Safety Management Strategy Ppt

International Organization Standardization 270001 Performance Indicators To Measure Information Security Controls Clipart PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this international organization standardization 270001 performance indicators to measure information security controls clipart pdf. Use them to share invaluable insights on information security policy, information security training, incident response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
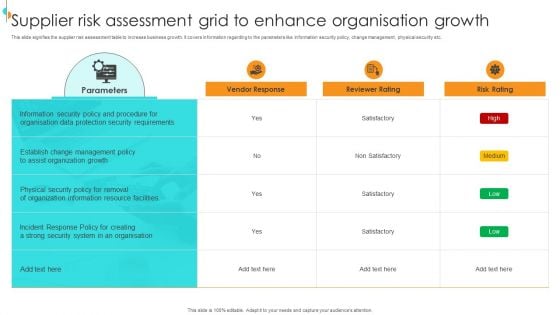
Supplier Risk Assessment Grid To Enhance Organisation Growth Download PDF
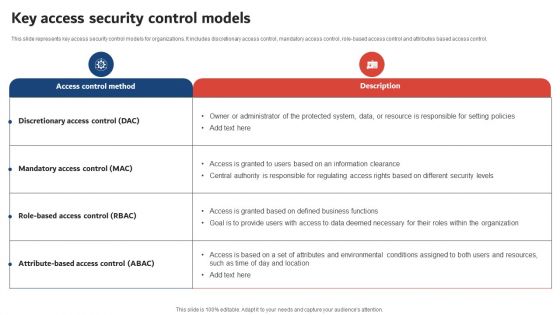
Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF
This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Do you know about Slidesgeeks Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
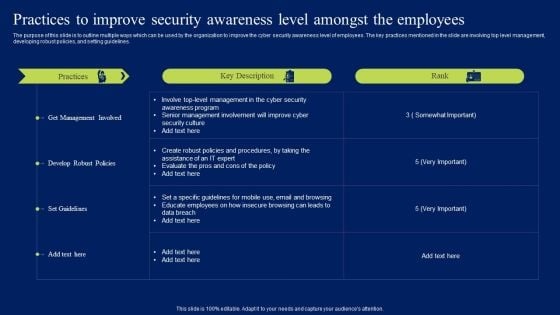
Practices To Improve Security Awareness Level Amongst The Employees Portrait PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Practices To Improve Security Awareness Level Amongst The Employees Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Practices To Improve Security Awareness Level Amongst The Employees Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
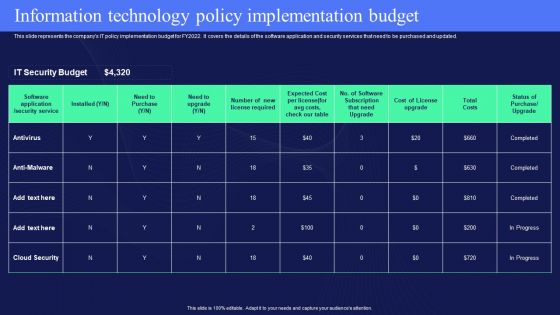
IT Policies And Procedures Information Technology Policy Implementation Budget Template PDF
This slide represents the companys IT policy implementation budget for FY2022. It covers the details of the software application and security services that need to be purchased and updated. This modern and well-arranged IT Policies And Procedures Information Technology Policy Implementation Budget Template PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Guidelines To Successfully Develop Flexible Work Policy Professional PDF
The following slide showcases important instructions related to the work from home WFH policy that can assist corporates to draft rules and regulations for remote employees. It contains information about security protocols, online meeting etiquette, expenditure, and team building activities. Welcome to our selection of the Guidelines To Successfully Develop Flexible Work Policy Professional PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
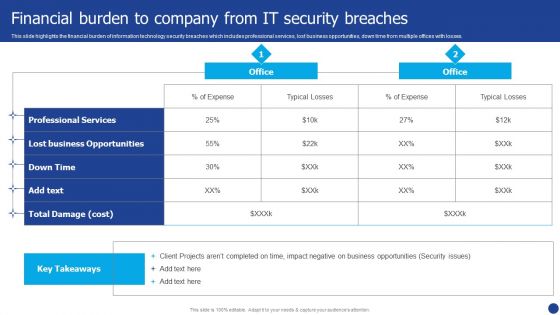
Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF. Use them to share invaluable insights on Professional Services, Lost Business Opportunities, Expense and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
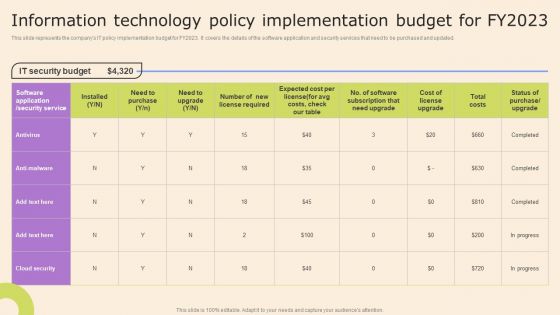
Information Technology Policy Processes Information Technology Policy Implementation Budget Fy2023 Pictures PDF
