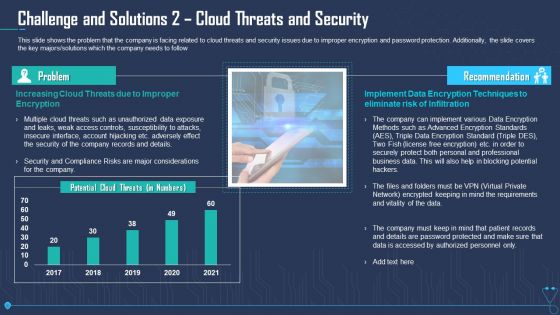
Challenge And Solutions 2 Cloud Threats And Security Ppt Gallery Images PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt gallery images pdf bundle. Topics like challenge and solutions 2 cloud threats and security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Challenge And Solutions 2 Cloud Threats And Security Ppt Inspiration Slideshow PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver and pitch your topic in the best possible manner with this challenge and solutions 2 cloud threats and security ppt inspiration slideshow pdf. Use them to share invaluable insights on security, risks, encryption methods, echniques and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cybersecurity Dashboard For Threat Tracking In Electronic Information Security Ppt Ideas Graphics PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cybersecurity dashboard for threat tracking in electronic information security ppt ideas graphics pdf bundle. Topics like dashboard for threat tracking in electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Dashboard For Threat Tracking In Information Technology Security Ppt Portfolio Shapes PDF
This slide depicts the dashboard for threat tracking in network security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver and pitch your topic in the best possible manner with this dashboard for threat tracking in information technology security ppt portfolio shapes pdf. Use them to share invaluable insights on dashboard for threat tracking in information technology security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
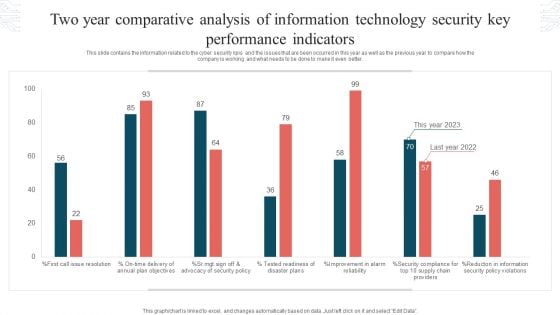
Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF
This slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Showcasing this set of slides titled Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF. The topics addressed in these templates are Tested Readiness, Disaster Plans, Security Policy Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
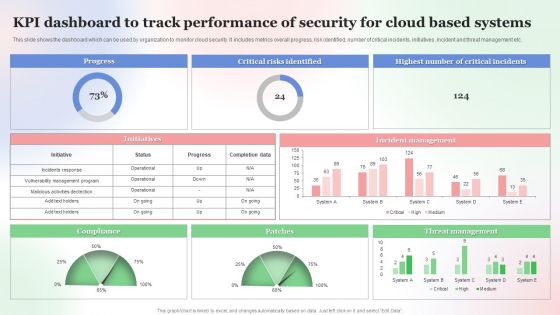
KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF
This slide shows the dashboard which can be used by organization to monitor cloud security. It includes metrics overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Showcasing this set of slides titled KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF. The topics addressed in these templates are Kpi Dashboard To Track, Performance Of Security, Cloud Based Systems . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
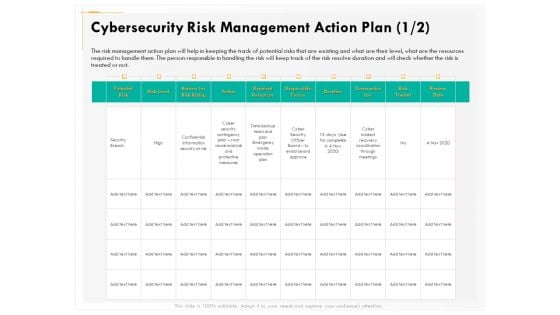
