Safety Icons
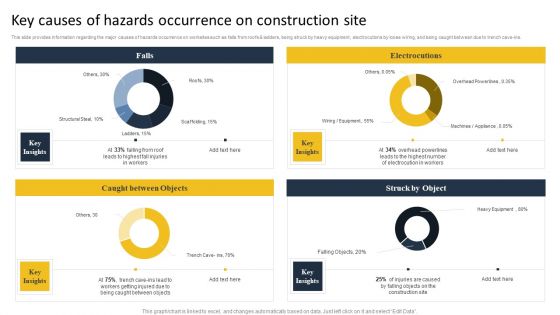
Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF
This slide provides information regarding the major causes of hazards occurrence on worksites such as falls from roofs AND ladders, being struck by heavy equipment, electrocutions by loose wiring, and being caught between due to trench cave-ins. Find a pre designed and impeccable Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for. Download the template from Slidegeeks today and give a unique touch to your presentation.
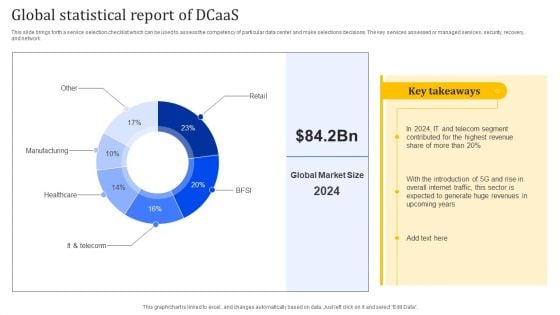
Global Statistical Report Of Dcaas Portrait PDF
This slide brings forth a service selection checklist which can be used to assess the competency of particular data center and make selections decisions. The key services assessed or managed services, security, recovery, and network. Showcasing this set of slides titled Global Statistical Report Of Dcaas Portrait PDF. The topics addressed in these templates are Manufacturing, Healthcare, Global Statistical. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF
This slide represents the technical analysis of ddos attacks against ukrainian websites by showing the internet traffic to the oschad bank website on 15 16 february 2022. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
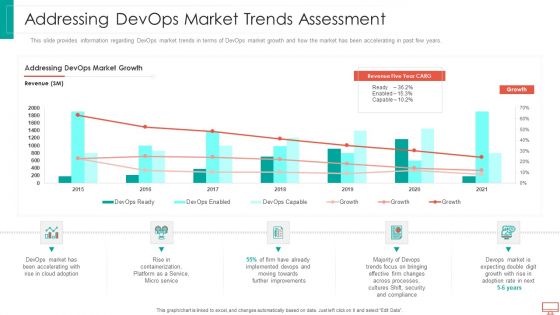
Addressing Devops Market Trends Assessment Information PDF
This slide provides information regarding DevOps market trends in terms of DevOps market growth and how the market has been accelerating in past few years. Deliver and pitch your topic in the best possible manner with this addressing devops market trends assessment information pdf. Use them to share invaluable insights on Service, Implemented, improvements, processes, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
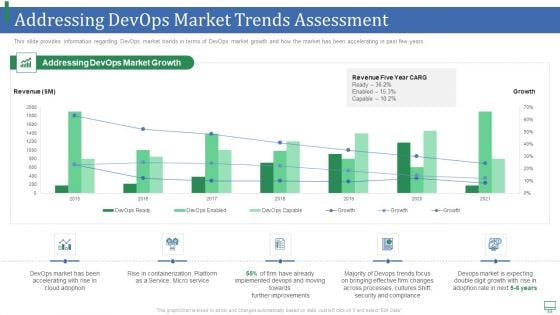
Addressing Devops Market Trends Assessment Portrait PDF
This slide provides information regarding DevOps market trends in terms of DevOps market growth and how the market has been accelerating in past few years. Deliver an awe inspiring pitch with this creative addressing devops market trends assessment portrait pdf bundle. Topics like service, implemented, processes, security, growth can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
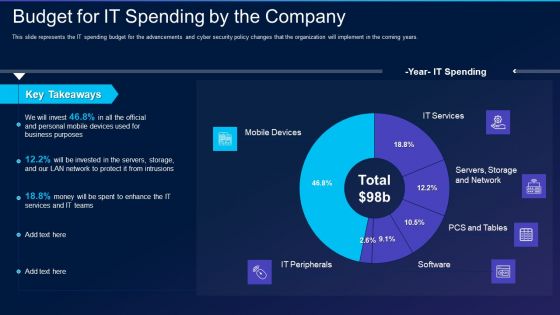
Cyber Exploitation IT Budget For IT Spending By The Company Professional PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years. Deliver an awe inspiring pitch with this creative cyber exploitation it budget for it spending by the company professional pdf bundle. Topics like mobile devices, it peripherals, it services, servers, storage and network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
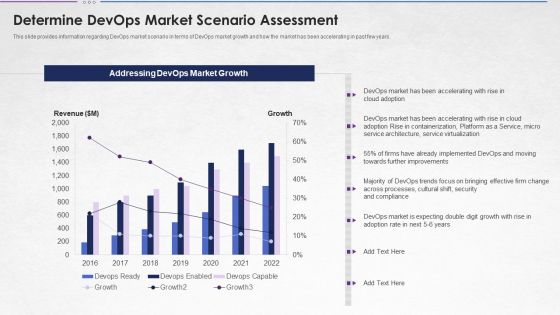
Steps For Devops Implementation IT Determine Devops Market Scenario Assessment Clipart PDF
This slide provides information regarding DevOps market scenario in terms of DevOps market growth and how the market has been accelerating in past few years. Deliver and pitch your topic in the best possible manner with this steps for devops implementation it determine devops market scenario assessment clipart pdf. Use them to share invaluable insights on market, service, security, growth and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
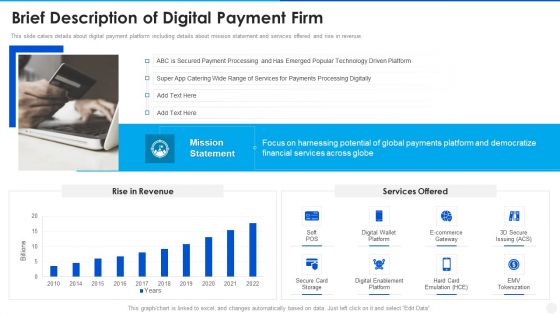
Digital Payment Solution Company Stakeholder Brief Description Of Digital Payment Firm Template PDF
This slide caters details about digital payment platform including details about mission statement and services offered and rise in revenue. Deliver an awe inspiring pitch with this creative digital payment solution company stakeholder brief description of digital payment firm template pdf bundle. Topics like secure card storage, digital enablement platform, digital wallet platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
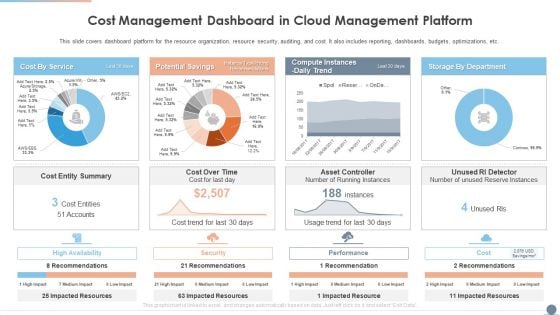
Multi Cloud Complexity Management Cost Management Dashboard In Cloud Management Platform Slides PDF
This slide covers dashboard platform for the resource organization, resource security, auditing, and cost. It also includes reporting, dashboards, budgets, optimizations, etc. Deliver and pitch your topic in the best possible manner with this Multi Cloud Complexity Management Cost Management Dashboard In Cloud Management Platform Slides PDF. Use them to share invaluable insights on Cost Entity Summary, Potential Savings, Cost By Service and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
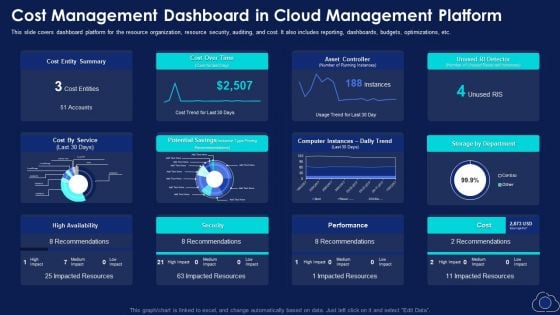
Cost Management Dashboard In Cloud Management Platform Pictures PDF
This slide covers dashboard platform for the resource organization, resource security, auditing, and cost. It also includes reporting, dashboards, budgets, optimizations, etc. Deliver and pitch your topic in the best possible manner with this Cost Management Dashboard In Cloud Management Platform Pictures PDF. Use them to share invaluable insights on Cost By Service, Cost Entity Summary, Storage By Department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
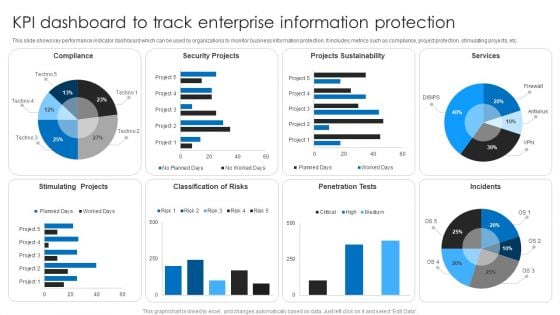
KPI Dashboard To Track Enterprise Information Protection Topics PDF
This slide shows key performance indicator dashboard which can be used by organizations to monitor business information protection. It includes metrics such as compliance, project protection, stimulating projects, etc. Showcasing this set of slides titled KPI Dashboard To Track Enterprise Information Protection Topics PDF. The topics addressed in these templates are Security Projects, Projects Sustainability, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
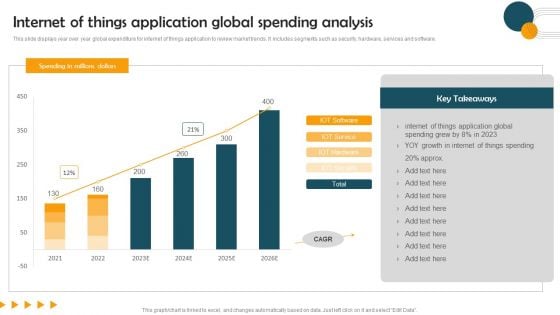
Internet Of Things Application Global Spending Analysis Guidelines PDF
This slide displays year over year global expenditure for internet of things application to review market trends. It includes segments such as security, hardware, services and software. Showcasing this set of slides titled Internet Of Things Application Global Spending Analysis Guidelines PDF. The topics addressed in these templates are Internet Of Things Application, Global Spending Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Components Of Enterprise Architecture Diagram Presentation Diagrams
This is a components of enterprise architecture diagram presentation diagrams. This is a four stage process. The stages in this process are risk and security, program management, technology driven, business driven.

Database Platform Powerpoint Slides Themes
This is a database platform powerpoint slides themes. This is a four stage process. The stages in this process are database platform, data warehouse platform, security and identity, development.
Expand Distribution Powerpoint Slide Themes
This is a expand distribution powerpoint slide themes. This is a four stage process. The stages in this process are expand distribution, executive initiatives, secure future technology leadership, optimize productivity infrastructure.

Integrating Naas Service Model What A Naas Model Should Look Like Ppt Inspiration Objects PDF
This slide depicts how a network as a service model should contain, covering hardware or equipment, flexible consumption, predictable costs about usage, managing the NaaS model from the cloud and updates and security. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating Naas Service Model What A Naas Model Should Look Like Ppt Inspiration Objects PDF can be your best option for delivering a presentation. Represent everything in detail using Integrating Naas Service Model What A Naas Model Should Look Like Ppt Inspiration Objects PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Omnichannel Services Solution In Financial Sector Factors Driving Usability Of Omnichannel Banking Elements PDF
This slide covers imperative drivers that helps in usability of omnichannel banking services. It includes factors such a multi-channel experience, ease of integration, customizable, highly secure and easy adaptability. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Omnichannel Services Solution In Financial Sector Factors Driving Usability Of Omnichannel Banking Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Omnichannel Services Solution In Financial Sector Factors Driving Usability Of Omnichannel Banking Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
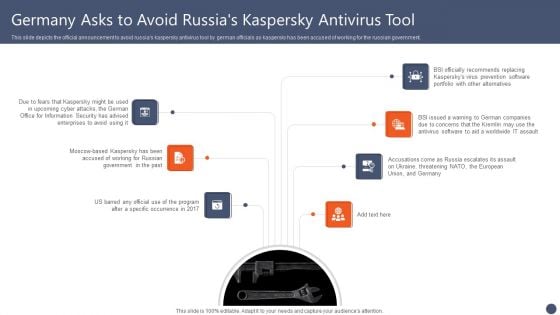
Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF
This slide depicts the official announcement to avoid russias kaspersky antivirus tool by german officials as kaspersky has been accused of working for the russian government. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF today and make your presentation stand out from the rest.