This slide represents the companys IT policy implementation budget for FY2023. It covers the details of the software application and security services that need to be purchased and updated. Create an editable Information Technology Policy Processes Information Technology Policy Implementation Budget Fy2023 Pictures PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Information Technology Policy Processes Information Technology Policy Implementation Budget Fy2023 Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
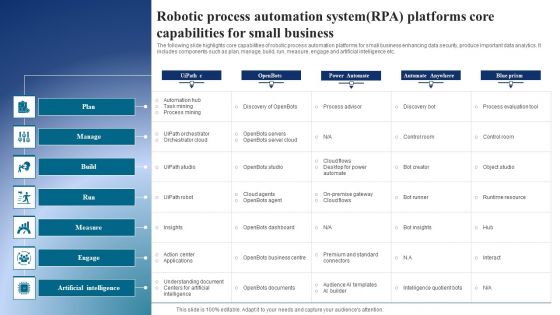
Robotic Process Automation Systemrpa Platforms Core Capabilities For Small Business Structure PDF
The following slide highlights core capabilities of robotic process automation platforms for small business enhancing data security, produce important data analytics. It includes components such as plan, manage, build, run, measure, engage and artificial intelligence etc. Showcasing this set of slides titled Robotic Process Automation Systemrpa Platforms Core Capabilities For Small Business Structure PDF. The topics addressed in these templates are Plan, Manage, Build . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
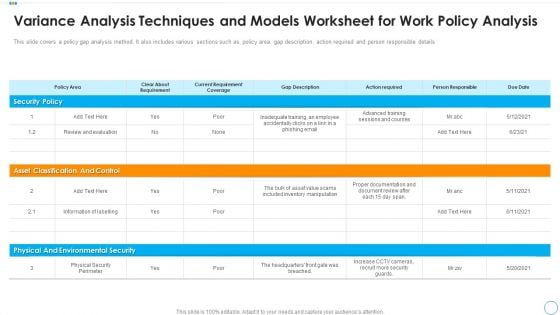
Variance Analysis Techniques And Models Worksheet For Work Policy Analysis Pictures PDF
This slide covers a policy gap analysis method. It also includes various sections such as, policy, gap desareacription, action required and person responsible details. Pitch your topic with ease and precision using this variance analysis techniques and models worksheet for work policy analysis pictures pdf. This layout presents information on security policy, asset classification and control, physical and environmental security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
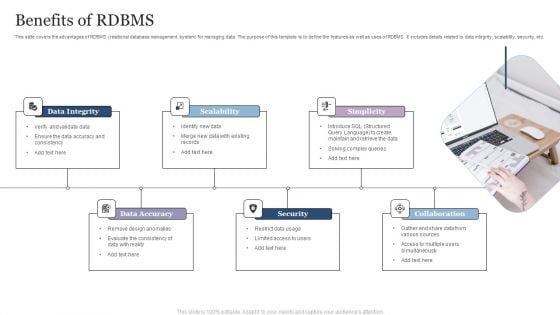
Benefits Of RDBMS Summary PDF
This slide covers the advantages of RDBMS relational database management system for managing data. The purpose of this template is to define the features as well as uses of RDBMS. It includes details related to data integrity, scalability, security, etc.Persuade your audience using this v. This PPT design covers Six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Integrity, Scalability, Simplicity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organization Project Transition Plan For Commercialization Elements PDF
This slide covers project transition plan which includes technical security, portfolio program project, service, commercialization of project. Showcasing this set of slides titled Organization Project Transition Plan For Commercialization Elements PDF. The topics addressed in these templates are Portfolio Programmer Project, Service, Commercial, Organizational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
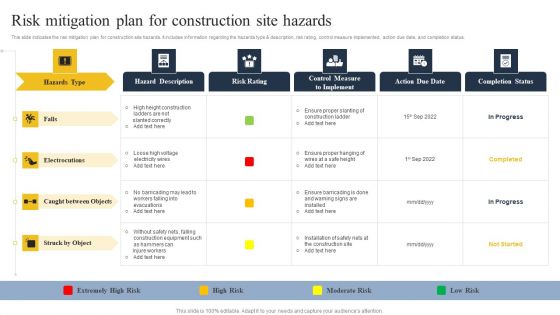
