Safety Icons
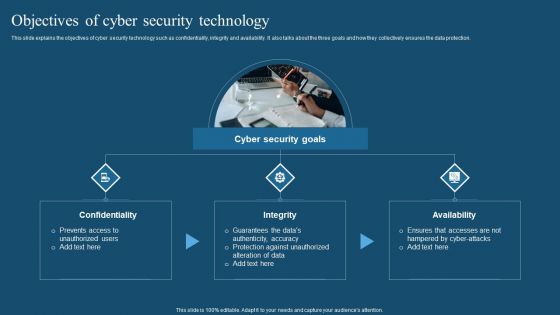
Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Checklist For Technological Smart Homes Devices And Firewall Security Microsoft PDF
This side showcase the checklist of working condition and firewall security of smart home to know updates of standard devices and their benchmarks. It includes status of devices such as garage locks, remote access, data sharing, door openers, policies of devices and update cycle. Presenting Checklist For Technological Smart Homes Devices And Firewall Security Microsoft PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Devices Firewall, Working Condition, Access Points. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Securing Market Leadership Through Competitive Excellence Table Of Contents Portrait PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Securing Market Leadership Through Competitive Excellence Table Of Contents Portrait PDF can be your best option for delivering a presentation. Represent everything in detail using Securing Market Leadership Through Competitive Excellence Table Of Contents Portrait PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
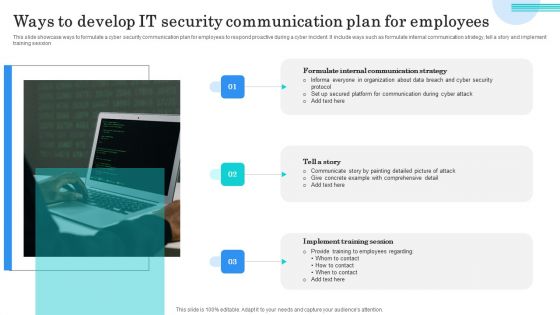
Ways To Develop IT Security Communication Plan For Employees Elements PDF
This slide showcase ways to formulate a cyber security communication plan for employees to respond proactive during a cyber incident. It include ways such as formulate internal communication strategy, tell a story and implement training session. Presenting Ways To Develop IT Security Communication Plan For Employees Elements PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Formulate Internal Communication, Tell Story, Implement Training Session. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF
This slide consists of a communication plan information technology security to be deployed by managers based on the type of audience. Key elements include communication, frequency, communication goal, owner, etc. Presenting Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Project Status Report, Team Standup, Task Progress Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
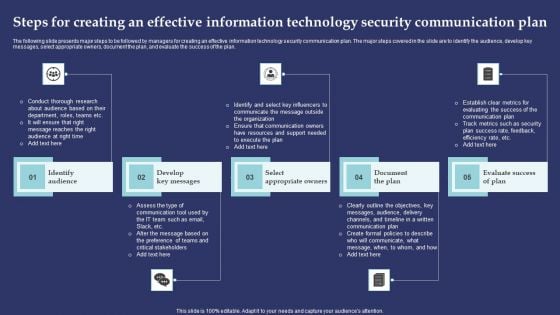
Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF
The following slide presents major steps to be followed by managers for creating an effective information technology security communication plan. The major steps covered in the slide are to identify the audience, develop key messages, select appropriate owners, document the plan, and evaluate the success of the plan. Presenting Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Audience, Develop Key Messages, Select Appropriate Owners. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.m
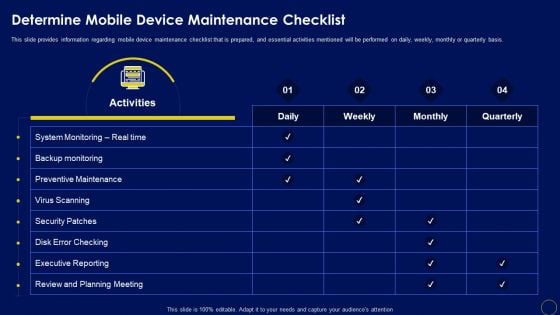
Determine Mobile Device Maintenance Checklist Business Mobile Device Security Management Professional PDF
This slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Retrieve professionally designed Determine Mobile Device Maintenance Checklist Business Mobile Device Security Management Professional PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
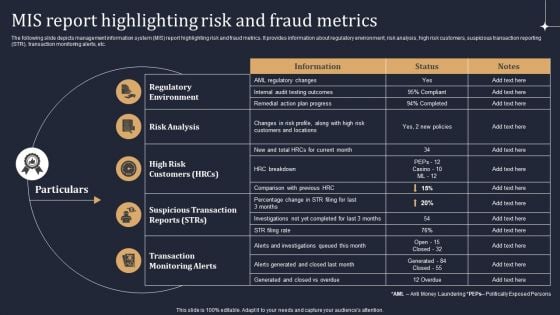
KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF
The following slide depicts management information system MIS report highlighting risk and fraud metrics. It provides information about regulatory environment, risk analysis, high risk customers, suspicious transaction reporting STR, transaction monitoring alerts, etc. Retrieve professionally designed KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
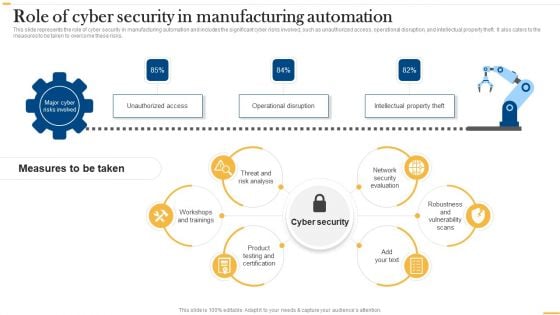
Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Are you searching for a Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF from Slidegeeks today.
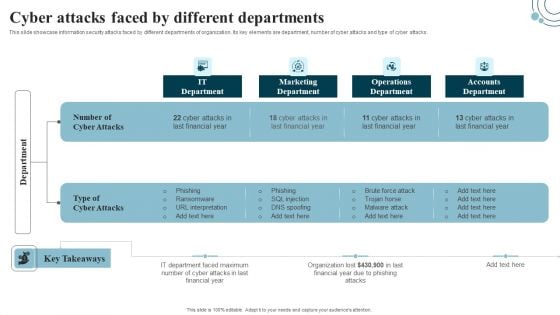
Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF from Slidegeeks today.

SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF
This slide depicts the importance of software defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Are you searching for a SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF from Slidegeeks today.
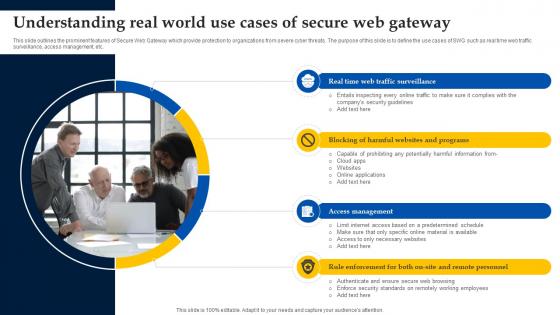
Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.
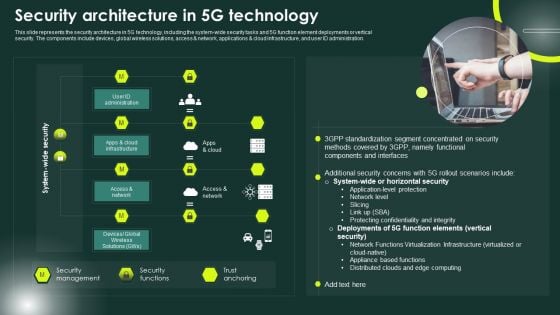
5G Network Applications And Features Security Architecture In 5G Technology Elements PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF can be your best option for delivering a presentation. Represent everything in detail using 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
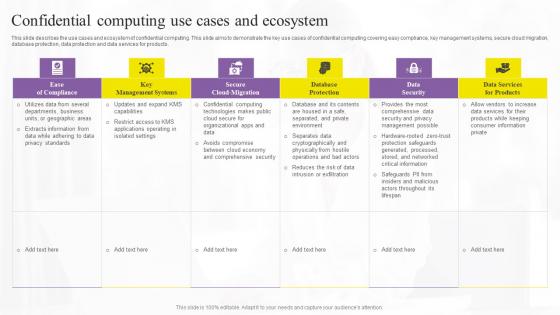
Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Slidegeeks has constructed Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.

Key Takeaways And Strategic Port Terminal Industry Ppt PowerPoint
The purpose of this slide is to provide a brief insights related to the ports market and its growth. It covers opportunity protection, macro and geopolitical insights related to the insurers, and demand for cyber security ports and services analysis.Explore a selection of the finest Key Takeaways And Strategic Port Terminal Industry Ppt PowerPoint here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Takeaways And Strategic Port Terminal Industry Ppt PowerPoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The purpose of this slide is to provide a brief insights related to the ports market and its growth. It covers opportunity protection, macro and geopolitical insights related to the insurers, and demand for cyber security ports and services analysis.
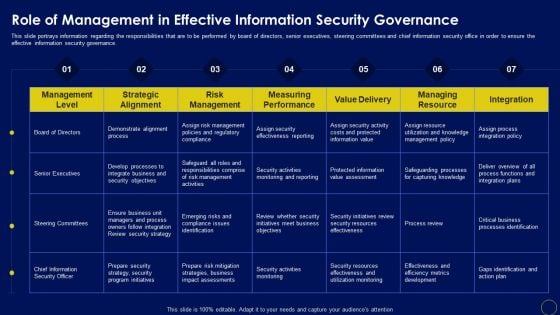
Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF can be your best option for delivering a presentation. Represent everything in detail using Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
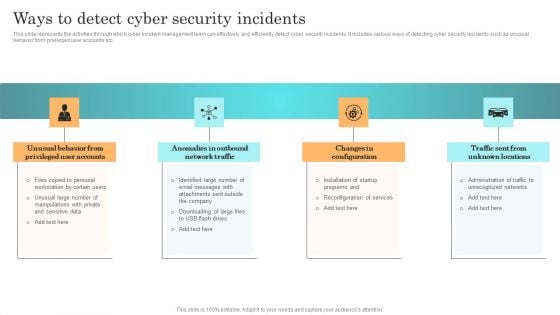
Incident Response Techniques Deployement Ways To Detect Cyber Security Incidents Infographics PDF
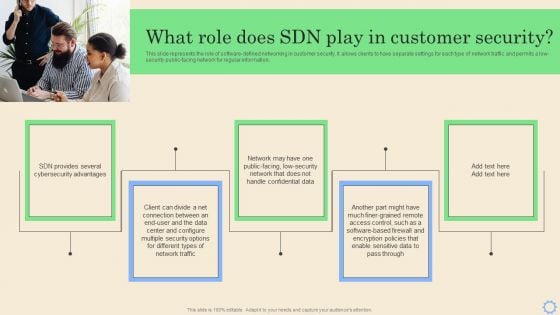
Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
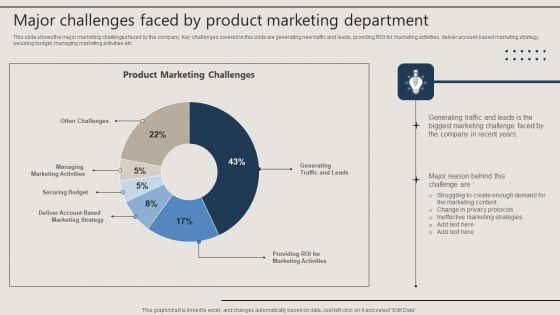
Major Challenges Faced By Product Marketing Department Themes PDF
This slide shows the major marketing challenges faced by the company. Key challenges covered in this slide are generating new traffic and leads, providing ROI for marketing activities, deliver account-based marketing strategy, securing budget, managing marketing activities etc. Presenting this PowerPoint presentation, titled Major Challenges Faced By Product Marketing Department Themes PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Challenges Faced By Product Marketing Department Themes PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Challenges Faced By Product Marketing Department Themes PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
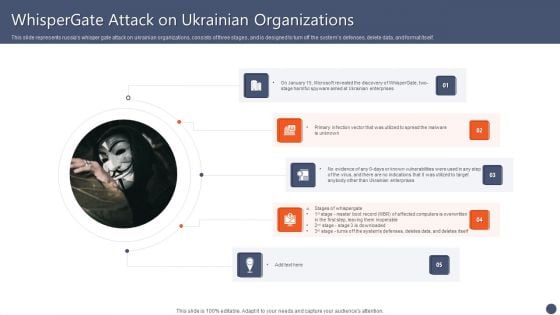
Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF
This slide represents russias whisper gate attack on ukrainian organizations, consists of three stages, and is designed to turn off the systems defenses, delete data, and format itself. Are you searching for a Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF from Slidegeeks today.

Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets.Are you searching for a Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF from Slidegeeks today.
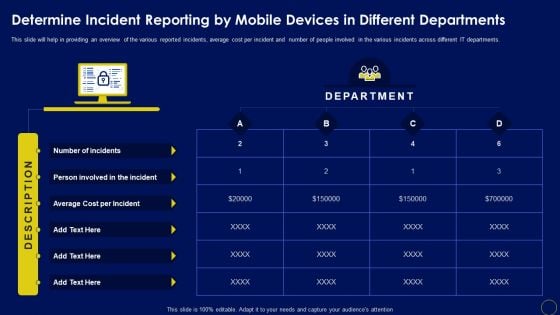
Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different IT departments. Are you searching for a Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF from Slidegeeks today.
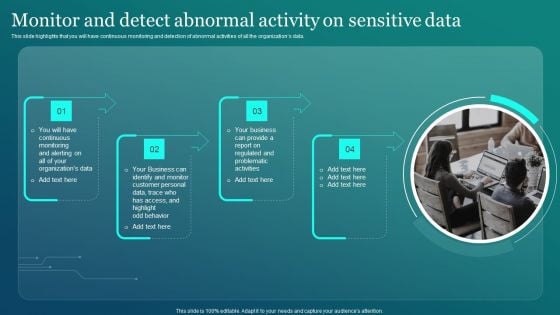
Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Are you searching for a Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF from Slidegeeks today.
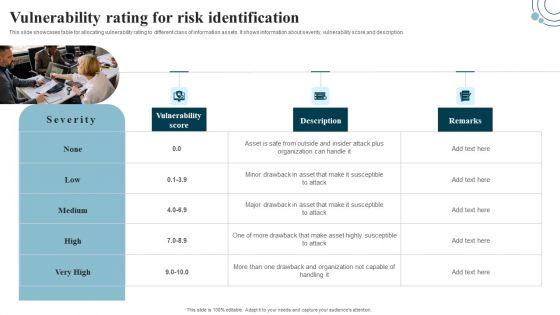
Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Are you searching for a Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF from Slidegeeks today.
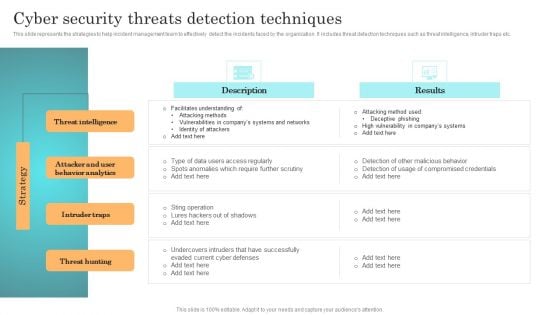
Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.
Mutual Fund Marketing Diagram Powerpoint Slide Designs
This is a mutual fund marketing diagram powerpoint slide designs. This is a four stage process. The stages in this process are returns, investors, fund, securities.
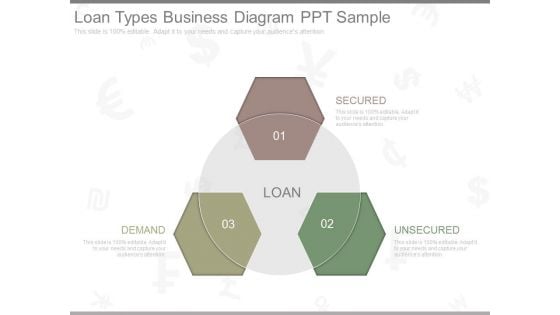
Loan Types Business Diagram Ppt Sample
This is a loan types business diagram ppt sample. This is a three stage process. The stages in this process are loan, secured, unsecured, demand.
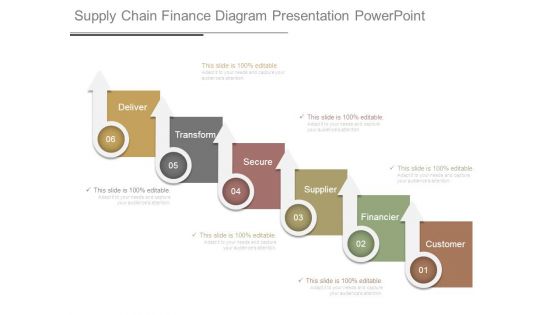
Supply Chain Finance Diagram Presentation Powerpoint
This is a supply chain finance diagram presentation powerpoint. This is a six stage process. The stages in this process are deliver, transform, secure, supplier, financier, customer.

Interaction Process Automation Reviews Diagram Ppt Slide
This is a interaction process automation reviews diagram ppt slide. This is a three stage process. The stages in this process are security, performance, the contact center.
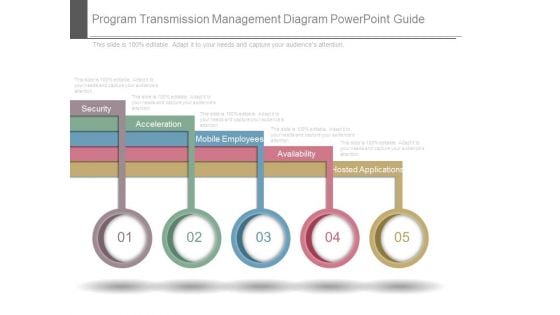
Program Transmission Management Diagram Powerpoint Guide
This is a program transmission management diagram powerpoint guide. This is a five stage process. The stages in this process are security, acceleration, mobile employees, availability, hosted applications.

Personal Liability Policy Diagram Presentation Images
This is a personal liability policy diagram presentation images. This is a five stage process. The stages in this process are protection, insurance, security, liability, planning.

Business Operating Costs Diagram Ppt Files
This is a business operating costs diagram ppt files. This is a five stage process. The stages in this process are taxes, insurance, utilities, security, supplies.

Outsourcing Workflow Development Diagram Ppt Examples Professional
This is a outsourcing workflow development diagram ppt examples professional. This is a six stage process. The stages in this process are outsourcing, business, finance, messenger, security, relationship.
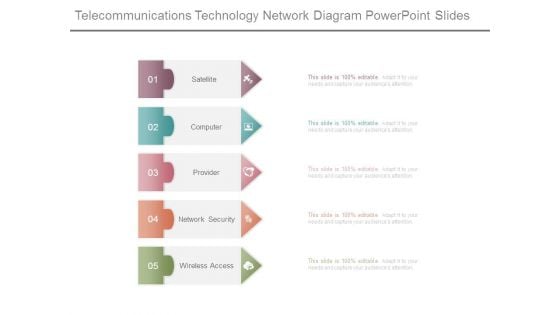
Telecommunications Technology Network Diagram Powerpoint Slides
This is a telecommunications technology network diagram powerpoint slides. This is a five stage process. The stages in this process are satellite, computer, provider, network security, wireless access.
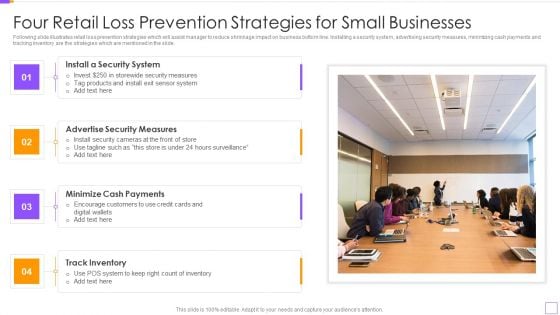
Four Retail Loss Prevention Strategies For Small Businesses Themes PDF
Following slide illustrates retail loss prevention strategies which will assist manager to reduce shrinkage impact on business bottom line. Installing a security system, advertising security measures, minimizing cash payments and tracking inventory are the strategies which are mentioned in the slide. Persuade your audience using this Four Retail Loss Prevention Strategies For Small Businesses Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Install A Security System, Advertise Security Measures, Minimize Cash Payments, Track Inventory. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
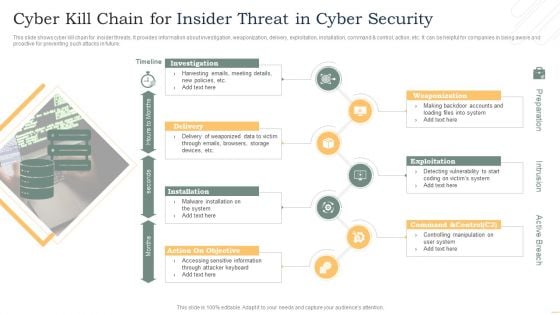
Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
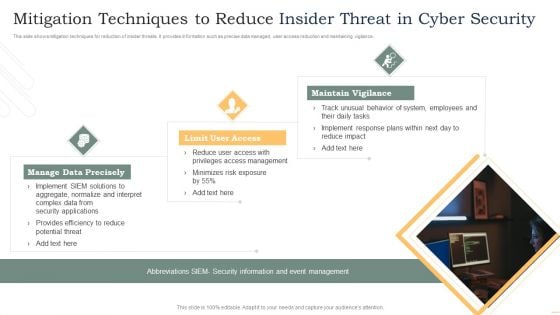
Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
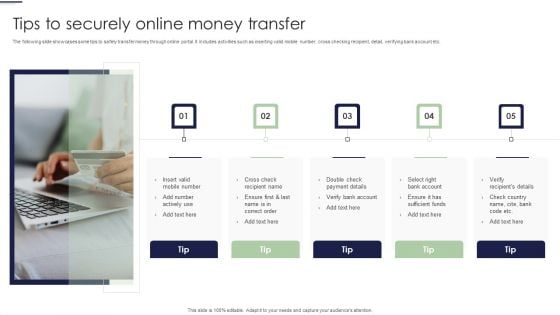
Tips To Securely Online Money Transfer Ppt PowerPoint Presentation File Visual Aids PDF
The following slide showcases some tips to safely transfer money through online portal. It includes activities such as inserting valid mobile number, cross checking recipient, detail, verifying bank account etc. Presenting Tips To Securely Online Money Transfer Ppt PowerPoint Presentation File Visual Aids PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Select Right, Bank Account, Verify Recipients Details. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
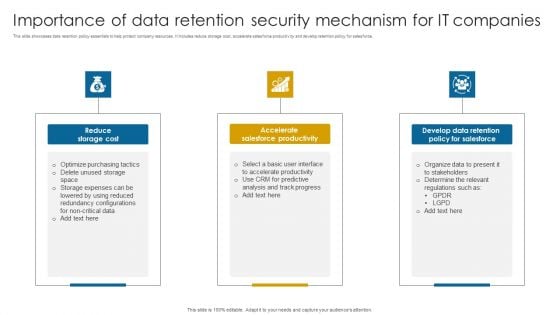
Importance Of Data Retention Security Mechanism For It Companies Professional PDF
This slide showcases data retention policy essentials to help protect company resources. It includes reduce storage cost, accelerate salesforce productivity and develop retention policy for salesforce.Presenting Importance Of Data Retention Security Mechanism For It Companies Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Salesforce Productivity, Develop Data Retention, Determine Relevant. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
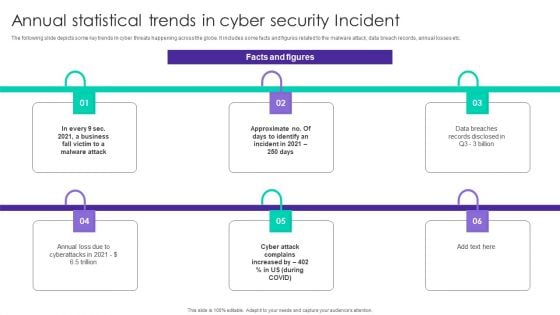
Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF
The following slide depicts some key trends in cyber threats happening across the globe. It includes some facts and figures related to the malware attack, data breach records, annual losses etc. Presenting Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Malware Attack, Business Fall, Data Breaches. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
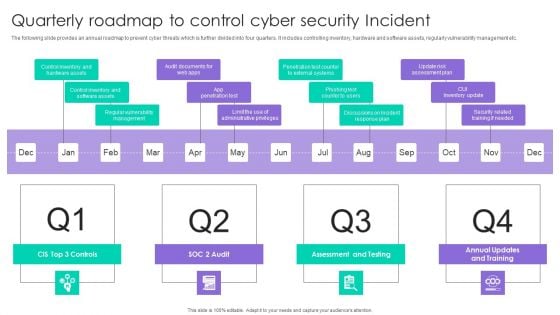
Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF
The following slide provides an annual roadmap to prevent cyber threats which is further divided into four quarters. It includes controlling inventory, hardware and software assets, regularly vulnerability management etc. Presenting Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assessment And Testing, CUI Inventory Update, App Penetration Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Do you know about Slidesgeeks Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
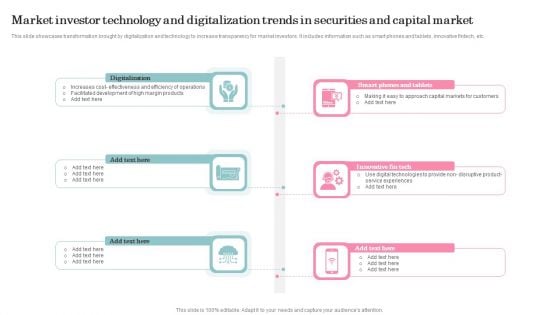
Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF
This slide showcases transformation brought by digitalization and technology to increase transparency for market investors. It includes information such as smart phones and tablets, innovative fintech, etc. Presenting Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF to dispense important information. This template comprises Six stages. It also presents valuable insights into the topics including Digitalization, Innovative Fin Tech. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF
Do you know about Slidesgeeks Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
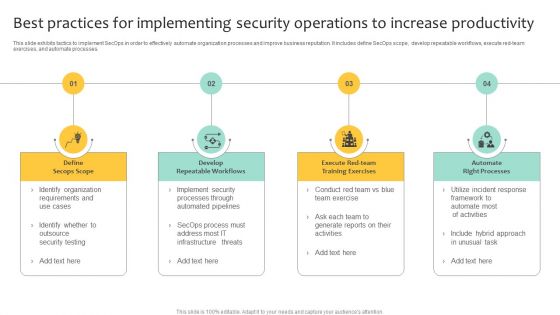
Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF
This slide exhibits tactics to implement SecOps in order to effectively automate organization processes and improve business reputation. It includes define SecOps scope, develop repeatable workflows, execute red-team exercises, and automate processes. Presenting Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Develop Repeatable Workflows, Automate Right Processes, Define Secops Scope. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Safeguarding Network With SDN Security Ppt PowerPoint Presentation Complete Deck With Slides
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Safeguarding Network With SDN Security Ppt PowerPoint Presentation Complete Deck With Slides has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has fifty nine slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance.
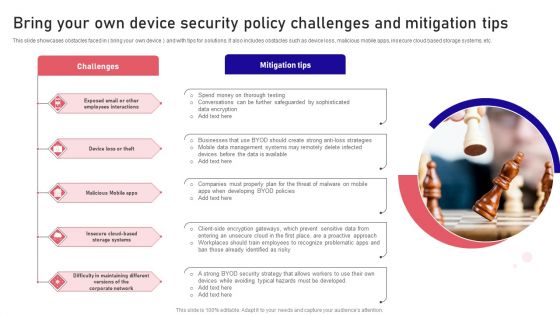
Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF
This slide showcases obstacles faced in bring your own device and with tips for solutions. It also includes obstacles such as device loss, malicious mobile apps, insecure cloud based storage systems, etc. Presenting Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Challenges, Mitigation Tips, Malicious Mobile. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
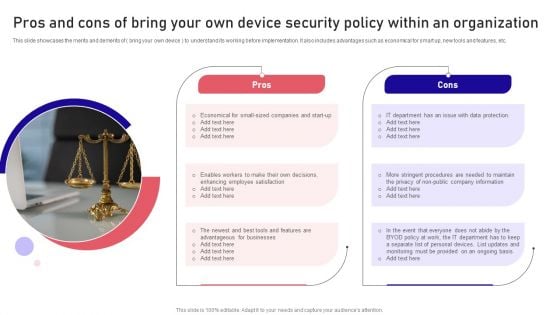
Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF
This slide showcases the merits and demerits of bring your own device to understand its working before implementation. It also includes advantages such as economical for smart up, new tools and features, etc. Presenting Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Data Protection, Organization, Company Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
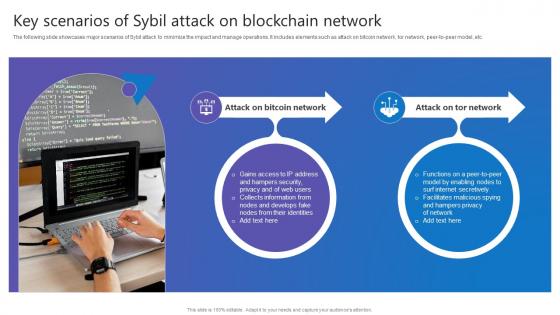
Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc.