Cloud Based Computing Analysis Strategies For Every Phase Of The Cloud Journey Clipart PDF
This slide covers the strategies to overcome network complexities and increase reliability, enhanced user experience, increasing efficiency and high security. Do you know about Slidesgeeks Cloud Based Computing Analysis Strategies For Every Phase Of The Cloud Journey Clipart PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

DAD Framework Disciplined Agile Delivery Phases And Goals Ppt Model Professional PDF
This slide covers delivery phases like Inception, Construction, Transition and ongoing. Each of these phases are described by specific goals. Some goals, such as Grow Team Members and Address Risk, are applicable throughout the entire lifecycle. Deliver and pitch your topic in the best possible manner with this DAD framework disciplined agile delivery phases and goals ppt model professional pdf. Use them to share invaluable insights on develop test strategy, grow team members, produce a potentially consumable solution, secure funding, goals and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
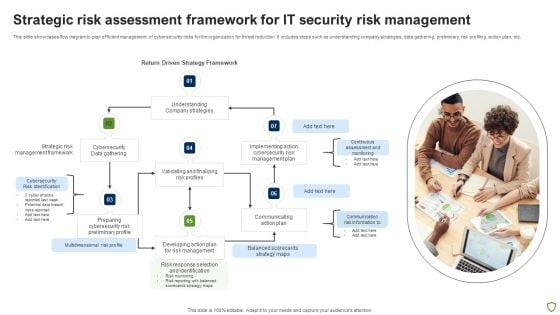
Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF
This slide showcases flow diagram to plan efficient management of cybersecurity risks for the organization for threat reduction. It includes steps such as understanding company strategies, data gathering, preliminary risk profiling, action plan, etc. Presenting Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Strategic Risk, Cybersecurity, Management Framework, Data Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
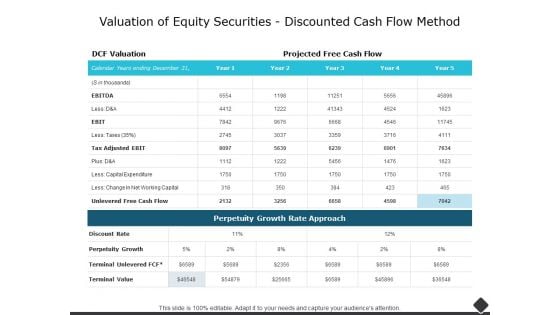
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Outline Designs
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation outline designs. The topics discussed in this diagram are business, management, marketing, compare. This is a completely editable PowerPoint presentation, and is available for immediate download.
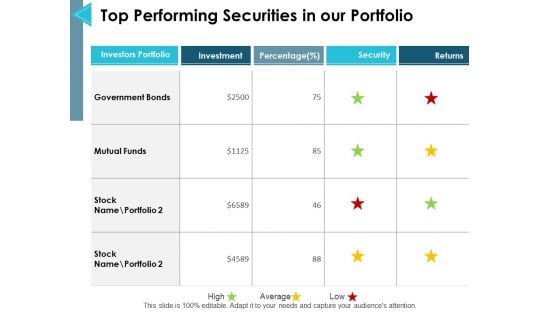
Top Performing Securities In Our Portfolio Ppt PowerPoint Presentation Ideas Slides
This is a top performing securities in our portfolio ppt powerpoint presentation ideas slides. The topics discussed in this diagram are mutual funds, management, marketing, business, strategy. This is a completely editable PowerPoint presentation and is available for immediate download.
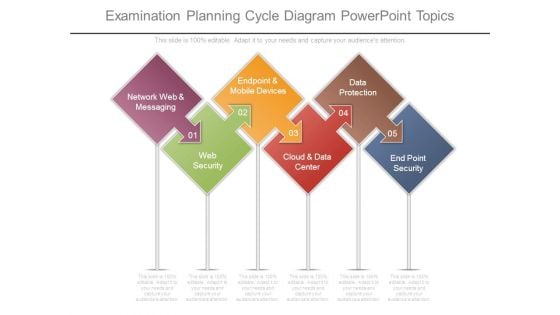
Examination Planning Cycle Diagram Powerpoint Topics
This is a examination planning cycle diagram powerpoint topics. This is a five stage process. The stages in this process are network web and messaging, web security, endpoint and mobile devices, cloud and data center, data protection, end point security.
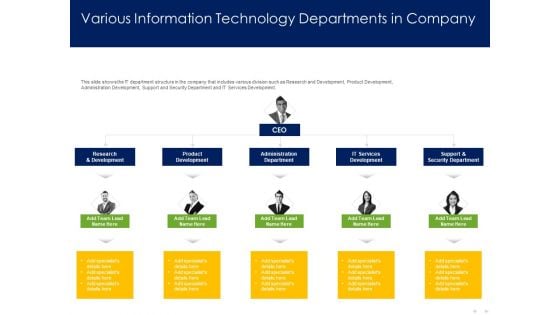
Optimizing Tasks Team Collaboration Agile Operations Various Information Technology Departments In Company Download PDF
Presenting this set of slides with name optimizing tasks team collaboration agile operations various information technology departments in company download pdf. This is a three stage process. The stages in this process are research and development, product development, administration department, it services development, support and security department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
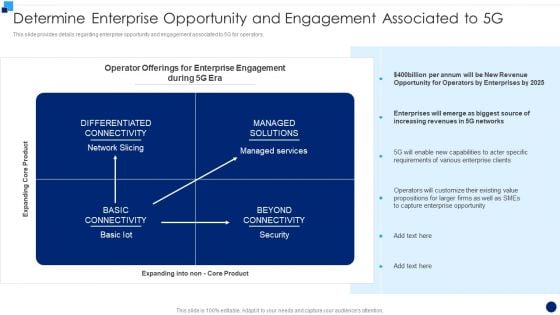
Determine Enterprise Opportunity And Engagement Associated To 5G Guidelines PDF
This slide provides details regarding enterprise opportunity and engagement associated to 5G for operators. This is a Determine Enterprise Opportunity And Engagement Associated To 5G Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Slicing, Managed Services, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
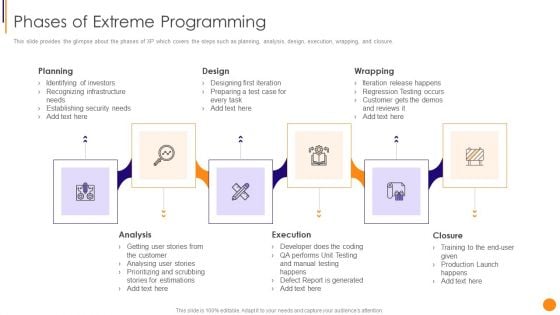
Scrum Crystal And Extreme Programming Procedure Phases Of Extreme Programming Graphics PDF
This slide provides the glimpse about the phases of XP which covers the steps such as planning, analysis, design, execution, wrapping, and closure. This is a scrum crystal and extreme programming procedure phases of extreme programming graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, infrastructure, recognizing, investors, security, prioritizing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
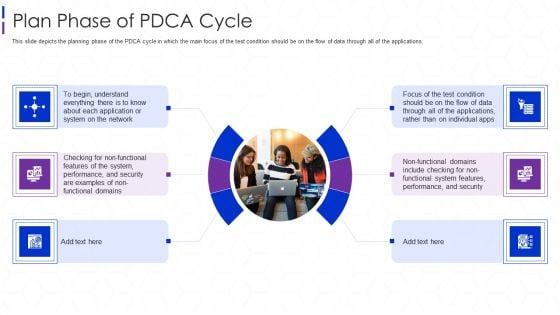
Software Interoperability Examination IT Plan Phase Of PDCA Cycle Clipart PDF
This slide depicts the planning phase of the PDCA cycle in which the main focus of the test condition should be on the flow of data through all of the applications. This is a software interoperability examination it plan phase of pdca cycle clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, system, security, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
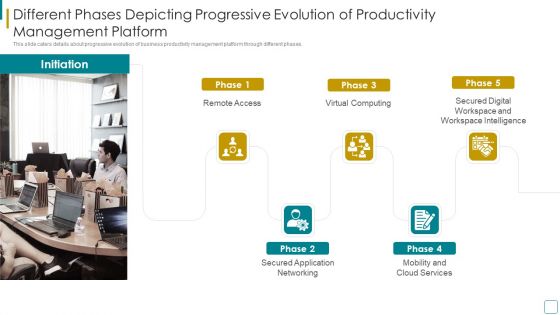
Strategic Business Efficiency Administration Tool Investor Financing Elevator Pitch Deck Different Phases Depicting Graphics PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. This is a strategic business efficiency administration tool investor financing elevator pitch deck different phases depicting graphics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like remote access, virtual computing, secured application networking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Application Development Life Cycle Phase 2 Designing The Product Architecture Template PDF
This slide depicts the designing of the product architecture phase of SDLC, including the factors documented in the DDS sheet such as risk assessment, product resilience, design flexibility, cost, etc. Presenting application development life cycle phase 2 designing the product architecture template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like overview and importance of secure sdlc. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
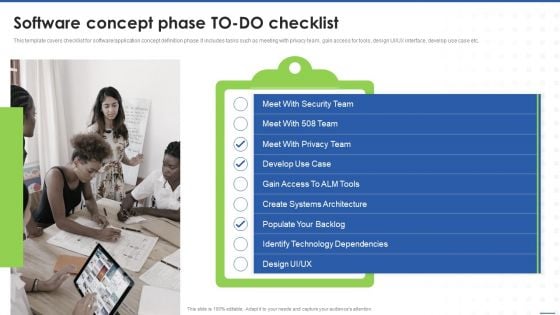
Business Software Playbook Software Concept Phase TO DO Checklist Template PDF
This template covers checklist for software or application concept definition phase. It includes tasks such as meeting with privacy team, gain access for tools, design UI or UX interface, develop use case etc.Presenting Business Software Playbook Software Concept Phase TO DO Checklist Template PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Security Team, Privacy Team, Systems Architecture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
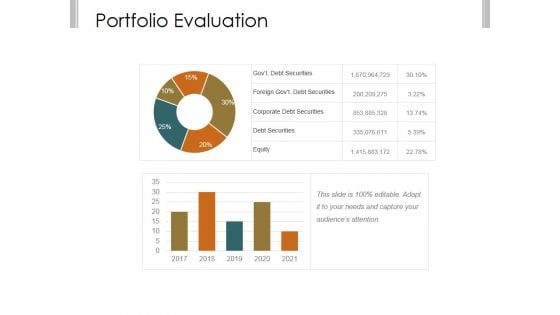
Portfolio Evaluation Ppt PowerPoint Presentation Topics
This is a portfolio evaluation ppt powerpoint presentation topics. This is a five stage process. The stages in this process are govt debt securities, foreign govt debt securities, corporate debt securities, corporate debt securities, equity.
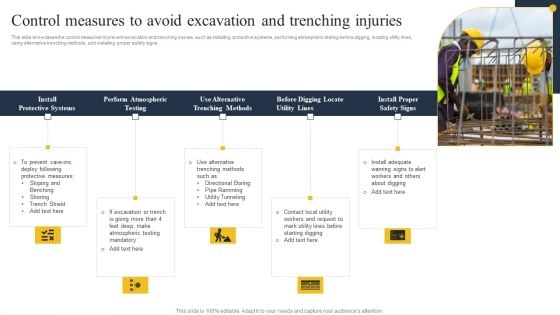
Security Control Techniques For Real Estate Project Control Measures To Avoid Excavation And Trenching Injuries Diagrams PDF
Welcome to our selection of the Security Control Techniques For Real Estate Project Control Measures To Avoid Excavation And Trenching Injuries Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Application Development Life Cycle Phase 1 Requirement Gathering And Analysis Ideas PDF
This slide represents the requirement gathering and analysis phase of the software development life cycle, including the steps taken in this stage, such as collecting needed information about the product to be made. This is a application development life cycle need of software development life cycle sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like overview and importance of secure sdlc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
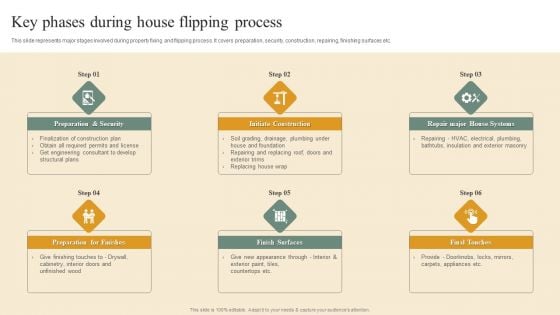
Deploying House Flipping Business Plan Key Phases During House Flipping Process Portrait PDF
This slide represents major stages involved during property fixing and flipping process. It covers preparation, security, construction, repairing, finishing surfaces etc. Present like a pro with Deploying House FlippDeploying House Flipping Business Plan Key Phases During House Flipping Process Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
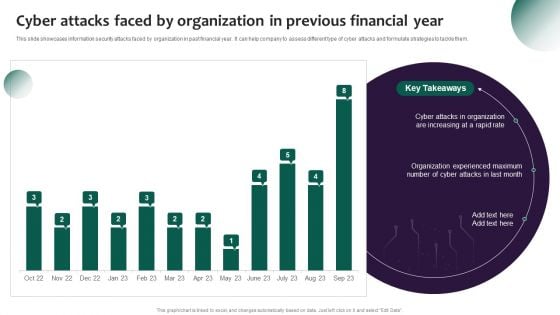
Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
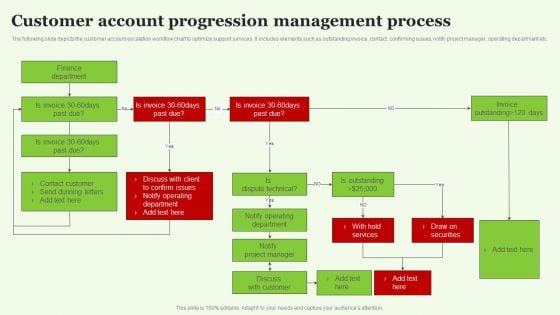
Customer Account Progression Management Process Introduction PDF
The following slide depicts the customer account escalation workflow chart to optimize support services. It includes elements such as outstanding invoice, contact, confirming issues, notify project manager, operating department etc. Presenting Customer Account Progression Management Process Introduction PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Finance Department, Notify Operating Department, Draw On Securities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Convenience Food Business Plan Ownership And Business Formation For Fast Food Restaurant Business Themes PDF
The purpose of this slide is to provide glimpse about startup ownership, legalities, etc. Deliver and pitch your topic in the best possible manner with this convenience food business plan ownership and business formation for fast food restaurant business themes pdf. Use them to share invaluable insights on ownership, business formation, start up summary, quick service foodservice, independent fine dining, furniture fixtures, liquid assets, marketable securities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
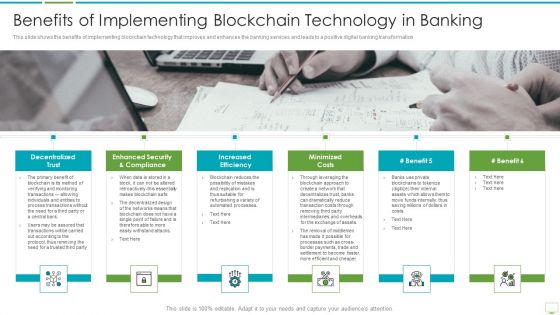
Major Advantages Of Banking Industry Revolution Benefits Of Implementing Themes PDF
This slide shows the benefits of implementing blockchain technology that improves and enhances the banking services and leads to a positive digital banking transformation.Presenting major advantages of banking industry revolution benefits of implementing themes pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like decentralized trust, enhanced security and compliance, increased efficiency In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Are you searching for a Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF from Slidegeeks today.