Security Control Techniques For Real Estate Project Risk Mitigation Plan For Construction Site Hazards Microsoft PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Security Control Techniques For Real Estate Project Risk Mitigation Plan For Construction Site Hazards Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cyber Security Administration In Organization Contingency Plan For Cyber Threat Handling Brochure PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver an awe inspiring pitch with this creative cyber security administration in organization contingency plan for cyber threat handling brochure pdf bundle. Topics like contingency, implementation, components, documentation, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
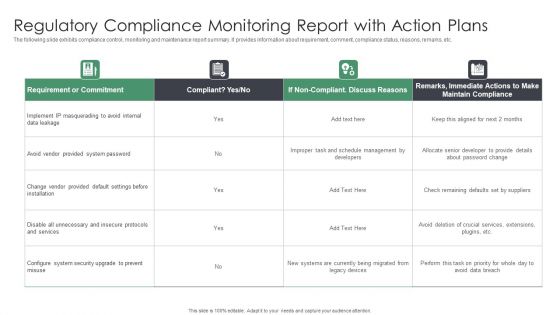
Regulatory Compliance Monitoring Report With Action Plans Download PDF
The following slide exhibits compliance control, monitoring and maintenance report summary. It provides information about requirement, comment, compliance status, reasons, remarks, etc. Showcasing this set of slides titled Regulatory Compliance Monitoring Report With Action Plans Download PDF. The topics addressed in these templates are Requirement Or Commitment, System, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workforce Security Realization Coaching Plan Security Training Program Frameworks Contd Rules PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks contd rules pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
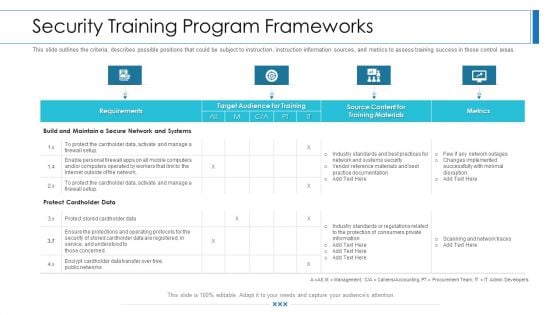
Workforce Security Realization Coaching Plan Security Training Program Frameworks Brochure PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks brochure pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
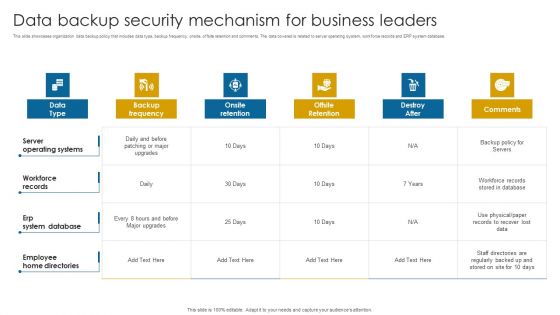
Data Backup Security Mechanism For Business Leaders Infographics PDF
This slide showcases organization data backup policy that includes data type, backup frequency, onsite, offsite retention and comments. The data covered is related to server operating system, workforce records and ERP system database.Showcasing this set of slides titled Data Backup Security Mechanism For Business Leaders Infographics PDF. The topics addressed in these templates are Operating Systems, Workforce Records, Employee Home Directories. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
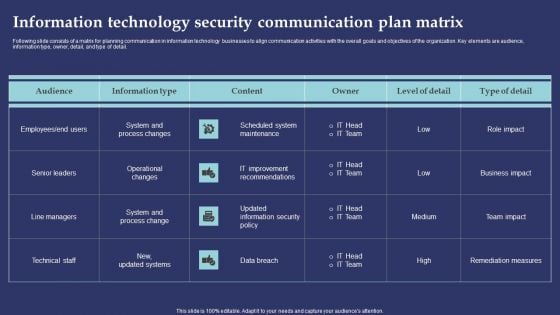
Information Technology Security Communication Plan Matrix Template PDF
Following slide consists of a matrix for planning communication in information technology businesses to align communication activities with the overall goals and objectives of the organization. Key elements are audience, information type, owner, detail, and type of detail. Showcasing this set of slides titled Information Technology Security Communication Plan Matrix Template PDF. The topics addressed in these templates are Scheduled System Maintenance, IT Improvement Recommendations, Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
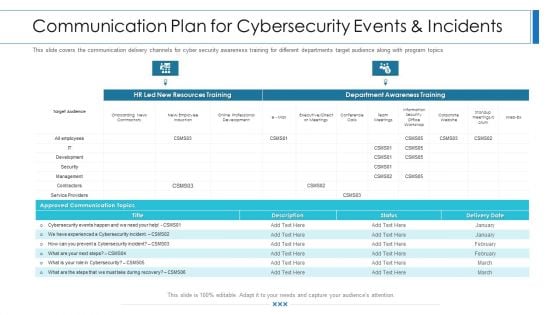