Overview Of Non Fungible Tokens Ppt PowerPoint Presentation Diagram Graph Charts PDF
This slide depicts the overview of non-fungible tokens these are secure tokens that confirm the ownership of one-of-a-kind goods as a blockchain asset. If you are looking for a format to display your unique thoughts, then the professionally designed Overview Of Non Fungible Tokens Ppt PowerPoint Presentation Diagram Graph Charts PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Overview Of Non Fungible Tokens Ppt PowerPoint Presentation Diagram Graph Charts PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
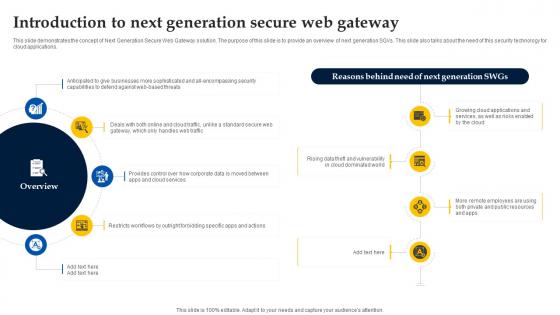
Web Access Control Solution Introduction To Next Generation Secure Web Gateway
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Are you searching for a Web Access Control Solution Introduction To Next Generation Secure Web Gateway that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Web Access Control Solution Introduction To Next Generation Secure Web Gateway from Slidegeeks today. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
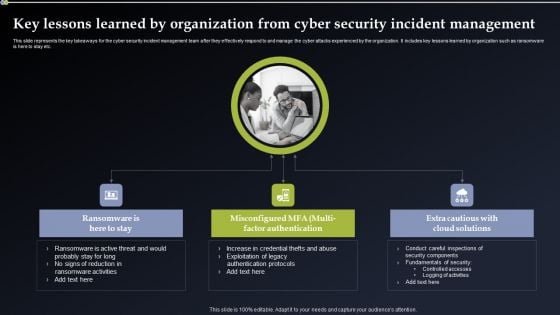
Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF can be your best option for delivering a presentation. Represent everything in detail using Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
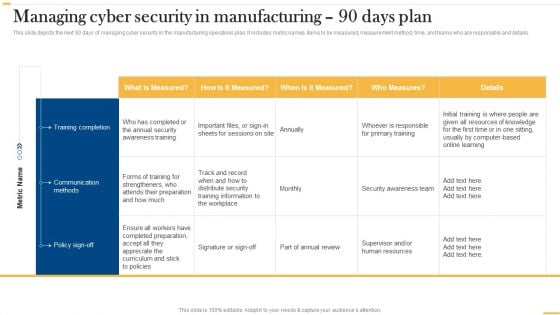
Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
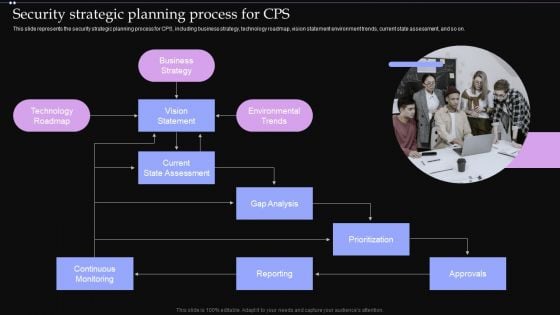
Security Strategic Planning Process For CPS Ppt PowerPoint Presentation File Pictures PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Strategic Planning Process For CPS Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Security Strategic Planning Process For CPS Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
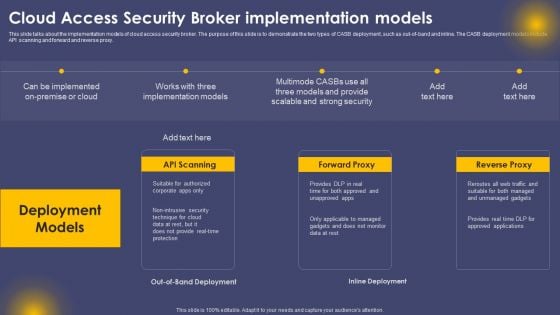
Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF
This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
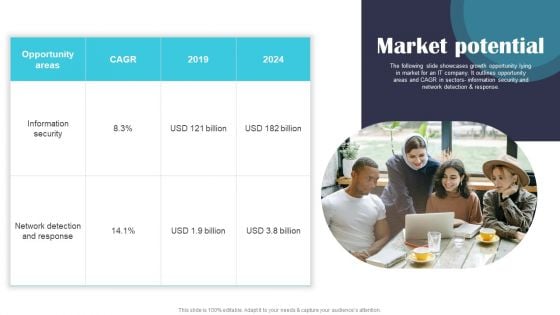
Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF
The following slide showcases growth opportunity lying in market for an IT company. It outlines opportunity areas and CAGR in sectors information security and network detection and response. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
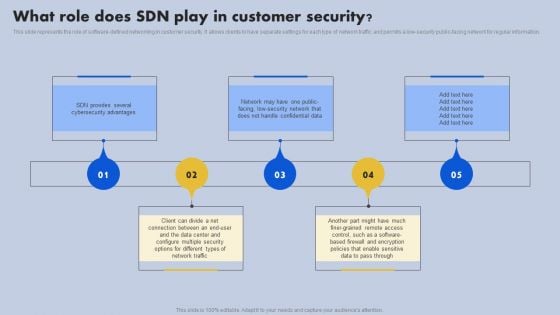
What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
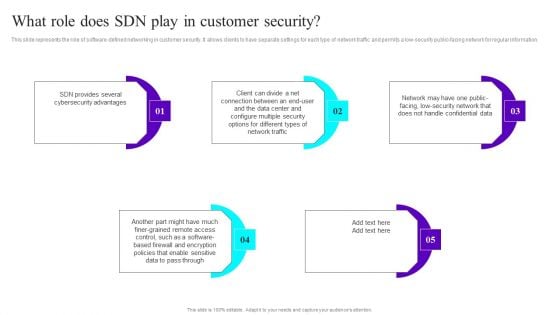
What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
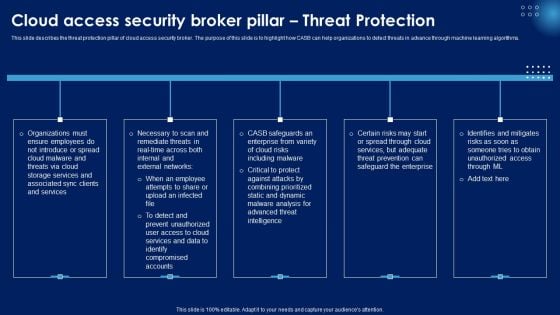
Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
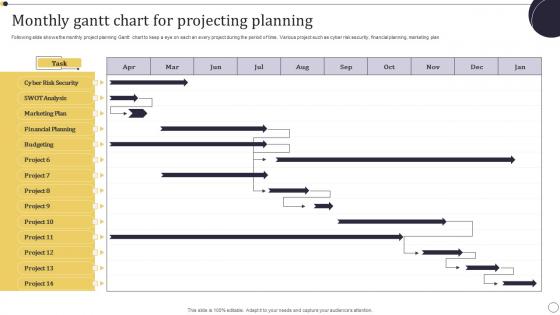
Monthly Gantt Chart For Projecting Planning Information Pdf
Following slide shows the monthly project planning Gantt chart to keep a eye on each an every project during the period of time. Various project such as cyber risk security, financial planning, marketing plan Showcasing this set of slides titled Monthly Gantt Chart For Projecting Planning Information Pdf. The topics addressed in these templates are Marketing Plan, Financial Planning, Cyber Risk Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the monthly project planning Gantt chart to keep a eye on each an every project during the period of time. Various project such as cyber risk security, financial planning, marketing plan
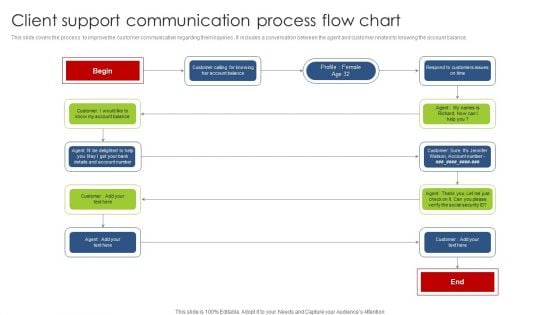
Client Support Communication Process Flow Chart Pictures PDF
This slide covers the process to improve the customer communication regarding their inquiries . It includes a conversation between the agent and customer related to knowing the account balance. Presenting Client Support Communication Process Flow Chart Pictures PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Customers Issues, Social Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
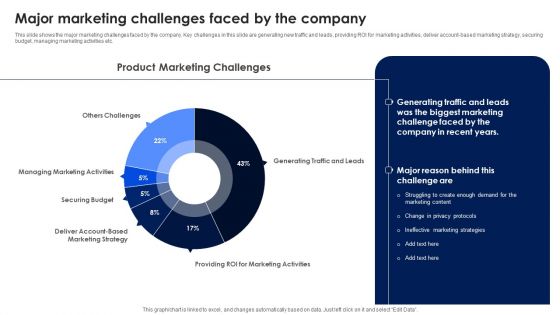
Major Marketing Challenges Faced By The Company Ppt PowerPoint Presentation Diagram Graph Charts PDF
This slide shows the major marketing challenges faced by the company. Key challenges in this slide are generating new traffic and leads, providing ROI for marketing activities, deliver account based marketing strategy, securing budget, managing marketing activities etc. Find highly impressive Major Marketing Challenges Faced By The Company Ppt PowerPoint Presentation Diagram Graph Charts PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Major Marketing Challenges Faced By The Company Ppt PowerPoint Presentation Diagram Graph Charts PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

