Safety Management Strategy Ppt

Detailed Analysis Of Cobots Why Should Organizations Invest In Cobots Clipart PDF
This slide describes the reasons for organizations to invest in cobots. It includes low-cost, safety, flexibility, more straightforward automation for all sizes of organizations, and is designed to work in a shared environment. Find highly impressive Detailed Analysis Of Cobots Why Should Organizations Invest In Cobots Clipart PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Detailed Analysis Of Cobots Why Should Organizations Invest In Cobots Clipart PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.

Incorporating HIS To Enhance Healthcare Services Analysis Of Current Scenario Before HIS Implementation Structure PDF
This slide covers requirement of effective health information system in healthcare services. It involves key benefits such as organized treatment process, improved patient safety, minimized operational expense and improved patient satisfaction. Create an editable Incorporating HIS To Enhance Healthcare Services Analysis Of Current Scenario Before HIS Implementation Structure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Incorporating HIS To Enhance Healthcare Services Analysis Of Current Scenario Before HIS Implementation Structure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
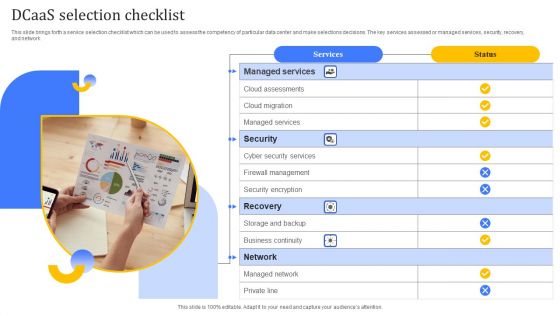
Dcaas Selection Checklist Summary PDF
This slide brings forth a service selection checklist which can be used to assess the competency of particular data center and make selections decisions. The key services assessed or managed services, security, recovery, and network. Presenting Dcaas Selection Checklist Summary PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Managed Services, Security, Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Risk Administration Plan Table Of Contents Topics PDF
This is a Cybersecurity Risk Administration Plan Table Of Contents Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing The Risk, Defining Risk Level, Setting Scenario For Security Control You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Our Business Approach Diagrams PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. This is a Security Agency Business Profile Our Business Approach Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategic Planning, Participatory Management, Productivity Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
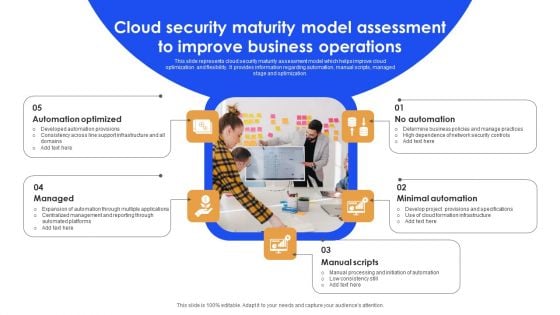
Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF
This slide represents cloud security maturity assessment model which helps improve cloud optimization and flexibility. It provides information regarding automation, manual scripts, managed stage and optimization. Persuade your audience using this Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Automation Optimized, Minimal Automation, Manual Scripts. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Project Tracking Risk Tracker Matrix Themes PDF