Computer Security Incident Handling Cybersecurity Risk Management Action Plan Diagrams PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management action plan diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason for risk rating, action, required resources, responsible person, duration, communication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
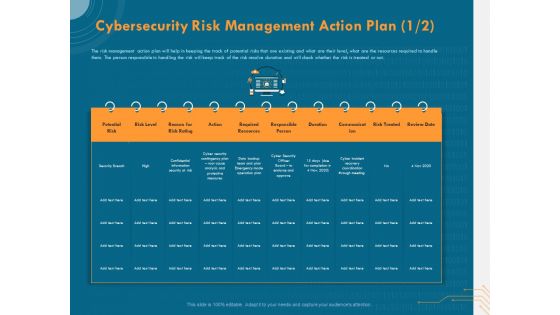
Cyber Security Implementation Framework Cybersecurity Risk Management Action Plan Potential Diagrams PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity risk management action plan potential diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason risk rating, action, required resources, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
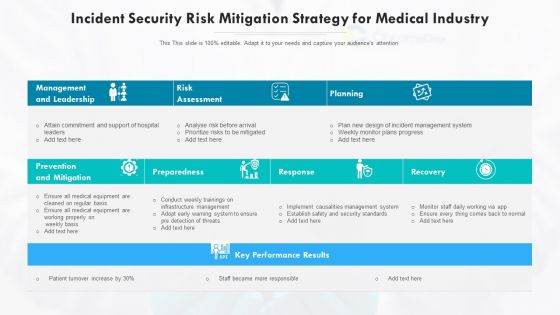
Incident Security Risk Mitigation Strategy For Medical Industry Ppt PowerPoint Presentation Gallery Diagrams PDF
Showcasing this set of slides titled incident security risk mitigation strategy for medical industry ppt powerpoint presentation gallery diagrams pdf. The topics addressed in these templates are preparedness, planning, prevention and mitigation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
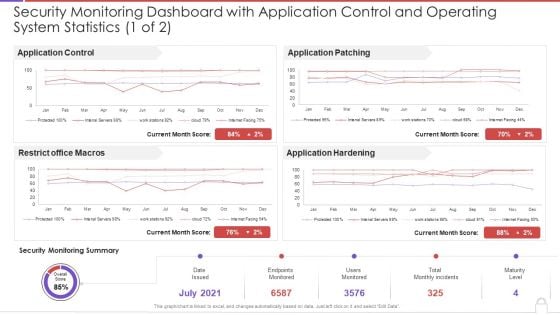
Security Monitoring Dashboard With Application Control And Operating System Statistics Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this security monitoring dashboard with application control and operating system statistics template pdf. Use them to share invaluable insights on application control, restrict office macros, application patching, application hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
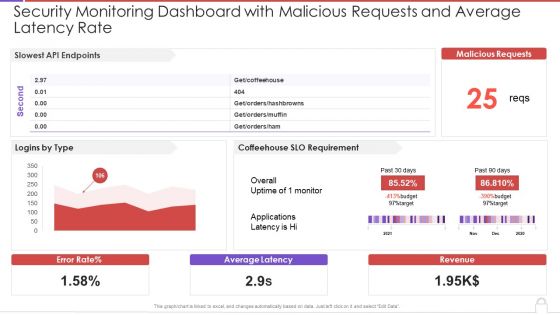
Security Monitoring Dashboard With Malicious Requests And Average Latency Rate Topics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative security monitoring dashboard with malicious requests and average latency rate topics pdf bundle. Topics like slowest api endpoints, malicious requests, coffeehouse slo can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
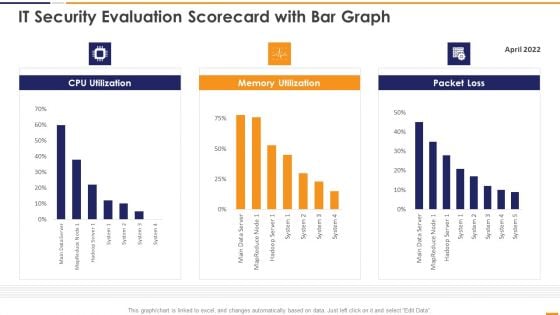
IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF. Use them to share invaluable insights on CPU Utilization Memory, Utilization Packet Loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
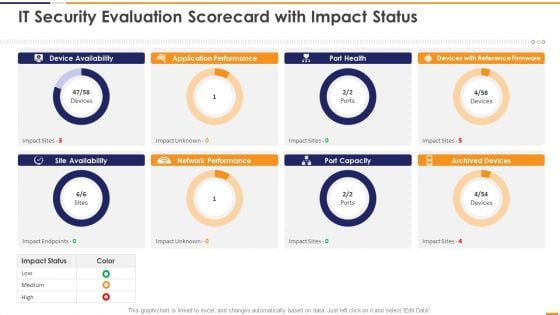
IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF. Use them to share invaluable insights on Device Availability Application, Performance Port Health, Devices Reference Firmware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
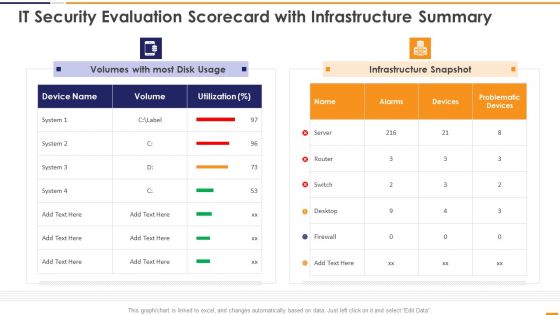
IT Security Evaluation Scorecard With Infrastructure Summary Ppt Slides Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Infrastructure Summary Ppt Slides Portrait PDF bundle. Topics like Volumes Most Disk, Usage Infrastructure Snapshot can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