Workforce Security Realization Coaching Plan Communication Plan For Cybersecurity Events And Incidents Graphics PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan communication plan for cybersecurity events and incidents graphics pdf bundle. Topics like resources training, department awareness training, approved communication topics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF Use them to share invaluable insights on Accessible Within Organization, Individual System, Accessible To Key Shareholders and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
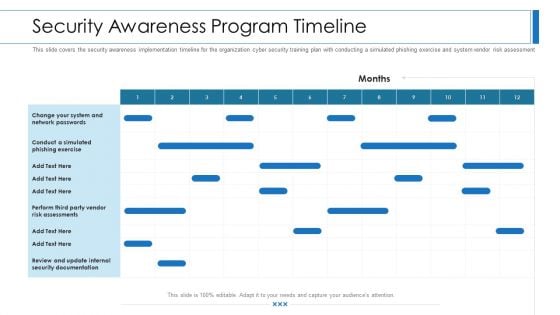
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
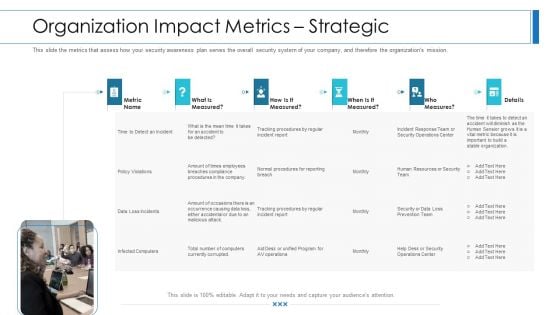
Workforce Security Realization Coaching Plan Organization Impact Metrics Strategic Infographics PDF
This slide the metrics that assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan organization impact metrics strategic infographics pdf. Use them to share invaluable insights on organization impact metrics strategicand impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
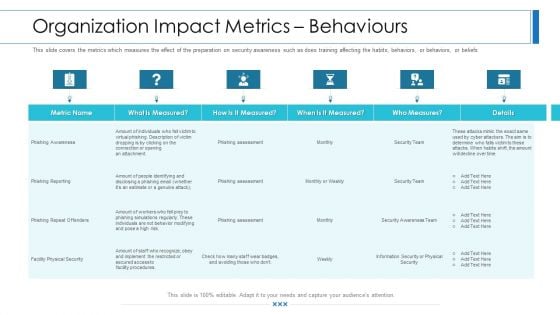
Workforce Security Realization Coaching Plan Organization Impact Metrics Behaviours Infographics PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization impact metrics behaviours infographics pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF
This slide showcases distinguish between bring your own device and choose your own device policies and programs for mobile devices. It also includes differentiation on basis such as benefits , challenges, etc. Pitch your topic with ease and precision using this Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF. This layout presents information on Basis, Benefits, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Implementing Adaptive Work Arrangements Guidelines To Successfully Develop Flexible Work Policy Pictures PDF
The following slide showcases important instructions related to the work from home WFH policy that can assist corporates to draft rules and regulations for remote employees. It contains information about security protocols, online meeting etiquette, expenditure, and team building activities. This modern and well arranged Implementing Adaptive Work Arrangements Guidelines To Successfully Develop Flexible Work Policy Pictures PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
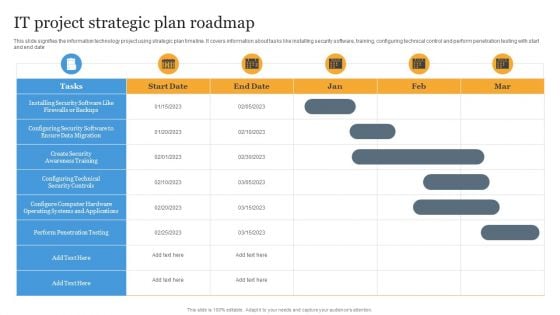
IT Project Strategic Plan Roadmap Ideas PDF
This slide signifies the information technology project using strategic plan timeline. It covers information about tasks like installing security software, training, configuring technical control and perform penetration testing with start and end date Showcasing this set of slides titled IT Project Strategic Plan Roadmap Ideas PDF. The topics addressed in these templates are Roadmap, Project, Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workforce Security Realization Coaching Plan Automated Security Awareness Platform And Cost Elements PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan automated security awareness platform and cost elements pdf bundle. Topics like platform, functioning, benefits, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