The following slide depicts the risk assessment matrix of project tracking to manage uncertain activities and improve decision making. It includes activities such as assessment, configuration, advancement, security check and dispose etc. Persuade your audience using this Project Tracking Risk Tracker Matrix Themes PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Project Tracking Risk, Tracker Matrix. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Implementing Effective Ecommerce Managemnet Platform Challenges Faced By Ecommerce Marketing Topics PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. There are so many reasons you need a Implementing Effective Ecommerce Managemnet Platform Challenges Faced By Ecommerce Marketing Topics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
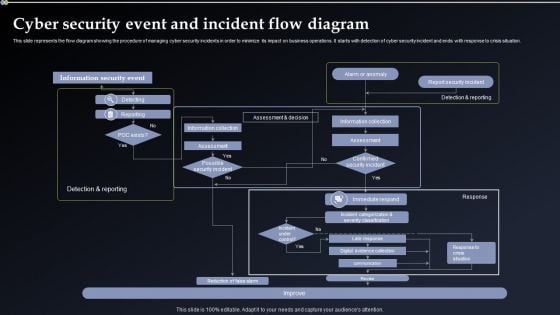
Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Welcome to our selection of the Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. This Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
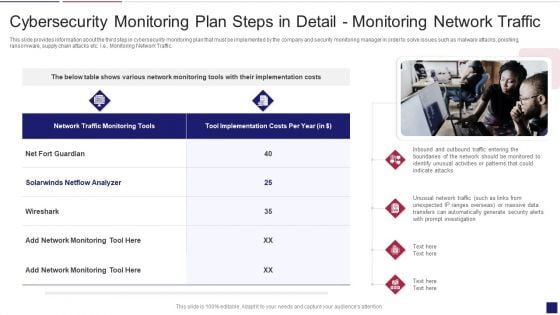
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Crucial Measures For Devops Success Contd Formats PDF
This slide provides information regarding crucial measures for DevOps success in terms of focus on configuration management, considering policy as a code. This is a determine crucial measures for devops success contd formats pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, management, quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
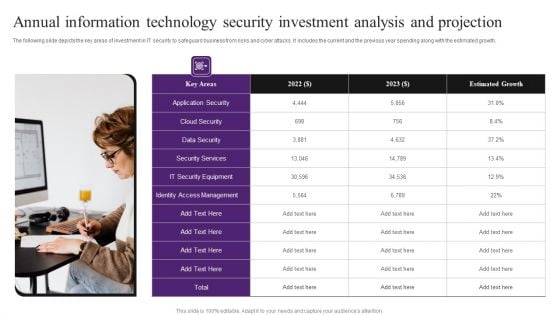
Annual Information Technology Security Investment Analysis And Projection Portrait PDF
The following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Presenting Annual Information Technology Security Investment Analysis And Projection Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cloud Security, Security Services, Identity Access Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
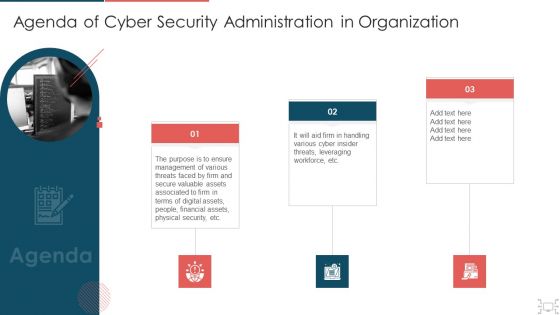
Agenda Of Cyber Security Administration In Organization Information PDF
This is a agenda of cyber security administration in organization information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda, purpose, management, valuable, assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Project Security Administration IT Diagrams PDF
This is a agenda for project security administration it diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, management, implemented, security center, improvement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Company Vulnerability Administration Introduction Designs PDF
Presenting company vulnerability administration introduction designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like need for vulnerability management, vulnerability management model, vulnerability management levels, overview. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
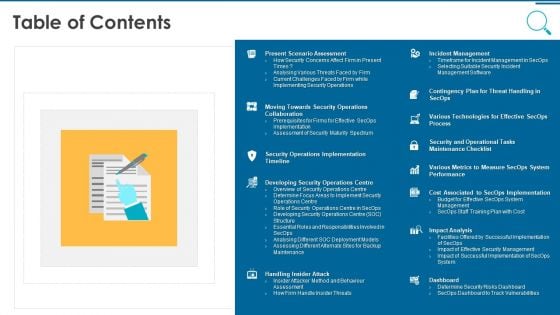
Information And Technology Security Operations Table Of Contents Pictures PDF