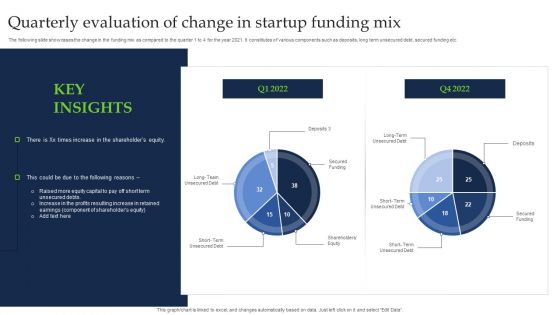
Quarterly Evaluation Of Change In Startup Funding Mix Diagrams PDF
The following slide showcases the change in the funding mix as compared to the quarter 1 to 4 for the year 2021. It constitutes of various components such as deposits, long term unsecured debt, secured funding etc. Showcasing this set of slides titled Quarterly Evaluation Of Change In Startup Funding Mix Diagrams PDF. The topics addressed in these templates are Secured Funding, Term Unsecured Debt, Shareholder Equity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
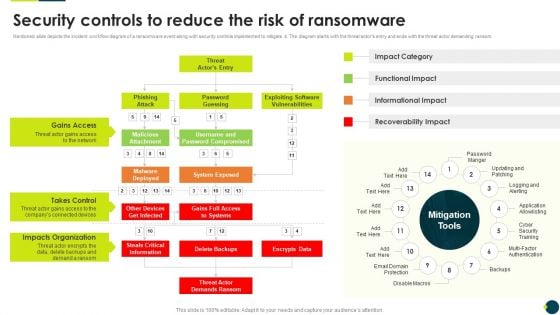
IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF bundle. Topics like Gains Access, Takes Control, Impacts Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Pros And Cons Of API Scanning CASB Deployment Ppt PowerPoint Presentation Diagram Graph Charts PDF
This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Pros And Cons Of API Scanning CASB Deployment Ppt PowerPoint Presentation Diagram Graph Charts PDF can be your best option for delivering a presentation. Represent everything in detail using Pros And Cons Of API Scanning CASB Deployment Ppt PowerPoint Presentation Diagram Graph Charts PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
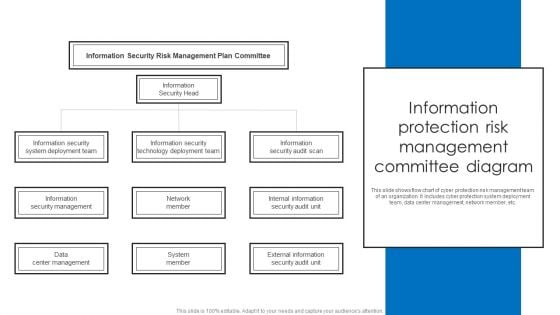
Information Protection Risk Management Committee Diagram Information PDF
This slide shows flow chart of cyber protection risk management team of an organization. It includes cyber protection system deployment team, data center management, network member, etc. Persuade your audience using this Information Protection Risk Management Committee Diagram Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security Head, Information Security Audit Scan, Network Member. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
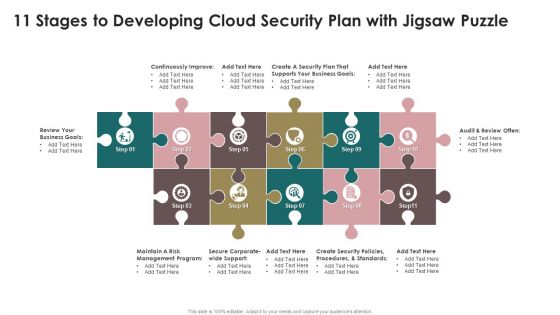
11 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Topics PDF
Presenting 11 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Topics PDF to dispense important information. This template comprises eleven stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
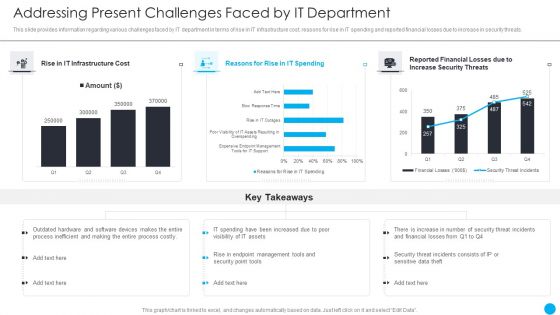
Cios Methodologies To Improve IT Spending Addressing Present Challenges Faced By It Department Themes PDF
This slide provides information regarding various challenges faced by IT department in terms of rise in IT infrastructure cost, reasons for rise in IT spending and reported financial losses due to increase in security threats. Deliver an awe inspiring pitch with this creative Cios Methodologies To Improve IT Spending Addressing Present Challenges Faced By It Department Themes PDF bundle. Topics like Infrastructure Cost, Reported Financial, Increase Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
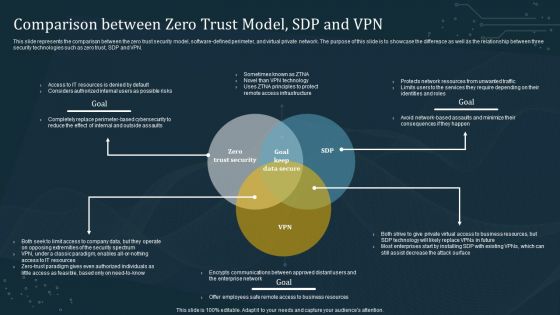
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
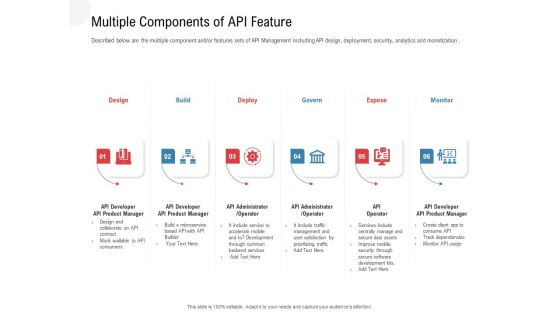
API Outline Multiple Components Of API Feature Ppt Diagram Templates PDF
Described below are the multiple component and or features sets of API Management including API design, deployment, security, analytics and monetization. This is a api outline multiple components of api feature ppt diagram templates pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like design, build, deploy, govern, expose. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
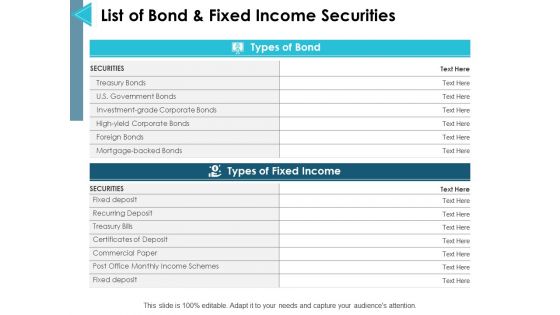
List Of Bond And Fixed Income Securities Ppt PowerPoint Presentation Layouts Graphics Design
This is a list of bond and fixed income securities ppt powerpoint presentation layouts graphics design. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.
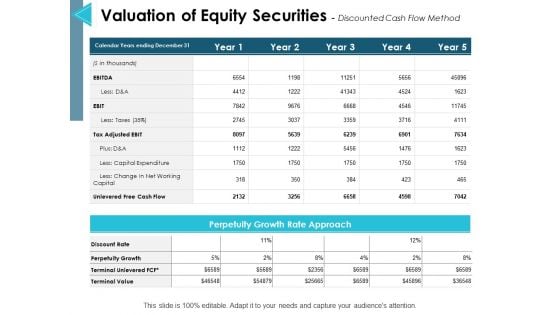
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Infographic Template Introduction
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation infographic template introduction. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.
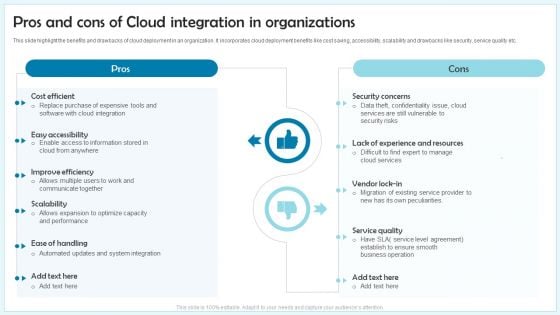
Pros And Cons Of Cloud Integration In Organizations Ppt Inspiration Sample PDF
This slide highlight the benefits and drawbacks of cloud deployment in an organization. It incorporates cloud deployment benefits like cost saving, accessibility, scalability and drawbacks like security, service quality etc. Presenting Pros And Cons Of Cloud Integration In Organizations Ppt Inspiration Sample PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Pros, Cons, Security concerns, Service quality. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
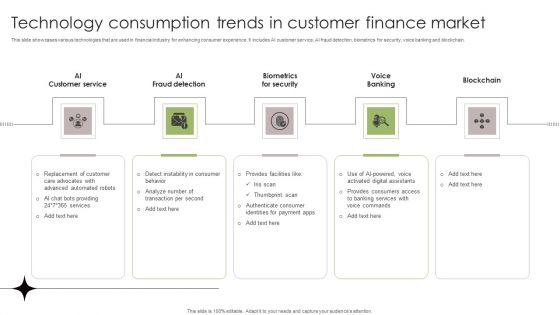
Technology Consumption Trends In Customer Finance Market Graphics PDF
This slide showcases various technologies that are used in financial industry for enhancing consumer experience. It includes AI customer service, AI fraud detection, biometrics for security, voice banking and blockchain. Presenting Technology Consumption Trends In Customer Finance Market Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Biometrics For Security, Customer Service, Blockchain. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
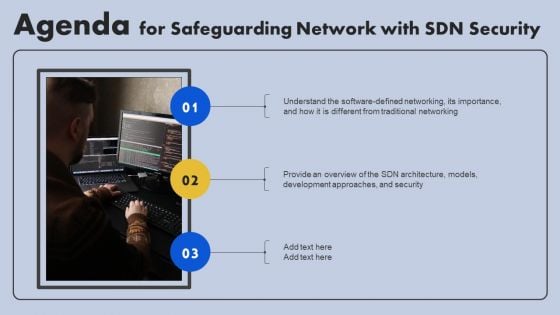
Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Arrow 5 Stages Diverging Process Diagram Circular Network PowerPoint Templates
We present our arrow 5 stages diverging process diagram Circular Network PowerPoint templates.Present our Arrows PowerPoint Templates because you can present your opinions in this field using our impressive templates. Present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download and present our Shapes PowerPoint Templates because they are Designed to attract the attention of your audience. Download our Process and Flows PowerPoint Templates because you are the star of your enlightened team. Use our Flow charts PowerPoint Templates because it helps to anticipate the doubts and questions in the minds of your colleagues and enlighten them with your inspired strategy to garner desired success.Use these PowerPoint slides for presentations relating to Arrow, green ,brochure, business, button, catalog, chart, circle, company, cross, design, diagram, direction, financial, glossy, goals,graph, green, junction, management, market, marketing, model, multicolored, multiple, navigation, network, options, orange, pie, plan, presentation, process, gray, sphere, statistics . The prominent colors used in the PowerPoint template are Green, Black, White. You can be sure our arrow 5 stages diverging process diagram Circular Network PowerPoint templates are Fantastic. Presenters tell us our catalog PowerPoint templates and PPT Slides are Gorgeous. We assure you our arrow 5 stages diverging process diagram Circular Network PowerPoint templates are Cheerful. Customers tell us our catalog PowerPoint templates and PPT Slides are Versatile. Presenters tell us our arrow 5 stages diverging process diagram Circular Network PowerPoint templates are designed by professionals You can be sure our catalog PowerPoint templates and PPT Slides are Graceful. Imagine winning it all with our Arrow 5 Stages Diverging Process Diagram Circular Network PowerPoint Templates. Download without worries with our money back guaranteee.