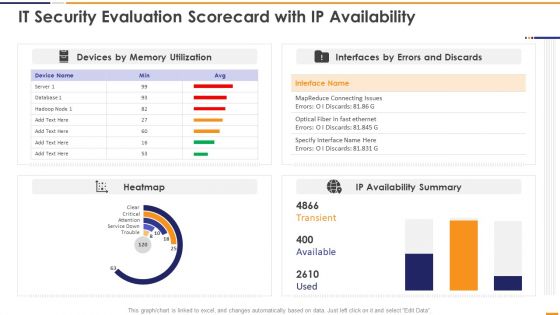
IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF. Use them to share invaluable insights on Devices Memory Utilization, Interfaces Errors Discards, IP Availability Summary and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
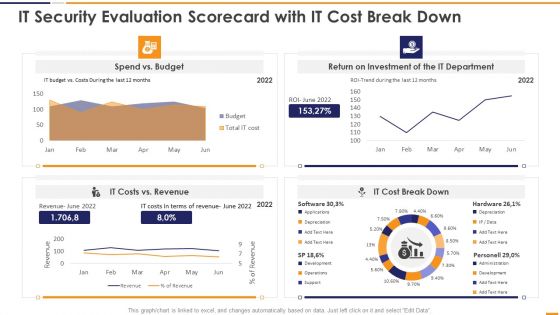
IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF bundle. Topics like Spend Vs Budget, Return On Investment, IT Department Revenue, IT Costs Vs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
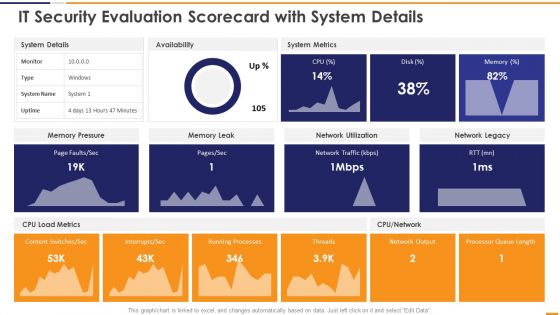
IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF. Use them to share invaluable insights on System Details Availability, System Metrics Memory, Pressure Memory Leak and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
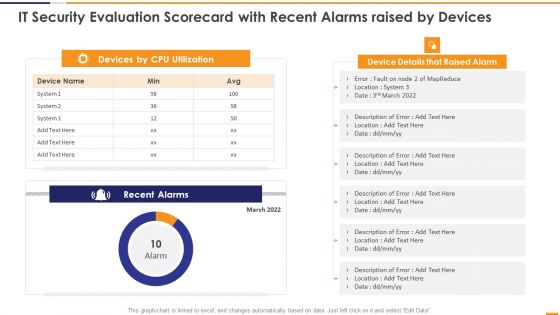
IT Security Evaluation Scorecard With Recent Alarms Raised By Devices Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Recent Alarms Raised By Devices Guidelines PDF bundle. Topics like Devices CPU Utilization, Device Details Raised can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF. Use them to share invaluable insights on Response Time 2022, Disk Utilization Availability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
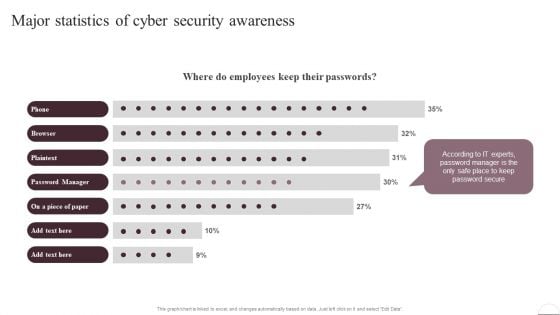
Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. There are so many reasons you need a Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
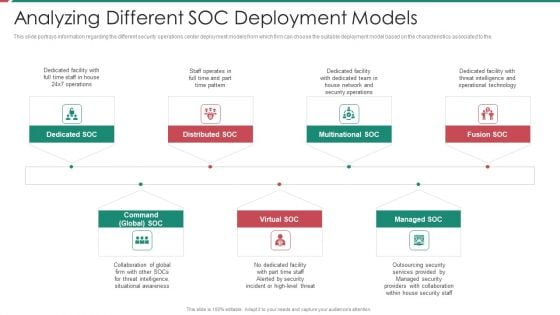
Security And Process Integration Analyzing Different SOC Deployment Models Diagrams PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a security and process integration analyzing different soc deployment models diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
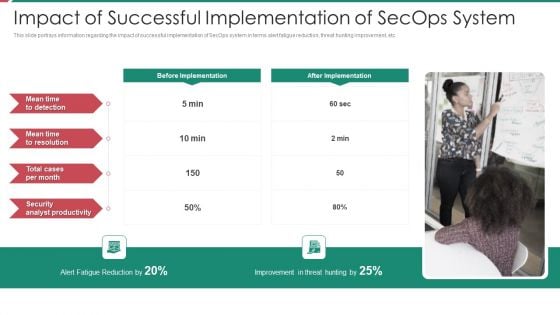
Security And Process Integration Impact Of Successful Implementation Of Secops System Diagrams PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting security and process integration impact of successful implementation of secops system diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
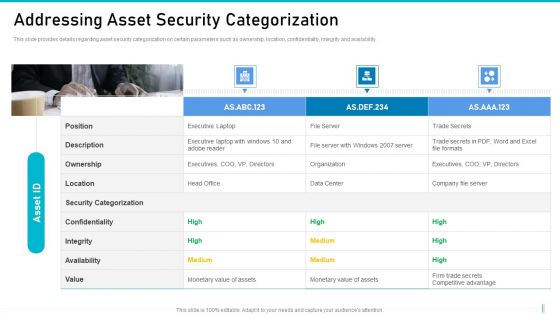
Risk Management For Organization Essential Assets Addressing Asset Security Categorization Diagrams PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Presenting risk management for organization essential assets addressing asset security categorization diagrams pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ownership, location, confidentiality, integrity, availability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
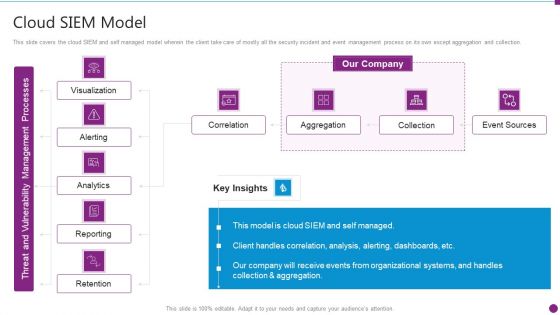