This is a information and technology security operations table of contents pictures pdf template with various stages. Focus and dispense information on thirteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, implementation, analysis, technologies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Evaluation Of HR Security Policy And Procedure Diagrams PDF
Persuade your audience using this Evaluation Of HR Security Policy And Procedure Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluation HR Security, Policy Procedure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
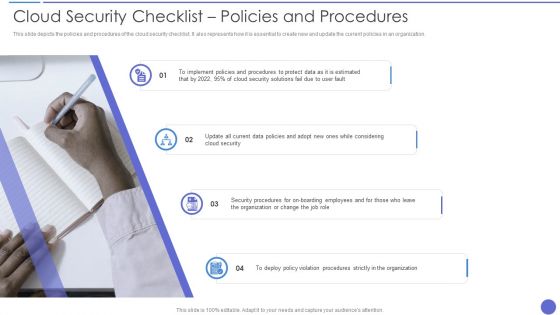
Cloud Security Checklist Policies And Procedures Rules PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. This is a Cloud Security Checklist Policies And Procedures Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Organization, Security Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it nowC

Information Technology Policy And Processes Information Security Policy For Employees Structure PDF
This slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Technology Policy And Processes Information Security Policy For Employees Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Web App Firewall Services IT Features Of WAF Application Vulnerability Prevention Information PDF
This slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Presenting web app firewall services it features of waf application vulnerability prevention information pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management, security, application, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Intelligent Infrastructure Capabilities For Digital Business Table Of Contents Introduction PDF
Presenting Intelligent Infrastructure Capabilities For Digital Business Table Of Contents Introduction PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Improved Security Standards, Facilities Offered, Timeframe for Incident Management, Security Centre. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Policies And Procedures Information Security Policy For Employees Download PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Policies And Procedures Information Security Policy For Employees Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Policies And Procedures Information Security Policy For Employees Download PDF.
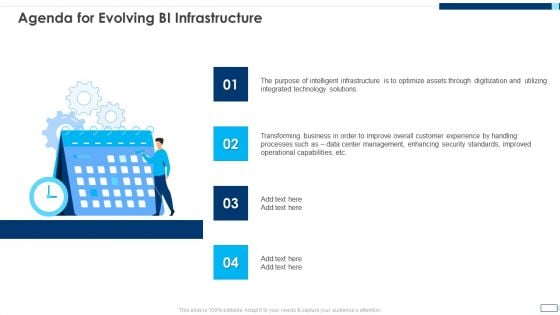
Agenda For Evolving BI Infrastructure Professional PDF
This is a agenda for evolving bi infrastructure professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like operational capabilities, enhancing security standards, data center management, business, integrated technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
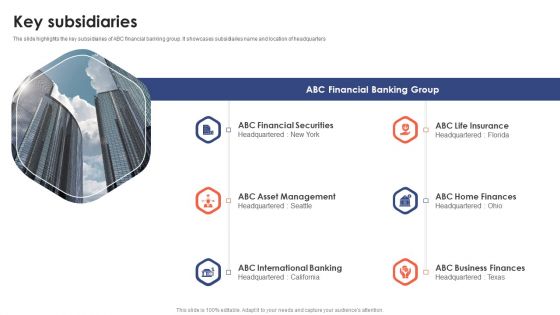
Banking Institution Company Profile Key Subsidiaries Background PDF
This is a Banking Institution Company Profile Key Subsidiaries Background PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Financial Securities, Asset Management, International Banking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Deploying Automation In Logistics And Supply Chain Summary PDF