IT Career Certifications Benefits Of IT Certifications Technical Certifications And Business Individuals Themes PDF
This template covers IT certification Benefits for the employees such as expand individuals employment opportunities, gaining professional credibility, increase your job security and job stability etc. Deliver an awe inspiring pitch with this creative IT Career Certifications Benefits Of IT Certifications Technical Certifications And Business Individuals Themes PDF bundle. Topics like Expand Individuals, Employment Opportunities, Knowledge And Qualifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
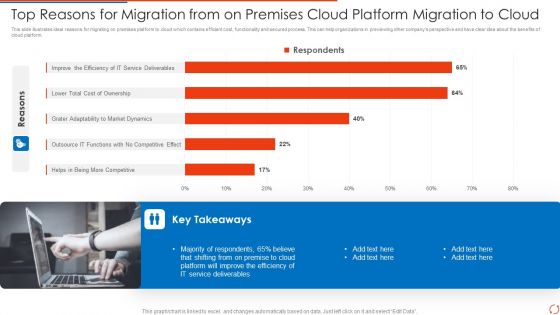
Top Reasons For Migration From On Premises Cloud Platform Migration To Cloud Introduction PDF Download PDF
This slide illustrates ideal reasons for migrating on premises platform to cloud which contains efficient cost, functionality and secured process. This can help organizations in previewing other companys perspective and have clear idea about the benefits of cloud platform.Showcasing this set of slides titled Top Reasons For Migration From On Premises Cloud Platform Migration To Cloud Introduction PDF Download PDF The topics addressed in these templates are Cost, Service Deliverables, Market. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
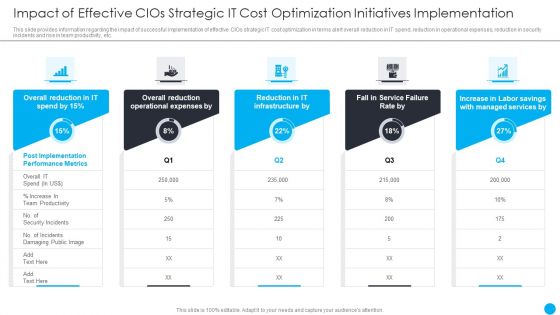
Cios Methodologies To Improve IT Spending Impact Of Effective Cios Strategic It Cost Optimization Inspiration PDF
This slide provides information regarding the impact of successful implementation of effective CIOs strategic IT cost optimization in terms alert overall reduction in IT spend, reduction in operational expenses, reduction in security incidents and rise in team productivity, etc. Deliver an awe inspiring pitch with this creative Cios Methodologies To Improve IT Spending Impact Of Effective Cios Strategic It Cost Optimization Inspiration PDF bundle. Topics like Overall Reduction, Operational Expenses, Managed Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
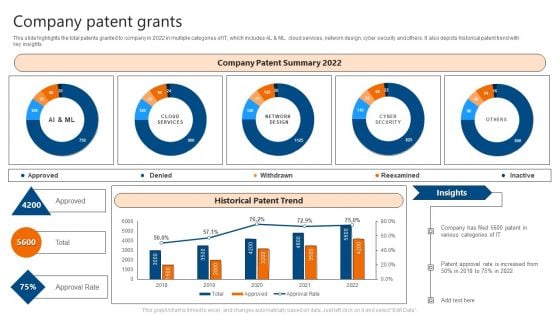
Company Patent Grants IT Software Development Company Profile Introduction PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver and pitch your topic in the best possible manner with this Company Patent Grants IT Software Development Company Profile Introduction PDF. Use them to share invaluable insights on Company Patent Summary, Historical Patent Trend and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
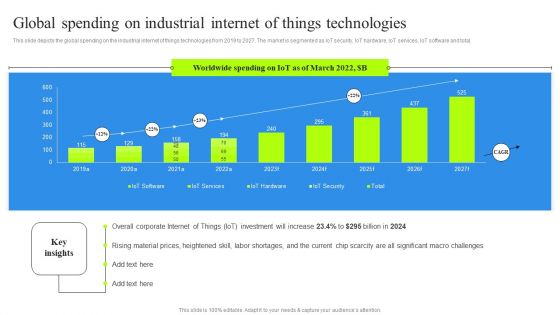
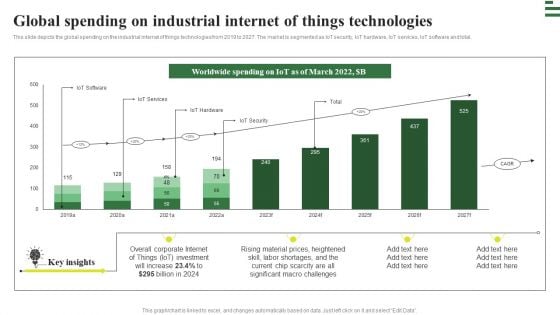
Global Spending On Industrial Internet Of Things Technologies Graphics PDF
This slide depicts the global spending on the industrial internet of things technologies from 2019 to 2027. The market is segmented as IoT security, IoT hardware, IoT services, IoT software and total. Boost your pitch with our creative Global Spending On Industrial Internet Of Things Technologies Graphics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Transforming Manufacturing With Automation Global Spending On Industrial Elements PDF
This slide depicts the global spending on the industrial internet of things technologies from 2019 to 2027. The market is segmented as IoT security, IoT hardware, IoT services, IoT software and total. Find a pre designed and impeccable Transforming Manufacturing With Automation Global Spending On Industrial Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
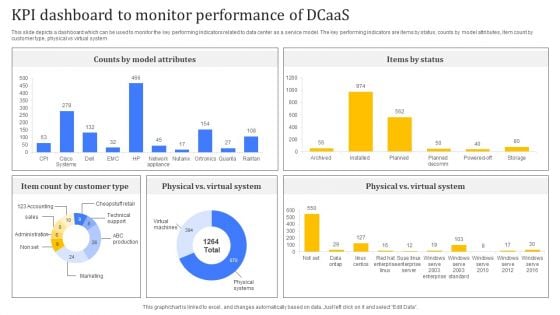
KPI Dashboard To Monitor Performance Of Dcaas Pictures PDF
Following slide highlights major benefits of applying data center as a service to business operations which can be used by businesses looking to modernize their IT infrastructure. Major benefits are in terms of scalability, flexibility, cost effectiveness, and security. Pitch your topic with ease and precision using this KPI Dashboard To Monitor Performance Of Dcaas Pictures PDF. This layout presents information on Customer Type, Counts By Model Attributes, Items By Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Public Governance Risk Rating And Analysis Software Dashboard Brochure PDF
This slide covers the status report of risks and security breaches in government initiated public services. It includes risk analysis progress, risk assessment matrix, risk rating and action plan breakdown. Showcasing this set of slides titled Public Governance Risk Rating And Analysis Software Dashboard Brochure PDF. The topics addressed in these templates are Risk Rating Breakdown, Risks Analysis Progress, Analysis Software Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
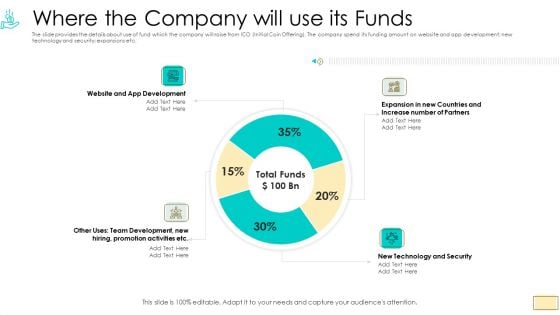
Investor Pitch Ppt For Crypto Funding Where The Company Will Use Its Funds Diagrams PDF
The slide provides the details about use of fund which the company will raise from ICO Initial Coin Offering. The company spend its funding amount on website and app development new technology and security expansions etc.Deliver an awe-inspiring pitch with this creative investor pitch ppt for crypto funding where the company will use its funds diagrams pdf. bundle. Topics like website and app development, new technology and security, expansion in new countries and increase number of partners can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
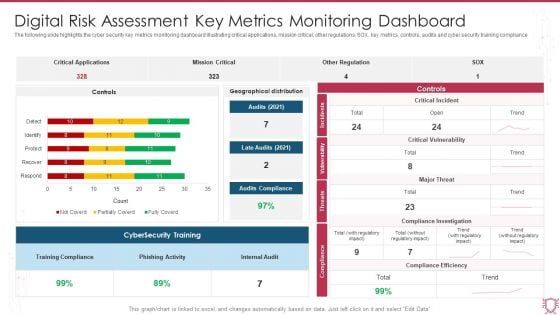
Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF
The following slide highlights the cyber security key metrics monitoring dashboard illustrating critical applications, mission critical, other regulations, SOX, key metrics, controls, audits and cyber security training compliance. Showcasing this set of slides titled Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF. The topics addressed in these templates are Critical Applications, Mission Critical, Other Regulation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
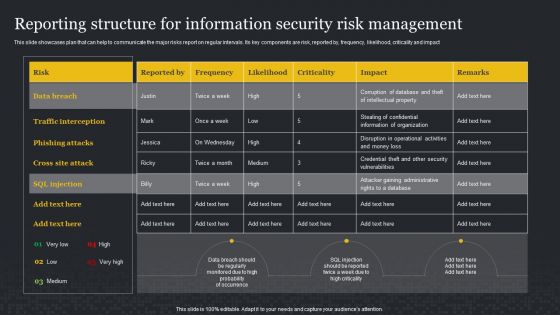
Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF can be your best option for delivering a presentation. Represent everything in detail using Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Do you know about Slidesgeeks Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
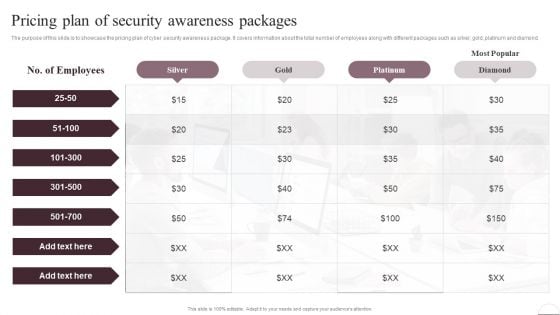
Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF
This slide represents the seven principles of GDPR law, including lawfulness and transparency, purpose limitation, data minimization, accuracy, storage limitation, integrity and confidentiality, accountability. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
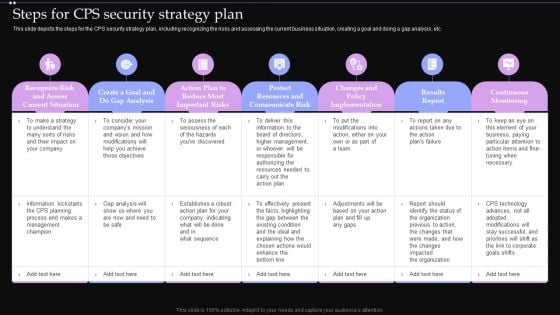
Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Do you know about Slidesgeeks Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
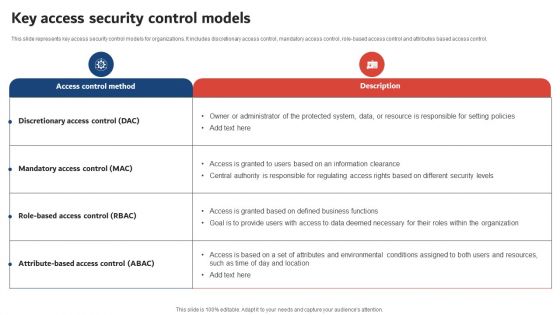
Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF
This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Do you know about Slidesgeeks Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
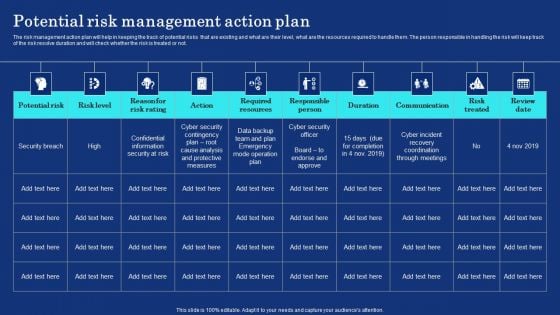
Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF can be your best option for delivering a presentation. Represent everything in detail using Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
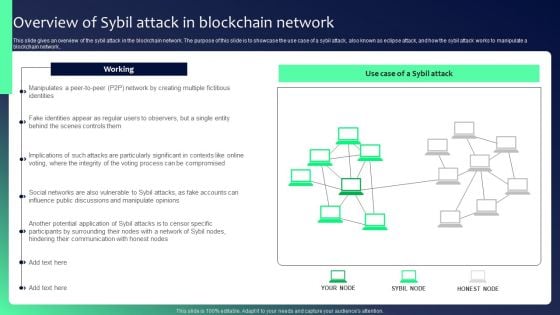
Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF
This slide gives an overview of the sybil attack in the blockchain network. The purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network.. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf
Do you know about Slidesgeeks Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. Our Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
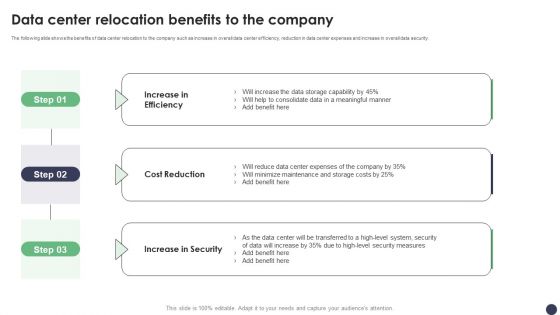
Data Center Relocation Benefits To The Company Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide shows the benefits of data center relocation to the company such as increase in overall data center efficiency, reduction in data center expenses and increase in overall data security. Slidegeeks is here to make your presentations a breeze with Data Center Relocation Benefits To The Company Ppt PowerPoint Presentation Diagram Graph Charts PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Business PowerPoint Templates Download Process Circular Flow Network Slides
We present our business powerpoint templates download process Circular Flow Network Slides.Download and present our Globe PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Download and present our Ring Charts PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Download our Circle Charts PowerPoint Templates because this Layout can explain the relevance of the different layers and stages in getting down to your core competence, ability and desired result. Use our Arrows PowerPoint Templates because it shows various choices to be made. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries.Use these PowerPoint slides for presentations relating to Business, chart, circle,colors, concept, corporate, cycle, data,design, detail, development, diagram,engineering, graphic, ideas, illustration,image, implement, implementation, life,lifecycle, management, model, objects,organization, phase, plan, process,product, professional, project, quality,schema, shape. The prominent colors used in the PowerPoint template are Blue, Yellow, White. You can be sure our business powerpoint templates download process Circular Flow Network Slides will make you look like a winner. PowerPoint presentation experts tell us our circle PowerPoint templates and PPT Slides are designed by professionals Professionals tell us our business powerpoint templates download process Circular Flow Network Slides are Graceful. Presenters tell us our data PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. Professionals tell us our business powerpoint templates download process Circular Flow Network Slides are Whimsical. Customers tell us our corporate PowerPoint templates and PPT Slides are Beautiful. Build teams with our Business PowerPoint Templates Download Process Circular Flow Network Slides. Download without worries with our money back guaranteee.