Security Information And Event Management Strategies For Financial Audit And Compliance Cloud SIEM Model Diagrams PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance cloud siem model diagrams pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
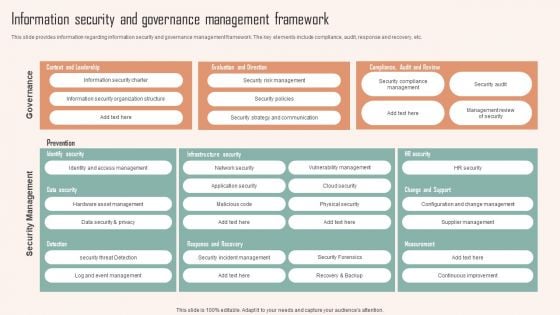
Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF
The following slide showcases perceptive of expert analysts about IT company i.e. Awake Society. It showcase reviews of IT manager, chief information security officer and IT director. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
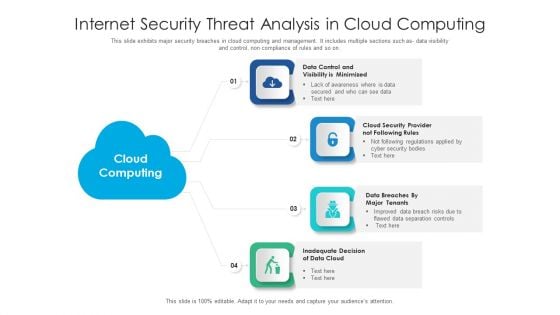
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
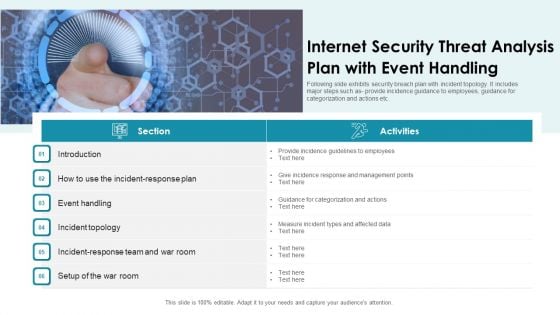
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
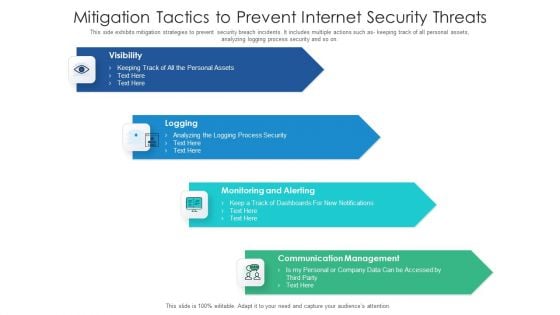
Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
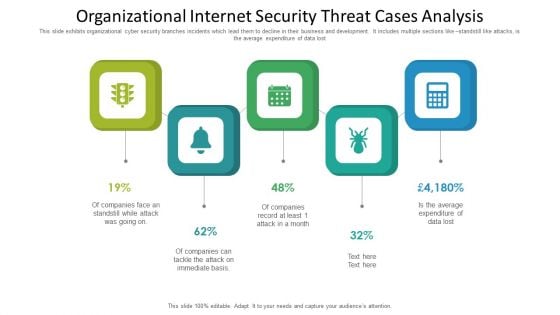
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
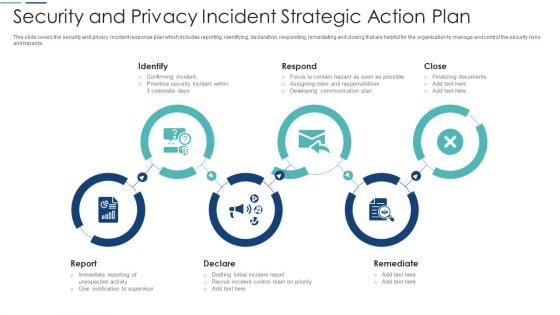
Security And Privacy Incident Strategic Action Plan Download PDF
This slide covers the security and privacy incident response plan which includes reporting, identifying, declaration, responding, remediating and closing that are helpful for the organization to manage and control the security risks and hazards. Presenting security and privacy incident strategic action plan download pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including confirming incident, assigning responsibilities, communication plan, supervisor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
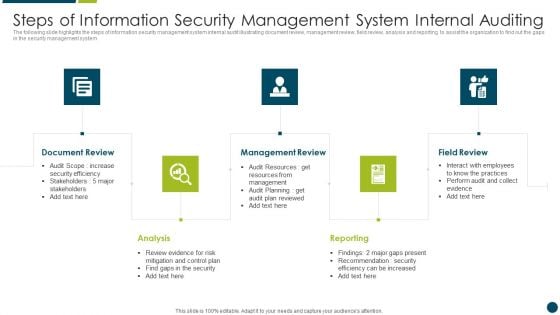
Steps Of Information Security Management System Internal Auditing Structure PDF
The following slide highlights the steps of information security management system internal audit illustrating document review, management review, field review, analysis and reporting to assist the organization to find out the gaps in the security management system Presenting Steps Of Information Security Management System Internal Auditing Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Management Review, Reporting, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully

Six Practices For IT Security Management Program Microsoft PDF
This slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency.Presenting Six Practices For IT Security Management Program Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Analysis Prioritization, Consolidation Procedure, Strategic Initiatives This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
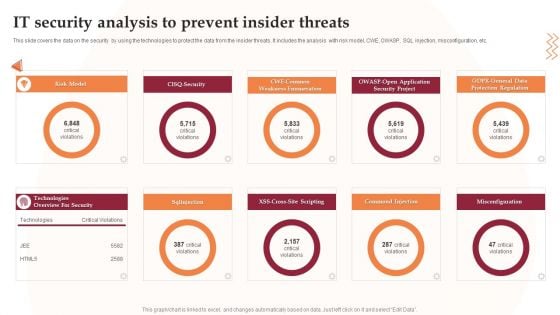
IT Security Analysis To Prevent Insider Threats Infographics PDF