This is a Agenda For Deploying Automation In Logistics And Supply Chain Summary PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Logistics Management, Business And Technology, Secured Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Assessment Of Cloud And Traditional Integrating Cloud Computing To Enhance Projects Effectiveness Mockup PDF
The following slide showcases comparative analysis of cloud and traditional project management. It provides information about capital expenditure, scalability, efficiency, real time information, security, fixes, etc. There are so many reasons you need a Comparative Assessment Of Cloud And Traditional Integrating Cloud Computing To Enhance Projects Effectiveness Mockup PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
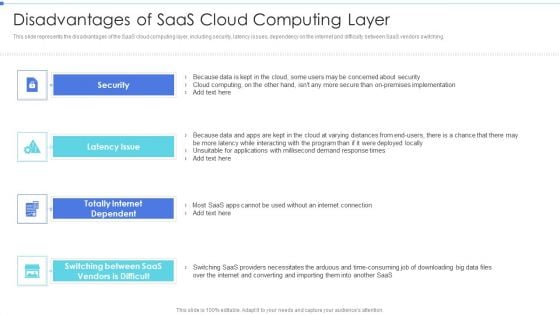
Cloud Based Service Models Disadvantages Of Saas Cloud Computing Layer Designs PDF
This slide depicts the factors such as cloud security, cloud compliance, service levels, architecture, manageability, costs, and support to choose the right cloud service provider.Presenting Cloud Based Service Models Disadvantages Of Saas Cloud Computing Layer Designs PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Cloud Security, Manageability, Architecture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
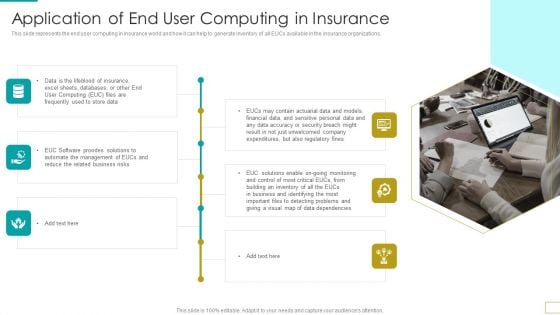
Computer Virtualization Application Of End User Computing In Insurance Demonstration PDF
This slide represents the end user computing in insurance world and how it can help to generate inventory of all EUCs available in the insurance organizations.This is a Computer Virtualization Application Of End User Computing In Insurance Demonstration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Provides Solutions, Automate Management, Accuracy Or Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Implement Cloud Collaboration Comparative Assessment Of Cloud And Traditional Project Structure PDF
The following slide showcases comparative analysis of cloud and traditional project management. It provides information about capital expenditure, scalability, efficiency, real time information, security, fixes, etc. Presenting How To Implement Cloud Collaboration Comparative Assessment Of Cloud And Traditional Project Structure PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Parameters Cloud, Capital Expenditure, Real Time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Role Based Access Control RBAC Securities Icon Demonstration PDF
Persuade your audience using this Role Based Access Control RBAC Securities Icon Demonstration PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Role Based, Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
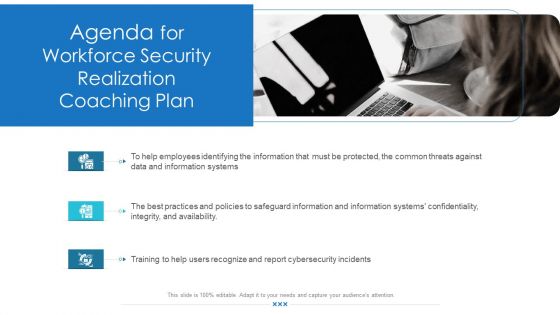
Workforce Security Realization Coaching Plan Agenda For Workforce Security Realization Coaching Plan Topics PDF