Issues Addressed By Dcaas Elements PDF
This slide brings forth various issues which are addressed by data service centers to provide users a solution in order to improve current business performance. The various issues addressed are data management, hyper converged infrastructure, data security and file storage. Presenting Issues Addressed By Dcaas Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Management, Data Security, Converged Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
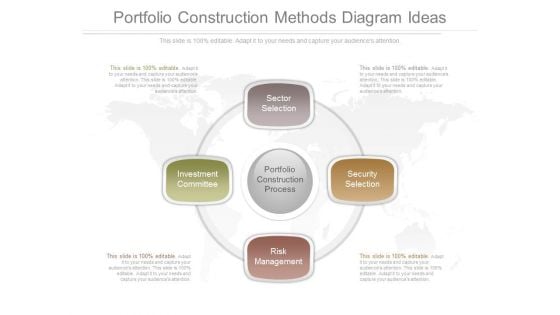
Portfolio Construction Methods Diagram Ideas
This is a portfolio construction methods diagram ideas. This is a four stage process. The stages in this process are portfolio construction process, sector selection, investment committee, risk management, security selection.

Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Retrieve professionally designed Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc.
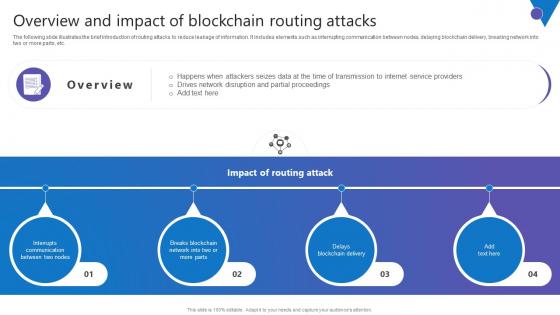
Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf
The following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc. Retrieve professionally designed Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc.
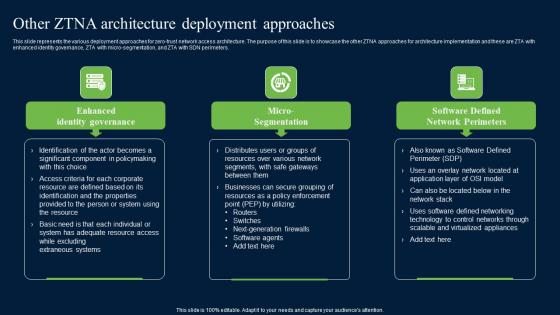
Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.

Optimization Of IoT Remote Monitoring Smart Doorbells Used For Maintaining Security IoT SS V
This slide provides an overview of the smart displays used in smart homes to monitor home activities. It further includes popular brands and factors to consider that are usage, size, resolution, cost, sound quality and energy use. Are you searching for a Optimization Of IoT Remote Monitoring Smart Doorbells Used For Maintaining Security IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Optimization Of IoT Remote Monitoring Smart Doorbells Used For Maintaining Security IoT SS V from Slidegeeks today. This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc.

Security Operations Center Strategic Tactical Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this security operations center strategic tactical ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Security Control Laptop Access Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this security control laptop access ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the eleven slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the thirty slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

IT Security Awareness Training Program Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this IT Security Awareness Training Program Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty four slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Do you know about Slidesgeeks Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
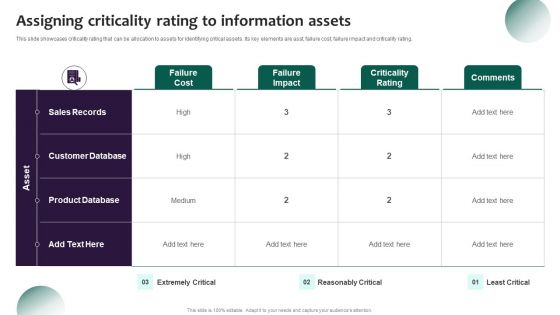
Information Systems Security And Risk Management Plan Assigning Criticality Rating To Information Assets Ideas PDF
This slide showcases criticality rating that can be allocation to assets for identifying critical assets. Its key elements are asst, failure cost, failure impact and criticality rating. Do you know about Slidesgeeks Information Systems Security And Risk Management Plan Assigning Criticality Rating To Information Assets Ideas PDFThese are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
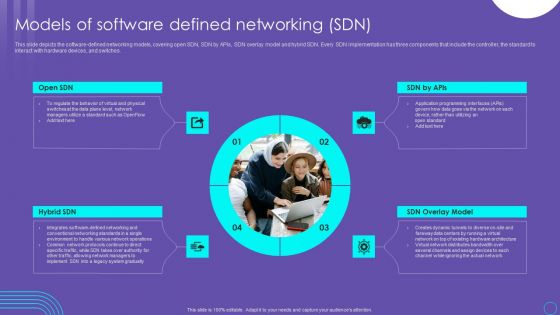
SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF
This slide depicts the software defined networking models, covering open SDN, SDN by APIs, SDN overlay model and hybrid SDN. Every SDN implementation has three components that include the controller, the standard to interact with hardware devices, and switches. Do you know about Slidesgeeks SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

IT Security Communication Plan Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this IT Security Communication Plan Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the seventeen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
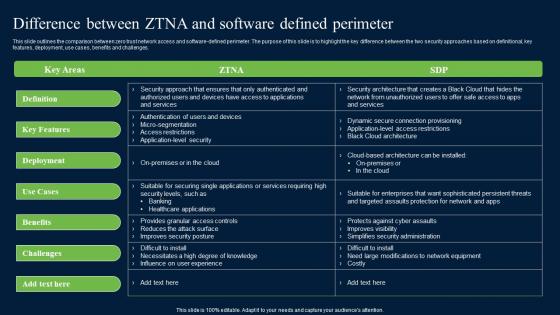
Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf can be your best option for delivering a presentation. Represent everything in detail using Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.

Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.

Web Access Control Solution Steps To Select Next Generation Secure Web Gateway
This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Web Access Control Solution Steps To Select Next Generation Secure Web Gateway can be your best option for delivering a presentation. Represent everything in detail using Web Access Control Solution Steps To Select Next Generation Secure Web Gateway and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc.

Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF
This slide represents the official announcement from lotem finkelstein, head of threat intelligence at check point software, that anyone can join ukraine and russia cyber warfare. Slidegeeks is here to make your presentations a breeze with Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
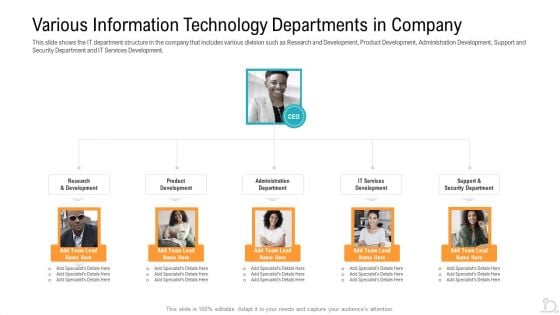
Various Information Technology Departments In Company Designs PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development.Presenting various information technology departments in company designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like various information technology departments in company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
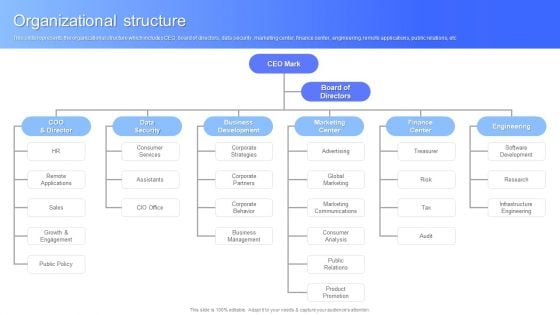
Organizational Structure Facebook Business Outline Slides PDF
This slide represents the organizational structure which includes CEO, board of directors, data security, marketing center, finance center, engineering, remote applications, public relations, etc. This is a Organizational Structure Facebook Business Outline Slides PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Consumer Services, Corporate Strategies, Corporate Behavior, Business Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
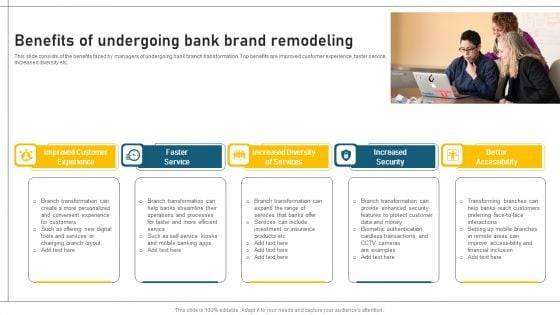
Benefits Of Undergoing Bank Brand Remodeling Information PDF
This slide consists of the benefits faced by managers of undergoing bank branch transformation. Top benefits are improved customer experience, faster service, increased diversity etc. Presenting Benefits Of Undergoing Bank Brand Remodeling Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Improved Customer Experience, Faster Service, Increased Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
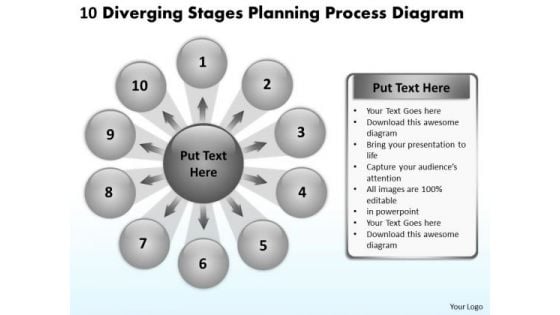
10 Diverging Stages Planning Process Diagram Ppt Circular Flow Spoke Chart PowerPoint Slides
We present our 10 diverging stages planning process diagram ppt Circular Flow Spoke Chart PowerPoint Slides.Download and present our Arrows PowerPoint Templates because individual components well researched and understood in their place. Download and present our Flow charts PowerPoint Templates because the foundation stones of many a life. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Present our Process and Flows PowerPoint Templates because you can see In any endeavour people matter most. Download and present our Circle charts PowerPoint Templates because you can blaze a brilliant trail from point to point.Use these PowerPoint slides for presentations relating to Business, catalog, chart, circle, concept, conceptual, conference, connection, corporate, description, design, development, diagram, goal, graphic, idea, illustration, item, management, marketing, mind, mind map, model, navigation, organization, parts, plans, presentation, process, reports, solutions, strategy, success, target. The prominent colors used in the PowerPoint template are Yellow, Black, Gray. You can be sure our 10 diverging stages planning process diagram ppt Circular Flow Spoke Chart PowerPoint Slides are Versatile. Presenters tell us our corporate PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. We assure you our 10 diverging stages planning process diagram ppt Circular Flow Spoke Chart PowerPoint Slides are Chic. Customers tell us our connection PowerPoint templates and PPT Slides are Spiffy. Presenters tell us our 10 diverging stages planning process diagram ppt Circular Flow Spoke Chart PowerPoint Slides will impress their bosses and teams. You can be sure our conference PowerPoint templates and PPT Slides are Fun. Cross the chasm with our 10 Diverging Stages Planning Process Diagram Ppt Circular Flow Spoke Chart PowerPoint Slides. You will come out on top.

Risk Procedure Security Threads Ppt PowerPoint Presentation Complete Deck With Slides
This risk procedure security threads ppt powerpoint presentation complete deck with slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing eleven slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this risk procedure security threads ppt powerpoint presentation complete deck with slides PPT slideshow.

Internet Security Risk Severity Probability Ppt PowerPoint Presentation Complete Deck With Slides
This internet security risk severity probability ppt powerpoint presentation complete deck with slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this internet security risk severity probability ppt powerpoint presentation complete deck with slides PPT slideshow.

Incident Business Security Threat Ppt PowerPoint Presentation Complete Deck With Slides
This incident business security threat ppt powerpoint presentation complete deck with slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing eleven slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this incident business security threat ppt powerpoint presentation complete deck with slides PPT slideshow.

Digitization Of Security Systems Ppt PowerPoint Presentation Complete Deck With Slides
This Digitization Of Security Systems Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing sixteen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Digitization Of Security Systems Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides
This Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twenty slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Information Technology Security KPI Ppt PowerPoint Presentation Complete Deck With Slides
This Information Technology Security KPI Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Information Technology Security KPI Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.
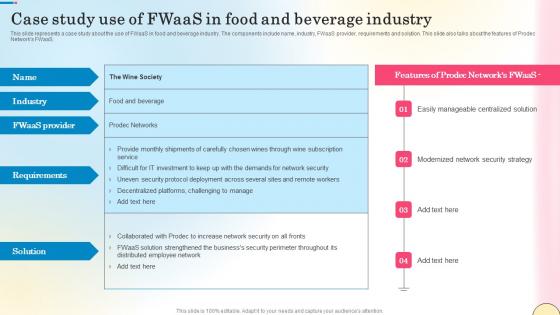
Case Study Use Of Fwaas In Food And Beverage Industry Network Security Pictures Pdf
This slide represents a case study about the use of FWaaS in food and beverage industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the features of Prodec Networks FWaaS. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Case Study Use Of Fwaas In Food And Beverage Industry Network Security Pictures Pdf can be your best option for delivering a presentation. Represent everything in detail using Case Study Use Of Fwaas In Food And Beverage Industry Network Security Pictures Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents a case study about the use of FWaaS in food and beverage industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the features of Prodec Networks FWaaS.