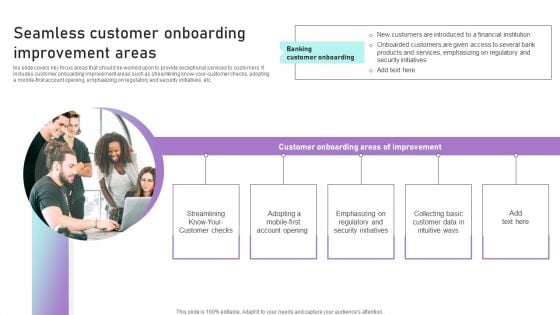
Seamless Customer Onboarding Improvement Areas Ppt Infographics Themes PDF
his slide covers key focus areas that should be worked upon to provide exceptional services to customers. It includes customer onboarding improvement areas such as streamlining know-your-customer checks, adopting a mobile-first account opening, emphasizing on regulatory and security initiatives, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Seamless Customer Onboarding Improvement Areas Ppt Infographics Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Seamless Customer Onboarding Improvement Areas Ppt Infographics Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Vector For Cloud Data Management And Security Model Ppt PowerPoint Presentation File Graphics Design PDF
Presenting vector for cloud data management and security model ppt powerpoint presentation file graphics design pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vector for cloud data management and security model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Badge Showing Sign Of Reliability Ppt PowerPoint Presentation Gallery Slide PDF
Presenting security badge showing sign of reliability ppt powerpoint presentation gallery slide pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including security badge showing sign of reliability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

3Rd Party API Integration To Check Security Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting 3rd party api integration to check security ppt powerpoint presentation gallery example topics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including check security, implementation, mission. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Computer Protected With Security System From Online Threat Ppt PowerPoint Presentation File Example Topics PDF
Presenting computer protected with security system from online threat ppt powerpoint presentation file example topics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer protected with security system from online threat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Vector Showing IT Security From Online Threat Ppt PowerPoint Presentation File Layout PDF
Presenting vector showing it security from online threat ppt powerpoint presentation file layout pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vector showing it security from online threat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Benefits Of Blockchain Technology With Enhanced Security Ppt PowerPoint Presentation Gallery Infographics PDF
Presenting benefits of blockchain technology with enhanced security ppt powerpoint presentation gallery infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including decentralised trust, enhanced security, decreased costs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Assessment By Computer Forensics Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting internet security assessment by computer forensics ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including internet security assessment by computer forensics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Four Steps Arrow For Business Data Security Process Ppt PowerPoint Presentation File Background Image PDF
Presenting four steps arrow for business data security process ppt powerpoint presentation file background image pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including four steps arrow for business data security process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Governance Plan Framework For Data Security Ppt PowerPoint Presentation Gallery Model PDF
Presenting governance plan framework for data security ppt powerpoint presentation gallery model pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including data security, data governance, physical data governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Person Using Smart Phone With Security Protection Ppt Portfolio Templates PDF
Presenting person using smart phone with security protection ppt portfolio templates pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including person using smart phone with security protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone With Various Security Features For Data Protection Ppt Outline Gallery PDF
Presenting smart phone with various security features for data protection ppt outline gallery pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including smart phone with various security features for data protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Online Security Lock To Prevent Internet Threats Ppt PowerPoint Presentation File Layouts PDF
Presenting online security lock to prevent internet threats ppt powerpoint presentation file layouts pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including online security lock to prevent internet threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Firewall Security Solutions Vector Illustration Ppt PowerPoint Presentation Gallery Professional PDF
Presenting business firewall security solutions vector illustration ppt powerpoint presentation gallery professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business firewall security solutions vector illustration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Protection With Firewall Security System Ppt PowerPoint Presentation File Pictures PDF
Presenting network protection with firewall security system ppt powerpoint presentation file pictures pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network protection with firewall security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
5 Benchmarks Visual For Mobile Security Ppt PowerPoint Presentation Gallery Tips PDF
Presenting 5 benchmarks visual for mobile security ppt powerpoint presentation gallery tips pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including 5 benchmarks visual for mobile security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
3 Groups Slide For Cloud Native Security Assessments Ppt PowerPoint Presentation File Professional PDF
Presenting 3 groups slide for cloud native security assessments ppt powerpoint presentation file professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including 3 groups slide for cloud native security assessments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparing Two Choices Visual For Teradata Security Ppt PowerPoint Presentation Gallery Topics PDF
Presenting comparing two choices visual for teradata security ppt powerpoint presentation gallery topics pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including comparing two choices visual for teradata security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Wireless Network Security System Camera Connected With Computer System Portrait PDF
Presenting wireless network security system camera connected with computer system portrait pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system camera connected with computer system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
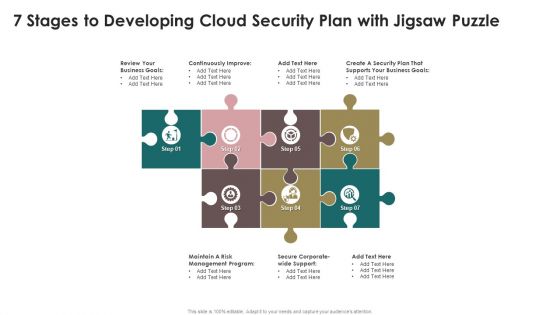
7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF
Presenting 7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
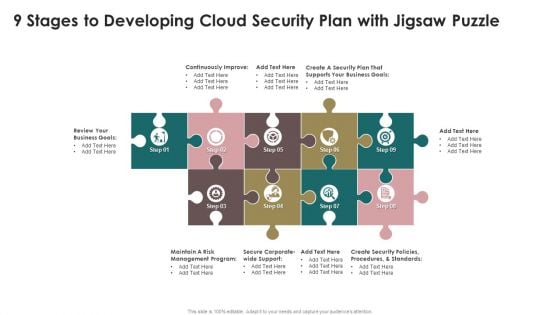
9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF
Presenting 9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Management Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
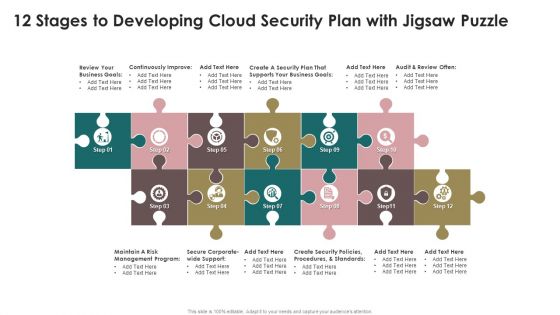
12 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Infographics PDF
Presenting 12 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Infographics PDF to dispense important information. This template comprises tweleve stages. It also presents valuable insights into the topics including Continuously Improve, Business Goals, Security Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
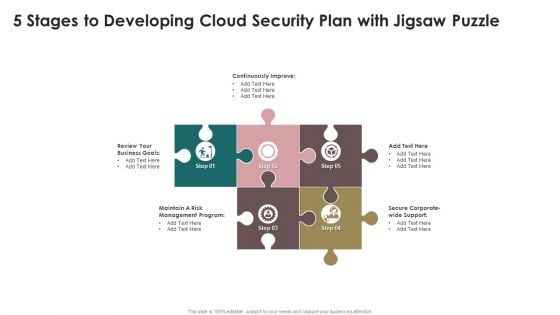
5 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Portrait PDF
Presenting 5 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Portrait PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Business Goals, Management Program, Secure Corporate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Top 5 Issues In Security Problem Management Ppt Slides Show PDF
Presenting Top 5 Issues In Security Problem Management Ppt Slides Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Lack Threat Program, No Operational Exercises, Security Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Use Of AI In Financial Institution Industry To Improve Security Mockup PDF
Presenting Use Of AI In Financial Institution Industry To Improve Security Mockup PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Financial Institution, Industry Improve Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
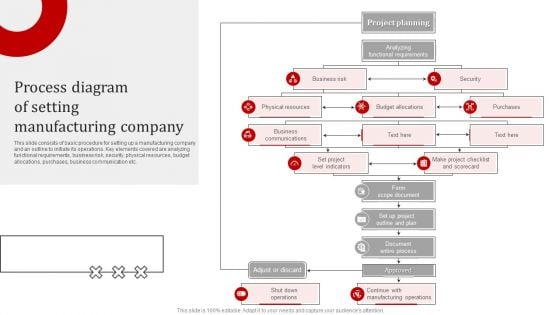
Process Diagram Of Setting Manufacturing Company Introduction PDF
This slide consists of basic procedure for setting up a manufacturing company and an outline to initiate its operations. Key elements covered are analyzing functional requirements, business risk, security, physical resources, budget allocations, purchases, business communication etc. Presenting Process Diagram Of Setting Manufacturing Company Introduction PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Business Risk, Security, Budget Allocations, Business Communications, Physical Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
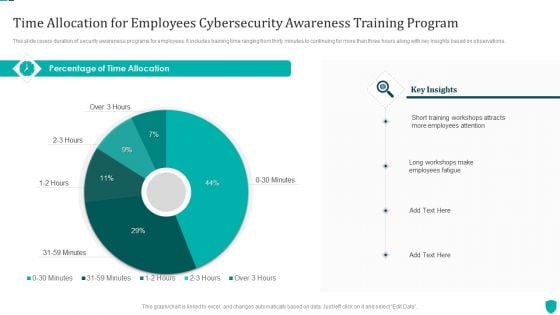
Time Allocation For Employees Cybersecurity Awareness Training Program Themes PDF
This slide covers duration of security awareness programs for employees. It includes training time ranging from thirty minutes to continuing for more than three hours along with key insights based on observations.Pitch your topic with ease and precision using this Time Allocation For Employees Cybersecurity Awareness Training Program Themes PDF. This layout presents information on Training Workshops, Employees Attention, Employees Fatigue. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
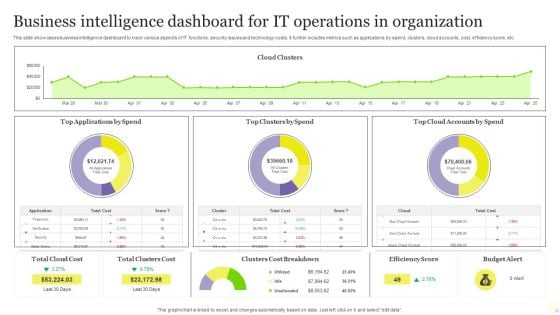
Business Intelligence Dashboard For It Operations In Organization Themes PDF
This slide showcases business intelligence dashboard to track various aspects of IT functions, security issues and technology costs. It further includes metrics such as applications by spend, clusters, cloud accounts, cost, efficiency score, etc. Showcasing this set of slides titled Business Intelligence Dashboard For It Operations In Organization Themes PDF. The topics addressed in these templates are Business Intelligence Dashboard, IT Operations, Organization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Technology Risks With Security Incident Management Ppt PowerPoint Presentation Gallery Graphics Template PDF
Presenting cloud technology risks with security incident management ppt powerpoint presentation gallery graphics template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification and allowance, management interface vulnerability, security incident management, application security management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF
This slide covers the strategies to overcome network complexities and increase reliability, enhanced user experience, increasing efficiency and high security.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF.