Presenting workforce security realization coaching plan agenda for workforce security realization coaching plan topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cybersecurity, information, information systems, threats, training. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
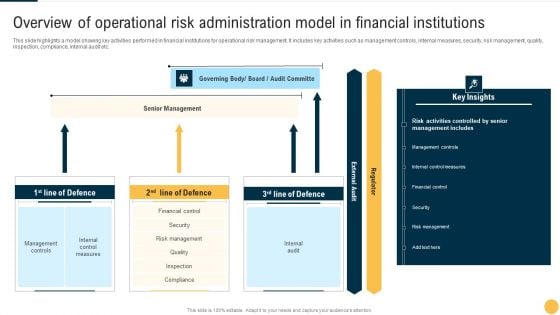
Overview Of Operational Risk Administration Model In Financial Institutions Microsoft PDF
This slide highlights a model showing key activities performed in financial institutions for operational risk management. It includes key activities such as management controls, internal measures, security, risk management, quality, inspection, compliance, internal audit etc. Showcasing this set of slides titled Overview Of Operational Risk Administration Model In Financial Institutions Microsoft PDF The topics addressed in these templates are Senior Management, Board, Key Insights. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
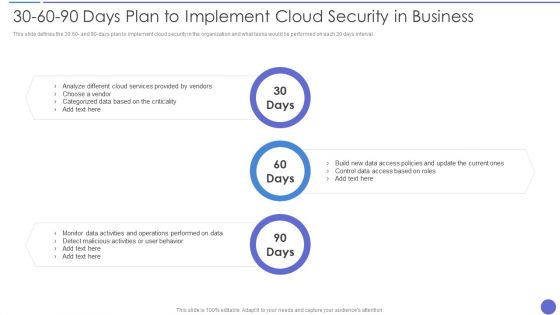
30 60 90 Days Plan To Implement Cloud Security In Business Information PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. This is a 30 60 90 Days Plan To Implement Cloud Security In Business Information PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyze, Cloud Services Provided , Control Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
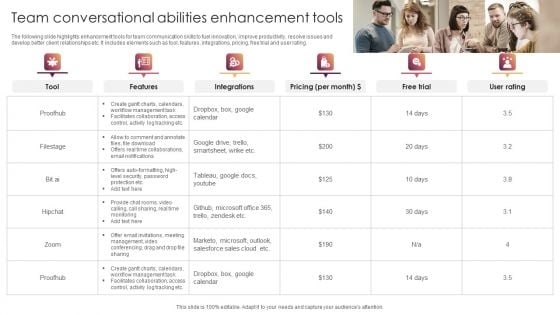
Team Conversational Abilities Enhancement Tools Demonstration PDF
The following slide highlights enhancement tools for team communication skills to fuel innovation, improve productivity, resolve issues and develop better client relationships etc. It includes elements such as tool, features, integrations, pricing, free trial and user rating. Presenting Team Conversational Abilities Enhancement Tools Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security, Password, Management, Salesforce Sales. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
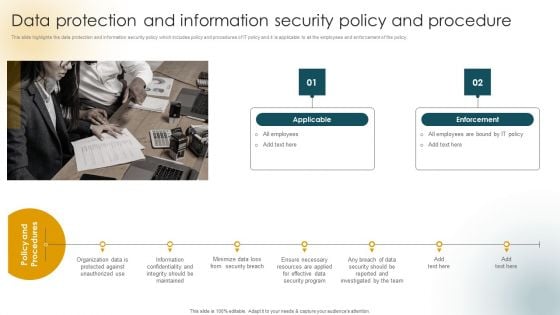
Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF
This is a Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
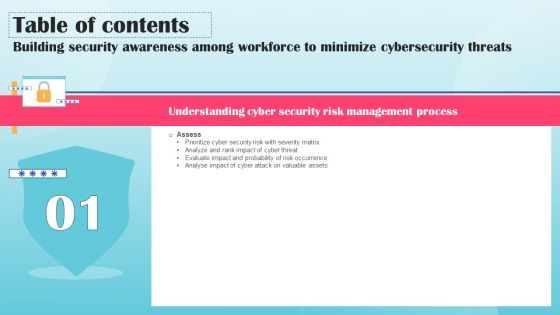
Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF
Boost your pitch with our creative Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
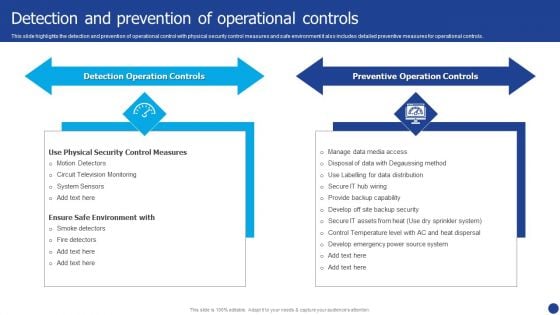
Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. This is a Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Detection Operation Controls, Preventive Operation Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT 30 60 90 Days Plan Ideas PDF
This is a project security administration it 30 60 90 days plan ideas pdf template with various stages. Focus and dispense information on threestages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF
Presenting Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Scenario Assessment, Security Capabilities, Overview Of Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
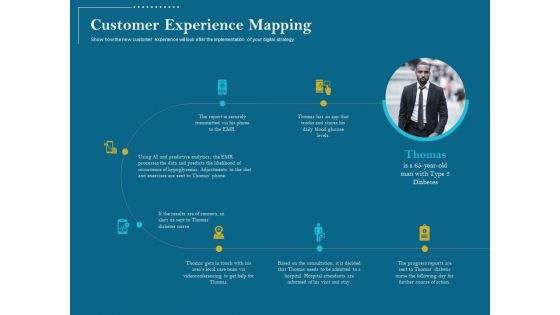
Utilizing Cyber Technology For Change Process Customer Experience Mapping Mockup PDF