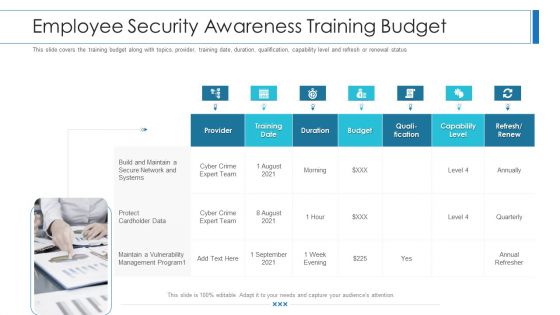
Workforce Security Realization Coaching Plan Employee Security Awareness Training Budget Summary PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan employee security awareness training budget summary pdf bundle. Topics like training date, duration, budget, capability level, qualification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
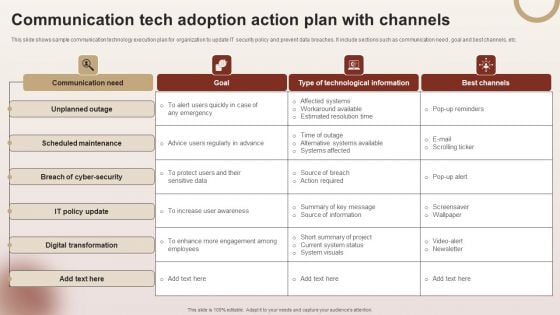
Communication Tech Adoption Action Plan With Channels Ideas PDF
This slide shows sample communication technology execution plan for organization to update IT security policy and prevent data breaches. It include sections such as communication need , goal and best channels, etc. Showcasing this set of slides titled Communication Tech Adoption Action Plan With Channels Ideas PDF. The topics addressed in these templates are Goal, Technological Information, Best Channels. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
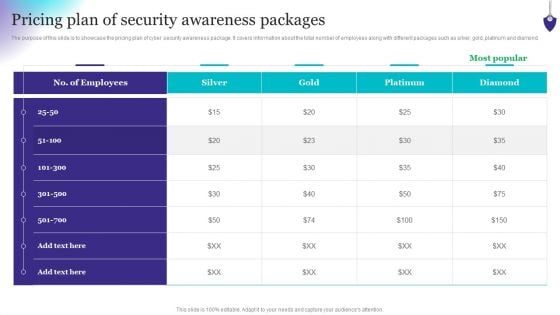
Organizing Security Awareness Pricing Plan Of Security Awareness Packages Diagrams PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Take your projects to the next level with our ultimate collection of Organizing Security Awareness Pricing Plan Of Security Awareness Packages Diagrams PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
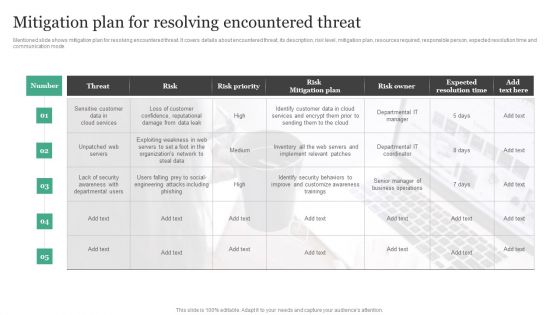
Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Slidegeeks has constructed Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
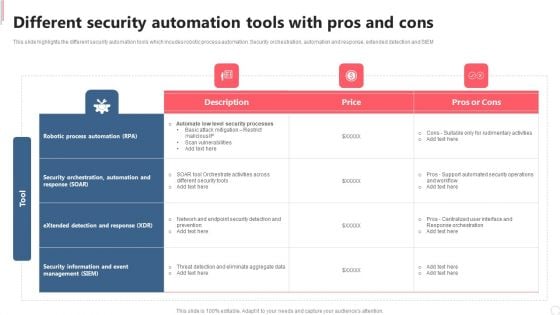
Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
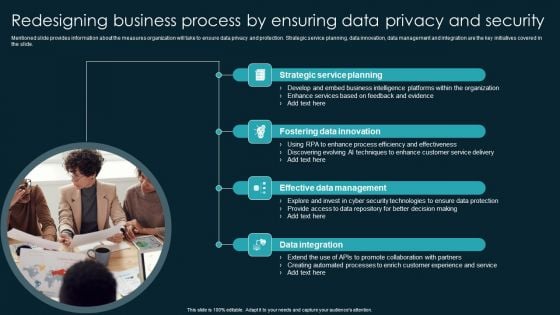
Redesigning Business Process By Ensuring Data Privacy And Security Infographics PDF
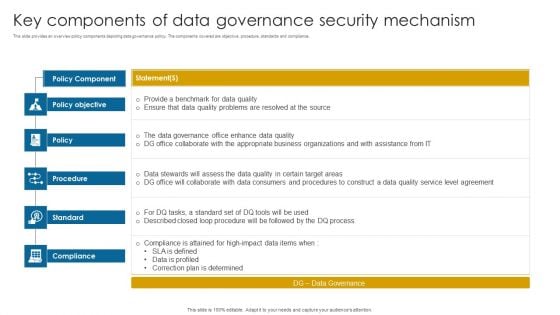
Key Components Of Data Governance Security Mechanism Information PDF
This slide provides an overview policy components depicting data governance policy. The components covered are objective, procedure, standards and compliance.Pitch your topic with ease and precision using this Key Components Of Data Governance Security Mechanism Information PDF. This layout presents information on Data Governance, Compliance Attained, Correction Determined. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Organization Compliance Metrics Hacking Prevention Awareness Training For IT Security Inspiration PDF
This slide covers the metrics that measure what you are doing with the awareness project, exactly how you will train and how. Such metrics are of particular importance for purposes of compliance and monitoring. Deliver and pitch your topic in the best possible manner with this organization compliance metrics hacking prevention awareness training for it security inspiration pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
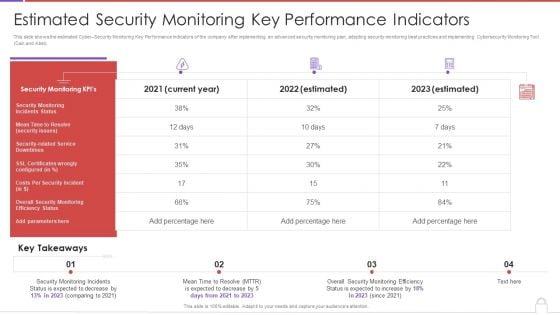