This slide covers the data on the security by using the technologies to protect the data from the insider threats. It includes the analysis with risk model, CWE, OWASP, SQL injection, misconfiguration, etc. Presenting IT Security Analysis To Prevent Insider Threats Infographics PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Project, Application, Risk Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
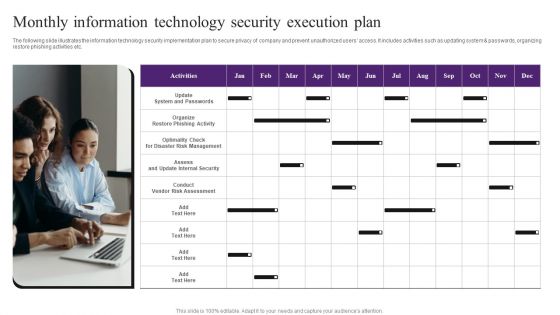
Monthly Information Technology Security Execution Plan Template PDF
The following slide illustrates the information technology security implementation plan to secure privacy of company and prevent unauthorized users access. It includes activities such as updating system and passwords, organizing restore phishing activities etc. Presenting Monthly Information Technology Security Execution Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Update System And Passwords, Conduct Vendor Risk Assessment, Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
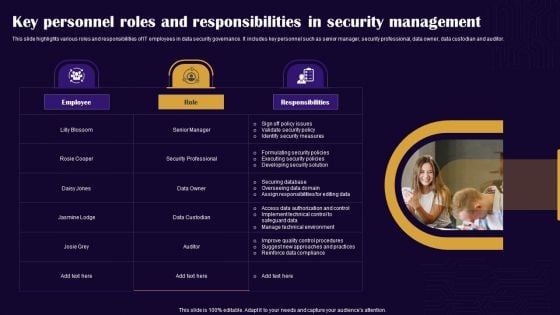
Key Personnel Roles And Responsibilities In Security Management Slides PDF
This slide highlights various roles and responsibilities of IT employees in data security governance. It includes key personnel such as senior manager, security professional, data owner, data custodian and auditor. Presenting Key Personnel Roles And Responsibilities In Security Management Slides PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Employee, Role, Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Data Encryption Security Management Technology Ideas PDF
This slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting Business Data Encryption Security Management Technology Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Authentication, Privacy, Regulatory Compliance, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
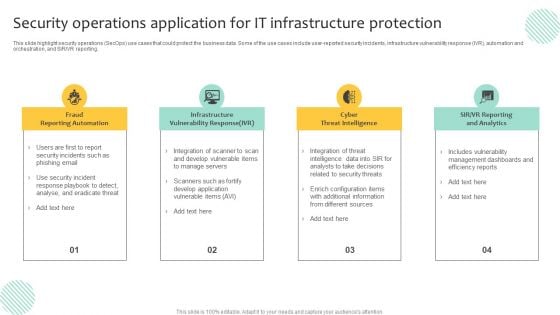
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
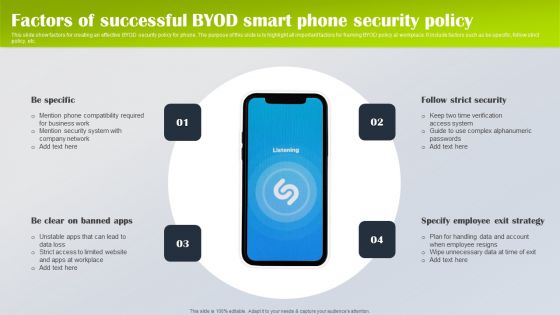
Factors Of Successful Byod Smart Phone Security Policy Designs PDF
This slide show factors for creating an effective BYOD security policy for phone. The purpose of this slide is to highlight all important factors for framing BYOD policy at workplace. It include factors such as be specific, follow strict policy, etc. Presenting Factors Of Successful Byod Smart Phone Security Policy Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Be Specific, Specify Employee Exit Strategy, Follow Strict Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
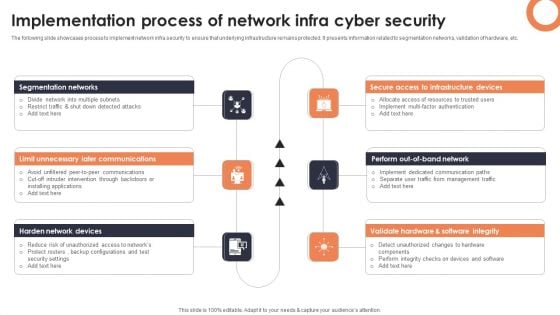
Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
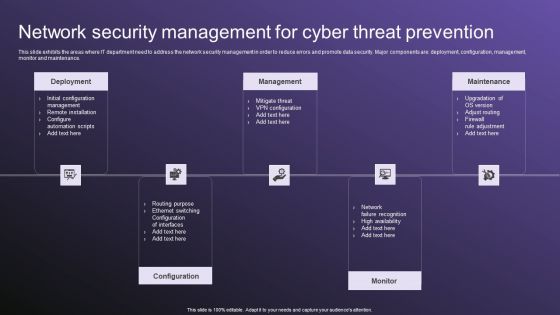
Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