Show how the new customer experience will look after the implementation of your digital strategy. This is a utilizing cyber technology for change process customer experience mapping mockup pdf. template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like thomas has an app that tracks and stores his daily blood glucose levels, if the results are of concern, an alert us sent to thomas diabetes nurse, the report is securely transmitted via his phone to the emr You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
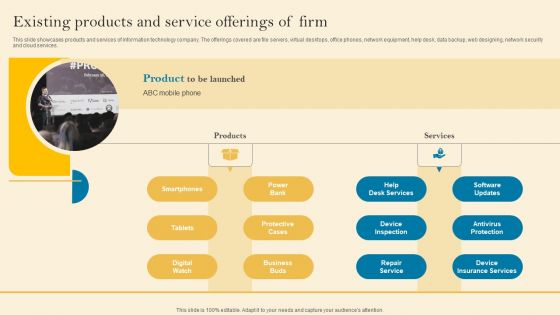
Product Inauguration Event Planning And Administration Existing Products And Service Guidelines PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Want to ace your presentation in front of a live audience Our Product Inauguration Event Planning And Administration Existing Products And Service Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Architecture Transformation Playbook Hybrid Or Semi Volumetric Construction Method Topics PDF
This slide provides information regarding hybrid or semi volumetric construction method as modern method of construction along with benefits associated to it. Presenting Architecture Transformation Playbook Hybrid Or Semi Volumetric Construction Method Topics PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Panel Systems, Secured Working Environment, Project Quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Workforce Security Realization Coaching Plan Ideas PDF
This is a table of contents for workforce security realization coaching plan ideas pdf template with various stages. Focus and dispense information on fourteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security awareness, tracking, communication plan, current scenario, training formats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Executing Devops Framework Global Devops Market Trends Themes PDF
Mentioned slide provides information about the trends of DevOps Market. Trends covered in the slide are Cloud-Native DevOps, Serverless Architecture, Security and DevSecOps. This is a Executing Devops Framework Global Devops Market Trends Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Undeterred Growth, Cloud Native DevOps, Rise Serverless Architecture, Enhanced Security and DevSecOps. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Google Cloud Features For Disaster Recovery Plan Clipart PDF
This slide represents the Google cloud features of the disaster recovery plan, and it includes global network, redundancy, scalability, security, and compliance. This is a Google Cloud Features For Disaster Recovery Plan Clipart PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Redundancy, Global Network, Programming Characterized Systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organization Impact Metrics Strategic Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Presenting organization impact metrics strategic hacking prevention awareness training for it security graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like organization, policy violations, data loss incidents, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