Methods To Develop Advanced Estimated Security Monitoring Key Performance Indicators Structure PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver an awe inspiring pitch with this creative methods to develop advanced estimated security monitoring key performance indicators structure pdf bundle. Topics like security monitoring kpis, costs per security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
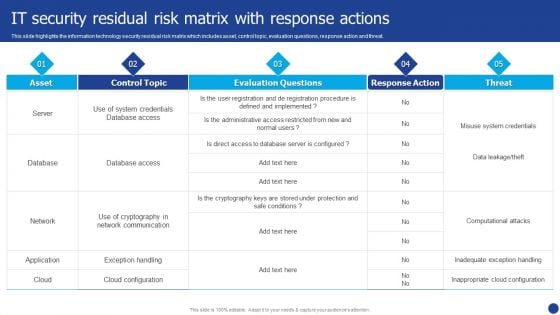
Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cybersecurity Guidelines IT Information Technology Policy Implementation Budget For FY2022 Icons PDF
This slide represents the companys IT policy implementation budget for FY2022. It covers the details of the software application and security services that need to be purchased and updated. This Cybersecurity Guidelines IT Information Technology Policy Implementation Budget For FY2022 Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cybersecurity Guidelines IT Information Technology Policy Implementation Budget For FY2022 Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
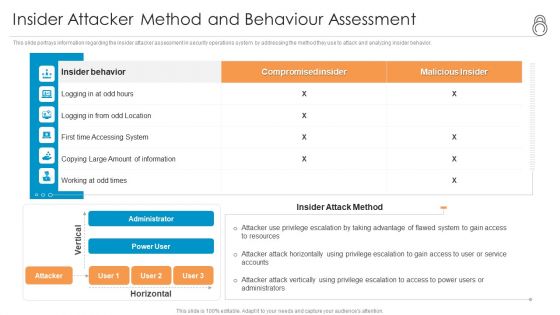
Enhanced Protection Corporate Event Administration Insider Attacker Method And Behaviour Assessment Topics PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration insider attacker method and behaviour assessment topics pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Collaboration Plan Key Activities Information PDF
This slide presents a schedule timeline for tracking and monitoring key activities in order to successful completion of project. Its key tasks includes combined event action plan, short term security generation, competitive intelligence processes, branding, linking contacts in datasets, etc. Showcasing this set of slides titled Business Collaboration Plan Key Activities Information PDF. The topics addressed in these templates are Branding, Acquisition Positioning, Partners Communication, Short Term Security Generation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
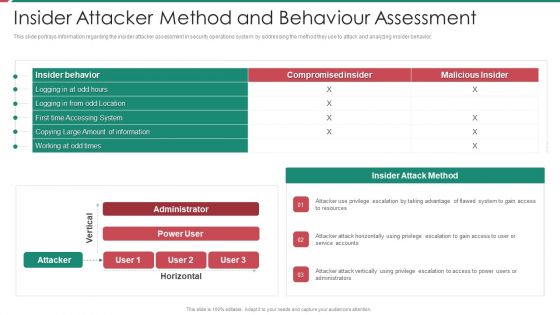
Security And Process Integration Insider Attacker Method And Behaviour Assessment Microsoft PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security and process integration insider attacker method and behaviour assessment microsoft pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
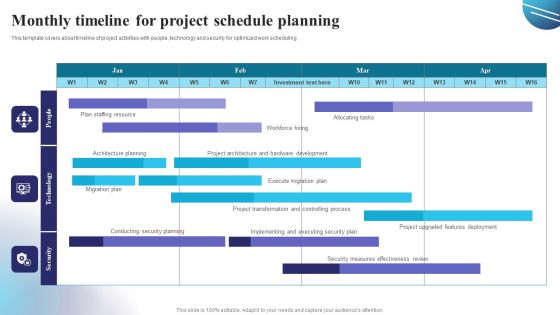
Monthly Timeline For Project Schedule Planning Guidelines PDF
This template covers about timeline of project activities with people, technology and security for optimized work scheduling. Showcasing this set of slides titled Monthly Timeline For Project Schedule Planning Guidelines PDF. The topics addressed in these templates are Project Transformation, Security Plan, Migration Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
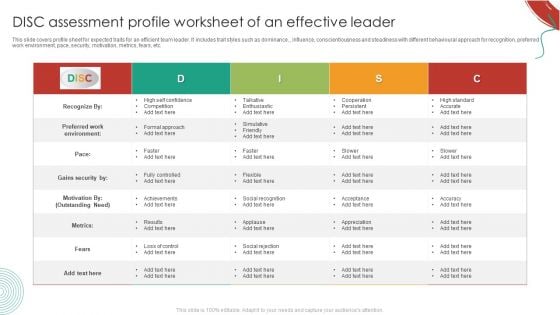
DISC Assessment Profile Worksheet Of An Effective Leader Rules PDF