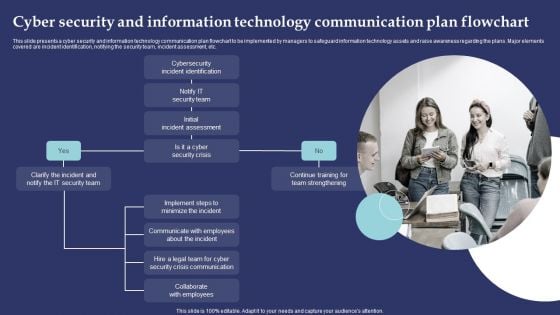
Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF
This slide presents a cyber security and information technology communication plan flowchart to be implemented by managers to safeguard information technology assets and raise awareness regarding the plans. Major elements covered are incident identification, notifying the security team, incident assessment, etc. Presenting Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cybersecurity Incident Identification, Initial Incident Assessment, Continue Training Team Strengthening. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
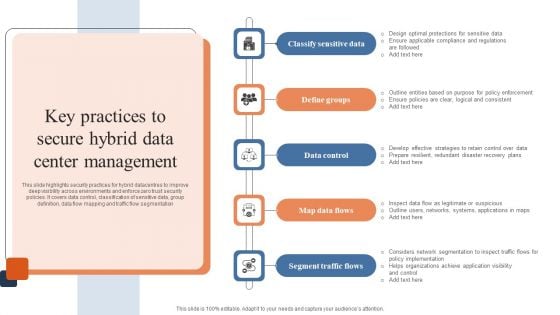
Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Managing Cyber Security In Manufacturing 60 Days Plan Information PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Retrieve professionally designed Managing Cyber Security In Manufacturing 60 Days Plan Information PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
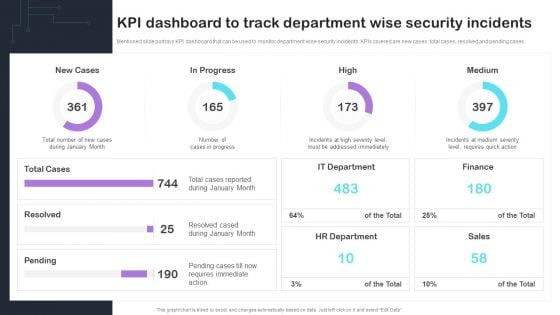
Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases. Presenting this PowerPoint presentation, titled Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
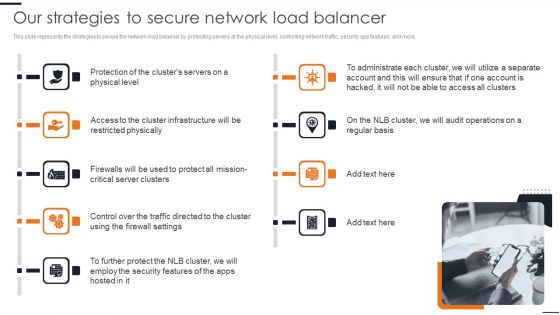
Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. This modern and well arranged Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
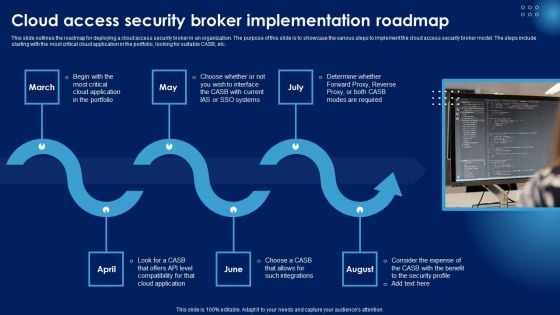
Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
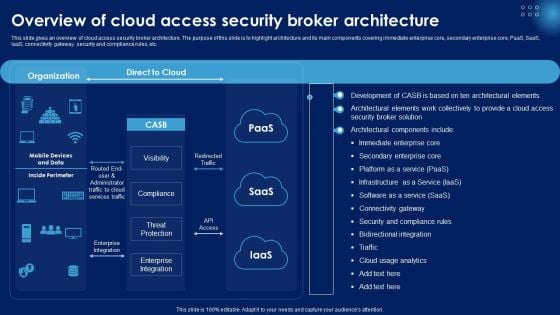
Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Slidegeeks has constructed Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Slidegeeks is here to make your presentations a breeze with Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Business Intelligence With Data Governance And Security Ppt PowerPoint Presentation Infographics Example PDF
Pitch your topic with ease and precision using this business intelligence with data governance and security ppt powerpoint presentation infographics example pdf. This layout presents information on data governance, data discovery, data quality management, connected clouds, security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
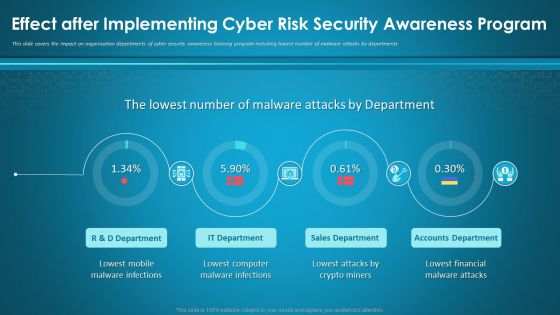
Effect After Implementing Cyber Risk Security Awareness Program Ppt Layouts Visuals PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Deliver an awe-inspiring pitch with this creative effect after implementing cyber risk security awareness program ppt layouts visuals pdf bundle. Topics like mobile, sales department, accounts department, financial, computer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
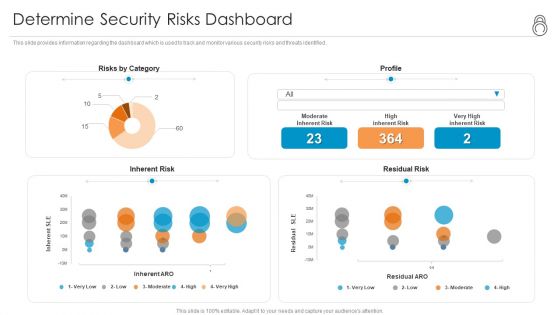