Tableau Business Intelligence Tool Salesforce Business Profile Diagrams PDF
This slide highlights the salesforce analytics software reports and dashboards which showcases the dashboard that includes chart, table, gauge with real-time reporting, and security controls. Deliver an awe inspiring pitch with this creative Tableau Business Intelligence Tool Salesforce Business Profile Diagrams PDF bundle. Topics like Server Management, Embedded Analytics, Security Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Multi Aspect Verification Secure Access Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this multi aspect verification secure access ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
Software Architecture Security Scalability Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this software architecture security scalability ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Composite Strategy Database Security Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this composite strategy database security ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Wireless Network Security System Smart Lock Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this wireless network security system smart lock ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
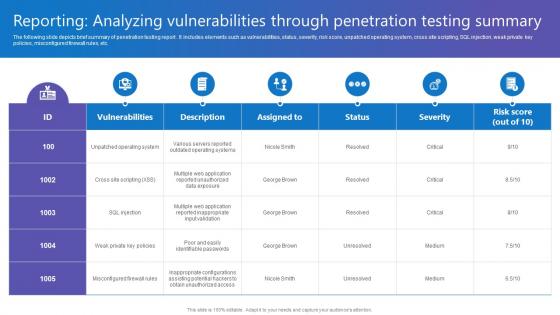
Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf
The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc. Do you know about Slidesgeeks Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc.
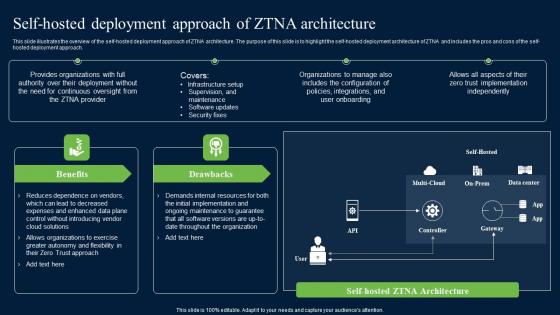
Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Network Security Graphics Pdf
This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Do you know about Slidesgeeks Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Network Security Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.
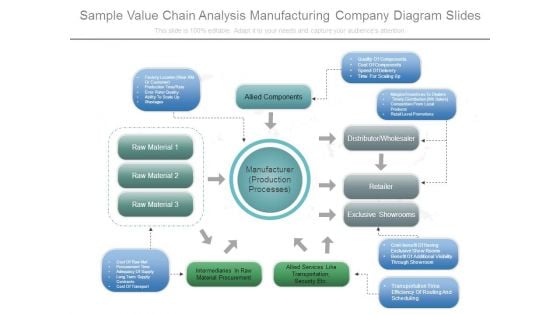
Sample Value Chain Analysis Manufacturing Company Diagram Slides
This is a sample value chain analysis manufacturing company diagram slides. This is a eight stage process. The stages in this process are manufacturer production processes, factory location near rm or customer, production time rate, error rate quality, ability to scale up, wastages, allied components, quality of components, cost of components, speed of delivery, time for scaling up, margins incentives to dealers, timely distribution wh salers, competition from local products, retail level promotions, distributor wholesaler, retailer, exclusive showrooms, cost benefit of having exclusive show rooms, benefit of additional visibility through showroom, transportation time efficiency of routing and scheduling, cost of raw mat, procurement time, adequacy of supply, long term supply contracts, cost of transport, intermediaries in raw material procurement, allied services like transportation security etc, raw material.

5 Investment Opportunities For Growth In Healthcare Sector Diagrams PDF
This slide highlights investment opportunities to foster growth in the healthcare sector. The purpose of growth in the healthcare sector is to achieve advancements, improve patient experience and generate financial returns for investors. These opportunities aim to develop innovative healthcare technologies and services to address needs and improve outcomes. It also provides benefits derived from each opportunity. Showcasing this set of slides titled 5 Investment Opportunities For Growth In Healthcare Sector Diagrams PDF. The topics addressed in these templates are Biotech And Pharmaceutical Innovations, Potential, Cyber Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
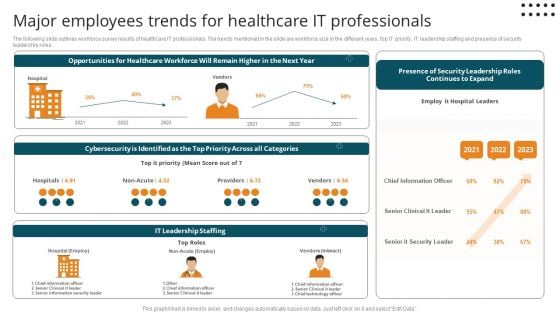
Major Employees Trends For Healthcare It Professionals Diagrams PDF
The following slide outlines workforce survey results of healthcare IT professionals. The trends mentioned in the slide are workforce size in the different years, top IT priority, IT leadership staffing and presence of security leadership roles.Pitch your topic with ease and precision using this Major Employees Trends For Healthcare It Professionals Diagrams PDF. This layout presents information on Cybersecurity Identified, Chief Information, Senior Clinical. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
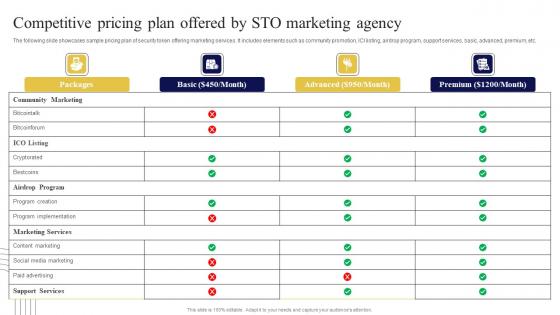
Competitive Pricing Plan Offered Exploring Investment Opportunities Elements Pdf
The following slide showcases sample pricing plan of security token offering marketing services. It includes elements such as community promotion, ICI listing, airdrop program, support services, basic, advanced, premium, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Competitive Pricing Plan Offered Exploring Investment Opportunities Elements Pdf can be your best option for delivering a presentation. Represent everything in detail using Competitive Pricing Plan Offered Exploring Investment Opportunities Elements Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide showcases sample pricing plan of security token offering marketing services. It includes elements such as community promotion, ICI listing, airdrop program, support services, basic, advanced, premium, etc.
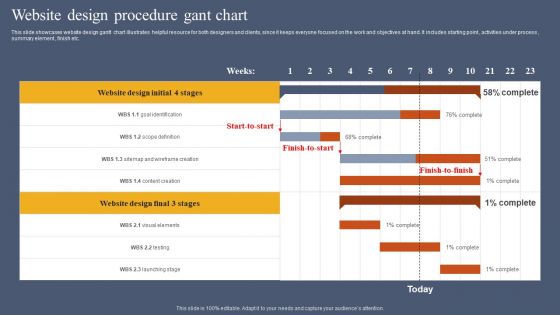
Website Design Procedure Gant Chart Graphics PDF
This slide showcases website design gantt chart illustrates helpful resource for both designers and clients, since it keeps everyone focused on the work and objectives at hand. It includes starting point , activities under process , summary element , finish etc. Showcasing this set of slides titled Website Design Procedure Gant Chart Graphics PDF. The topics addressed in these templates are Stages, Weeks, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
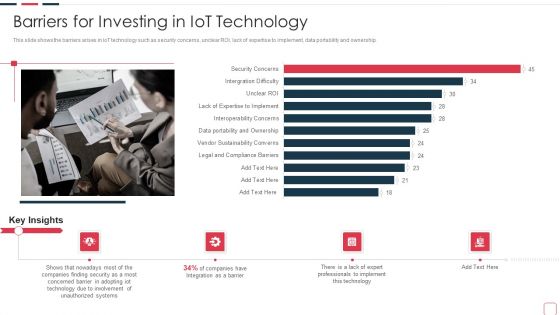
Price Benefit Internet Things Digital Twins Execution After Covid Barriers For Investing In Iot Themes PDF
This slide shows the barriers arises in IoT technology such as security concerns, unclear ROI, lack of expertise to implement, data portability and ownership. Deliver and pitch your topic in the best possible manner with this price benefit internet things digital twins execution after covid barriers for investing in iot themes pdf . Use them to share invaluable insights on barriers for investing in iot technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
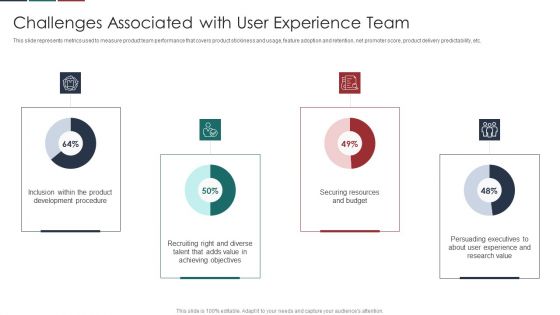
Deliver Efficiency Innovation Challenges Associated With User Experience Team Themes PDF
This slide represents metrics used to measure product team performance that covers product stickiness and usage, feature adoption and retention, net promoter score, product delivery predictability, etc. Deliver an awe inspiring pitch with this creative Deliver Efficiency Innovation Challenges Associated With User Experience Team Themes PDF bundle. Topics like Product Development Procedure, Value Achieving Objectives, Securing Resources And Budget, Experience And Research Value can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
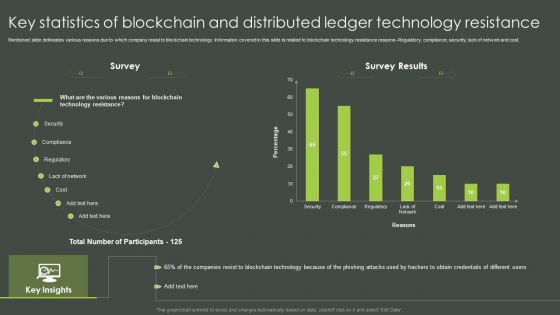
Key Statistics Of Blockchain And Distributed Ledger Technology Resistance Themes PDF
Mentioned slide delineates various reasons due to which company resist to blockchain technology. Information covered in this slide is related to blockchain technology resistance reasons -Regulatory, compliance, security, lack of network and cost. Showcasing this set of slides titled Key Statistics Of Blockchain And Distributed Ledger Technology Resistance Themes PDF. The topics addressed in these templates are Blockchain, Technology Resistance, Total Number Participants. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
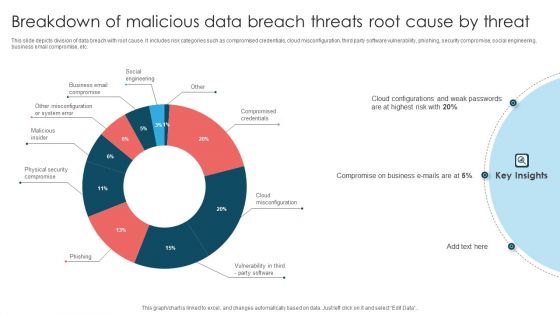
Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF
This slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Showcasing this set of slides titled Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF. The topics addressed in these templates are Compromise On Business, Cloud Configurations, Weak Passwords. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
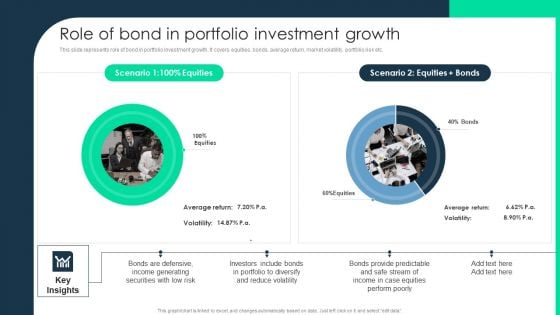
Monetary Investment Portfolio Growth And Administration Role Of Bond In Portfolio Investment Growth Structure PDF Themes PDF
This slide represents role of bond in portfolio investment growth. It covers equities, bonds, average return, market volatility, portfolio risk etc. Deliver and pitch your topic in the best possible manner with this Monetary Investment Portfolio Growth And Administration Role Of Bond In Portfolio Investment Growth Structure PDF Themes PDF. Use them to share invaluable insights on Low Risk, Securities, Income Generating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
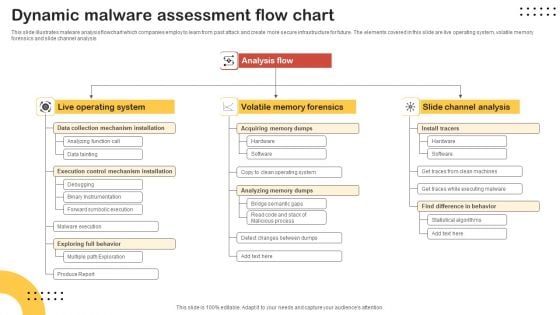
Dynamic Malware Assessment Flow Chart Infographics PDF
This slide illustrates malware analysis flowchart which companies employ to learn from past attack and create more secure infrastructure for future. The elements covered in this slide are live operating system, volatile memory forensics and slide channel analysis. Showcasing this set of slides titled Dynamic Malware Assessment Flow Chart Infographics PDF. The topics addressed in these templates are Live Operating System, Volatile Memory Forensics, Slide Channel Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
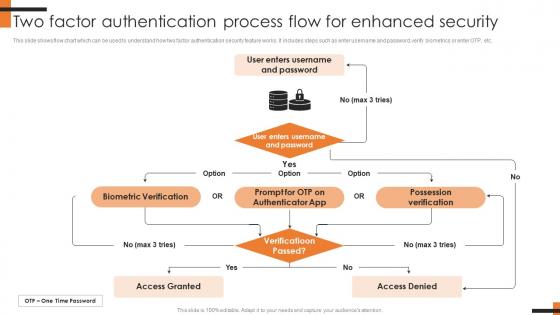
Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. The Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.