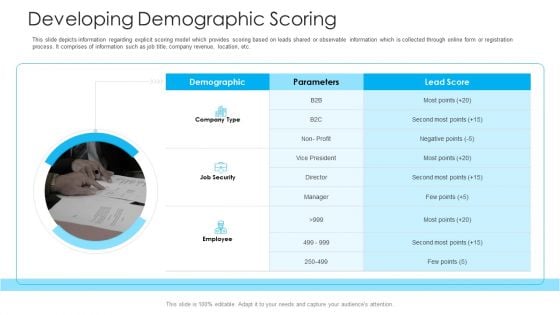
How To Build A Revenue Funnel Developing Demographic Scoring Sample PDF
This slide depicts information regarding explicit scoring model which provides scoring based on leads shared or observable information which is collected through online form or registration process. It comprises of information such as job title, company revenue, location, etc. This is a how to build a revenue funnel developing demographic scoring sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like demographic, parameters, job security, employee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
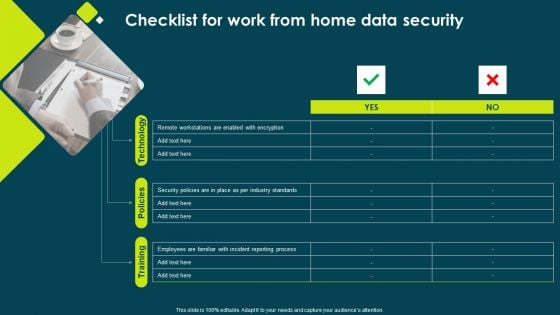
IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Roadmap To Implement Zero Trust Network Access Model Structure PDF
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Want to ace your presentation in front of a live audience Our Roadmap To Implement Zero Trust Network Access Model Structure PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Agenda For Information Security Risk Administration And Mitigation Plan Download PDF
Explore a selection of the finest Agenda For Information Security Risk Administration And Mitigation Plan Download PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Agenda For Information Security Risk Administration And Mitigation Plan Download PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
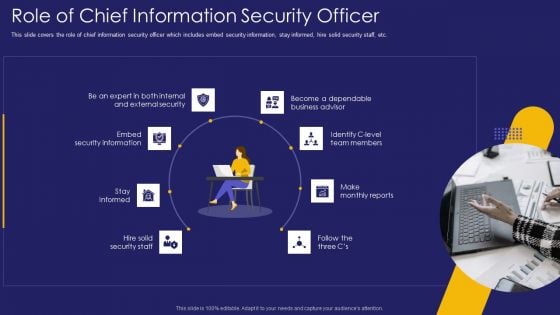
Role IT Team Digital Transformation Role Of Chief Information Security Officer Summary PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting role it team digital transformation role of chief information security officer summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like security information, security staff, monthly reports. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
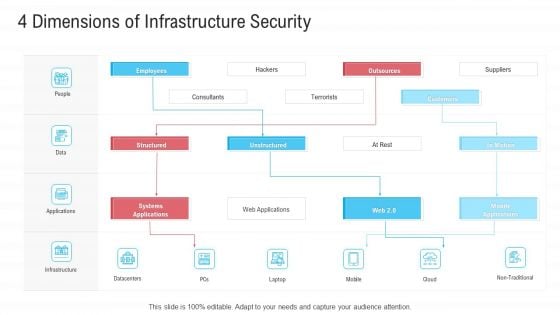
Infrastructure Designing And Administration 4 Dimensions Of Infrastructure Security Pictures PDF
This is a infrastructure designing and administration 4 dimensions of infrastructure security pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Risk Administration Plan Icon To Improve Cyber Security Project Summary PDF
Presenting Risk Administration Plan Icon To Improve Cyber Security Project Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk Administration Plan, Icon To Improve, Cyber Security, Project. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
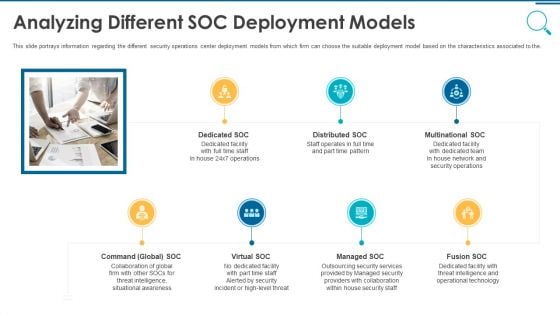
Information And Technology Security Operations Analyzing Different SOC Deployment Models Rules PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a information and technology security operations analyzing different soc deployment models rules pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF
Slidegeeks has constructed Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.


 Continue with Email
Continue with Email

 Home
Home


