Enhanced Protection Corporate Event Administration Determine Security Risks Dashboard Summary PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration determine security risks dashboard summary pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
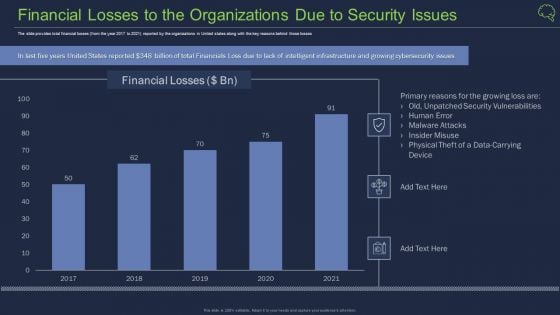
Financial Losses To The Organizations Due To Security Issues Ppt Background PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues ppt background pdf bundle. Topics like financial losses to the organizations due to security issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
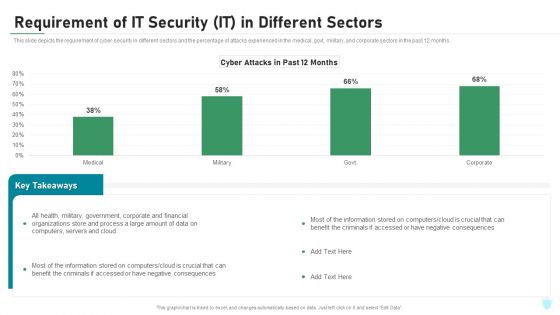
Requirement Of IT Security IT In Different Sectors Ppt Inspiration Deck PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative requirement of it security it in different sectors ppt inspiration deck pdf bundle. Topics like corporate, financial, organizations, process, computers, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
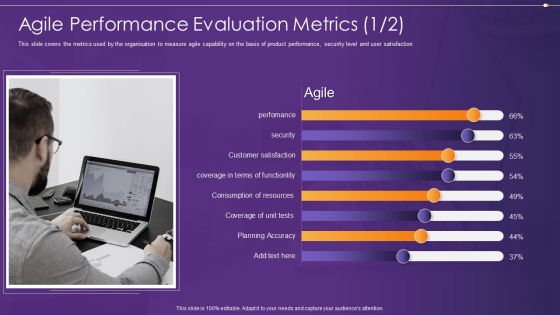
Agile Information Technology Project Administration Agile Performance Evaluation Metrics Security Ideas PDF
This slide covers the metrics used by the organisation to measure agile capability on the basis of product performance, security level and user satisfaction Deliver and pitch your topic in the best possible manner with this agile information technology project administration agile performance evaluation metrics security ideas pdf. Use them to share invaluable insights on agile performance evaluation metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
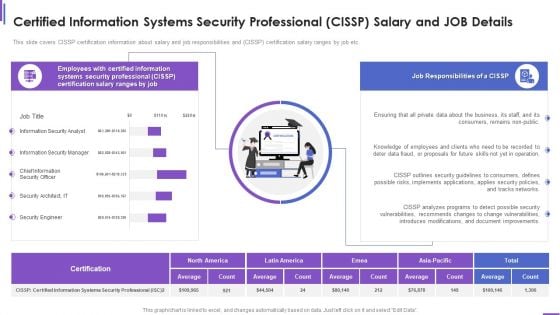
Certified Information Systems Security Professional Cissp Salary And Job Details Brochure PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver and pitch your topic in the best possible manner with this certified information systems security professional cissp salary and job details brochure pdf. Use them to share invaluable insights on consumers, security, document, networks, implements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Effective IT Risk Management Process Impact On Security Infrastructure Structure PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this effective it risk management process impact on security infrastructure structure pdf. Use them to share invaluable insights on target, risk, performance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
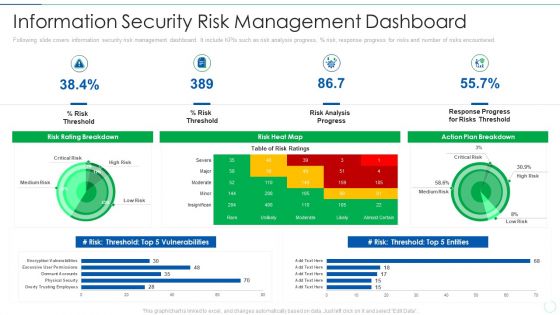
Effective IT Risk Management Process Information Security Risk Management Brochure PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percentage risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative effective it risk management process information security risk management brochure pdf bundle. Topics like analysis, plan, risk, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