Synopsis For House Flipping Techniques Key Phases During House Flipping Process Ideas PDF
This slide represents major stages involved during property fixing and flipping process. It covers preparation, security, construction, repairing, finishing surfaces etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Synopsis For House Flipping Techniques Key Phases During House Flipping Process Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Synopsis For House Flipping Techniques Key Phases During House Flipping Process Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks.If you are looking for a format to display your unique thoughts, then the professionally designed Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Key Objectives Of People Centric Work Culture Security System Infographics PDF
The following slide highlights the main reasons to develop human centric security system for better security features. It mainly includes activities such as establishing secure perimeter, comprehending cause behind user actions, optimizing remote security operations etc. Presenting Key Objectives Of People Centric Work Culture Security System Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Establish Secure Perimeter, Acknowledges Potential Threats, Employee Roles. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
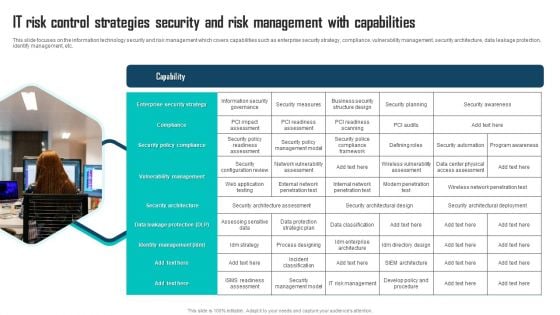
IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF
This slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Presenting IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Enterprise Security Strategy, Compliance, Security Policy Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
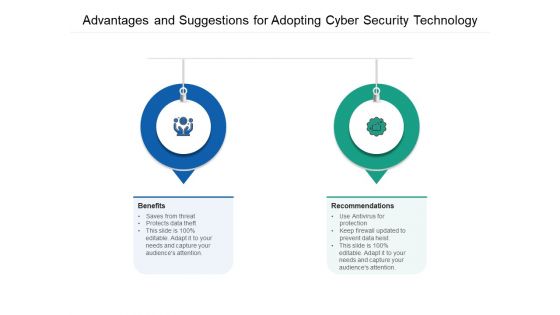
Advantages And Suggestions For Adopting Cyber Security Technology Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting advantages and suggestions for adopting cyber security technology ppt powerpoint presentation gallery example topics pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including benefits, recommendation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
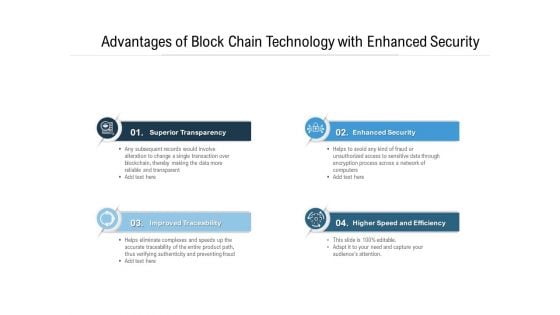
Advantages Of Block Chain Technology With Enhanced Security Ppt PowerPoint Presentation Gallery Good PDF
Presenting advantages of block chain technology with enhanced security ppt powerpoint presentation gallery good pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including transparency, traceability, efficiency. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
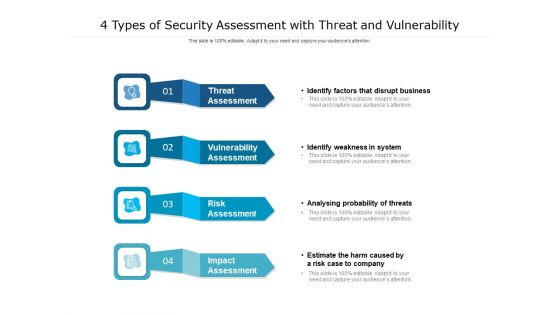
4 Types Of Security Assessment With Threat And Vulnerability Ppt PowerPoint Presentation Outline Inspiration PDF
Presenting 4 types of security assessment with threat and vulnerability ppt powerpoint presentation outline inspiration pdf. to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including risk assessment, vulnerability assessment, threat assessment, impact assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
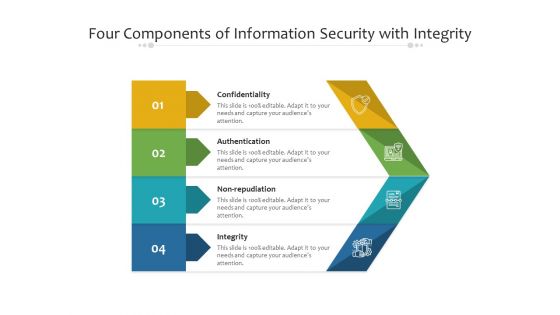
Four Components Of Information Security With Integrity Ppt PowerPoint Presentation File Gallery PDF
Presenting four components of information security with integrity ppt powerpoint presentation file gallery pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including confidentiality, authentication, integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
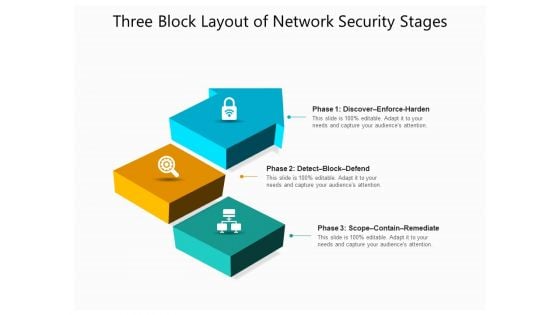
Three Block Layout Of Network Security Stages Ppt PowerPoint Presentation File Graphics Design PDF
Presenting three block layout of network security stages ppt powerpoint presentation file graphics design pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
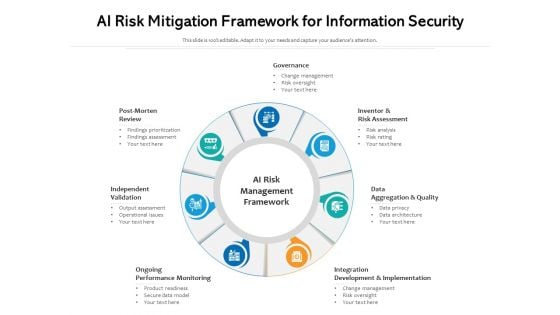
AI Risk Mitigation Framework For Information Security Ppt PowerPoint Presentation Gallery Slides PDF
Presenting ai risk mitigation framework for information security ppt powerpoint presentation gallery slides pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including governance, independent validation, ongoing performance monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
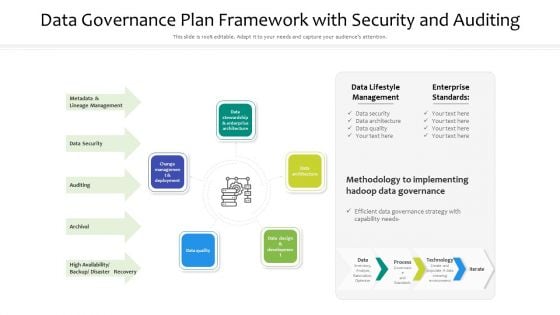
Data Governance Plan Framework With Security And Auditing Ppt PowerPoint Presentation File Template PDF
Presenting data governance plan framework with security and auditing ppt powerpoint presentation file template pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including data architecture, data quality, change management and deployment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
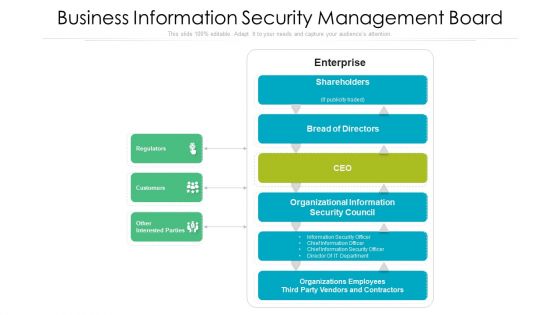
Business Information Security Management Board Ppt PowerPoint Presentation Gallery Designs Download PDF
Presenting business information security management board ppt powerpoint presentation gallery designs download pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including shareholders, enterprise, regulators. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
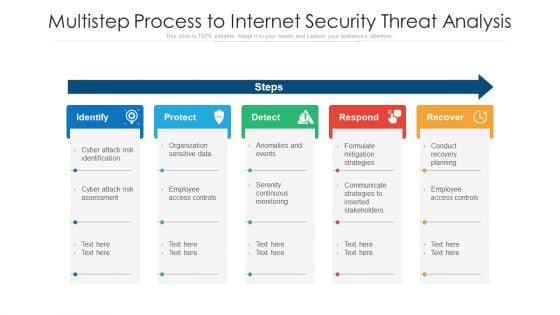
Multistep Process To Internet Security Threat Analysis Ppt PowerPoint Presentation Layouts Maker PDF
Presenting multistep process to internet security threat analysis ppt powerpoint presentation layouts maker pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identify, protect, detect, respond, recover. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
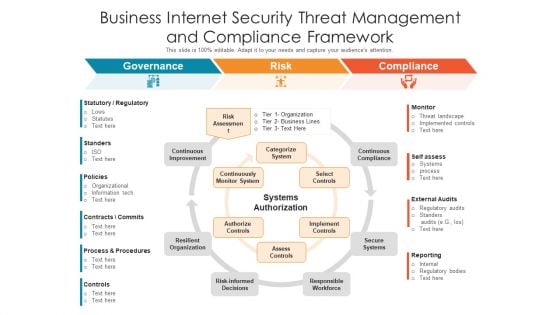
Business Internet Security Threat Management And Compliance Framework Ppt PowerPoint Presentation Gallery Picture PDF
Presenting business internet security threat management and compliance framework ppt powerpoint presentation gallery picture pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including governance, risk, compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Three Area Ppt Visual For Static Application Security Testing Sast Ppt PowerPoint Presentation File Show PDF
Presenting three area ppt visual for static application security testing sast ppt powerpoint presentation file show pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
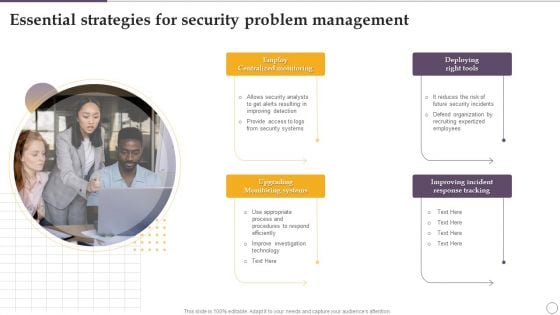
Essential Strategies For Security Problem Management Ppt Slides Infographic Template PDF
Presenting Essential Strategies For Security Problem Management Ppt Slides Infographic Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Employ Centralized Monitoring, Deploying Right Tools, Upgrading Monitoring Systems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF
Retrieve professionally designed Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
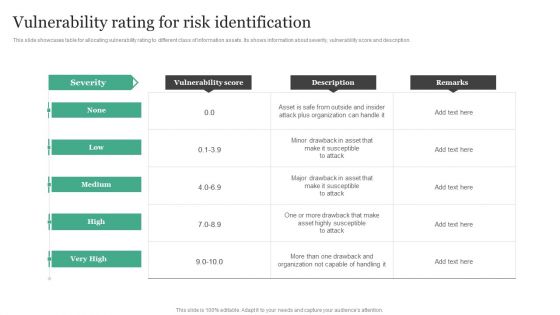
Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF
Retrieve professionally designed Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF
Retrieve professionally designed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Information Systems Security And Risk Management Plan Swot Analysis Topics PDF
Retrieve professionally designed Information Systems Security And Risk Management Plan Swot Analysis Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
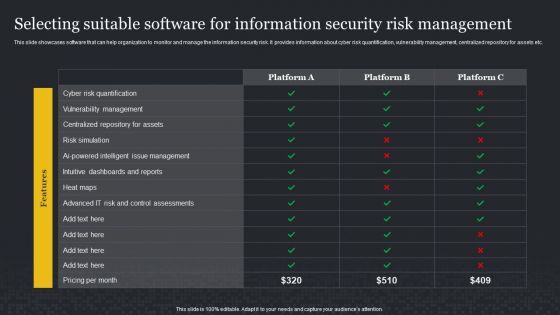
Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases software that can help organization to monitor and manage the information security risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. If you are looking for a format to display your unique thoughts, then the professionally designed Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
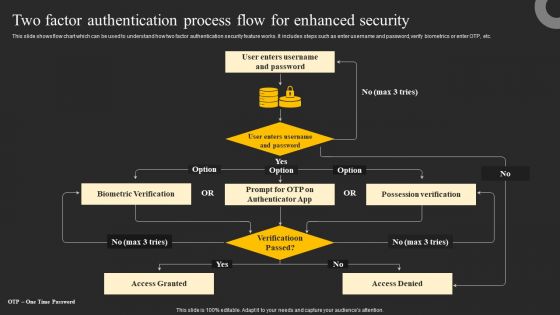
Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Explore a selection of the finest Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. If you are looking for a format to display your unique thoughts, then the professionally designed User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
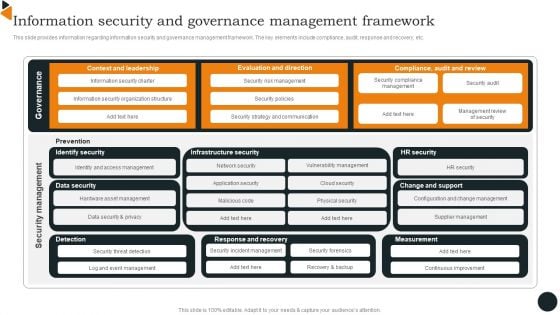
Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF
The following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Run Security Test, Planned Backup, New Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
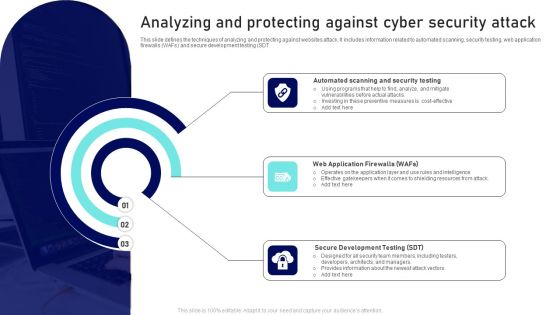
Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF
This slide defines the techniques of analyzing and protecting against websites attack. It includes information related to automated scanning, security testing, web application firewalls WAFs and secure development testing SDT. Presenting Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewalls, Secure Development Testing, Automated Scanning, Security Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
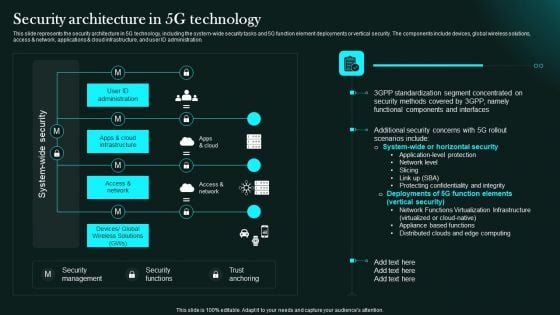