This slide covers profile sheet for expected traits for an efficient team leader. It includes trait styles such as dominance, , influence, conscientiousness and steadiness with different behavioural approach for recognition, preferred work environment, pace, security, motivation, metrics, fears, etc. Showcasing this set of slides titled DISC Assessment Profile Worksheet Of An Effective Leader Rules PDF. The topics addressed in these templates are Metrics, Preferred Work Environment, High Self Confidence. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets.Are you searching for a Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF from Slidegeeks today.
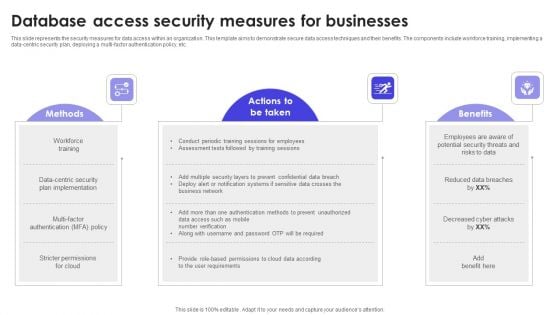
Database Access Security Measures For Businesses Portrait PDF
This slide represents the security measures for data access within an organization. This template aims to demonstrate secure data access techniques and their benefits. The components include workforce training, implementing a data-centric security plan, deploying a multi-factor authentication policy, etc. Pitch your topic with ease and precision using this Database Access Security Measures For Businesses Portrait PDF. This layout presents information on Methods, Benefits, Actions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. This Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
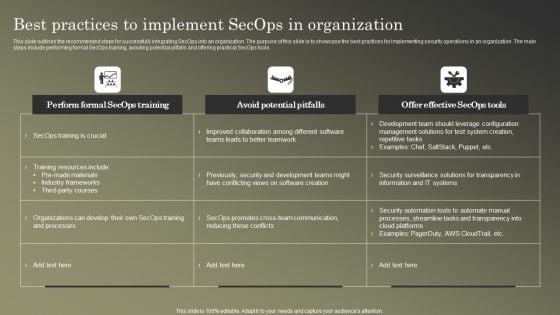
Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF
This slide outlines the recommended steps for successfully integrating SecOps into an organization. The purpose of this slide is to showcase the best practices for implementing security operations in an organization. The main steps include performing formal SecOps training, avoiding potential pitfalls and offering practical SecOps tools. Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
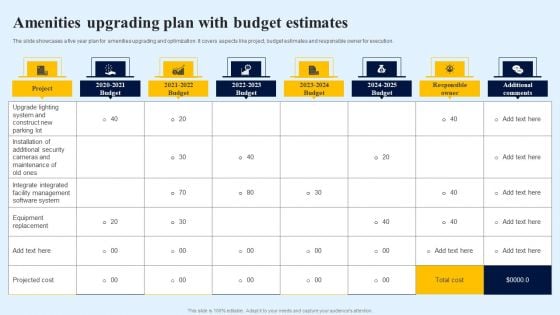
Amenities Upgrading Plan With Budget Estimates Graphics PDF
The slide showcases a five year plan for amenities upgrading and optimization. It covers aspects like project, budget estimates and responsible owner for execution. Showcasing this set of slides titled Amenities Upgrading Plan With Budget Estimates Graphics PDF. The topics addressed in these templates are Upgrade Lighting System, Construct New Parking Lot, Installation Additional Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
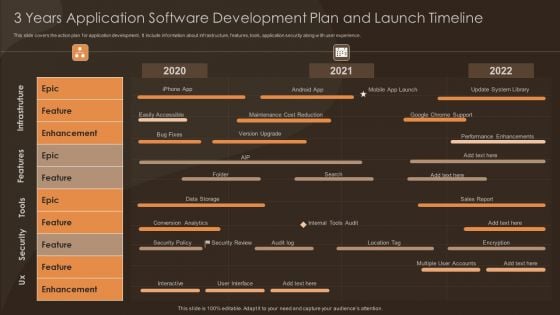
3 Years Application Software Development Plan And Launch Timeline Themes PDF
This slide covers the action plan for application development. It include information about infrastructure, features, tools, application security along with user experience. Showcasing this set of slides titled 3 Years Application Software Development Plan And Launch Timeline Themes PDF. The topics addressed in these templates are Security, Enhancement, Internal Tools Audit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Software Company Investor Funding Pitch Deck Quotes Background PDF