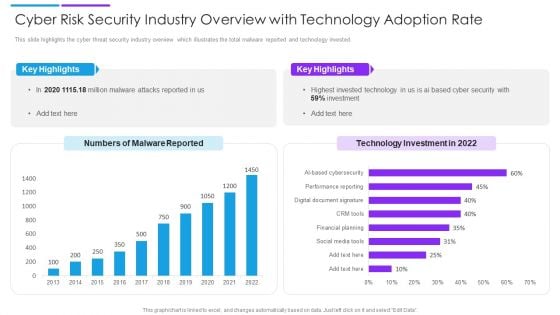
Cyber Risk Security Industry Overview With Technology Adoption Rate Slides PDF
This slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Pitch your topic with ease and precision using this cyber risk security industry overview with technology adoption rate slides pdf. This layout presents information on key highlights, technology investment, malware reported. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
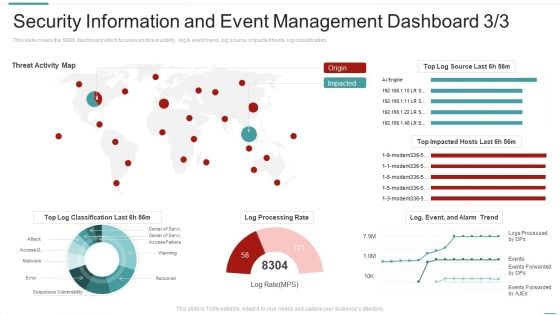
Risk Recognition Automation Security Information And Event Management Dashboard Activity Ppt Styles Influencers PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard activity ppt styles influencers pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
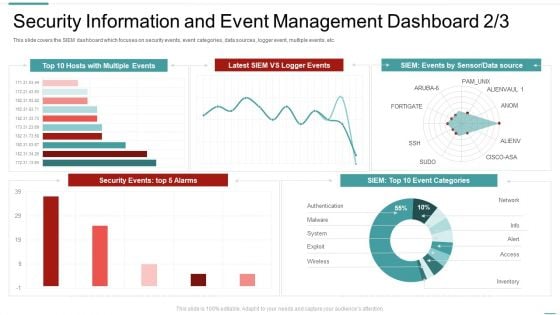
Risk Recognition Automation Security Information And Event Management Dashboard Source Ppt Professional Display PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this risk recognition automation security information and event management dashboard source ppt professional display pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
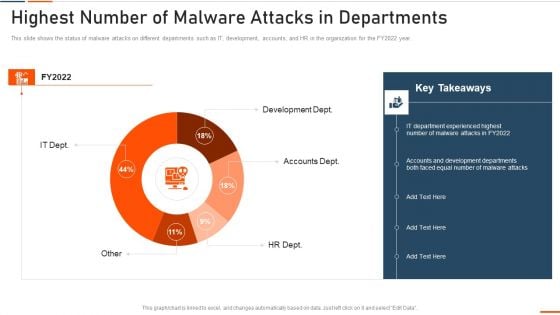
Information Technology Security Highest Number Of Malware Attacks In Departments Ppt Styles Slide Portrait PDF
This slide depicts the impact of network security training on an organization. It also shows how trained employees can reduce network attacks in the organization. Deliver and pitch your topic in the best possible manner with this information technology security highest number of malware attacks in departments ppt styles slide portrait pdf. Use them to share invaluable insights on phishing, network, intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF Use them to share invaluable insights on Assessment Process, Target Met After Introducing, Standard And Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
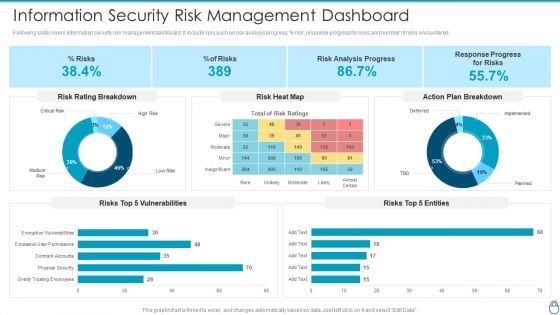
Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
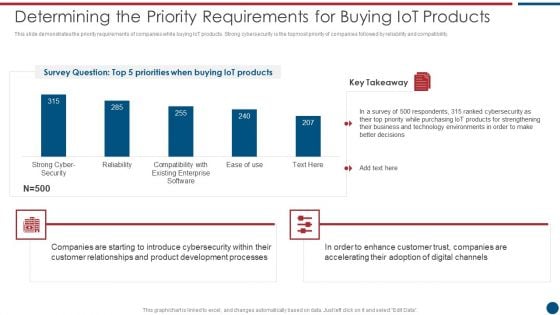
Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF bundle. Topics like Risk Heat, Action Plan, Risk Rating Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
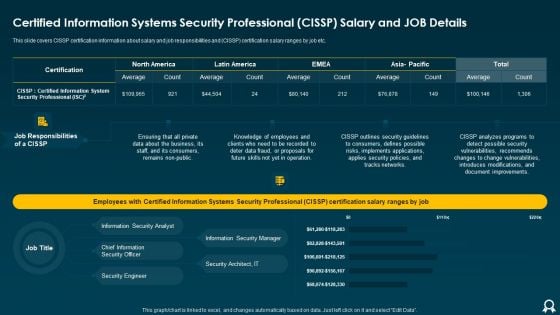
Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF bundle. Topics like Average, Tracks Networks, Applies Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
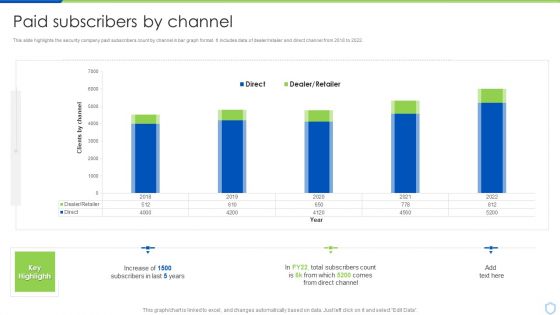
Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF bundle. Topics like Direct Channel, Subscribers In Last, Key Highlights can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home