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
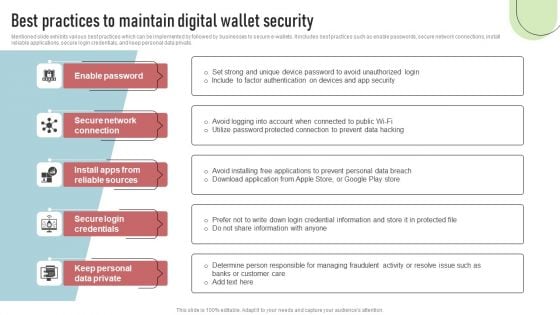
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
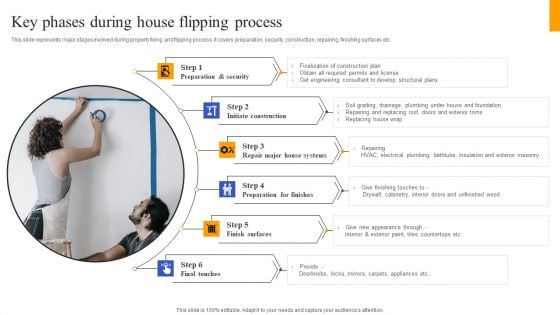
Fix And Flip Method For Renovating Real Estate Key Phases During House Flipping Process Professional PDF
This slide represents major stages involved during property fixing and flipping process. It covers preparation, security, construction, repairing, finishing surfaces etc. This modern and well arranged Fix And Flip Method For Renovating Real Estate Key Phases During House Flipping Process Professional PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
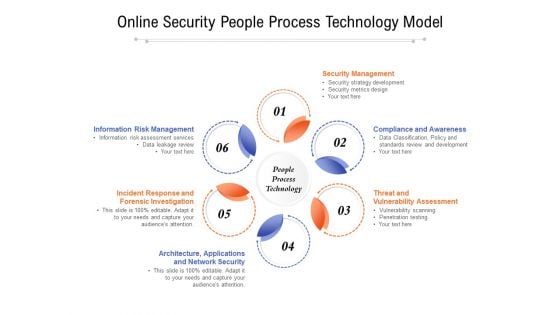
Online Security People Process Technology Model Ppt PowerPoint Presentation Slides Example Introduction PDF
Presenting online security people process technology model ppt powerpoint presentation slides example introduction pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including security management, compliance and awareness, threat and vulnerability assessment, architecture, applications, incident response and forensic investigation, information risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
RPA Operating Model With Security And Compliance Ppt PowerPoint Presentation Model Styles PDF
Presenting rpa operating model with security and compliance ppt powerpoint presentation model styles pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including strategy leadership and organizational fit, organizational enablement and change, deployment and operations, security and compliance, technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Ecosystem Plan With Security And Disability Ppt PowerPoint Presentation File Example PDF
Presenting business ecosystem plan with security and disability ppt powerpoint presentation file example pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including business friendly environment, diverse, funding source, strong support, strategic location, security and disability, digital transformation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
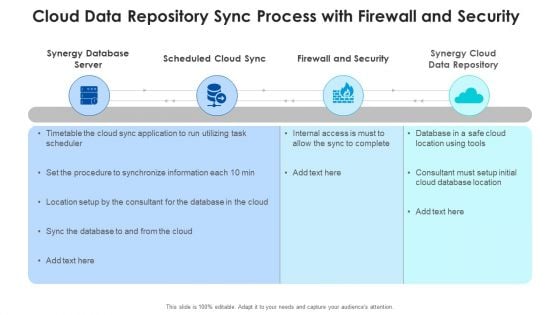
Cloud Data Repository Sync Process With Firewall And Security Brochure PDF
Presenting cloud data repository sync process with firewall and security brochure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including synergy database server, scheduled cloud sync, firewall and security, synergy cloud data repository . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
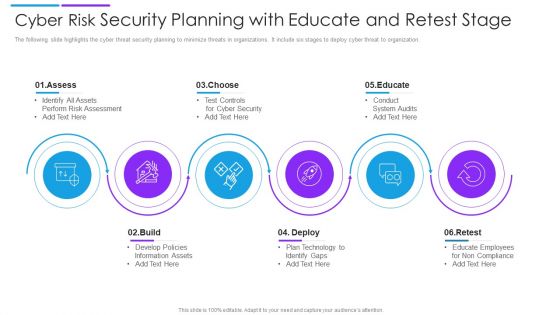
Cyber Risk Security Planning With Educate And Retest Stage Demonstration PDF
The following slide highlights the cyber threat security planning to minimize threats in organizations. It include six stages to deploy cyber threat to organization. Presenting cyber risk security planning with educate and retest stage demonstration pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including assess, choose, educate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
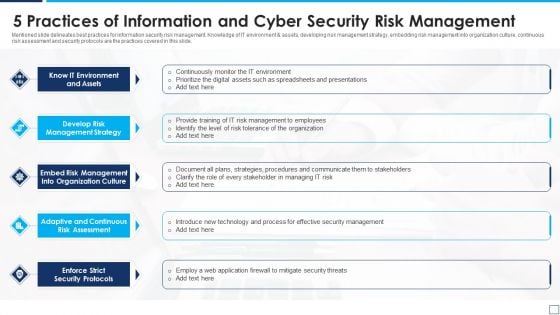
5 Practices Of Information And Cyber Security Risk Management Graphics PDF
Mentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting 5 practices of information and cyber security risk management graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including know it environment and assets, develop risk management strategy, enforce strict security protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Saas Cloud Security Challenges For IT Department Ppt PowerPoint Presentation Gallery Design Templates PDF
The following slide highlights some SaaS security challenges faced by IT team to plan mitigation actions. It mainly includes file security, insider threat, privilege access etc. Presenting Major Saas Cloud Security Challenges For It Department Ppt PowerPoint Presentation Gallery Design Templates PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including File Security, Insider Threat, Imposing Minimum, Privilege Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
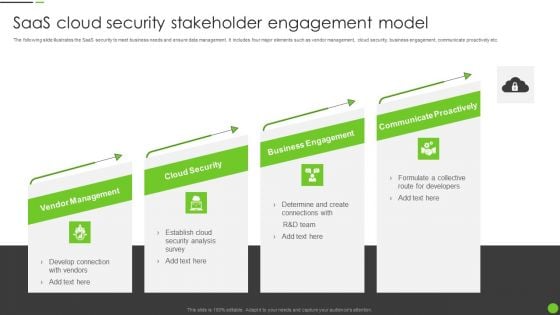
Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide illustrates the SaaS security to meet business needs and ensure data management. It includes four major elements such as vendor management, cloud security, business engagement, communicate proactively etc. Presenting Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vendor Management, Cloud Security, Business Engagement, Communicate Proactively. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
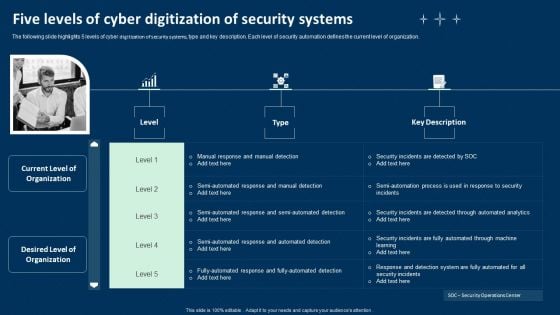
Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF
The following slide highlights 5 levels of cyber digitization of security systems, type and key description. Each level of security automation defines the current level of organization. Presenting Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF
The following slide highlights a comprehensive checklist for digitization of security systems. The checklist covers key points such as deciding the budget, selecting the right tools, deciding the tasks for automation etc. Presenting Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security Automation, Checklist, Security Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
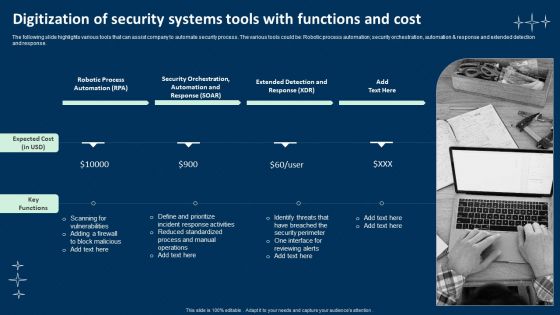
Digitization Of Security Systems Tools With Functions And Cost Mockup PDF
The following slide highlights various tools that can assist company to automate security process. The various tools could be Robotic process automation, security orchestration, automation and response and extended detection and response. Presenting Digitization Of Security Systems Tools With Functions And Cost Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Robotic Process Automation, Security Orchestration, Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
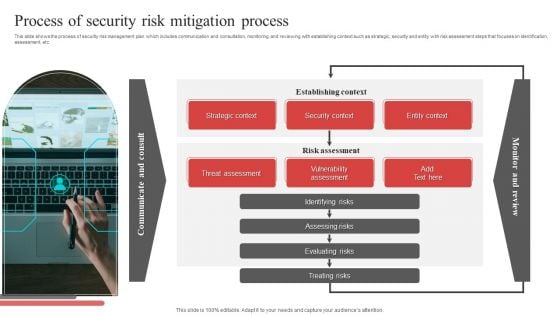
Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide shows the process of security risk management plan which includes communication and consultation, monitoring and reviewing with establishing context such as strategic, security and entity with risk assessment steps that focuses on identification, assessment, etc. Presenting Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Strategic Context, Security Context, Entity Context, Establishing Context. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
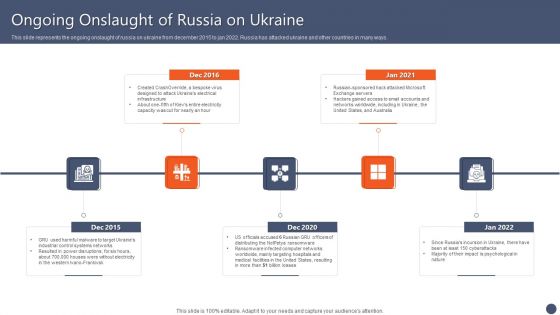
Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF
This slide represents the ongoing onslaught of russia on ukraine from december 2015 to jan 2022. Russia has attacked ukraine and other countries in many ways. If you are looking for a format to display your unique thoughts, then the professionally designed Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
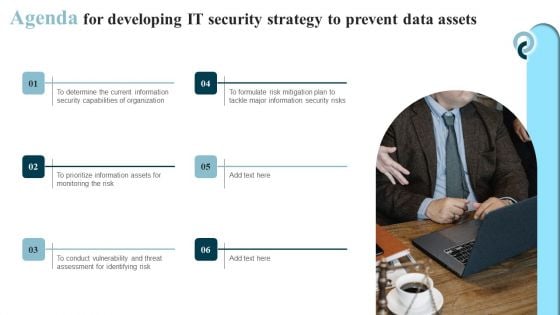
Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
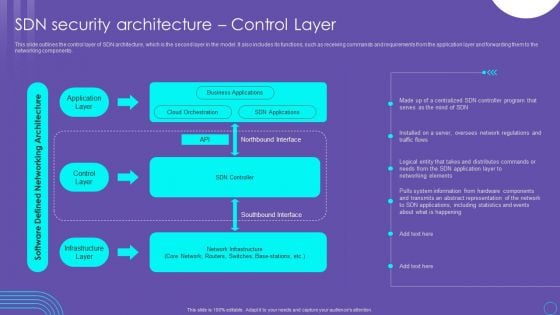
SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. If you are looking for a format to display your unique thoughts, then the professionally designed SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
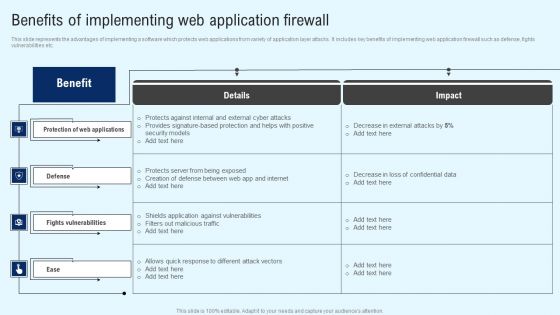
Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
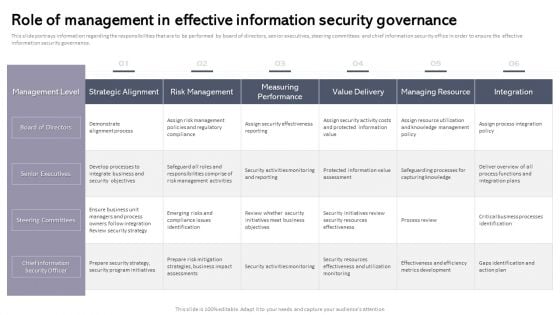
Workplace Portable Device Monitoring And Administration Role Of Management In Effective Information Security Governance Inspiration PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Retrieve professionally designed Workplace Portable Device Monitoring And Administration Role Of Management In Effective Information Security Governance Inspiration PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
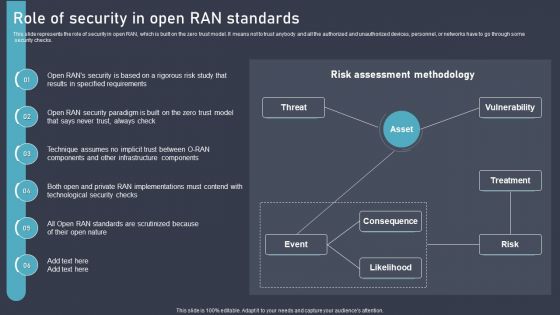
O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Retrieve professionally designed O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Recent Technologies In IT Industry Need For Cyber Security Technology Brochure PDF
This slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Retrieve professionally designed Recent Technologies In IT Industry Need For Cyber Security Technology Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
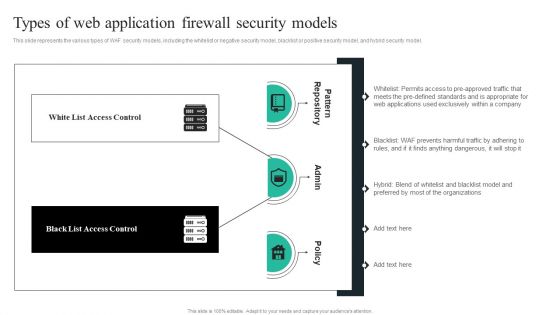
WAF Introduction Types Of Web Application Firewall Security Models Information PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Are you searching for a WAF Introduction Types Of Web Application Firewall Security Models Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download WAF Introduction Types Of Web Application Firewall Security Models Information PDF from Slidegeeks today.