Organization Impact Metrics Strategic Themes PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission.Presenting organization impact metrics strategic themes pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like data loss incidents, infected computers, total number of computers currently corrupted. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risks Associated To Gym Staff Themes PDF
This slide covers the key risks related to gym staff members during the Covid 19. Major risk includes risks related to job security, risk associated to work, risk of getting stresses etc.Presenting risks associated to gym staff themes pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like risk related to job security, risks associated to work, risk of getting stressed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
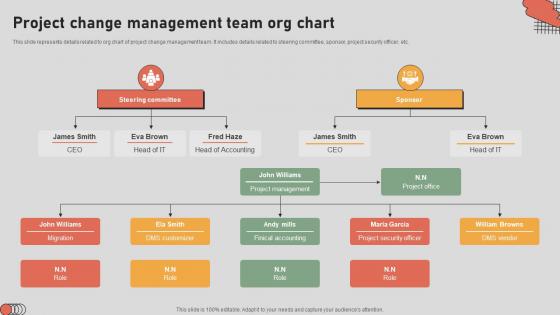
Project Change Management Team Org Chart The Digital Project Managers
This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc. Create an editable Project Change Management Team Org Chart The Digital Project Managers that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Project Change Management Team Org Chart The Digital Project Managers is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc.
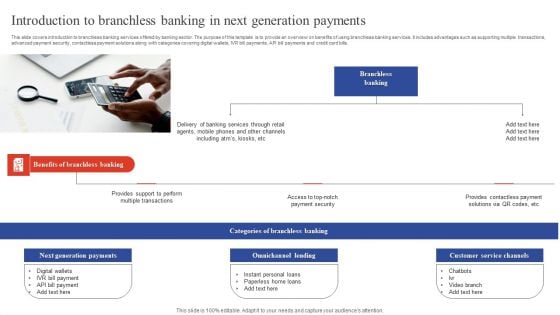
Deployment Of Omnichannel Banking Solutions Introduction To Branchless Banking In Next Generation Diagrams PDF
This slide covers introduction to branchless banking services offered by banking sector. The purpose of this template is to provide an overview on benefits of using branchless banking services. It includes advantages such as supporting multiple transactions, advanced payment security, contactless payment solutions along with categories covering digital wallets, IVR bill payments, API bill payments and credit card bills. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deployment Of Omnichannel Banking Solutions Introduction To Branchless Banking In Next Generation Diagrams PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Systematic Concentric Process Diagram Business Plan Outline PowerPoint Templates
We present our systematic concentric process diagram business plan outline PowerPoint templates.Use our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Download our Shapes PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Download and present our Business PowerPoint Templates because It can Bubble and burst with your ideas. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity.Use these PowerPoint slides for presentations relating to Login, cyber, radar, protocol, elimination, secure, corporate, future, concept, lan, infrastructure, data, process, scan, viral, technology, security, wan, abstract,creative, illustration, system, up, focus, terrorism, futuristic, recognition, precaution, check, processing, zoom, information, background, virus, conceptual,precautionary, pattern, systematic, measure. The prominent colors used in the PowerPoint template are Blue, Blue light, White. Force out your enemies with our Systematic Concentric Process Diagram Business Plan Outline PowerPoint Templates. Just download, type and present.
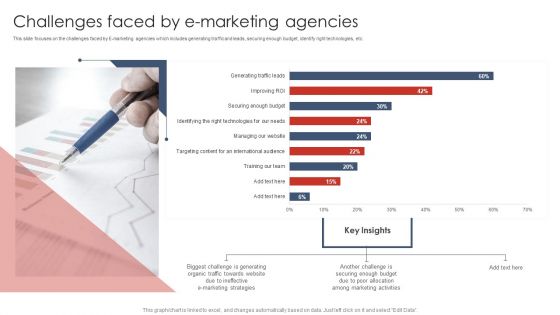
Challenges Faced By E Marketing Agencies Digital Marketing Strategy Deployment Diagrams PDF
This slide focuses on the challenges faced by E-marketing agencies which includes generating traffic and leads, securing enough budget, identify right technologies, etc.Find a pre-designed and impeccable Challenges Faced By E Marketing Agencies Digital Marketing Strategy Deployment Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
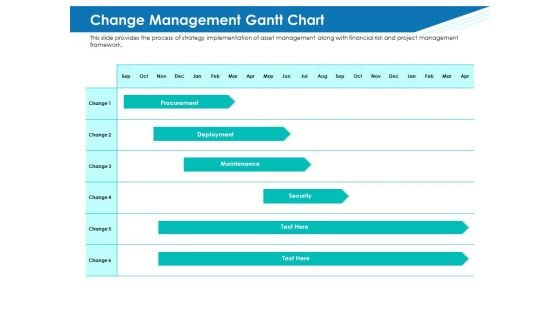
Application Lifecycle Management ALM Change Management Gantt Chart Topics PDF
Presenting this set of slides with name application lifecycle management alm change management gantt chart topics pdf. The topics discussed in these slides are procurement, deployment, maintenance, security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategic Management Of Assets Change Management Gantt Chart Mockup PDF
Presenting this set of slides with name strategic management of assets change management gantt chart mockup pdf. The topics discussed in these slides are procurement, deployment, maintenance, security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Agile Kanban Methodology Chart With Stories Microsoft PDF
Deliver an awe inspiring pitch with this creative agile kanban methodology chart with stories microsoft pdf bundle. Topics like security integration, automation processes, product development can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Business Strategy PowerPoint Templates Business Three Factors Linked To Center Diagram Ppt Slides
Business Strategy PowerPoint Templates Business Three Factors Linked To Center Diagram PPT Slides-This PowerPoint Diagram consists of three factors needed for development of Business. This Diagram will definitely make your Presentation more attractive and interesting.-Business Strategy PowerPoint Templates Business Three Factors Linked To Center Diagram PPT Slides Secure your promotion with our Business Strategy PowerPoint Templates Business Three Factors Linked To Center Diagram Ppt Slides. Download without worries with our money back guaranteee.
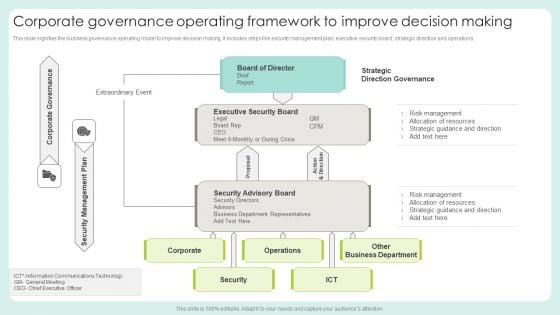
Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
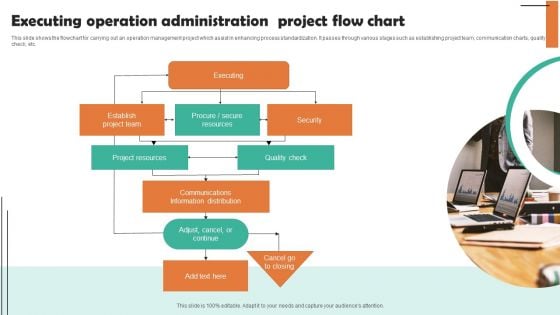
Executing Operation Administration Project Flow Chart Clipart PDF
This slide shows the flowchart for carrying out an operation management project which assist in enhancing process standardization. It passes through various stages such as establishing project team, communication charts, quality check, etc. Presenting Executing Operation Administration Project Flow Chart Clipart PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Executing Security, Establish Project Team. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

AI Applications Use To Improve Business Operations Diagrams PDF
This slide signifies the artificial intelligence software used to increase organisation operations. It covers information about hiring, market prediction, customer analysis and cyber security Presenting AI Applications Use To Improve Business Operations Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Market Prediction, Customer Analysis, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Project Change Management Team Org Chart Digital Project Management Strategies
This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc. Get a simple yet stunning designed Project Change Management Team Org Chart Digital Project Management Strategies. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Project Change Management Team Org Chart Digital Project Management Strategies can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc.
Corporate Reorganization In Bankruptcy Template Powerpoint Slide Themes
This is a corporate reorganization in bankruptcy template powerpoint slide themes. This is a five stage process. The stages in this process are secure, broke, recovery, bankruptcy, in debt.

Hotel Security Personnel Looking At Various CCTV Footage On Computers Ppt PowerPoint Presentation File Visual Aids PDF
Presenting hotel security personnel looking at various cctv footage on computers ppt powerpoint presentation file visual aids pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including hotel security personnel looking at various cctv footage on computers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Employee Motivation Strategy Cycle Diagram Ppt Sample
This is a employee motivation strategy cycle diagram ppt sample. This is a four stage process. The stages in this process are working conditions, company politics, job security, pay and benefits, relationships, supervision, status.
Integrated Technology Solutions Diagram Powerpoint Shapes
This is a integrated technology solutions diagram powerpoint shapes. This is a three stage process. The stages in this process are cross browser user interface library, optimized application object library, secure datastore for data and document.

Employee Motivation Factors Diagram Powerpoint Topics
This is a employee motivation factors diagram powerpoint topics. This is a seven stage process. The stages in this process are status, supervision, relationship, working condition, company policies, job security, pay and benefits.
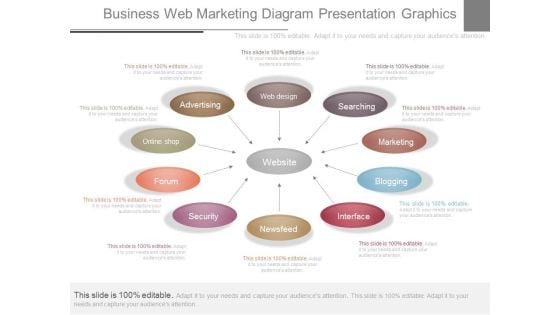
Business Web Marketing Diagram Presentation Graphics
This is a business web marketing diagram presentation graphics. This is a ten stage process. The stages in this process are web design, searching, marketing, blogging, interface, newsfeed, security, forum, online shop, advertising.
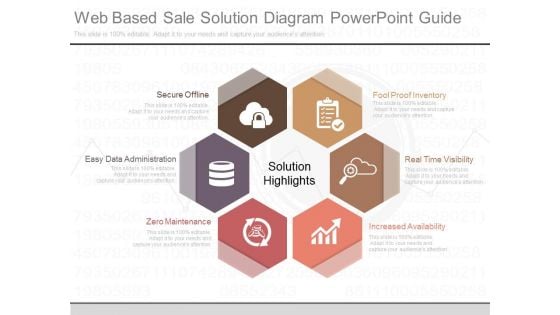
Web Based Sale Solution Diagram Powerpoint Guide
This is a web based sale solution diagram powerpoint guide. This is a six stage process. The stages in this process are fool proof inventory, real time visibility, increased availability, zero maintenance, easy data administration, secure offline.