This Security Software Company Investor Funding Pitch Deck Quotes Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Enhanced Protection Corporate Event Administration Contingency Plan For Threat Handling Icons PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration contingency plan for threat handling icons pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
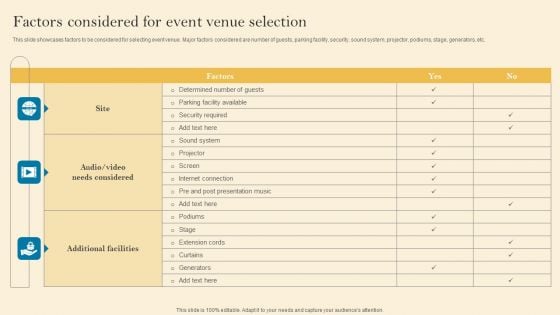
Product Inauguration Event Planning And Administration Factors Considered For Event Diagrams PDF
This slide showcases factors to be considered for selecting event venue. Major factors considered are number of guests, parking facility, security, sound system, projector, podiums, stage, generators, etc. There are so many reasons you need a Product Inauguration Event Planning And Administration Factors Considered For Event Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Chief Information Officers Guide On Technology Plan Strategic IT Infrastructure Augmentation Designs PDF
This slide provides information regarding the strategic IT infrastructure augmentation roadmap. The focus areas include testing, improvement, integration and security, etc. Explore a selection of the finest Chief Information Officers Guide On Technology Plan Strategic IT Infrastructure Augmentation Designs PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Chief Information Officers Guide On Technology Plan Strategic IT Infrastructure Augmentation Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Analyzing The Impact Of Security Threats On Organization Elements PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets .Deliver and pitch your topic in the best possible manner with this Analyzing The Impact Of Security Threats On Organization Elements PDF. Use them to share invaluable insights on Security Threats, Impact Organization, Average Financial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF bundle. Topics like Implement Information, Security Policies, Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF. Use them to share invaluable insights on Security And Compliance, SAML Authentication, Data Subject Requests and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
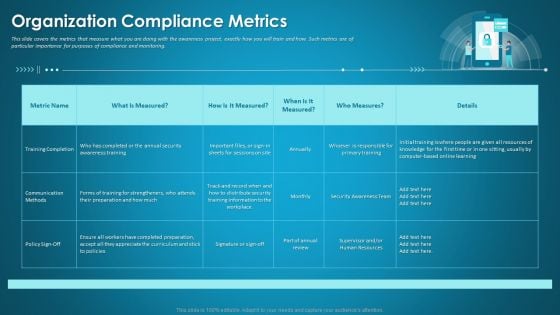
Organizational Network Security Awareness Staff Learning Organization Compliance Metrics Introduction PDF
This slide covers the metrics that measure what you are doing with the awareness project, exactly how you will train and how. Such metrics are of particular importance for purposes of compliance and monitoring. Deliver an awe inspiring pitch with this creative organizational network security awareness staff learning organization compliance metrics introduction pdf bundle. Topics like training completion, communication methods, security training information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