IT System Risk Management Guide Table Of Contents Security Background PDF
Are you searching for a IT System Risk Management Guide Table Of Contents Security Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT System Risk Management Guide Table Of Contents Security Background PDF from Slidegeeks today.

Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF
Are you searching for a Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF from Slidegeeks today.
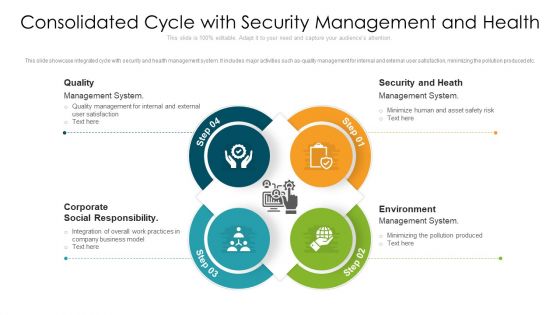
Consolidated Cycle With Security Management And Health Ppt PowerPoint Presentation File Show PDF
This slide showcase integrated cycle with security and health management system. It includes major activities such as-quality management for internal and external user satisfaction, minimizing the pollution produced etc. Presenting consolidated cycle with security management and health ppt powerpoint presentation file show pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including security and heath, corporate social responsibility, environment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
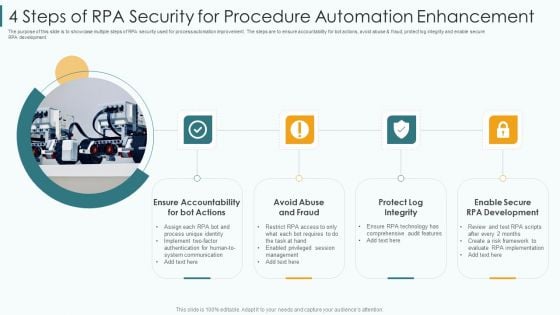
4 Steps Of RPA Security For Procedure Automation Enhancement Slides PDF
The purpose of this slide is to showcase multiple steps of RPA security used for process automation improvement. The steps are to ensure accountability for bot actions, avoid abuse and fraud, protect log integrity and enable secure RPA development. Presenting 4 steps of rpa security for procedure automation enhancement slides pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication, implement, requires. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
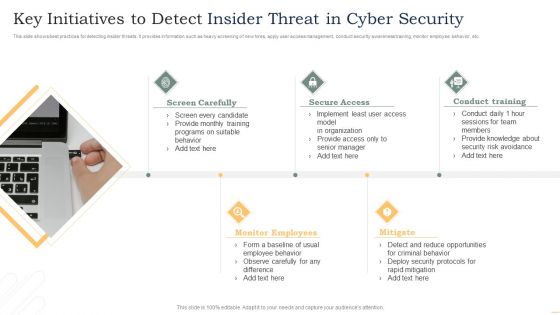
Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
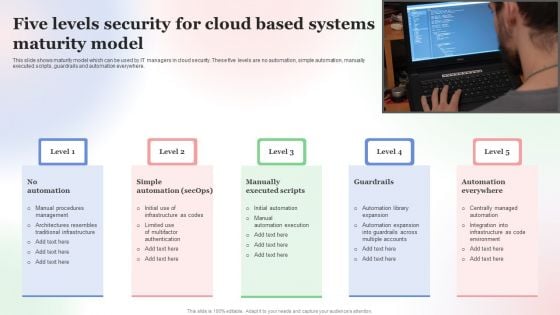
Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF
This slide shows maturity model which can be used by IT managers in cloud security. These five levels are no automation, simple automation, manually executed scripts, guardrails and automation everywhere. Presenting Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Five Levels Security, Cloud Based Systems, Maturity Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
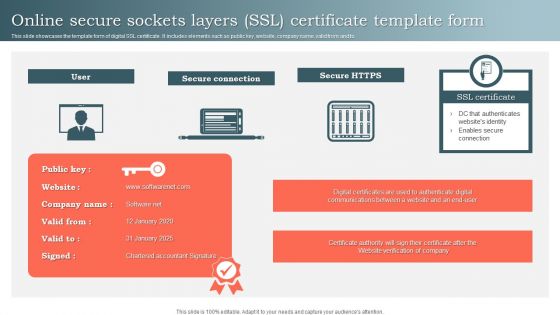
Online Secure Sockets Layers SSL Certificate Template Form Ppt Summary Examples PDF
This slide showcases the template form of digital SSL certificate. It includes elements such as public key, website, company name, valid from and to. Presenting Online Secure Sockets Layers SSL Certificate Template Form Ppt Summary Examples PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User, Secure Connection, Secure HTTPS, SSL Certificate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
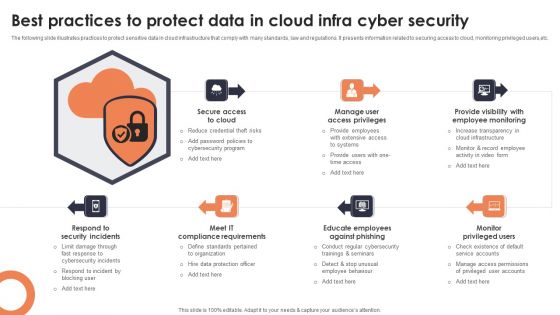
Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF
The following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users,etc. Presenting Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Secure Access Cloud, Manage User Access Privileges, Provide Visibility Employee. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
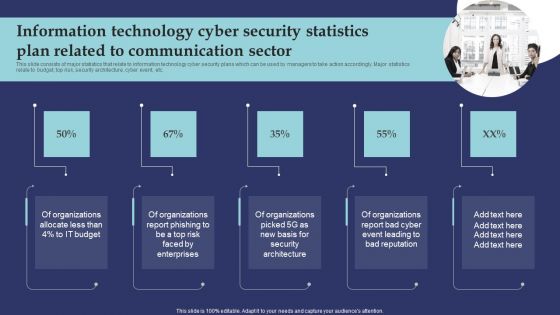
Information Technology Cyber Security Statistics Plan Related To Communication Sector Microsoft PDF
This slide consists of major statistics that relate to information technology cyber security plans which can be used by managers to take action accordingly. Major statistics relate to budget, top risk, security architecture, cyber event, etc. Presenting Information Technology Cyber Security Statistics Plan Related To Communication Sector Microsoft PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organizations Allocate, Organizations Report Phishing, Organizations Report Bad Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
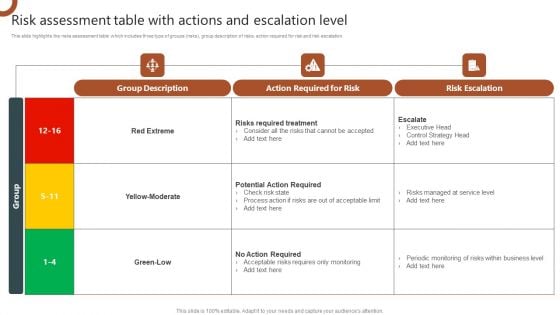
Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF
This slide highlights the risks assessment table which includes three type of groups risks, group description of risks, action required for risk and risk escalation. Retrieve professionally designed Organizations Risk Management And IT Security Technical Security Control Model With Supporting Function Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
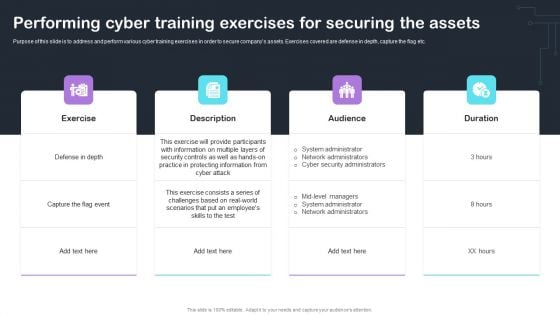
Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Retrieve professionally designed Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Retrieve professionally designed Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
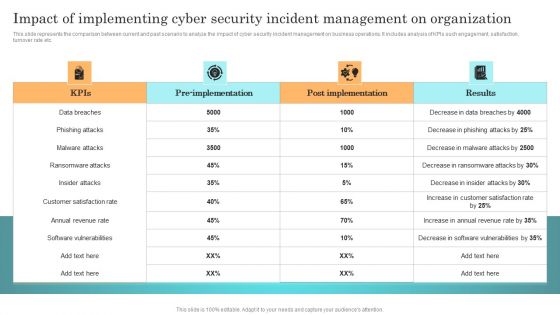
Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
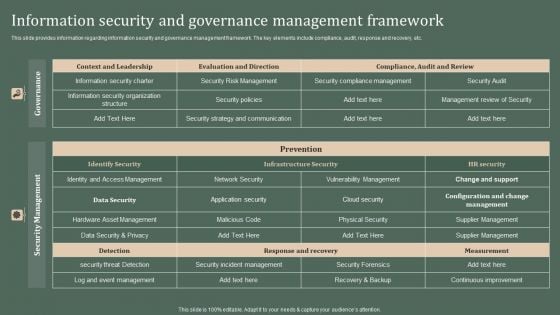
Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Retrieve professionally designed Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
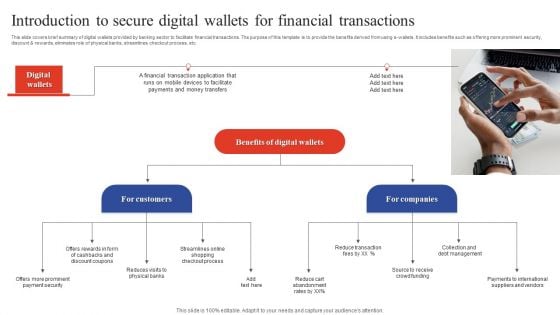
Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Retrieve professionally designed Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Advantages For IT Security In Business Ppt PowerPoint Presentation Infographic Template Microsoft PDF
Presenting advantages for it security in business ppt powerpoint presentation infographic template microsoft pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including valuable information protection, evade loss of crucial data, risk mitigation, privacy of customer and employee is ensured, recovery time is improved. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Benefits Of Information Technology Security Ppt PowerPoint Presentation Layouts Layouts PDF
Presenting benefits of information technology security ppt powerpoint presentation layouts layouts pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including evade loss of crucial data, valuable information protection, risk mitigation, recovery time is improved, privacy of customer and employee is ensured, increase productivity by avoiding website to go down. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
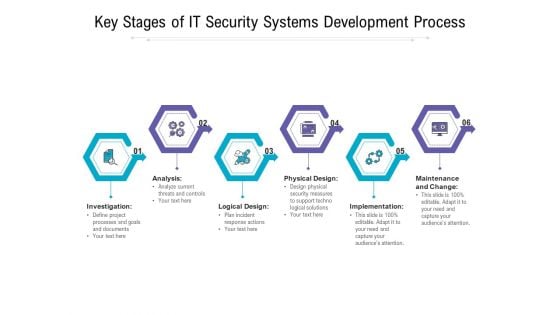
Key Stages Of IT Security Systems Development Process Ppt PowerPoint Presentation Slides Display PDF
Presenting key stages of it security systems development process ppt powerpoint presentation slides display pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including investigation, analysis, logical design, physical design, implementation, maintenance and change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
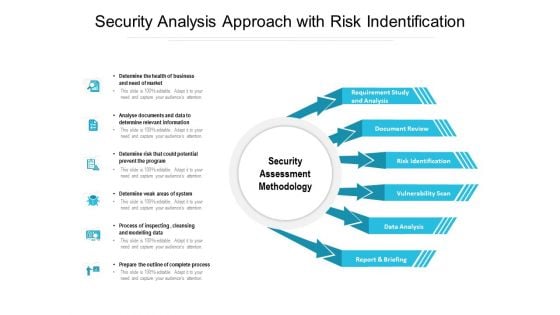
Security Analysis Approach With Risk Indentification Ppt PowerPoint Presentation Professional Gridlines PDF
Presenting security analysis approach with risk indentification ppt powerpoint presentation professional gridlines pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including analyse, of business, need of market, prevent the program, process of inspecting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
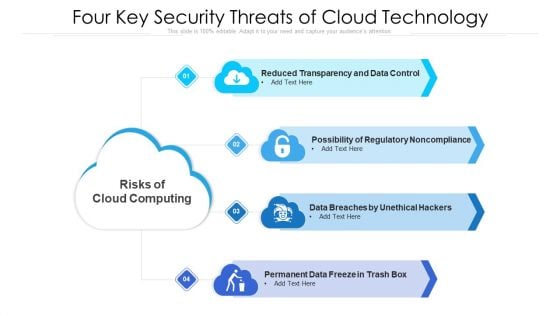
Four Key Security Threats Of Cloud Technology Ppt PowerPoint Presentation Gallery Introduction PDF
Presenting four key security threats of cloud technology ppt powerpoint presentation gallery introduction pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data breaches by unethical hackers, permanent data freeze in trash box, possibility of regulatory noncompliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