Employee Motivation Mind Map Diagram Ppt Slides
This is a employee motivation mind map diagram ppt slides. This is a seven stage process. The stages in this process are company policies, job security, relationships, pay benefits, supervision, status, working conditions, employee motivation.
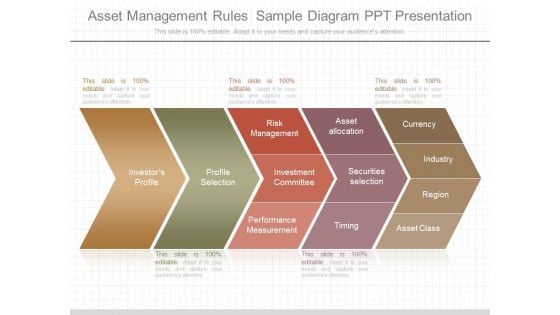
Asset Management Rules Sample Diagram Ppt Presentation
This is a asset management rules sample diagram ppt presentation. This is a five stage process. The stages in this process are investor s profile, profile, profile selection, risk management, investment committee, performance measurement, securities selection, asset allocation, timing.
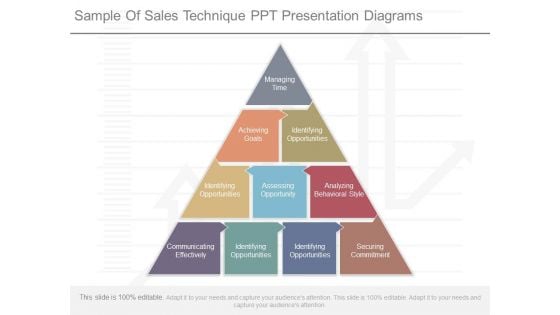
Sample Of Sales Technique Ppt Presentation Diagrams
This is a sample of sales technique ppt presentation diagrams. This is a ten stage process. The stages in this process are managing time, achieving goals, identifying opportunities, assessing opportunity, analyzing behavioral style, communicating effectively, securing commitment.
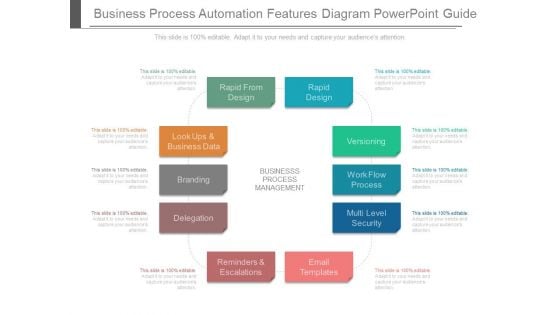
Business Process Automation Features Diagram Powerpoint Guide
This is a business process automation features diagram powerpoint guide. This is a eleven stage process. The stages in this process are rapid from design, rapid design, versioning, workflow process, multi level, security, email templates, delegation, branding.
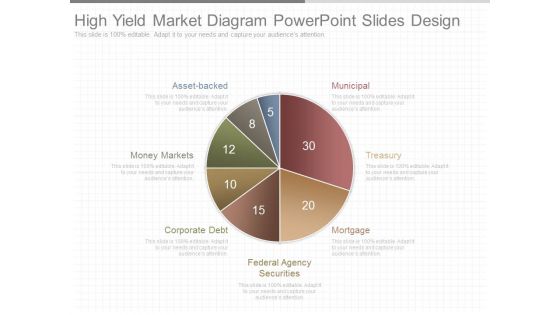
High Yield Market Diagram Powerpoint Slides Design
This is a high yield market diagram powerpoint slides design. This is a seven stage process. The stages in this process are municipal, treasury, mortgage, federal agency securities, corporate debt, money markets, asset backed.
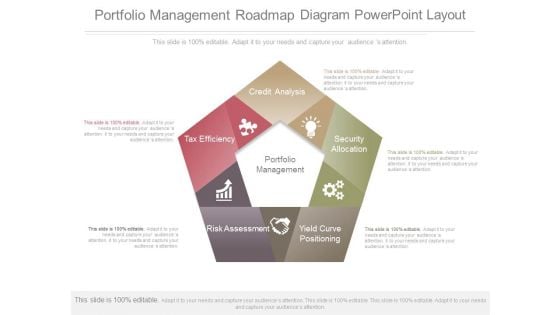
Portfolio Management Roadmap Diagram Powerpoint Layout
This is a portfolio management roadmap diagram powerpoint layout. This is a five stage process. The stages in this process are portfolio management, tax efficiency, credit analysis, security allocation, yield curve positioning, risk assessment.
Weak Business Skill Diagram Powerpoint Shapes
This is a weak business skill diagram powerpoint shapes. This is a four stage process. The stages in this process are weak business skill, technical leadership, financially secure, weak market consciousness.
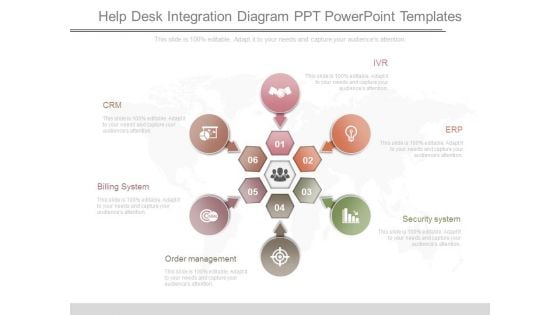
Help Desk Integration Diagram Ppt Powerpoint Templates
This is a help desk integration diagram ppt powerpoint templates. This is a six stage process. The stages in this process are crm, billing system, order management, ivr, erp, security system.
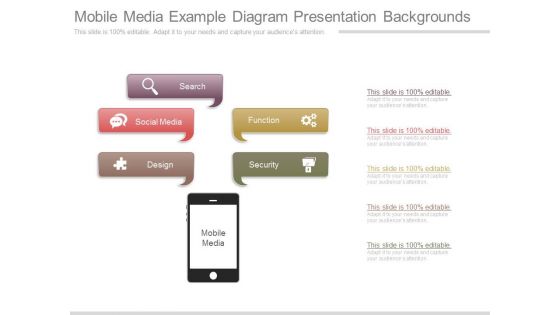
Mobile Media Example Diagram Presentation Backgrounds
This is a mobile media example diagram presentation backgrounds. This is a five stage process. The stages in this process are function, security, mobile media, design, social media, search.
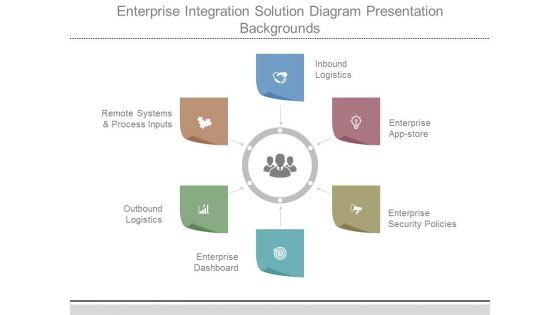
Enterprise Integration Solution Diagram Presentation Backgrounds
This is a enterprise integration solution diagram presentation backgrounds. This is a six stage process. The stages in this process are remote systems and process inputs, outbound, logistics, enterprise, dashboard, enterprise, policies, security, enterprise app store, inbound logistics.
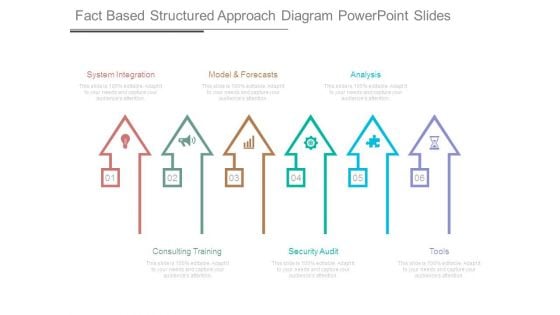
Fact Based Structured Approach Diagram Powerpoint Slides
This is a fact based structured approach diagram powerpoint slides. This is a six stage process. The stages in this process are system integration, model and forecasts, analysis, consulting training, security audit, tools.
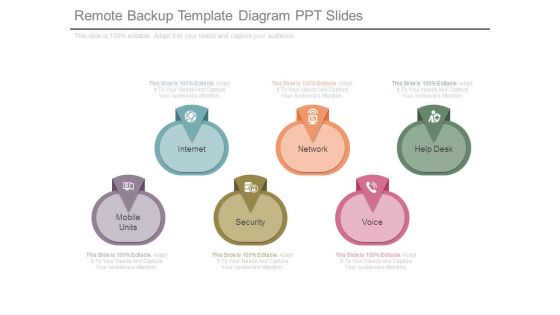
Remote Backup Template Diagram Ppt Slides
This is a remote backup template diagram ppt slides. This is a six stage process. The stages in this process are mobile units, internet, network, help desk, security, voice.

Digitized Solutions Example Diagram Ppt Slides Show
This is a digitized solutions example diagram ppt slides show. This is a six stage process. The stages in this process are people, physical things, virtual things, virtual spaces, maintain nurture, secure protect.
Merchandise Management Sample Diagram Powerpoint Layout
This is a Merchandise Management Sample Diagram Powerpoint Layout. This is a four stage process. The stages in this process are warehousing of merchandise range, secure ordering centre web interface, managing merchandise assortments chapter, merchandise planning systems chapter.
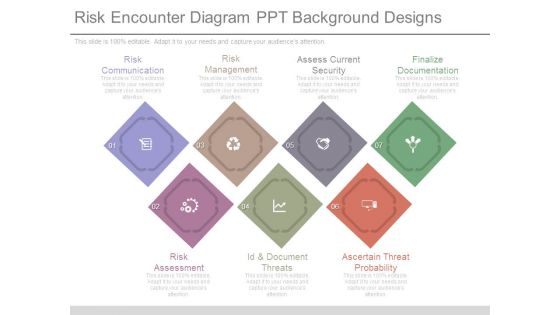
Risk Encounter Diagram Ppt Background Designs
This is a risk encounter diagram ppt background designs. This is a seven stage process. The stages in this process are risk communication, risk management, assess current security, finalize documentation, risk assessment, id and document threats, ascertain threat probability.
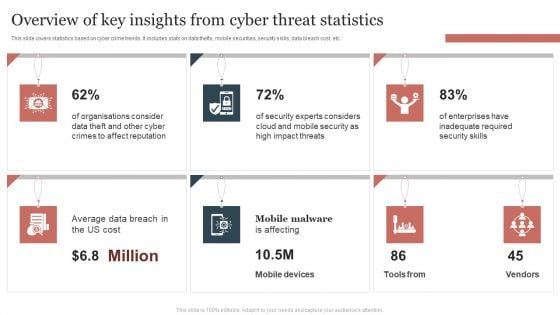
Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
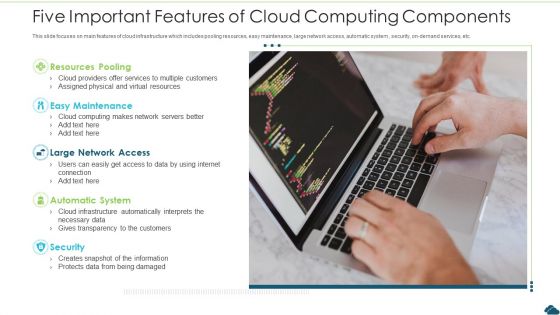
Five Important Features Of Cloud Computing Components Inspiration PDF
This slide focuses on main features of cloud infrastructure which includes pooling resources, easy maintenance, large network access, automatic system , security, on-demand services, etc. Presenting five important features of cloud computing components inspiration pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including resources pooling, easy maintenance, large network access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Warehousing Process For Managing Supply Chain Management Template PDF
This slide focuses on the several warehousing services for managing supply chain process which includes receiving, put-away, picking, packing, dispatching and product returning which helps in effective warehouse management. Presenting Warehousing Process For Managing Supply Chain Management Template PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Determining, Quality Assurance, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
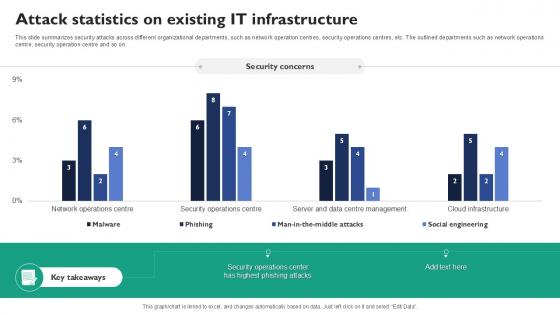
Attack Statistics On Existing It Infrastructure Corrective Regression Testing Ppt Slides
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Existing It Infrastructure Corrective Regression Testing Ppt Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
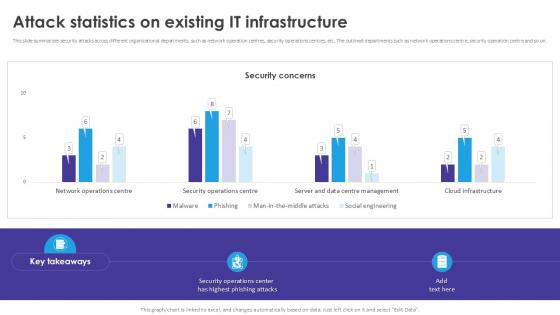
Attack Statistics On Existing Automated Regression Testing And Achieving PPT Slide
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Existing Automated Regression Testing And Achieving PPT Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
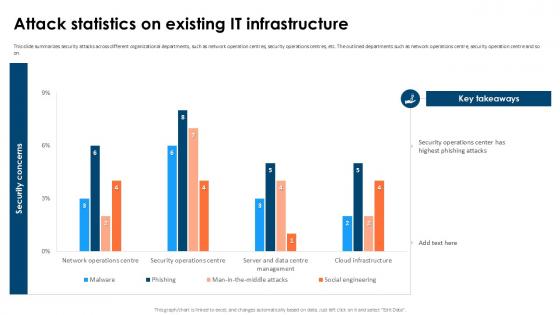
Attack Statistics On Partial Regression Testing For A Best PPT Slide
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Partial Regression Testing For A Best PPT Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
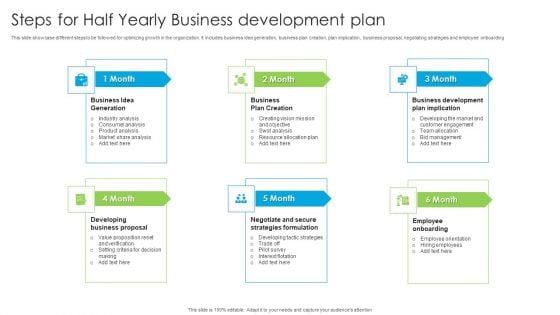
Steps For Half Yearly Business Development Plan Ppt PowerPoint Presentation Layout PDF
This slide showcase different steps to be followed for optimizing growth in the organization. It includes business idea generation, business plan creation, plan implication, business proposal, negotiating strategies and employee onboarding.Presenting Steps For Half Yearly Business Development Plan Ppt PowerPoint Presentation Layout PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Business Idea, Developing Business, Negotiate Secure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Optimization Of IoT Remote Monitoring Factors To Consider While Selecting IoT Monitoring Devices IoT SS V
This slide provides an overview of the consideration factors for choosing IoT devices. Major factors covered are security and compliance, user-friendly interface, maintenance service, budget and deployment. Are you searching for a Optimization Of IoT Remote Monitoring Factors To Consider While Selecting IoT Monitoring Devices IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Optimization Of IoT Remote Monitoring Factors To Consider While Selecting IoT Monitoring Devices IoT SS V from Slidegeeks today. This slide provides an overview of the consideration factors for choosing IoT devices. Major factors covered are security and compliance, user-friendly interface, maintenance service, budget and deployment.
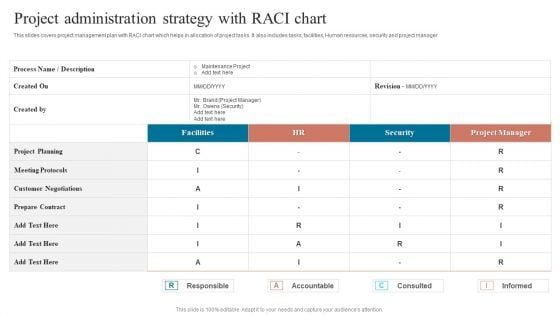
Project Administration Strategy With Raci Chart Rules PDF
This slides covers project management plan with RACI chart which helps in allocation of project tasks. It also includes tasks, facilities, Human resources, security and project manager. Showcasing this set of slides titled Project Administration Strategy With Raci Chart Rules PDF. The topics addressed in these templates are Meeting Protocols, Customer Negotiations, Meeting Protocols. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

 Home
Home