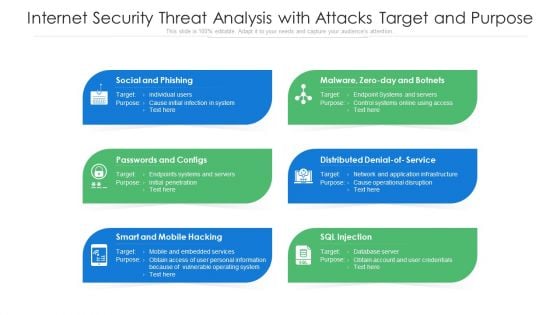
Internet Security Threat Analysis With Attacks Target And Purpose Ppt PowerPoint Presentation Pictures Structure PDF
Presenting internet security threat analysis with attacks target and purpose ppt powerpoint presentation pictures structure pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social and phishing, passwords and configs, smart and mobile hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
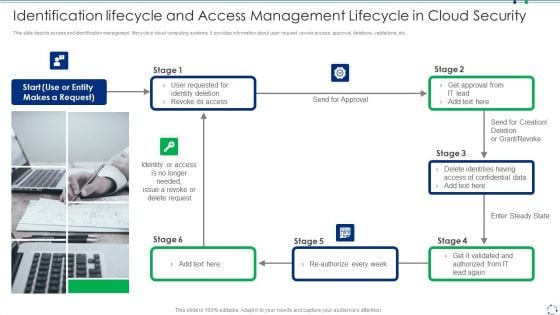
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
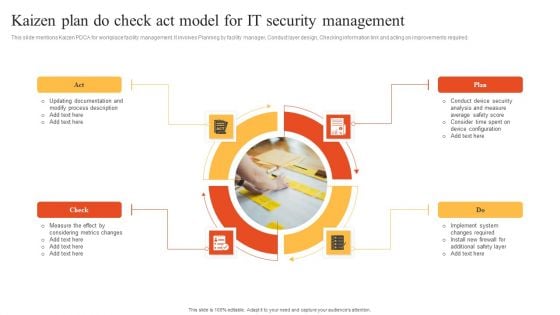
Kaizen Plan Do Check Act Model For IT Security Management Information PDF
This slide mentions Kaizen PDCA for workplace facility management. It involves Planning by facility manager, Conduct layer design, Checking information link and acting on improvements required. Presenting Kaizen Plan Do Check Act Model For IT Security Management Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Check, Plan, Act. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Critical Measures For Ensuring Business Security Ppt PowerPoint Presentation Complete Deck With Slides
Take advantage of this well-researched and professionally-designed Critical Measures For Ensuring Business Security Ppt PowerPoint Presentation Complete Deck With Slides to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the twenty slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below.

Comprehensive Guide For Ensuring IT Infrastructure Security Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Comprehensive Guide For Ensuring IT Infrastructure Security Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Enhancing Cloud Security With CASB Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Enhancing Cloud Security With CASB Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Profile Monitoring Methodology Sample Diagram Sample Ppt Presentation
This is a profile monitoring methodology sample diagram sample ppt presentation. This is a five stage process. The stages in this process are macro analysis, security screening, gaussian kernel, security screening, sector and asset class focus.
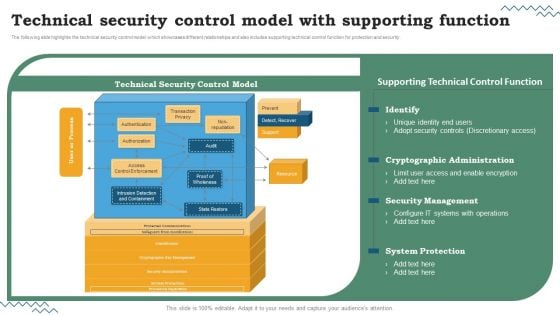
Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Are you searching for a Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF from Slidegeeks today.
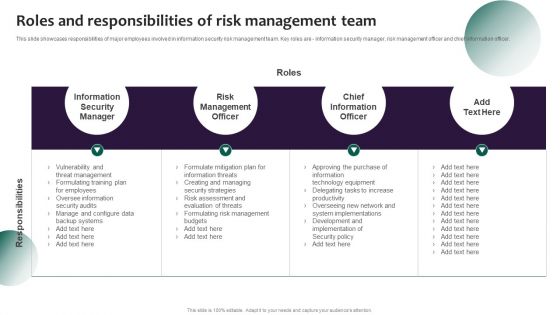
Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are - information security manager, risk management officer and chief information officer. Are you searching for a Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF from Slidegeeks today.
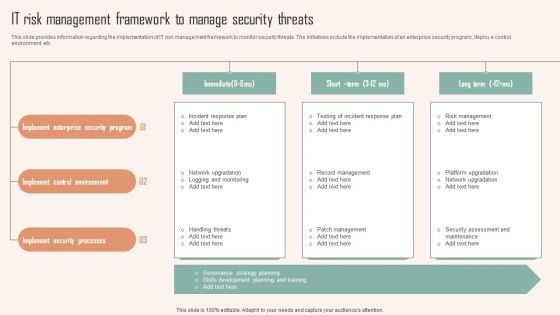
IT Risk Management Framework To Manage Security Threats Ppt PowerPoint Presentation File Outline PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Are you searching for a IT Risk Management Framework To Manage Security Threats Ppt PowerPoint Presentation File Outline PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT Risk Management Framework To Manage Security Threats Ppt PowerPoint Presentation File Outline PDF from Slidegeeks today.

Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF
This slide talks about the skills required for security operation teams. The purpose of this slide is to showcase the various skills that can help SecOps to secure an organization completely. The primary skills include no-code automation, communicating modern threats from first principles, peer influence, and so on. Are you searching for a Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF from Slidegeeks today.
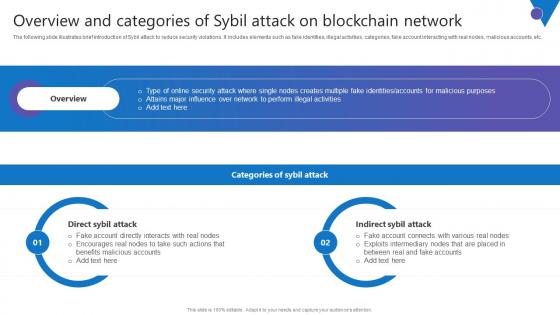
Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf
The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Are you searching for a Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf from Slidegeeks today. The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc.
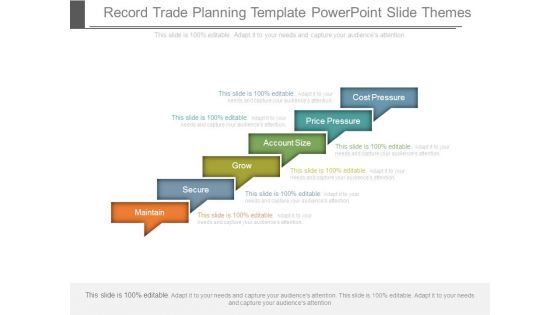
Record Trade Planning Template Powerpoint Slide Themes
This is a record trade planning template powerpoint slide themes. This is a six stage process. The stages in this process are maintain, secure, grow, account size, price pressure, cost pressure.
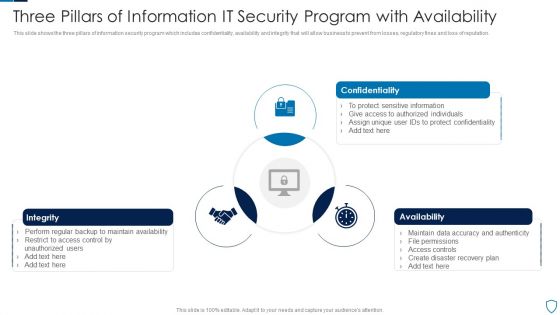
Three Pillars Of Information IT Security Program With Availability Summary PDF
This slide shows the three pillars of information security program which includes confidentiality, availability and integrity that will allow business to prevent from losses, regulatory fines and loss of reputation.Presenting Three Pillars Of Information IT Security Program With Availability Summary PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Confidentiality, Integrity, Availability This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
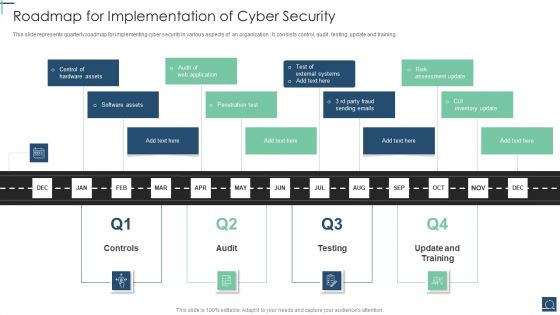
Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Penetration Test, Software Assets, Control Hardware Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
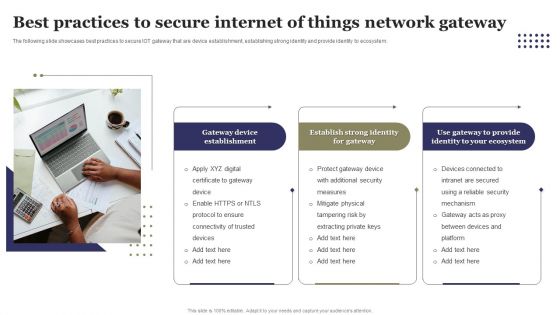
Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF
The following slide showcases best practices to secure IOT gateway that are device establishment, establishing strong identity and provide identity to ecosystem. Presenting Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Performance Metrics For Project Management Office, Requirement Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF
This This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting 6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prioritize, Evaluate, Analyse, Treat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
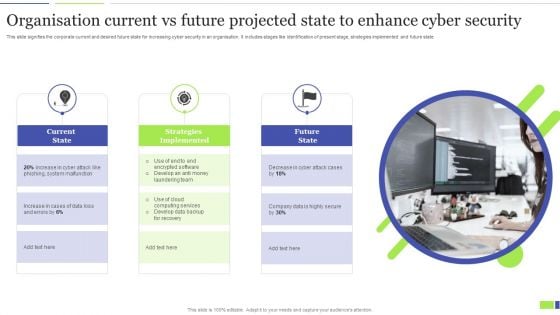
Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF
This slide signifies the corporate current and desired future state for increasing cyber security in an organisation. It includes stages like identification of present stage, strategies implemented and future state. Presenting Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Current State, Strategies Implemented, Future State. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security KPI With Measures Taken By The Company Formats PDF
This slide covers the KPIs of the company used for the security of data or privacy of the customers or businesss own confidential information. It also includes the things that is to be covered under each KPI. Some of them are NHT, days to patch, intrusion attempts ,etc. Presenting Information Technology Security KPI With Measures Taken By The Company Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Key Performance Indicators, Measures Taken, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Governance Risk And Compliance Implementation Process To Manage Security Risks Pictures PDF
Mentioned slide outlines 3 step process of governance, risk and compliance GRC. Information covered in this slide is related to governance, risk management and compliance which will assist organization to successfully mitigate IT and security risks. Presenting Governance Risk And Compliance Implementation Process To Manage Security Risks Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Governance, Risk Management, Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home